
Thursday, February 23: The Clark Library is closed today.

APA Style (7th Edition) Citation Guide: Books & Ebooks
- Introduction
- Journal Articles
- Magazine/Newspaper Articles
- Books & Ebooks
- Government & Legal Documents
- Biblical Sources
- Secondary Sources
- Films/Videos/TV Shows
- How to Cite: Other
- Additional Help
Table of Contents
Book In Print With One Author
Book in Print More Than One Author
Chapters, Short Stories, Essays, or Articles From a Book (Anthology or Collection)
Article in an online reference book (e.g. encyclopedias, dictionaries).
Note: All citations should be double spaced and have a hanging indent in a Reference List.
A "hanging indent" means that each subsequent line after the first line of your citation should be indented by 0.5 inches.
This Microsoft support page contains instructions about how to format a hanging indent in a paper.
Authors/Editors
An author won't necessarily be a person's name. It may be an organization or company, for example Health Canada. These are called group or corporate authors.
If a book has no author or editor, begin the citation with the book title, followed by the year of publication in round brackets.
If an author is also the publisher, omit the publisher from the reference. This happens most often with corporate or group authors.
When a book has one to 20 authors or editors, all authors' names are cited in the Reference List entry. When a book has 21 or more authors or editors, list the first 19 authors followed by three spaced ellipse points (. . .) , and then the last author's name. Rules are different for in-text citations; please see the examples provided.
Cite author names in the order in which they appear on the source, not in alphabetical order (the first author is usually the person who contributed the most work to the publication).
Capitalize the first letter of the first word of the title. If there is a colon (:) in the title, also capitalize the first letter of the first word after the colon.
Capitalize the first letter of proper names in titles, such as names of places or people.
Italicize titles of journals, magazines, newspapers, and books. Do not italicize the titles of articles or book chapters.
Capitalize only the first letter of the first word of the article title. If there is a colon in the article title, also capitalize the first letter of the first word after the colon.
Place of Publication
Do not include the publisher location in the reference. Only for works associated with a specific location, like conference presentations, include the location. For cities in the US and Canada list the city name and the province or state code. For other countries, list the city name and the country. Examples: Toronto, ON ; Tokyo, Japan
Electronic Books
Don't include the format, platform, or device (e.g. Kindle) in the reference. Include the publisher name. For audiobooks, include the narrator and audiobook notation.
Ebooks from Websites (not from library databases)
If an ebook from a website was originally published in print, give the author, year, title, edition (if given) and the url. If it was never published in print, treat it like a multi-page website.
Book In Print With One Author or Editor
Author's Last Name, First Initial. Second Initial if Given. (Year of Publication). Title of book: Subtitle if given (edition if given and is not first edition). Publisher Name.
Note: If the named person is an editor, place "(Ed.)." after the name.
Mulholland, K. (2003). Class, gender and the family business . Palgrave McMillan.
In-Text Paraphrase:
(Author's Last Name, Year)
Example: (Mulholland, 2003)
In-Text Quote:
(Author's Last Name, Year, p. Page Number)
Example: (Mulholland, 2003, p. 70)
Book in Print More Than One Author or Editor
Last Name of First Author, First Initial. Second Initial if Given, & Last Name of Second Author, First Initial. Second Initial if Given. (Year of Publication). Title of book: Subtitle if given (edition if given and is not first edition). Publisher Name.
Note: Authors' names are separated by commas. Put a comma and an ampersand (&) before the name of the last author cited.
Note : For works with three or more authors, the first in-text citation is shortened to include the first author's surname followed by "et al."
Note: If the listed names are editors rather than authors, include "(Eds.)." at the end of the list of names. The below example shows a list of editors.
Reference List Example:
Kaakinen, J., Coehlo, D., Steele, R., Tabacco, L., & Hanson, H. (Eds.). (2015). Family health care nursing: Theory, practice, and research (5th ed.). F.A. Davis Company.
In-text Citation
Two Authors/Editors
(Kaakinen & Coehlo, 2015)
Direct quote: (Kaakinen & Coehlo, 2015, p. 57)
Three or more Authors/Editors
(Kaakinen et al., 2015)
Direct quote: (Kaakinen et al., 2015, p. 57)
Author's Last Name, First Initial. Second Initial if Given. (Year of Publication). Title of book: Subtitle if given (edition if given and is not first edition). Publisher Name. URL
Example from Website:
Rhode, D. L. (2002). Divorce, American style . University of California Press. http://www.escholarship.org/editions/view?docId=kt9z09q84w;brand=ucpress
Example: (Rhode, 2002)
Example: (Rhode, 2002, p. 101)
If no author or creator is provided, start the citation with the title/name of the item you are citing instead. Follow the title/name of the item with the date of publication, and the continue with other citation details.
Remember: an author/creator may be an organization or corporation, for example Health Canada. If you don't have a person's name as the author, but do have the name of an organization or corporation, put that organization/corporation's name as the author.
If and only if an item is signed as being created by Anonymous, use "Anonymous" where you'd normally put the author's name.
When you have no author, use a shortened version of the title where you'd normally put the author's name.
If you're citing something which is part of a bigger work, like an article from a magazine, newspaper, journal, encyclopedia, or chapter/short story from a book, put the shortened title in quotation marks in your in-text citation:
Example, paraphrase: ("A few words," 2014)
If you're citing an entire work, like a book, website, video, etc., italicize the shortened title in your in-text citation:
Example, paraphrase: ( A few words , 2014)
Author's Last Name, First Initial. Second Initial if Given. (Year of Publication). Title of chapter, article, essay or short story. In Editor's First Initial. Second Initial if Given. Editor's Last Name (Ed.), Title of book: Subtitle if given (edition if given and is not first edition, pp. first page number-last page number). Publisher Name.
Note: If you have more than one editor list their name(s) after the first editor listed in the book, giving their initials and last name. Put an ampersand (&) before the last editor's name.
When you have one editor the short form (Ed.) is used after the editor's name. If you have more than one editor use (Eds.) instead.
O'Neil, J. M., & Egan, J. (1992). Men's and women's gender role journeys: A metaphor for healing, transition, and transformation. In B. R. Wainrib (Ed.), Gender issues across the life cycle (pp. 107-123). Springer.
Note: If there is no editor given you may leave out that part of the citation.
(Author's Last Name, Year)
Example (2 authors): (O'Neil & Egan, 1992)
(Author's Last Name, Year, p. Page Number)
Example (2 authors): (O'Neil & Egan, 1992, p. 998)
Author's Last Name, First Initial. Second Initial if Given. (Year of Publication). Title of article. In Editor's First Initial. Second Initial if Given. Editor's Last Name (Ed.), Title of book: Subtitle if given (edition if given and is not first edition). Publisher Name. URL or DOI
Caviness, L. B. (2008). Brain-relevant education. In N. J. Salkind (Ed.), Encyclopedia of educational psychology . Sage Publications. https://login.uportland.idm.oclc.org/login?url=https://search.credoreference.com/content/entry/sageedpsyc/brain_relevant_education/0?institutionId=5407
Example (1 author): (Caviness, 2008)
Example (1 author): (Caviness, 2008, Focus on the brain section, para. 2)
Note: When there are no visible page numbers or paragraph numbers, you may cite the section heading and the number of the paragraph in that section to identify where your quote came from.
- << Previous: Magazine/Newspaper Articles
- Next: Government & Legal Documents >>
- Last Updated: Apr 30, 2024 1:29 PM
- URL: https://libguides.up.edu/apa
- Essay Check
- Chicago Style
- APA Citation Examples
- MLA Citation Examples
- Chicago Style Citation Examples
- Writing Tips
- Plagiarism Guide
- Grammar Rules
- Student Life
- Create Account
APA Book Citation
- powered by chegg, create citations for free.
Website Book Journal Other
←Back to APA Citation Examples
How to Cite a Book in APA
Use the following template to cite a book using the APA citation format. We also provide style guides for the MLA and Chicago styles. To have your bibliography or works cited list automatically made for you, check out our free APA citation generator .
Once you’re finished with your citations, we can also help you with creating an APA title page .
Citing a book in APA (print)
Author, A. (Year of Publication). Title of work . Publisher Name.
Finney, J. (1970). Time and again . Simon and Schuster.
Notes: When citing a book in APA, keep in mind:
- The title of the book should be written in sentence case. This means you should capitalize the first letter of the first word of the title and any subtitles, as well as the first letter of any proper nouns.
- The full title of the book, including any subtitles, should be stated and italicized .
- You do not need to include the publisher location.
Citing an e-book in APA (digital or online)
E-book is short for “electronic book.” It is a digital version of a book that can be read on a computer, e-reader (Kindle, Nook, etc.), or other electronic device.
Author, A. (Year of Publication). Title of work (ed. if applicable). Publisher Name. URL
Coccia, E. (2021). The life of plants: The metaphysics of mixture (digital ed.). Hans Reitzel Forlag. https://planternesliv.digi.hansreitzel.dk/
- If you need to distinguish the e-book version from the print version, this can be included in the “edition” slot of the citation. Otherwise, the citation format is the same for both print books and e-books.
- If the e-book has a DOI or a stable URL, include it in the reference.
- Do not include a period after the URL.
Citing a book from a database in APA
Author, A. (Year of Publication). Title of work . Publisher Name. URL or DOI
Sayre, R., Devercelli, A. E., Neuman, M. J., & Wodon, Q. (2015). Investment in early childhood development: Review of the world bank’s recent experience . World Bank Group. https://doi.org/10.1596/978-1-4648-0403-8
Notes: When citing an online book or e-book in APA, keep in mind:
- A DOI (digital object identifier) is an assigned number that helps link content to its location on the Internet. It is therefore important, if one is provided, to use it when creating a citation.
- If an e-book is from an academic database but does not have a DOI or stable URL, end the citation after the publisher name (the citation format will then be the same as for a print book). Do not include the name of the database.
Citing a single volume of a multivolume book in APA
Author, A. (Year of Publication). Title of work (Vol. #). Publisher Name.
Kemble, J. M. (2020). The Saxons in England: A history of the English commonwealth till the period of the Norman conquest (Vol. 2). Gutenberg.
Citing a several volumes of a multivolume book in APA
Author, A. (Year of Publication). Title of work . (Vols. #-#). Publisher Name.
Kemble, J. M. (2020). The Saxons in England: A history of the English commonwealth till the period of the Norman conquest (Vols. 1-2). Gutenberg.
Citing an audiobook in APA
Author, A. (Year of Publication). Title of work (F. M. Narrator, Narr.) [Audiobook]. Publisher. URL or DOI (Original work published year if applicable)
Ruiz, D. M. (2005). The four agreements (P. Coyote, Narr.) [Audiobook]. Amber Allen Publishing. https://www.amazon.com/The-Four-Agreements-don-Miguel-Ruiz-audio/dp/B0007OB40E (Original work published 1997)
For more information on how to cite in APA, check out Cornell .
←Back to APA Citation Guide

“The art of writing is the art of discovering what you believe.” — Gustave Flaubert
How useful was this post?
Click on a star to rate it!
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?
When the book you quote has volume numbers or is a book from a series, then you need to mention them as part of your reference list entry. Use the format below to understand where and how.
Last Name, Initials. (Year). Title (Ed No., Vol no.). Publisher.
Creek, A.J. (1986). Handbook of mental disorders (5 th ed., Vol 3). Psychology Publishing Press.
In APA style, italicize sources that stand alone. Such works include books, reports, and websites. However, don’t italicize works that are part of the main source. Examples of such sources are journal articles and book chapters.
If an author name isn’t available, you may include a book, report, or website title in the in-text citation. In such cases, again only italicize sources that stand alone.
In APA style, italicize sources. Do not underline them.
Lynn University
- Paper Templates
- Academic Posters
- Citation Generators
- Multi-touch Books@Lynn
- Journal Articles
- Dictionaries & Encyclopedias
- News Sources
- Canvas Materials (PowerPoint Slides)
- Business Databases
- Reports & Case Studies
- Social Media
- Audio & Visual Works
- Interviews & Personal Communications
- Legal Documents
- Generative AI (Chat GPT)
Quick Guide to APA Citations
☑ include both parts of the apa citation:.
In-text citations (placed in your paper wherever you are quoting or paraphrasing a source) Reference list citations (placed at the end of your paper in an alphabetized reference list)
☑ If you quote OR paraphrase a source, you must cite it.
"Paraphrasing" includes describing someone else's idea in your own words. A quotation requires a "locator" which is the exact page number or paragraph number of the quote
☑ Do not include sources in your reference list if you did not use them.
In APA, reference citations are not a list of sources you read! Only include a source in your reference list if you quoted or paraphrased that source with an in-text citation in your paper.
☑ Each in-text citation must match its reference list citation.
The author name and year in the reference list citation and in-text citation must be the same. If you make a correction to the author and/or date in one of your references, you must also edit all of the corresponding in-text citations.
In-Text Citations
Citing paraphrased information:
(Author, Year).
Citing a direct quote:
(Author, Year, p. 3). OR (Author, Year, para. 3).
In-text Citation Examples
Paraphrasing a source with TWO AUTHORS:
(Tindall & Curtis, 2019).
Paraphrasing a source with THREE OR MORE AUTHORS:
(Amida et al., 2021).
Paraphrasing a source authored by a GROUP/ORGANIZATION with NO DATE:
(U.S. Department of Homeland Security, n.d.).
- 2023 In-Text Citation Instructions Help! I need more examples! Check out this PDF for what to do when you have long paraphrases, long quotations, you want to cite a source you found in another source, you have sources with the same author and date, and more!
Reference List Citations
Author. (Date). Title. Source. URL
Reference List Citation Examples
Reference list citation for a journal article with THREE OR MORE AUTHORS:*
Amida, A., Appianing, J., & Marafa, Y. (2022). Testing the predictors of college students' attitudes toward plagiarism. Journal of Academic Ethics, 20 (1), p. 85-99. https://doi.org/10.1007/s10805-021-09401-9
Reference list citation for an online article/webpage with ONE AUTHOR:
Bailey, J. (2022, July 6). 5 things new students need to know about plagiarism. Plagiarism Today . https://www.plagiarismtoday.com/2022/07/06/5-things-new-students-need-to-know-about-plagiarism/
Reference list citation for a source with a GROUP AUTHOR and NO DATE:
U. S. Department of Homeland Security. (n.d.). What is plagiarism? https://studyinthestates.dhs.gov/2014/11/what-plagiarism
*Never use "et al." in a reference citation. Include every author's name, up to 20 authors. For guidance on citing works with more than 20 authors, see the 2023 Reference List Instructions PDF below.
- 2023 APA Reference list instructions Help! I need more examples! Check out this PDF for what to do if there is no author or when there are twenty-one or more authors, how to capitalize the title, when the title has a title in it, and more!
- << Previous: Academic Posters
- Next: Citation Generators >>
- Last Updated: Jun 17, 2024 3:13 PM
- URL: https://lynn-library.libguides.com/apa
Purdue Online Writing Lab Purdue OWL® College of Liberal Arts
In-Text Citations: The Basics

Welcome to the Purdue OWL
This page is brought to you by the OWL at Purdue University. When printing this page, you must include the entire legal notice.
Copyright ©1995-2018 by The Writing Lab & The OWL at Purdue and Purdue University. All rights reserved. This material may not be published, reproduced, broadcast, rewritten, or redistributed without permission. Use of this site constitutes acceptance of our terms and conditions of fair use.
Note: This page reflects the latest version of the APA Publication Manual (i.e., APA 7), which released in October 2019. The equivalent resource for the older APA 6 style can be found here .
Reference citations in text are covered on pages 261-268 of the Publication Manual. What follows are some general guidelines for referring to the works of others in your essay.
Note: On pages 117-118, the Publication Manual suggests that authors of research papers should use the past tense or present perfect tense for signal phrases that occur in the literature review and procedure descriptions (for example, Jones (1998) found or Jones (1998) has found ...). Contexts other than traditionally-structured research writing may permit the simple present tense (for example, Jones (1998) finds ).
APA Citation Basics
When using APA format, follow the author-date method of in-text citation. This means that the author's last name and the year of publication for the source should appear in the text, like, for example, (Jones, 1998). One complete reference for each source should appear in the reference list at the end of the paper.
If you are referring to an idea from another work but NOT directly quoting the material, or making reference to an entire book, article or other work, you only have to make reference to the author and year of publication and not the page number in your in-text reference.
On the other hand, if you are directly quoting or borrowing from another work, you should include the page number at the end of the parenthetical citation. Use the abbreviation “p.” (for one page) or “pp.” (for multiple pages) before listing the page number(s). Use an en dash for page ranges. For example, you might write (Jones, 1998, p. 199) or (Jones, 1998, pp. 199–201). This information is reiterated below.
Regardless of how they are referenced, all sources that are cited in the text must appear in the reference list at the end of the paper.
In-text citation capitalization, quotes, and italics/underlining
- Always capitalize proper nouns, including author names and initials: D. Jones.
- If you refer to the title of a source within your paper, capitalize all words that are four letters long or greater within the title of a source: Permanence and Change . Exceptions apply to short words that are verbs, nouns, pronouns, adjectives, and adverbs: Writing New Media , There Is Nothing Left to Lose .
( Note: in your References list, only the first word of a title will be capitalized: Writing new media .)
- When capitalizing titles, capitalize both words in a hyphenated compound word: Natural-Born Cyborgs .
- Capitalize the first word after a dash or colon: "Defining Film Rhetoric: The Case of Hitchcock's Vertigo ."
- If the title of the work is italicized in your reference list, italicize it and use title case capitalization in the text: The Closing of the American Mind ; The Wizard of Oz ; Friends .
- If the title of the work is not italicized in your reference list, use double quotation marks and title case capitalization (even though the reference list uses sentence case): "Multimedia Narration: Constructing Possible Worlds;" "The One Where Chandler Can't Cry."
Short quotations
If you are directly quoting from a work, you will need to include the author, year of publication, and page number for the reference (preceded by "p." for a single page and “pp.” for a span of multiple pages, with the page numbers separated by an en dash).
You can introduce the quotation with a signal phrase that includes the author's last name followed by the date of publication in parentheses.
If you do not include the author’s name in the text of the sentence, place the author's last name, the year of publication, and the page number in parentheses after the quotation.
Long quotations
Place direct quotations that are 40 words or longer in a free-standing block of typewritten lines and omit quotation marks. Start the quotation on a new line, indented 1/2 inch from the left margin, i.e., in the same place you would begin a new paragraph. Type the entire quotation on the new margin, and indent the first line of any subsequent paragraph within the quotation 1/2 inch from the new margin. Maintain double-spacing throughout, but do not add an extra blank line before or after it. The parenthetical citation should come after the closing punctuation mark.
Because block quotation formatting is difficult for us to replicate in the OWL's content management system, we have simply provided a screenshot of a generic example below.

Formatting example for block quotations in APA 7 style.
Quotations from sources without pages
Direct quotations from sources that do not contain pages should not reference a page number. Instead, you may reference another logical identifying element: a paragraph, a chapter number, a section number, a table number, or something else. Older works (like religious texts) can also incorporate special location identifiers like verse numbers. In short: pick a substitute for page numbers that makes sense for your source.
Summary or paraphrase
If you are paraphrasing an idea from another work, you only have to make reference to the author and year of publication in your in-text reference and may omit the page numbers. APA guidelines, however, do encourage including a page range for a summary or paraphrase when it will help the reader find the information in a longer work.

- Peterborough

APA 7 Style: Citing Books and Sections of Books
- Book with single author
- Book with two authors
- Book with three to twenty authors
- Book with more than 20 authors
- Book with editor
- Book with translator
- Book with organizational author
- Reference book (Dictionary or Encyclopedia)
- Chapter or Essay in a Book
- Article or chapter reprinted in a Coursepack
- Entry with no author
- Entry with no publication date
- Entry in a print reference book (dictionary or encyclopedia)

Book With Single Author
In-text citation.
(Panagia, 2009)
Author's Name: Last Name, First Initial. (Year of Publication). Title of book . Publisher.
Panagia, D. (2009). The political life of sensation . Duke University Press.
Book With Two Authors
(Aronowitz & Giroux, 1991)
Author's Last Name, First Initial., & Author's Last Name, First Initial. (Year of Publication). Title of book . Publisher.
Aronowitz, S., & Giroux, H. A. (1991). Postmodern education: Politics, culture, and social criticism. University of Minnesota Press.
Article or Chapter in Edited Book
(Martino & Berrill, 2007)
Author's Last Name, First Initial. (Year of Publication). Article title. In Editor’s First Initial and Last Name (Ed.), Title of book (pp. #-#). Publisher.
Martino, W., & Berrill, D. (2007).' Dangerous pedagogies': Exploring issues of sexuality and masculinity in male teacher candidates' lives. In K. Davison & B. Frank (Eds.), Masculinities and schooling: International practices and perspectives (pp. 13-34). Althouse Press.
- For a book with one editor, use the abbreviation "Ed." For a work with multiple editors, use the abbreviation "Eds." The first and last page numbers of the article are listed after the title of the book, just before the publisher.
Book With Three to Twenty Authors
In the first reference for a work with three or more authors, use the surname of the first author followed by et al.
(Illston et al., 1979)
Provide last name and initials for all authors (up to twenty authors).
Author's Last Name, First Initial., Author's Last Name, First Initial., & Author's Last Name, First Initial. (Year of Publication). Title of book. Publisher.
Illston, J. M., Dinwood, J. M., & Smith, A. A. (1979). Concrete, timber, and metals: The nature and behaviour of structured materials . Van Nostrand Reinhold.
- Do not change the order of authors in a multi-authored work; the first author in the list is the lead author. For example, do not change Lee, Brown, & Green to Brown, Green, & Lee; Lee must be listed first.
Book With More Than 20 Authors
For a work with more than 20 authors, use the surname of the first author followed by et al.
(Eves et al., 2019).
For a work with more than 20 authors, list the first 20 authors and insert ellipses. After the ellipses, write the last author's name.
Author's Last Name, First Initial., Author's Last Name, First Initial., (list first 20 authors), . . . Final Author's Last Name, First Initial. (Year of Publication). Title of Book . Publisher.
Eves G., Dunaway, Z., Wilkins, R., Thompson, L., Martin, K., Corp, J., Leonard, F., Xi, F., Smith, S., Patel, S., Arnott, A., MacQuarrie, C., Stafa, A., Alam, J., Zuckerman, J., Brownlee, R., Lane, H., Goldman, H., Eamon, S., Ginter, T., . . . Goulding, N. (2019). How to succeed in university. First Line Press.
Electronic Book
Online only: in-text citation.
(Stevens, n.d.)
Author's Last Name, First Initial. (Year of Publication). Title. URL
Stevens, K. (n.d.). The dreamer and the beast. http://www.onlineoriginals .com/showitem.asp?itemID=321
Also in Print: In-Text Citation
If the book you are referencing is identical to the print version, there is no need to mention the e-reader or platform you used to access it. If, however, you are citing a special e-book version of the text, you should mention the platform.
(Chong, 2012)
(Downey & Baumann, 2004)
Author's Last Name, First Initial. (Year of Publication). Title. [E-reader file type]. Publisher. URL
Chong, K. (2012). My year of the racehorse: Falling in love with the sport of kings. [Kindle Edition]. Greystone Books. https://www.amazon.ca/My-Year-Racehorse-Falling-Sport-ebook/dp/B0073JCWB6
Downey M., Baumann A. O., & Nursing Study Sector Corporation. (2004). The international nursing labour market. [Gibson Library Connections]. Nursing Study Sector Corporation. http://books2.scholarsportal.info/viewdoc.html?id=27776
- When a URL is too long to fit on one line, create a break where there is punctuation (period, slash, dash). As you can see in the example, the punctuation starts the next line. Do not end the URL with a period if it is not in the original.
- If the electronic book provides a doi (digital object identifier), it will go in place of the URL.
Book with Editor
(Gibbs, 2001)
Editor's Last Name, First Initial. (Ed.). (Year of Publication). Title of book . Publisher.
Gibbs, J. T. (Ed.). (2001). Children of color: Psychological interventions with culturally diverse youth. Jossey-Bass.
- Use the abbreviation "Ed." in parentheses after the editor's name.If there is more than one editor, use the abbreviation Eds. in parentheses after listing all of the authors' names.
Article or Chapter in a Coursepack
An in-text citation for an article or chapter in a coursepack includes the original source publication date and the reprint date.
(Morgan, 2006/2013)
Author's Last Name, First Initial. (Year of Publication). Article Title. In Editor's First Initial and Last Name (Ed.), Title of Coursepack (pp. #- #). Publisher. (Reprinted from Original publication title, page range, original author or editor, original publication date, original publisher)
Morgan, G. (2013). Mechanization takes command: Organizations as machines. In B. Ahlstrand (Ed.), ADMN 2410H: Organization theory (pp. 31-50). CSPI - Coursepack. (Reprinted from Images of organization, pp. 19-38, by G. Morgan, 2006, Sage Publications)
- For a book with one editor, use the abbreviation "Ed." For a work with multiple editors, use the abbreviation "Eds." The coursepack page numbers are listed after the title of the book, just before the city of publication. The original source page numbers are listed in the reprint information. Any in-text citation that includes a page reference (i.e. for a direct quotation) should refer to the coursepack page numbers. The reprint information is usually listed on the first page of the article or chapter in the coursepack.
Book With Translator
Eisenstein (1943/1968)
Author's Last Name, First Initial. (Year of Republication). Title of Book (Translator’s First Initial. and Last Name, Trans.). Publisher. (Original work published YEAR).
Eisenstein, S. (1968). Film sense (J. Leyda, Trans.). Faberand Faber. (Original work published 1943).
- The translator's name is followed by "Trans." and placed in parentheses after the title. Because the example for a translated book is of a republished work, date of original publication and date of republication are given.
Book with Organizational Author
Associations, corporations, study groups, and government agencies are some examples of what is considered a group author. Only list individual authors if they are listed on the cover or title page of the work; otherwise, list organizational author in reference list and in-text citations.
If there is a readily identified abbreviation, in the first in-text citation the full name of the organization is given in full, with the abbreviation in square brackets:
(American Psychological Association [APA], 2010)
Subsequent references use the abbreviation:
(APA, 2010)
For in-text citations, where the organization has no abbreviation (Trent University, City of Oshawa), the full name of the organization continues to be given: (Trent University, 2010)
Name of Group or Corporate Author. (Year of Publication). Title of Book (Edition #). Publisher and/or URL
American Psychological Association. (2020). Publication manual of the American Psychological Association (7th ed.). https://doi.org/10.1037/0000165-000
- Do not abbreviate the name of the group in the reference.
- In this case the corporate author is also the publisher. Do not list publisher if the same as author. The APA (2020) manual (7th edition) lists its correct reference listing on the interior cover of its print manual, and it includes a doi, as shown above.
Reference Book
(Coleman, 1994)
Editor's Last Name, First Initial. (Ed.). (Year of Publication). Title of Book . Publisher.
Coleman, A. M. (Ed.). (1994). Companion encyclopedia of psychology . Routledge.
Entry in an Online Reference Book (Dictionary or Encyclopedia)
Often we wish to cite information, such as a definition or particular facts about a topic, and we need to cite an entry in a reference work, such as an encyclopedia or dictionary.
When the entry has no named author, begin the reference with the group or organization that created the reference work. If the reference work has an editor, include this information before the title of the reference work.
Entry in an Online Reference Book with No Author
(Cambridge University Press, 2015)
Institution or organization name. (Year). Title of entry. In Name of editor (ed.), Title of reference work. URL
Cambridge University Press. (2015). Cognitive dissonance. In R. Audi (ed.), The Cambridge dictionary of philosophy. https://www-cambridge-org.proxy1.lib.trentu.ca/core/books/cambridge-dict...
Entry in an Online Reference Book with No Publication Date
Many online reference works are continuously updated and thus do not have a publication date. In this case, use n.d. to indicate that there is no publication date, but also include the date on which you retrieved the information in your reference.
(American Psychological Association, n.d.)
Institutional or Group Author. (n.d.). Title of entry. In Title of reference work . Retrieved Month Day, year, from URL
American Psychological Association. (n.d.). Cognitive dissonance. In APA dictionary of psychology . Retrieved July 8, 2020, from https://dictionary.apa.org/cognitive-dissonance
Entry in a Print Reference Book (Dictionary or Encyclopedia)
(Merriam-Webster Incorporated., 2008).
Institution or Group Author. (Year of Publication). Title of entry. In Editor's First Initial and Last Name (Ed.), Title of reference work (edition and pp. #-#). Publisher.
Merriam Webster Incorporated. (2008). Cognitive dissonance. In Merriam-Webster’s collegiate dictionary (11th ed., p. 240). Merriam-Webster Incorporated.

Book chapters: What to cite

Imagine that after reading a long book, you have found one or two facts relevant to your research. Hooray! But it seems like going overboard to cite the entire book when you used just a paragraph or a chapter . . . so what to cite, then, the chapter or the book?
Well, it depends on the kind of book: authored or edited. This blog post explains how to cite both in seventh edition APA Style.
Notes before proceeding
The examples and guidance in this blog post and in the reference examples on the APA Style website apply to both print and digital book chapters, including books and chapters retrieved from academic research databases.
For ebooks and ebook chapters accessed from academic research databases, do not include the name of the database in the reference list entry (read more about why on the page about database information in references ).
Authored book chapters
An authored book is a book in which the same person has written all the chapters. If you used information from just one chapter of an authored book, write a reference for the whole authored book, as in the following example. Do not write a reference list entry for only a chapter in an authored book.
Kearney, D. J., & Simpson, T. L. (2020). Concise guides on trauma care. Mindfulness-based interventions for trauma and its consequences. American Psychological Association. https://doi.org/10.1037/0000154-000
When you have paraphrased a chapter, and you want to inform readers of which chapter, cite the specific chapter in the in-text citation along with the author and year, as shown in the following examples.
- Parenthetical citation of a paraphrase from an authored book chapter: (Kearney & Simpson, 2020, Chapter 2)
- Narrative citation of a paraphrase from an authored book chapter: Kearney and Simpson (2020, Chapter 2)
When you have directly quoted from a chapter, use a standard in-text citation for a quotation, which includes the author, year, and page number. (The format for quotations is the same for both authored and edited book chapters.)
- Parenthetical citation of a quotation: Research has demonstrated that “mindfulness significantly reshapes the clinical course of depression” (Kearney & Simpson, 2020, p. 42).
- Narrative citation of a quotation: Kearney and Simpson (2020) described how “mindfulness significantly reshapes the clinical course of depression” (p. 42).
Note that it is not required to cite a chapter of an authored book in the text. If you paraphrased information from multiple chapters or from the whole authored book, a standard in-text citation is sufficient, as in the following examples.
- Standard parenthetical citation of authored book: (Kearney & Simpson, 2020)
- Standard narrative citation of authored book: Kearney and Simpson (2020)
Last, you can cite more than just chapters in this way. For more information, see the page on citing specific parts of a source .
Edited book chapters
An edited book is a book in which different people have written different chapters, and the chapters have been compiled or put together by an editor. If you used information from just one chapter of an edited book , cite the chapter you used in the reference list. Create separate reference list entries for separate edited book chapters that you used.
Fountain, Y. (2019). Physical activity games. In J. Stone & C. E. Schaefer (Eds.), Game play: Therapeutic use of games with children and adolescents (3rd ed., pp. 79–98). John Wiley & Sons.
In the text, when you have paraphrased an edited book chapter, cite the author(s) of the chapter and the year of publication of the book, as shown in the following examples.
- Parenthetical citation of a paraphrase from an edited book chapter: (Fountain, 2019)
- Narrative citation of a paraphrase from an edited book chapter: Fountain (2019)
If the edited book chapter is particularly long or complex, you can add more specific location information (e.g., a page number or page range) to the citation of the paraphrase if desired, but this is not usually necessary and is not required.
Note that it is also possible to cite a whole edited book , for example, to direct readers to a relevant reference work. However, the more common case is to cite edited book chapters individually.
More information
More examples of book and book chapter references are provided in Chapter 10 of the Publication Manual , Sections 10.2 and 10.3. For more information about authored book references , see the authored book reference examples. For more information about edited book chapter references, see the edited book chapter reference examples .
Thanks for reading! Please leave a comment if you have any questions about citing chapters in APA Style.
Related and recent
Comments are disabled due to your privacy settings. To re-enable, please adjust your cookie preferences.
APA Style Monthly
Subscribe to the APA Style Monthly newsletter to get tips, updates, and resources delivered directly to your inbox.
Welcome! Thank you for subscribing.
APA Style Guidelines
Browse APA Style writing guidelines by category
- Abbreviations
- Bias-Free Language
- Capitalization
- In-Text Citations
- Italics and Quotation Marks
- Paper Format
- Punctuation
- Research and Publication
- Spelling and Hyphenation
- Tables and Figures
Full index of topics
- Bipolar Disorder
- Therapy Center
- When To See a Therapist
- Types of Therapy
- Best Online Therapy
- Best Couples Therapy
- Best Family Therapy
- Managing Stress
- Sleep and Dreaming
- Understanding Emotions
- Self-Improvement
- Healthy Relationships
- Student Resources
- Personality Types
- Guided Meditations
- Verywell Mind Insights
- 2024 Verywell Mind 25
- Mental Health in the Classroom
- Editorial Process
- Meet Our Review Board
- Crisis Support
How to Cite a Book in APA Format
Kendra Cherry, MS, is a psychosocial rehabilitation specialist, psychology educator, and author of the "Everything Psychology Book."
:max_bytes(150000):strip_icc():format(webp)/IMG_9791-89504ab694d54b66bbd72cb84ffb860e.jpg)
Emily is a board-certified science editor who has worked with top digital publishing brands like Voices for Biodiversity, Study.com, GoodTherapy, Vox, and Verywell.
:max_bytes(150000):strip_icc():format(webp)/Emily-Swaim-1000-0f3197de18f74329aeffb690a177160c.jpg)
Tom Werner / Getty Images
- Basic Structure
- One or More Authors
- Article Within a Book
Citation for a Translated Book
Citation for a multivolume work, citation for an ebook or audiobook.
Citing a book in APA format involves creating an in-text citation that refers to a source listed on your reference page. APA format is the official style of the American Psychological Association and is used in both academic and professional writing.
Before you create a reference page for your papers, essays, articles, or reports, it is important to learn how to format your citations in proper APA style . This style dictates certain rules and guidelines for different types of references, including books.
Not all book citations are the same in APA style. The format may vary depending on a number of factors including the type of book and number of authors.
At a Glance
If you are writing a paper in psychology or another social science, you will need to know how to create citations for books and other sources you plan to use as references. The format for your citations will vary somewhat depending on the type of book. For example, a citation for a book with a single author is a little different than an edited book that includes multiple authors. Most sources include the author's last name and first initials, publication year, book title, edition, and publisher.
APA Book Citation: Basic Structure
The basic structure of a book reference should list the author's last name, the first initial of their first name, the first initial of their middle name (if applicable), publication year, book title, edition (if it isn't the first), and publisher.
This is the same format for both books and ebooks. If the source has a DOI link, that should also be included at the end of the reference.
The following example shows one citation with a DOI hyperlink and the second without. Note the punctuation and style. The year of publication is in parentheses. The book title is italicized and in sentence case, and the edition information is in parentheses.
Book Citations in APA
Jackson, L. M. (2019). The psychology of prejudice: From attitudes to social action (2nd ed.). American Psychological Association. https://doi.org/10.1037/0000168-000
Rogers, C. R. (1961). On becoming a person. Houghton Mifflin.
- Parenthetical book citation : (Jackson, 2019); (Rogers, 1961)
- Narrative book citation : Jackson (2019); Rogers (1961)
This basic format can be used for many types of books that have a single author or multiple authors. However, you may need to use one of the following formats for books that are edited, have no author, are translated, or require some specialized formatting.
Citation for an Edited Book With One or More Authors
Edited books with one or more authors will include the names of the editors in the citation. It should follow the basic structure of a book reference but also include the first name initial, last name, and "Ed." for one editor or "Eds." for multiple editors in parentheses after the book title. Use an ampersand to separate multiple authors and multiple editors.
Citing Authors and Editors
Adler, A. (1956). The individual psychology of Alfred Adler: A systematic presentation of selections from his writings. (H. L. Ansbacher, & R. R. Ansbacher, Eds.). Basic Books.
Marson, G., Keenan-Miller, D., & Costin, C. (2020). The binge eating prevention workbook. (M. Solis, Ed.). New Harbinger Publications.
- Parenthetical book citation : (Adler, 1956); (Marson, Keenan-Miller, & Costin, 2020)
- Narrative book citation : Adler (1956); Marson, Keenan-Miller, and Costin (2020)
Citation for an Edited Book With No Author
Edited books with no author should list the editors first. List the last name and first initial of the editor, followed by "Ed." or "Eds." in parentheses. The remainder of the reference should follow the basic structure and include the publication year, book title in italics, and publisher.
If the book is anything other than the first edition, it should also be noted in parentheses after the title of the book, with no italics. Remember, you don't need to include the publisher's location.
Citing Editors
Atkinson, J. W., & Rayner, J. O. (Eds.). (1974). Motivation and achievement. V. H. Winston.
- Parenthetical book citation : (Atkinson, 1974)
- Narrative book citation : Atkinson (1974)
Citation for an Article Featured in an Edited Book
Sometimes edited books feature a collection of articles written by different authors. To cite an article in such a collection, you should list the last name and first initial of the individual author(s), followed by the publication date and chapter title.
Next, the editors should be listed, followed by the title of the book and the page numbers of the chapter. The publisher's name goes last.
Citing an Article in a Book
Bartol, C. R., & Bartol, A. M. (2005). History of forensic psychology. In I. B. Weiner, & A. K. Hess (Eds.), The Handbook of Forensic Psychology (pp.1-27). Wiley.
- Parenthetical book citation : (Bartol & Bartol, 2005)
- Narrative book citation : Bartol and Bartol (2005)
Many famous psychology texts were originally written in another language and then translated into English. Books translated from another language should include the last name and first initial of the author, followed by the year of publication and book title.
The first initials and last name of the translator and the notation "Trans." should then be included in parentheses. Next, provide the publisher and the original year of publication.
Citing a Translator
Freud, S. (1914). The psychopathology of everyday life (A. A. Brill, Trans.). T. Fisher Unwin. (Original work published 1901).
If you're referencing a republished book, the in-text citation should include both the original and republished date. For example, if you were to reference the publication above in text, you would write "(Freud, 1901/1914)" for a parenthetical citation.
- Parenthetical book citation : (Freud, 1904/1914)
- Narrative book citation : Freud (1901/1914)
The APA style guide also explains how to cite a multivolume work. You list the last name and first initial of the author(s) or editor(s), followed by the year of publication in parentheses. Then, you put the name of the publication in italics in sentence case.
You list the specific volumes in parentheses, using a hyphen between digits. You then list the name of the publisher.
Citing a Multivolume Work
Harris, K. R., Graham, S., & Urdan T. (Eds.). (2012). APA educational psychology handbook (Vols. 1–3). American Psychological Association.
- Parenthetical book citation : (Harris, Graham, & Urdan, 2012)
- Narrative book citation : Harris, Graham, and Urdan (2012)
If the ebook or audiobook is also in print and the content is the same, you can cite it the same way you would a print book. However, with audiobooks, you might wish to call out specific information such as the narrator's name.
If you are crediting the narrator of an audiobook, the format is the last name and the initial of the author's first name, then the year of publication in parentheses. After listing the name of the book in italics, you put the first initial and the last name of the narrator, followed by "Narr." in parentheses.
Then you add "Audiobook" in brackets, followed by the publisher's name and URL. The seventh edition of the "Publication Manual of the American Psychological Association" gives the following example:
Citing an Audiobook
Rowling, J. K. (2015). Harry Potter and the sorcerer’s stone (J. Dale, Narr.) [Audiobook]. Pottermore Publishing. http://bit.ly/2TcHchx (Original work published 1997)
In-text citations of an audio source should also add the relevant time or time ranges of the information you are citing. This should be listed as hours, minutes, and seconds.
- Parenthetical book citation : (Rowling, 02:36:05-55)
- Narrative book citation : Rowling (02:36:05-55)
More Tips for APA Book Citations
It may seem like there's a lot of information to keep in mind as you cite books in APA style. But remember, the more you practice, the easier it gets!
As you use citations throughout your paper, you'll want to make sure you keep track of them separately so you can add them to your reference page at the end.
Citations vs. References
Traditionally the term "citation" is used to refer to an in-text source, while "reference " is the correct term for a source listed on the reference page of an APA format paper.
The following are some helpful tips to keep in mind as you write an APA-style reference paper:
- Double-space : Remember that your reference page needs to be double-spaced.
- Indent : The first line of each reference should be flush left with the margin of the page. Each subsequent line of your reference should be indented.
- Use the DOI : If a digital object identifier (DOI) is available, include it at the end of the reference.
- Include the URL : If a book has been accessed via an online database , follow the basic APA format and include the full URL at the end.
- Follow additional guidelines : Ensure you follow the other guidelines for your reference page.
APA citations are an integral part of writing in APA style. It's best to consult the latest edition of the "Publication Manual of the American Psychological Association" to stay up to date on all guidelines and helpful tips.
American Psychological Association. Publication Manual of the American Psychological Association . 7th ed. American Psychological Association; 2020.
APA Style. How to cite translated works .
American Psychological Association. Book/ebook references .
By Kendra Cherry, MSEd Kendra Cherry, MS, is a psychosocial rehabilitation specialist, psychology educator, and author of the "Everything Psychology Book."

APA Citation Guidelines (7th Edition): Style & Format
- Style & Format
- Page Formats
- In-text Citations
- Reference Examples
- Sample Paper & Template
About this Page
This page contains information on the style and format of papers according to APA 7th edition using the Concise Guide to APA Style: The Official APA Style for Students .
- APA Style and Grammar Guidelines
APA Style papers should have the same style and size of font throughout the text of the paper (title page to reference page). APA considers the following fonts acceptable: 11- point Calibri, 11-point Arial, 10-point Lucida Sans Unicode, 12-point Times New Roman, 11-point Georgia, or 10-point Computer Modern. It is recommended that you check with your instructor to see if they have a preferred font style.
(See section 1.18 of the Concise Guide to APA Style )
The first line of every paragraph in the text of your paper and every reference on your reference page is indented (hit the tab key once). The remaining lines are left flush with the left-hand margin of the paper (this is known as a "hanging indent").
Other Format Guidelines
Page numbers : Title page through reference pages are numbered using Arabic numerals; place each number in the top right corner of the page.
Running heads: Are NOT required in student papers, but you should still check with your instructor to see if they wish them to be used.
Dashes: APA uses em dashes (long dash) and en dashes (short dash). See section 4.6 of the Concise Guide to APA Style for more information.
Additional Resources
- Heading Levels: Template: Student Papers
- Abbreviations Guide
- Transititions Guide
- Number and Statistics Guide
Other APA Pages
- Style and Format
- In-text citations
- Title and Reference Page Format
- I Want to See A Sample Paper
Lines and Margins
APA Style papers should have double-spaced text throughout the entire paper (including quotations and references). To make your paper double-spaced in Microsoft Word, highlight the text you want double-spaced, and then click Layout . Next, click on the arrow to the right of the word Paragraph (a pop-up appears). From the drop-down menu under Line Spacing , select Double (default choice is Multiple ) and click OK .
APA Style papers use 1 inch margins all around (top to bottom and left to right). Margins in Microsoft Word are set to 1 inch by default. If you are unsure, you can check your margins by clicking Layout, and clicking Margins. Once the drop-down menu appears, make sure Normal is selected to ensure you have 1 inch margins all around your paper.
(See sections 1.20 and 1.21 of the Concise Guide to APA Style )
APA Style recommends ONE space after a period when the period ends a sentence, separates parts of a reference list entry, or follows initials in names (J.B. Jones).
Do NOT put a space after a period when the period is part of an internal abbreviations (U.S. or a.m.)
Do NOT use periods for the abbreviation of state, province, or territory names (AZ; KS; BC); capital letter abbreviations and acronyms (APA, AMA, EPA); for abbreviations of academic degrees (PhD, MD, DO); or for abbreviations of metric and nonmetric measurements (cm, hr, kg,). Note: Use a period when abbreviating "inch" or "inches" (in.) or else it could be misread.
(See sections 4.1 and 4.2 of the Concise Guide to APA Style )
Sentence Case vs. Title Case
Sentence case is where most words in a sentence are going to be lower case.
The EXCEPTIONS are the first word in a title, heading, or sub-title ; proper nouns ; the first word after an em dash, semi-colon, or end punctuation; and any noun followed by a letter or number.
Title case is where major words are capitalized while minor words are lower case.
In APA style, major words are nouns, verbs, adjectives, pronouns, adverbs, or any word that is four letters or longer.
Minor words are articles, short prepositions, and conjunctions that are three letters or less.
(See section 5.7 of the Concise Guide to APA Style )
Paraphrasing
Refers to restating someone else's ideas or findings into your own words. Paraphrasing allows you to summarize information from one or more sources, compare and contrast information from multiple sources, and focus on the most important information from each source.
It is BEST to paraphrase information whenever possible rather than using direct quotations.
Paraphrased information must be cited in-text with either a parenthetical or narrative citation.
(See sections 8.23 and 8.24 of the Concise Guide to APA Style)
Reproduce words EXACTLY as written from another work (including your own). Quotations are best used in papers for when you want to reproduce an exact definition, when an author of a work has said something memorable, or when you want to respond to the exact wording (something someone said) from an author in your paper.
When not using a quotation for one of the above reasons, it is best to paraphrase information. Additionally, you should check with your instructor to see if they limit the number of quotations you are allowed to use.
Quotations must be cited in-text with either a parenthetical or narrative citation.
Short quotations consist of 40 words or less and should be incorporated into the text of your paper with quotation marks.
Long quotations consists of 40 words or more and do not use quotations marks. Instead, they should be incorporated into your paper as a block quotation. Block quotations begin on a new line, are double-spaced, and are indented 0.5 inches from the left hand margin of your paper.
(See sections 8.25 - 8.33 of the Concise Guide to APA Style)
Heading Levels
Heading Levels or "headings" are a way to organize information in APA papers and convey it clearly ( think of headings as "sections" and "subsections"). There are five levels of headings in APA Style, although for undergraduates it is rare to need to go past a Level 2 headings. If you are unsure if you need to use headings, check with your instructor.
| Levels | Format | Text |
| 1 | Text begins as a new paragraph. | |
| 2 | Text begins as a new paragraph. | |
| 3 | Text begins as a new paragraph. | |
| 4 | Text begins on the same line and continues as a regular paragraph. | |
| 5 | Text begins on the same line and continues as a regular paragraph. |
Note: Do NOT label an introduction as "Introduction" in APA papers. The title of your paper acts as a de facto Level 1 Heading.
(See section 1.26 of the Concise Guide to APA Style)
- Next: Page Formats >>
- Last Updated: Jun 24, 2024 9:16 AM
- URL: https://mohave.libguides.com/apa

- The Complete Guide to APA Format in 2020
- APA Reference Page
How to Cite Sources in APA Format
- Headings and Subheadings
- Discussion Section
- Websites and Online Sources
- Journals and Periodicals
- Other Print Sources
- Other Non-Print Sources
- In-text Citations
- Footnotes and Endnotes
- Using MyBib Responsibly
- Miscellaneous Questions

The most confusing and time-consuming part of writing an APA style paper is formatting each source in the reference list correctly, because the format is different depending on whether the source is a website, book, journal, newspaper, or any other medium.
💡 Our interactive templates automatically update to show how a citation should be formatted if some of the information is missing, or if you can't find it. You can edit, add, or remove parts of the citation data, and immediately see how the correct citation changes.
Our interactive templates follow the Publication Manual of the American Psychological Association (6th edition, 2nd printing).
Websites and Electronic Sources
Details required:.
- Date published (use n.d. if there isn't one)
- Title of blog post
- Name of blog or website
- Article URL
- Date of access
Lastname, F. N. ( Year Published , Month and Day Published ). Post title . Retrieved Month and Day Accessed , Year Accessed , from Blog or website Name website: URL .
The Tesla Team ( 2019 , April 3 ) Introducing a more seamless navigate on autopilot . Retrieved April 3 , 2019 from Tesla Blog website: https://www.tesla.com/blog/introducing-more-seamless-navigate-autopilot .
If there is no author you should move the title in place of the author instead.
If there is no date published , use n.d. instead.
You should only include the Date of access if the page is likely to change over time. Otherwise this is optional.
Database Article
- Title of article
- Publication title (if the article is part of a journal or magazine)
- Volume number (if the article is part of a journal or magazine)
- Issue number (if the article is part of a journal or magazine)
- Page (if the article is part of a journal or magazine)
- Database name
Lastname, F. N. ( Year Published ). Title of Article . Publication Title , Volume Number (Issue Number) , Page Range . Retrieved from Database Name .
- Title of e-book
Lastname, F. N. ( Year Published ). E-book title ( Edition ed., Vol. Volume , pp. Page range ; Editor first name initial . Editor lastname , ed.). Retrieved from URL .
Gunnis, E. ( 2018 ) The girl in the letter (pp. 45-46 ). Retrieved from https://www.amazon.com/Girl-Letter-gripping-heartwrenching-page-turner-ebook/dp/B079RMFFCJ/ref=sr_1_3?keywords=e+book&qid=1554551923&s=gateway&sr=8-3 .
Online Journal or Periodical Article
- Name of journal or periodical
- Volume number
- Issue number
- Page number or range
- Article URL or DOI
- Date of access (optional)
Lastname, F. N. ( Year published , Month and day published ). Title of article . Name of journal or periodical , Volume number ( Issue number ), Page number or range . Article URL or DOI
Zyblock, D. M. ( 2010 ). Nursing presence in contemporary nursing practice . Nursing Forum , 45 ( 2 ), 120-124 . https://doi.org/10.1111/j.1744-6198.2010.00173.x
Online Newspaper Article
- Title of newspaper
Lastname, F. N. ( Year published ). Title of Article . Name of Source , pp. Page Number or Range . Retrieved from Article URL .
Schwartz, J. ( 2019, May 1 ). In a warming world, evidence of a human ‘fingerprint’ on drought . The New York Times . Retrieved from https://www.nytimes.com/2019/05/01/climate/global-warming-drought-human-influence.html
Online Video
- Title of video
- Publisher (or website name)
- Video format
Lastname, F. N. ( Year published ). Title of video . Retrieved from Video URL .
Linus Tech Tips. ( 2018 ) The FASTEST gaming PC money can buy . Retrieved from https://www.youtube.com/watch?v=sCfmM71NOTo .
The Date of access is required if the page is likely to change over time. Otherwise this is optional.

Website / Web Page
- Title of article or page
- Website or publisher name
Lastname, F. N. ( Year published , Month and day published ). Title of article . Retrieved Month and day accessed , Year accessed , from Website or publisher Name website: Article URL .
Elias, D. A. ( 2019 , April 2 ) The complete guide to APA format in 2019 . Retrieved April 2 , 2019 from MyBib website: https://www.mybib.com/guides/apa-format .
- Book Author
- Title of book
- Publisher location
- URL (if accessible online)
- Date accessed/viewed (if accessible online)
Lastname, F. N. ( Year published ). Title of Book . ( Edition ed., pp. Page Number or Range ). Publisher Location : Publisher
Rowling, J. K. ( 1998 ). Harry Potter and the chamber of secrets ( 1st ed., pp. 23–24 ). New York : Arthur A. Levine Books .
Edited Book
- Book Editors
Lastname, F. N. ( Year Published ). Title of Book . ( Edition ed., pp. Page Number or Range ; Editor Lastname, F. N. , ed.). Publisher Location : Publisher
Rowling, J. K. ( 1998 ). Harry Potter and the prisoner of Azkaban ( 2nd ed., p. 38 ; M. Grandpré & B. Selznick, eds.). New York : Scholastic Inc .
Translated Book
- Book Translators
Lastname, F. N. ( Year Published ). Title of Book . ( Edition ed., pp. Page Number or Range ; Translator Lastname, F. N. , trans.). Publisher Location : Publisher . (Original work published Year Originally Published )
Rowling, J. K. ( 2013 ). Harry Potter a l’ecole des sorciers . ( M. Coulliard , trans.). Paris : Gallimard . (Original work published 1997 )
- Plagiarism and grammar
- Citation guides
Cite a Book

Don't let plagiarism errors spoil your paper
Citing books in apa, print books with one author:.
APA citation format:
Author Last name, First initial. Middle initial. (Year Published). Title of work . Publisher.
Moriarty, L. (2014). Big little lies . G. P. Putnam’s Sons.
Print books with two or more authors:
Last name, First initial. Middle initial., Last name, First initial. Middle initial., & Last name, First initial. Middle initial. (Date). Title . Publisher.
Goldin, C. D., & Katz, L. F. (2008). The race between education and technology . Belknap Press of Harvard University Press.
Matthews, G., Smith, Y., & Knowles, G. (2009). Disaster management in archives, libraries and museums . Ashgate.
Full versions of E-books:
E-books are generally read either on a website, on an e-reader, or on a database.
Author Last Name, First initial. Middle initial. (Year Published). Title of work . https://doi.org/xxxx or http://xxxx
Auster, P. (2007). The Brooklyn follies . http://www.barnesandnoble.com/
To cite your ebooks automatically, use the “Book” form at CitationMachine.com, click “Manual entry mode,” and click the “E-book” tab. Everything will be properly formatted following APA bibliography guidelines.
Featured links:
APA Citation Generator | Website | Books | Journal Articles | YouTube | Images | Movies | Interview | PDF
- Citation Machine® Plus
- Citation Guides
- Chicago Style
- Harvard Referencing
- Terms of Use
- Global Privacy Policy
- Cookie Notice
- DO NOT SELL MY INFO
APA In-Text Citations and Sample Essay 7th Edition
This handout focuses on how to format in-text citations in APA.
Proper citation of sources is a two-part process . You must first cite each source in the body of your essay; these citations within the essay are called in-text citations . You MUST cite all quoted, paraphrased, or summarized words, ideas, and facts from sources. Without in-text citations, you are technically in danger of plagiarism, even if you have listed your sources at the end of the essay.
In-text citations point the reader to the sources’ information on the references page. The in-text citation typically includes the author's last name and the year of publication. If you use a direct quote, the page number is also provided.
More information can be found on p. 253 of the 7th edition of the Publication Manual of the American Psychological Association.
Citation Rules
Direct quotation with the author named in the text.
Heinze and Lu (2017) stated, “The NFL shifted its responses to institutional change around concussions significantly as the field itself evolved” (p. 509).
Note: The year of publication is listed in parenthesis after the names of the authors, and the page number is listed in parenthesis at the end of the quote.
Direct Quotation without the Author Named in the Text
As the NFL developed as an organization, it “shifted its responses to institutional change around concussions significantly” (Heinze & Lu, 2017, p. 509).
Note: At the end of the quote, the names of the authors, year of publication, and page number are listed in parenthesis.
Paraphrase with 1-2 Authors
As the NFL developed as an organization, its reactions toward concussions also transformed (Heinze & Lu, 2017).
Note: For paraphrases, page numbers are encouraged but not required.
Paraphrase with 3 or More Authors
To work toward solving the issue of violence in prisons begins with determining aspects that might connect with prisoners' violent conduct (Thomson et al., 2019).
Direct Quotation without an Author
The findings were astonishing "in a recent study of parent and adult child relationships" ("Parents and Their Children," 2007, p. 2).
Note: Since the author of the text is not stated, a shortened version of the title is used instead.
Secondary Sources
When using secondary sources, use the phrase "as cited in" and cite the secondary source on the References page.
In 1936, Keynes said, “governments should run deficits when the economy is slow to avoid unemployment” (as cited in Richardson, 2008, p. 257).
Long (Block) Quotations
When using direct quotations of 40 or more words, indent five spaces from the left margin without using quotation marks. The final period should come before the parenthetical citation.
At Meramec, an English department policy states:
To honor and protect their own work and that of others, all students must give credit to proprietary sources that are used for course work. It is assumed that any information that is not documented is either common knowledge in that field or the original work of that student. (St. Louis Community College, 2001, p. 1)
Website Citations
If citing a specific web document without a page number, include the name of the author, date, title of the section, and paragraph number in parentheses:
In America, “Two out of five deaths among U.S. teens are the result of a motor vehicle crash” (National Center for Injury Prevention and Control, 2004, Overview section, para. 1).
Here is a print-friendly version of this content.
Learn more about the APA References page by reviewing this handout .
For information on STLCC's academic integrity policy, check out this webpage .
For additional information on APA, check out STLCC's LibGuide on APA .
Sample Essay
A sample APA essay is available at this link .
Home / Guides / Citation Guides / How to Cite Sources
How to Cite Sources
Here is a complete list for how to cite sources. Most of these guides present citation guidance and examples in MLA, APA, and Chicago.
If you’re looking for general information on MLA or APA citations , the EasyBib Writing Center was designed for you! It has articles on what’s needed in an MLA in-text citation , how to format an APA paper, what an MLA annotated bibliography is, making an MLA works cited page, and much more!
MLA Format Citation Examples
The Modern Language Association created the MLA Style, currently in its 9th edition, to provide researchers with guidelines for writing and documenting scholarly borrowings. Most often used in the humanities, MLA style (or MLA format ) has been adopted and used by numerous other disciplines, in multiple parts of the world.
MLA provides standard rules to follow so that most research papers are formatted in a similar manner. This makes it easier for readers to comprehend the information. The MLA in-text citation guidelines, MLA works cited standards, and MLA annotated bibliography instructions provide scholars with the information they need to properly cite sources in their research papers, articles, and assignments.
- Book Chapter
- Conference Paper
- Documentary
- Encyclopedia
- Google Images
- Kindle Book
- Memorial Inscription
- Museum Exhibit
- Painting or Artwork
- PowerPoint Presentation
- Sheet Music
- Thesis or Dissertation
- YouTube Video
APA Format Citation Examples
The American Psychological Association created the APA citation style in 1929 as a way to help psychologists, anthropologists, and even business managers establish one common way to cite sources and present content.
APA is used when citing sources for academic articles such as journals, and is intended to help readers better comprehend content, and to avoid language bias wherever possible. The APA style (or APA format ) is now in its 7th edition, and provides citation style guides for virtually any type of resource.
Chicago Style Citation Examples
The Chicago/Turabian style of citing sources is generally used when citing sources for humanities papers, and is best known for its requirement that writers place bibliographic citations at the bottom of a page (in Chicago-format footnotes ) or at the end of a paper (endnotes).
The Turabian and Chicago citation styles are almost identical, but the Turabian style is geared towards student published papers such as theses and dissertations, while the Chicago style provides guidelines for all types of publications. This is why you’ll commonly see Chicago style and Turabian style presented together. The Chicago Manual of Style is currently in its 17th edition, and Turabian’s A Manual for Writers of Research Papers, Theses, and Dissertations is in its 8th edition.
Citing Specific Sources or Events
- Declaration of Independence
- Gettysburg Address
- Martin Luther King Jr. Speech
- President Obama’s Farewell Address
- President Trump’s Inauguration Speech
- White House Press Briefing
Additional FAQs
- Citing Archived Contributors
- Citing a Blog
- Citing a Book Chapter
- Citing a Source in a Foreign Language
- Citing an Image
- Citing a Song
- Citing Special Contributors
- Citing a Translated Article
- Citing a Tweet
6 Interesting Citation Facts
The world of citations may seem cut and dry, but there’s more to them than just specific capitalization rules, MLA in-text citations , and other formatting specifications. Citations have been helping researches document their sources for hundreds of years, and are a great way to learn more about a particular subject area.
Ever wonder what sets all the different styles apart, or how they came to be in the first place? Read on for some interesting facts about citations!
1. There are Over 7,000 Different Citation Styles
You may be familiar with MLA and APA citation styles, but there are actually thousands of citation styles used for all different academic disciplines all across the world. Deciding which one to use can be difficult, so be sure to ask you instructor which one you should be using for your next paper.
2. Some Citation Styles are Named After People
While a majority of citation styles are named for the specific organizations that publish them (i.e. APA is published by the American Psychological Association, and MLA format is named for the Modern Language Association), some are actually named after individuals. The most well-known example of this is perhaps Turabian style, named for Kate L. Turabian, an American educator and writer. She developed this style as a condensed version of the Chicago Manual of Style in order to present a more concise set of rules to students.
3. There are Some Really Specific and Uniquely Named Citation Styles
How specific can citation styles get? The answer is very. For example, the “Flavour and Fragrance Journal” style is based on a bimonthly, peer-reviewed scientific journal published since 1985 by John Wiley & Sons. It publishes original research articles, reviews and special reports on all aspects of flavor and fragrance. Another example is “Nordic Pulp and Paper Research,” a style used by an international scientific magazine covering science and technology for the areas of wood or bio-mass constituents.
4. More citations were created on EasyBib.com in the first quarter of 2018 than there are people in California.
The US Census Bureau estimates that approximately 39.5 million people live in the state of California. Meanwhile, about 43 million citations were made on EasyBib from January to March of 2018. That’s a lot of citations.
5. “Citations” is a Word With a Long History
The word “citations” can be traced back literally thousands of years to the Latin word “citare” meaning “to summon, urge, call; put in sudden motion, call forward; rouse, excite.” The word then took on its more modern meaning and relevance to writing papers in the 1600s, where it became known as the “act of citing or quoting a passage from a book, etc.”
6. Citation Styles are Always Changing
The concept of citations always stays the same. It is a means of preventing plagiarism and demonstrating where you relied on outside sources. The specific style rules, however, can and do change regularly. For example, in 2018 alone, 46 new citation styles were introduced , and 106 updates were made to exiting styles. At EasyBib, we are always on the lookout for ways to improve our styles and opportunities to add new ones to our list.
Why Citations Matter
Here are the ways accurate citations can help your students achieve academic success, and how you can answer the dreaded question, “why should I cite my sources?”
They Give Credit to the Right People
Citing their sources makes sure that the reader can differentiate the student’s original thoughts from those of other researchers. Not only does this make sure that the sources they use receive proper credit for their work, it ensures that the student receives deserved recognition for their unique contributions to the topic. Whether the student is citing in MLA format , APA format , or any other style, citations serve as a natural way to place a student’s work in the broader context of the subject area, and serve as an easy way to gauge their commitment to the project.
They Provide Hard Evidence of Ideas
Having many citations from a wide variety of sources related to their idea means that the student is working on a well-researched and respected subject. Citing sources that back up their claim creates room for fact-checking and further research . And, if they can cite a few sources that have the converse opinion or idea, and then demonstrate to the reader why they believe that that viewpoint is wrong by again citing credible sources, the student is well on their way to winning over the reader and cementing their point of view.
They Promote Originality and Prevent Plagiarism
The point of research projects is not to regurgitate information that can already be found elsewhere. We have Google for that! What the student’s project should aim to do is promote an original idea or a spin on an existing idea, and use reliable sources to promote that idea. Copying or directly referencing a source without proper citation can lead to not only a poor grade, but accusations of academic dishonesty. By citing their sources regularly and accurately, students can easily avoid the trap of plagiarism , and promote further research on their topic.
They Create Better Researchers
By researching sources to back up and promote their ideas, students are becoming better researchers without even knowing it! Each time a new source is read or researched, the student is becoming more engaged with the project and is developing a deeper understanding of the subject area. Proper citations demonstrate a breadth of the student’s reading and dedication to the project itself. By creating citations, students are compelled to make connections between their sources and discern research patterns. Each time they complete this process, they are helping themselves become better researchers and writers overall.
When is the Right Time to Start Making Citations?
Make in-text/parenthetical citations as you need them.
As you are writing your paper, be sure to include references within the text that correspond with references in a works cited or bibliography. These are usually called in-text citations or parenthetical citations in MLA and APA formats. The most effective time to complete these is directly after you have made your reference to another source. For instance, after writing the line from Charles Dickens’ A Tale of Two Cities : “It was the best of times, it was the worst of times…,” you would include a citation like this (depending on your chosen citation style):
(Dickens 11).
This signals to the reader that you have referenced an outside source. What’s great about this system is that the in-text citations serve as a natural list for all of the citations you have made in your paper, which will make completing the works cited page a whole lot easier. After you are done writing, all that will be left for you to do is scan your paper for these references, and then build a works cited page that includes a citation for each one.
Need help creating an MLA works cited page ? Try the MLA format generator on EasyBib.com! We also have a guide on how to format an APA reference page .
2. Understand the General Formatting Rules of Your Citation Style Before You Start Writing
While reading up on paper formatting may not sound exciting, being aware of how your paper should look early on in the paper writing process is super important. Citation styles can dictate more than just the appearance of the citations themselves, but rather can impact the layout of your paper as a whole, with specific guidelines concerning margin width, title treatment, and even font size and spacing. Knowing how to organize your paper before you start writing will ensure that you do not receive a low grade for something as trivial as forgetting a hanging indent.
Don’t know where to start? Here’s a formatting guide on APA format .
3. Double-check All of Your Outside Sources for Relevance and Trustworthiness First
Collecting outside sources that support your research and specific topic is a critical step in writing an effective paper. But before you run to the library and grab the first 20 books you can lay your hands on, keep in mind that selecting a source to include in your paper should not be taken lightly. Before you proceed with using it to backup your ideas, run a quick Internet search for it and see if other scholars in your field have written about it as well. Check to see if there are book reviews about it or peer accolades. If you spot something that seems off to you, you may want to consider leaving it out of your work. Doing this before your start making citations can save you a ton of time in the long run.
Finished with your paper? It may be time to run it through a grammar and plagiarism checker , like the one offered by EasyBib Plus. If you’re just looking to brush up on the basics, our grammar guides are ready anytime you are.
How useful was this post?
Click on a star to rate it!
We are sorry that this post was not useful for you!
Let us improve this post!
Tell us how we can improve this post?
Citation Basics
Harvard Referencing
Plagiarism Basics
Plagiarism Checker
Upload a paper to check for plagiarism against billions of sources and get advanced writing suggestions for clarity and style.
Get Started
- Western Libraries
- Ask Us! Answer Service
Q. How do I refer to a book by title in-text in APA format?
- Research & Writing Studio
- 21 Accounts
- 14 Acquisitions
- 4 Anthropology
- 71 APA citations and formatting
- 35 Archives
- 31 Archives & Special Collections
- 36 Articles
- 14 Business resources
- 11 Center for Pacific Northwest Studies
- 3 Chemistry
- 8 Chicago citations and formatting
- 85 Circulation Services (check out/return/renew items)
- 42 Citations and style guides
- 44 Collections
- 50 Community services
- 1 Computer science
- 38 Computers
- 47 Copyright
- 79 Databases
- 22 Digital collections
- 87 Directions
- 7 Education (studies)
- 3 Engineering
- 2 English literature
- 7 Environmental studies/sciences
- 23 Equipment
- 42 Faculty services
- 3 Fairhaven
- 9 Fines and fees
- 12 Fun facts
- 21 Government information
- 5 Graduate students
- 2 Grant writing
- 1 Guest services
- 5 Human Services
- 50 Inter-library loan
- 17 Journals
- 29 Learning Commons
- 8 Library instruction
- 78 Library services
- 13 MLA citations and formatting
- 29 Multimedia
- 6 Newspapers
- 55 OneSearch
- 4 Online Learning
- 64 Outreach and Continuing Education
- 29 Policies
- 2 Political science
- 29 Primary sources
- 30 Printing related
- 3 Psychology
- 2 Rehabilitation Counseling
- 86 Research
- 17 Research & Writing Studio
- 37 Reserves
- 6 Scholarly communication
- 3 Sociology
- 10 Special Collections
- 1 Streaming video
- 44 Student services
- 28 Student Technology Center
- 1 Teaching and Learning Academy
- 16 Technology
- 3 Troubleshooting
- 5 Tutoring Center
- 5 Undergraduate Research Award
- 5 Undergraduate Students
- 18 Video tutorial
- 11 Western CEDAR
- 1 Women's Studies
- 37 Writing related
- 93 WWU general info
Answered By: Gabe Gossett Last Updated: Jun 22, 2023 Views: 642750
The basic format for an in-text citation is: Title of the Book (Author Last Name, year).
One author: Where the Wild Things Are (Sendak, 1963) is a depiction of a child coping with his anger towards his mom.
Two authors (cite both names every time): Brabant and Mooney (1986) have used the comic strip to examine evidence of sex role stereotyping. OR The comic strip has been used to examine evidence of sex role stereotyping (Brabant & Mooney, 1986).
Three or more authors (cite the first author plus et al.): Tales from the Shadowhunter Academy (Clare et al., 2016) depicts a young man's experience at the Shadowhunter Academy, a place where being a former vampire is looked down upon.OR Clare et al. (2016) have crafted a unique story about a young man's journey to find himself.
No author: Cite the first few words of the reference entry (usually the title) and the year. Use double quotation marks around the title of an article or chapter, and italicize the title of a periodical, book, brochure, or report. Examples: From the book Study Guide (2000) ... or ("Reading," 1999).
Note: Titles of periodicals, books, brochures, or reports should be in italics and use normal title capitalization rules.
If you are citing multiple sources by multiple authors in-text, you can list all of them by the author's last name and year of publication within the same set of parentheses, separated by semicolons.
Example: (Adams, 1999; Jones & James, 2000; Miller, 1999)
For more information on how to cite books in-text and as a reference entry, see the APA Publication Manual (7th edition) Section 10.2 on pages 321-325 .
Links & Files
- APA Workshop
- Citation Quick Guides and Style Manuals
- Share on Facebook
Was this helpful? Yes 111 No 86
Comments (13)
- This was very useful for me! I was having a really hard time finding information on how to mention an article title AND the author in text in APA so this was very helpful!!! by Ryan Waddell on Jun 27, 2019
- If I just mention that I used a book to teach a topic do I have to include it in the reference list? by Franw on Oct 17, 2019
- @Franw, if it is a source that informs your paper in any way, or if your reader would have reason to look it up, then you should include a full reference list entry for the book. by Gabe [Research & Writing Studio] on Oct 18, 2019
- Maybe I'm misunderstanding the question, but I think the OP is asking how to refer to a book title, not how to cite one. I believe APA uses quotation marks around book titles and MLA uses italics. by AB on Dec 12, 2019
- @AB: The first sentence has been tweaked to clarify title of book usage, reflecting the examples given. For APA style you should use italics for book titles. It would be quotation marks. by Gabe [Research & Writing Studio] on Dec 12, 2019
- Hi, can any one help me with in-text-citation of this, how can i cite it in the text Panel, I. L. (2002). Digital transformation: A framework for ICT literacy. Educational Testing Service, 1-53. by Milad on Aug 20, 2021
- @Milad: In that case it would be (Panel, 2002). If you are quoting, or otherwise choosing to include page numbers, put a comma after the year, then p. and the page number(s). by Gabe Gossett on Aug 20, 2021
- Hey, I'm a little bit curious, what if I'm mentioning a book and paraphrasing it but still want to give credit. Would I put the information into parenthesis instead? Like: Paraphrased info. ("Title in Italics" Author, year) by Kai on Sep 14, 2023
- @Kai: Apologies for not seeing your question sooner! (Our academic year has not started yet). If I am understanding your question correctly, what I suggest is referring to the book title in the narrative of your writing, rather than in the in-text citation. I do not see an examples of using a book title in an in-text citation except for rare circumstances including citing a classic religious text or using the title when there is no author information because it is the start of your reference list entry. Basically, APA's in-text convention is supposed to make it easy for your reader to locate the source being cited in the reference list. So the first part of the in-text citation, usually authors, comes first to locate it alphabetically. Putting the book title first when you have an author name can throw that off. by Gabe Gossett on Sep 21, 2023
- Perhaps this is along the lines of the response to Kai - Can you reference a book title as a common point of social understanding to demonstrate a common concept? Is official citing required if you use widely known titles such as "Where's Waldo" and "Who Moved My Cheese?" to make a point of illustration? by Chez Renee on Sep 30, 2023
- @Chez: Aside from some classical religious texts, if it is a published book, I'd try to make sure that it is appropriately cited for APA style. That said, I think I understand where it gets tricky with things like Where's Waldo, since that is a series of books and stating "Where's Waldo" is a cultural reference many people would understand, though you can't reasonably cite the entire series. I don't believe that APA gives guidance for this particular issue. If it is being referred to in order to back up a claim, it would help to cite a particular book. If not, then it might work to use a statement such as, "Hanford's Where's Waldo series . . ." by Gabe Gossett on Oct 02, 2023
- How to cite a dissertation thesis in apa form? by Elizabeth on Feb 05, 2024
- @Elizabeth: For citing a dissertation or thesis you can check out our page answering that here https://askus.library.wwu.edu/faq/153308 by Gabe Gossett on Feb 05, 2024
- Find the librarian for your subject area
Related Topics
- APA citations and formatting

APA Style Guide: 7th Edition
- How To Use This Guide
- Ethical Use of Sources & Plagiarism This link opens in a new window
- Introduction to DOI
- Formatting: Title Page, Body, References
- Formatting: Annotated Bibliographies
- Formatting: Appendices
- Formatting: Quotations
- Formatting: Business Reports
- How to Format In-text Citations
- Citing Multiple Works
- Number and Type of Author
- Publication Date
- Page, Paragraph Number, Heading, and Time Stamp
- Citing Text Content Created by AI
- Citing Image Content Created by AI
- Brightspace, with Author
- Brightspace, No Author
- Comment on Blog Post
- Book with Author(s)
- Book with Author(s) and Editor(s)
- Book with Editor(s), No Author
- Book with Organization as Author
- Book with the Same Organization as Author & Publisher
- Textbook Chapter with Book Editor(s) and Chapter Author(s)
- Translation, Print Book
Work in an Anthology
- Cochrane Database of Systematic Reviews
- Dictionary with Editor(s)
- Entry in Online Dictionary, No Author
- Report with Author(s)
- Report, No Author
- Report with Report Number
- Report with Multiple Levels of Government
- eBook from Website or Library Database, with DOI
- eBook from Library Database, no DOI
- eBook from Website, no DOI
- Open Textbook
- General Information & Checklist
- Figure Notes & Legend
- In-text Citation & Reference Formatting
- Journal Article, Print
- Journal Article from Website or Library Database, with DOI
- Journal Article from Library Database, no DOI
- Journal Article from Website, no DOI
- Referencing: Images
- Referencing: Indigenous Elders & Knowledge Keepers
- Magazine Article, Print
- Magazine Article from Website, with DOI
- Magazine Article from Website, no DOI
- Newspaper Article, Print
- Newspaper Article from Library Database
- Newspaper Article from Website
- Newspaper Article, No Author
- Personal Communication, General
- Traditional Knowledge or Oral Traditions of Indigenous Peoples
- Referencing: Podcasts
- Referencing: PowerPoint Presentations
- Referencing: Secondary Sources
- Twitter Profile
- X (Tweet) or Instagram Post
- Facebook Page
- Post on Facebook, Tumblr, Linkedin, etc.
- TikTok Profile
- TikTok Post
- Referencing: Statistics Canada
- Table Notes
- Film or Video
- Online Film or Streaming Video
- YouTube Video, Personal Author
- YouTube Video, Username (No Personal Author Listed)
- Webpage on a News Website
- Webpage with Group or Organization as Author
- Webpage with a Personal Author
- Webpage with a Retrieval Date
- Common Knowledge
- Additional Resources
- Annotated Bibliographies This link opens in a new window
- Take A Quiz
Anthologies have an editor or editors for the entire work and separate authors for each story, essay or poem. You must cite and reference every story, essay or poem that you use in your paper separately , unless you are referring generally to the entire work.
Formatting Examples
- Reference Format
- In-text Citation Format
- Author, A. A. = Author's surname followed by first and middle initials, when available.
- Start the reference with the author of the story, essay, or poem.
- Follow the title with the editor(s) first initial and last name and "Ed." for one editor or "Eds." for multiple.
- Always include the original publication date of the story, essay, or poem.
Examples of formatting an in-text citation for this item are outlined below:
| Reference Information | Faulkner, W. (2012). A rose for Emily. In J. Guance, S. Mayr, D. LePan, M. Mather, & B. Miller (Eds.), . (2nd ed., pp. 154-216). Broadview Press. (Original work published 1930) |
| In-text Citation Guidelines | Examples |
|
Story, essay or poem author's last name and year of original publication/year of anthology publication placed in brackets at the end of a paraphrased sentence. Note: If you are paraphrasing from a lengthy document, also include page, paragraph or heading info. |
Consider this a paraphrased sentence (Faulkner, 1930/2012). |
|
Sentence beginning with story, essay or poem author's last name followed immediately by year of original publication/year of anthology publication in brackets; page # in brackets at the end of the quote. |
According to Faulkner (1930/2012), "consider this a direct quote" (p. 158). |
Remember, in-text citation formatting changes depending on a number of factors .
See Number of Authors , Publication Date , and Page/Paragraph Number or Heading for more information.
- << Previous: Translation, Print Book
- Next: Referencing: Clinical and Health Science Web Sources >>
- Last Updated: Jun 3, 2024 1:47 PM
- URL: https://library.nic.bc.ca/apa7th
Copy of Writing, Citing, Tutoring, and Studying Resources: APA
- Study Support This link opens in a new window
- Subject Support This link opens in a new window
Changes in APA 7th Edition
- LIst of Changes from OWL From Purdue Online Writing Lab: "The seventh edition of the APA Publication Manual contains a number of updates and additions designed to make APA style more useful for students, teachers, and other educational stakeholders. While there are too many changes to list here, we’ve chosen to focus on the changes that are most pertinent to students and teachers. These include changes to the ways academic papers are formatted, changes to the ways sources are cited, and more."
- Introduction to the 7th Edition of APA Manual
APA 7th Edition Citation Examples for Online Sources
General Information for References Page
- References pages are double spaced with no extra spacing between entries.
- The word References is centered and bolded.
- Arrange all entries alphabetically by author.
- Apply the hanging indent to all entries: first line begins at the margin, subsequent lines begin ½ inch from the margin.
Online Sources Examples
An Article with DOI assigned
Nelson, A. M. (2014). Best practice in nursing: A concept analysis. International Journal o f Nursing Studies , 51 (11), 1507-1516 . http://d oi .org/ 10.1016/j.ijnurstu.2014.05.003
An Article with no DOI assigned
Urban , E., & Palmer, L. B. (2016). International students' perceptions of the value of U.S. higher e ducation. Journal o f International Students , 6 (1), 153-174.
An Online Journal Article Not in a Database
Gunn , M . A., Koeplin , J. P., Lorton Jr., P. V., Kane, K., & Masterson, N. (20 16 ). The presence of Jesuit values in a selection of University of San Francisco courses: The students’ perspective. Jesuit Higher Education: A Journal , 5 (1), 55-75.
http://epublications.regis.edu/jhe/vol5/iss1/9
An Article from a Newspaper or News Service
Davis, J. H. (20 15 , Dec 10 ). President Obama s igns i nto l aw a r ewrite of No Child Left Behin d . The New York Times . http://www.nytimes.com
Book or eBook
Shi, L. (2014). Introduction to health policy . Health Administration Press.
Web page on a web site with author
Fagan, J. (2019, March 25). Nursing clinical brain. OER Commons. Retrieved September 17, 2019, from https://www.oercommons.org/authoring/53029-nursing-clinical-brain/view
A Web Site with Group Author
American Psychological Association. (20 20 ). APA Style . https://apastyle.apa.org/
Dictionary
Merriam-Webster. (n.d.). Culture. In Merriam-Webster.com dictionary. Retrieved September 9, 2019, from https://www.merriam webster.com/dictionary/culture
Film or video
MacCulloch , D . (Writer /Presenter ) , Bancroft , G . (Director/Producer) , & Salt, S. (Director/Producer) . ( 2010 ). Diarmaid MacCulloch’s a history of Christianity [ Film ]. BBC Productions .
YouTube or streaming media
Harvard University. (2019, August 28). Soft robotic gripper for jellyfish [Video]. YouTube. https://www.youtube.com/watch v=guRoWTYfxMs
Books McDonald, G. (2015). Business ethics: A contemporary approach. Cambridge University Press. B ook Chapter Roberts, J. (2015). Mindfulness for all in action. In S. Walker (Ed.), Psychosocial interventions in mental health nursing (pp. 63-80).
Sage Publications. Newspaper Articles Pollack, A. (2016, July 16). New patents aim to delay generics of biologics. The New York Times , B1, B4. Encyclopedias Falola , T. , & Jean-Jacques, D. (Ed s .). ( 2016 ). Africa: An e ncyclopedia of culture and society (Vols. 1 ‐ 3 ). A BC-CLIO .
Research Help | [email protected]
303-458-4031 | 1-800-388-2366 x 4031
Research Help
Research Help hours 303-458-4031 1-800-388-2366 x4031 [email protected] Schedule a research consultation
APA Handouts
- APA 7th Edition Reference Examples Printable handout of APA Reference Examples
- APA Note on DOIs & URLs A guide to including DOIs & URLs in the References section.
- APA In-text Citations An overview of how to use in-text citations following APA guidelines.
- APA Student Template A student template to use to format a paper in APA 7th Edition
- APA Student Paper Setup Guide A guide to help you setup your paper in APA 7th edition from APA Style Blog
APA Style Guides & Tutorials
- APA Style Instructional Aids APA Style tutorials, handouts, and samples from the American Psychological Association.
- APA Style Blog The APA Style Blog is the official companion to the Publication Manual of the American Psychological Association. It is run by a group of experts who work with APA Style daily. They publish weekly posts addressing writing, publishing, and APA Style.
- Purdue OWL: APA Formatting and Style Guide Purdue University's Online Writing Lab (OWL) guide to formatting and citing in APA Style.
APA Style Manuals
Publication Manual of the American Psychological Association (6th ed.)
Call number: BF76.7 .P83 2020
Multiple copies are available in the Dayton Memorial Library. If you need assistance, please contact the Research Help Desk.
Free Citation Generators
The library does not guarantee the citations created by the following services. It is suggested that all citations are thoroughly checked after creation.
EasyBib- Free MLA citation generator.
Mendeley - Free, downloadable "reference manager".
Zotero- Free, open source tool to help you collect, organize, and cite your research sources.
KnightCite - Maintained by the Heckman Library at Calvin College. Cite in APA, MLA, and Chicago.
UCSU Citation Builder - Created and managed by NCSU Libraries. Cite in APA, MLA, and Chicago.
Reference Management Tools
- Zotero Basics This is a 3 part tutorial by Kimberly Kemp, Research & Instruction Librarian introducing the basics of using Zotero to manage your references and citing while you write.
- Mendeley Basics This is a 3-part tutorial on the basics of using Mendeley by Research & Instruction Librarian Kimberly Kemp.
- << Previous: AMA
- Next: Chicago >>
- Last Updated: Jun 24, 2024 4:31 PM
- URL: https://libguides.regis.edu/c.php?g=1407512

APA Referencing: Formatting, Footnotes and Appendices
- In-Text Citation
- Reference List
- Formatting, Footnotes and Appendices
- AI - ChatGPT, Grammarly, Quilbot
- Audio Visual Material - Film, TV, YouTube, TED Talks
- Books, eBooks, Dictionaries, Encyclopedias
- Figures (Including images), Tables
- Health Resources
- Journal Articles, Magazines, Newspapers
- Legal Material - Acts, Regulations, Standards, Te Tiriti o Waitangi/Treaty of Waitangi
- Other - Brochures, Course Handouts
- Personal communication, Intranet, Indigenous Oral Traditions
- Webpages, Blog Post, Social Media
- Theses, Conference Papers, Reports, Grey Literature
For papers or manuscripts being submitted for publication , the order is as follows.
Student assignments will not include all these sections.
- Your tutor may or may not request a cover page for the front of your assignment. Please check with them. If they do request a cover page, there should be a copy of it in Moodle.
- Student assignments do not include an abstract.
- You do have text (the body of your assignment)
- You have a reference list
- You may have tables, figures or appendices depending on your assignment
- APA does not use footnotes for references as it is an author-date citation style. The only time you use footnotes with APA is to provide additional content or copyright attribution (See information below)
Font Size and Line Spacing
Papers or manuscripts being submitted for publication
Check the guidelines set out in the journal you are submitting to or the Whitireia/WelTec Master's theses guidelines. The APA Manual has these recommendations:
- Font size is Calibri 11, Arial 11, Times New Roman 12, Georgia 11, Lucida Sans Unicode 10 (see APA Manual p. 44 for more information)
- Line spacing is usually double-spaced for the entire paper (for exceptions see the APA Manual p. 45)
Student assignments
Check with your tutor or in your programme handbook about what font size and spacing you should use for assignments.
Some options APA suggest for font size are:
- Times New Roman 12
Line spacing
- For the body of your assignment it is usually 1.5
- The reference list is double-spaced. Check out the APA Referencing Guide to Hanging Indentation to see how to do this)
APA does not use footnotes for references because it is an author-date citation style where it uses in-text citations to direct the reader to a source in the reference list. The footnote – bibliography method is used in other referencing styles such as MHRA or Chicago etc.
The only time you use footnotes with APA is to provide additional content or copyright attribution .
Content footnotes:
- Additional content that supplements the text
- Should be included only if they strengthen/enhance the discussion
Copyright attribution:
- Copyright attribution is required in a footnote when reproducing lengthy quotations or test/scale items in text
Numbering and Formatting
- Number all footnotes consecutively in the order they appear, use superscript Arabic numerals within the text
- They appear in the footer or on a separate page following references
- If on a separate page - Label section "Footnotes" in bold, centred at the top of the page. Write footnotes as double-spaced indented paragraphs which begin with superscript footnote number.
Sometimes you may want to include information that supplements your assignment or manuscript's content. Include an Appendix only if it helps your reader understand, evaluate or replicate the study or theoretical argument being made.
- Begin each appendix on a separate page
- Appendices are after any references, footnotes, tables and figures
- If a paper has one appendix label it Appendix
- If there is more than one appendix, label each with Appendix and a capital letter e.g., Appendix A Appendix B etc in the order in which they are mentioned in text
- Each appendix should be mentioned at least once in the text by its label
- The appendix title should describe its contents
- Place the appendix labels and titles in bold and centred on separate lines at the top of the page on which the appendix begins
- Use Title Case for the appendix label and appendix title i.e., Main words have a capital letter, minor words have a lower case
Appendix A (Appendix label)
List of Research Questions (Appendix title)
- The content of the appendix is formatted the same as the body of the assignment.
For more information see the APA Manual p. 41.
Useful links
Whitireia/weltec library guides.
APA Referencing Quick Guide
APA Referencing Guide to Hanging Indentation
Introduction to APA Referencing Guide
Key Changes between APA 6th and APA 7th edition (University of Auckland)
Paraphrasing Author(s) Multiple Times in a Paragraph
Whitireia/WelTec Learning Support Guides
Assignment Writing - Covers p lagiarism , paraphrasing
Tūāpapa Online Study Hub Modules. To access go to Moodle:
Click here if you are a Whitireia student.
Click here if you are a Weltec student.
- Log in if prompted
- Click Academic Communication, then Introduction to APA and Plagiarism & Academic Integrity
Referencing Tools
APA Interactive, Massey University
APA Style Blog
Referencite, University of Auckland
Referencing software
Mendeley
Avoiding plagiarism guide
Hill, D. J. (2015). A beginners' guide to plagiarism: What is plagiarism and how can you avoid it? Ako Aotearoa. https://ako.ac.nz/assets/Knowledge-centre/RHPF-c57-A-beginners-guide-to-plagiarism/PRACTICAL-GUIDE-BOOK-A-Beginners-Guide-to-Plagiarism.pdf
- << Previous: Reference List
- Next: AI - ChatGPT, Grammarly, Quilbot >>
- Last Updated: Jun 24, 2024 8:57 AM
- URL: https://whitireia.libguides.com/APA_Referencing

- Harvard Library
- Research Guides
- Harvard Graduate School of Design - Frances Loeb Library
Write and Cite
- Using Sources and AI
- Academic Integrity
Why acknowledge sources?
When is citing necessary, citing textual sources, citing images and non-textual sources, citing generative ai, links to style guides and citation resources.
- Academic Writing
- From Research to Writing
- GSD Writing Services
- Grants and Fellowships
- Reading, Notetaking, and Time Management
- Theses and Dissertations
Reasons for citing sources are based on academic, professional, and cultural values. At the GSD, we cite to promote
- Integrity and honesty by acknowledging the creative and intellectual work of others.
- The pursuit of knowledge by enabling others to locate the materials you used.
- The development of design excellence through research into scholarly conversations related to your subject.
Cite your source whenever you quote, summarize, paraphrase, or otherwise include someone else's
- Words
- Opinions, thoughts, interpretations, or arguments
- Original research, designs, images, video, etc.
- Chicago Style
Citations follow different rules for structure and content depending on which style you use. At the GSD, mostly you will use Chicago or APA style. Often you can choose the style you prefer, but it's good to ask your professor or TA/TF. Whichever style you use, be consistent. We recommend using Zotero , a citation-management tool, to structure your citations for you, but you should always check to make sure the tool captures the correct information in the correct place.
Chicago Style
Citing print sources.
Footnote - long (first time citing the source)
1. Joseph Rykwert, The Idea of a Town: The Anthropology of Urban Form in Rome, Italy and the Ancient World , (New Jersey: Princeton University Press, 1976), 35.
Footnote - short (citing the source again)
1. Rykwert, The Idea of a Town , 35.
In-text citation (alternative to footnotes)
(Rykwert 1976, 35)
Bibliography (alphabetical order and hanging indentation)
Rykwert, Joseph. The Idea of a Town: the Anthropology of Urban Form in Rome, Italy and the Ancient World . New Jersey: Princeton University Press, 1976.
Chapter
1. Diane Favro, “The Street Triumphant: The Urban Impact of Roman Triumphal Parades,” in Streets: Critical Perspectives on Public Space , ed. Zeynep Çelik , Diana Favro, and Richard Ingersoll (Berkeley: University of California Press,1994), 153.
1. Favro, “The Street Triumphant,” 156.
In-text citation (called "author-date," an alternative to footnotes)
(Favro 1994, 153)
Bibliography (alphabetical order and hanging indentation)
Favro, Diane. “The Street Triumphant: The Urban Impact of Roman Triumphal Parades.” In Streets: Critical Perspectives on Public Space, edited by Zeynep Çelik, Diane G. Favro, and Richard Ingersoll, 151-164. Berkeley: University of California Press, 1994.
Journal Article
1. Hendrik Dey, “From ‘Street’ to ‘Piazza’: Urban Politics, Public Ceremony, and the Redefinition of platea in Communal Italy and Beyond” Speculum 91, no.4 (October 2016): 919.
1. Dey, “From ‘Street’ to ‘Piazza,’” 932.
Dey, Hendrik. “From ‘Street’ to ‘Piazza’: Urban Politics, Public Ceremony, and the Redefinition of platea in Communal Italy and Beyond.” Speculum 91, no.4 (October 2016): 919-44.
APA Style
In-text citation
(Rykwert 1976 p. 35)
Footnote (for supplemental information)
1. From The idea of a town: The anthropology of urban form in Rome, Italy and the ancient world by Joseph Rykwert, 1976, New Jersey: Princeton University Press.
Bibliography/Reference (alphabetical order and hanging indentation)
Rykwert, J. (1976). The idea of a town: The anthropology of urban form in Rome, Italy and the ancient world . Princeton University Press.
In-Text Citation
(Favro 1994 p.153)
Footnote (for supplemental information)
1. From the chapter "The street triumphant: The urban impact of Roman triumphal parades" in Streets: Critical perspectives on public space, edited by Zeynep Çelik , Diana Favro, and Richard Ingersoll, 1994, Berkeley: University of California Press.
Favro, D. (1994) “The street triumphant: The Urban Impact of Roman Triumphal Parades.” In Zeynep Çelik, Diane G. Favro, and Richard Ingersoll (Eds.), Streets: Critical Perspectives on Public Space ( pp.151-164). University of California Press.
(Dey 2016 p.919)
Footnote (for supplemental material)
1. From the article “From ‘street’ to ‘Piazza’: Urban politics, public ceremony, and the Redefinition of platea in Communal Italy and Beyond” by Hendrik Dey in Speculum 91(4), 919. www.journals.uchicago.edu/toc/spc/2016/91/4
Dey, H. (2016). From "street" to "piazza": Urban politics, public ceremony, and the redefinition of platea in communal Italy and beyond. Speculum 91 (4), 919-44. www.journals.uchicago.edu/toc/spc/2016/91/4
Citing Visual Sources
Visual representations created by other people, including photographs, maps, drawings, models, graphs, tables, and blueprints, must be cited. Citations for visual material may be included at the end of a caption or in a list of figures, similar to but usually separate from the main bibliography.
When they are not merely background design, images are labeled as figures and numbered. In-text references to them refer to the figure number. Sometimes you will have a title after the figure number and a brief descriptive caption below it.
If you choose to include the citation under the caption, format it like a footnote entry. If you would prefer to have a list of figures for citation information, organize them by figure number and use the format of a bibliographic entry.

The construction of citations for artwork and illustrations is more flexible and variable than textual sources. Here we have provided an example with full bibliographic information. Use your best judgment and remember that the goals are to be consistent and to provide enough information to credit your source and for someone else to find your source.
Some borrowed material in collages may also need to be cited, but the rules are vague and hard to find. Check with your professor about course standards.
Visual representations created by other people, including photographs, maps, drawings, models, graphs, tables, and blueprints, must be cited. In APA style, tables are their own category, and all other visual representations are considered figures. Tables and figures both follow the same basic setup.
When they are not merely background design, images are labeled as figures and numbered and titled above the image. If needed to clarify the meaning or significance of the figure, a note may be placed below it. In-text references to visual sources refer to the figure number (ex. As shown in Figure 1...").
Citations for visual material created by other people may either be included under the figure or note or compiled in a list of figures, similar to but usually separate from the main bibliography.
Figures may take up a whole page or be placed at the top or bottom of the page with a blank double-space below or above it.
If you choose to include the citation under the figure, format it like a bibliographic entry. If you would prefer to have a list of figures for citation information, organize them by figure number and use the format of a bibliographic entry. Here is a detailed example. Some figures will require less bibliographic information, but it is a good practice to include as much as you can.

The construction of citations for artwork and illustrations is more flexible and variable than for textual sources. Here we have provided an example with full bibliographic information. Use your best judgment and remember that the goals are to be consistent and to provide enough information to credit your source and for someone else to find your source.
Citing Generative AI
The rules for citing the use of generative AI, both textual and visual, are still evolving. For guidelines on when to cite the use of AI, please refer to the section on Academic Integrity. Here, we will give you suggestions for how to cite based on what the style guides say and what Harvard University encourages. We again recommend that you to ask your instructors about their expectations for use and citation and to remain consistent in your formatting.
The Chicago Manual of Style currently states that "for most types of writing, you can simply acknowledge the AI tool in your text" with a parenthetical comment stating the use of a specific tool. For example: (Image generated by Midjourney).
For academic papers or research articles, you should have a numbered footnote or endnote
Footnote - prompt not included in the text of the paper
1. ChatGPT, response to "Suggest three possible responses from community stakeholders to the proposed multi-use development project," OpenAI, March 28, 2024, https://chat.openai.com/chat.
Footnote - prompt included in the text of the paper
1. Text generated by ChatGPT, OpenAI, March 28, 2024, https://chat.oenai.com/chat
Footnote - edited AI-generated text
1. Text generated by ChatGPT, OpenAI, March 28, 2024, edited for clarity, https://chat.oenai.com/chat
In-text citation (called "author-date," an alternative to footnotes)
(Text generated by ChatGPT, OpenAI) or (Text generated by ChatGPT, OpenAI, edited for clarity)
Chicago does not encourage including generative AI in a bibliography unless the tool also generates a direct link to the same generated content.
https://www-chicagomanualofstyle-org.ezp-prod1.hul.harvard.edu/qanda/data/faq/topics/Documentation/faq0422.html
The APA style team currently says to "describe how you used the tool in your Methods section or in a comparable section of your paper," perhaps the introduction for literature reviews and response papers. In your paper, state the prompt followed by the resulting generated text. Cite generative AI use according to the rules you would use for citing an algorithm. Include the URL if it leads directly to the same generated material; otherwise, the URL is optional.
(OpenAI, 2024)
Footnote (for supplemental material)
APA does not yet provide a structure or example for a footnote. If you need to mention generative AI in a footnote, stay as consistent with formatting as possible.
OpenAI. (2024). ChatGPT (Mar 14 version) [Large language model]. https://chat.openai.com/chat
These links take you to external resources for further research on citation styles.
- Chicago Manual of Style 17th Edition Online access to the full manual through Hollis with a quick guide, Q&A, video tutorials, and more.
- CMOS Shop Talk: How Do I Format a List of Figures? A brief description of how to format a list of figures with an attached sample document.
- Documenting and Citing Images in Chicago A Research guide from USC with nice examples of images with citations.
- Harvard Guide to Citing Sources A guide from Harvard Libraries on citing sources in Chicago style.
- A Manual for Writers of Research Papers, Theses, and Dissertations: Chicago Style for Students and Researchers A Chicago manual specifically for students with clear and detailed information about citing for papers rather than publications.
- Chicago Manual of Style Q&A Citing Generative Artificial Intelligence
- APA Style The main page of the official APA website that directs you to various topics on style and formatting
- APA Style Manual 7th Edition Online access to the full APA Style Manual (scanned) through Hollis.
- APA Style Common Reference Examples A list of sample references organized by type.
- APA Style Sample Papers Links to sample papers that model how to create citations in APA.
- Formatting Checklist This page is a quick guide to all kinds of formatting, from the title page to the bibliography, with links to more detailed instructions.
- Harvard Guide to Citing Sources A guide from Harvard Libraries on citing sources in APA style.
- Journal Article References This page contains reference examples for journal articles.
- In-Text Citations in APA Style A place to learn more about rules for citing sources in your text.
- Tables and Figures This page leads to explanations about how to format tables and figures as well as examples of both.
- How to Cite ChatGPT Here are the APA's current rules for citing generative AI and ChatGPT in particular.
- << Previous: Academic Integrity
- Next: Academic Writing >>
- Last Updated: Jun 24, 2024 11:19 AM
- URL: https://guides.library.harvard.edu/gsd/write
Harvard University Digital Accessibility Policy
Generate accurate APA citations for free
- Knowledge Base
- APA Style 6th edition
- How to cite a book in APA Style (6th edition)
Citing a Book in APA Style (6th Edition) | Format & Examples
Published on November 5, 2020 by Jack Caulfield . Revised on January 25, 2024.
A book citation in APA Style always includes the author’s name, the publication year, the book title, and the publisher.
You can use our free APA Citation Generator to generate your APA book citations . Just paste the ISBN or DOI and the generator retrieves all the necessary information.
Generate accurate APA citations with Scribbr
Table of contents, basic book citation format, ebooks and online books in apa, citing a chapter from an edited book, multivolume books, where to find the information for an apa book citation.
The APA in-text citation for a book includes the author’s last name, the year, and (if relevant) a page number.
In the reference list , start with the author’s last name and initials, followed by the year. The book title is written in sentence case (only capitalize the first word and any proper nouns). Include other contributors (e.g. editors and translators) and the edition if specified.
| Format | Last name, Initials. (Year). . (Contributor initials, last name, role.) (Edition). City, State/Country: Publisher. |
| Example | Anderson, B. (1983). . London, UK: Verso. |
| In-text citation | (Anderson, 1983, p. 23) |
Are your APA in-text citations flawless?
The AI-powered APA Citation Checker points out every error, tells you exactly what’s wrong, and explains how to fix it. Say goodbye to losing marks on your assignment!
Get started!
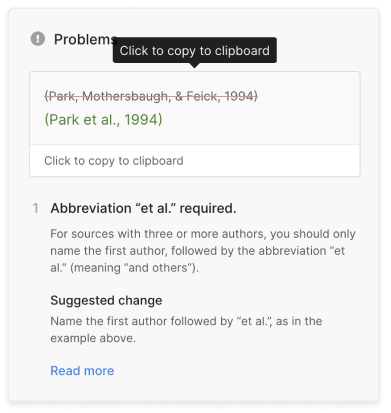
To cite a book you accessed online, replace information about the publisher with information about the book’s format and location online.
Books accessed on e-readers
A citation of an ebook (i.e. a book accessed on an e-reader) includes the ebook format in square brackets. Add a DOI where available, and otherwise link to the page where the ebook can be purchased or accessed.
Since ebooks sometimes do not include page numbers, APA recommends using other methods of identifying a specific passage in your in-text citations – for example, a chapter or section title or a paragraph number.
| Format | Last name, Initials. (Year). [ebook format information]. Retrieved from URL or https://doi.org/xxxxxx |
| Example | Burns, A. (2018). [Kindle version]. Retrieved from https://amzn.to/2ObKrVf |
| In-text citation | (Burns, 2018, para. 15) |
Books accessed online
A book accessed through a web browser (for example, in PDF form or on Google Books) follows a slightly different format:
| Format | Last name, Initials. (Year). . Retrieved from URL or https://doi.org/xxxxxxxx |
| Example | Brück, M. (2009). . https:/doi.org/10.1007/978-90-481-2473-2 |
| In-text citation | (Brück, 2009, p. 15) |
When citing a particular chapter from a book containing texts by various authors (e.g. a collection of essays), begin the citation with the author of the chapter and mention the book’s editor(s) later in the reference. A page range identifies the chapter’s location in the book:
| Format | Last name, Initials. (Year). Title of chapter. In Initials. Last name (Ed. or Eds.), (pp. page range). Publisher. DOI if available |
| Example | Belsey, C. (2006). Poststructuralism. In S. Malpas & P. Wake (Eds.), (pp. 51–61). New York, NY: Routledge. |
| In-text citation | (Belsey, 2006, p. 55). |
Citing a single volume
When citing from one volume of a multivolume book, the format varies slightly depending on whether each volume has a title or just a number.
If the volume has a specific title, this should simply be written as part of the title in your reference list entry:
Eliot, T. S. (2015). The poems of T. S. Eliot: Vol. 1. Collected and uncollected poems (Ricks, C., & McCue, J., Eds.). London, England: Faber & Faber.
If the volume is only numbered, not titled, the volume number is not italicized and appears in parentheses after the title:
Dylan, B. (2005). Chronicles (Vol. 1) . New York, NY: Simon & Schuster.
Citing a multivolume book as a whole
If you refer to the book in general, you may wish to cite the whole thing rather than a specific volume. In this case, individual volume titles are not included even if they do exist:
Eliot, T. S. (2015). The poems of T. S. Eliot (Vols. 1–2) (Ricks, C., & McCue, J., Eds.). London, England: Faber & Faber.
Scribbr Citation Checker New
The AI-powered Citation Checker helps you avoid common mistakes such as:
- Missing commas and periods
- Incorrect usage of “et al.”
- Ampersands (&) in narrative citations
- Missing reference entries
All the information you need to cite a book can usually be found on the title page and the copyright page:

The APA reference list entry for the book above would look like this:
Butler, C. (2002). Postmodernism: A very short introduction . Oxford, England: Oxford University Press.
Cite this Scribbr article
If you want to cite this source, you can copy and paste the citation or click the “Cite this Scribbr article” button to automatically add the citation to our free Citation Generator.
Caulfield, J. (2024, January 25). Citing a Book in APA Style (6th Edition) | Format & Examples. Scribbr. Retrieved June 24, 2024, from https://www.scribbr.com/apa-style/6th-edition/archived-apa-book-citation/
Is this article helpful?

Jack Caulfield
Scribbr apa citation checker.
An innovative new tool that checks your APA citations with AI software. Say goodbye to inaccurate citations!
Citation Examples

APA Citation Examples - References of Different Sources
Published on: Jun 17, 2024
Last updated on: Jun 21, 2024

A Writer's Guide to How to Cite a Book | APA, MLA, Chicago and Harvard
How to Cite a Newspaper Article - A Comprehensive Guide
How to Cite an Image in Different Citation Styles
ChatGPT Citations - How to Cite AI-Generated Content
How to Cite a Website in Different Citation Styles
A Comprehensive Guide on How to Cite a Journal Article
Quick and Easy Guide on How to Cite Videos in Common Formats
How to Cite Wikipedia in APA, MLA & Chicago Styles
How to Cite a PDF in APA, MLA, Chicago & Harvard Format
A Complete Guide on How to Cite an Interview
MLA Citation Examples: A Clear Guide for Easy Referencing
How to Cite a Lecture in Various Styles | Examples & Tips
In-Text Citation Examples Made Easy: A Practical Guide
Do you need to write a paper or a report using APA style ? If so, you may be wondering how to cite different sources correctly and avoid plagiarism.
APA style is one of the most common writing styles and formats for academic documents, especially in the field of behavioral and social sciences. It consists of two main components:
In-text citations (parenthetical citation) and reference list entries .
In this blog post, we will show you some examples of how to cite different sources in APA style.
So, let’s dive right in!
Examples of Citing Different Sources in APA
In APA format, the rules for citing different sources may vary. The format of your reference list entry and in-text citation depends on the type of source, such as a book, a journal article, a website, or an online source.
Here are some examples of how to cite different sources in APA style.
Books are one of the most common sources in academic writing. To cite a book in APA style, you need to provide the author, year, title, and publisher of the book. If it's a chapter, be sure to include page numbers as well.
Here are some examples of how to cite books in APA style:
Basic Format:
Smith, J. (2024). The History Of Chocolate. New York, NY: Chocolate Press.
Book Chapter:
Doe, J. (2024). The Health Benefits Of Chocolate. In J. Smith (Ed.), The History Of Chocolate (Pp. 123-145). New York, NY: Chocolate Press.
Online Book:
James, J. (2024). The Art Of Chocolate Making. Retrieved From https://www.chocolate.com/ebooks/art-of-chocolate.pdf
Here are some examples of how you can add in-text citations of books in APA:
(Smith, 2024)
(Doe, 2024)
(James, 2024) |
Journal Articles
Journal articles are another common source in academic writing. Here are some examples of how to cite journal articles in APA style:
Smith, J., & Doe, J. (2024). Chocolate Consumption And Cognitive Performance: A Meta-Analysis. Journal Of Chocolate Studies , 12(1), 1-15.
Online Journal:
James, J., Smith, J., & Doe, J. (2024). Chocolate Preferences And Personality Traits: A Cross-Cultural Study. Chocolate Psychology , 5(2), 23-37. Https://doi.org/10.1001234/123
Multiple Authors:
Smith, J., Doe, J., James, J., Lee, S., & Kim, J. (2024). Chocolate And Happiness: A Longitudinal Survey Of Chocolate Lovers. Journal Of Happiness Research , 7(3), 89-105.
Here are some examples of how you can add in-text citations of journal in APA:
Here is an example of how to cite a website in APA style:
Chocolate World. (2024). About Our World. Retrieved from https://www.chocolate.com/about-our-world.
Other Online Sources
Besides websites, other online sources can be cited in APA style, such as videos, images, blogs, etc.
Here are some examples of how to cite other online sources in APA style:
Smith, J. (2024, February 14). How To Make Chocolate Brownies . Chocolate Lovers Blog. https://www.chocolate.com/blog/how-to-make-chocolate-brownies .
In-text Citations:
(Smith, 2024)
Youtube Video:
Doe, J. [Chocolate Channel]. (2024, January 10). How To Temper Chocolate . [Video]. Youtube. https://www.youtube.com/watch?v=123456789
(Doe, 2024)
James, J. (2024). Chocolate Cake. [Photograph]. Chocolate Gallery. https://www.chocolate.com/gallery/chocolate-cake
(James, 2024)
Say Goodbye to Citation Troubles with PerfectEssayWriter.ai’s Citation Machine
Citing sources can be a tedious and time-consuming task for any student or researcher. But with PerfectEssayWriter.ai’s APA citation machine , you can easily generate accurate and consistent citations in any style you need.
All you need to do is select the source type, enter the relevant information, and click the generate button.
With our citation machine , you will get a ready-to-use citation that you can copy and paste into your document.
Cathy Aranda (Marketing)
Cathy is a highly dedicated author who has been writing for the platform for over five years. With a Master's degree in Mass Communication, she is well-versed in various forms of writing such as articles, press releases, blog posts, and whitepapers. As an essay writing guide author at PerfectEssayWriter.ai, she has been helping students and professionals improve their writing skills by offering practical tips on research, citation, sentence structure, and style.
On This Page On This Page
Share this article
Keep Reading


IMAGES
VIDEO
COMMENTS
In the reference list, start with the author's last name and initials, followed by the year. The book title is written in sentence case (only capitalize the first word and any proper nouns ). Include any other contributors (e.g. editors and translators) and the edition if specified (e.g. "2nd ed."). APA format. Last name, Initials.
Book/Ebook References. Use the same formats for both print books and ebooks. For ebooks, the format, platform, or device (e.g., Kindle) is not included in the reference. This page contains reference examples for books, including the following: Whole authored book. Whole edited book. Republished book, with editor.
Cite a book automatically in APA. The following contains a list of the most commonly cited print book sources. E-books are described on our "Electronic Sources" page . For a complete list of how to cite print sources, please refer to the 7 th edition of the APA Publication Manual. Note: If available, APA 7 requires a DOI for all works that have ...
Solution #2: How to cite a republished translated book. For translated books, include the name of the original author at the start of the citation, but for the year, include the date of publication for the version you are using. After the title, include the translator's name, and after the publisher, provide the original publication date.
Put a comma and an ampersand (&) before the name of the last author cited. Note: For works with three or more authors, the first in-text citation is shortened to include the first author's surname followed by "et al." Note: If the listed names are editors rather than authors, include " (Eds.)." at the end of the list of names.
Basic guidelines for formatting the reference list at the end of a standard APA research paper Author/Authors Rules for handling works by a single author or multiple authors that apply to all APA-style references in your reference list, regardless of the type of work (book, article, electronic resource, etc.)
To cite a book chapter, first give the author and title (in quotation marks) of the chapter cited, then information about the book as a whole and the page range of the specific chapter. The in-text citation lists the author of the chapter and the page number of the relevant passage. MLA format. Author last name, First name.
Throughout your paper, you need to apply the following APA format guidelines: Set page margins to 1 inch on all sides. Double-space all text, including headings. Indent the first line of every paragraph 0.5 inches. Use an accessible font (e.g., Times New Roman 12pt., Arial 11pt., or Georgia 11pt.).
Example: Finney, J. (1970). Time and again. Simon and Schuster. Notes: When citing a book in APA, keep in mind: The title of the book should be written in sentence case. This means you should capitalize the first letter of the first word of the title and any subtitles, as well as the first letter of any proper nouns.
☑ Each in-text citation must match its reference list citation. The author name and year in the reference list citation and in-text citation must be the same. If you make a correction to the author and/or date in one of your references, you must also edit all of the corresponding in-text citations.
How to Cite an Edited Book in APA Format. This reference format is very similar to the book format apart from one extra inclusion: (Ed(s)). The basic format is as follows: Edited book example: Williams, S.T. (Ed.). (2015). Referencing: A guide to citation rules (3rd ed.). New York, NY: My Publisher . How to Cite a Chapter in an Edited Book in ...
When using APA format, follow the author-date method of in-text citation. This means that the author's last name and the year of publication for the source should appear in the text, like, for example, (Jones, 1998). One complete reference for each source should appear in the reference list at the end of the paper.
For a work with more than 20 authors, list the first 20 authors and insert ellipses. After the ellipses, write the last author's name. Author's Last Name, First Initial., Author's Last Name, First Initial., (list first 20 authors), . . . Final Author's Last Name, First Initial. (Year of Publication). Title of Book.
In the text, when you have paraphrased an edited book chapter, cite the author (s) of the chapter and the year of publication of the book, as shown in the following examples. Parenthetical citation of a paraphrase from an edited book chapter: (Fountain, 2019) Narrative citation of a paraphrase from an edited book chapter: Fountain (2019) If the ...
To cite an article in such a collection, you should list the last name and first initial of the individual author (s), followed by the publication date and chapter title. Next, the editors should be listed, followed by the title of the book and the page numbers of the chapter. The publisher's name goes last.
APA Style papers should have double-spaced text throughout the entire paper (including quotations and references). To make your paper double-spaced in Microsoft Word, highlight the text you want double-spaced, and then click Layout.Next, click on the arrow to the right of the word Paragraph (a pop-up appears).From the drop-down menu under Line Spacing, select Double (default choice is Multiple ...
The most confusing and time-consuming part of writing an APA style paper is formatting each source in the reference list correctly, because the format is different depending on whether the source is a website, book, journal, newspaper, or any other medium. 💡 Our interactive templates automatically update to show how a citation should be ...
On the first line of the page, write the section label "References" (in bold and centered). On the second line, start listing your references in alphabetical order. Apply these formatting guidelines to the APA reference page: Double spacing (within and between references) Hanging indent of ½ inch.
Citing books in APA Print books with one author: APA citation format: Author Last name, First initial. Middle initial. (Year Published). Title of work. Publisher. Example: Moriarty, L. (2014). Big little lies. G. P. Putnam's Sons. Print books with two or more authors: Structure:
In-text citations point the reader to the sources' information on the references page. The in-text citation typically includes the author's last name and the year of publication. If you use a direct quote, the page number is also provided. More information can be found on p. 253 of the 7th edition of the Publication Manual of the American ...
The Chicago/Turabian style of citing sources is generally used when citing sources for humanities papers, and is best known for its requirement that writers place bibliographic citations at the bottom of a page (in Chicago-format footnotes) or at the end of a paper (endnotes). The Turabian and Chicago citation styles are almost identical, but ...
The basic format for an in-text citation is: Title of the Book (Author Last Name, year). Examples. One author: Where the Wild Things Are (Sendak, 1963) is a depiction of a child coping with his anger towards his mom. Two authors (cite both names every time): Brabant and Mooney (1986) have used the comic strip to examine evidence of sex role stereotyping.
Introduction to APA Style Toggle Dropdown. ... Referencing: Books. Book with Author(s) Book with Author(s) and Editor(s) ... You must cite and reference every story, essay or poem that you use in your paper separately, unless you are referring generally to the entire work. Formatting Examples.
Mendeley- Free, downloadable "reference manager". Zotero- Free, open source tool to help you collect, organize, and cite your research sources. KnightCite- Maintained by the Heckman Library at Calvin College. Cite in APA, MLA, and Chicago. UCSU Citation Builder- Created and managed by NCSU Libraries. Cite in APA, MLA, and Chicago.
APA Referencing Quick Guide . APA Referencing Guide to Hanging Indentation . Introduction to APA Referencing Guide. Key Changes between APA 6th and APA 7th edition (University of Auckland) Paraphrasing Author(s) Multiple Times in a Paragraph . Whitireia/WelTec Learning Support Guides. Assignment Writing - Covers p lagiarism, paraphrasing
APA Style Citing Print Sources . Book . In-text citation (Rykwert 1976 p. 35) Footnote (for supplemental information). 1. From The idea of a town: The anthropology of urban form in Rome, Italy and the ancient world by Joseph Rykwert, 1976, New Jersey: Princeton University Press.. Bibliography/Reference (alphabetical order and hanging indentation). Rykwert, J. (1976).
Basic book citation format. The APA in-text citation for a book includes the author's last name, the year, and (if relevant) a page number. In the reference list, start with the author's last name and initials, followed by the year. The book title is written in sentence case (only capitalize the first word and any proper nouns).
APA Style has specific guidelines for the format of the reference page, which is where you list all the sources you've cited in your paper. The guidelines here are for the most recent edition, the 7th edition, of the APA Publication Manual.. Your reference page should begin on a new page immediately after the main text, and the references should be listed in alphabetical order.
Here are some examples of how to cite different sources in APA style. Books. Books are one of the most common sources in academic writing. To cite a book in APA style, you need to provide the author, year, title, and publisher of the book. If it's a chapter, be sure to include page numbers as well. Here are some examples of how to cite books in ...