Design and implementation of a real-time face recognition system based on artificial intelligence techniques
- Regular Paper
- Published: 05 April 2024
- Volume 30 , article number 114 , ( 2024 )

Cite this article
- Chih-Yung Chang 1 ,
- Arpita Samanta Santra 2 ,
- I-Hsiung Chang 3 ,
- Shih-Jung Wu 1 ,
- Diptendu Sinha Roy 4 &
- Qiaoyun Zhang 1 , 5
42 Accesses
Explore all metrics
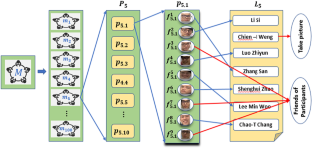
This paper mainly discusses the asymmetric face recognition problem where the number of names in a name list and the number of faces in the photo might not be equal, but each face should be automatically labeled with a name. The motivation for this issue is that there had been many meetings in the past. After each meeting, the participant took group photos. The meeting provided only a corresponding name list of participants without one-to-one labels. In the worst case, the group photo might mix with the faces that were not participating in the meeting. Another reason for asymmetric face recognition is that some meeting personnel did not appear in photos because they assisted in taking pictures. This paper proposes an asymmetric face recognition mechanism, called AFRM in short. Initially, the proposed AFRM adopts the histogram of oriented gradients (HOG) and support vector machine (SVM) to detect and extract all faces from photos. Next, AFRM extracts the features from each face using the convolution feature map ( Conv_FF ) and adopts the features to partition the faces into different classes. Then, the AFRM applies the statistic-based mechanism to map each name in the name list to each face class. According to this mapping, each face will be associated with one name. To quickly identify a face during the meeting, the AFRM applies the K-nearest neighbors ( KNN ) to represent the features of each face. During the new meeting, the proposed AFRM can extract the feature of one face and then adopts KNN to derive the features. Experimental results show that the proposed mechanism achieves more than 97% accuracy without one-to-one name and face labeling.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Real-Time Face Detection and Face Recognition: Study of Approaches

Face Detection and Recognition System
Face Recognition Based on Relative Gradient Magnitude Strength
Mona Nagy ElBedwehy, G. M. Behery & Reda Elbarougy
Data availability
The datasets generated during the current study are not publicly available but are available from the corresponding author.
Damale, R. C. and Pathak, B. V.: Face recognition based attendance system using machine learning algorithms. In: 2018 Second International Conference on Intelligent Computing and Control Systems (ICICCS), IEEE, pp. 414–419 (2018)
Wang, H. and Guo, L.: Research on face recognition based on deep learning. In: 2021 3rd International Conference on Artificial Intelligence and Advanced Manufacture (AIAM), IEEE, pp. 540–546 (2021)
Haji, S. and Varol, A.: Real time face recognition system (RTFRS). In: 2016 4th International Symposium on Digital Forensic and Security (ISDFS), pp. 107–111 (2016)
Stekas, N. and Heuvel, D.: Face recognition using local binary patterns histograms (LBPH) on an FPGA-Based System on Chip (SoC). In: 2016 IEEE International Parallel and Distributed Processing Symposium Workshops (IPDPSW), Chicago, pp. 300–304 (2016)
Ghorbel, A., Tajouri, I., Elaydi, W. and Masmoudi, N.: The effect of the similarity measures and the interpolation techniques on fractional eigenfaces algorithm. In: 2015 World Symposium on Computer Networks and Information Security (WSCNIS), IEEE, pp. 1–4 (2015)
Wan, M.H., Lai, Z.H.: Generalized discriminant local median preserving projections (GDLMPP) for face recognition. Neural Process 49 (3), 951–963 (2019)
Article Google Scholar
Rose, J., and Bourlai, T.: On designing a forensic toolkit for rapid detection of factors that impact face recognition performance when processing large scale face datasets. Securing Social Identity in Mobile Platforms. Springer, pp. 61–76 (2020)
Bao, J., Wang, Y., Cheng, Y.: Asymmetry label correlation for multi-label learning. Appl. Intell. 52 (6), 6093–6105 (2022)
Zhang, X., Yang, T., and Srinivasan, P.: Online asymmetric active learning with imbalanced data. In: Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, pp. 2055–2064 (2016)
Zheng, L., Yang, Y. and Hauptmann, A.G.: Person reidentification: Past, present and future. arXiv preprint arXiv:1610.02984 (2016).
Fu, B., Chen, C., Henniger, O., and Damer, N.: The relative contributions of facial parts qualities to the face image utility. In: 2021 International Conference of the Biometrics Special Interest Group (BIOSIG), IEEE, isbn. 978-1-66542-693-0, pp. 1–5, (2021)
Fu, B., Chen, C., Henniger, O., and Damer, N.: A deep insight into measuring face image utility with general and face-specific image quality metrics. In: Proceedings of the IEEE/CVF Winter Conference on Applications of Computer Vision, pp. 905–914 (2022)
Chen, K., Yi, T., Lv, Q.: LightQNet: lightweight deep face quality assessment for risk-controlled face recognition. IEEE Signal Process. Lett. 28 , 1878–1882 (2021)
Meng, Q., Zhao, S., Huang, Z. and Zhou, F.: Magface: a universal representation for face recognition and quality assessment. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 14225–14234 (2021)
Ge, Y., Zhu, F., Chen, D., Zhao, R., Li, H.: Self-paced contrastive learning with hybrid memory for domain adaptive object re-id. Adv. Neural. Inf. Process. Syst. 33 , 11309–11321 (2020)
Google Scholar
Lin, Y., Dong, X., Zheng, L., Yan, Y., Yang, Y.: A bottom-up clustering approach to unsupervised person reidentification. Proc. AAAI Conf. Artif. Intell. 33 (01), 8738–8745 (2019)
Fan, H., Zheng, L., Yan, C., Yang, Y.: Unsupervised person reidentification: clustering and fine-tuning. ACM Trans. Multimed. Comput. Commun. Appl. 14 (4), 1–18 (2018)
Lin, Y., Xie, L., Wu, Y., Yan, C. and Tian, Q.: Unsupervised person reidentification via softened similarity learning. In Proceedings of the IEEE/CVF conference on computer vision and pattern recognition, pp. 3390–3399 (2020)
Zeng, K., Ning, M., Wang, Y., and Guo, Y.: Hierarchical clustering with hard-batch triplet loss for person reidentification. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 13657–13665 (2020)
Wang, D. and Zhang, S.: Unsupervised person reidentification via multi-label classification. In: Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, pp. 10981–10990 (2020)
Cheng, E.J., Chou, K.P., et al.: Deep sparse representation classifier for facial recognition and detection system. Pattern Recogn. Lett. 125 , 71–77 (2019)
Zangeneh, E., Rahmati, M., Mohsenzadeh, Y.: Low resolution face recognition using a two-branch deep convolutional neural network architecture. Expert Syst. Appl. 139 , art. no. 112854 (2020)
Nguyen, D.T., Pham, T.D., Lee, M.B., Park, K.R.: Visible-light camera sensor-based presentation attack detection for face recognition by combining spatial and temporal information. Sensors 19 (2), 410 (2019)
He, G. and Jiang, Y.: Real-time Face Recognition using SVM, MLP and CNN. In 2022 International Conference on Big Data, Information and Computer Network (BDICN) . IEEE, pp. 762–767 (2022)
Download references
This study was not funded by any institution.
Author information
Authors and affiliations.
Tamkang University, New Taipei, Taiwan
Chih-Yung Chang, Shih-Jung Wu & Qiaoyun Zhang
National Tsing Hua University, Hsinchu, Taiwan
Arpita Samanta Santra
National Taiwan Normal University, Taipei, Taiwan
I-Hsiung Chang
National Institute of Technology, Shillong, India
Diptendu Sinha Roy
Chuzhou University, Chuzhou, China
Qiaoyun Zhang
You can also search for this author in PubMed Google Scholar
Contributions
All the authors have equally contributed, and all the authors have read and agreed to the published version of the manuscript.
Corresponding author
Correspondence to Chih-Yung Chang .
Ethics declarations
Conflict of interest.
The authors declare that they have no conflict of interest.
Ethical approval
This study does not involve either human subjects or animals.
Informed consent
All participating authors have been informed.
Additional information
Communicated by R. Huang.
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
Reprints and permissions
About this article
Chang, CY., Santra, A.S., Chang, IH. et al. Design and implementation of a real-time face recognition system based on artificial intelligence techniques. Multimedia Systems 30 , 114 (2024). https://doi.org/10.1007/s00530-024-01306-y
Download citation
Received : 29 March 2023
Accepted : 26 February 2024
Published : 05 April 2024
DOI : https://doi.org/10.1007/s00530-024-01306-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Face recognition
- Unsupervised learning
- Asymmetric training resources
- Meeting applications
- Find a journal
- Publish with us
- Track your research
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- Comput Intell Neurosci
- v.2021; 2021

Design of Facial Recognition System Based on Visual Communication Effect
Culture and Art Management of Hunan University, Korea, Guangzhou City 62399, Republic of Korea
Associated Data
The dataset can be obtained from the corresponding author upon request.
At present, facial recognition technology is a very cutting-edge science and technology, and it has now become a very hot research branch. In this research, first, the thesis first summarized the research status of facial recognition technology and related technologies based on visual communication and then used the OpenCV open source vision library based on the design of the system architecture and the installed system hardware conditions. The face detection program and the image matching program are realized, and the complete face recognition system based on OpenCV is realized. The experimental results show that the hardware system built by the software can realize the image capture and online recognition. The applied objects are testers. In general, the OpenCV-based face recognition system for testers can reliably, stably, and quickly realize face detection and recognition in this situation. Facial recognition works well.
In the context of continuous advancement in technology, traditional identification methods continue to withstand more and more challenges, and the accuracy of identification can no longer meet the needs. Nowadays, the recognition of biometric information is gradually attracting attention.
As one of the biometric recognition technologies, facial recognition technology occupies a pivotal position in identity recognition. [ 1 ] Facial recognition, as a multidisciplinary cross-integration technology, mainly includes technologies such as computers, information processing, and image feature recognition. Facial recognition technology has made great progress in recent years. Nature contains a variety of information, such as sound information, electric field information, visual information, magnetic field information, and thermal field information. Among them, visual information contains a huge amount of data [ 2 ]. How to extract useful information from these data? And applying these data to change our actual life and work will be of great significance. The proposition of “how to distinguish human identities” is embodied in the field of image processing technology, which is to use image processing methods to use specific algorithms to extract in-depth characteristic information related to individuals and to use the obtained characteristic information to distinguish other acquired characteristic information [ 3 ]. Therefore, according to the uniqueness of the characteristic information identification, the identification and confirmation of different people can be realized, so as to further use this as a credential to realize a technology for supervision, management, and control of individuals.
According to the development process of facial recognition technology, it can be divided into the following three recognition methods. (1) The facial recognition method is based on geometric features. The method is simple, but the recognition accuracy is low, and the recognition effect is not ideal, but it provides a new research idea for face recognition [ 4 ]. (2) The face recognition method based on template matching is implemented based on the global features of the face to be recognized. It is implemented based on the global features of the face to be recognized. First, the facial image is normalized and normalized. After morphological processing such as scale normalization, histogram equalization, and corrosion expansion, an 8 ∗ 8 template is then used to extract features from it using a method similar to the LBP algorithm to obtain a 64-bit hash code. There are n images in the training set. We will process all these n images by the above method to obtain the hash codes of n training sets. Similarly, we will process a face image to be recognized in the same way. Finally, we will wait. The hash code that recognizes the face image is compared with the hash code of each person in the training set. The main purpose is to compare the Hamming distance between them. The hash code of the face image to be recognized is compared with the hash code of each image in the training set. After hash code comparison, n Hamming distances are generated, the minimum value of these n Hamming distances is calculated, and it is determined that the human face image to be recognized is the most similar to the picture in the training set that produces the distance [ 5 ]. (3) The model-based facial recognition method, through the method of sample analysis, to obtain the template is used in the model; common models such as the human face recognition method are based on the hidden Markov model [ 6 ]; the facial image is regarded as the different expressions of the various organs of the face The face organ is regarded as an abstract state; the state and the form of expression are related through two random processes; a large number of face pictures are used as the actual training set, the model is trained, and this is determined by a certain algorithm. The optimal parameters of the model so that every person in the training set have an optimal model to match with it. In face recognition, calculate which model has the highest matching degree with the face feature to be recognized; then, the person to be identified and the person corresponding to the model in the training set are grouped into one category, that is, to find out which model is the most likely to produce the expression [ 7 ].
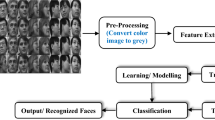
Facial recognition is the process of comparing the images collected by the camera with the facial images in the database, using relevant computer algorithms to analyze and extract effective identification feature information [ 8 – 10 ]. It combines multiple research fields such as image processing, computer graphics, visualization technology, human physiology, and pattern recognition. The basic process of facial recognition is shown in Figure 1 , and its technical process is divided into the following main parts.

Schematic diagram of facial recognition.
Aiming at the deficiencies in the current commonly used facial recognition technologies, this topic relies on Linux as the development platform, uses the Qt5 development environment, and uses the relevant image processing algorithms of the computer image processing software OpenCV to design a facial recognition system based on image processing [ 11 ]. Its core technology is facial image acquisition, image preprocessing, image feature value extraction, and image matching and recognition. Facial recognition technology is one of the most widely used technologies for image processing and analysis, which greatly facilitates people's work and life.
2. Facial Recognition System Design
2.1. design system architecture.
Based on the effect of visual communication, facial recognition technology uses image acquisition equipment to collect human facial information and input it into a computer for program calculation, and uses computer algorithm technology to process the collected facial information and analyze and extract features, so as to perform identity recognition. In a kind of technical way, the concrete facial recognition system design structure is shown in Figure 2 .

The architecture of the facial recognition system.
The architecture includes the use layer, the central layer, and the database layer. The use layer provides an environment with visual communication effects, and the user is using the layer operating system to meet expected needs [ 12 ]. As the control center of the facial recognition system, the central layer is the most important part of the entire system. It is composed of the resource management and facial system design center. The facial system design center is responsible for maintaining the task activity process. The hardware tool communication module, power supply module, wireless router module, and software tool combine visual communication elements, facial recognition programs, and image matching programs to form a facial recognition system design center [ 13 – 15 ]. Resource management is responsible for the initiation and termination of mission activities. The database layer collects facial image information through the image database data center and provides the system with relevant data required for facial recognition. The user layer provides a visual communication effect environment and sends instructions to the system according to the user's needs. The central layer recognizes the facial image after receiving the instructions [ 16 ]. After the recognition is completed, the image information is fed back to the user layer, and the user obtains what they need. The facial recognition image is sent to the database layer for storage, and when the central layer needs any relevant data, it is retrieved through the database layer.
2.2. System Hardware Construction
The initial task is received by the client and then assigned to the server. The client processes the facial image and submits the task to the processor. After the facial image is automatically recognized, the result of the image sequence is retrieved and used as the processor for automatic facial recognition during automatic recognition. Monitor the server for facial recognition to solve the problem of fewer network nodes. Task scheduling and facial recognition are completed by the processor and server [ 17 ]. Therefore, the most important part of the hardware of the automatic facial recognition system is to consider the memory size of the hardware. Because the smart device lacks a network port during image recognition, a wireless router needs to be used to establish a local area network ( Figure 3 ).

Hardware architecture of the automatic facial recognition system.
2.3. Structural Design of the Facial System
The facial recognition program is implemented based on the OpenCV library of the Linux platform. The facial recognition program of this system is completed under the integrated development environment Qt Creator. The program uses multiple functions in OpenCV [ 18 ]. Therefore, the OpenCV library must be transplanted to the embedded system, and the program can be executed smoothly. There is a wealth of functions available in the OpenCV library. It can run on operating systems such as Linux/Window/Mac. It provides a variety of algorithms related to image processing and machine vision, and it supports multiple computer programming languages. This system mainly uses the function functions in the two header files in the OpenCV library. cv.h: this header file contains functions that can realize image processing and computer vision and other related functions, such as image processing, pattern recognition, and camera calibration. highgui.h contains the functional functions of user interaction, such as image encoding and decoding, video capture, and GUI interface. The realization of the node function is mainly divided into two parts: face detection and image matching. The following content will describe the program realization of these two parts in detail.
2.3.1. Face Detection Program
Face detection is the first step of the facial recognition program, that is, the process of detecting and determining the location of the face from the image collected by the camera and separating the face from the image.

This function will open the camera after the program is executed and cyclically intercept a frame of the camera's image. The captured image is stored in the pCapture pointer of CvCapture type.

The cvLoad() function will load the file “haarcascade_frontalface_alt2.xm1” as a string. This file is an Adaboost cascaded face detection classifier based on Haar features. It is trained by extracting feature information from a large amount of face image information and is obtained. After the function loads the classifier, it will be cast to the CvHaarClassifierCascade type and assigned to the pointer cascadeo of the CvHaarClassifierCascade type.

Create a single-channel image, and its return value type is IplImage type, which is the preprocessed image information to be detected, which is passed to the detection function cvHaarDetectObjects() as a parameter.

The parameter pgray is the image information to be detected after preprocessing, and cascade is loaded with cvLoad( ), which is used to compare the features of the image to be detected with the Haar cascade classifier, through the cvHaarDetectObjects() function passing in the relevant parameters which realizes the function of detecting and locating the face from the image [ 19 ]. Use the above function to realize the function of the face detection part of the program, and then, save the face area image for subsequent use through the function. The realization process of the face detection function is shown in Figure 4 .

The execution flowchart of the face detection program.
2.3.2. Image Matching Program
The image matching program is another important part of the realization of the function of the system recognition node. The accuracy of the recognition result directly determines the success of the function. The image matching program of this system is implemented based on the SIFT algorithm [ 20 ]. The rotation invariance and scale invariance of the SIFT algorithm can just solve various problems encountered in the actual use of the system. There are mainly the following function calls in the process of program realization.
- unread(const string& filename, int flags = 1)
You can use this function to read the image and save the image information in a Mat variable.
- class SiftFeatureDetector

This program uses the function of detectoxdetect(). The detector is an object of the SiftFeatureDetecto: class. The function of the member function detect() it contains is to calculate the feature points in the image. The extractor.compute() function is used in the program, the extractor is an object of the SiftDescriptorExtractor class, and its member function compute() is used to specify the direction parameter for each key point and generate the key point descriptor. After the feature vectors of the two images are generated, the feature vectors of the respective key points of the two images can be used as the criterion for image similarity judgment. The process of implementing the image matching function call function is shown in Figure 5 .

Schematic diagram of image matching program execution.
2.3.3. Data Transmission Program Design
The master node with communication module will complete the image transmission function of the face [ 21 ]. When the face recognition node detects the current face, the facial image information of the current face will be transmitted to the designated master node through the facial recognition system In the directory, when the program detects that there is a file coming from the bus, the program will start the communication transmission module to send the image data to the facial recognition system. Among them, when the image information is transmitted through the Socket program, it is transmitted cyclically in a character array of 64 bytes. In order to make the program run normally, a communication module driver must be added to the kernel. ZTE's communication module driver is supported by files in the Linux kernel [ 22 ]. You only need to select the relevant options in the kernel compilation options. At this time, the content in the .config file needs to be changed as follows.

The usb_hcd structure is included in the Linux kernel, and the USB driver is described by it. The internal information, hardware resources, and he_ driver functions of the USB controller are all in this structure. The member function he_ drive in usb_ hed is a function used to operate the host controller, so it is very important. In the Linux kernel, we use the following functions to create HCD.

In the Kconfig file of the Linux kernel, we select “USB driver for GSM and CDMA modems.” This file contains the USB driver option configuration introduction. The location of the file is the kernel file\drivers\usb\serial directory. At this point, the driver of the communication module is added. The program running process is shown in Figure 6 .

Data transmission process program diagram.
Through the above program, the current facial image information is collected and the accuracy of the recognition with the face is realized. If it is not the face recognition system, the image information will be saved and transmitted to the socket program in the communication module on the master node through the network, and the image will be transmitted to the face recognition system.
3. Experimental Analysis
3.1. debugging of facial recognition program.
After the initialization procedure is completed, the facial recognition system will be started by the master node. The face recognition node will assign the logical address 0 × 101, and then, the recognition program will be started to collect and recognize the image. The program needs to be compiled and debugged before being transplanted to the embedded system. When the program is executed in the embedded system, only a recognition result will be returned, and the picture collection and recognition process will not be displayed. During debugging, the display picture collection will be added for the convenience of debugging and the code of the recognition process; just comment it when the program is transplanted to the embedded system. First, after the system program is started, the camera will be called to continuously collect image information, and the collection result is shown in Figure 7 :

Collection result.
Second, the face detection program will identify whether there is a face in the image. If there is a face, the face detection program will locate and intercept the face image. The interception result is shown in Figure 8 .

Screenshot of face.
Facial recognition algorithms have two important indicators: rejection rate and false recognition rate. The rejection rate is the probability that recognition is falsely rejected; that is, a copy of an image that belongs to the face database is mistakenly considered that it does not belong to the face database during recognition. The false recognition rate is the probability that a recognition error is accepted; that is, a copy of an image that does not belong to the face database is mistakenly considered to belong to the face database during recognition. In this paper, for experimental verification, the total number of samples collected was 20 people, and each person was collected 10 facial images. Due to the relatively complex external natural environment, the recognition threshold of this system is set to 0.8 after a multiperson sampling experiment, and the verification results obtained are shown in Table 1 .
Test results.
When the total number of collected samples is 20 people, each person has been collected 20 facial images, and after a multiperson sampling test, the recognition threshold of the system is set to 0.7, and the verification results obtained are shown in Table 2 .
Finally, the program compares the captured face image with the user's facial image (assuming the current tester is the user). The matching result is shown in Figure 9 .

Face matching operation results.
3.2. Data Transmission Test
When the user's facial recognition node wants to transmit image data through the asynchronous channel, the system establishes a connection to transmit the asynchronous data. The code is as follows.

Figure 10 shows the asynchronous data sending status of the user's facial recognition node displayed in the serial port debugging tool after executing the 03 command during the asynchronous data sending test.

Sending asynchronous data test.
Figure 11 is the serial port display of the face recognition node after the master node sends the command 04. When the master node sends the command 04, the facial recognition node will send the pictures collected by the camera to the master node. The image data in this system are transmitted through an asynchronous data channel and need to be divided into multiple segments because the system allocates 40 bytes of asynchronous data fields for each subsystem frame. In this way, the image information is sent to the master node in segments. Whenever an asynchronous data packet is received by the master node, the master node will return a notification message to the slave node to inform the slave node of the receiving status of the asynchronous data.

Picture transmission test.
4. Conclusion
This paper builds a facial recognition system based on visual communication effects. From the perspective of visual communication effects, the overall design plan of the system is determined, and facial recognition technology and communication transmission technology are combined to design the facial recognition nodes and facial recognition nodes that realize the main functions of the system. The main control node with communication transmission function analyzes the existing face detection and facial recognition methods through face detection and facial recognition technology, uses the OpenCV library to design the facial recognition program, and combines the development and practical application of the system environment, the embedded environment and system test platform required for program operation are built, and the program of each node is debugged and verified. Experimental results show that the algorithm has a recognition success rate of 88.2% and a misrecognition rate of only 0.7%. Compared with traditional facial recognition technology, the success rate is significantly improved. In addition, through threshold adjustment experiments, it is shown that the optimal threshold of the algorithm is 0.8, and the recognition success rate and false recognition rate are better than other low threshold results. The feasibility of the system is verified by experiments.
Data Availability
Conflicts of interest.
The authors declare that they have no conflicts of interest.
Accessibility Links
- Skip to content
- Skip to search IOPscience
- Skip to Journals list
- Accessibility help
- Accessibility Help
Click here to close this panel.
Purpose-led Publishing is a coalition of three not-for-profit publishers in the field of physical sciences: AIP Publishing, the American Physical Society and IOP Publishing.
Together, as publishers that will always put purpose above profit, we have defined a set of industry standards that underpin high-quality, ethical scholarly communications.
We are proudly declaring that science is our only shareholder.
Face Recognition and Identification using Deep Learning Approach
KH Teoh 2 , RC Ismail 1,2 , SZM Naziri 2 , R Hussin 2 , MNM Isa 2 and MSSM Basir 3
Published under licence by IOP Publishing Ltd Journal of Physics: Conference Series , Volume 1755 , 5th International Conference on Electronic Design (ICED) 2020 19 August 2020, Perlis, Malaysia Citation KH Teoh et al 2021 J. Phys.: Conf. Ser. 1755 012006 DOI 10.1088/1742-6596/1755/1/012006
Article metrics
27481 Total downloads
Share this article
Author e-mails.

Author affiliations
1 School of Computing and Informatics, Albukhary International University, Kedah Malaysia.
2 School of Microelectronic Engineering, Universiti Malaysia Perlis, Perlis, Malaysia.
3 Department of Electrical Engineering, Politeknik Mukah, Sarawak, Malaysia.
Buy this article in print
Human face is the significant characteristic to identify a person. Everyone has their own unique face even for twins. Thus, a face recognition and identification are required to distinguish each other. A face recognition system is the verification system to find a person's identity through biometric method. Face recognition has become a popular method nowadays in many applications such as phone unlock system, criminal identification and even home security system. This system is more secure as it does not need any dependencies such as key and card but only facial image is needed. Generally, human recognition system involves 2 phases which are face detection and face identification. This paper describes the concept on how to design and develop a face recognition system through deep learning using OpenCV in python. Deep learning is an approach to perform the face recognition and seems to be an adequate method to carry out face recognition due to its high accuracy. Experimental results are provided to demonstrate the accuracy of the proposed face recognition system.
Export citation and abstract BibTeX RIS
Content from this work may be used under the terms of the Creative Commons Attribution 3.0 licence . Any further distribution of this work must maintain attribution to the author(s) and the title of the work, journal citation and DOI.
- How it works
Useful Links
How much will your dissertation cost?
Have an expert academic write your dissertation paper!
Dissertation Services

Get unlimited topic ideas and a dissertation plan for just £45.00
Order topics and plan

Get 1 free topic in your area of study with aim and justification
Yes I want the free topic

Dissertation Topics on Facial Recognition
Published by Grace Graffin at January 9th, 2023 , Revised On August 16, 2023
Introduction
The facial recognition system refers to the technology capable of identifying a person from a digital image or a video frame from a video source. There are various methods through which facial recognition systems operate; however, generally, they work by comparing facial features from the given image with the faces in a database.
Previously facial recognition technology was developed as a computer application program. However, now it is more prevalent in both IOS and Android apps and is also used in other different forms of technology such as robotics.
The facial recognition system is more commonly employed as a security mechanism than biometric systems such as fingerprint and eye recognition technology. More recent use of this technology is in the mobile world, where the latest mobile phone models have a built-in face recognition application.
Through this technology, users can easily unlock their mobile phones without having to enter their passwords. Once the systems recognise their face, their device is unlocked. Here are a few essential dissertation topics on facial recognition to explore the world of this revolutionary technology.
These topics have been developed by PhD qualified writers of our team , so you can trust to use these topics for drafting your dissertation.
You may also want to start your dissertation by requesting a brief research proposal from our writers on any of these topics, which includes an introduction to the topic, research question , aim and objectives , literature review along with the proposed methodology of research to be conducted. Let us know if you need any help in getting started.
Check our dissertation examples to get an idea of how to structure your dissertation .
Review the full list of dissertation topics for 2022 here.
2022 Dissertation Topics on Facial recognition
Topic 1: examining multi-dimension in facial emotion detection..
Research Aim: When it comes to communications, human expressions are extraordinary. Humans can identify it very easily and accurately. Getting the same outcome from a 3D machine is a difficult task. This is because of the present challenges in 3D face data scanning. This study will examine the facial emotion identification in humans using different multi-point for 3D face landmarks.
Topic 2: A novel face recognition system based on the fusion of LDB and HOG.
Research Aim: Face recognition has become more relevant in a variety of situations involving visual security systems. This study will provide a novel face recognition method based on the fusion of LDB and HOG. For this study, many techniques will be employed and will also improve the drawbacks of poor accuracy and eliminate the issues that the dimension of the general fusion causes.
Topic 3: Face recognition techniques- Challenges and implementation.
Research Aim: Various biometric applications are being used in our daily activities for recognising, such as eye recognition, fingerprint, and face recognition. Facial recognition is one of the essential issues in AI and modern technology. This study aims to find the challenges and implementation of facial recognition techniques. This research will review different previous studies to analyse various techniques and challenges for recognition.
Topic 4: Facial recognition while using masks in mobile Phones.
Research Aim: Due to the Covid-19 pandemic, the use of face masks was mandatory as a safety precaution. This has generated many issues for the facial recognition systems. This study will focus on the development of the facial recognition system when people are wearing a face mask through various frameworks. A face detector will be employed, and through different stages, we will analyse whether the face can be detected or not when wearing a mask.
Topic 5: Assessing Low and High-resolution images reconstruction using different methods.
Research Aim: Deep learning in computer vision and advancements in technology have made low and high-resolution image reconstruction possible. Image reconstruction is a technical procedure; it has a significant influence on image quality. This study aims to examine the low and high reconstruction of images using various methods. Furthermore, it will analyse the best method used for image reconstruction and help restore pictures successfully. It will also focus on previous studies and help understand how it has evolved in these years.
Covid-19 Facial Recognition Research Topics
Topic 1: facial recognition technology and covid-19.
Research Aim: This study will focus on the increasing market of facial recognition technology and its use to combat the Coronavirus pandemic.
Topic 2: Facial recognition and biometric contact system during COVID-19
Research Aim: This study will show the role of facial recognition and contact in the Biometric system during COVID-19.
Topic 3: An Introduction to Facial Recognition Technology
Research Aim: Facial Recognition technology is biometric software that maps the facial features of an individual mathematically and stores them as data of a face print. With the help of deep learning algorithms, the software recognizes and stores whether the image is a live capture or a digital image. Whenever an individual utilizes the software, the face is verified through the stored images in the system. If it matches the stored image, the individual is granted access. This dissertation will focus on the basics of facial recognition technology. The software will be discussed in detail. The various characteristics of the system, how it works, features it encompasses, uses, and benefits of the system, including the drawbacks, will be discussed in this research. In short, this research will be a complete guide regarding facial recognition technology.
Topic 4: How do Facial Recognition Systems Work?
Research Aim: To keep up with the latest trends and technologies, and to get the maximum benefits, we must know how a specific technology or software functions. Facial recognition systems run on an algorithm. They map a particular device, photo, ID against a person concerning its facial features.
Thus, the next time a similar image appears on the software, the face is recognised, and the user is granted access. However, the whole technology is not as easy as it sounds. This research will delve deep into how the software works through algorithms and what aspects are considered by the system.
How Can ResearchProspect Help?
ResearchProspect writers can send several custom topic ideas to your email address. Once you have chosen a topic that suits your needs and interests, you can order for our dissertation outline service which will include a brief introduction to the topic, research questions , literature review , methodology , expected results , and conclusion . The dissertation outline will enable you to review the quality of our work before placing the order for our full dissertation writing service !
Topic 5: Exploring High-Performance Face Detection Methods
Research Aim: Facial recognition technology employs different methods to capture and store images. These images are stored in the system for future use, and when a user uses the feature the next time, the idea is matched with the ones stored in the system.
If and when the system recognises the image, the user is granted access. The whole process includes three different methods for storing images as data. The first method is preprocessing, the second is feature extraction, and the third is classification.
The best method is determined based on technology, the system, and its utilisation. This research will explore all these three methods in detail and understand which way is chosen under which circumstance. All three forms may also be used together by the software for storing one image. Thus, all the details will be discussed in this dissertation.
Topic 6: Facial Recognition Technology in Surveillance: How Effective is it?
Research Aim: With the increasing trend of facial recognition in our everyday lives, this technology has increased in the surveillance industry. Many companies now depend on facial recognition technology to enhance their organisation’s safety.
In addition to this, this technology has also increased in homes where people have deployed facial recognition systems to ensure the safety of their living places. This research will explore in-depth how effective facial recognition is in the surveillance industry.
The study will include specific examples of how facial recognition is used for surveillance and evaluate its effectiveness.
Topic 7: Facial Recognition Algorithms: An Overview
Research Aim: Facial recognition technology relies on the use of algorithms. Without algorithms, the system cannot function. Thus, to understand the system, the algorithms must be thoroughly understood.
This research will focus on the algorithms that the system deploys to help understand how images are captured, stored, and recognized by the system to grant access to a user. These algorithms are complex in nature. Thus the research will provide the basics of it to make sure that the readers can easily understand the system.
Topic 8: The Future of Facial Recognition Technology
Research Aim: Facial Recognition is one of the most advanced technologies of the modern sciences. Many computer devices make use of this technology to enhance security as well as the user experience.
This research will discuss how this technology has successfully helped people and companies overcome their security issues, what the future holds for this technology and the benefits of implementing facial recognition.
A comparison will also be drawn with other security measures such as fingerprint and manual password entering systems. This research will provide a detailed analysis of how facial recognition technology has performed compared to other security measures and whether or not it has been successful in terms of security.
Moreover, the research will also discuss the future of this technology, how it can be improved, how and where it can be implemented, and how this system can prove to be even more beneficial for its users.
Important Notes:
As a student of facial recognition looking to get good grades, it is essential to develop new ideas and experiment with existing facial recognition theories – i.e., to add value and interest in your research topic.
Facial recognition is vast and interrelated to so many other academic disciplines like Facebook , Instagram , Cryptocurrency , Twitter , civil engineering , facial recognition , construction , project management , engineering management , healthcare , finance and accounting , artificial intelligence , tourism , physiotherapy , sociology , management , and project management , graphic design , and nursing . That is why it is imperative to create a project management dissertation topic that is articular, sound, and actually solves a practical problem that may be rampant in the field.
We can’t stress how important it is to develop a logical research topic based on your entire research. There are several significant downfalls to getting your topic wrong; your supervisor may not be interested in working on it, the topic has no academic creditability, the research may not make logical sense, and there is a possibility that the study is not viable.
This impacts your time and efforts in writing your dissertation as you may end up in the cycle of rejection at the initial stage of the dissertation. That is why we recommend reviewing existing research to develop a topic, taking advice from your supervisor, and even asking for help in this particular stage of your dissertation.
While developing a research topic, keeping our advice in mind will allow you to pick one of the best facial recognition dissertation topics that fulfil your requirement of writing a research paper and add to the body of knowledge.
Therefore, it is recommended that when finalizing your dissertation topic, you read recently published literature to identify gaps in the research that you may help fill.
Remember- dissertation topics need to be unique, solve an identified problem, be logical, and be practically implemented. Please look at some of our sample facial recognition dissertation topics to get an idea for your own dissertation.
How to Structure your Facial Recognition Dissertation
A well-structured dissertation can help students to achieve a high overall academic grade.
- A Title Page
- Acknowledgements
- Declaration
- Abstract: A summary of the research completed
- Table of Contents
- Introduction : This chapter includes the project rationale, research background, key research aims and objectives, and the research problems. An outline of the structure of a dissertation can also be added to this chapter.
- Literature Review : This chapter presents relevant theories and frameworks by analysing published and unpublished literature available on the chosen research topic to address research questions . The purpose is to highlight and discuss the selected research area’s relative weaknesses and strengths whilst identifying any research gaps. Break down the topic, and binding terms can positively impact your dissertation and your tutor.
- Methodology : The data collection and analysis methods and techniques employed by the researcher are presented in the Methodology chapter which usually includes research design , research philosophy, research limitations, code of conduct, ethical consideration, data collection methods, and data analysis strategy .
- Findings and Analysis : Findings of the research are analysed in detail under the Findings and Analysis chapter. All key findings/results are outlined in this chapter without interpreting the data or drawing any conclusions. It can be useful to include graphs, charts, and tables in this chapter to identify meaningful trends and relationships.
- Discussion and Conclusion : The researcher presents his interpretation of the results in this chapter, and states whether the research hypothesis has been verified or not. An essential aspect of this section of the paper is to draw a linkage between the results and evidence from the literature. Recommendations with regards to implications of the findings and directions for the future may also be provided. Finally, a summary of the overall research, along with final judgments, opinions, and comments, must be included in the form of suggestions for improvement.
- References : This should be completed following your University’s requirements
- Bibliography
- Appendices : Any additional information, diagrams, and graphs used to complete the dissertation but not part of the dissertation should be included in the Appendices chapter. Essentially, the purpose is to expand the information/data.
About ResearchProspect Ltd
ResearchProspect is the world’s best academic writing service that provides help with Dissertation Proposal Writing , PhD Proposal Writing , Dissertation Writing , Dissertation Editing, and Improvement .
Our team of writers is highly qualified. They are experts in their respective fields. They have been working in the industry for a long, thus are aware of the issues and the trends of the industry they are working in.
Free Dissertation Topic
Phone Number
Academic Level Select Academic Level Undergraduate Graduate PHD
Academic Subject
Area of Research
Frequently Asked Questions
How to find facial recognition dissertation topics.
To find facial recognition dissertation topics:
- Research recent advancements.
- Explore ethical and privacy concerns.
- Examine applications in various fields.
- Investigate accuracy and bias issues.
- Consider legal and social implications.
- Select a topic aligning with your expertise and passion.
You May Also Like
It is common knowledge that students can only graduate with honours if their dissertations are well written. You can develop a successful career by writing a dissertation on the subject matter that interests you most.
It might be difficult to come up with an interesting study topic. Biology dissertation topic ideas should be attractive, captivating, and intellectually relevant.
Portfolio management examines the projects and programs of an organization. There are three aspects involved here: selection, prioritization, and control. This is done by taking into account the strategic goals of the organization.
USEFUL LINKS
LEARNING RESOURCES

COMPANY DETAILS

- How It Works
- International edition
- Australia edition
- Europe edition

Shoplifting crackdown to include £55m for facial recognition tools in England and Wales
Mobile units will be deployed on high streets to identify wanted people – including repeat offenders
The government is investing more than £55m in expanding facial recognition systems – including vans that will scan crowded high streets – as part of a renewed crackdown on shoplifting.
The scheme was announced alongside plans for tougher punishments for serial or abusive shoplifters in England and Wales, including being forced to wear a tag to ensure they do not revisit the scene of their crime, under a new standalone criminal offence of assaulting a retail worker.
The new law, under which perpetrators could be sent to prison for up to six months and receive unlimited fines, will be introduced via an amendment to the criminal justice bill that is working its way through parliament. The change could happen as early as the summer.
The government said it would invest £55.5m over the next four years. The plan includes £4m for mobile units that can be deployed on high streets using live facial recognition in crowded areas to identify people wanted by the police – including repeat shoplifters.
That investment follows the development of Project Pegasus under which some of the UK’s biggest retailers, including Marks & Spencer, Boots and Primark run their CCTV images through police databases using facial recognition technology.
Silkie Carlo, director of civil liberties at campaign group Big Brother Watch, said the government’s investment in facial recognition technology was “an abysmal waste of public money”.
“This Orwellian tech has no place in Britain,” she said, adding: “Criminals should be brought to justice, but papering over the cracks of broken policing with Orwellian tech is not the solution. It is completely absurd to inflict mass surveillance on the general public under the premise of fighting theft while police are failing to even turn up to 40% of violent shoplifting incidents or to properly investigate many more serious crimes.”
The £55.5m will come out of a £240m investment in police producticity over four years announced in the budget, while the £4m on more mobile units will be spent over the next year.
Backing for a specific retail worker assault offence marks a U-turn for the government, which previously blocked a Labour-backed amendment to the criminal justice bill that would have made the assault of a retail worker a specific criminal offence carrying a sentence of 12 months behind bars or a fine of up to £10,000.
Chris Philp, the policing minister, said at the time the move could lead to a problem of “equity between retail workers and other public-facing workers”.
However, retailers have demanded action against what they say is an epidemic of retail crime driven by organised by gangs targeting vulnerable stores. In October 90 retail leaders, including the bosses of Tesco, Sainsbury’s, Boots and WH Smith, wrote to the government demanding action on rising retail crime .
Last week the Co-op Group, which has been at the forefront of a campaign to create a specific crime for assault on a retail worker, said it had lost £70m from shoplifting after a 44% surge in retail crime last year to about 1,000 incidents a day.
Paul Gerrard, the campaigns and public affairs director of Co-op, said: “I’m glad that after six years of hard campaigning we have got to the point where this offence will become law.” He said that in Scotland, where a similar law is already in place, the arrest rate for retail crime was 60% compared with just 10% in England.
Sharon White, the outgoing chair of the John Lewis Partnership, which owns Waitrose supermarkets and department stores, said: “Retail crime is never victimless – it costs retailers over £1bn every year and can have a huge impact on the shop workers involved.
“We’ve long called for violence towards retail workers to be recognised as a standalone offence so welcome this announcement.”
Rishi Sunak said his government was backing a change in the law as “shoplifting and violence and abuse towards retail workers continues to rise”.
“I am sending a message to those criminals – whether they are serious organised criminal gangs, repeat offenders or opportunistic thieves – who think they can get away with stealing from these local businesses or abusing shop workers, enough is enough.”
- Retail industry
- Facial recognition

Co-op boss urges police to take shoplifting more seriously after £33m cost

‘It’s organised looting’: UK in grip of a shoplifting epidemic, say store owners

I work in a supermarket and see how desperate some shoplifters are. My heart goes out to them

A rise in shoplifting has Australian supermarkets ramping up surveillance

Instead of pursuing shoplifters, the big supermarkets should use their record profits to prevent food waste

Shoplifting is out of control. Forget the police – stores need to up their game

Waitrose offers free coffees for police officers amid shoplifting rise

Shoplifters need access to support services, not prison
Most viewed.

IMAGES
VIDEO
COMMENTS
A face recognition system is designed, implemented and tested in this thesis study. The system utilizes a combination of techniques in two topics; face detection and recognition.
facial recognition is known as the Karhunen-Loeve method. It is the most thoroughly studied. method for face recognition, with its main usability being a reduction in the dimensionality of the image. This method was first applied for face recognition and then subsequently used for facial. reconstruction.
the open computer vision library (OpenCV). Face recognition is a non-inv asive identification system and. faster than other systems since multiple faces can be analysed at the same time. The ...
The Designated Thesis Committee Approves the Thesis Titled FACE RECOGNITION: AN ENGINEERING APPROACH . by . Farshad Ghahramani APPROVED BY THE DEPARTMENT OF COMPUTER ENGINEERING SAN JOSÉ STATE UNIVERSITY ... the subject is required to interact with the system by placing a finger under a fingerprint reader, and the results must be verified by ...
Design and Develop a One-Shot Learning Face Recognition System using Deep Convolutional Network. July 2020. Md Mehedi Hasan. Md.abdullah-Al- Imran. Md.Rijoan Rabbi. PDF | On Aug 20, 2020, Anirban ...
Boulos, Mira M., "Facial Recognition and Face Mask Detection Using Machine Learning Techniques" (2021). Theses, Dissertations and Culminating Projects. 728. https://digitalcommons.montclair.edu/etd/728. This Thesis is brought to you for free and open access by Montclair State University Digital Commons.
Feature extraction is the most crucial stage for the success of the face recognition system. However, deep learning methods have freed the user from handcrafting the features. In this article, we have surveyed state-of-the-art methods of last few decades and the comparative study of various feature extraction methods is provided. Article also ...
rotation. Therefore, face recognition based on deep learning can greatly improve the recognition speed and compatible external interference. In this thesis, we use convolutional neural networks (ConvNets) for face recognition, the neural networks have the merits of end-to-end, sparse connection and weight sharing.
In this dissertation, we introduce an enhanced human face recognition framework. with a high recognition rate. This improvement based on improving the features extraction. approach and improving the image registration based on active shape model deep learning.
The work of this thesis aims at designing a robust Facial Expression Recognition (FER) system by combining various techniques from computer vision and pattern recognition. Expression recognition is closely related to face recognition where a lot of research has been done and a vast array of algorithms have been introduced. FER can also be
This paper mainly discusses the asymmetric face recognition problem where the number of names in a name list and the number of faces in the photo might not be equal, but each face should be automatically labeled with a name. The motivation for this issue is that there had been many meetings in the past. After each meeting, the participant took group photos. The meeting provided only a ...
At present, facial recognition technology is a very cutting-edge science and technology, and it has now become a very hot research branch. In this research, first, the thesis first summarized the research status of facial recognition technology and related technologies based on visual communication and then used the OpenCV open source vision library based on the design of the system ...
Deep learning is an approach to perform the face recognition and seems to be an adequate method to carry out face recognition due to its high accuracy. Experimental results are provided to demonstrate the accuracy of the proposed face recognition system. Export citation and abstract BibTeX RIS. Content from this work may be used under the terms ...
A face recognition system is designed, implemented and tested in this thesis study. The system utilizes a combination of techniques in two topics; face detection and recognition.
The project consists of building a facial recognition, electronics operation, and webpage design for the database. Firstly, machine learning and deep learning algorithms were used to recognize faces. In the second step, AI data is transmitted to the electronics components and sensors to make a smart lock system.
largest user of face biometrics systems, including face recognition [3], over the next 10 years. Face recognition technologies are also at the forefront of a wide range of consumer applications and devices, from user verification tasks enabling account access, to digital camera applications, and social media tagging.
Goal of this master thesis Developing a face recognition system so that: Keeps a DB of known users Given a new picture, determines the closest match Capable of on-line learning Usable in uncontrolled environments Reasonably fast Barcelona School of Informatics Face recognition using Deep Learning 7 / 44. Outline
FaceNet [3] is a notable face-recognition technique, which uses a deep convolutional neural network with 22 layers trained via a triplet loss function to directly output a 128-dimensional embedding. VGGFace2 [4] is a dataset for training face recognition models taking into account pose and age. At the heart of the proposed system is the face ...
Topic 2: A novel face recognition system based on the fusion of LDB and HOG. Topic 3: Face recognition techniques- Challenges and implementation. Topic 4: Facial recognition while using masks in mobile Phones. Topic 5: Assessing Low and High-resolution images reconstruction using different methods.
Face detection, Feature Extraction, and face Recognition (Singhal et al., 2022). The face dete ction method is a difficult task in image anal ysis. Face detection is an application for detecting ...
Keywords: Local Binary Pattern Histogram(LBPH), Face Detection, Face Recognition, Haarcascade Classifier, Python, Student Attendance. Suggested Citation: Suggested Citation SAI, E CHARAN and HUSSAIN, SHAIK ALTHAF and KHAJA, SYED and SHYAM, AMARA, Student Attendance Monitoring System Using Face Recognition (May 22, 2021).
At present, facial recognition technology is a very cutting-edge science and technology, and it has now become a very hot research branch. In this research, first, the thesis first summarized the research status of facial recognition technology and related technologies based on visual communication and then used the OpenCV open source vision library based on the design of the system ...
cameras with facial recognition systems to identify criminals and search for missing persons. As facial recognition technology and algorithms advance, we would see it being implemented more and more in our society. [4] 2.3 Challenges of Facial Recognition System A facial recognition system can revolutionize how businesses and governments
Abstract and Figures. The task of face recognition has been actively researched in recent years. This paper provides an up-to-date review of major human face recognition research. We first present ...
The government is investing more than £55m in expanding facial recognition systems - including vans that will scan crowded high streets - as part of a renewed crackdown on shoplifting.