CS 253 Web Security
Assignment 4 – swiss cheese security 🧀.
- Due: Friday, December 3 at 11:59pm
Welcome to Assignment 4 for CS 253: Web Security . ✨

Check your Node.js version
You should already have Node.js installed from previous assignments. For this assignment, it's highly recommended to use Node.js 16. Open your terminal and run this command to confirm you're running some version 16.x.x:
If not, you can install Node.js from the official site.
Get the starter code
Run this command to clone the code with git :
Enter the folder you just created:
Install the necessary local dependencies with npm :
In this assignment, you will learn how web application vulnerabilities can be exploited and how to defend against these attacks. This assignment has a bit of overlap with the XSS challenges in Assignment 2 , but goes beyond XSS and offers you the chance to try a variety of other attacks.
The best way to learn things is by doing, so you'll get a chance to do some real penetration testing , actually exploiting a real application. Specifically, you'll learn the following:
- How an application can be attacked using common web security vulnerabilities, like cross-site scripting vulnerabilities (XSS) and cross-site request forgery (XSRF).
- How to find, fix, and avoid these common vulnerabilities and other bugs that have a security impact, such as denial-of-service, information disclosure, or remote code execution.
This assignment is built around Gruyere /ɡruːˈjɛər/ - a small, cheesy web application that allows its users to publish snippets of text and store assorted files. "Unfortunately", Gruyere has multiple security bugs ranging from cross-site scripting and cross-site request forgery, to information disclosure, denial of service, and remote code execution. The goal of this assignment is to guide you through discovering some of these bugs and learning ways to fix them both in Gruyere and in general.
Types of vulnerabilities
The assignment is organized by types of vulnerabilities. In each section, you'll find a brief description of a vulnerability and a task to find an instance of that vulnerability in Gruyere. Your job is to play the role of a malicious hacker and find and exploit the security bugs. In this assignment, you'll use both black-box hacking and white-box hacking.
In black-box hacking , you try to find security bugs by experimenting with the application and manipulating input fields and URL parameters, trying to cause application errors, and looking at the HTTP requests and responses to guess server behavior. You do not have access to the source code, although understanding how to view source and being able to view http headers is valuable. Using a web proxy like Burp or ZAP may be helpful in creating or modifying requests.
In white-box hacking , you have access to the source code and can use automated or manual analysis to identify bugs. You can treat Gruyere as if it's open source: you can read through the source code to try to find bugs. Gruyere is written in Python, so some familiarity with Python can be helpful. However, the security vulnerabilities covered are not Python-specific and you can do most of the assignment without even looking at the code. You can run a local instance of Gruyere to assist in your hacking: for example, you can create an administrator account on your local instance to learn how administrative features work and then apply that knowledge to the instance you want to hack, though again, this is not required.
Security researchers use both hacking techniques, often in combination, in real life.
Part 1: Hacking (40 points)
The assignment is split into sections for each type of attack. For each section, you'll learn about a new type of attack and try using it against the Gruyere web server.
Each section has one or more challenges. If you get stuck on a challenge, there are hints provided inline. If you get stuck for more than 10 minutes on a particular challenge, then you are free to expand the solution (under the title "Exploit and Fix") which is provided for you inline.
When coming up with an attack, there's usually an amazing aha moment when you finally figure out the "trick"; if you look at the solution before you've figured it out yourself you'll be robbed of the best part. But we also don't want you to get stuck forever, so you are free to look at the solution after you've been stuck on a given challenge for 10 minutes .
Once you've come up with a solution that works, read the official solution and compare with yours. There's lots of useful information about defense techniques discussed along with the solution (under the title "Exploit and Fix") and throughout the Gruyere codelab.
Access the assignment
To access Gruyere, go to https://google-gruyere.appspot.com/part1 . Find the link to start a Gruyere instance for yourself.
AppEngine will start a new instance of Gruyere for you, assign it a unique id and redirect you to https://google-gruyere.appspot.com/123/ (where 123 is your unique id). Each instance of Gruyere is "sandboxed" from the other instances so your instance won't be affected by anyone else using Gruyere. You'll need to use your unique id instead of 123 in all the examples.
The Gruyere source code is available online so that you can use it for white-box hacking. You can browse the source code at https://google-gruyere.appspot.com/code/ or download all the files from https://google-gruyere.appspot.com/gruyere-code.zip . If want to debug it or actually try fixing the bugs, you can download it and run it locally. You do not need to run Gruyere locally in order to do the assignment.
What to submit
Include your solution to each challenge in REPORT.md . It's okay if your solution matches the official solution - just include it anyway.
You only need to include the exploits in your answers. No need to discuss fixes, though you should read through this content (it’s fair game for the final).
You only need to answer the initial question. No need to answer the followup questions which appear within some "Exploit and Fix" sections, though again you should read through this content.
Part 2: Survey (3 points)
Your feedback matters a lot! Please help us improve by answering the survey questions in SURVEY.md. As a reward, enjoy some easy points!
Before you submit
Ensure that the sanity tests pass:
This command just runs a basic sanity test that ensures your project passes npm run lint . If npm test doesn't report any errors that doesn't necessarily mean that you've solved every exercise perfectly!
🌟 PRO TIP: You can automatically fix some lint errors by running:
We'll use Gradescope for submissions.
The moment of truth
When you're ready to submit your work, you'll upload two files to Gradescope: REPORT.md and SURVEY.md .
You should submit early and often! There's no downside to repeatedly submitting your assignment.

Lesson 1 (Beta)
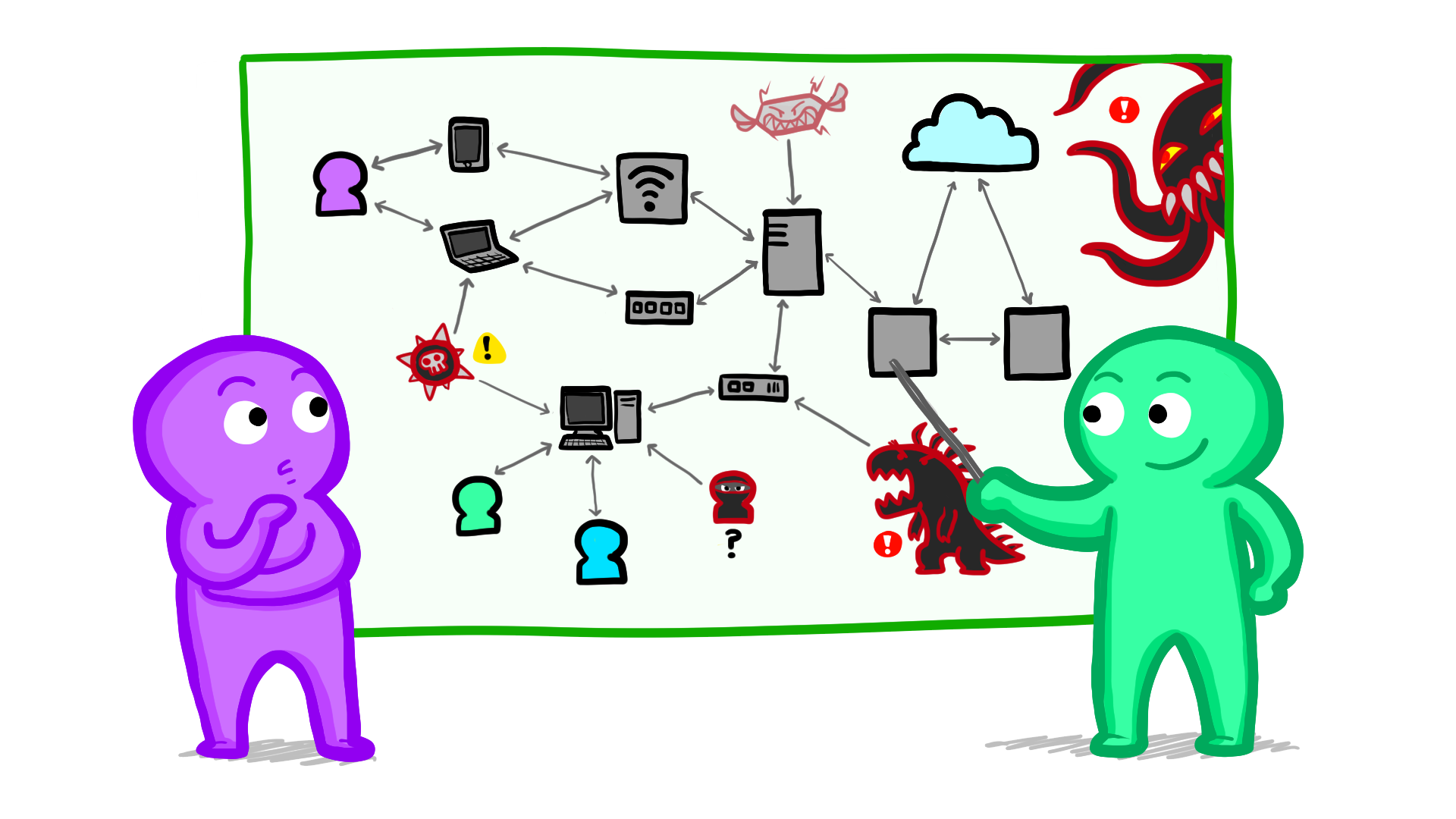
The Security Mindset:
Cybersecurity through threat modeling, about this lesson:.
Lesson 1 introduces students to the basic concepts of cybersecurity and the “Security Mindset”. This perspective frames the topics in the remaining lessons.
Intended Audience: High school students or early undergraduates. Geared towards AP Computer Science Principles , but compatible with any introductory computer science course.
Delivery Format: Traditional classroom.
Duration for Whole Unit: 75 minutes (with options to shorten or lengthen).
Lesson Rationale
Beginning a cybersecurity unit with threat modeling and the “security mindset” provides an overarching framework that students can continue applying as they engage with specific cybersecurity topics in later lessons. This lesson is built around a series of progressively more structured threat modeling activities, demonstrating the value of taking an organized approach. Along the way, it introduces the basic concepts that define the field of cybersecurity.
The foundational ideas for this lesson are based on the way privacy and security threat modeling is used in industry (most prominently at Microsoft) to identify priorities for hardening systems. As Adam Shostack, author of Threat Modeling: Designing for Security, puts it: “Threat modeling is the use of abstractions to aid in thinking about risks. […] Threat modeling is the key to a focused defense. Without threat models, you can never stop playing whack-a-mole.” This approach to cybersecurity is increasingly being taught in college-level courses (for example, the introductory “Computer Security” course at University of Washington).
Learning Objectives
- Students can explain what cybersecurity is.
- Students can enumerate some reasons cybersecurity is important.
- Students can discuss some of the unique challenges in the field of cybersecurity that differentiate it from other design and engineering efforts.
- Students can identify the goals and summarize the overall process of threat modeling.
- Given a description of a system, students can predict and prioritize some potential threats (who might attack it and how) and the human impacts of those threats.
Alignment with AP Computer Science Principles -- SY 2020--21 Onward
This lesson addresses standards laid out in the AP Computer Science Principles Framework for 2020–21, Fall 2019 version .
Supports the following Learning Objectives under Big Idea 4, Computing Systems and Networks:
LO CSN-1.A Explain how computing devices work together in a network. Essential Knowledge points covered:
- EK CSN-1.A.3 A computer network is a group of interconnected computing devices capable of sending or receiving data.
LO CSN-1.B Explain how the Internet works.
Supports the following Learning Objectives under Big Idea 5, Impact of Computing:
LO IOC-1.A Explain how an effect of a computing innovation can be both beneficial and harmful. Essential Knowledge points covered:
- EK IOC-1.A.3 Not every effect of a computing innovation is anticipated in advance.
LO IOC-1.B Explain how a computing innovation can have an impact beyond its intended purpose. Essential Knowledge points covered:
- EK IOC-1.B.2 Some of the ways computing innovations can be used may have a harmful impact on society, economy, or culture.
LO IOC-2.B Explain how computing resources can be protected and can be misused. Essential Knowledge points covered:
- EK IOC-2.B.9 Malware is software intended to damage a computing system or to take partial control over its operation.
- EK IOC-2.B.10 All real-world systems have errors or design flaws that can be exploited to compromise them. Regular software updates help fix errors that could compromise a computing system.
LO IOC-2.C Explain how unauthorized access to computing resources is gained.
LO IOC-1.F Explain how the use of computing can raise legal and ethical concerns.
Also touches on the following Essential Knowledge:
Under Big Idea 1, Creative Development:
- EK CRD-2.E.3 A development process that is iterative requires refinement and revision based on feedback, testing, or reflection throughout the process. This may require revisiting earlier phases of the process.
Under Big Idea 3, Algorithms and Programming:
- EK AAP-3.F.1 Simulations are abstractions of more complex objects or phenomena for a specific purpose.
- EK AAP-3.F.4 The process of developing an abstract simulation involves removing specific details or simplifying functionality.
Under Big Idea 5, Impact of Computing:
- EK IOC-1.A.1 People create computing innovations.
- EK IOC-1.A.2 The way people complete tasks often changes to incorporate new computing innovations.
- EK IOC-1.A.4 A single effect can be viewed as both beneficial and harmful by different people, or even by the same person.
- EK IOC-1.B.3 Responsible programmers try to consider the unintended ways their computing innovations can be used and the potential beneficial and harmful effects of these new uses.
- EK IOC-1.B.4 It is not possible for a programmer to consider all the ways a computing innovation can be used.
- EK IOC-1.F.8 As with any technology or medium, using computing to harm individuals or groups of people raises legal and ethical concerns.
- EK IOC-1.F.9 Computing can play a role in social and political issues, which in turn often raise legal and ethical concerns.
- EK IOC-2.A.5 Technology enables the collection, use, and exploitation of information about, by, and for individuals, groups, and institutions.
- EK IOC-2.A.10 Commercial and governmental curation of information may be exploited if privacy and other protections are ignored.
- EK IOC-2.A.11 Information placed online can be used in ways that were not intended and that may have a harmful impact. For example, an email message may be forwarded, tweets can be retweeted, and social media posts can be viewed by potential employers.
- EK IOC-2.B.1 Authentication measures protect devices and information from unauthorized access. Examples of authentication measures include strong passwords and multifactor authentication.
- EK IOC-2.B.8 A computer virus is a malicious program that can copy itself and gain access to a computer in an unauthorized way. Computer viruses often attach themselves to legitimate programs and start running independently on a computer.
- EK IOC-2.C.3 Data sent over public networks can be intercepted, analyzed, and modified. One way that this can happen is through a rogue access point.
Provides opportunities to use the following Computational Thinking Practices:
P1 Computational Solution Design: Design and evaluate computational solutions for a purpose.
- P1.D Evaluate solution options.
P3 Abstraction in Program Development: Develop programs that incorporate abstractions.
- P3.B Use abstraction to manage complexity in a program.
P4 Code Analysis: Evaluate and test algorithms and programs.
- P4.C Identify and correct errors in algorithms and programs, including error discovery through testing.
P5 Computing Innovations: Investigate computing innovations.
- P5.A Explain how computing systems work.
- P5.C Describe the impact of a computing innovation.
- P5.D Describe the impact of gathering data.
- P5.E Evaluate the use of computing based on legal and ethical factors.
P6 Responsible Computing: Contribute to an inclusive, safe, collaborative, and ethical computing culture.
- P6.A Collaborate in the development of solutions.
- P6.B Use safe and secure methods when using computing devices.
Curriculum Standards Addressed
Ap computer science principles curriculum framework.
The lesson substantially addresses the following Essential Knowledge under Big Idea X, NAME:
- EK XXX. Essential knowledge statement.
The following Essential Knowledge is also touched on:
- Under Big Idea X: NAME: XX, XXX.
CSTA K–12 Computer Science Standards (Level 3 — High School)
The lesson substantially addresses the following learning objectives under Level X, Course Y: NAME:
- XXX. Learning objective.
The following learning objectives are also touched on:
- Under Level X, Course Y: NAME: XX; XXX.
ACM Computer Science Curricula 2013 (CS2013) Guidelines (Undergraduate)
The lesson substantially addresses the following Learning Outcomes under NAME:
- SUBNAME X: Learning outcome.
The following Learning Outcomes are also touched on:
- Under NAME: SUBNAME X; SUBNAME Y.
Cybersecurity Ethics Agreement
Some activities in this lesson involve learning skills that could be used to attack networked systems. Before beginning your cybersecurity unit, we recommend you ask students to sign an agreement such as the one below. The agreement commits them to use their powers only for good, and lays out some specifics of what that means.
Download Agreement: "Cybersecurity Ethics Agreement"
Be sure to give students plenty of time to read through the agreement (emphasize that this isn't a click-through yeah-sure-whatever terms of service agreement!) and invite them to ask questions if anything is unclear. Give them a copy to sign and a copy to keep.
- Check your district's policies to see whether students will need to have their parents sign the agreement as well.
Credits: Inspiration for the points to cover in this agreement came from Avi Rubin, Michael E. Whitman and Herbert J. Mattord (the Hands-On Information Security Lab Manual), an anonymous CS teacher from a Facebook group, and EC-Council’s Code of Ethics.
“Engage” Activities:
Introduce the topic, probe prior knowledge, and ignite students’ interest. (Choose one Engage activity, or use more if you have time.)
Quick Opening Questions (Whole-Class Mini-Discussion)
Estimated Time: 5-7 minutes.
What You’ll Need: Blackboard/whiteboard (optional).
Ignite Question
Are there any computer systems in the world that are safe from being hacked? Why or why not?
Optional Follow-Up Prompt:
- What would a totally safe system look like?
Target Answer + Details: No system is safe from attack. For a computer/system to actually be useful, it has to have some way for information to go in and come out (whether or not it’s connected to the Internet). It’s impossible to think of and protect against every way someone could possibly abuse those channels, other than just disabling them entirely.
Quick Knowledge Check
What is cybersecurity? What have you heard about it?
Optional Follow-Up Prompts:
- In what ways is it important?
- Who is it important to?
- Why do you need to protect systems from attackers? Who would do such a thing and why?
Target Answer + Details: Cybersecurity is about studying and protecting computer systems from adversaries who attempt to use the system in a way that it wasn’t meant to be used. (Where “computer systems” include many kinds of networked — or non-networked — devices, from smartphones to traffic lights.) It’s important because any system that’s designed for whatever purpose can be misused by an attacker/adversary. In other words, it’s important to anyone who interacts with computer systems, which is pretty much everybody! It’s common for criminals to attack a system for financial gain, i.e., to make money. It’s common for people to attack a system to exercise or demonstrate power, to prevent the real users from accessing the system, or simply because they’re bored or want to prove they can.
Small-Group Brainstorming Activity: Defend and Attack
Estimated Time: 5-10 minutes.
What You’ll Need: Print or write out slips of paper with a “secret” written on each one. Print one secret for each Blue Team, for them to keep hidden from the Red Team. Examples:
- “[Teacher] likes [title of movie/book/etc.].”
- “[Rival school]’s mascot is [name].”
- A random number
- An inspirational quote or a silly phrase
Description: In this activity, students get a taste of how cybersecurity involves thinking about possible attacks — but also experience the drawbacks of not using a structured approach to that thought process. This activity works best as a lead-in/contrast to the more organized activities later in this lesson plan.
Running the Activity:
- Ask your students to form groups of three or four. There should be an even number of groups overall.
- Red Team/Blue Team exercises take their name from a military exercise. The idea is simple: One group of security pros — a red team — attacks something, and an opposing group — the blue team — defends it.
- In the physical world, these exercises are used by the military to test force-readiness. They are also used to test the physical security of sensitive sites like nuclear facilities and government labs that conduct top-secret research.
- In the 1990s, cybersecurity experts began using Red Team/Blue Team exercises to test the security of information systems.
- Label each group as a Red Team or a Blue Team.
- Give each Blue Team a slip of paper with their “secret”.
- Tell the Blue Teams their task is to figure out a plan for protecting the information on the paper.
- Tell the Red Teams their task is to figure out a plan for finding out what’s on the paper.
- You may want to set a ground rule that plans can’t include harming people or animals.
- Give the teams 3-5 minutes to discuss their ideas for protecting or obtaining the information.
- Beginning with one of the Red Teams, ask the groups to report back. After hearing a Red Team plan to get the paper, ask if any of the Blue Teams has a plan to prevent that specific attack. (Repeat a few times.)
Types of Plans You’re Likely to Hear: Red Teams’ ideas will likely sort into two broad categories: Direct attacks: Plans that rely on directly pursuing the secret or attempting brute force; and Indirect attacks: Plans that rely on tricking the people involved into breaking protocol or exposing vulnerabilities. Blue Teams may attempt to reduce their risk of direct or indirect attacks. Higher-Level Ideas That May Emerge: It’s tough to cover every possible attack. It’s easier to think of attacks than it is to think of protection measures. Brainstorming attacks and protections feels disorganized. Both sides may have lots of open questions about what’s possible, or answers that begin with “It depends”.
Computing in the News - Cybersecurity Edition
Estimated Time: 3-7 minutes.
What You’ll Need: Computer and projector (optional).
Description: Teachers can use current news items about cyberattacks/data breaches or cybersecurity innovations to grab students’ attention at the beginning of class and illustrate the relevance of cybersecurity.
View Outline: “Computing in the News – Cybersecurity Edition”
Other media resources for "engage".
Estimated Time: TIME minutes. What You’ll Need: Computer, projector, and speakers.
Summary: SUMMARY
Video: VIDEO TITLE
- Content Advisory: IF YOU NEED ONE.
(Produced by PRODUCER.)
“Explore” Activities:
Ground students’ learning in firsthand experience and spark new ideas.
Small-Group Activity: Threat Model a House
Estimated Time: 20-30 minutes.
What You’ll Need:
- A whiteboard or a computer and projector
- Copies of the worksheet (1 per group)
- Students will need extra paper and pens/pencils
Description: Students practice a more structured approach to planning defenses against possible attacks, using a house as an example “system”.
Download Worksheet: “House Model Worksheet”
Introduction (2 minutes)
- Ask your students to form groups of 3-4.
- We’re going to talk about a process that can be used to approach thinking about security. It’s called threat modeling.
- At a high level, in threat modeling, you consider questions like what are you building or protecting, and what could go wrong?
- In groups, we’ll work through an example of how you would create a threat model for a basic house.
Blue Team Portion (10-15 minutes)
- Pass out pages 1 and 2 of the worksheet to each group
- In this activity, every group will start out as a Blue Team.
- The house on the worksheet and your answers to the first couple of questions are the “model” of what you’re protecting. This is an abstraction of the system at the heart of your threat model.
- The rest of the Blue Team questions involve thinking of ways that someone might attack the house or gain unauthorized access to the things inside.
- Write detailed notes for the whole group on one copy of the worksheet. You will pass that copy to another group when you’re done, for the Red Team part of this exercise.
- Give students 10-15 minutes to complete the Blue Team part of the worksheet (i.e. pages 1-2).
Red Team Portion (5 – 10 minutes)
- Have groups swap worksheets (pages 1-2) and pass out page 3.
- Give students 5-10 minutes to plan how they could gain access to the valuables inside the houses.
- If you’re short on time, you can direct Red Teams to write their responses on page 3, but skip having them represent their attacks on the Blue Teams’ diagrams.
Debrief/Wrap-Up (3-10 minutes)
- Have students return the worksheets to the original group so each Blue Team can spend a couple of minutes review the attacking Red Team’s plans.
- Optional: Ask each group to share an example of a clever or unexpected Red Team attack against their house, or one that would be difficult to prevent. (I.E., they should share examples thunk up by the group attacking them, not their own attack on someone else.)
- Wrap up by highlighting how designing a secure system differs from other fields of engineering, in that you have an active, motivated adversary to contend with. That’s why cybersecurity is often called an arms race. And it’s just a fact that you cannot predict or prevent all attacks.
- Allow both teams’ imaginations to run wild.
- Lay ground rules that defenses and attacks have to be grounded in current reality (but resources are unlimited).
- Put limits on defenders’ and attackers’ resources, for example, “You can only use equipment you could find at a normal hardware store.”
- Allow students to assume unlimited resources during the main part of the activity, but ask them at the end to revisit their Blue Team plans and think about how the plans would have been different if their resources had been limited (for example, to normal hardware-store equipment).
Whole-Class Brainstorm & Discussion: TITLE
Estimated Time: TIME minutes. What You’ll Need: Blackboard/whiteboard (optional).
Ask students to give examples of SOMETHING. Examples can be written on the board. Pick a few interesting example and ask:
Some examples you can start them off with: EXAMPLE INFORMATION ABOUT THE EXAMPLE
Extended Version:
FURTHER QUESTION
Interactive App: APP TITLE
Estimated Time: TIME minutes. What You’ll Need: Computer and projector.
DESCRIPTION
TITLE App: URL
“explain” activities:.
Introduce important facts and underlying concepts.
Slide Deck: Cybersecurity and Threat Modeling
Estimated Time: 15 minutes. What You’ll Need : Computer, projector, and speakers.
Description: In this presentation, students learn about what cybersecurity is, how threat modeling works, and why threat modeling is a useful place to start for cybersecurity. The slides are accompanied by Notes with details and examples to guide your lecture.
Access Slide Deck: “Cybersecurity and Threat Modeling”
- Presents an overview of web security (4-minute video), slide 2
- Defines cybersecurity, slides 3–9
- Defines cyber attack, slide 10
- Defines threat modeling, slides 11–14
- Explains the strengths and limitations of threat modeling, slides 15–24
Options: If you’re short on time, you might condense the material presented on slides 3–6 and/or skip/remove slides 17–24.
Coming Soon: Graphic organizer for student note-taking.
Estimated Time: TIME minutes. What You’ll Need: Computer, speakers, and projector.
DESCRIPTION.
“Elaborate” Activities:
Go deeper into the underlying concepts and/or let students practice important cybersecurity skills.
Small-Group Activity: Threat Modeling with the Security Cards
Estimated Time: 20-30 minutes What You’ll Need :
- Several sets of Security Cards (1 set per group)
- “Suggested Systems” handouts (1 system/page per group) or students’ sketches of systems they’re already studying or building (if they already have sketches) or blank paper for students to sketch the systems they’re studying or building
- Computer and projector
Description: Students use the Security Cards (from University of Washington) as a tool to practice threat modeling for a computer system. This activity further develops the framework for structured security thinking introduced in the Explore and Explain activities. Includes a slide deck for introducing the activity.
Get (Free) Printable PDFs or Purchase Pre-Printed Decks: The Security Cards from University of Washington
Access slide deck: “threat modeling with the security cards” (continues from explain deck.), download worksheet: “suggested systems”.
- Introduce the activity, using the slides and lecture notes.
- Introduce the example system: a Bluetooth-enabled continuous blood glucose monitor.
- Pass out a deck of Security Cards to each group.
- Introduce the Security Cards.
- Human Impact (blue)
- Adversary’s Motivations (orange)
- Adversary’s Resources (red)
- Adversary’s Methods (green)
- Break students into groups.
- Pass out “Suggested Systems” handouts. The handout has four pages, one for each system. Have students choose which system their group will model, or otherwise explain what system they’ll be using (see Options below). Each group should model only one system.
- Identify stakeholders (direct and indirect) and what data the system handles. Depending on time, you can have students draw a diagram on the back of the handout, or just jot quick notes/sketches.
- Sort the Security Cards by dimension.
- Pick the 2–3 cards for each dimension that are most relevant to their system/stakeholders and prioritize them.
- Ask groups to report back on their card choices and priorities.
- Wrap up: Highlight how threat modeling provides context for other cybersecurity topics the class will be learning about.
Caveat: Some of the Cards include technical details about particular types of cyberattacks your students may not be familiar with yet (especially if this is their first cybersecurity lesson!). For this activity, students don’t need to focus on those details. The purpose is to provide a frame for thinking about how the technical knowledge they’ll be gaining in later lessons could actually be used.
- Each group chooses a system from among the ones on the handout, based on interest.
- Choose which system each group will model at random, and pass them that handout.
- Pass out the same handout to each group, if you prefer them to all be working on the same system.
- The makers of the Security Cards provide some system suggestions .
- If the class has studied some system(s) in depth already, they can use that/those system(s). Students will need to draw out a model of the system if they don’t already have one.
- (Advanced version) If your students are designing or building systems in groups, they can work with their regular group and use the systems they’re building. Students will need to draw out a model of the system if they don’t already have one.
Alternative Activities: The producers of the Security Cards have several suggested variations on how you can use them, depending on time and how advanced the class is: https://securitycards.cs.washington.edu/activities.html
Credits: Some of our instructions and explanations are paraphrased with permission from the University of Washington’s “ Sorting by Importance ” activity. Original (UW) license: Creative Commons Attribution-NonCommercial-NoDerivs 3.0 (CC BY-NC-ND 3.0).
Coming Soon: Unplugged version with “Introducing the Security Cards” handout and slide-free teacher’s notes.
In-Class Whole-Group Activity: TITLE
More stuff here.
Making Connections: Small-Group Discussion Questions
Estimated Time: Depends on protocol chosen. What You’ll Need: Blackboard/whiteboard (optional).
Use one or more of the following questions to help students digest the information presented in the lesson so far and personalize the content. The questions are compatible with many common classroom discussion protocols. We suggest Think-Pair-Share , Inside/Outside Circles , Chalk Talk , or Listening Dyads , but many others can be found on the NSRF’s protocol list .
QUESTION(S).
“Evaluate” Activities:
Assess students’ understanding of the material and development of new skills.
Assignment: Interpreting the Cybersecurity News
Estimated Time: 10-15 minutes.
- Copies of the assignment handout (one per student/group)
- Students will need pens/pencils
Description: Students (individuals or groups) read an article about a cybersecurity breach (or attempted breach) and complete an assignment by answering questions about the incident.
Download Handout: “Interpreting the Cybersecurity News”
Good sources for recent articles on cybersecurity incidents:
- SANS NewsBites (semiweekly newsletter on security incidents and news, with links to full news articles)
- Krebs on Security (blog about recent security breaches and related news/analysis)
- Wired , “ The Biggest Cybersecurity Crises of 2019 So Far ” (similar roundups once or twice a year; summaries and links to news articles)
- CSIS, “ Significant Cyber Incidents Since 2006 ” (running list of incidents; does not cite articles)
Suggestions when picking articles (or incidents) to assign:
- Think about whether students can easily relate to the incident or its consequences.
- Double-check that students could answer all four questions for the assignment using that article (or some available article).
Assignment Options:
- Pick one article for the whole class.
- Present a list of articles they can choose from.
- Assign a different article to each student/group.
Optional Extensions
- If students/groups are assigned different incidents, have them present their incident to the class.
- Teach Global Impact’s tips for identifying good sources (boxes at bottom left and top right)
Download Sample Responses: “Interpreting the Cybersecurity News (Example Responses)”
Review questions (quiz/homework).
Estimated Time: TIME minutes. What You’ll Need: Copies of review sheet.
This learning assessment can be used as an in-class quiz or as homework.
Download Assessment: “MODULE TITLE: Review Questions”
Answer key coming soon!
More for Teachers
Resources and background information to help you brush up on the technical nitty-gritty and be prepared for student questions.
Other Recommended Classroom Resources for Threat Modeling and the Security Mindset
Activity type: title.
- Target grades: XXX
- Summary: One or two sentences.
- Produced by: Producer.
Contact us and let us know what you think!
Email Address
Security-Assignments.com
Content for an information security management course.
By Drs. Dave Eargle and Anthony Vance
Learn more · Adoption guide
Book and Film List
Reading topics, in-class activities.
Assignment Five: Web Security (Group Assignment)
This project presents an insecure website that you will attack. You will focus on three common classes of vulnerabilities: SQL injection, cross-site request forgery, and cross-site scripting. We will present you with several flawed defenses for each of these classes. By exploiting these vulnerabilities, you will improve your own understanding of secure web application programming and get a taste of how web security analyst may probe a customer’s product. This is a group assignment and must be done in groups of two or three only. You will complete three parts in this assignment, and each group member must contribute to all of the parts.
This project asks you to perform several tasks that would be considered network attacks in many situations. For this project, you have our permission to target a website that we are providing for this purpose. Attempting the same kinds of attacks against other websites without authorization is prohibited by law and university policies. You must not attack any website without explicit permission from an authorized administrator of that website.
The purpose of this assignment is to help you become familiar with three specific vulnerability classes. You may also notice other security flaws on this site, such as insecure password handling and a lack of HTTPS. Exploiting any vulnerability that is not directly instructed below is out of scope for this assignment. In particular, exploiting (either passively or actively) any vulnerability that allows you to view or tamper with another group’s work will be considered academic misconduct in violation of Princeton University’s “ Rights, Rules, Responsibilities .”
Target Website Scenario
You will play the role of a security contractor for a fictitious startup named “ BUNGLE .” This startup is about to launch its first product – a search engine – but their investors are nervous about security problems. Unlike the bunglers who developed this site, you’re studying information security, so the investors have hired you to perform a security evaluation before it goes live.
A prototype version of the BUNGLE search engine is live at https://bungle.cos432.org . The site is written using the Python Bottle framework. Although this framework has built-in mechanisms to prevent certain vulnerabilities, the bunglers in charge of performance optimization disabled or circumvented many of them to “improve the user experience.”
In addition to providing search results, the site manages user sessions and search histories. It stores usernames, passwords, and search history in a MySQL-style database. Your colleagues have determined that the website responds to the following five paths:
Defense Levels: The bunglers have been experimenting with some primitive defense mechanisms to protect against web attacks, so you must demonstrate unique attacks against each defense level. The sections below will describe the defense mechanisms for each part. It is important to note that the defense mechanisms for part two and three are invoked using drop-down menus at the top of each page. These drop-down menus allow you to change the defense mechanisms to various levels. The solutions you submit must override these selections by including the extra csrfdefense=n and/or xssdefense=n parameters in the target URL, as specified by each of the sections below. Attempting to subvert the mechanism for changing defense levels will award no credit for any of the attacks. Be sure you are testing your solutions with the correct defense levels!
Tools and Resources
This assignment depends on more background knowledge than a lecture could teach. Do not be afraid to search online for basic tutorials on web application technologies or vulnerabilities and exploits, just be sure to respect the Collaboration Policy . Here are some examples of tools and resources that may help you get started:
- Firefox Developer Tools
- SQL Tutorials
- SQL Syntax Guide
- Intro to HTML
- JavaScript 101
- Using jQuery Core
- jQuery API Docs
- Web Technology Made Really Easy
One very valuable resource for anyone who touches web programming is the Open Web Application Security Project (OWASP) . It has many different articles and best practices for both defending and auditing websites and web applications. The following “cheat sheets” in particular should be useful for you:
- SQL Injection Prevention Cheat Sheet
- Cross-Site Request Forgery (CSRF) Prevention Cheat Sheet
- Cross-Site Scripting Prevention (XSS) Cheat Sheet
- XSS Filter Evasion Cheat Sheet
Getting Started
Please complete this assignment using the same VM as the previous assignment to help keep your attacks consistent with our solutions/testing environment. Log into the virtual machine, download this assignment’s files to the virtual machine, and proceed to the following parts. You will submit your solutions in a zipped directory of various text files that are described in each part of the assignment.
Part 1: SQL Injection
Your first goal is to demonstrate SQL injection attacks that log you into arbitrary user accounts without knowing the password. In order to protect other students’ accounts, you will perform these attacks on a series of separate login forms outside of the default BUNGLE website. For each of the following defenses, exploit a SQL injection vulnerability that successfully logs you into the user account named “victim”. When you are successful, you will see a page titled “Login successful! (victim)” and it will instruct you as to what should go in your submission file.
0. No Defenses
1. simple escaping, 2. escaping and hashing.
The server now uses the following PHP code to escape the username and apply the MD5 hash function to the password:
This will be more challenging than the previous two defenses. You need to write a program that generates a working exploit. You can use any language you like, but pay close attention to the size of your search space and the performance of your program. Consider using C to avoid unnecessary computational overhead, but focus primarily on reducing the search space of your program.
3. SQL Extra Credit
This defense level is testing a different database configuration. Your job is to use SQL injection to retrieve the following information:
- The name of the database.
- The version of the SQL server.
- All of the table names in the database.
- A secret string hidden in the database.
Example submission file:
What to submit:
For 1.0, 1.1, and 1.2, when you successfully log in as victim, the server will provide a URL-encoded version of your form inputs. Submit the appropriate text files with each containing only this line. For 1.2, also submit the source code for the program you wrote, as a zip file (sql_2_src.zip). For 1.3, submit a text file as specified if you attempt the extra credit.
Part 2: Cross-Site Request Forgery (CSRF)
Your next step is to demonstrate CSRF vulnerabilities against the login form. BUNGLE has provided two variations of this implementation for you to test. Your goal is to construct attacks that cause a victim to log into an account you control. This will cause all of the victim’s search history to save into an account you can monitor.
For each of the following defenses, create an HTML file that logs a victim into BUNGLE with the username attacker and password l33th4x . The HTML file should log into the account with no interaction; it should not display any evidence of an attack (i.e., just a blank page). The next time the victim’s browser visits the BUNGLE page, it should say “logged in as attacker.”
1. Token Validation
The server will now set a cookie named csrf_token with a random 16-byte value and include the value as a hidden field in the login form. When the form is submitted, the server will verify that the client’s cookie matches the value in the form. The CSRF Prevention Cheat Sheet will be very helpful here. You should consider exploring cross-site scripting attacks to help circumvent this defense.
2. Token Validation without XSS (Extra Credit)
This is exactly the same as the previous task, but you are no longer allowed to use XSS. This should be impossible unless there is a mistake in the implementation of the project.
For each defense level, submit an HTML file with the appropriate name. Be sure your exploits are targeting the correct defense levels. Your code must be self-contained, but you are allowed (and encouraged) to use inline JavaScript imports for jQuery and jQuery cookies library (i.e., http://ajax.googleapis.com/ajax/libs/jquery/2.1.4/jquery.min.js and https://cdnjs.cloudflare.com/ajax/libs/jquery-cookie/1.4.1/jquery.cookie.min.js ).
Test your solutions by opening them as local files in a new private browser session with the VM web browser and then browsing to the BUNGLE page in a new tab; you should see that the new tab is already logged into the attacker account.
Part 3: Cross-Site Scripting (XSS)
Your final goal is to demonstrate XSS attacks against the BUNGLE search box, which does not properly filter input before echoing it to the results page. For each of the defenses below, your goal is to construct a URL that will execute the payload described below. Your constructed URL should execute the payload when it is pasted into the browser address bar or clicked as a link. We recommend that you begin testing a simple payload such as alert(0); before moving to the full payload. Note that you should implement the payload once, then encode it in different ways that bypass each of the different defenses.
The payload is simply a program or code-snippet that the attack will execute in a victim’s browser. The goal of your payload is to steal the username and most recent search query of the victim. When a victim clicks on your malicious URL or pastes it into the browser address bar, the payload will steal the username and the search query from the browser and send it to the attacker. For this assignment, you can construct the destination for your exfiltration using javascript code similar to this snippet:
You can use this log_listener python script to test your exploit. In a terminal window, find the log_listener.py file you just downloaded then run python log_listener.py . When your exploit work successfully, you will see the username and search query reported in the terminal window.
There are five levels of defense for this part of the assignment. In each case, you must submit the simplest attack that you can find. Each defense level must have a different solution in your submission for full credit. Each text file you submit should have only the malicious URL that will execute your exploit.
1. Remove “ script “
2. remove several tags, 3. remove some punctuation, 4. encode < and > (extra credit).
This should be impossible unless there is a mistake in the implementation of the project.
Your submission for each level of defense will be a text file with the appropriate filename and containing a single URL. When the URL is loaded into the victim’s browser, your payload should execute as described above. Your code must be self-contained, but you are allowed (and encouraged) to use inline JavaScript imports for jQuery and jQuery cookies library (i.e., http://ajax.googleapis.com/ajax/libs/jquery/2.1.4/jquery.min.js and https://cdnjs.cloudflare.com/ajax/libs/jquery-cookie/1.4.1/jquery.cookie.min.js ).
Part 4: Better Defenses Writeup
For each of the three classes of vulnerability (SQL injection, CSRF, and XSS), write a short paragraph of advice that describes the best practices for defending against these attacks. Be sure to understand what the current state of the art defenses are and describe them in just enough detail to demonstrate that. You will submit this in part4/writeup.txt .

Submission Requirements
You will submit all of your files in the same structure as the assignment files you downloaded. Please zip the directory and upload it to Gradescope with this directory structure:
- sql_0.txt - 1.0 No Defenses
- sql_1.txt - 1.1 Simple Escaping
- sql_2.txt - 1.2 Escaping and Hashing
- sql_2_src.zip - Source code for 1.2 Escaping and Hashing
- sql_3.txt - 1.3 SQL Extra Credit
- csrf_0.html - 2.0 No Defenses
- csrf_1.html - 2.1 Token Validation
- csrf_2.html - 2.2 Token Validation (Extra Credit)
- xss_payload.html - Human-readable payload script
- xss_0.txt - 3.0 No Defenses
- xss_1.txt - 3.1 Remove script
- xss_2.txt - 3.2 Remove Several Tags
- xss_3.txt - 3.3 Remove Some Punctuation
- xss_4.txt - 3.4 Encode < and > (Extra Credit)
- writeup.txt - Better Defenses Writeup
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Microsoft.Security assignments
- 1 contributor
- 2021-08-01-preview
Bicep resource definition
The assignments resource type can be deployed with operations that target:
- Resource groups - See resource group deployment commands
For a list of changed properties in each API version, see change log .
Resource format
To create a Microsoft.Security/assignments resource, add the following Bicep to your template.
Property values
Assignments, assignmentproperties, assignmentpropertiesadditionaldata, assignedcomponentitem, assignedstandarditem, arm template resource definition.
To create a Microsoft.Security/assignments resource, add the following JSON to your template.
Terraform (AzAPI provider) resource definition
- Resource groups
To create a Microsoft.Security/assignments resource, add the following Terraform to your template.
Was this page helpful?
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback .
Submit and view feedback for
Additional resources
Cyber Insight
What is cyber security assignment? Tips from an expert.
Updated on: June 17, 2023

I have seen firsthand the devastating consequences that can come from a cyber attack. It’s not just about protecting your personal data anymore; it’s about safeguarding the entire infrastructure that our society relies on. So, if you’re tasked with a cyber security assignment, it’s not just a homework task – it’s a responsibility to help keep our world safe and secure.
But where do you start? With the rapidly evolving landscape of cyber threats and the complex technology used to counter them, it can be overwhelming for even the most tech-savvy of individuals. That’s why I’m here. In this article, I’ll share some tips and tricks for tackling your cyber security assignment like a pro. From understanding the basics to implementing advanced techniques, you’ll have the tools you need to make a difference in the fight against cybercrime. So, let’s dive in and get started.
What is cyber security assignment?
In summary, a cybersecurity assignment revolves around ensuring the security of internet-related devices and services from malicious attacks. This is achieved by identifying potential threats, developing a security strategy, implementing security measures, and monitoring and reviewing these measures to remain effective.
???? Pro Tips:
1. Understand the scope of the assignment: Before starting, ensure that you have a clear understanding of what is expected from the cyber security assignment. Be sure to read and reread the instructions given and clarify any doubts with your instructor.
2. Research different aspects of cyber security: Cyber security is a vast field, and it is crucial to have a basic understanding of its various areas, such as network security, data security, and incident management, to name a few.
3. Consider real-world scenarios: To make your assignment relevant, consider real-world scenarios and apply the knowledge you have acquired. This could be an analysis of a cyber attack or suggestions to prevent a similar occurrence.
4. Follow best practices: Ensure that you follow industry-recognized best practices to create a well-researched and comprehensive assignment. Use credible sources for reference, and provide due credit to sources used.
5. Stay up-to-date: Cybersecurity is a rapidly evolving field, with new threats and solutions emerging regularly. It is, therefore, essential to stay current and up-to-date with the latest trends and developments in the field. This will help make your assignment informative and relevant.
Understanding Cybersecurity and Its Importance
Cybersecurity is the practice of protecting internet-connected devices and services from cyber attacks. Cyber attacks include malicious activities, such as hacking, stealing sensitive information, spreading malware, and disrupting critical infrastructure systems.
In today’s digital age, where the majority of businesses and organizations rely on digital technologies to perform their daily operations, cybersecurity has become more critical than ever before. The increasing use of the internet and connected devices has led to a surge in the number of cyber attacks, which can cause severe financial and reputational damages for businesses.
The importance of cybersecurity cannot be overstated. A successful cyber attack can cause significant losses and damage to a company’s reputation. Therefore, organizations must implement robust cybersecurity measures to protect their systems and data.
Types of Cyber Attacks and Threat Actors
Cyber attacks can come in many forms, each with a specific objective. Here are some of the most common types of cyber attacks:
Phishing Attacks: These are social engineering attacks that trick users into sharing sensitive information, such as passwords or credit card details.
Ransomware: This type of malware encrypts the victim’s files and demands a ransom payment to restore access.
Denial-of-Service (DoS) Attacks: These attacks overload a target system with requests, making it unavailable to legitimate users.
Malware: This is a type of software designed to infiltrate a system and cause harm.
The threat actors behind cyber attacks can be anyone from lone-wolf hackers to state-sponsored hacking groups. Many of these attacks can be prevented by implementing cybersecurity best practices and protocols.
Cybersecurity Protocols and Best Practices
Here are some of the best cybersecurity protocols and practices that businesses can implement to protect their systems and data:
Use Strong Passwords: Passwords should be complex and unique for each account.
Implement Firewall and Antivirus Software: This helps to prevent unauthorized access and malware infections.
Encrypt Sensitive Data: Encryption helps to protect data even if it falls into the wrong hands.
Provide Cybersecurity Awareness Training: This helps to educate employees on best cybersecurity practices.
Conduct Regular Security Audits: Regular security audits help to identify vulnerabilities and threats before they can be exploited.
The Role of Cybersecurity in Business Operations
The role of cybersecurity in business operations cannot be emphasized enough. Cybersecurity helps to protect the company’s intellectual property, sensitive data, reputation, and financial stability. Moreover, implementing cybersecurity measures can attract customers who are increasingly concerned about the safety of their data.
The consequences of a successful cyber attack can be severe. It can lead to legal penalties, loss of revenue, and even bankruptcy. Therefore, businesses must prioritize cybersecurity in their operational strategies.
Cybersecurity Challenges and Emerging Threats
The cybersecurity landscape is continually evolving, and new threats emerge every year. Some of the most significant challenges that organizations face today are:
Advanced Persistent Threats (APTs): These are stealthy attacks that infiltrate a system and remain undetected for a long period.
Internet of Things (IoT) Vulnerabilities: The proliferation of IoT devices creates new vulnerabilities that can be exploited by cybercriminals.
Cloud Security: As more businesses move their operations to the cloud, the risk of cloud-based attacks increases.
Organizations must stay up-to-date with emerging threats and implement robust measures to mitigate them.
Advancements in Cybersecurity Technologies
As cyber attacks become more sophisticated, cybersecurity technologies have evolved to keep up. Some of the significant advancements in cybersecurity technologies include:
Artificial Intelligence (AI): AI-powered cybersecurity solutions can help detect and mitigate cyber threats in real-time.
Biometric Authentication: Biometric authentication, such as fingerprint or facial recognition, strengthens the security of sensitive data.
Quantum Cryptography: Quantum cryptography is an emerging technology that uses quantum mechanics to encrypt data securely.
Cybersecurity Compliance and Legal Regulations
Compliance with cybersecurity regulations and laws is critical for any business that collects, stores, or processes customer data. Some of the most prominent cybersecurity regulations include:
General Data Protection Regulation (GDPR): This regulation governs how businesses in the European Union (EU) handle, process, and store personal data.
California Consumer Privacy Act (CCPA): This act requires businesses to inform Californian consumers about the personal data they collect, use, and share and provide them with the right to opt-out.
Payment Card Industry Data Security Standard (PCI DSS): This standard regulates how businesses that accept credit card payments handle cardholder data.
In summary, cybersecurity is critical for any business that uses digital technologies to perform its operations. Organizations must implement robust cybersecurity measures, protocols, and practices to protect their systems and data from cyber attacks. As the cybersecurity landscape continues to evolve, organizations must stay up-to-date with emerging threats and comply with legal regulations and standards.
most recent

Cybersecurity Basics
What are the three approaches to security in cyber security: explained.

Services & Solutions
What is security solution and why it matters: ultimate guide.

Training & Certification
Is a masters in cybersecurity worth the investment.

What is the Cyber Security Strategy Objective? Protecting Against Breaches.

What is Dart in Cyber Security? A Powerful Tool for Threat Detection.

Decoding SLED: Is Public Sector Cybersecurity the Same?
PH +1 000 000 0000
24 M Drive East Hampton, NY 11937
© 2024 INFO
- Practical Law
Security assignment of contractual rights
Practical law uk standard document 9-508-0695 (approx. 96 pages), get full access to this document with a free trial.
Try free and see for yourself how Practical Law resources can improve productivity, efficiency and response times.
About Practical Law
This document is from Thomson Reuters Practical Law, the legal know-how that goes beyond primary law and traditional legal research to give lawyers a better starting point. We provide standard documents, checklists, legal updates, how-to guides, and more.
650+ full-time experienced lawyer editors globally create and maintain timely, reliable and accurate resources across all major practice areas.
83% of customers are highly satisfied with Practical Law and would recommend to a colleague.
81% of customers agree that Practical Law saves them time.
- Security and Quasi Security
- Trade Finance
- Asset finance and trade finance
- Corporate lending
- Insurance in commercial transactions
- Browse topics
SNYK LEARN LOGIN
- 🌍 Snyk (recommended)
OTHER REGIONS
For Snyk Enterprise customers with regional contracts. More info
- 🇦🇺 Snyk AUS
Mass assignment
Be careful with parameters that are automatically bound from requests to objects, select your ecosystem, mass assignment: the basics, what are mass assignment vulnerabilities.
To make it easier to save data submitted via an HTML form into a database or object, many web application frameworks have included libraries to automatically bind HTTP request parameters (typically sent via forms) to the fields of database models or members of an object, requiring only minimal coding.
Let’s say we have a (very simple) HTML form:
When the form is submitted to the web application, it will send the form data as HTTP request parameters, and the backend code will have to read each parameter individually into a corresponding variable. Then, once all the fields have been read, the application will usually execute a database update or insert operation to save the data.
Mass Assignment makes it possible to write less code to handle this process - think about how much coding this technique could save if it was an object that had dozens of fields, and multiply this across a complex application that has many of these objects in its database.
Mass assignment vulnerabilities occur when the database model that is being assigned contains security-relevant fields, and the application user can supply values in the POST request that are saved to those fields, even though they are not present in the HTML form.
For example, if the User model contained a field isAdmin: Boolean , the user could add the POST body parameter isAdmin=true and make themselves an administrator.
For this to occur, an attacker would need to guess the names of the sensitive fields, or the source code for the vulnerable application would have to be available to the attacker (allowing them to see what sensitive fields are present in the data model).
Impacts of this attack can include bypassing authentication or authorization logic or elevation of privilege. This could then result in the destruction or disclosure of data within the application.
About this lesson
In this lesson, you will learn how mass assignment vulnerabilities work and how to protect your applications against them. We will begin by exploiting a Mass Assignment vulnerability in a simple application. Then we will analyze the vulnerable code and explore some options for remediation and prevention.
Mass assignment in the wild
In 2012, a GitHub user exploited a Mass Assignment vulnerability in GitHub’s public key update form. The flaw allowed the user to add their public key to another organization they were not a member of. The user added their key to the Ruby on Rails organization. To demonstrate proof of the exploit, the user added a file to the Rails project repository. GitHub responded, quickly fixing the vulnerability and they conducted a wide audit of their code to ensure the issue was detected and fixed if it existed anywhere else.
Mass assignment in action
New SaaS startup SuperCloudCRM recently launched their web platform designed to help businesses boost their sales and marketing efforts.
Setting the stage
SuperCloudCRM recently launched its web platform. Unfortunately, they suffered a security breach, resulting in data being leaked. What went wrong?
Mass assignment details
As mentioned, SuperCloudCRM’s developers had been logging request data for API endpoints like the POST /user/create endpoint, which creates new user accounts when a user submits the signup form.
A typical JSON payload in the request sent to the /user/create endpoint was supposed to look like this:
But a search of the /user/create endpoint’s logs for the [email protected] account around the time the user was created, found JSON POST data starting with the following excerpt:
It was different to the normal requests, and had a long request body with dozens more fields all starting with the letter r . What was the attacker doing? All of these weird field names that weren’t part of the user model schema, which was:
After doing some testing like the scenario above showed, a few things were discovered.
First, the new user account’s password was apparently being saved to the database in plaintext. Not good! But what stuck out was that the application ignored the non-existent fields and just assigned the fields that were actually part of the User model schema.
The data from the new User document was sent back to the API client and the attacker could then infer which of the list of fields starting with r were part of the User model schema, because if a field existed it was saved and echoed back in the response with the other user data.
A search of the /user/create endpoint’s request log entries around the same time revealed that thousands of similar requests had been sent. Each request testing lists of possible field names in the User model schema.
It was concluded that the attackers had brute-forced HTTP requests with various field name guesses to enumerate the organization and role fields in the schema. Despite them not being referred to anywhere in the client-side JavaScript code, the attackers were able to discover these security-related field names.
So, if the attackers knew these field names, what would they do then? Well, this could have led to a possible mass assignment attack. After hours of reviewing logs for the POST /user/create and POST /user/update endpoints the incident response team found dozens of requests had been submitted to the application, which looked similar to:
The requests appeared to be successful. Each of the requests changed the organization to a different customer, essentially giving the attackers access to each of them as admins. The last request was:
This seemed to explain why [email protected] was an administrator in the Cowmoo Industries organization.
By exploiting this mass assignment vulnerability and adding themselves as the administrator for various customers, the attackers were able to access the organizations’ data within SuperCloudCRM and steal it.
Mass assignment by different names
The concept of mass assignment is known by different names in various programming languages or frameworks. NodeJS and Ruby on Rails call it mass assignment. It is referred to as autobinding in Java Spring MVC and ASP NET MVC. PHP calls it object injection.
Mass assignment under the hood
Let’s have a look at this vulnerable application in more detail by going through the server-side code.
The schema for the User model is defined here, with the user’s credentials, email address, plus their role and organization they belong to. During signup, the credentials and email address are the only values that are supposed to be supplied by the user and accepted by the application.
Firstly, let's recap what took place in the example above.
- The User schema consisted of several fields: username, password, email, role and organization.
- Only the username, password and email fields were sent from the web browser to the /user/create endpoint
- The API endpoint used mass assignment to blindly assign any field from the POST request’s JSON data to the User model in the database (if the field existed in the User schema).
- The attackers were able to determine the names of security-related fields in the schema (role and organization)
- The attackers could supply arbitrary values for these fields when creating or updating a user account
- This let the attackers add themselves to other organizations and elevate their privileges to those of an administrator
Here ( $user = new User($request->post()); ), the endpoint creates a new User object and in doing so, passes all contents of the POST request to the constructor. PHP can “smartly” figure out which parameters go to which attributes of the class; however, this isn’t so smart when those attributes are certain things that shouldn’t be assignable! Even if the form only accepts inputs with username , password and email , a malicious actor can guess the other forms and simply add those fields to the JSON manually. As PHP has no way of discerning what it receives from “good” and “bad”, it simply updates them all. If only there were a way to tell PHP exactly which fields we don’t want to be assignable like that!
Impacts of mass assignment
By exploiting mass assignment vulnerabilities, a malicious actor could create multiple security problems including
- Data tampering : Attackers can modify sensitive information in the database, such as password or account balance
- Data theft : Attackers can gain access to confidential information stored in the database
- Elevation of privilege : Attackers can manipulate the properties of an object to gain additional privileges, such as administrator access
- Unauthorized access : Attackers can manipulate the properties of an object to gain unauthorized access to sensitive resources
Scan your code & stay secure with Snyk - for FREE!
Did you know you can use Snyk for free to verify that your code doesn't include this or other vulnerabilities?
Mass assignment mitigation
Use an allowlist of fields that can be assigned to.
Most mass assignment libraries or helper libraries should provide the ability to restrict the fields that will be read from a request and assigned to the data model. By restricting the assignment of user-supplied fields to only fields in the schema that are known safe ones, the values of security-sensitive fields will be prevented from tampering.
Using this strategy, the code for the application would be changed to add an allowlist using the pick() method of the underscore package and listing the allowed fields in the userCreateSafeFields array:
Laravel provides a library, eloquent , which, among other things, introduces object injection protection features! It gives you the ability to indicate variables that can be assigned, or otherwise, you can indicate variables that you don’t want assignable. This means that when you use mass assignment to populate a class with request data, the Laravel backend can (with your guiding hand) separate POST request input data from fields that should be populated and those that should not!
Using this strategy, the code for the application can be changed to add an allow-list of class attributes, enforcing that only these will be updated:
Use a Data Transfer Object (DTO)
Another option is to create an intermediary object (the DTO) that only has safe, assignable properties, which would be a subset of the target object that has those same fields plus any sensitive fields. Using our User example, the DTO would be:
The mass assignment operation can assign any user-supplied data to the DTO without the risk of inadvertently assigning any sensitive fields. The DTO can be copied to the final object, and during this process, any sensitive fields can be set to secure default values.
This method might require much more coding though. DTOs need to be created for all classes with sensitive fields. If there are many schemas with sensitive fields that require corresponding DTOs, then this becomes nearly as much work as not using mass assignment.
Use a denylist to declare fields that can’t be assigned to
The opposite of using an allowlist to define fields that are allowed to be assigned is to use a denylist of fields that shouldn’t be assigned. Security wisdom says to use allowlisting over denylisting because it’s safer to accidentally not include a safe field than to accidentally omit a dangerous field. So, following this advice, a denylist would be the less preferred option of the two. If there are 50 fields in a schema and only one is security-sensitive, then it is obviously much quicker to just denylist the one sensitive field. The danger here though would be if additional sensitive fields were added to the schema later and the developer forgot to add them to the denylist, then you would have a mass assignment vulnerability.
To use denylists, the code for the application would be changed in a similar manner to the code shown in the allow-list strategy shown earlier, except it would use the omit() method of the underscore package and listing the disallowed fields in the userCreateDisallowedFields array:
To use deny-lists, the code for the application would be changed in a similar manner to the code shown in the allow-list strategy shown earlier, the only difference being the User class is changed to have a “hidden” array:
Utilize a static analysis tool
Adding a static application security testing ( SAST ) tool to your devops pipeline as an additional line of defense is an excellent way to catch vulnerabilities before they make it to production. There are many, but Snyk Code is our personal favorite, as it scans in real-time, provides actionable remediation advice, and is available from your favorite IDE.
Keep learning
To learn more about mass assignment vulnerabilities, check out some other great content:
- OWASP guide to mass assignment vulnerabilties
- Find mass assignment in our top 10 list
Congratulations
You have taken your first step into learning what mass assignment is, how it works, what the impacts are, and how to protect your own applications. We hope that you will apply this knowledge to make your applications safer.
We'd really appreciate it if you could take a minute to rate how valuable this lesson was for you and provide feedback to help us improve! Also, make sure to check out our lessons on other common vulnerabilities.
What is mass assignment?
Mass assignment is a type of security vulnerability that occurs when an application code allows user-provided data to be used to set properties on an object without verifying that the user has the right to do so.
What to learn next?
Insecure plugins for llms, snyk apprisk pro - using application analytics (tenant->analytics->applications), snyk apprisk pro - secrets detection coverage with nightfall ai.
Security Assignments – Not Always What They Say They Are?
Contributor

The nature of security created under a security document does not always match its description in the document. Charlotte Drake explains how this recharacterisation risk can apply to security assignments.
Is an "absolute" security assignment legal or equitable?
Legal assignments – key requirements.
Lenders commonly take security over "choses in action" (such as debts or rights under contracts) by way of assignment. An assignment involves the transfer of either legal ownership (legal assignment) or equitable ownership (equitable assignment).
Section 136 of the Law of Property Act 1925 dictates the formalities for taking a legal assignment. It requires that a legal assignment must (among other things):
- be in writing;
- be executed by the assignor;
- be "absolute";
- not be expressed to be "by way of charge" only; and
- be notified in writing to the person against whom the assignor could enforce the assigned rights (the third party).
Legal assignments by way of security
There has been much case law on what "absolute" means. An assignment will not be absolute if it is conditional, or of part of a debt. However, a security assignment can qualify (provided it is not "by way of charge"): the fact the assignor has an equity of redemption under a security assignment does not of itself prevent the assignment from being "absolute". Security assignments sometimes use the term "absolute" to make clear they are intended to be legal assignments. However, the terminology used is not decisive. An assignment will not be "absolute" unless the third party can then deal with the assignee alone in respect of the assigned rights. The assignee owes an obligation to the assignor to reassign the rights on discharge of the secured liability. But the third party can continue to deal with the assignee until it receives notice of that reassignment.
In practice, this usually presents a considerable stumbling block to taking security by way of a legal assignment. Security assignments often allow the assignor to continue to deal with the third party, which commercially suits assignor, assignee and third party alike. However, such an assignment will not be "absolute" and so will take effect in equity only, even if the security document claims to effect a legal assignment.
The recent case of Ardila Investments NV v. ENRC NV and another 1 highlighted this. The judge accepted that the assignment clause in the document used "the words of a legal assignment". However, he pointed to other clauses in the assignment document which suggested the parties had intended it to take effect in equity rather than law. One of these clauses obliged the assignor to "pursue its rights" under the assigned contracts, which is clearly inconsistent with an absolute assignment.
Legal or equitable – does it matter?
Often not. A notified equitable assignment has as strong a priority against other interests in the assigned rights as a legal assignment.
One advantage of a legal assignment is that a legal assignee can sue the third party without the assignor's involvement. Received wisdom used to be that an equitable assignee could not sue alone and the assignor (as owner of the legal interest) must be joined in as party to proceedings (either as co-plaintiff if willing, or as co-defendant if not).
In Ardila the judge held that the assignment took effect in equity and that both assignor and assignee should join in the proceedings as co-claimants. As it happened, when the hearing took place, the assignor had been joined as co-claimant anyway. In other cases, an equitable assignee has been able to sue the third party alone. As a purely practical matter, even if the assignor does need to be joined into proceedings this is unlikely to be more than an inconvenience.
Could a security assignment be "floating" security?
Could there be another, more unpalatable, result of control remaining with the assignor following a security assignment? In Re Spectrum Plus 2 , the House of Lords of course held that a charge over a debt will be floating, not fixed, if the security holder fails to exercise control over the debt proceeds. Is a security assignment of a debt or similar contractual right also at risk of being recharacterised in this way? This is far from a settled point, but these obiter comments from Lord Scott in Re Spectrum Plus (at paragraph 107) suggest so:
" Suppose, for example, a case where an express assignment of a specific debt by way of security were accompanied by a provision that reserved to the assignor the right, terminable by written notice from the assignee, to collect the debt and to use the proceeds for its (the assignor's) business purposes, ie, a right, terminable on notice, for the assignor to withdraw the proceeds of the debt from the security. This security would, in my opinion, be a floating security notwithstanding the express assignment. "
There is some logic in this approach. If it were possible to "solve" Re Spectrum Plus by renaming all charges over debts as security assignments, the case would not have taken on the significance that it has. The risk of this type of recharacterisation is most obvious in a UK insolvency, where there is a clear distinction between the application of fixed and floating recoveries. In this context, at least, the "fixed/floating" distinction is likely to be more of a concern to a lender than whether its security assignment is "legal" rather than "equitable".
1. [2015] EWHC 1667 (Comm) (11 June 2015)
2. [2005] UKHL 41.
The content of this article is intended to provide a general guide to the subject matter. Specialist advice should be sought about your specific circumstances.

Finance and Banking
Mondaq uses cookies on this website. By using our website you agree to our use of cookies as set out in our Privacy Policy.
How To Prevent
- API7:2019 Security Misconfiguration
- API8:2019 Injection
- API9:2019 Improper Assets Management
- API10:2019 Insufficient Logging & Monitoring
- What's Next For Developers
- What's Next For DevSecOps
- Methodology and Data
- Acknowledgments
API6:2019 - Mass Assignment
Is the api vulnerable.
Objects in modern applications might contain many properties. Some of these properties should be updated directly by the client (e.g., user.first_name or user.address ) and some of them should not (e.g., user.is_vip flag).
An API endpoint is vulnerable if it automatically converts client parameters into internal object properties, without considering the sensitivity and the exposure level of these properties. This could allow an attacker to update object properties that they should not have access to.
Examples for sensitive properties:
- Permission-related properties : user.is_admin , user.is_vip should only be set by admins.
- Process-dependent properties : user.cash should only be set internally after payment verification.
- Internal properties : article.created_time should only be set internally by the application.
Example Attack Scenarios
Scenario #1.
A ride sharing application provides a user the option to edit basic information for their profile. During this process, an API call is sent to PUT /api/v1/users/me with the following legitimate JSON object:
The request GET /api/v1/users/me includes an additional credit_balance property:
The attacker replays the first request with the following payload:
Since the endpoint is vulnerable to mass assignment, the attacker receives credits without paying.
Scenario #2
A video sharing portal allows users to upload content and download content in different formats. An attacker who explores the API found that the endpoint GET /api/v1/videos/{video_id}/meta_data returns a JSON object with the video’s properties. One of the properties is "mp4_conversion_params":"-v codec h264" , which indicates that the application uses a shell command to convert the video.
The attacker also found the endpoint POST /api/v1/videos/new is vulnerable to mass assignment and allows the client to set any property of the video object. The attacker sets a malicious value as follows: "mp4_conversion_params":"-v codec h264 && format C:/" . This value will cause a shell command injection once the attacker downloads the video as MP4.
- If possible, avoid using functions that automatically bind a client’s input into code variables or internal objects.
- Whitelist only the properties that should be updated by the client.
- Use built-in features to blacklist properties that should not be accessed by clients.
- If applicable, explicitly define and enforce schemas for the input data payloads.
- CWE-915: Improperly Controlled Modification of Dynamically-Determined Object Attributes
Navigation Menu
Search code, repositories, users, issues, pull requests..., provide feedback.
We read every piece of feedback, and take your input very seriously.
Saved searches
Use saved searches to filter your results more quickly.
To see all available qualifiers, see our documentation .
- Notifications
This repository contains internship assignments completed at Albus Security, showcasing networking and Python skills in concise solutions.
kartavyaojha/albus_security_internship_assignment
Folders and files, repository files navigation, albus_security_internship_assignment.
This repository showcases assignments completed during my internship at Albus Security. Through a series of networking and Python challenges, I've demonstrated problem-solving skills, technical proficiency, and a commitment to learning and growth. Each assignment reflects hands-on experience, meticulous documentation, and the application of best practices in networking and Python programming. Explore the repository to delve into the solutions developed and insights gained throughout my internship journey.
Internship Projects
Networking assignment.
- Successfully resolved various networking challenges including VLAN configuration, SSH setup, and trunking issues.
- Demonstrated proficiency in troubleshooting network problems and implementing solutions for optimal performance.
- Documented approaches and solutions for each challenge, showcasing problem-solving skills and technical knowledge.
Python Assignment
- Completed Python assignment with proficiency, showcasing programming skills and understanding of Python concepts.
- Developed solutions to address specific requirements outlined in the assignment.
- Demonstrated ability to write clean and efficient code, adhering to best practices and principles of Python programming.
- Python 100.0%
- Using Global Human Resources
The Manager Hierarchy: How It's Maintained
In many situations, a person's manager hierarchy must be readily available. For example, a person's line manager may be required during line manager security check, and business intelligence reports often retrieve data based on a manager hierarchy.
How the Manager Hierarchy Is Maintained
A person's manager hierarchy could be derived from active data tables, but the impact of that approach on performance is unpredictable. Therefore, the complete manager hierarchy for each person is extracted from data tables and stored in a separate manager hierarchy table. This table is known as the denormalized manager hierarchy. The denormalized manager hierarchy ensures that a person's manager hierarchy is both easily accessible and up to date.
These denormalized tables are populated during processing based on the source data in the PER_ASSIGNMENT_SUPERVISORS_F table.
- PER_MANAGER_HRCHY_DN / CF – This table is required for evaluating line manager security, head counts, and some of the flows in HCM are based on this table. It’s also used for the assignment list dimensions for OTBI.
- PER_MANAGER_HRCHY_REPORTEES_DN is specific to OTBI reporting only and for assignment manager dimensions data.
When You Run the Refresh Manager Hierarchy Process
Whenever a change is made to a person's manager hierarchy through the application pages, the change is reflected automatically in the denormalized manager hierarchy table. You use the Refresh Manager Hierarchy process to populate the denormalized manager hierarchy table when person records are migrated from other applications.
How You Run the Refresh Manager Hierarchy Process
You run the Refresh Manager Hierarchy process in the Scheduled Processes work area. To run the process, you must have the Human Resource Specialist job role. The process has no default schedule. You can run the process occasionally to perform a complete refresh of the denormalized manager hierarchy. Alternatively, you can specify a schedule to run the process at regular intervals. Refresh Manager Hierarchy processes all types of manager hierarchies.
You can run the process using these processing modes based on the parameter Updated Within the Last N Days value.
To improve performance, few additional parameters are introduced that are considered when running process with NULL or 0 parameter value, that is, Normal – Full Run or OTBI – Full Run
Normal denormalized tables (PER_MANAGER_HRCHY_DN and PER_MANAGER_HRCHY_CF) are automatically synchronized when assignment supervisor data is created or updated from the application pages (New Hire, Change Manager, and so on) or HDL. Automatic synchronization of denormalized data won't happen if Events process is disabled, that is if, HRC: Disable HcmEvents Processing (HRC_DISABLE_HCM_EVENTS_PROCESSING) profile is set to Y, or when assignment supervisor data being uploaded through HDL and in .dat file post process task of RefreshManagerHierarchy is disabled using the setting SET DISABLE_POST_PROCESS_TASKS RefreshManagerHierarchy, or due to SOA composite instances not getting triggered or infrastructure issues.
Guidelines for Running the Process
These are the guidelines to run the process.
- Normal Full Mode (parameter value of blank/NULL) can be run ad-hoc if denormalized data isn’t in synchronization with source assignment supervisor data, or can be scheduled to run once every week (during weekend) or daily once if more frequent full refresh is needed.
- Normal Incremental Mode (positive value) can be scheduled to run daily or multiple times in day if needed, with parameter value, for example 1, all assignment supervisor data created or updated in last 1 day will be considered for processing.
- OTBI Full Mode (parameter value of 0) and OTBI Incremental Mode (parameter value of -ve. For example, -1 needed only if OTBI reports are based on assignment manager dimensions data. De-normalized table PER_MANAGER_HRCHY_REPORTEES_DN doesn’t get synchronized automatically when assignment supervisor data gets created or updated from the application pages or HDL. Process can be scheduled to run in OTBI Full or Incremental mode once daily for populating data.
- In addition to performing full refreshes of the manager hierarchy, you can perform incremental refreshes. With this approach, you refresh the hierarchy based on manager changes occurring in the previous N days. Schedule a full refresh every month or quarter and an incremental refresh every day or week, for example.
- You can select to run for a period of days since the last updated date, and you can exclude inactive assignment and any historical data by selecting the Ignore Inactive Assignments and Ignore Historical Data options when the process is run on Full mode.

- English (United States)
- English (United Kingdom)
- français (Suisse)
- norsk bokmål (Norge)
- português (Brasil)
- Deutsch (Deutschland)
- SIRVA
- Learning Center
How Duty of Care Can Help Support and Retain Talent

As the world of work continues to evolve, global mobility has experienced a substantial shift, especially after the pandemic. One aspect of global mobility in particular, duty of care, has had to adjust accordingly.
Recently, Sirva’s Jennifer Rowe, senior manager, intercultural services, participated on a panel of Mobility and Human Resources experts at a NYC SHRM event discussing duty of care and the evolution of this important aspect of mobility. Among the topics discussed were:
As the world has faced challenging situations over the past few years, it is important that global mobility programs adapt to accommodate the evolving needs of a changing workforce. Looking at ways to support employees with robust duty of care support can ensure the right candidates are moving to the right locations, their families are supported, and the company’s goals are met.
For more information on the ways you can incorporate duty of care into your relocation program, please contact your Sirva representative or email us at [email protected] .
Smart. Helpful. Human. Responsible.

- Applications
App Control
- Private Community
- Community Home
Execution Control and dynamic policy assignment
mgorton May 18, 2022 09:28 PM
i_smith May 19, 2022 12:03 PM Best Answer
mgorton May 19, 2022 12:12 PM
1. execution control and dynamic policy assignment.

Just curious if its possible to assign policies based on AD OU location or security group within CB. We do the initial deploy via AD using scheduled tasks, however I'm looking for a way to dynamically adjust policies when AD OU's change for either computer or user. Thanks.
2. RE: Execution Control and dynamic policy assignment Best Answer

3. RE: Execution Control and dynamic policy assignment
Ah, thanks for that. I wasn't seeing that until I enabled the AD based policy management setting under System Configuration, so I just assumed there wasn't a way to do it. Thanks again, appreciate it.
New Best Answer
- Terms of Use

IMAGES
VIDEO
COMMENTS
Your job is to play the role of a malicious hacker and find and exploit the security bugs. In this assignment, you'll use both black-box hacking and white-box hacking. In black-box hacking, you try to find security bugs by experimenting with the application and manipulating input fields and URL parameters, trying to cause application errors ...
Lesson 1 introduces students to the basic concepts of cybersecurity and the "Security Mindset". This perspective frames the topics in the remaining lessons. Intended Audience: High school students or early undergraduates. Geared towards AP Computer Science Principles, but compatible with any introductory computer science course.
Security labs for a university course, "Information Security Management." Authors Dave Eargle and Anthony Vance. Security-Assignments.com. Labs Tutorials Projects In-class Activities Cases Books and Films Store Dark Mode. Security-Assignments.com. Content for an information security management course. ...
Lenders commonly take security over "choses in action" (such as debts or rights under contracts) by way of assignment. An assignment involves the transfer of either legal ownership (legal ...
Select a security assignment from the displayed list of assignments or search for a security assignment and select it. In the security assignment details region, click Manage Users. In Manage Users: Under Add User, search for a user and select the user. Under User, click the Delete icon to revoke the user from the assignment.
On Oct. 2, 2019, Worthy sent New Style a notice of its security interest and collateral assignment in respect of amounts owed to Checkmate. Such notice specifically referred to UCC §9-406 and ...
For a security assignment holder to have the right to look to enforce directly against the debtor (a 'legal assignment'), a number of legal hoops have to be jumped through. In addition to giving ...
You will complete three parts in this assignment, and each group member must contribute to all of the parts. Assignment Sections. Part 1: SQL Injection. Part 2: Cross-Site Request Forgery (CSRF) Part 3: Cross-Site Scripting (XSS) Part 4: Better Defenses Writeup.
Security Assignment means the Assignment of Sublease (Trust No. 116-A) dated as of July 10, 1995 between Lessor, as assignor, and Head Lessor, as assignee. Sample 1. Based on 4 documents. Security Assignment means a first assignment of the Borrower 's rights in respect of Insurances and all benefits thereof (including the right to receive ...
This document is from Thomson Reuters Practical Law, the legal know-how that goes beyond primary law and traditional legal research to give lawyers a better starting point. We provide standard documents, checklists, legal updates, how-to guides, and more. 650+ full-time experienced lawyer editors globally create and maintain timely, reliable ...
Assignment by way of security. A borrower's rights against third parties, such as the right to receive payment for debts on its own books, can be assigned to a third party as a way of selling those rights - this is an absolute, or direct, assignment. It is also possible to carry out an assignment by way of security over a borrower's choses in ...
In the security assignment details region, click Manage Users. In Manage Users: Under Add User, search for a user and select the user. Under User, click the Delete icon to revoke the user from the assignment. Click Save. As a security administrator, you need to map data security assignments to users to enable data level access.
security assignment, but it would not be a floating charge. Even if a security assignment is drafted as an absolute, notified assignment it could still be liable to be re-characterised as a floating charge if, in practice, the assignee too readily and frequently releases some of the assigned rights or their proceeds from its security at the
A security risk assessment is a process that helps organizations identify, analyze, and implement security controls in the workplace. It prevents vulnerabilities and threats from infiltrating the organization and protects physical and informational assets from unauthorized users.
Standard item with key as applied to this standard assignment over the given scope: AssignedStandardItem: description: description of the standardAssignment: string: displayName: display name of the standardAssignment: string: effect: expected effect of this assignment (Disable/Exempt/etc) string: expiresOn: Expiration date of this assignment ...
In summary, a cybersecurity assignment revolves around ensuring the security of internet-related devices and services from malicious attacks. This is achieved by identifying potential threats, developing a security strategy, implementing security measures, and monitoring and reviewing these measures to remain effective.
by Practical Law Finance. A standard form security assignment of contractual rights, created by a company incorporated in England and Wales in favour of a single corporate lender. This standard document creates a mortgage by way of assignment over the benefit of specified contracts entered into by the company and over the benefit of specified ...
By exploiting mass assignment vulnerabilities, a malicious actor could create multiple security problems including. Data tampering: Attackers can modify sensitive information in the database, such as password or account balance; Data theft: Attackers can gain access to confidential information stored in the database; Elevation of privilege: Attackers can manipulate the properties of an object ...
Security assignments sometimes use the term "absolute" to make clear they are intended to be legal assignments. However, the terminology used is not decisive. An assignment will not be "absolute" unless the third party can then deal with the assignee alone in respect of the assigned rights. The assignee owes an obligation to the assignor to ...
API6:2019 - Mass Assignment. Exploitation usually requires an understanding of the business logic, objects' relations, and the API structure. Exploitation of mass assignment is easier in APIs, since by design they expose the underlying implementation of the application along with the properties' names. Modern frameworks encourage developers ...
In this assignment there is a description about the cyber security as well as the importance and effectiveness of the cyber security. Nowadays each and every company uses network facilities in their business process. Basically, with the help of network facilities they can maintain or manage their business data as well as get proper idea about ...
1 Press the Win + R keys to open Run, type secpol.msc into Run, and click/tap on OK to open Local Security Policy. 2 Expand open Local Policies in the left pane of Local Security Policy, and click/tap on User Rights Assignment. (see screenshot below step 3) 3 In the right pane of User Rights Assignment, double click/tap on the policy (ex: "Shut down the system") you want to add users and/or ...
LO4 Manage organisational security. Assignment Brief and Guidance: 8. Assuming the role of External Security Analyst, you need to compile a report focusing on following elements to the board of EMC Cyber'; 1 Identify the CIA Triad concept and evaluate why and how the CIA Triad could be utilize to EMC Cyber in order to improve the organization ...
Completed Python assignment with proficiency, showcasing programming skills and understanding of Python concepts. Developed solutions to address specific requirements outlined in the assignment. Demonstrated ability to write clean and efficient code, adhering to best practices and principles of Python programming.
PER_MANAGER_HRCHY_DN / CF - This table is required for evaluating line manager security, head counts, and some of the flows in HCM are based on this table. It's also used for the assignment list dimensions for OTBI. PER_MANAGER_HRCHY_REPORTEES_DN is specific to OTBI reporting only and for assignment manager dimensions data.
Today, the Australian Signals Directorate's Australian Cyber Security Centre (ASD's ACSC), together with CISA, the Canadian Centre for Cyber Security (CCCS), the United Kingdom's National Cyber Security Centre (NCSC-UK), and the New Zealand National Cyber Security Centre (NCSC-NZ) are releasing the following guidance: Secure by Design Choosing Secure and Verifiable Technologies.
No one-size-fits-all formula works for every assignee or every assignment. The framework of security support needs to be adapted to fit the particular person or location. Considerations need to be made for the employee, their family, and the country they are moving to. Additional education and support may be necessary. Virtual Assignments:
Yes. Click on Rules- Policies (top menu) and then the mappings (tab) I have about 25 mappings in place and it works well. I use for automatic machine assignment to specific policies that have certain client required controls, or for a medium enforcement policy for helpdesk technician. Of course, you have to have the AD groups and OUs configured ...