Risk Management 101: Process, Examples, Strategies
Emily Villanueva
August 16, 2023
Effective risk management takes a proactive and preventative stance to risk, aiming to identify and then determine the appropriate response to the business and facilitate better decision-making. Many approaches to risk management focus on risk reduction, but it’s important to remember that risk management practices can also be applied to opportunities, assisting the organization with determining if that possibility is right for it.
Risk management as a discipline has evolved to the point that there are now common subsets and branches of risk management programs, from enterprise risk management (ERM) , to cybersecurity risk management, to operational risk management (ORM) , to supply chain risk management (SCRM) . With this evolution, standards organizations around the world, like the US’s National Institute of Standards and Technology (NIST) and the International Standards Organization (ISO) have developed and released their own best practice frameworks and guidance for businesses to apply to their risk management plan.
Companies that adopt and continuously improve their risk management programs can reap the benefits of improved decision-making, a higher probability of reaching goals and business objectives, and an augmented security posture. But, with risks proliferating and the many types of risks that face businesses today, how can an organization establish and optimize its risk management processes? This article will walk you through the fundamentals of risk management and offer some thoughts on how you can apply it to your organization.


What Are Risks?
We’ve been talking about risk management and how it has evolved, but it’s important to clearly define the concept of risk. Simply put, risks are the things that could go wrong with a given initiative, function, process, project, and so on. There are potential risks everywhere — when you get out of bed, there’s a risk that you’ll stub your toe and fall over, potentially injuring yourself (and your pride). Traveling often involves taking on some risks, like the chance that your plane will be delayed or your car runs out of gas and leave you stranded. Nevertheless, we choose to take on those risks, and may benefit from doing so.
Companies should think about risk in a similar way, not seeking simply to avoid risks, but to integrate risk considerations into day-to-day decision-making.
- What are the opportunities available to us?
- What could be gained from those opportunities?
- What is the business’s risk tolerance or risk appetite – that is, how much risk is the company willing to take on?
- How will this relate to or affect the organization’s goals and objectives?
- Are these opportunities aligned with business goals and objectives?
With that in mind, conversations about risks can progress by asking, “What could go wrong?” or “What if?” Within the business environment, identifying risks starts with key stakeholders and management, who first define the organization’s objectives. Then, with a risk management program in place, those objectives can be scrutinized for the risks associated with achieving them. Although many organizations focus their risk analysis around financial risks and risks that can affect a business’s bottom line, there are many types of risks that can affect an organization’s operations, reputation, or other areas.
Remember that risks are hypotheticals — they haven’t occurred or been “realized” yet. When we talk about the impact of risks, we’re always discussing the potential impact. Once a risk has been realized, it usually turns into an incident, problem, or issue that the company must address through their contingency plans and policies. Therefore, many risk management activities focus on risk avoidance, risk mitigation, or risk prevention.
What Different Types of Risks Are There?
There’s a vast landscape of potential risks that face modern organizations. Targeted risk management practices like ORM and SCRM have risen to address emerging areas of risk, with those disciplines focused on mitigating risks associated with operations and the supply chain. Specific risk management strategies designed to address new risks and existing risks have emerged from these facets of risk management, providing organizations and risk professionals with action plans and contingency plans tailored to unique problems and issues.
Common types of risks include: strategic, compliance, financial, operational, reputational, security, and quality risks.
Strategic Risk
Strategic risks are those risks that could have a potential impact on a company’s strategic objectives, business plan, and/or strategy. Adjustments to business objectives and strategy have a trickle-down effect to almost every function in the organization. Some events that could cause strategic risks to be realized are: major technological changes in the company, like switching to a new tech stack; large layoffs or reductions-in-force (RIFs); changes in leadership; competitive pressure; and legal changes.
Compliance Risk
Compliance risks materialize from regulatory and compliance requirements that businesses are subject to, like Sarbanes-Oxley for publicly-traded US companies, or GDPR for companies that handle personal information from the EU. The consequence or impact of noncompliance is generally a fine from the governing body of that regulation. These types of risks are realized when the organization does not maintain compliance with regulatory requirements, whether those requirements are environmental, financial, security-specific, or related to labor and civil laws.
Financial Risk
Financial risks are fairly self-explanatory — they have the possibility of affecting an organization’s profits. These types of risks often receive significant attention due to the potential impact on a company’s bottom line. Financial risks can be realized in many circumstances, like performing a financial transaction, compiling financial statements, developing new partnerships, or making new deals.
Operational Risk
Risks to operations, or operational risks, have the potential to disrupt daily operations involved with running a business. Needless to say, this can be a problematic scenario for organizations with employees unable to do their jobs, and with product delivery possibly delayed. Operational risks can materialize from internal or external sources — employee conduct, retention, technology failures, natural disasters, supply chain breakdowns — and many more.
Reputational Risk
Reputational risks are an interesting category. These risks look at a company’s standing in the public and in the media and identify what could impact its reputation. The advent of social media changed the reputation game quite a bit, giving consumers direct access to brands and businesses. Consumers and investors too are becoming more conscious about the companies they do business with and their impact on the environment, society, and civil rights. Reputational risks are realized when a company receives bad press or experiences a successful cyber attack or security breach; or any situation that causes the public to lose trust in an organization.
Security Risk
Security risks have to do with possible threats to your organization’s physical premises, as well as information systems security. Security breaches, data leaks, and other successful types of cyber attacks threaten the majority of businesses operating today. Security risks have become an area of risk that companies can’t ignore, and must safeguard against.
Quality Risk
Quality risks are specifically associated with the products or services that a company provides. Producing low-quality goods or services can cause an organization to lose customers, ultimately affecting revenue. These risks are realized when product quality drops for any reason — whether that’s technology changes, outages, employee errors, or supply chain disruptions.
Steps in the Risk Management Process
The six risk management process steps that we’ve outlined below will give you and your organization a starting point to implement or improve your risk management practices. In order, the risk management steps are:
- Risk identification
- Risk analysis or assessment
- Controls implementation
- Resource and budget allocation
- Risk mitigation
- Risk monitoring, reviewing, and reporting
If this is your organization’s first time setting up a risk management program, consider having a formal risk assessment completed by an experienced third party, with the goal of producing a risk register and prioritized recommendations on what activities to focus on first. Annual (or more frequent) risk assessments are usually required when pursuing compliance and security certifications, making them a valuable investment.
Step 1: Risk Identification
The first step in the risk management process is risk identification. This step takes into account the organization’s overarching goals and objectives, ideally through conversations with management and leadership. Identifying risks to company goals involves asking, “What could go wrong?” with the plans and activities aimed at meeting those goals. As an organization moves from macro-level risks to more specific function and process-related risks, risk teams should collaborate with critical stakeholders and process owners, gaining their insight into the risks that they foresee.
As risks are identified, they should be captured in formal documentation — most organizations do this through a risk register, which is a database of risks, risk owners, mitigation plans, and risk scores.

Step 2: Risk Analysis or Assessment
Analyzing risks, or assessing risks, involves looking at the likelihood that a risk will be realized, and the potential impact that risk would have on the organization if that risk were realized. By quantifying these on a three- or five-point scale, risk prioritization becomes simpler. Multiplying the risk’s likelihood score with the risk’s impact score generates the risk’s overall risk score. This value can then be compared to other risks for prioritization purposes.
The likelihood that a risk will be realized asks the risk assessor to consider how probable it would be for a risk to actually occur. Lower scores indicate less chances that the risk will materialize. Higher scores indicate more chances that the risk will occur.
Likelihood, on a 5×5 risk matrix, is broken out into:
- Highly Unlikely
- Highly Likely
The potential impact of a risk, should it be realized, asks the risk assessor to consider how the business would be affected if that risk occurred. Lower scores signal less impact to the organization, while higher scores indicate more significant impacts to the company.
Impact, on a 5×5 risk matrix, is broken out into:
- Negligible Impact
- Moderate Impact
- High Impact
- Catastrophic Impact
Risk assessment matrices help visualize the relationship between likelihood and impact, serving as a valuable tool in risk professionals’ arsenals.
Organizations can choose whether to employ a 5×5 risk matrix, as shown above, or a 3×3 risk matrix, which breaks likelihood, impact, and aggregate risk scores into low, moderate, and high categories.
Step 3: Controls Assessment and Implementation
Once risks have been identified and analyzed, controls that address or partially address those risks should be mapped. Any risks that don’t have associated controls, or that have controls that are inadequate to mitigate the risk, should have controls designed and implemented to do so.
Step 4: Resource and Budget Allocation
This step, the resource and budget allocation step, doesn’t get included in a lot of content about risk management. However, many businesses find themselves in a position where they have limited resources and funds to dedicate to risk management and remediation. Developing and implementing new controls and control processes is timely and costly; there’s usually a learning curve for employees to get used to changes in their workflow.
Using the risk register and corresponding risk scores, management can more easily allocate resources and budget to priority areas, with cost-effectiveness in mind. Each year, leadership should re-evaluate their resource allocation as part of annual risk lifecycle practices.
Step 5: Risk Mitigation
The risk mitigation step of risk management involves both coming up with the action plan for handling open risks, and then executing on that action plan. Mitigating risks successfully takes buy-in from various stakeholders. Due to the various types of risks that exist, each action plan may look vastly different between risks.
For example, vulnerabilities present in information systems pose a risk to data security and could result in a data breach. The action plan for mitigating this risk might involve automatically installing security patches for IT systems as soon as they are released and approved by the IT infrastructure manager. Another identified risk could be the possibility of cyber attacks resulting in data exfiltration or a security breach. The organization might decide that establishing security controls is not enough to mitigate that threat, and thus contract with an insurance company to cover off on cyber incidents. Two related security risks; two very different mitigation strategies.
One more note on risk mitigation — there are four generally accepted “treatment” strategies for risks. These four treatments are:
- Risk Acceptance: Risk thresholds are within acceptable tolerance, and the organization chooses to accept this risk.
- Risk Transfer : The organization chooses to transfer the risk or part of the risk to a third party provider or insurance company.
- Risk Avoidance : The organization chooses not to move forward with that risk and avoids incurring it.
- Risk Mitigation : The organization establishes an action plan for reducing or limiting risk to acceptable levels.
If an organization is not opting to mitigate a risk, and instead chooses to accept, transfer, or avoid the risk, these details should still be captured in the risk register, as they may need to be revisited in future risk management cycles.
Step 6: Risk Monitoring, Reviewing, and Reporting
The last step in the risk management lifecycle is monitoring risks, reviewing the organization’s risk posture, and reporting on risk management activities. Risks should be monitored on a regular basis to detect any changes to risk scoring, mitigation plans, or owners. Regular risk assessments can help organizations continue to monitor their risk posture. Having a risk committee or similar committee meet on a regular basis, such as quarterly, integrates risk management activities into scheduled operations, and ensures that risks undergo continuous monitoring. These committee meetings also provide a mechanism for reporting risk management matters to senior management and the board, as well as affected stakeholders.
As an organization reviews and monitors its risks and mitigation efforts, it should apply any lessons learned and use past experiences to improve future risk management plans.
Examples of Risk Management Strategies
Depending on your company’s industry, the types of risks it faces, and its objectives, you may need to employ many different risk management strategies to adequately handle the possibilities that your organization encounters.
Some examples of risk management strategies include leveraging existing frameworks and best practices, minimum viable product (MVP) development, contingency planning, root cause analysis and lessons learned, built-in buffers, risk-reward analysis, and third-party risk assessments.
Leverage Existing Frameworks and Best Practices
Risk management professionals need not go it alone. There are several standards organizations and committees that have developed risk management frameworks, guidance, and approaches that business teams can leverage and adapt for their own company.
Some of the more popular risk management frameworks out there include:
- ISO 31000 Family : The International Standards Organization’s guidance on risk management.
- NIST Risk Management Framework (RMF) : The National Institute of Standards and Technology has released risk management guidance compatible with their Cybersecurity Framework (CSF).
- COSO Enterprise Risk Management (ERM) : The Committee of Sponsoring Organizations’ enterprise risk management guidance.
Minimum Viable Product (MVP) Development
This approach to product development involves developing core features and delivering those to the customer, then assessing response and adjusting development accordingly. Taking an MVP path reduces the likelihood of financial and project risks, like excessive spend or project delays by simplifying the product and decreasing development time.
Contingency Planning
Developing contingency plans for significant incidents and disaster events are a great way for businesses to prepare for worst-case scenarios. These plans should account for response and recovery. Contingency plans specific to physical sites or systems help mitigate the risk of employee injury and outages.
Root Cause Analysis and Lessons Learned
Sometimes, experience is the best teacher. When an incident occurs or a risk is realized, risk management processes should include some kind of root cause analysis that provides insights into what can be done better next time. These lessons learned, integrated with risk management practices, can streamline and optimize response to similar risks or incidents.
Built-In Buffers
Applicable to discrete projects, building in buffers in the form of time, resources, and funds can be another viable strategy to mitigate risks. As you may know, projects can get derailed very easily, going out of scope, over budget, or past the timeline. Whether a project team can successfully navigate project risks spells the success or failure of the project. By building in some buffers, project teams can set expectations appropriately and account for the possibility that project risks may come to fruition.
Risk-Reward Analysis
In a risk-reward analysis, companies and project teams weigh the possibility of something going wrong with the potential benefits of an opportunity or initiative. This analysis can be done by looking at historical data, doing research about the opportunity, and drawing on lessons learned. Sometimes the risk of an initiative outweighs the reward; sometimes the potential reward outweighs the risk. At other times, it’s unclear whether the risk is worth the potential reward or not. Still, a simple risk-reward analysis can keep organizations from bad investments and bad deals.
Third-Party Risk Assessments
Another strategy teams can employ as part of their risk management plan is to conduct periodic third-party risk assessments. In this method, a company would contract with a third party experienced in conducting risk assessments, and have them perform one (or more) for the organization. Third-party risk assessments can be immensely helpful for the new risk management team or for a mature risk management team that wants a new perspective on their program.
Generally, third-party risk assessments result in a report of risks, findings, and recommendations. In some cases, a third-party provider may also be able to help draft or provide input into your risk register. As external resources, third-party risk assessors can bring their experience and opinions to your organization, leading to insights and discoveries that may not have been found without an independent set of eyes.
Components of an Effective Risk Management Plan
An effective risk management plan has buy-in from leadership and key stakeholders; applies the risk management steps; has good documentation; and is actionable. Buy-in from management often determines whether a risk management function is successful or not, since risk management requires resources to conduct risk assessments, risk identification, risk mitigation, and so on. Without leadership buy-in, risk management teams may end up just going through the motions without the ability to make an impact. Risk management plans should be integrated into organizational strategy, and without stakeholder buy-in, that typically does not happen.
Applying the risk management methodology is another key component of an effective plan. That means following the six steps outlined above should be incorporated into a company’s risk management lifecycle. Identifying and analyzing risks, establishing controls, allocating resources, conducting mitigation, and monitoring and reporting on findings form the foundations of good risk management.
Good documentation is another cornerstone of effective risk management. Without a risk register recording all of a company’s identified risks and accompanying scores and mitigation strategies, there would be little for a risk team to act on. Maintaining and updating the risk register should be a priority for the risk team — risk management software can help here, providing users with a dashboard and collaboration mechanism.
Last but not least, an effective risk management plan needs to be actionable. Any activities that need to be completed for mitigating risks or establishing controls, should be feasible for the organization and allocated resources. An organization can come up with the best possible, best practice risk management plan, but find it completely unactionable because they don’t have the capabilities, technology, funds, and/or personnel to do so. It’s all well and good to recommend that cybersecurity risks be mitigated by setting up a 24/7 continuous monitoring Security Operations Center (SOC), but if your company only has one IT person on staff, that may not be a feasible action plan.
Executing on an effective risk management plan necessitates having the right people, processes, and technology in place. Sometimes the challenges involved with running a good risk management program are mundane — such as disconnects in communication, poor version control, and multiple risk registers floating around. Risk management software can provide your organization with a unified view of the company’s risks, a repository for storing and updating key documentation like a risk register, and a space to collaborate virtually with colleagues to check on risk mitigation efforts or coordinate on risk assessments. Get started building your ideal risk management plan today!

Emily Villanueva, MBA, is a Senior Manager of Product Solutions at AuditBoard. Emily joined AuditBoard from Grant Thornton, where she provided consulting services specializing in SOX compliance, internal audit, and risk management. She also spent 5 years in the insurance industry specializing in SOX/ICFR, internal audits, and operational compliance. Connect with Emily on LinkedIn .
Related Articles

- Twitter icon
- Facebook icon
- LinkedIn icon
7 Steps to Write a Risk Management Plan For Your Next Project (With Free Template!)
🎁 Bonus Material: Free Risk Management Template

5 Steps to Find Your Definition of Done (With Examples and Workflows)

3 Steps to Minimize Workplace Distraction And Take Back Control of your Focus

The Essential Guide to Writing a Project Communication Plan: What It Is and Why You (Actually) Need One
Working with planio, see how our customers use planio.
Introduction to Risk Assessment in Project Management
Project Management Institute’s (PMI) inclusion of risk management skills in multiple PMI certifications indicates the importance of risk across industries and in all projects. The risk management process includes risk identification and risk assessment. During an assessment, the project manager uses standard risk tools and quality data to help the team better avert later problems, manage the project cost, and keep project work on schedule. Risk assessment is the process by which the identified risks are systematically analyzed to determine their probability of occurrence and the potential impact of that occurrence.
On this page:
What is a risk assessment?
What are risk assessment pmp and risk reassessment pmp, when is a risk assessment needed, why is a risk assessment important, example use of risk assessment: hurricane impacting town, what inputs are needed for a risk assessment, what is a risk data quality assessment pmp, what outputs does a risk assessment generate, how to create a risk assessment, risk assessment matrix, risk assessment best practices, risk assessment pmp and risk reassessment pmp.
Get Your Comprehensive Guide to Risk Management
Learn how to manage risk in every project.
Project teams use risk assessment, a qualitative measure using risk data and the parameters of probability and impact, to identify, categorize, prioritize, and manage risks before they happen.
A “risk reassessment” is the work done to update the original risk assessment due to changes in the project or overall risk management efforts.
For the original and subsequent assessments, the quality of data used to determine the impact directly correlates to the accuracy of the risk assessment and resulting decisions.
Project Management Professional (PMP)® credential holders have shown their knowledge of a risk assessment and their understanding of the high cost of a failure to do a risk assessment. For the PMP certification exam, students need to know the importance of a risk assessment and how to use a probability and impact scoring matrix to help inform the priority of the risk.
Within the PMP exam context, “risk assessment PMP” and “risk reassessment PMP” are informal terms referring to taking identified risks and assessing them using qualitative data, such as the probability of occurrence, to determine the potential impact. From that, project managers determine the risk score, which is an input to subsequent risk response activities.
Risk identification should happen early in the project , closely followed by the risk assessment. Project teams should conduct risk reassessment throughout the life of a project. Updating the risk register is a good reminder to update the corresponding risk assessment. The project’s scope and risk management plan will inform how frequently the reassessment should be conducted (projects of bigger scope should have more reassessments; similarly, smaller scope requires fewer reassessments).
Performing a risk assessment is critical to ensuring the success of a project because it puts the project team in a state of preparedness. When done with verified tools and quality inputs, risk assessment may take time but can prevent problems from negative risks and enable opportunities from positive risks. As shared in the PMI conference paper Risk Assessments—developing the right assessment for your organization , “The best project organizations are those who realize that a risk assessment template is a valuable asset in managing the organization’s bottom line.” Risk assessment connects to managing cost, timelines, and quality.
For an example of how a risk assessment can be used, we use the example of a small municipality located on the east coast of North Carolina. The coastal town has been impacted by natural disasters in the form of hurricanes several times in the past fifty years. A hurricane is a storm that starts in the ocean and moves inland, causing all levels of flooding, electrical storms, and damaging winds. The National Weather Service provides annual forecasts of which geographic regions are predicted to have hurricanes, as well as the number of occurrences and strength of hurricanes.
The town manager (“project manager”) and the town administration (“project team”) know a hurricane will happen but not when or how strong it may be. In the risk category of weather events, the project manager and project team identify the risk type of hurricane storm. Then the project team identifies specific potential risks, such as flooding that may cause building damage. The team assesses each risk in terms of probability (or how likely it is to occur), the impact if it occurs, and the probability-impact score (weighing the significance of the risk on the project). The information is captured in a risk assessment matrix as part of the project management and risk management documentation.
For example, they do a risk assessment after the project manager and team identify the risk of water damage to downtown buildings due to hurricane-induced flooding. The team uses standard tools to determine the probability of that specific risk (flooding) and the impact if it occurs (water damage to buildings). The project team uses verified data, like National Weather Service hurricane projections, for probability estimates. For the potential impact, the project team uses cost and quality data like town records to determine what could happen to town property. The data and risk scoring are organized in the project risk assessment matrix and communicated to stakeholders.
Continuing our example of the identified risk of water damage to ground floors, if the assessment indicates the risk is highly likely to occur with a high impact of damage, it will have a higher risk score. That can mean more time invested in risk response planning (such as securing funding to buy and store sandbag materials during flooding to reduce the impact of water damage on buildings). The risk response plan would likely include purchasing sandbag materials before a hurricane, storing them in an accessible space, and training the town staff to set up the sandbags to protect critical buildings when a hurricane is imminent. The cost of buying and storing sandbag materials to protect the buildings is much lower than the cost of fully repairing water-damaged buildings.
In this risk example, the project team:
- determined the appropriate risk categories (natural disasters)
- determined the types within the category (hurricane storms)
- identified a risk event (hurricane bringing flooding to downtown buildings),
- assessed the impact of that risk (flooding damages ground floors),
- assessed the probability of the impact (flooding may be higher or lower but always occurs with hurricanes),
- documented the risk information, including risk scores in the risk assessment matrix,
- communicated the risk assessment results to the team and stakeholders, and then
- used the risk assessment matrix as an input for risk response planning (making sandbag materials available when needed and training people to set them up).
With this example, you should see the risk assessment allows the project team to identify, categorize, prioritize, and mitigate/avoid/exploit risks prior to their occurrence. A risk assessment is a proactive approach in which the risk is identified and assessed to manage cost, reduce negative impact, and protect the project (in this example, town buildings).
A risk assessment should be customized to fit the project context. Standard risk assessment inputs include:
- Project management plan
- Risk management plan
- Risk assessment methodology
- Risk parameter definitions
- Risk tolerance levels
- Risk probability and impact matrix template
- Risk assessment scale (what criteria are used to determine if the risk score is high, mid, or low)
- Risk assessment matrix template
Project managers and project management students use what is informally referred to as the “assessment of other risk parameters PMP” to tailor their risk assessment to a specific project. While probability and impact values are used in all risk assessments, additional parameters, like cost or schedule, can be standalone matrices.
Risk assessment is a qualitative assessment. Therefore, risk data quality (sometimes referred to as “risk data quality assessment PMP”) always impacts the risk assessment quality. A risk data audit helps ensure the quality of data used in the risk assessment. Project managers may use experts or previous project documentation as part of the risk data quality assessment to ensure the accuracy of the overall risk assessment.
The risk assessment outputs are part of the overall project and risk management documentation. A risk assessment can generate the following:
- Project Management Plan updates
- Project document updates
- Risk Management Plan updates
- Risk Register updates
- Risk Response Plan updates
Risk assessment should occur throughout the project. With each iteration, known as a risk reassessment, the risk documentation should be updated accordingly.
For the PMP exam, students need to know the importance of a risk assessment and how to use a probability and impact scoring matrix to help inform the priority of the risk. Project Managers and PMP credential holders should know the seven steps to risk assessment.
1. Identify applicable risk types and organize them
You cannot assess risk if you have not identified it. Begin your risk assessment with risk identification. With your project team, identify potential scenarios that could harm your project. Risks can be of any size and with internal or external triggers. Your team may identify risks that include computer viruses, manufacturing defects, natural disasters, or shipping delays. Each risk is identified and documented in the risk register. The risk may be organized by different factors (internal or external triggers, for example) or by categories (environmental, regulatory, technology, or staffing, for example).
2. Determine how these risks will be qualified and quantified
With risks identified and organized, the project manager should conduct a risk assessment. Each risk must be qualified and quantified. The project manager will use a probability and impact matrix to document the probability of each risk and the impact if it does happen. Remember, the quality of the data used in the assessment impacts its accuracy.
3. Determine your organization’s risk tolerance
Every organization has a risk tolerance level, with variances due to the type of risk, the specific stakeholders of a project, and the scope of the project. Additionally, there are industries with negligible risk tolerance (such as health care) and others with an acceptance of some level of risk (like software development). While every organization has a risk tolerance level, so the project manager should get stakeholder input to determine risk tolerance for each project.
4. Determine the final output format of the risk assessment
Within the risk management activities, determine during the risk planning process how the risk assessment output should be documented and communicated. Spreadsheet programs are often used for the ease of organizing large data sets. However, a company may have risk assessment output requirements, such as storing it on a secure server or capturing it in a shareable file, determining the output format. How the risk assessment output is documented is important because it determines how the information is made available to the project team and stakeholders.
5. Create a plan to maximize the risk assessments applicability to every project
Within a risk assessment and the resulting risk response plan, project managers have a wealth of knowledge that can protect the active project and future projects.
Project managers should have a plan to document the risk assessment, the result of risk responses applied to risks that occur, and the risk assessment matrices with the appropriate risk parameters. Maintaining a consistent and detailed project documentation archive helps ensure a project’s lessons learned are available to other project managers with similar projects, which can reduce the impact of negative risks. The plan should include documentation format requirements, how assessment documentation will be accessed, and how the assessment (and reassessments) will be communicated to the project team and stakeholders.
6. Create a final risk assessment that is flexible and scalable
Knowing the project manager and team will be doing reassessments throughout the project as part of risk reassessment, the process must be flexible and scalable. You may have to add risks throughout the project or incorporate other criteria to ensure the accuracy of the probability and impact scores. Additionally, the risk assessment should work for projects of different scopes. The risk assessment should be flexible enough to remain aligned with project changes and scalable enough to be used in multiple projects.
7. Determine the process to update the risk assessment
PMP credential holders know the importance of risk assessment and reassessment in managing the project cost. Without a process to update risk assessments, the project is vulnerable when risks occur. Changes are inevitable, and a risk assessment that is not current is not effective. Project managers should have a consistent risk assessment update process within their overall risk management activities.
Risk management documentation, such as the risk assessment matrix, is part of the overall project management documentation. The risk matrix documents at least four core areas for each identified risk: (1) risk name, (2) probability, (3) impact, and (4) risk level/ranking. The risk assessment also includes the calculated overall Project Risk score (the project’s probability-impact, or PI, score). The risk assessment matrix is an output of the Risk Assessment process and an input to the Risk Response process.
In a risk assessment matrix, each identified risk is listed along with its corresponding information.:
RISK CATEGORY
- Risk category : from a standardized list of risk categories (e.g., technology, natural disaster, regulations, transportation, etc.), the ones that most closely align with the project are used; not all projects have risks in all categories; therefore, each project will have a different combination of risk categories in its matrix
PROBABILITY
- Probability criteria : used to assign the probability values for a risk category; criteria should come from a standardized list but customized for each project
- Probability (“P”) score : a value given to each risk driven by the probability criteria; the matrix’s score scale will state the parameters for the minimum and maximum value of a P score; the project manager and project team use data and criteria to assign the P score to each risk
- Impact criteria : used to assign the impact values for a risk category; criteria should come from a standardized list but customized for each project
- Impact (“I”) score : a value given to each risk driven by the impact criteria; the matrix’s score scale will state the parameters for the minimum and maximum value of an I score; the project manager and project team use data and criteria to assign the I score to each risk
PROBABILITY AND IMPACT VALUES
- Probability-to-Impact (“PI”) score : the Probability score multiplied by the Impact score results in the PI score; the PI score is the overall risk assessment score; the PI score is used to rank all project risks by lowest probability and impact to highest, so resources are assigned accordingly
- Total Project Risk : all PI scores are added, and then that sum is divided by the quantity (total number of risks) of risks to determine the average; the project’s PI average value of PI scores is the Total Project Risk value.
Probability and impact are integral data points for risk assessment. Project risk tailoring occurs within the specifics of the risk categories, probability criteria, and impact criteria.
Risk Assessment Matrix Example
Project Manager Kestel’s PMI conference paper “ Risk assessments—developing the risk assessment for your organization ” includes an example risk assessment matrix:
From the completed risk assessment matrix, the project manager communicates the total Project Risk score to the team and stakeholders. Communication is part of risk assessment and helps ensure commonly understood terms are used for standardized risk assessment processes.
The risk matrix template ensures key data is consistently defined and included in the project documentation. For a risk matrix , project managers work with the project team and stakeholders to determine the specific risk criteria and refine the criteria for probability and impact. The format of the risk matrix should be determined early in the project and use company standards for project tools when available. The risk matrix should be stored with other project documentation, along with all risk reassessments for a project.
Project managers should complete the risk assessment as part of their risk management activities for all projects. Best practices for risk assessment include:
- Risk assessments should use quality data.
- Risk assessments incorporate expertise and knowledge from the project team and stakeholders.
- Risk data should undergo an audit to determine quality.
- Risk reassessment is conducted frequently throughout the life of a project.
- Risk assessments should use tailored and scalable tools.
- Risk assessment results, including the overall project risk score, are communicated to the team and stakeholders.
Project Managers should:
- lead the risk assessment efforts using standard tools
- customize the risk assessment matrix to the specific needs of the project,
- document the probability and impact of each risk,
- use standard data and terms for risk audit efforts, and
- communicate risk assessment progress and results to the project team and stakeholders.
Project managers should customize the risk assessment criteria to the project type. For example, you would not assess the risk of a particular weather event occurring using the criteria for the probability of manufacturing defects.
Additionally, project managers should use organizational templates and project management office (PMO) standards when available in their company. Customization of a project’s risk assessment should be balanced against the need for standards to contribute to knowledge sharing. No single tool will ensure quality assessment for all projects, but there are standards shared by all projects.
To prepare for the PMP exam, students need to know the importance of risk assessment and how to use a probability and impact scoring matrix to help inform the priority of the risk. Students should understand that a risk assessment is a tool to help manage the project’s cost by closely monitoring highly probable and high (negative or positive) impact risks.
American billionaire fund manager and philanthropist Bruce Kovner is credited with saying, “Risk management is the most important thing to be well understood.” A project manager with the PMP credential has demonstrated knowledge of risk assessment and the role it serves within risk management. Remember these components of creating a risk assessment:
- identify applicable risk types and organize them
- determine how risks will be qualified and quantified
- determine your organization’s risk tolerance
- determine the final output format of the risk assessment
- create a plan to maximize the risk assessment’s applicability to every project
- create a final risk assessment that is flexible and scalable
- determine a process to update the risk assessment
Project Managers managing risk using a scalable risk assessment template and standard processes consistently have successful projects. In addition to earning PMI’s Project Management Professional (PMP) certification, you may continue your certification journey by pursuing the PMI Risk Management Professional (PMP-RMP)® certification to advance your risk project management skills further.
- Megan Bell #molongui-disabled-link What is a Project Schedule Network Diagram?
- Megan Bell #molongui-disabled-link Scheduling Methodology: Build & Control Your Project Schedule
- Megan Bell #molongui-disabled-link Schedule Baseline: How to Create, Use, and Optimize
- Megan Bell #molongui-disabled-link How to Use Agile in Project Management as a PMP® Credential Holder
Popular Courses
PMP Exam Preparation
PMI-ACP Exam Preparation
Lean Six Sigma Green Belt Training
CBAP Exam Preparation
Corporate Training
Project Management Training
Agile Training
Read Our Blog
Press Release
Connect With Us
PMI, PMBOK, PMP, CAPM, PMI-ACP, PMI-RMP, PMI-SP, PMI-PBA, The PMI TALENT TRIANGLE and the PMI Talent Triangle logo, and the PMI Authorized Training Partner logo are registered marks of the Project Management Institute, Inc. | PMI ATP Provider ID #3348 | ITIL ® is a registered trademark of AXELOS Limited. The Swirl logo™ is a trademark of AXELOS Limited | IIBA ® , BABOK ® Guide and Business Analysis Body of Knowledge ® are registered trademarks owned by International Institute of Business Analysis. CBAP ® , CCBA ® , IIBA ® -AAC, IIBA ® -CBDA, and ECBA™ are registered certification marks owned by International Institute of Business Analysis. | BRMP ® is a registered trademark of Business Relationship Management Institute.
- Contact sales
Start free trial
The Risk Management Process in Project Management

When you start the planning process for a project, one of the first things you need to think about is: what can go wrong? It sounds negative, but pragmatic project managers know this type of thinking is preventative. Issues will inevitably come up, and you need a mitigation strategy in place to know how to manage risks when project planning .
But how do you work towards resolving the unknown? It sounds like a philosophical paradox, but don’t worry—there are practical steps you can take. In this article, we’ll discuss strategies that let you get a glimpse at potential risks, so you can identify and track risks on your project.
What Is Risk Management on Projects?
Project risk management is the process of identifying, analyzing and responding to any risk that arises over the life cycle of a project to help the project remain on track and meet its goal. Risk management isn’t reactive only; it should be part of the planning process to figure out the risk that might happen in the project and how to control that risk if it in fact occurs.
A risk is anything that could potentially impact your project’s timeline, performance or budget. Risks are potentialities, and in a project management context, if they become realities, they then become classified as “issues” that must be addressed with a risk response plan . So risk management, then, is the process of identifying, categorizing, prioritizing and planning for risks before they become issues.
Risk management can mean different things on different types of projects. On large-scale projects, risk management strategies might include extensive detailed planning for each risk to ensure mitigation strategies are in place if project issues arise. For smaller projects, risk management might mean a simple, prioritized list of high, medium and low-priority risks.
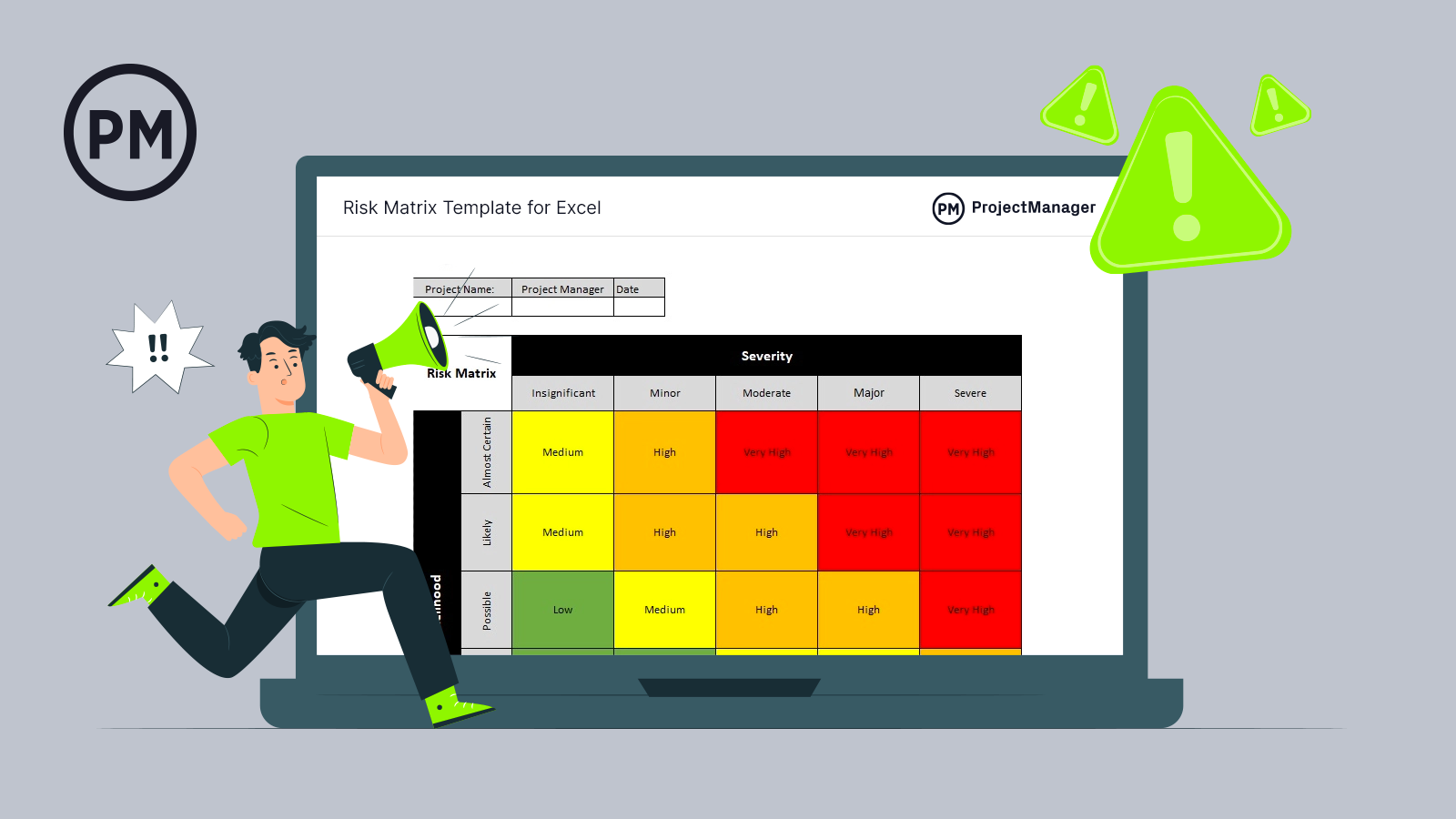
Get your free
Risk Matrix Template
Use this free Risk Matrix Template for Excel to manage your projects better.
How to Manage Project Risk
To begin managing risk, it’s crucial to start with a clear and precise definition of what your project has been tasked to deliver. In other words, write a very detailed project charter , with your project vision, objectives, scope and deliverables. This way risks can be identified at every stage of the project. Then you’ll want to engage your team early in identifying any and all risks.
Don’t be afraid to get more than just your team involved to identify and prioritize risks, too. Many project managers simply email their project team and ask to send them things they think might go wrong on the project. But to better plot project risk, you should get the entire project team, your client’s representatives, and vendors into a room together and do a risk identification session.
With every risk you define, you’ll want to log it somewhere—using a risk tracking template helps you prioritize the level of risk. Then, create a risk management plan to capture the negative and positive impacts of the project and what actions you will take to deal with them. You’ll want to set up regular meetings to monitor risk while your project is ongoing. Transparency is critical.
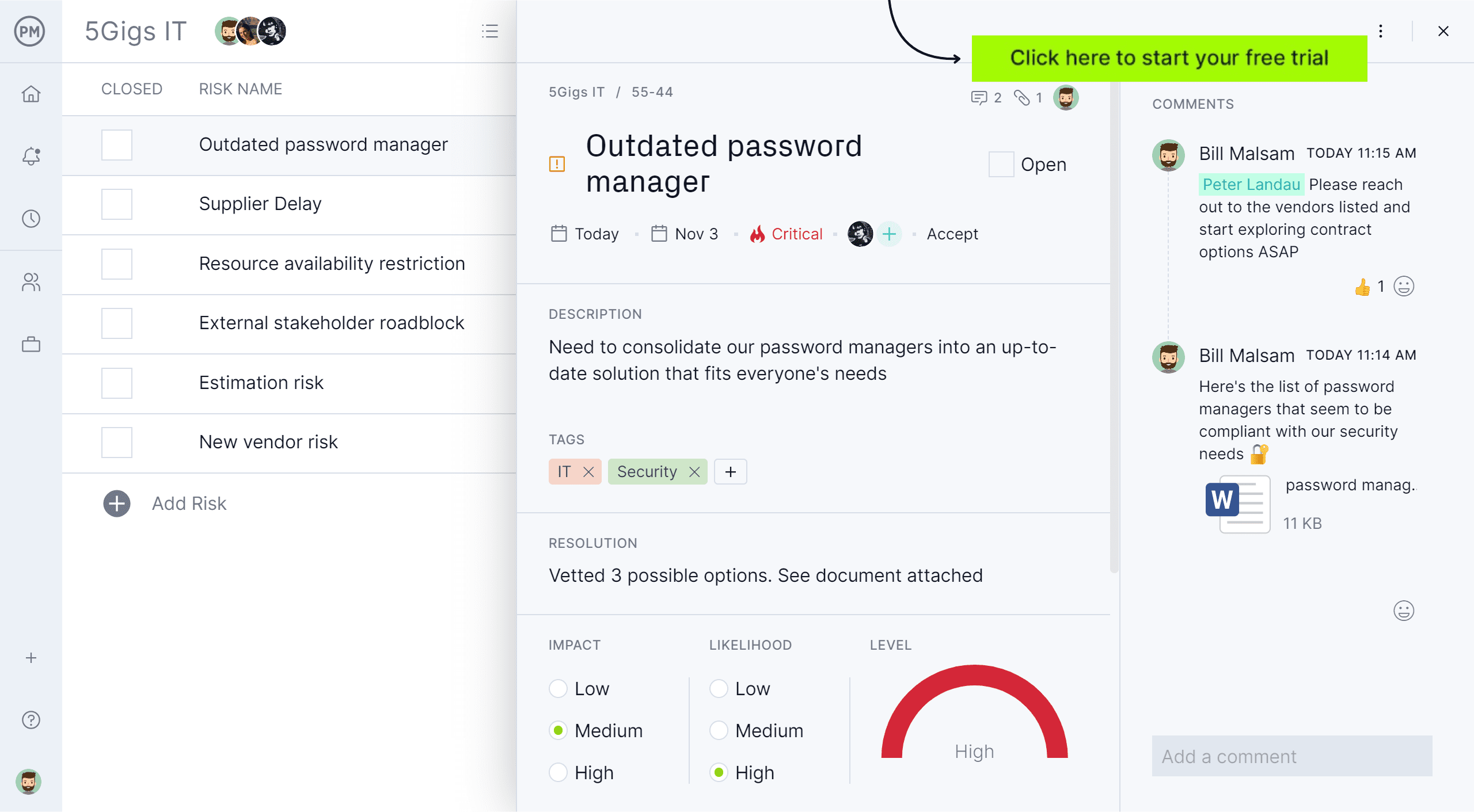
Project management software can help you keep track of risk. ProjectManager is online software that helps you identify risks, track them and calculate their impact. With our Risk view, you can make a risk list with your team and stay on top of all the risks within your project. Write a description, add tags, identify a resolution, mark impact and likelihood, even see a risk matrix—all in one place. Get started today with a free trial.
What Is Positive Risk In Project Management?
Not all risk is created equally. Risk can be either positive or negative, though most people assume risks are inherently the latter. Where negative risk implies something unwanted that has the potential to irreparably damage a project, positive risks are opportunities that can affect the project in beneficial ways.
Negative risks are part of your risk management plan, just as positive risks should be, but the difference is in approach. You manage and account for known negative risks to neuter their impact, but positive risks can also be managed to take full advantage of them.
There are many examples of positive risks in projects: you could complete the project early; you could acquire more customers than you accounted for; you could imagine how a delay in shipping might open up a potential window for better marketing opportunities, etc. It’s important to note, though, that these definitions are not etched in stone. Positive risk can quickly turn to negative risk and vice versa, so you must be sure to plan for all eventualities with your team.
Managing Risk Throughout the Organization
Can your organization also improve by adopting risk management into its daily routine? Yes! Building a risk management protocol into your organization’s culture by creating a consistent set of risk management tools and templates, with training, can reduce overhead over time. That way, each time you start a new project, it won’t be like having to reinvent the wheel.
Things such as your organization’s records and history are an archive of knowledge that can help you learn from that experience when approaching risk in a new project. Also, by adopting the attitudes and values of your organization to become more aware of risk, your organization can develop a risk culture . With improved governance comes better planning, strategy, policy and decisions.
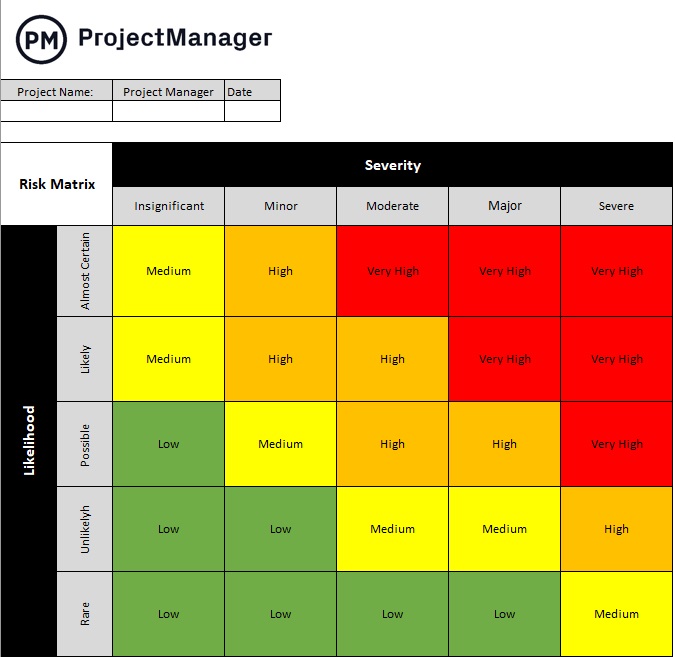
Free Risk Matrix Template
To manage project risks throughout your organization, it’s important to create a risk matrix. A risk matrix is going to help you organize your risks by severity and likelihood, so you can stay on top of potential issues that threaten the greatest impact. Try this free risk matrix template for Excel so you and your team can organize project risks.
6 Steps in the Risk Management Process
So, how do you handle something as seemingly elusive as project risk management? You make a risk management plan. It’s all about the process. Turn disadvantages into an advantage by following these six steps.
Identify the Risk
You can’t resolve a risk if you don’t know what it is. There are many ways to identify risk. As you do go through this step, you’ll want to collect the data in a risk register .
One way is brainstorming with your team, colleagues or stakeholders. Find the individuals with relevant experience and set up interviews so you can gather the information you’ll need to both identify and resolve the risks. Think of the many things that can go wrong. Note them. Do the same with historical data on past projects. Now your list of potential risks has grown.
Make sure the risks are rooted in the cause of a problem. Basically, drill down to the root cause to see if the risk is one that will have the kind of impact on your project that needs identifying. When trying to minimize risk, it’s good to trust your intuition. This can point you to unlikely scenarios that you just assume couldn’t happen. Use a risk breakdown structure process to weed out risks from non-risks.
Analyze the Risk
Analyzing risk is hard. There is never enough information you can gather. Of course, a lot of that data is complex, but most industries have best practices, which can help you with your risk analysis . You might be surprised to discover that your company already has a framework for this process.
When you assess project risk you can ultimately and proactively address many impacts, such as avoiding potential litigation, addressing regulatory issues, complying with new legislation, reducing your exposure and minimizing impact.
So, how do you analyze risk in your project? Through qualitative and quantitative risk analysis, you can determine how the risk is going to impact your schedule and budget.
Project management software helps you analyze risk by monitoring your project. ProjectManager takes that one step further with real-time dashboards that display live data. Unlike other software tools, you don’t have to set up our dashboard. It’s ready to give you a high-level view of your project from the get-go. We calculate the live date and then display it for you in easy-to-read graphs and charts. Catch issues faster as you monitor time, costs and more.
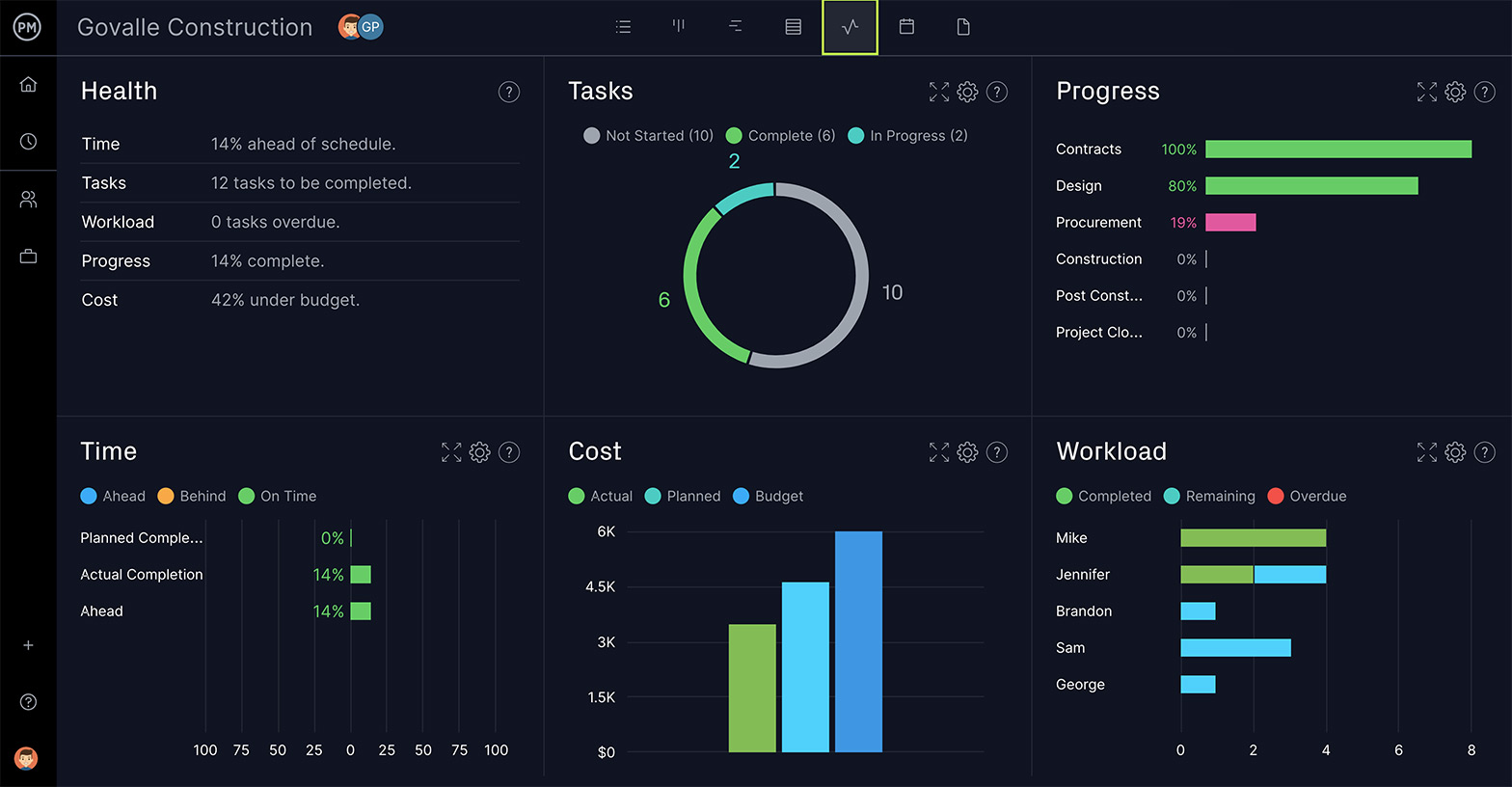
Prioritize Risks & Issues
Not all risks are created equally. You need to evaluate the risk to know what resources you’re going to assemble towards resolving it when and if it occurs.
Having a large list of risks can be daunting. But you can manage this by simply categorizing risks as high, medium or low. Now there’s a horizon line and you can see the risk in context. With this perspective, you can begin to plan for how and when you’ll address these risks. Then, if risks become issues, it’s advisable to keep an issue log so you can keep track of each of them and implement corrective actions.
Some risks are going to require immediate attention. These are the risks that can derail your project. Failure isn’t an option. Other risks are important, but perhaps do not threaten the success of your project. You can act accordingly. Then there are those risks that have little to no impact on the overall project’s schedule and budget . Some of these low-priority risks might be important, but not enough to waste time on.
Assign an Owner to the Risk
All your hard work identifying and evaluating risk is for naught if you don’t assign someone to oversee the risk. In fact, this is something that you should do when listing the risks. Who is the person who is responsible for that risk, identifying it when and if it should occur and then leading the work toward resolving it?
That determination is up to you. There might be a team member who is more skilled or experienced in the risk. Then that person should lead the charge to resolve it. Or it might just be an arbitrary choice. Of course, it’s better to assign the task to the right person, but equally important in making sure that every risk has a person responsible for it.
Think about it. If you don’t give each risk a person tasked with watching out for it, and then dealing with resolving it when and if it should arise, you’re opening yourself up to more risk. It’s one thing to identify risk, but if you don’t manage it then you’re not protecting the project.
Respond to the Risk
Now the rubber hits the road. You’ve found a risk. All that planning you’ve done is going to be put to use. First, you need to know if this is a positive or negative risk. Is it something you could exploit for the betterment of the project? If not you need to deploy a risk mitigation strategy .
A risk mitigation strategy is simply a contingency plan to minimize the impact of a project risk. You then act on the risk by how you prioritize it. You have communications with the risk owner and, together, decide on which of the plans you created to implement to resolve the risk.
Monitor the Risk
You can’t just set forces against risk without tracking the progress of that initiative. That’s where the monitoring comes in. Whoever owns the risk will be responsible for tracking its progress towards resolution. However, you’ll need to stay updated to have an accurate picture of the project’s overall progress to identify and monitor new risks.
You’ll want to set up a series of project meetings to manage the risks. Make sure you’ve already decided on the means of communication to do this. It’s best to have various channels dedicated to communication.
Whatever you choose to do, remember to always be transparent. It’s best if everyone in the project knows what is going on, so they know what to be on the lookout for and help manage the process.
In the video below, Jennifer Bridges, professional project manager (PMP) dives deeper into the steps in the risk management process.
Risk Management Templates
We’ve created dozens of free project management templates for Excel and Word to help you manage projects. Here are some of our risk management templates to help you as you go through the process of identifying, analyzing, prioritizing and responding to risks.
Risk Register Template
A risk register is a risk management document that allows project managers to identify and keep track of potential project risks. Using a risk register to list down project risks is one of the first steps in the risk management process and one of the most important because it sets the stage for future risk management activities.
A risk matrix is a project management tool that allows project managers to analyze the likelihood and potential impact of project risks. This helps them prioritize project risks and build a risk mitigation plan to respond to those risks if they were to occur.
Managing Risk With ProjectManager
Using a risk-tracking template is a start, but to gain even more control over your project risks you’ll want to use project management software. ProjectManager has a number of tools including risk management that let you address risks at every phase of a project.
Make an Online Risk Register
Identify and track all the risks for your project in one place. Unlike other project management software, you can manage risks alongside your project rather than in a separate tool. Set due dates, mark priority, identify resolutions and more.

Gantt Charts for Risk Management Plans
Use our award-winning Gantt charts to create detailed risk management plans to prevent risks from becoming issues. Schedule, assign and monitor project tasks with full visibility. Gantt charts allow team members add comments and files to their assigned tasks, so all the communication happens on the project level—in real time.
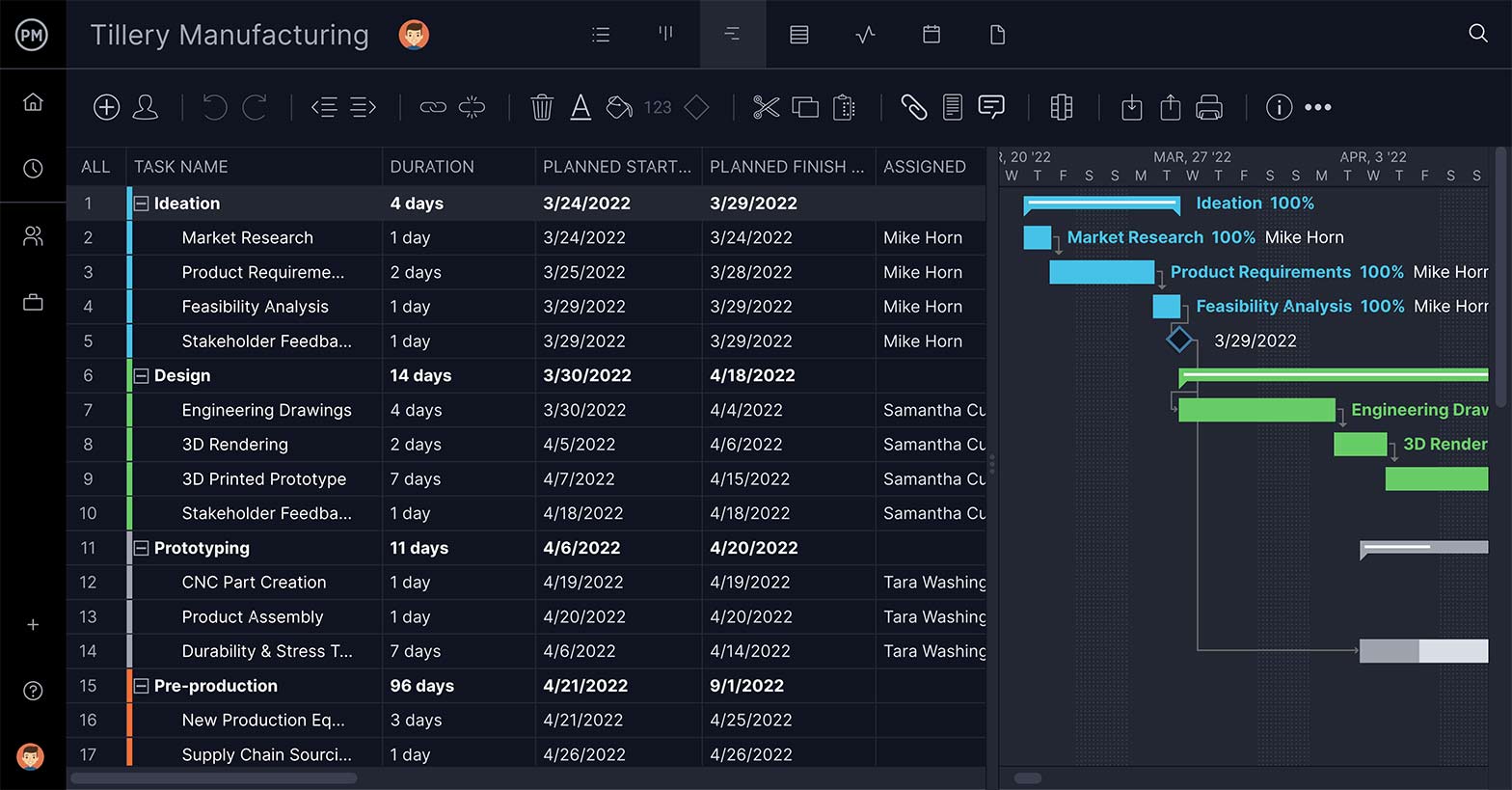
Risk management is complicated. A risk register or template is a good start, but you’re going to want robust project management software to facilitate the process of risk management. ProjectManager is an online tool that fosters the collaborative environment you need to get risks resolved, as well as provides real-time information, so you’re always acting on accurate data. Try it yourself and see, take this free 30-day trial.

Deliver your projects on time and on budget
Start planning your projects.
Risk management is the process of identifying, assessing and controlling financial, legal, strategic and security risks to an organization’s capital and earnings. These threats , or risks, could stem from a wide variety of sources, including financial uncertainty, legal liabilities, strategic management errors, accidents and natural disasters.
If an unforeseen event catches your organization unaware, the impact could be minor, such as a small impact on your overhead costs. In a worst-case scenario, though, it could be catastrophic and have serious ramifications, such as a significant financial burden or even the closure of your business.
To reduce risk, an organization needs to apply resources to minimize, monitor and control the impact of negative events while maximizing positive events. A consistent, systemic and integrated approach to risk management can help determine how best to identify, manage and mitigate significant risks.
Get insights to better manage the risk of a data breach with the latest Cost of a Data Breach report.
Register for the X-Force Threat Intelligence Index
At the broadest level, risk management is a system of people, processes and technology that enables an organization to establish objectives in line with values and risks.
A successful risk assessment program must meet legal, contractual, internal, social and ethical goals, as well as monitor new technology-related regulations. By focusing attention on risk and committing the necessary resources to control and mitigate risk, a business protects itself from uncertainty, reduce costs and increase the likelihood of business continuity and success.
Three important steps of the risk management process are risk identification, risk analysis and assessment, and risk mitigation and monitoring.
Risk identification is the process of identifying and assessing threats to an organization, its operations and its workforce. For example, risk identification can include assessing IT security threats such as malware and ransomware, accidents, natural disasters and other potentially harmful events that could disrupt business operations.
Risk analysis involves establishing the probability that a risk event might occur and the potential outcome of each event. Risk evaluation compares the magnitude of each risk and ranks them according to prominence and consequence.
Risk mitigation refers to the process of planning and developing methods and options to reduce threats to project objectives. A project team might implement risk mitigation strategies to identify, monitor and evaluate risks and consequences inherent to completing a specific project, such as new product creation. Risk mitigation also includes the actions put into place to deal with issues and effects of those issues regarding a project.
Risk management is a nonstop process that adapts and changes over time. Repeating and continually monitoring the processes can help assure maximum coverage of known and unknown risks.
There are five commonly accepted strategies for addressing risk. The process begins with an initial consideration of risk avoidance then proceeds to 3 additional avenues of addressing risk (transfer, spreading and reduction). Ideally, these three avenues are employed in concert with one another as part of a comprehensive strategy. Some residual risk may remain.
Avoidance is a method for mitigating risk by not participating in activities that may negatively affect the organization. Not making an investment or starting a product line are examples of such activities as they avoid the risk of loss.
This method of risk management attempts to minimize the loss, rather than completely eliminate it. While accepting the risk, it stays focused on keeping the loss contained and preventing it from spreading. An example of this in health insurance is preventive care.
When risks are shared, the possibility of loss is transferred from the individual to the group. A corporation is a good example of risk sharing—several investors pool their capital and each only bears a portion of the risk that the enterprise may fail.
Contractually transferring a risk to a third-party, such as, insurance to cover possible property damage or injury shifts the risks associated with the property from the owner to the insurance company.
After all risk sharing, risk transfer and risk reduction measures have been implemented, some risk will remain since it is virtually impossible to eliminate all risk (except through risk avoidance). This is called residual risk.
Risk management standards set out a specific set of strategic processes that start with the objectives of an organization and intend to identify risks and promote the mitigation of risks through best practice.
Standards are often designed by agencies who are working together to promote common goals, to help to ensure high-quality risk management processes. For example, the ISO 31 000 standard on risk management is an international standard that provides principles and guidelines for effective risk management.
While adopting a risk management standard has its advantages, it is not without challenges. The new standard might not easily fit into what you are doing already, so you could have to introduce new ways of working. And the standards might need customizing to your industry or business.
Manage risk from changing market conditions, evolving regulations or encumbered operations while increasing effectiveness and efficiency.
Speed insights, cut infrastructure costs and increase efficiency for risk-aware decisions with IBM RegTech.
Simplify how you manage risk and regulatory compliance with a unified GRC platform fueled by AI and all your data.
Better manage your risks, compliance and governance by teaming with our security consultants.
Identify IT security vulnerabilities to help mitigate business risks.
Create a smarter security framework to manage the full threat lifecycle.
Understand your cybersecurity landscape and prioritize initiatives together with senior IBM security architects and consultants in a no-cost, virtual or in-person, 3-hour design thinking session.
Understand your cyberattack risks with a global view of the threat landscape.
Discover how a governance, risk, and compliance (GRC) framework helps an organization align its information technology with business objectives, while managing risk and meeting regulatory compliance requirements.
Find out how threat management is used by cybersecurity professionals to prevent cyber attacks, detect cyber threats and respond to security incidents.
Explore financial impacts and security measures that can help your organization avoid a data breach, or in the event of a breach, mitigate costs.
Keep up to date with the latest strategies from our expert writers.
Protect your business from potential risks and strive towards compliance with regulations as you explore the world of proper governance.
Cybersecurity threats are becoming more advanced, more persistent and are demanding more effort by security analysts to sift through countless alerts and incidents. IBM Security QRadar SIEM helps you remediate threats faster while maintaining your bottom line. QRadar SIEM prioritizes high-fidelity alerts to help you catch threats that others miss.
- Product overview
- All features
- App integrations
CAPABILITIES
- project icon Project management
- Project views
- Custom fields
- Status updates
- goal icon Goals and reporting
- Reporting dashboards
- workflow icon Workflows and automation
- portfolio icon Resource management
- Time tracking
- my-task icon Admin and security
- Admin console
- asana-intelligence icon Asana Intelligence
- list icon Personal
- premium icon Starter
- briefcase icon Advanced
- Goal management
- Organizational planning
- Campaign management
- Creative production
- Marketing strategic planning
- Request tracking
- Resource planning
- Project intake
- View all uses arrow-right icon
- Project plans
- Team goals & objectives
- Team continuity
- Meeting agenda
- View all templates arrow-right icon
- Work management resources Discover best practices, watch webinars, get insights
- What's new Learn about the latest and greatest from Asana
- Customer stories See how the world's best organizations drive work innovation with Asana
- Help Center Get lots of tips, tricks, and advice to get the most from Asana
- Asana Academy Sign up for interactive courses and webinars to learn Asana
- Developers Learn more about building apps on the Asana platform
- Community programs Connect with and learn from Asana customers around the world
- Events Find out about upcoming events near you
- Partners Learn more about our partner programs
- Support Need help? Contact the Asana support team
- Asana for nonprofits Get more information on our nonprofit discount program, and apply.
Featured Reads
- Project planning |
- Risk matrix template: How to assess ris ...
Risk matrix template: How to assess risk for project success (with examples)

A risk matrix analyzes project risks based on likelihood and severity. Once you map your risks, you can calculate overall impact and prioritize risks accordingly. In this piece, you’ll learn how to create a risk matrix template and how to use the information from this analysis tool to develop a comprehensive risk management plan.
Risks are a part of any project, and there’s no surefire way to know which ones will occur and when. Sometimes, you'll get through an entire project without experiencing a single hiccup. Other times, you’ll feel like all the odds are against you. Without the help of a crystal ball, the only way to prevent project risks is to proactively prepare for them.
A risk matrix helps you analyze risk by assigning each event as high, medium, or low impact on a scale of one through 25. Once you assess the severity and likelihood of each risk, you’ll prioritize your risks and prepare for them accordingly. In this article, we’ll explain how to create a risk matrix template and offer helpful tools for turning your results into action.
What is a risk matrix in project management?
Types of risks.
As part of the process, you’ll need to brainstorm a list of risks to chart in your risk matrix. The risks you may face will likely fall into these categories:
Strategic risk : Strategic risks involve performance or decision errors, such as choosing the wrong vendor or software for a project.
Operational risk : Operational risks are process errors or procedural mistakes, like poor planning or a lack of communication among teams.
Financial risk : Financial risk can involve various events that cause a loss of company profit, including market changes, lawsuits, or competitors.
Technical risk: Technical risk may include anything related to company technology, such as a security breach, power outage, loss of internet, or damage to property.
External risk: External risks are out of your control, like floods, fires, natural disasters, or pandemics.
There are other risk categories to consider depending on your work industry. For example, if you have government clients, then you also want to brainstorm legal risks. If your company sells a physical product, you may have to think about manufacturing risks.
How to create a risk matrix template
When creating your risk matrix template, you’ll first identify your scale of severity, which you’ll place in the columns of your matrix. The scale of severity measures how severe the consequences will be for each risk. In a five-by-five matrix, there are five levels in your scale of severity.
Negligible (1): The risk will have little consequences if it occurs.
Minor (2): The consequences of the risk will be easy to manage.
Moderate (3): The consequences of the risk will take time to mitigate.
Major (4): The consequences of this risk will be significant and may cause long-term damage.
Catastrophic (5): The consequences of this risk will be detrimental and may be hard to recover from.
You’ll then identify your scale of likelihood, which you’ll place in the rows of your risk matrix template. The scale of likelihood identifies the probability of each risk occurring.
Very likely (5): You can be pretty sure this risk will occur at some point in time.
Probable (4): There’s a good chance this risk will occur.
Possible (3): This risk could happen, but it might not. This risk has split odds.
Not likely (2): There’s a good chance this risk won’t occur.
Very unlikely (1): It’s a long shot that this risk will occur.
When you place a risk in your matrix based on its likelihood and severity, you’ll find the level of risk impact. The risk impact is both color-coded from green to red and rated on a one through 25 scale.
Low (1-6): Low-risk events likely won’t happen, and if they do, they won’t cause significant consequences for your project or company. You can label these as low priority in your risk management plan .
Medium (7-12): Medium-risk events are a nuisance and can cause project hiccups, but if you take action during project planning to prevent and mitigate these risks, you’ll set yourself up for project success. You shouldn’t ignore these risks, but they also don’t need to be a top priority.
High (13-25): High-risk events can derail your project if you don’t keep them top of mind during project planning. Because these risks are likely to happen and have serious consequences, these are most important in your risk management plan.
![risk management in assignment [inline illustration] risk matrix criteria (infographic)](https://assets.asana.biz/transform/6e112071-56ef-4646-ad85-b474220851f0/inline-project-planning-risk-matrix-template-2-2x?io=transform:fill,width:2560&format=webp)
You don’t have to stick to the labels above for your risk matrix template if they don’t feel right for your company or project. You can customize the size and terminology of your matrix to your needs.
How to use a risk matrix
Once you’ve created a risk matrix, you can use it as a comprehensive analysis tool. The best part about a risk matrix template is that you don’t need to change it for every project. Once you have one, you can reuse it and share it with others.
![risk management in assignment [inline illustration] 5 steps to use a risk matrix (infographic)](https://assets.asana.biz/transform/9bc214f5-661e-4696-854a-f6f9ec87502f/inline-project-planning-risk-matrix-template-3-2x?io=transform:fill,width:2560&format=webp)
1. Identify project risks
You’ll need a list of potential risks to make use of your risk matrix. In this step, you’ll determine what risks may affect the specific project you’re working on.
To come up with relevant risks for your project, you’ll need to understand your project scope and objectives. This includes the project’s:
Constraints
Using your project scope as a guide, think of risky situations that might affect your project. If you’re not sure where to start, try brainstorming techniques like mind mapping or starbursting to list as many risks as you can under each risk type.
2. Determine severity of risks
When you created your risk matrix, you defined the criteria for your risk severity and likelihood. Now that you have a list of project risks, categorize them using the matrix criteria. Start with the scale of severity and go through each risk you’ve listed. Consider the following questions:
What is the most negative outcome that could come from this risk?
What are the worst damages that could occur from this risk?
How hard will it be to recover from this risk?
Which of the five severity levels most closely matches this risk?
You may not always have the perspective you need to know how severe the consequences of a risk are. In that case, work with other project stakeholders to determine the potential risk impact.
3. Identify likelihood of risks
Once you’ve defined the severity of each risk, you’ve completed half of the risk analysis equation. Next, identify the likelihood of each risk. To do this, consider the following questions:
Has this risk occurred before and, if so, how often?
Are there risks similar to this one that have occurred?
Can this risk occur, and if so, how likely is it to occur?
Team collaboration is also crucial in this step because you may not have a good idea of similar risks that have occurred in past projects. Make sure to reference past projects and analyze the probability of each risk with your team in order to create a more accurate mitigation plan.
4. Calculate risk impact
The last part of your risk analysis equation is to calculate risk impact. The equation you’ll use is:
Likelihood x severity = risk impact
Place each risk in your matrix based on its likelihood and severity, then multiply the numbers in the row and column where it lands to find the level of risk impact. For example, if you think the risk of a data breach is of major severity (4) and probable likelihood (4), you’d multiply four by four to get a risk impact of 16. This is considered a high-risk impact.
5. Prioritize risks and take action
You should now have a risk impact level on a scale of 1–25 for each risk you’ve identified. With these number values, it’s easier to determine which risks are of top priority. When you have risks with the same risk impact score, it will be up to you and your team to determine which risk to prioritize. Risks with equal risk impact may require equal attention as you create your action plan.
Your risk response plan should include steps to prevent risk and ways to mitigate risk if unfortunate events occur. Because so much goes into project planning, the best strategy when tackling risks may be to divide and conquer.
Risk assessment matrix template
The size of your risk matrix template determines how closely you can analyze your project risks. A larger risk matrix template offers more room on the risk impact spectrum, while a smaller risk matrix template keeps your risk impact rating simpler and less subjective.
Each square in your matrix represents a risk level of likelihood and severity, so you shouldn’t make your risk matrix smaller than three squares in length and width.
A five-by-five risk matrix is ideal so you can further analyze each risk. Once you chart your risks along your finished risk matrix template, this matrix creates a larger color spectrum to see the impact of each risk as high, medium, or low.
The example below shows a five by five risk matrix template.
![risk management in assignment [inline illustration] Risk matrix (example)](https://assets.asana.biz/transform/17e35ed4-e05d-41a4-bb25-6e7cec43f468/inline-project-planning-risk-matrix-template-1-2x?io=transform:fill,width:2560&format=webp)
You can download a free risk matrix template using the link below. Use this template to chart your project risks and determine their overall level of risk impact.
Pair your risk matrix template with a work management tool
You can use the same risk matrix template when measuring risk across multiple projects. However, it’s important to remember that the risks you face will evolve. The environment changes, technology becomes smarter, and the workplace grows. Every project faces unique risks, and you must reevaluate these risks year after year.
When you pair your risk matrix template with work management software , you can use past data to inform current processes. Asana helps you share the results of your risk matrix with stakeholders so you can collaborate on a risk management plan. Once you have a solid plan in place, you can monitor your team in real-time as they take action.
Related resources
How to use a feasibility study in project management
How to track utilization rate and drive team profitability
How to accomplish big things with long-term goals
Smooth product launches are simpler than you think
The Ultimate List of Visual Risk Management Techniques
Updated on: 1 March 2023
Whether it’s a multinational corporation or startup, risks cannot be avoided. It’s a part of any new or routine endeavor.
The best way to reduce the negative impact risks may have on your business is to incorporate risk management techniques into your business structure.
In this post, we will discuss visual risk management techniques that you can use during each stage of your risk management strategy.
What is Risk Management?
Risk management is a process in which risks are identified and controlled proactively. It allows businesses to improve their chances of success by minimizing threats and maximizing opportunities.
Risk management is essential to a business as it helps prevent financial losses and increase revenue. Other benefits of risk management include,
- Help to identify projects that might be headed toward trouble and apply solutions
- Help to prepare for unexpected threats beforehand
- Help to provide enough data to make better decisions regarding projects/ events
- Help to improve communication between stakeholders and project teams
- Help teams stay more focused on the key outcomes
Key stages of a risk management process are identifying risks, analyzing risks and planning to mitigate risks. These are detailed below along with risk management techniques you can use.
Identify Risks
The risk management process begins with identifying risks in advance once you have set the goal. Identifying risks should be done early in a project and shouldn’t be done in the middle of or during a project, as it may be too late.
Identifying risks can be done in 2 ways
- By identifying root causes and the impact they may have
- By identifying the essential functions the company must perform to reach a goal and identifying how they can fail
The following visual risk management methods can be used to identify risks beforehand.
1. Decision Tree Diagram
Decision trees are used to make decisions when you are faced with multiple options. It allows you to assess the values of outcomes and possibilities of achieving them. This, in turn, helps make a better decision.
How to use it
Step 1: Identify decisions and prepare a decision tree diagram based on decisions, costs, and rewards of uncertain options available to you.
Step 2: Figure out the probability of a risk occurring and assign it
Step 3: In this step you have to identify the monetary value of the risk, or in other words how much it would cost you if the risk is to occur
Step 4: Calculate the Expected Monetary Value (EMV) of each decision path by multiplying probability and impact
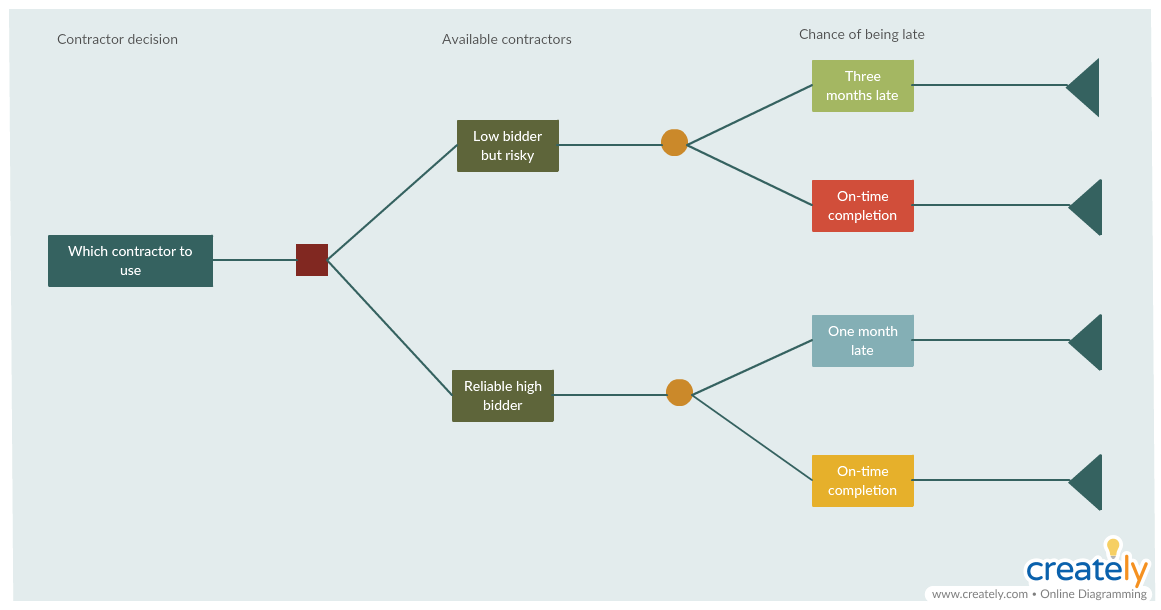
Decision Tree Analysis Template (Click on the template to edit it online)
2. Influence Diagram
An influence diagram is used to represent the summary of information of a decision tree. It shows variables that are known and unknown when making a decision and the relationships that exist among them.
Rectangles indicate decisions, ovals represent uncertainties and values or the required outputs are indicated by diamonds. The influence each variable have on the other is represented by arrows.
Step 1: Identify the decisions to be made to reach your objective
Step 2: Consider the risks and performance factors that may have an influence on achieving your objective.
Step 3: Recognize secondary factors that affect uncertainty associated with the performance factors.
Step 4: Identify second-order risk factors that can influence secondary factors.
Step 5: Continue to figure out what factors influence uncertainty until all key risks are identified.
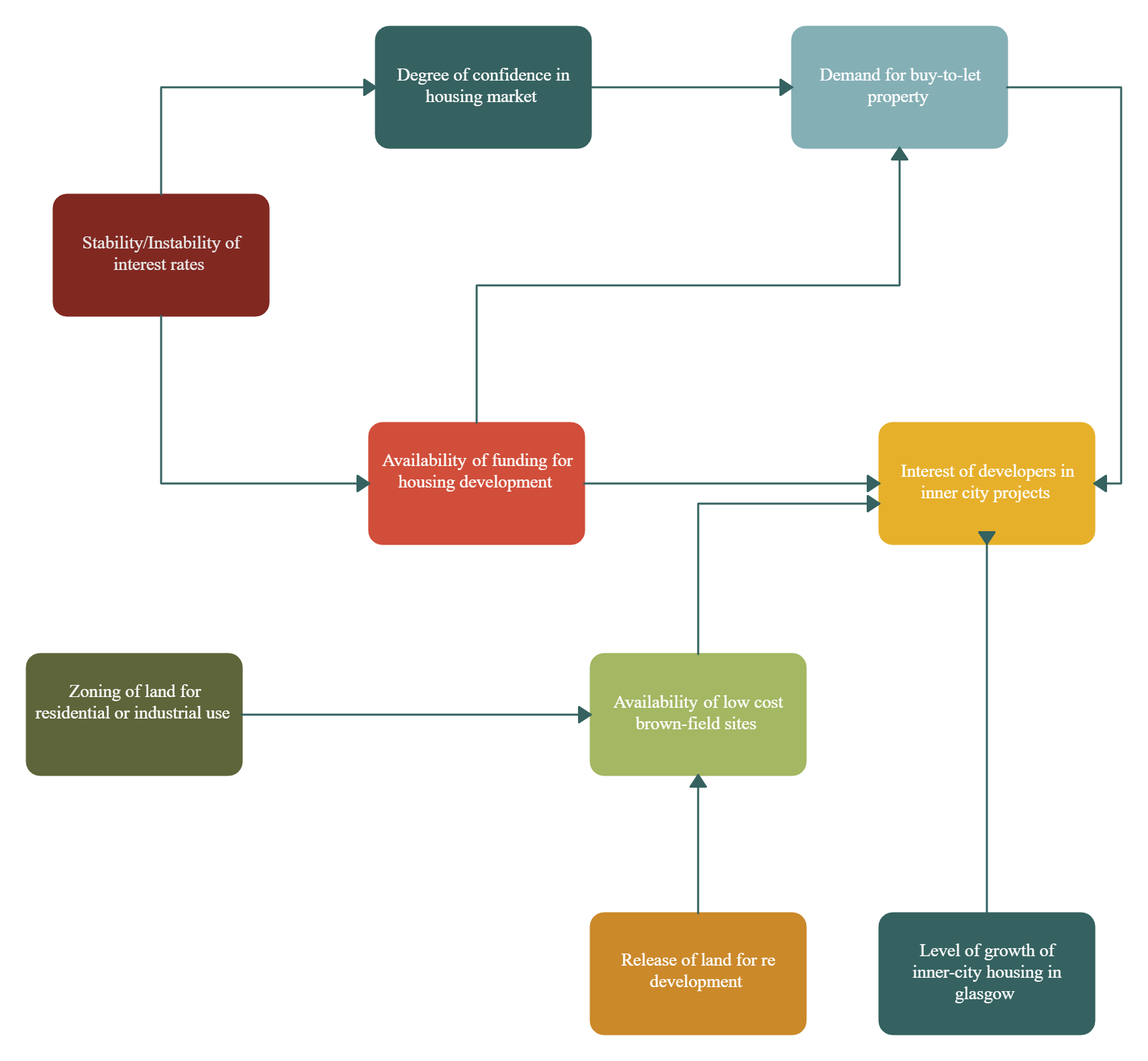
Click on the template to edit it online
3. SWOT analysis
Whether you are planning a new project or developing a new process, a SWOT analysis can help you get insight into any risks that may occur. It helps you identify the Strengths, Weaknesses, Threats and Opportunities associated with the event.
To learn how to use a SWOT analysis refer to our article SWOT Analysis: What, Why and How to Use Them Effectively .
4. Fishbone Diagram
Also known as the Ishikawa diagram and the cause and effect diagram, the fishbone diagram is used to break apart a problem and identify the root causes behind it. It works backward as it helps identify the causes of a certain effect.
Our Ultimate Guide to Fishbone Diagrams covers how to use a fishbone diagram in depth.
Fishbone Diagram Template (Click on the template to edit it online)
5. Process Maps
Process maps help visualize the major steps and relationships between them in a process. By having the people who actually perform it outline the process using a process map , you can check for its accuracy. This also helps identify bottlenecks and blockers in advance.
Step 1: Identify the team you need to map – whether its a new process or a process being redesigned
Step 2: Bring together everyone who is involved in performing/ developing the process and brainstorm all information related to the process, such as inputs, outputs etc.
Step 3: Take the steps you identified and put them in a sequential order
Step 4: Draw a map that shows the current state of the process
Step 5: Identify the bottlenecks and flaws in your process
Check out The Easy Guide to Process Mapping to learn about what process maps are, process map symbols, types of process maps, etc.
Process Map for Risk Management (Click on the template to edit online)
Analyze the Identified Risk
Once you have identified the risks, the next step is to assess the risks to see what kind of an impact they have on your business and current projects. By correctly analyzing the risks, you will be able to prioritize as to which risk has the highest impact on your business.
Analyzing risks can be done in two ways
- Qualitative risk analysis – here the risks are analyzed based on the likelihood of them occurring and the impact they may have on projects, business etc.
- Quantitative risk analysis – quantifies the possible outcomes and evaluate the probability of achieving objects
Following are a few risk management methods you can use to help during the analysis phase of the risk management process.
1. Risk Probability and Impact Matrix
This is a tool that can be used to do a qualitative risk assessment. It helps to evaluate the relative impact (high or low) of a risk and the probability of its occurrence (high or low).
According to the risk probability and impact matrix , there are two dimensions to risks
- Probability- The probability of a risk occurring can range from 0% to below 100%, therefore it is an event that may occur.
- Impact – A risk always has a negative impact
In the risk probability and impact matrix, you can rate potential risks based on these two dimensions. Based on where the risk is placed on the matrix, you can prioritize it as
- Low impact – low probability
- Low impact – high probability
- High impact – low probability
- High impact – high probability
While the risks on the bottom left corner can often be disregarded, the risks placed on the top right corner should be given top priority.
Risk Probability and Impact Matrix (Click on the template to edit it online)
2. Pareto Chart
Pareto diagrams are a great way to identify which problems should be prioritized based on the cumulative effect it has on a system. While the length of the bars represents the frequency or cost (time or money), the bars are arranged with the longest bars to the right and shortest bars to the right. This way it depicts which situation is the most significant.
Step 1: Identify the categories you want to use to group the items, and the measurements (i.e. frequency, cost, time etc.)
Step 2: Decide the period of time (an hour, week or day etc.) you want the Pareto chart to cover
Step 3: Collect the data along with the category and subtotal the measurements for each category
Step 4: Determine the right scale for the measurements and mark the scale on the left side of the chart
Step 5: Label bars for each category, placing the tallest at the far left
Step 6: Calculate the percentage for each category
Step 7 : Calculate and draw cumulative sums
Pareto Chart for Risk Management (Click on the template to edit online)

3. Fault Tree Analysis
The fault tree analysis helps to identify the probabilities of various outcomes from given faults and failures. The fault tree analysis helps to identify the likelihood of an event occurring by visualizing a certain event at a top and the conditions causing that event.
Step 1: Identify the fault/ failure that should be analyzed
Step 2: List down the immediate or direct causes of the fault. Thoroughly examine each step until the root causes are analyzed
Step 3: Once you apply the data to the fault tree, use it to do the evaluation
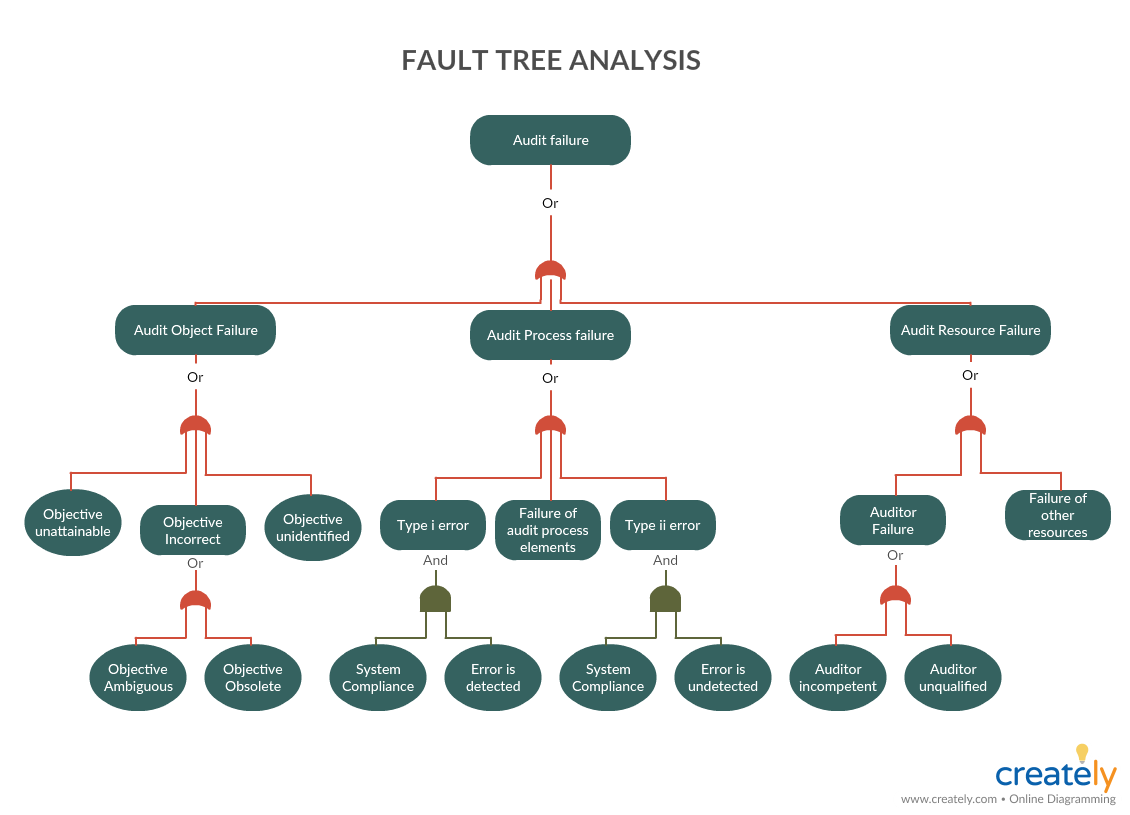
Fault Tree Analysis Diagram (Click on the template to edit it online)
Planning to Avoid Future Risks
In the planning phase of the risk management cycle , you need to pay attention to mitigating risks by finding solutions and controlling them. Starting from the risks that have the most severe impact on your projects or organization, find out how to minimize their effect.
1. Futures wheel diagram
Futures wheel is a tool that you can use to identify direct and indirect results of a certain trend, event or decision.
Step 1: Identify the change. This could be a problem or a potential risk.
Step 2: Brainstorm possible consequences of the trend.
Step 3: Brainstorm the secondary or “second-order” consequences related to the “first-order” consequences you identified earlier. You can continue to expand the diagram by adding several layers.
Step 4: Once the futures wheel is complete you can get an overview of the direct and indirect consequences of the change you want to implement.
Step 5: Take the negative consequences and identify possible actions you can take to control them.
Futures Wheel Template (Click on the template to edit it online)
2. Process Decision Program Chart
The process decision program chart (PDPC) help you look into what might go wrong in a plan that is under development. You can use the chart to alter your plan in order to prevent the problem from occurring and to prepare a contingency plan to mitigate the risk.
Step 1: Create a tree diagram of the plan, listing the objectives, main activities and the tasks that should be completed under each activity.
Step 2: Take the tasks on the third level and brainstorm what could go wrong
Step 3: If the consequences of the problems identified earlier are insignificant leave them out. Add the significant problems related to each task on the tree diagram as a fourth level.
Step 4: Come up with countermeasures for each problem, and add them as a fifth level to the diagram
Step 5: Consider how practical each countermeasure is in terms of time, resources, cost etc. You can use an X to mark the impractical solution and an O to mark those that are practical.
Refer to this article on PDPC to learn more about the tool.
Process Decision Program Chart – PDPC (Click on the template to edit it online)
3. Risk-Reward Analysis
Risk reward analysis is a tool you can use to evaluate the risk and reward profile of different options.
Step 1: List down the options and possible risks related to them
Step 2: Plot the risks and rewards on the risk-reward analysis chart
Step 3: While some options may have a positive risk-reward profile, take time to see whether you should spend time on mitigating risks of other options as well.
Step 4: Compare each option against one another to identify the best option for you
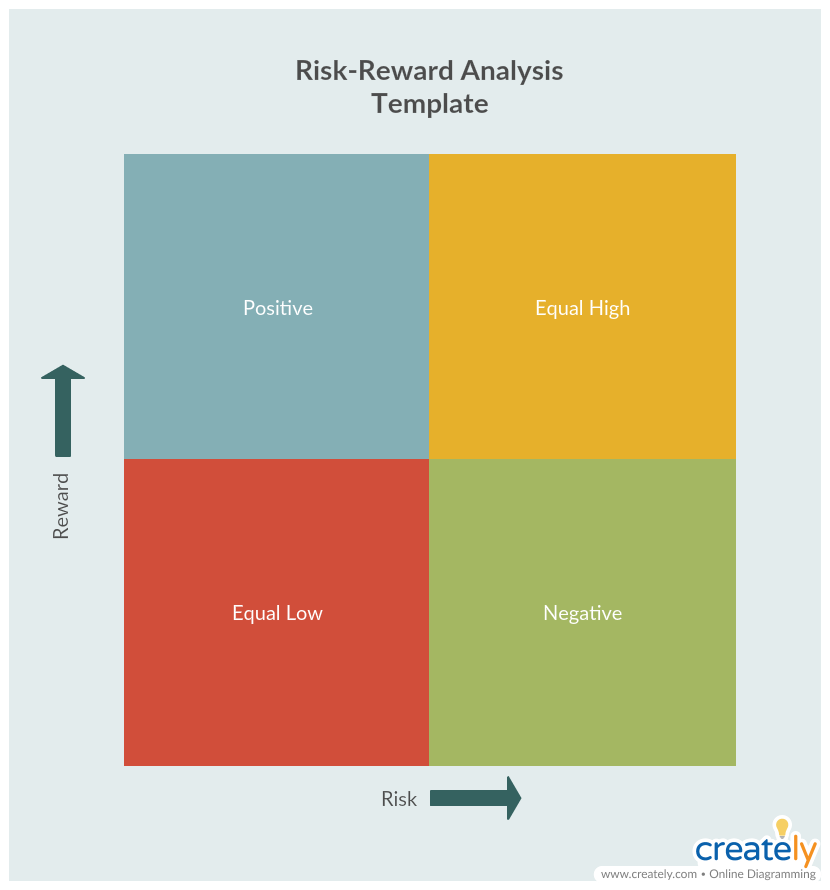
Risk – Reward Analysis Template (Click on the template to edit online)
Add to the List of Visual Risk Management Techniques
The risk management techniques we’ve discusses above will help you identify, analyze and control risks that may occur during your projects or the development of new business processes.
Do you know of any other visual techniques that can be used to manage risks? Let us know in the comment section below.
Join over thousands of organizations that use Creately to brainstorm, plan, analyze, and execute their projects successfully.

More Related Articles
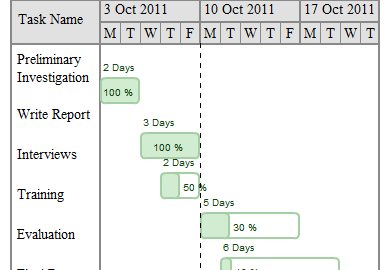
This work is quite resourceful especially for specialists in project management. The diagrams are quite impressive
Leave a comment Cancel reply
Please enter an answer in digits: 5 × 3 =
Download our all-new eBook for tips on 50 powerful Business Diagrams for Strategic Planning.
Popular Insights:
Best Project Management Software
Mind Mapping Software
Risk Assessment Matrix: What It Is and How to Use It
Share this Article:
Our content and product recommendations are editorially independent. We may make money when you click links to our partners. Learn more in our Editorial & Advertising Policy .
Key Takeaways
Featured Partners
{{ POSITION }}. {{ TITLE }}
What is a Risk Assessment Matrix?
A risk assessment matrix is a chart used for prioritizing and tracking project risks. It’s a visual aid that provides a complete overview of the risks involved and the likelihood that each one will occur, and it is vital when creating a risk management strategy.
Generally speaking, most projects present several different types of risk. Some common risks include:
- Operational risks: This includes risks that result from poor project implementation. Depending on the project, this could include issues with production, resource allocation, procurement, distribution, and more.
- Technological risks: Risks that affect software and hardware systems include cyber attacks, device failures, virus infections, and any sort of technological failure.
- Performance risks: These risks describe how likely—or unlikely—it is that the project will create the desired results.
- Scheduling risks: Anything that has the potential to disrupt the project timeline is considered a scheduling risk.
- Cost risks: Generally the result of poor project planning or scope creep, these risks either increase project budgets or result in unfinished or incomplete projects.
- Governance risks: These are risks that could affect the company’s reputation, their community, or their ethics, and they generally fall on the shoulders of executive board members and senior managerial staff.
- Scope creep risks: Do your project requirements often expand beyond the initial project scope? If so, you’re probably experiencing scope creep. While it can be controlled, failure to do so could result in complete failure of the project at hand.
- Legal risks: Most projects contain several legal risks, such as contractual and regulatory requirements, that must be followed at all times.
While other risks may exist, specific risks are often grouped into one of four categories or buckets. These buckets include:
- Project management risks: These risks involve your project team members and how they could affect the overall success of the project at hand. Examples include project planning, communications, and project controls.
- Organizational risks: Organizational risks refer to your ability to allocate resources, prioritize tasks, and make key decisions regarding the project.
- Technical risks: This category includes technological risks such as issues with software or hardware. It also includes risks involved in requirements gathering, process documentation, and performance analysis.
- External risks: Risks that are beyond the control of the PM or project team members are considered external risks. This could include weather-related risks, governmental risks, regulatory risks, societal risks, supplier-related risks, and others.
Depending on the project and the exact risks involved, some additional risk categories may need to be established.
Why is a Risk Assessment Matrix Important?
The average project is fraught with risk. Not only are there legal risks, like regulatory and contractual responsibilities, but there are financial concerns, technical and technological risks, external risks, and many more. If ignored, such risks could spell disaster for even the most skilled project managers . When properly analyzed and addressed by a veteran PM, however, many of these risks are easily mitigated.
How to Create a Risk Assessment Matrix
When creating your risk assessment matrix, the very first step involves identifying and isolating any issues that pose a threat to overall project success. For best results, review the above lists and work on identifying risks with your team. Including all project stakeholders in this manner will ensure that all of the potential threats are fully uncovered and identified.
Before the identified risks can be added to your risk assessment matrix, you’ll need to establish your risk criteria. This essentially means organizing all risks according to their likelihood and severity. However, the criteria you ultimately use depends on the exact sizing of your risk matrix.
Creating a 5×5 Risk Matrix
One of the most common examples of a risk assessment matrix is the 5×5 risk matrix. In this case, you’ll use five different likelihood ratings. From least likely to most likely, these include:
Additionally, each likelihood rating corresponds with a numerical value. Risks that are “improbable” are given a value of one, while those identified to be “frequent” are given the maximum value of five. These likelihood ratings comprise the left side of the risk matrix.
Next, you’ll establish five different severity ratings. From least severe to most severe, these include:
- Catastrophic
Severity ratings are listed across the top of the matrix. Similar to likelihood ratings, each severity rating is assigned with a numerical equivalent. The least severe “negligible” rating, for example, has a numerical value of one. On the other end of the scale, the “catastrophic” rating has a numerical value of five.
A 5×5 risk matrix then results in one of four different risk impact ratings: low, medium, high, or extreme. Those with the lowest likelihood to occur and the lowest severity rating will be on the low end of the matrix, while risks with the highest likelihood and highest severity will appear on the extreme end of the matrix.
Creating a 4×4 Risk Matrix
The 4×4 risk matrix is very similar to the 5×5 risk matrix, except instead of resulting in a grid that contains 25 squares (5 x 5), it creates a grid with 16 (4 x 4) total squares. While it is functionally identical to the 5×5 risk matrix, the 4×4 matrix has only four different ratings of risk likelihood and severity. From least likely to most likely, the likelihood ratings in a 4×4 risk matrix are:
Conversely, the four severity ratings are:
Although a 4×4 risk matrix has fewer grid squares than a 5×5 risk matrix, there are still four different risk impact ratings, which are low, medium, high, and extreme.
Creating a 3×3 Risk Matrix
Best suited for smaller projects, the 3×3 risk matrix only comprises a total of nine grid squares. Likelihood ratings for a 3×3 risk matrix include:
Listed in order from least severe to most severe, the severity ratings for a 3×3 risk matrix include:
Unlike the 5×5 and 4×4 risk matrices, the 3×3 risk matrix only produces three different risk impact ratings: low, medium, and high.
How to Use Your Risk Assessment Matrix
Now that you’ve brainstormed potential project risks and created your risk matrix, it’s time to begin measuring each risk according to the ratings indicated above. Remember that many of the risks and their respective ratings are highly subjective. Not only do they vary between industries and professions, but they can also vary between projects.
Using a 5×5 Risk Matrix
One of the most common sizes used, most project managers agree that the 5×5 risk matrix offers the perfect mixture of risk detail and clarity. However, it is generally reserved for larger projects. Most small projects can be completed using a 4×4 or 3×3 risk matrix.
When using a risk matrix, regardless of size, it’s important to remember the numerical values assigned to each likelihood and severity rating. This makes it easy to calculate a numerical value for each one of the project’s risks as you simply need to multiply the likelihood that it is to occur by the severity of its impact.
For example, a risk that would have a negligible impact on the project’s success and is considered “improbable” or unlikely to happen would have a risk impact rating of 1 (1 x 1). Any risk that would have a moderate impact and might happen “occasionally” results in an impact rating of 9 (3 x 3). On the highest end of the scale, a risk that would have a “catastrophic” impact on the project and occurs “frequently” ends up with a risk impact rating of 25 (5 x 5).
After you’ve determined the numerical risk impact rating for any given risk, compare it to the list below to determine whether it poses a low, medium, high, or extreme threat to project success.
- Medium: 4–9
- High: 10–16
- Extreme: 15–25
You will notice a bit of crossover between the “high” and “extreme” impact ratings. This is because a risk with “critical” impact (4) that is considered “probable” (4) to happen will have an impact rating of 16 (high), but a risk with “catastrophic” (5) consequences that has a “moderate” (3) chance of occurring will have an impact rating of 15 (extreme).
Using a 4×4 Risk Matrix
Another common sizing, the 4×4 risk matrix is for large projects that don’t require the level of granular detail that the 5×5 risk matrix provides. Depending on its usage, however, the 4×4 risk matrix could result in too many risks falling into a “medium” impact rating. In cases like this, it’s rather easy for risks to be mislabeled, and as such, some mitigation strategies might fall to the wayside.
Other than that, the 4×4 risk matrix functions identically to the 5×5 risk matrix. Once a risk has been placed onto the matrix, its risk impact rating is determined by multiplying the likelihood and severity ratings. Then compare the final sum to the list below to separate risks into the “low,” “medium,” “high,” and “extreme” categories.
- Medium: 3–4
- Extreme: 12–16
Using a 3×3 Risk Matrix
Many smaller projects can be completed with a 3×3 risk matrix. While it lacks the specificity of the 5×5 or 4×4 risk matrices, its basic design and straightforward process make it a great solution for novice PMs.
But the biggest drawback of the 3×3 risk matrix also lies in its simplicity. With only three likelihood and severity ratings, it can be difficult to accurately rank certain risks. That’s why large or complex projects often need a 4×4 or 5×5 risk matrix.
After you’ve multiplied the numerical values of the likelihood and severity ratings for each risk, compare the result against the list below in order to further categorize each project risk.
Risk Assessment Matrix Templates
There are a plethora of risk assessment matrix templates available online. While some of these are geared toward one particular industry or toward a specific project type, they all provide a great starting point for novice PMs and project teams who are trying to get started with the risk assessment matrix.
Someka Risk Assessment Matrix Template
Created by the team at Someka, this risk assessment matrix template is available in two different formats: Microsoft Excel and Google Sheets. Referred to as a Hazard Identification & Risk Assessment (HIRA), the document is ideal for tracking cyber threats, internal corruption, and other issues. It consists of three separate parts:
- Risk report: Provides a systematic examination of workplace risks, how to assess personal injuries on the job, and the likelihood of reducing risks.
- Risk list: This section lets the user list specific hazards, including the people who are at risk, the person responsible for overseeing the risk, and any recommended actions.
- Risk matrix: The last section comprises a 4×4 risk matrix for tracking the likelihood and severity of personal injuries in the workplace.
Smartsheet Risk Assessment Matrix Template
The development team at Smartsheet offers a variety of free risk matrix templates that are compatible with Smartsheet, Microsoft Excel, Microsoft Word, and Adobe software (PDF). Moreover, they provide risk matrices in several different sizes including 3×3, 3×4, and 5×5. They also provide more insight into the usage and application of risk assessment matrices in general.
TeamGantt Risk Assessment Matrix Template
Users who need a highly customizable, 3×3 risk assessment matrix template can find a basic version from TeamGantt. Available exclusively for Microsoft Excel, their simplified chart includes three different elements:
- Risk Assessment Matrix : This 3×3 risk matrix is simple to use and easy to customize as needed.
- Risk Assessment List : A pre-formatted list of all potential risks, the areas that are affected by these risks, the severity of each risk, the likelihood of each risk, the total risk impact rating, and any recommended actions
- Lists : A master list with all of the available severity, likelihood, and impact ratings
Risk Assessment Matrix FAQs
While risk assessment matrices tend to be highly accessible and straightforward, some users might have some remaining questions surrounding their usage or application.
What is the significance of risk severity levels in the matrix?
Risk severity levels provide a quantifiable measurement of the threat posed by any given risk. In a 5×5 risk matrix, there are five different severity levels (negligible, marginal, moderate, critical, and catastrophic). A 4×4 risk matrix has four different severity levels (negligible, marginal, critical, catastrophic), while a 3×3 risk matrix has three different severity levels (marginal, moderate, and critical).
Classifying risks in this manner makes it easy to see which risks need to be addressed immediately and which ones can be delayed to a later date (if at all).
How often should a risk assessment matrix be updated?
While risk matrices should be updated over the course of time, there is no right or wrong answer regarding the frequency of these updates. It is worth noting, however, that regular updates give you the opportunity to remove any resolved risks and add any new risks that have been uncovered since the project began. Moreover, updating the risk matrix at regular intervals is a great way to give novice PMs and new project teammates more experience with the entire process.
Can a risk assessment matrix be used in different industries?
Absolutely! Risk matrices aren’t limited to one specific industry, field, or profession. In fact, they are often customized in order to meet the user’s exact needs. Feel free to customize your risk assessment matrix by adding more risk categories, modifying the scoring criteria, or by using a different sized matrix altogether. The most important thing to remember here is that the risk matrix needs to work for you and your team. If it doesn’t or if it’s confusing to your project teammates, then it’s time to make a change.
Is risk assessment matrix sizing really important?
Yes and no. Generally speaking, smaller risk matrices work better for smaller projects. However, depending on the size and scope of the project, any matrix size should do. Most professionals don’t recommend going any larger than 5×5, however, as this often results in more complexity than it’s worth. For best results, stick to a 3×3, 4×4, or 5×5 risk assessment matrix.
Making the Most of Your Risk Assessment Matrix
In the hands of a skilled PM, a risk assessment matrix helps clarify risks and forecast their potential impact on the project as a whole. Most risk management strategies begin by prioritizing each risk on the matrix and allocating the resources needed to tackle the most impactful ones. Since it is virtually impossible to overcome every single risk, expert PMs need to know how to pick their battles and mitigate those that pose the most threat to overall project success.
Sign up for our emails and be the first to see helpful how-tos, insider tips & tricks, and a collection of templates & tools. Subscribe Now
{{ TITLE }}
You should also read.

Creating Gantt Charts in Microsoft Project: Ultimate Guide

Project Executive: Roles, Responsibilities, and How to Become One

What Is Cost-Benefit Analysis: A Practical Guide
Join our newsletter.
Subscribe to Project Management Insider for best practices, reviews and resources.
By clicking the button you agree of the privacy policy

Get the Newsletter
You might also like.

83 Project Management Terms & Concepts to Know
What Is a Problem Statement & How to Effectively Create One

How to Hire the Best Project Manager
Enterprise Risk Management Case Studies: Heroes and Zeros
By Andy Marker | April 7, 2021
- Share on Facebook
- Share on LinkedIn
Link copied
We’ve compiled more than 20 case studies of enterprise risk management programs that illustrate how companies can prevent significant losses yet take risks with more confidence.
Included on this page, you’ll find case studies and examples by industry , case studies of major risk scenarios (and company responses), and examples of ERM successes and failures .
Enterprise Risk Management Examples and Case Studies
With enterprise risk management (ERM) , companies assess potential risks that could derail strategic objectives and implement measures to minimize or avoid those risks. You can analyze examples (or case studies) of enterprise risk management to better understand the concept and how to properly execute it.
The collection of examples and case studies on this page illustrates common risk management scenarios by industry, principle, and degree of success. For a basic overview of enterprise risk management, including major types of risks, how to develop policies, and how to identify key risk indicators (KRIs), read “ Enterprise Risk Management 101: Programs, Frameworks, and Advice from Experts .”
Enterprise Risk Management Framework Examples
An enterprise risk management framework is a system by which you assess and mitigate potential risks. The framework varies by industry, but most include roles and responsibilities, a methodology for risk identification, a risk appetite statement, risk prioritization, mitigation strategies, and monitoring and reporting.
To learn more about enterprise risk management and find examples of different frameworks, read our “ Ultimate Guide to Enterprise Risk Management .”
Enterprise Risk Management Examples and Case Studies by Industry
Though every firm faces unique risks, those in the same industry often share similar risks. By understanding industry-wide common risks, you can create and implement response plans that offer your firm a competitive advantage.
Enterprise Risk Management Example in Banking
Toronto-headquartered TD Bank organizes its risk management around two pillars: a risk management framework and risk appetite statement. The enterprise risk framework defines the risks the bank faces and lays out risk management practices to identify, assess, and control risk. The risk appetite statement outlines the bank’s willingness to take on risk to achieve its growth objectives. Both pillars are overseen by the risk committee of the company’s board of directors.
Risk management frameworks were an important part of the International Organization for Standardization’s 31000 standard when it was first written in 2009 and have been updated since then. The standards provide universal guidelines for risk management programs.
Risk management frameworks also resulted from the efforts of the Committee of Sponsoring Organizations of the Treadway Commission (COSO). The group was formed to fight corporate fraud and included risk management as a dimension.
Once TD completes the ERM framework, the bank moves onto the risk appetite statement.
The bank, which built a large U.S. presence through major acquisitions, determined that it will only take on risks that meet the following three criteria:
- The risk fits the company’s strategy, and TD can understand and manage those risks.
- The risk does not render the bank vulnerable to significant loss from a single risk.
- The risk does not expose the company to potential harm to its brand and reputation.
Some of the major risks the bank faces include strategic risk, credit risk, market risk, liquidity risk, operational risk, insurance risk, capital adequacy risk, regulator risk, and reputation risk. Managers detail these categories in a risk inventory.
The risk framework and appetite statement, which are tracked on a dashboard against metrics such as capital adequacy and credit risk, are reviewed annually.
TD uses a three lines of defense (3LOD) strategy, an approach widely favored by ERM experts, to guard against risk. The three lines are as follows:
- A business unit and corporate policies that create controls, as well as manage and monitor risk
- Standards and governance that provide oversight and review of risks and compliance with the risk appetite and framework
- Internal audits that provide independent checks and verification that risk-management procedures are effective
Enterprise Risk Management Example in Pharmaceuticals
Drug companies’ risks include threats around product quality and safety, regulatory action, and consumer trust. To avoid these risks, ERM experts emphasize the importance of making sure that strategic goals do not conflict.
For Britain’s GlaxoSmithKline, such a conflict led to a breakdown in risk management, among other issues. In the early 2000s, the company was striving to increase sales and profitability while also ensuring safe and effective medicines. One risk the company faced was a failure to meet current good manufacturing practices (CGMP) at its plant in Cidra, Puerto Rico.
CGMP includes implementing oversight and controls of manufacturing, as well as managing the risk and confirming the safety of raw materials and finished drug products. Noncompliance with CGMP can result in escalating consequences, ranging from warnings to recalls to criminal prosecution.
GSK’s unit pleaded guilty and paid $750 million in 2010 to resolve U.S. charges related to drugs made at the Cidra plant, which the company later closed. A fired GSK quality manager alerted regulators and filed a whistleblower lawsuit in 2004. In announcing the consent decree, the U.S. Department of Justice said the plant had a history of bacterial contamination and multiple drugs created there in the early 2000s violated safety standards.
According to the whistleblower, GSK’s ERM process failed in several respects to act on signs of non-compliance with CGMP. The company received warning letters from the U.S. Food and Drug Administration in 2001 about the plant’s practices, but did not resolve the issues.
Additionally, the company didn’t act on the quality manager’s compliance report, which advised GSK to close the plant for two weeks to fix the problems and notify the FDA. According to court filings, plant staff merely skimmed rejected products and sold them on the black market. They also scraped by hand the inside of an antibiotic tank to get more product and, in so doing, introduced bacteria into the product.
Enterprise Risk Management Example in Consumer Packaged Goods
Mars Inc., an international candy and food company, developed an ERM process. The company piloted and deployed the initiative through workshops with geographic, product, and functional teams from 2003 to 2012.
Driven by a desire to frame risk as an opportunity and to work within the company’s decentralized structure, Mars created a process that asked participants to identify potential risks and vote on which had the highest probability. The teams listed risk mitigation steps, then ranked and color-coded them according to probability of success.
Larry Warner, a Mars risk officer at the time, illustrated this process in a case study . An initiative to increase direct-to-consumer shipments by 12 percent was colored green, indicating a 75 percent or greater probability of achievement. The initiative to bring a new plant online by the end of Q3 was coded red, meaning less than a 50 percent probability of success.
The company’s results were hurt by a surprise at an operating unit that resulted from a so-coded red risk identified in a unit workshop. Executives had agreed that some red risk profile was to be expected, but they decided that when a unit encountered a red issue, it must be communicated upward when first identified. This became a rule.
This process led to the creation of an ERM dashboard that listed initiatives in priority order, with the profile of each risk faced in the quarter, the risk profile trend, and a comment column for a year-end view.
According to Warner, the key factors of success for ERM at Mars are as follows:
- The initiative focused on achieving operational and strategic objectives rather than compliance, which refers to adhering to established rules and regulations.
- The program evolved, often based on requests from business units, and incorporated continuous improvement.
- The ERM team did not overpromise. It set realistic objectives.
- The ERM team periodically surveyed business units, management teams, and board advisers.
Enterprise Risk Management Example in Retail
Walmart is the world’s biggest retailer. As such, the company understands that its risk makeup is complex, given the geographic spread of its operations and its large number of stores, vast supply chain, and high profile as an employer and buyer of goods.
In the 1990s, the company sought a simplified strategy for assessing risk and created an enterprise risk management plan with five steps founded on these four questions:
- What are the risks?
- What are we going to do about them?
- How will we know if we are raising or decreasing risk?
- How will we show shareholder value?
The process follows these five steps:
- Risk Identification: Senior Walmart leaders meet in workshops to identify risks, which are then plotted on a graph of probability vs. impact. Doing so helps to prioritize the biggest risks. The executives then look at seven risk categories (both internal and external): legal/regulatory, political, business environment, strategic, operational, financial, and integrity. Many ERM pros use risk registers to evaluate and determine the priority of risks. You can download templates that help correlate risk probability and potential impact in “ Free Risk Register Templates .”
- Risk Mitigation: Teams that include operational staff in the relevant area meet. They use existing inventory procedures to address the risks and determine if the procedures are effective.
- Action Planning: A project team identifies and implements next steps over the several months to follow.
- Performance Metrics: The group develops metrics to measure the impact of the changes. They also look at trends of actual performance compared to goal over time.
- Return on Investment and Shareholder Value: In this step, the group assesses the changes’ impact on sales and expenses to determine if the moves improved shareholder value and ROI.
To develop your own risk management planning, you can download a customizable template in “ Risk Management Plan Templates .”
Enterprise Risk Management Example in Agriculture
United Grain Growers (UGG), a Canadian grain distributor that now is part of Glencore Ltd., was hailed as an ERM innovator and became the subject of business school case studies for its enterprise risk management program. This initiative addressed the risks associated with weather for its business. Crop volume drove UGG’s revenue and profits.
In the late 1990s, UGG identified its major unaddressed risks. Using almost a century of data, risk analysts found that extreme weather events occurred 10 times as frequently as previously believed. The company worked with its insurance broker and the Swiss Re Group on a solution that added grain-volume risk (resulting from weather fluctuations) to its other insured risks, such as property and liability, in an integrated program.
The result was insurance that protected grain-handling earnings, which comprised half of UGG’s gross profits. The greater financial stability significantly enhanced the firm’s ability to achieve its strategic objectives.
Since then, the number and types of instruments to manage weather-related risks has multiplied rapidly. For example, over-the-counter derivatives, such as futures and options, began trading in 1997. The Chicago Mercantile Exchange now offers weather futures contracts on 12 U.S. and international cities.
Weather derivatives are linked to climate factors such as rainfall or temperature, and they hedge different kinds of risks than do insurance. These risks are much more common (e.g., a cooler-than-normal summer) than the earthquakes and floods that insurance typically covers. And the holders of derivatives do not have to incur any damage to collect on them.
These weather-linked instruments have found a wider audience than anticipated, including retailers that worry about freak storms decimating Christmas sales, amusement park operators fearing rainy summers will keep crowds away, and energy companies needing to hedge demand for heating and cooling.
This area of ERM continues to evolve because weather and crop insurance are not enough to address all the risks that agriculture faces. Arbol, Inc. estimates that more than $1 trillion of agricultural risk is uninsured. As such, it is launching a blockchain-based platform that offers contracts (customized by location and risk parameters) with payouts based on weather data. These contracts can cover risks associated with niche crops and small growing areas.
Enterprise Risk Management Example in Insurance
Switzerland’s Zurich Insurance Group understands that risk is inherent for insurers and seeks to practice disciplined risk-taking, within a predetermined risk tolerance.
The global insurer’s enterprise risk management framework aims to protect capital, liquidity, earnings, and reputation. Governance serves as the basis for risk management, and the framework lays out responsibilities for taking, managing, monitoring, and reporting risks.
The company uses a proprietary process called Total Risk Profiling (TRP) to monitor internal and external risks to its strategy and financial plan. TRP assesses risk on the basis of severity and probability, and helps define and implement mitigating moves.
Zurich’s risk appetite sets parameters for its tolerance within the goal of maintaining enough capital to achieve an AA rating from rating agencies. For this, the company uses its own Zurich economic capital model, referred to as Z-ECM. The model quantifies risk tolerance with a metric that assesses risk profile vs. risk tolerance.
To maintain the AA rating, the company aims to hold capital between 100 and 120 percent of capital at risk. Above 140 percent is considered overcapitalized (therefore at risk of throttling growth), and under 90 percent is below risk tolerance (meaning the risk is too high). On either side of 100 to 120 percent (90 to 100 percent and 120 to 140 percent), the insurer considers taking mitigating action.
Zurich’s assessment of risk and the nature of those risks play a major role in determining how much capital regulators require the business to hold. A popular tool to assess risk is the risk matrix, and you can find a variety of templates in “ Free, Customizable Risk Matrix Templates .”
In 2020, Zurich found that its biggest exposures were market risk, such as falling asset valuations and interest-rate risk; insurance risk, such as big payouts for covered customer losses, which it hedges through diversification and reinsurance; credit risk in assets it holds and receivables; and operational risks, such as internal process failures and external fraud.
Enterprise Risk Management Example in Technology
Financial software maker Intuit has strengthened its enterprise risk management through evolution, according to a case study by former Chief Risk Officer Janet Nasburg.
The program is founded on the following five core principles:
- Use a common risk framework across the enterprise.
- Assess risks on an ongoing basis.
- Focus on the most important risks.
- Clearly define accountability for risk management.
- Commit to continuous improvement of performance measurement and monitoring.
ERM programs grow according to a maturity model, and as capability rises, the shareholder value from risk management becomes more visible and important.
The maturity phases include the following:
- Ad hoc risk management addresses a specific problem when it arises.
- Targeted or initial risk management approaches risks with multiple understandings of what constitutes risk and management occurs in silos.
- Integrated or repeatable risk management puts in place an organization-wide framework for risk assessment and response.
- Intelligent or managed risk management coordinates risk management across the business, using common tools.
- Risk leadership incorporates risk management into strategic decision-making.
Intuit emphasizes using key risk indicators (KRIs) to understand risks, along with key performance indicators (KPIs) to gauge the effectiveness of risk management.
Early in its ERM journey, Intuit measured performance on risk management process participation and risk assessment impact. For participation, the targeted rate was 80 percent of executive management and business-line leaders. This helped benchmark risk awareness and current risk management, at a time when ERM at the company was not mature.
Conduct an annual risk assessment at corporate and business-line levels to plot risks, so the most likely and most impactful risks are graphed in the upper-right quadrant. Doing so focuses attention on these risks and helps business leaders understand the risk’s impact on performance toward strategic objectives.
In the company’s second phase of ERM, Intuit turned its attention to building risk management capacity and sought to ensure that risk management activities addressed the most important risks. The company evaluated performance using color-coded status symbols (red, yellow, green) to indicate risk trend and progress on risk mitigation measures.
In its third phase, Intuit moved to actively monitoring the most important risks and ensuring that leaders modified their strategies to manage risks and take advantage of opportunities. An executive dashboard uses KRIs, KPIs, an overall risk rating, and red-yellow-green coding. The board of directors regularly reviews this dashboard.
Over this evolution, the company has moved from narrow, tactical risk management to holistic, strategic, and long-term ERM.
Enterprise Risk Management Case Studies by Principle
ERM veterans agree that in addition to KPIs and KRIs, other principles are equally important to follow. Below, you’ll find examples of enterprise risk management programs by principles.
ERM Principle #1: Make Sure Your Program Aligns with Your Values
Raytheon Case Study U.S. defense contractor Raytheon states that its highest priority is delivering on its commitment to provide ethical business practices and abide by anti-corruption laws.
Raytheon backs up this statement through its ERM program. Among other measures, the company performs an annual risk assessment for each function, including the anti-corruption group under the Chief Ethics and Compliance Officer. In addition, Raytheon asks 70 of its sites to perform an anti-corruption self-assessment each year to identify gaps and risks. From there, a compliance team tracks improvement actions.
Every quarter, the company surveys 600 staff members who may face higher anti-corruption risks, such as the potential for bribes. The survey asks them to report any potential issues in the past quarter.
Also on a quarterly basis, the finance and internal controls teams review higher-risk profile payments, such as donations and gratuities to confirm accuracy and compliance. Oversight and compliance teams add other checks, and they update a risk-based audit plan continuously.
ERM Principle #2: Embrace Diversity to Reduce Risk
State Street Global Advisors Case Study In 2016, the asset management firm State Street Global Advisors introduced measures to increase gender diversity in its leadership as a way of reducing portfolio risk, among other goals.
The company relied on research that showed that companies with more women senior managers had a better return on equity, reduced volatility, and fewer governance problems such as corruption and fraud.
Among the initiatives was a campaign to influence companies where State Street had invested, in order to increase female membership on their boards. State Street also developed an investment product that tracks the performance of companies with the highest level of senior female leadership relative to peers in their sector.
In 2020, the company announced some of the results of its effort. Among the 1,384 companies targeted by the firm, 681 added at least one female director.
ERM Principle #3: Do Not Overlook Resource Risks
Infosys Case Study India-based technology consulting company Infosys, which employees more than 240,000 people, has long recognized the risk of water shortages to its operations.
India’s rapidly growing population and development has increased the risk of water scarcity. A 2020 report by the World Wide Fund for Nature said 30 cities in India faced the risk of severe water scarcity over the next three decades.
Infosys has dozens of facilities in India and considers water to be a significant short-term risk. At its campuses, the company uses the water for cooking, drinking, cleaning, restrooms, landscaping, and cooling. Water shortages could halt Infosys operations and prevent it from completing customer projects and reaching its performance objectives.
In an enterprise risk assessment example, Infosys’ ERM team conducts corporate water-risk assessments while sustainability teams produce detailed water-risk assessments for individual locations, according to a report by the World Business Council for Sustainable Development .
The company uses the COSO ERM framework to respond to the risks and decide whether to accept, avoid, reduce, or share these risks. The company uses root-cause analysis (which focuses on identifying underlying causes rather than symptoms) and the site assessments to plan steps to reduce risks.
Infosys has implemented various water conservation measures, such as water-efficient fixtures and water recycling, rainwater collection and use, recharging aquifers, underground reservoirs to hold five days of water supply at locations, and smart-meter usage monitoring. Infosys’ ERM team tracks metrics for per-capita water consumption, along with rainfall data, availability and cost of water by tanker trucks, and water usage from external suppliers.
In the 2020 fiscal year, the company reported a nearly 64 percent drop in per-capita water consumption by its workforce from the 2008 fiscal year.
The business advantages of this risk management include an ability to open locations where water shortages may preclude competitors, and being able to maintain operations during water scarcity, protecting profitability.
ERM Principle #4: Fight Silos for Stronger Enterprise Risk Management
U.S. Government Case Study The terrorist attacks of September 11, 2001, revealed that the U.S. government’s then-current approach to managing intelligence was not adequate to address the threats — and, by extension, so was the government’s risk management procedure. Since the Cold War, sensitive information had been managed on a “need to know” basis that resulted in data silos.
In the case of 9/11, this meant that different parts of the government knew some relevant intelligence that could have helped prevent the attacks. But no one had the opportunity to put the information together and see the whole picture. A congressional commission determined there were 10 lost operational opportunities to derail the plot. Silos existed between law enforcement and intelligence, as well as between and within agencies.
After the attacks, the government moved toward greater information sharing and collaboration. Based on a task force’s recommendations, data moved from a centralized network to a distributed model, and social networking tools now allow colleagues throughout the government to connect. Staff began working across agency lines more often.
Enterprise Risk Management Examples by Scenario
While some scenarios are too unlikely to receive high-priority status, low-probability risks are still worth running through the ERM process. Robust risk management creates a culture and response capacity that better positions a company to deal with a crisis.
In the following enterprise risk examples, you will find scenarios and details of how organizations manage the risks they face.
Scenario: ERM and the Global Pandemic While most businesses do not have the resources to do in-depth ERM planning for the rare occurrence of a global pandemic, companies with a risk-aware culture will be at an advantage if a pandemic does hit.
These businesses already have processes in place to escalate trouble signs for immediate attention and an ERM team or leader monitoring the threat environment. A strong ERM function gives clear and effective guidance that helps the company respond.
A report by Vodafone found that companies identified as “future ready” fared better in the COVID-19 pandemic. The attributes of future-ready businesses have a lot in common with those of companies that excel at ERM. These include viewing change as an opportunity; having detailed business strategies that are documented, funded, and measured; working to understand the forces that shape their environments; having roadmaps in place for technological transformation; and being able to react more quickly than competitors.
Only about 20 percent of companies in the Vodafone study met the definition of “future ready.” But 54 percent of these firms had a fully developed and tested business continuity plan, compared to 30 percent of all businesses. And 82 percent felt their continuity plans worked well during the COVID-19 crisis. Nearly 50 percent of all businesses reported decreased profits, while 30 percent of future-ready organizations saw profits rise.
Scenario: ERM and the Economic Crisis The 2008 economic crisis in the United States resulted from the domino effect of rising interest rates, a collapse in housing prices, and a dramatic increase in foreclosures among mortgage borrowers with poor creditworthiness. This led to bank failures, a credit crunch, and layoffs, and the U.S. government had to rescue banks and other financial institutions to stabilize the financial system.
Some commentators said these events revealed the shortcomings of ERM because it did not prevent the banks’ mistakes or collapse. But Sim Segal, an ERM consultant and director of Columbia University’s ERM master’s degree program, analyzed how banks performed on 10 key ERM criteria.
Segal says a risk-management program that incorporates all 10 criteria has these characteristics:
- Risk management has an enterprise-wide scope.
- The program includes all risk categories: financial, operational, and strategic.
- The focus is on the most important risks, not all possible risks.
- Risk management is integrated across risk types.
- Aggregated metrics show risk exposure and appetite across the enterprise.
- Risk management incorporates decision-making, not just reporting.
- The effort balances risk and return management.
- There is a process for disclosure of risk.
- The program measures risk in terms of potential impact on company value.
- The focus of risk management is on the primary stakeholder, such as shareholders, rather than regulators or rating agencies.
In his book Corporate Value of Enterprise Risk Management , Segal concluded that most banks did not actually use ERM practices, which contributed to the financial crisis. He scored banks as failing on nine of the 10 criteria, only giving them a passing grade for focusing on the most important risks.
Scenario: ERM and Technology Risk The story of retailer Target’s failed expansion to Canada, where it shut down 133 loss-making stores in 2015, has been well documented. But one dimension that analysts have sometimes overlooked was Target’s handling of technology risk.
A case study by Canadian Business magazine traced some of the biggest issues to software and data-quality problems that dramatically undermined the Canadian launch.
As with other forms of ERM, technology risk management requires companies to ask what could go wrong, what the consequences would be, how they might prevent the risks, and how they should deal with the consequences.
But with its technology plan for Canada, Target did not heed risk warning signs.
In the United States, Target had custom systems for ordering products from vendors, processing items at warehouses, and distributing merchandise to stores quickly. But that software would need customization to work with the Canadian dollar, metric system, and French-language characters.
Target decided to go with new ERP software on an aggressive two-year timeline. As Target began ordering products for the Canadian stores in 2012, problems arose. Some items did not fit into shipping containers or on store shelves, and information needed for customs agents to clear imported items was not correct in Target's system.
Target found that its supply chain software data was full of errors. Product dimensions were in inches, not centimeters; height and width measurements were mixed up. An internal investigation showed that only about 30 percent of the data was accurate.
In an attempt to fix these errors, Target merchandisers spent a week double-checking with vendors up to 80 data points for each of the retailer’s 75,000 products. They discovered that the dummy data entered into the software during setup had not been altered. To make any corrections, employees had to send the new information to an office in India where staff would enter it into the system.
As the launch approached, the technology errors left the company vulnerable to stockouts, few people understood how the system worked, and the point-of-sale checkout system did not function correctly. Soon after stores opened in 2013, consumers began complaining about empty shelves. Meanwhile, Target Canada distribution centers overflowed due to excess ordering based on poor data fed into forecasting software.
The rushed launch compounded problems because it did not allow the company enough time to find solutions or alternative technology. While the retailer fixed some issues by the end of 2014, it was too late. Target Canada filed for bankruptcy protection in early 2015.
Scenario: ERM and Cybersecurity System hacks and data theft are major worries for companies. But as a relatively new field, cyber-risk management faces unique hurdles.
For example, risk managers and information security officers have difficulty quantifying the likelihood and business impact of a cybersecurity attack. The rise of cloud-based software exposes companies to third-party risks that make these projections even more difficult to calculate.
As the field evolves, risk managers say it’s important for IT security officers to look beyond technical issues, such as the need to patch a vulnerability, and instead look more broadly at business impacts to make a cost benefit analysis of risk mitigation. Frameworks such as the Risk Management Framework for Information Systems and Organizations by the National Institute of Standards and Technology can help.
Health insurer Aetna considers cybersecurity threats as a part of operational risk within its ERM framework and calculates a daily risk score, adjusted with changes in the cyberthreat landscape.
Aetna studies threats from external actors by working through information sharing and analysis centers for the financial services and health industries. Aetna staff reverse-engineers malware to determine controls. The company says this type of activity helps ensure the resiliency of its business processes and greatly improves its ability to help protect member information.
For internal threats, Aetna uses models that compare current user behavior to past behavior and identify anomalies. (The company says it was the first organization to do this at scale across the enterprise.) Aetna gives staff permissions to networks and data based on what they need to perform their job. This segmentation restricts access to raw data and strengthens governance.
Another risk initiative scans outgoing employee emails for code patterns, such as credit card or Social Security numbers. The system flags the email, and a security officer assesses it before the email is released.
Examples of Poor Enterprise Risk Management
Case studies of failed enterprise risk management often highlight mistakes that managers could and should have spotted — and corrected — before a full-blown crisis erupted. The focus of these examples is often on determining why that did not happen.
ERM Case Study: General Motors
In 2014, General Motors recalled the first of what would become 29 million cars due to faulty ignition switches and paid compensation for 124 related deaths. GM knew of the problem for at least 10 years but did not act, the automaker later acknowledged. The company entered a deferred prosecution agreement and paid a $900 million penalty.
Pointing to the length of time the company failed to disclose the safety problem, ERM specialists say it shows the problem did not reside with a single department. “Rather, it reflects a failure to properly manage risk,” wrote Steve Minsky, a writer on ERM and CEO of an ERM software company, in Risk Management magazine.
“ERM is designed to keep all parties across the organization, from the front lines to the board to regulators, apprised of these kinds of problems as they become evident. Unfortunately, GM failed to implement such a program, ultimately leading to a tragic and costly scandal,” Minsky said.
Also in the auto sector, an enterprise risk management case study of Toyota looked at its problems with unintended acceleration of vehicles from 2002 to 2009. Several studies, including a case study by Carnegie Mellon University Professor Phil Koopman , blamed poor software design and company culture. A whistleblower later revealed a coverup by Toyota. The company paid more than $2.5 billion in fines and settlements.
ERM Case Study: Lululemon
In 2013, following customer complaints that its black yoga pants were too sheer, the athletic apparel maker recalled 17 percent of its inventory at a cost of $67 million. The company had previously identified risks related to fabric supply and quality. The CEO said the issue was inadequate testing.
Analysts raised concerns about the company’s controls, including oversight of factories and product quality. A case study by Stanford University professors noted that Lululemon’s episode illustrated a common disconnect between identifying risks and being prepared to manage them when they materialize. Lululemon’s reporting and analysis of risks was also inadequate, especially as related to social media. In addition, the case study highlighted the need for a system to escalate risk-related issues to the board.
ERM Case Study: Kodak
Once an iconic brand, the photo film company failed for decades to act on the threat that digital photography posed to its business and eventually filed for bankruptcy in 2012. The company’s own research in 1981 found that digital photos could ultimately replace Kodak’s film technology and estimated it had 10 years to prepare.
Unfortunately, Kodak did not prepare and stayed locked into the film paradigm. The board reinforced this course when in 1989 it chose as CEO a candidate who came from the film business over an executive interested in digital technology.
Had the company acknowledged the risks and employed ERM strategies, it might have pursued a variety of strategies to remain successful. The company’s rival, Fuji Film, took the money it made from film and invested in new initiatives, some of which paid off. Kodak, on the other hand, kept investing in the old core business.
Case Studies of Successful Enterprise Risk Management
Successful enterprise risk management usually requires strong performance in multiple dimensions, and is therefore more likely to occur in organizations where ERM has matured. The following examples of enterprise risk management can be considered success stories.
ERM Case Study: Statoil
A major global oil producer, Statoil of Norway stands out for the way it practices ERM by looking at both downside risk and upside potential. Taking risks is vital in a business that depends on finding new oil reserves.
According to a case study, the company developed its own framework founded on two basic goals: creating value and avoiding accidents.
The company aims to understand risks thoroughly, and unlike many ERM programs, Statoil maps risks on both the downside and upside. It graphs risk on probability vs. impact on pre-tax earnings, and it examines each risk from both positive and negative perspectives.
For example, the case study cites a risk that the company assessed as having a 5 percent probability of a somewhat better-than-expected outcome but a 10 percent probability of a significant loss relative to forecast. In this case, the downside risk was greater than the upside potential.
ERM Case Study: Lego
The Danish toy maker’s ERM evolved over the following four phases, according to a case study by one of the chief architects of its program:
- Traditional management of financial, operational, and other risks. Strategic risk management joined the ERM program in 2006.
- The company added Monte Carlo simulations in 2008 to model financial performance volatility so that budgeting and financial processes could incorporate risk management. The technique is used in budget simulations, to assess risk in its credit portfolio, and to consolidate risk exposure.
- Active risk and opportunity planning is part of making a business case for new projects before final decisions.
- The company prepares for uncertainty so that long-term strategies remain relevant and resilient under different scenarios.
As part of its scenario modeling, Lego developed its PAPA (park, adapt, prepare, act) model.
- Park: The company parks risks that occur slowly and have a low probability of happening, meaning it does not forget nor actively deal with them.
- Adapt: This response is for risks that evolve slowly and are certain or highly probable to occur. For example, a risk in this category is the changing nature of play and the evolution of buying power in different parts of the world. In this phase, the company adjusts, monitors the trend, and follows developments.
- Prepare: This category includes risks that have a low probability of occurring — but when they do, they emerge rapidly. These risks go into the ERM risk database with contingency plans, early warning indicators, and mitigation measures in place.
- Act: These are high-probability, fast-moving risks that must be acted upon to maintain strategy. For example, developments around connectivity, mobile devices, and online activity are in this category because of the rapid pace of change and the influence on the way children play.
Lego views risk management as a way to better equip itself to take risks than its competitors. In the case study, the writer likens this approach to the need for the fastest race cars to have the best brakes and steering to achieve top speeds.
ERM Case Study: University of California
The University of California, one of the biggest U.S. public university systems, introduced a new view of risk to its workforce when it implemented enterprise risk management in 2005. Previously, the function was merely seen as a compliance requirement.
ERM became a way to support the university’s mission of education and research, drawing on collaboration of the system’s employees across departments. “Our philosophy is, ‘Everyone is a risk manager,’” Erike Young, deputy director of ERM told Treasury and Risk magazine. “Anyone who’s in a management position technically manages some type of risk.”
The university faces a diverse set of risks, including cybersecurity, hospital liability, reduced government financial support, and earthquakes.
The ERM department had to overhaul systems to create a unified view of risk because its information and processes were not linked. Software enabled both an organizational picture of risk and highly detailed drilldowns on individual risks. Risk managers also developed tools for risk assessment, risk ranking, and risk modeling.
Better risk management has provided more than $100 million in annual cost savings and nearly $500 million in cost avoidance, according to UC officials.
UC drives ERM with risk management departments at each of its 10 locations and leverages university subject matter experts to form multidisciplinary workgroups that develop process improvements.
APQC, a standards quality organization, recognized UC as a top global ERM practice organization, and the university system has won other awards. The university says in 2010 it was the first nonfinancial organization to win credit-rating agency recognition of its ERM program.
Examples of How Technology Is Transforming Enterprise Risk Management
Business intelligence software has propelled major progress in enterprise risk management because the technology enables risk managers to bring their information together, analyze it, and forecast how risk scenarios would impact their business.
ERM organizations are using computing and data-handling advancements such as blockchain for new innovations in strengthening risk management. Following are case studies of a few examples.
ERM Case Study: Bank of New York Mellon
In 2021, the bank joined with Google Cloud to use machine learning and artificial intelligence to predict and reduce the risk that transactions in the $22 trillion U.S. Treasury market will fail to settle. Settlement failure means a buyer and seller do not exchange cash and securities by the close of business on the scheduled date.
The party that fails to settle is assessed a daily financial penalty, and a high level of settlement failures can indicate market liquidity problems and rising risk. BNY says that, on average, about 2 percent of transactions fail to settle.
The bank trained models with millions of trades to consider every factor that could result in settlement failure. The service uses market-wide intraday trading metrics, trading velocity, scarcity indicators, volume, the number of trades settled per hour, seasonality, issuance patterns, and other signals.
The bank said it predicts about 40 percent of settlement failures with 90 percent accuracy. But it also cautioned against overconfidence in the technology as the model continues to improve.
AI-driven forecasting reduces risk for BNY clients in the Treasury market and saves costs. For example, a predictive view of settlement risks helps bond dealers more accurately manage their liquidity buffers, avoid penalties, optimize their funding sources, and offset the risks of failed settlements. In the long run, such forecasting tools could improve the health of the financial market.
ERM Case Study: PwC
Consulting company PwC has leveraged a vast information storehouse known as a data lake to help its customers manage risk from suppliers.
A data lake stores both structured or unstructured information, meaning data in highly organized, standardized formats as well as unstandardized data. This means that everything from raw audio to credit card numbers can live in a data lake.
Using techniques pioneered in national security, PwC built a risk data lake that integrates information from client companies, public databases, user devices, and industry sources. Algorithms find patterns that can signify unidentified risks.
One of PwC’s first uses of this data lake was a program to help companies uncover risks from their vendors and suppliers. Companies can violate laws, harm their reputations, suffer fraud, and risk their proprietary information by doing business with the wrong vendor.
Today’s complex global supply chains mean companies may be several degrees removed from the source of this risk, which makes it hard to spot and mitigate. For example, a product made with outlawed child labor could be traded through several intermediaries before it reaches a retailer.
PwC’s service helps companies recognize risk beyond their primary vendors and continue to monitor that risk over time as more information enters the data lake.
ERM Case Study: Financial Services
As analytics have become a pillar of forecasting and risk management for banks and other financial institutions, a new risk has emerged: model risk . This refers to the risk that machine-learning models will lead users to an unreliable understanding of risk or have unintended consequences.
For example, a 6 percent drop in the value of the British pound over the course of a few minutes in 2016 stemmed from currency trading algorithms that spiralled into a negative loop. A Twitter-reading program began an automated selling of the pound after comments by a French official, and other selling algorithms kicked in once the currency dropped below a certain level.
U.S. banking regulators are so concerned about model risk that the Federal Reserve set up a model validation council in 2012 to assess the models that banks use in running risk simulations for capital adequacy requirements. Regulators in Europe and elsewhere also require model validation.
A form of managing risk from a risk-management tool, model validation is an effort to reduce risk from machine learning. The technology-driven rise in modeling capacity has caused such models to proliferate, and banks can use hundreds of models to assess different risks.
Model risk management can reduce rising costs for modeling by an estimated 20 to 30 percent by building a validation workflow, prioritizing models that are most important to business decisions, and implementing automation for testing and other tasks, according to McKinsey.
Streamline Your Enterprise Risk Management Efforts with Real-Time Work Management in Smartsheet
Empower your people to go above and beyond with a flexible platform designed to match the needs of your team — and adapt as those needs change.
The Smartsheet platform makes it easy to plan, capture, manage, and report on work from anywhere, helping your team be more effective and get more done. Report on key metrics and get real-time visibility into work as it happens with roll-up reports, dashboards, and automated workflows built to keep your team connected and informed.
When teams have clarity into the work getting done, there’s no telling how much more they can accomplish in the same amount of time. Try Smartsheet for free, today.
Discover why over 90% of Fortune 100 companies trust Smartsheet to get work done.
Geography Department Penn State
- Instructor Information
- Program Home Page
- Library Resources
- Getting Help
Assignment #7 - Risk Identification and Analysis
Assignment #7 Overview
Timing : See Canvas Calendar Target Word Count : 1800-3000 words (this is just a target to provide a general idea on level of detail) Total Points: 70 points - see rubric for details
Assignment #7 will also be completed as a team assignment. Teams for Assignment #7 will be the same as those assigned for Assignment #6 . At the beginning of or prior to Week 8, the team should assign a different team leader to coordinate the team's work on Assignment #7. This Assignment follows work that you have already carried out in planning and preparing for the City of Metropolis Geodatabase Development Project in past assignments. Assignment #7 is to identify project risks, prepare a risk probability matrix, and carry out an analysis of selected risks and risk responses (one for each team member). As described in Assignment #6, you may use any appropriate communication and group collaboration tools to support your work on this Assignment.
Your team represents the City’s contractor selected by the City to carry out the City of Metropolis Geodatabase Design and Development Project. Your company's senior management and the City's Project Manager have requested that you prepare a risk management plan that identifies potential risks and identifies risk management strategies. From the course content and readings, you know that the overall purpose of risk planning is to anticipate possible risk events and be ready to take appropriate action when risk events occur—to eliminate or reduce negative impacts on the project.
Your Submittal for Assignment #7
You may wish to begin this exercise with a brainstorming session about potential risks to get candidate risks “on the table” for consideration by the team, and then identify and refine that wording for risks that have some realistic chance of occurring in this project. For example, potential weather problems present a real obstacle to completing field data collection by the planned completion date. It is also an issue that the project manager will ultimately have to plan for, as opposed to other issues that may more align with company policy, such as employee retention policies. Also, a major disaster (e.g., your office burning down), is not a high-enough probability event that requires much time in planning. As described below, you will select several of the identified risks and carry out a risk analysis.
Your team will use the distilled list of risks to make a risk matrix (see Figure 8-1 for an example). The matrix will have at least three classes (high/medium/low) for probability and impact, but you may include more classes if you like. All team members should contribute to identifying risks and organizing them into the matrix. Remember that it is important to name risks effectively—use words that describe the risk event and point to the impact on the project (e.g., “injury of field technician disrupts data collection work”) After completion of the risk matrix, each team member should then select one of the identified risks which the team finds critical to the project. The team members will carry out and document a risk analysis for their selected risk.
In summary, the Risk Management Plan you submit should cover the following main parts:
- Cover page with prominent title and all necessary information identifying the course, assignment, author, and date. The main title of the document should be "RISK MANAGEMENT PLAN". The Cover Page should also reference "City of Metropolis" and the full project name and the name of your company. At the bottom of the Cover Page (right side is best), include the course name and number, assignment number, Team number and team members, and date.
- Table of Contents.
- Summary of the project and its deliverables so the reader can understand the context for risk management in this project. Gie a reasonable amount of detail about the deliverables and scope: a) discssion of the field data collection, QC, and creation of new geodatabase feature classes, b) explanaiton of the 2 MD4 custom GIS applications including software platforms (e.g., ArcGIS Pro, ArcGIS Online Field Maps)
- Explanation of risk management with a description of key terms (e.g., risk, risk event, risk response strategy, etc.). Make reference to the PMI PMBoK.
- Risk identification register which includes a comprehensive set of risks (for all aspects and deliverables of the project) organized into risk categories (e.g., "Technical/Operational"). This list should show, at a minimum, the risk ID number, a descriptive name* of the risk, and a short description. You can decide on your own risk categories. You should use an alphanumeric risk numbering scheme where the alpha code represents the risk category and sequential numbering within each category (e.g., TO1, TO2, etc.). You can decide on your own categories but the categories should be described. A table format works best for this. That description can be one or two sentences that explain the risk event, condition, or circumstance and how it could impact the project.
- Risk matrix similar to that shown in Figure 8-1 with classification for Impact and Probability. Be sure to include and introduction on what the purpose of the matrix is and how it suports project planning and provides a basis for managing the project. It is importnt to includes a description of what "Probability" and "Impact" mean in the context of the project. The classes (e.g., Low, Medium, High) should be described. If you want to add a "Very High" category that is OK. While these categories (H, M, L) are qualitative in nature, your description of them should give a picture of what they mean relative to the project. For instance, "High Impact" could be defined as, "Occurrence of this risk will cause major disruption of the project schedule, qualty, or budget and response sction should be taken immediately to eliminate or reduce the level of disruption". It is a good idea to describe the Probability categories as a projected likelihood of occurrence--e.g., "High Probability" means that there is an approximately 85% likelihood or greater of occurrence.
- Risk analysis (one selected risk for each person on the team). This is a detailed evaluation of each selected risk that should include: a) description of the risk, b) triggers/indicators, and c) description of appropriate risk response strategies--making reference to the PMI's response strategy types** (main ones are: Avoidance, Mitigation, Transference). It is a good idea to structure this section into subsections coorespnding to each of the parts. Bullet point lists are an effective format to list and describe triggers/indicators and risk response strategies. Also, begin this Section with an introduction of what risk analysis and risk response is and mention the PMI PMBoK risk response types**.
*The risk name should be descriptive with enough words that a reader can understand the basic nature of the risk without the need the look at a more detailed explanation. Make sure to avoid the trap of defining a risk as the result of the risk. Focus on the actual condition or event that impacts the project. For example, "delay in field data collection" is not a risk--this is the potential result of one or more risk events.
**PMI Risk Response Strategies include: Acceptance, Avoidance, Mitigation, and Transference. It is OK not to focus on "Acceptance" since this is bacially a "do nothing" response.
Important Notes:
Remember that this assignment relates to the project as a whole--not just specific deliverables as in Assignment #6 . So step back and consider risk events, conditions, and circumstances that could impact any aspect of the project and understand that a single risk could impact work on one or more deliverables.
You may have discovered that the Project Management Institute (PMI) identifies both “negative” and “positive” risk. To simplify your work on this Assignment, deal only with negative risk —those potential risks that could have a negative impact on the project schedule, cost, quality, etc.
The team leader will have the main responsibility for assembling contributions from team members into a final deliverable and submit the assignment for the team.
The risk probability/impact matrix and the risk analysis write-ups on selected risks should be about 1800 to 3000 words in length. As is the case for all written assignments, the word count is a target to give you an idea about the level of detail expected. As a general rule, it is best to keep it concise and as brief as possible while still covering the necessary topics. No points will be deducted for submittals if they exceed the maximum word count by a small amount.
Refer to the grading rubric below for guidelines about the expected format and content of this Assignment.
As in all written assignments, you should include a cover page which includes the following information: a) course number and name, b) assignment number and name, c) your name, d) submittal date. The cover page should also have the full project name and document title ("Risk Management Plan"). Your submitted assignment should be formatted as specified in the Format Quality of this assignment’s rubric below to earn maximum points. As you prepare this assignment, START WITH AN OUTLINE, with sections and subsections that cover the topics above. We recommend that you use the Outline/Heading feature of your word processing software in document preparation. It is expected that you will organize the document into numbered and named sections. It is best practice today, for technical and management documents to use a "decimal" outline numbering scheme (1., 1.1, etc.) as opposed to the older Roman Numeral numbering approach.
Assignment Submittal and Grading
View specific directions for submitting Assignment #7. See Canvas Calendar for due date. Grading information and rubric is below.
This Assignment #7 is worth 70 points. The points awarded from the Instructor’s grading of this Assignment will be given to all members of the team.
The instructor may deduct points if the Assignment is turned in late, unless a late submittal has been approved by the Instructor prior to the Assignment submittal date.
- Skip to content
- Accessibility Policy
- Oracle blogs
- Lorem ipsum dolor
Risk Management Essentials
Organizations benefit from incorporating risk management into their strategic planning, and decision-making at all levels. Effective risk management helps to anticipate and address future circumstances proactively, adapting as needed to support the organization’s objectives.
What is risk management?
The International Organization for Standardization ( ISO ) defines risk as “the effect of uncertainty on objectives”, referring to the potential impact from possible future events on the organization’s ability to achieve its objectives.
An event may be a change or a lack of change – “event” simply means a situation. An event may have beneficial and/or detrimental effects on different objectives. For example, consider “high employee retention” as a potential event. This event is beneficial for operational continuity but may not necessarily support budgetary objectives for cost control.
Optimally, risk management is a continuous cycle of activities to monitor the operating environment and direct how an organization identifies, assesses and responds to or “treats” risks relevant to the organization’s objectives. The preliminary step to engage in effective risk management is to define or select a risk management methodology. At its most basic level, risk management involves these activities:
- Identify potential future events by monitoring internal and external environments.
- Assess the likelihood and impact of these potential future events, resulting in risk scores.
- Treat these risks, using the scores to help prioritize and select actions.
Identify risks
Compile a list of the potential events which may impact your organization’s ability to meet its objectives in the short and long term. External events include either stable or changed customer demand, competitive landscape, supplier products/services cost and availability, geopolitical environment, natural disasters, market forces, technology innovation, standards, economics and regulations. To anticipate external events, monitor legal and industry news for your own industry, plus that of essential suppliers and key customers. To anticipate internal events, stay attuned to your staffing, technology, policies, business-critical processes, acquisitions, go to market strategies, executive direction, and organizational roles and responsibilities.
Assess risks
Evaluate the identified risks to determine their relative importance. Risk is often calculated as a potential event’s likelihood (probability) multiplied by the impact if that event occurs. This means you can address the risk associated with potential events by activities which modify the likelihood, impact, or both:
Using a consistent methodology for scoring risk supports effective risk comparison and treatment planning. While determining likelihood and impact may be somewhat subjective, a defined methodology/ framework that includes thresholds and offers examples for various likelihood and impact levels helps align risk assessment decisions. Modify this basic equation as needed, such as adjusting scores by the priority of the associated organizational objective. Options for risk scoring include:
- Financial : assign monetary values to likelihood and impact
- Quantitative : assign numeric values such as a scale of 1-10 or 1-100 to likelihood and impact
- Qualitative : assign values such as low, medium, high, and critical to likelihood and impact
Treat risks
Focus on selecting and completing actions to improve the probability of achieving objectives, considering the impact of future possible events. Respond to risk using the appropriate treatment or response option:
- Transfer: engage a supplier, such as outsourcing a high-risk function or buying insurance
- Mitigate: implement controls which reduce the likelihood or impact of possible adverse events
- Accept: take no action when risk scores fall within executive risk tolerance guidance
- Avoid: prevent adverse events by excluding the source of risk, such as choosing not to offer certain product types or not to operate in particular markets
- Enhance: implement actions which increase the likelihood or impact of positive potential events
After completing risk treatments, recalculate the risk score using the new likelihood and impact values. The risk level after implementing risk treatments is the “ residual risk ”.
Summary of risk management
Clarify your organization objectives. Monitor the internal and external environments to identify potential future events. Assess risk scores by evaluating the likelihood and impact of possible events, adjusting these scores in the context of organizational controls to calculate residual risk levels. Select and implement risk treatments to bring residual risk in line with executive guidance.
Enterprise risk management should use a continuous feedback loop. For example, you may discover new future possible events that require consideration or that an event’s likelihood/impact score needs to change as a result of applying risk treatments and learning that organizational controls are stronger or weaker than initially anticipated.
References and resources
- EU ENISA Compendium of Risk Management Frameworks
- US NIST Risk Management Framework (RMF)
- US NIST IR 8286 Integrating Cybersecurity and Enterprise Risk Management (ERM) guidance
- ISO 31000:2018 series of international standards provides risk management guidelines
- Enterprise Risk Management Resource Center , including an overview
Nancy Kramer
With over 20 years of experience in managing risk, security, privacy and compliance audits relating to complex business processes and IT systems, Nancy Kramer helps define corporate information security policies and manages compliance and obligation management programs which oversee Oracle’s on-premises and cloud offerings. Nancy also provides thought leadership via engagement with industry organization such as Payment Card Industry Security Standards Council (PCI SSC).
- Analyst Reports
- Cloud Economics
- Corporate Responsibility
- Diversity and Inclusion
- Security Practices
- What is Customer Service?
- What is ERP?
- What is Marketing Automation?
- What is Procurement?
- What is Talent Management?
- What is VM?
- Try Oracle Cloud Free Tier
- Oracle Sustainability
- Oracle COVID-19 Response
- Oracle and SailGP
- Oracle and Premier League
- Oracle and Red Bull Racing Honda
- US Sales 1.800.633.0738
- How can we help?
- Subscribe to Oracle Content
- © 2024 Oracle
- Privacy / Do Not Sell My Info
A practical approach to supply-chain risk management
In the last decade , a number of organizations have been rocked by unforeseen supply-chain vulnerabilities and disruptions, leading to recalls costing hundreds of millions of dollars in industries ranging from pharmaceuticals and consumer goods to electronics and automotive . And multiple government organizations and private businesses have struggled with cybersecurity breaches, losing critical intellectual property due to failures in the supplier ecosystem.
Stay current on your favorite topics
At the heart of these crises is a common theme—the lack of robust processes to identify and successfully manage growing supply-chain risks as the world becomes more interconnected. New threats, such as cyber-ransom attacks, are emerging alongside more traditional and longer-acknowledged supplier risks, such as supplier bankruptcy.
The challenge of supply-chain risk management has been exacerbated by globalization, where even sensitive products like defense systems use raw materials, circuit boards, and related components that may have originated in countries where the system manufacturer did not even know it had a supply chain. This increased complexity has brought with it more potential failure points and higher levels of risk.
Yet progress in addressing these risks has been slow. In our 2010 survey of 639 executives covering a range of regions and industries, 71 percent said their companies were more at risk from supply-chain disruption than previously, and 72 percent expected those risks to continue to rise. In 2018, the United States government stood up multiple agencies and task forces to better address supply-chain risk (including the Critical Infrastructure Security and Cybersecurity Agency in the Department of Homeland Security and the Protecting Critical Technology Task Force at the Department of Defense), and the private sector continues to seek a uniform and proven methodology for assessing and monitoring risks in a way that truly minimizes business disruption.
We believe public- and private-sector organizations have struggled to progress significantly on this topic for several reasons:
- Supply-base transparency is hard (or impossible) to achieve. In modern multi-tier supply chains, hundreds or thousands of suppliers may contribute to a single product. Even identifying the full set of suppliers from the raw-material sources to a final assembled system can require a significant time investment.
- The scope and scale of risks is intimidating. The probability and severity of many risks is difficult to ascertain (How likely are certain weather patterns? How often will a supplier’s employee be careless in cybersecurity practices?), and therefore difficult to address, quantify, and mitigate.
- Proprietary data restrictions impede progress. In complex products, Tier 1 or 2 suppliers may consider their supply chains to be proprietary, limiting visibility at the purchaser or integrating-manufacturer level.
Rather than admiring the problem and these difficulties, we suggest organizations begin to tackle issues in a structured way, cataloging and addressing known risks while improving the organization’s resilience for the inevitable unknown risk that becomes a problem in the future.
Would you like to learn more about our Operations Practice ?
A structured approach to supply-chain risk management.
We recommend that organizations start by thinking of their risks in terms of known and unknown risks.
Known risks can be identified and are possible to measure and manage over time. For instance, a supplier bankruptcy leading to a disruption in supply would be a known risk. Its likelihood can be estimated based on the supplier’s financial history, and its impact on your organization can be quantified through consideration of the products and markets the supplier would disrupt. Newer risks such as cybersecurity vulnerabilities in the supply chain are also now quantifiable through systems that use outside-in analysis of a company’s IT systems to quantify cybersecurity risks.
Organizations should invest time with a cross-functional team to catalog a full scope of risks they face, building a risk-management framework that determines which metrics are appropriate for measuring risks, “what good looks like” for each metric, and how to rigorously track and monitor these metrics. This team can also identify gray areas where risks are hard to understand or define (e.g., tiers of the supply chain where no visibility exists). This analysis can dimensionalize the scale and scope of unknown risks.
Unknown risks are those that are impossible or very difficult to foresee. Consider the sudden eruption of a long dormant volcano that disrupts a supplier you didn’t know was in your supply chain, or the exploitation of a cybersecurity vulnerability buried deep the firmware of a critical electronic component. Predicting scenarios like these is likely impossible for even the most risk-conscious managers.
For unknown risks, reducing their probability and increasing the speed of response when they do occur is critical to sustaining competitive advantage. Building strong layers of defense combined with a risk-aware culture can give an organization this advantage.
Managing known risks
Organizations can use a combination of structured problem solving and digital tools to effectively manage their known-risk portfolio through four steps:
Step 1: Identify and document risks
A typical approach for risk identification is to map out and assess the value chains of all major products. Each node of the supply chain—suppliers, plants, warehouses, and transport routes—is then assessed in detail (Exhibit 1). Risks are entered on a risk register and tracked rigorously on an ongoing basis. In this step, parts of the supply chain where no data exist and further investigation is required should also be recorded.
Step 2: Build a supply-chain risk-management framework
Every risk in the register should be scored based on three dimensions to build an integrated risk-management framework: impact on the organization if the risk materializes, the likelihood of the risk materializing, and the organization’s preparedness to deal with that specific risk. Tolerance thresholds are applied on the risk scores reflecting the organization’s risk appetite.
It is critical to design and use a consistent scoring methodology to assess all risks. This allows for prioritizing and aggregating threats to identify the highest-risk products and value-chain nodes with the greatest failure potential.
Step 3: Monitor risk
Once a risk-management framework is established, persistent monitoring is one of the critical success factors in identifying risks that may damage an organization. The recent emergence of digital tools has made this possible for even the most complex supply chains, by identifying and tracking the leading indicators of risk. For example, a large organization operating in a regulated industry identified 25 leading indicators of quality issues at its plants and contract manufacturers, ranging from structural drivers including geographical location and number of years in operation to operational performance metrics, such as “right first time” and deviation cycle times. These 25 indicators were carefully weighted to develop a quality risk-exposure score, and then tracked on a regular cadence.
Successful monitoring systems are customized to an organization’s needs, incorporating impact, likelihood, and preparedness perspectives. Hence, while one organization may track deviations on manufacturing lines to predict quality issues, another may follow real-time Caribbean weather reports to monitor hurricane risk at its plants in Puerto Rico. Regardless, it is critical to have an early warning system to track top risks to maximize the chances of mitigating, or at the very least limiting, the impact from their occurrence.

Deliver on time or pay the fine: Speed and precision as the new supply-chain drivers
Step 4: Institute governance and regular review
The final critical step is to set up a robust governance mechanism to periodically review supply chain risks and define mitigating actions, improving the resilience and agility of the supply chain.
An effective supply-chain risk-management governance mechanism is a cross-functional risk board with participants representing every node of the value chain. It typically includes line managers who double-hat as risk owners for their function, giving them ownership of risk identification and mitigation. In most cases, the risk board receives additional support from a central risk-management function, staffed with experts to provide additional guidance on identifying and mitigating risks.
An effective board will meet periodically to review the top risks in the supply chain and define the mitigation actions. The participants will then own the execution of mitigation actions for their respective functional nodes. For example, if the board decides to qualify and onboard a new supplier for a critical component, the procurement representative on the board will own the action and ensure its execution.
Additionally, in many organizations the risk board will also make recommendations to improve the agility and resilience of the supply chain, ranging from reconfiguring the supply network, finding new ways of reducing lead times, or working with suppliers to help optimize their own operations. Increasing supply-chain agility can be a highly effective mitigation strategy for organizations to improve their preparedness for a wide range of risks.
Managing unknown risks
Unknown risks are, by their nature, difficult or impossible to predict, quantify, or incorporate into the risk-management framework discussed above for known risks. In our experience, mitigating unknown risks is best achieved through creating strong defenses combined with building a risk-aware culture.
Building strong defenses
Strong defenses, from request-for-proposal (RFP) language to worker training, all contribute to an organization identifying and stopping unknown risks before they affect operations. Exhibit 2 outlines typical layers of defense organizations employ to defend against unknown risks.
Building a risk-aware culture
A risk-aware culture helps an organization both establish and maintain strong defensive layers against unknown risks, as well as respond more quickly when an unknown risk surfaces and threatens operations.
- Acknowledgement. Management and employees need to feel empowered to pass on bad news and lessons from mistakes. This openness fosters an environment where it is okay to voice and deal with issues. Culturally, it is critical that the organization not get discouraged or point fingers when a risk event occurs, and instead works harmoniously towards a rapid resolution.
- Transparency. Leaders must clearly define and communicate an organization’s risk tolerance. Risk mitigation often has an associated incremental cost, and so it is important to align on which risks need to be mitigated and which can be borne by the organization. An organization’s culture should also allow for warning signs of both internal and external risks to be openly shared.
- Responsiveness. Employees need to be empowered to perceive and react rapidly to external change. This can be enabled by creating an ownership environment, where members feel responsible for outcome of actions and decisions.
- Respect. Employees’ risk appetites should be aligned with an organization, so that individuals or groups do not take risks or actions that benefit themselves but harm the broader organization.
The road ahead
Global supply chains are irreversible, as are the supply-chain risks that globalization has brought with it. Our experience suggests that it is critical for organizations to build robust programs for managing both known and unknown supply-chain risks. Leaders should also recognize that risk management is not merely about setting up processes and governance models, but also entails shifts in culture and mind-sets. By employing these approaches, organizations increase their chances of minimizing supply-chain disruptions and crises, while capturing the full value of their supply-chain strategies.
Tucker Bailey and Edward Barriball are partners in McKinsey’s Washington, DC office. Arnav Dey is an engagement manager in the Boston office, and Ali Sankur is a senior practice manager in Chicago.
Explore a career with us
Related articles.

The route to no-touch planning: Taking the human error out of supply chain planning

The automation imperative
Right product, right time, right location: Quantifying the semiconductor supply chain
- Securing Risk Management
Export and Import User Assignment Groups
You can export user assignment groups from a source instance to a file, then import them from the file to a second instance.
- When you export groups, security assignments configured for them aren't exported with them. A user who subsequently imports them automatically becomes their owner in the destination environment, and could configure additional security for them in that environment.
- The import job fails if the file contains a group whose name matches that of a group already existing in the destination instance.
- Navigate to Risk Management > Risk Management Data Security. This opens the User Assignment Groups page.
- Click the check boxes for the groups you want to export. You can select one or multiple groups.
- Select Actions > Export User Group. A message presents a job ID. Note the ID, then close the message.
- Click the Monitor Jobs button to navigate to the Monitor Jobs page.
- Locate the row displaying the job ID you noted.
- When the status displayed in that row reaches Completed, click the Download icon.
- A file-download window offers you options to open or save the export file. Select the Save option. In a distinct save-as dialog, navigate to the folder you want to save the file in.
- From the User Assignment Groups page, select Actions > Import User Group.
- In an Import User Group page, select a file that contains groups you want to import. Click Browse, navigate to the location of the file, and select the file name. It consists of the phrase "User_Groups" followed by a number, with a json file extension. That file name then populates the File field on the Import page.
- Click the Submit button. Again, a message presents a job ID. Note the ID, then close the message.
- Click the Monitor Jobs button to navigate to the monitor jobs page. Locate the row displaying the job ID you noted, and confirm that it reaches the Completed state.
Course offered by
PBP 402: Understanding Program Administrator Contracts and Submissions
Add to Cart

Gain skills to successfully interpret the unique features of program administrator contracts and master submissions. By completing PBP 402, you’ll be able to effectively navigate the program submission process, understand the details of program administrator contracts, and master the intricacies of contract and agency law so you can more effectively collaborate with key stakeholders.
Skills You’ll Gain
Ready-Made Career Skills
- Contract Law
- Strategic Collaboration
- Stakeholder Management
- Business Decision Making
- Critical Thinking
Assignments

Exam Prep Tools
PBP 402 comes with proven, comprehensive study materials to help you take The Institutes Designations' exam with confidence:
- Printable Study Outline: Perfect for taking notes, the printable study outline has key points for each assignment and review questions (and answers!) to help you test your knowledge as you move through the course.
- Practice Quizzes: Quickly see where your knowledge gaps are with online practice quizzes for each assignment and for the full course. You can take them as many times as you want!
- Simulated Exam: Designed to give you the full experience of your final exam, the simulated exam is a timed exam that you can take only once. It mimics the exam structure and level of questions you’ll find on the actual exam. Students who take their Institutes simulated exam pass their exams at higher rates than students who don’t.
- Discussion Boards: Better understand how concepts you’re learning apply to real-life professional experiences by connecting, gaining tips, and sharing best practices with other individuals in your field.
- Flashcards: Test yourself on key terms with flashcards that help you fit studying into your busy schedule.
Try PBP for Free!
Sample PBP in just 30-45 minutes to make sure it's the right fit for you.

Online PBP Micro-Course
- Unique Features of PA-Insurer Contracts
- Components of a Program Submission
- Strategic Keys to Mergers and Acquisitions
- Matching IT With Strategy

- Yes! PBP 402 gives you credit toward the Program Business Professional™ (PBP™) designation.
- PBP 402 typically takes students 6-8 weeks to complete.
- Virtual exams are timed. You will have 65 minutes to complete 50 questions.
- In addition to the online course, you have access to a printable study outline, practice quizzes, a simulated exam, discussion boards, and flashcards.
- Quarter 1: January 15 – March 15
- Quarter 2: April 15 – June 15
- Quarter 3: July 15 – September 15
- Quarter 4: October 15 – December 15
Trustwave SpiderLabs Exposes Unique Cybersecurity Threats in the Public Sector. Learn More
Experiencing a security breach?
Get access to immediate incident response assistance.
- AMERICAS +1 855 438 4305
- EMEA +44 8081687370
- AUSTRALIA +61 1300901211
- SINGAPORE +65 68175019
Eliminate active threats with 24/7 threat detection, investigation, and response.
Maximize your SIEM investment, stop alert fatigue, and enhance your team with hybrid security operations support.
Advance your cybersecurity program and get expert guidance where you need it most.
Test your physical locations and IT infrastructure to shore up weaknesses before exploitation.
Prevent unauthorized access and exceed compliance requirements.
Stop email threats others miss and secure your organization against the #1 ransomware attack vector.
Prepare for the inevitable with 24/7 global breach response in-region and available on-site.
Mitigate risk of a cyberattack with 24/7 incident and health monitoring and the latest threat intelligence.
- Financial Services
- Manufacturing
- Data Privacy
- Trustwave Blog
- SpiderLabs Blog
- Document Library
- Video Library
- Analyst Reports
- Webinar Replays
- Case Studies
- Trials & Evaluations
- Security Advisories
- Software Updates
Gartner ® Security & Risk Management Summit
June 3-5, 2024 | national harbor, md, it’s not offensive or defensive security. it’s both.
Come Visit Us at Booth #659 in the Security Operations and Analytics Solution Village & Hear Us Speak
Connect with Trustwave - a globally recognized defender known for reducing cyber risk, fortifying organizations against disruptive and damaging cyber threats, and decreasing the likelihood of attacks in your environment - at Gartner ® Security and Risk Management Summit this June. Maximize your experience with Trustwave's cybersecurity expertise!
Still need a pass? Use code: SEC30EDC for $375 off the standard pass price.
Hear from trustwave security experts.
Attend Trustwave’s Executive Strategy Session
Attend Trustwave’s Solution Provider Session
Request a Meeting with our Trustwave Experts
Schedule a time to meet with one of our security executives onsite to discuss everything from offensive security to FedRAMP at the show.
Won't be at the show, but will be in the area? We'd still love to meet with you!

Damian Archer
VP, Trustwave SpiderLabs
Talk to Damian about all things Offensive Security. With nearly 20 years of experience in testing for the weaknesses that technology alone cannot find and guiding security teams on the right security strategies for their environment. Work with Damian to boost your cyber resilience and fortify your approach with Trustwave's Offensive Security solutions. Aligned with Gartner's CTEM program, our proactive approach focuses on identifying and mitigating vulnerabilities before they become threats. Tap into our holistic portfolio for penetration testing, vulnerability scanning, threat intelligence as a service, database configuration, and red & purple teaming - all supported by CREST-certified methodology to ensure robust vulnerability identification and remediation.

Jesse Emerson
VP, Systems Engineering, Trustwave
Curious about best-of-breed versus best of platform ecosystems? Meet Jesse Emerson, a seasoned cybersecurity expert with 25 years of experience. With expertise in threat intelligence, operations, consulting, and Managed Detection & Response, Jesse can guide you through the benefits of transitioning to a best-of-breed platform, helping you mitigate threats, maximize your SIEM investment, and empower your security teams with 24/7 threat detection and response.

Bill Rucker
President, Trustwave Government Solutions
Interested in FedRAMP? Meet with Bill. Trustwave's Government Fusion platform recently received the “In Process Program Management Office (PMO) Review" designation by the Federal Risk and Authorization Management Program (FedRAMP). Trustwave Government Fusion is the platform used for Trustwave's MDR and Co-Managed SIEM/SOC (3SIEM) services designed for Federal agencies and clients who require US-only based personnel in a government community cloud environment.

Keith Ibarguen
Senior Vice President of Engineering
If it's additional details on the "how" and "why" behind our solutions, then look no further than new Trustwave product engineering expert, Keith. With over 25 years of experience, including roles as Chief Product Officer and Chief Engineer, Keith brings extensive expertise to our security team and drives innovation to enhance our product development. Tap into Ketih's insights on what - exactly - Trustwave can do to help you further your security posture.
Trustwave Schedule of Events
Trustwave solution provider session, trustwave: threat hunting evolution and critical infrastructure.
Attackers are hidden in many environments, including nation-state campaigns such as Volt Typhoon that are aggressively targeting U.S. critical infrastructure. The evolution of threat hunting demands a continuous process to thwart progressively advanced and emerging tactics. Hear Bobby Thompson, Deputy Associate Director of Threat Hunting at CISA; Keith Ibarguen, former MITRE engineer supporting intelligence and law enforcement and currently head of engineering at Trustwave; and Bill Rucker, head of government solutions at Trustwave, discuss the implications for public and private sectors.
Register for this session through the conference navigator here .

Bobby Thompson
Deputy Director, CISA

SVP Engineering, Trustwave
Trustwave Speakers

As the Deputy Associate Director of the Threat Hunting subdivision within CISA's Cybersecurity Division, Robert Thompson plays a pivotal role in safeguarding U.S. infrastructure against evolving cyber threats. Leading a multidisciplinary team of incident responders, intelligence analysts, and malware experts, Robert orchestrates strategic initiatives aimed at proactively identifying and neutralizing potential threats.
Bill Rucker is President of Trustwave Government Solutions and brings over 25 years of business, industry and public sector expertise gained from executive-level positions within IT and Information Security industries. Based in Reston, Virginia, Bill is responsible for providing the critical leadership and vision to drive Trustwave Government Solutions operations, sales and business development effort for the federal government.
Keith Ibarguen is the Senior Vice President of Engineering at Trustwave, where he leads the company’s engineering product development and SpiderLabs research. With over 25 years of extensive experience in software, cybersecurity, and leadership, Keith has dedicated his career to tackling complex challenges and translating vision into tangible results.
Stay Informed
Sign up to receive the latest security news and trends straight to your inbox from trustwave..
- Leadership Team
- Our History
- News Releases
- Media Coverage
- Global Locations
- Awards & Accolades
- Terms of Use
- Privacy Policy
Copyright © 2024 Trustwave Holdings, Inc. All rights reserved.

COMMENTS
1. Prepare supporting documentation. You'll want to review existing project management documentation to help you craft your risk management plan. This documentation includes: Project Charter: among other things, this document establishes the project objectives, the project sponsor, and you as the project manager.
The steps to make a risk management plan are outlined below. 1. Risk Identification. Risk identification occurs at the beginning of the project planning phase, as well as throughout the project life cycle. While many risks are considered "known risks," others might require additional research to discover.
Download the Blank Project Risk Management Plan for Microsoft Word. Use this blank template to create your own project risk management plan. The template includes sections to ensure that your team covers all areas of risk management, such as risk identification, risk assessment, and risk mitigation.
The six risk management process steps that we've outlined below will give you and your organization a starting point to implement or improve your risk management practices. In order, the risk management steps are: Risk identification. Risk analysis or assessment. Controls implementation.
Evaluate and assess the consequence, impact, and probability of each potential risk. 3. Assign roles and responsibilities to each risk. 4. Come up with preventative strategies for each risk. 5. Create a contingency plan in case things go really wrong. 6. Measure your risk threshold and work with project stakeholders.
ISBN:978-1-933890-38-8 Published by: Project Management Institute, Inc. 14 Campus Boulevard Newtown Square, Pennsylvania 19073-3299 USA. Phone:+610-356-4600
The risk management process includes risk identification and risk assessment. During an assessment, the project manager uses standard risk tools and quality data to help the team better avert later problems, manage the project cost, and keep project work on schedule. Risk assessment is the process by which the identified risks are ...
Project management software can help you keep track of risk. ProjectManager is online software that helps you identify risks, track them and calculate their impact. With our Risk view, you can make a risk list with your team and stay on top of all the risks within your project. Write a description, add tags, identify a resolution, mark impact ...
Abstract. Risk Analysis and Management is a key project management practice to ensure that the least number of surprises occur while your project is underway. While we can never predict the future with certainty, we can apply a simple and streamlined risk management process to predict the uncertainties in the projects and minimize the ...
Introduction to The Culminating Project (Capstone Course) Module 1 • 2 hours to complete. Learning objectives for the capstone project. What's included. 5 readings. Show info about module content. 5 readings • Total 160 minutes. Implementing a Risk Management Framework • 15 minutes. Assignment Overview • 10 minutes.
Risk management is the process of identifying, assessing and controlling financial, legal, strategic and security risks to an organization's capital and earnings. These threats, or risks, could stem from a wide variety of sources, including financial uncertainty, legal liabilities, strategic management errors, accidents and natural disasters.
When creating your risk matrix template, you'll first identify your scale of severity, which you'll place in the columns of your matrix. The scale of severity measures how severe the consequences will be for each risk. In a five-by-five matrix, there are five levels in your scale of severity. Negligible (1): The risk will have little ...
Overview. Project risk management provides a structured means to identify and manage risks within projects. The goal of project risk management is to "increase the probability and impact of positive events and decrease the probability and impact of negative events in the project" (Project Management Institute, 2009, p. 4). Risks can ...
Step 1: Identify the change. This could be a problem or a potential risk. Step 2: Brainstorm possible consequences of the trend. Step 3: Brainstorm the secondary or "second-order" consequences related to the "first-order" consequences you identified earlier.
There are options on the tools and techniques that can be seamlessly incorporated into a business' process. The four common risk assessment tools are: risk matrix, decision tree, failure modes and effects analysis (FMEA), and bowtie model. Other risk assessment techniques include the what-if analysis, failure tree analysis, and hazard ...
A risk assessment matrix is a visual chart that prioritizes and tracks project risks. Of more than a dozen different categories of risk, the four most important for a project manager to account for are management, organizational, technical, and external risks. Building a risk assessment matrix should be a core element of your overall approach ...
Project risk management is. continuous process of identifying, analysing, prioritising and mitigating risks that threaten. projects likelihood of success in terms of cost, schedule, quality, safety and technical performance. Organisations and owners often consider project risk management activities as "nice to have" on a project rather than ...
An enterprise risk management framework is a system by which you assess and mitigate potential risks. The framework varies by industry, but most include roles and responsibilities, a methodology for risk identification, a risk appetite statement, risk prioritization, mitigation strategies, and monitoring and reporting.
The team members will carry out and document a risk analysis for their selected risk. In summary, the Risk Management Plan you submit should cover the following main parts: Cover page with prominent title and all necessary information identifying the course, assignment, author, and date. The main title of the document should be "RISK MANAGEMENT ...
Optimally, risk management is a continuous cycle of activities to monitor the operating environment and direct how an organization identifies, assesses and responds to or "treats" risks relevant to the organization's objectives. The preliminary step to engage in effective risk management is to define or select a risk management methodology.
Risk assessment and management was established as a scientific field some 30-40 years ago. Principles and methods were developed for how to conceptualise, assess and manage risk. These principles and methods still represent to a large extent the foundation of this field today, but many advances have been made, linked to both the theoretical ...
1. Step 2: Build a supply-chain risk-management framework. Every risk in the register should be scored based on three dimensions to build an integrated risk-management framework: impact on the organization if the risk materializes, the likelihood of the risk materializing, and the organization's preparedness to deal with that specific risk.
Q-Chat. Study with Quizlet and memorize flashcards containing terms like what is risk?, What is risk management?, If a case involves a plaintiff and a defendant, it is generally called and more.
This assignment will firstly be looking at outcomes as a form of risk, along with and explanation on risk control and analysis on Eskom's risk steps, procedures or actions. Secondly, this assignment will be addressing enterprise risk management in relation to the King reports and will look at the key drivers of change.
Management document from University of Zambia, 5 pages, Bande Ngulube University of Zambia MAF6211: Project Risk and Quality Management Dr. Maja Zelihic March, 2024 Module 3 Assignment fSOFT SKILLS FOR EFFECTIVE PROJECT MANAGEMENT 2 Introduction Soft skills are the processes of managing and working with people.
Upcoming Assignment in Saudi Arabia, Overseas. Assignment Details: 1. Assignment ID: AS60677. 2. Nature of Assignment: ERM (Enterprise Risk Management)
To export user assignment groups: Navigate to Risk Management > Risk Management Data Security. This opens the User Assignment Groups page. Click the check boxes for the groups you want to export. You can select one or multiple groups. Select Actions > Export User Group. A message presents a job ID.
The Maurice R. Greenberg School of Risk Management, Insurance and Actuarial Science (GSRM) has a rich history and tradition. Initially formed as the Insurance Society of New York in 1901, it became the School of Insurance in 1947 and the College of Insurance (TCI) in 1962. GSRM evolved from the merger of TCI and St. John's University in 2001.
PBP 402 comes with proven, comprehensive study materials to help you take The Institutes Designations' exam with confidence: Printable Study Outline: Perfect for taking notes, the printable study outline has key points for each assignment and review questions (and answers!) to help you test your knowledge as you move through the course. Practice Quizzes: Quickly see where your knowledge gaps ...
With over 25 years of extensive experience in software, cybersecurity, and leadership, Keith has dedicated his career to tackling complex challenges and translating vision into tangible results. Join Trustwave at the 2024 Gartner Security & Risk Management Summit. Visit us at booth #659 to discuss the exploding threat landscape, modern security ...