

Home / Resources / ISACA Journal / Issues / 2022 / Volume 3 / Better Cybersecurity Awareness Through Research
Better cybersecurity awareness through research.

In the last few years, information security professionals have faced tremendous challenges. Just in 2021, there were more than two billion malware attacks and trillions of intrusion attempts. 1 Ransomware attacks alone have increased by 151 percent compared with 2020. 2 In fall of 2020, Cybersecurity Ventures estimated worldwide cybercrime costs would reach US$6 trillion annually by the end of 2021, ransomware damage costs would rise to US$20 billion, and an enterprise would fall victim to a ransomware attack every 11 seconds during the year. 3 The European Union introduced 474 separate enforcement actions for EU General Data Protection Regulations (GDPR) violations, starting from the time enforcement of the GDPR began in 2018 through December 2020, with fines totaling US$312.4 million. 4
Cybercrime is projected to worsen due to the rapid changes resulting from the COVID-19 pandemic. Thousands of organizations allowed employees to continue working from home throughout 2021, and there are indications that many will permit hybrid work indefinitely. Remote work opens a Pandora’s box of issues for organizations trying to maintain some semblance of security. Cybersecurity firm Malwarebytes reported in an August 2020 survey that remote workers caused security breaches in 20 percent of the organizations it surveyed. 5 Although the need for security awareness training for remote employees is pressing, many organizations have been finding it more difficult to implement than providing established training in a centralized workplace.
Importance of Awareness and Training
One study conducted with participation from more than 5,000 organizations around the world discovered that organizations are becoming more aware of the role of their employees play in information security incidents. Survey data collected as part of the study reported that 52 percent of organizations indicated employees were their biggest weakness in IT security, with their actions putting the business and the organizational information security strategy at risk. Forty-three percent of the organizations polled considered deployment of more sophisticated software an effective way to safeguard themselves against evolving threats ( figure 1 ). Offering staff training was the second most popular method for safeguarding organizations according to the survey, closely followed by increasing internal IT or IT security staff. 6

Similar to those findings, Verizon’s 2021 Data Breach Investigations Report states that nearly 85 percent of incidents and data breaches from 2020 were attributable to human error. 7 Additional data from the field comes from the Willis Towers Watson Cyber Claims Analysis Report , 8 which reveals that clients filed close to 1,200 data breach claims in nearly 50 countries from 2013 to December 2019. The report identifies human error such as employees clicking on links in phishing emails or replying to spoofed emails as the most common root causes of breaches (figure 2) . The costliest events were typically those where the threat actor impersonated a chief executive officer (CEO) or senior manager. The most frequently employed social engineering tactic was impersonation of a vendor or supplier. All these things could easily be prevented through employee education and training, the report concludes. 9

According to a white paper from Osterman Research, employees who received cybersecurity training demonstrated a significantly improved ability to recognize potential threats, earning the respect of their organization’s security teams. 10 By applying a model that Osterman developed to data acquired through a survey of 230 individuals in North American organizations, the researchers concluded that smaller organizations could achieve a return on investment (ROI) of nearly 70 percent and larger organizations could achieve an ROI of 500 percent, on average, by implementing security awareness training. 11
Deficiencies in Current Learning Techniques
The importance of cybersecurity awareness is underscored by reports of incidents attributed to careless human behavior and lack of training, which continue to rise at alarming rates, despite commitments from small and large organizations to increase staffing in information security support groups and expand cybersecurity technology budgets. Many organizations either underestimate the effort needed to educate a workforce or do not realize that their current cybersecurity training approaches are ineffective.
KnowBe4’s 2021 State of Privacy and Security Awareness Report notes that a large percentage of surveyed employees did not feel confident that they could identify a social engineering attack, recognize the warning signs that their computers were infected with malware or describe to their senior management the security risk associated with employees working from home. 12 Government, healthcare and education employees were the least aware of various social engineering threats.
Much of the current literature and research on improving cybersecurity awareness training is focused on how to develop an effective program or how to identify the components missing from a program. This is a great start, but it is not enough. For example, the 2021 SANS Security Awareness Report: Managing Human Cyber Risk 13 identifies which needs to prioritize while building an effective program, such as having several full-time employees focused on changing behavior, providing job titles commensurate with responsibilities, ensuring leadership support, fostering collaboration among departments and engaging people with specialized communication skills to strike the right balance by not being too technical or lengthy with organizational messaging.
Conspicuously missing from many current reports, including the ones already mentioned, are inquiries into whether both the training material content and its delivery are inherently flawed. Something is lacking in the current environment. Could it be related to the technique, or lack of it, in delivering cyberawareness material within organizations? Are some approaches more effective? Do people learn, absorb and remember better when material is presented a certain way?
For example, the SANS Security Awareness Maturity Model (figure 3) gives organizations the ability to compare and contrast the maturity level of their security awareness program and helps them focus on areas that need improvement. 14 However, the model could be made even more helpful if it included references to how organizations can apply research on how humans learn and the most effective methods of content delivery. Organizations that do this should be rated higher on the maturity scale.

Many organizations either underestimate the effort needed to educate a workforce or do not realize that their current cybersecurity training approaches are ineffective.
Models and frameworks are a great start, but developing a structured awareness program with tools for metrics monitoring only solves part of the puzzle. Organizations also need research-based information on how to create inspiring content, along with techniques for delivering it effectively.
Better Ways to Learn
Review of the literature on how humans learn and retain information reveals interesting techniques and practices that are applicable to cybersecurity awareness and training campaigns. Organizations looking to maximize return on investment when it comes to cyberawareness would do well to take a closer look at adopting some of the following into their own learning systems.
Distributed vs. Massed Practice There may be benefits to moving away from training assignments that offer a single, continuous training session. Offering an initial fact-sharing or concept-learning session followed by periodic reviews may be a better approach. Research indicates that providing the same information after the initial session in smaller chunks and at a carefully chosen frequency reinforces learning. 15 Short, spaced-out study sessions lead to meaningful learning, whereas cram sessions often lead to nothing deeper than memorization.
In a 2019 interview, a researcher at Dartmouth College, Hanover, New Hampshire, USA, said that studying information or practicing a task just once is not good enough. 16 For permanent learning, the timing of the review or practice of the information is critical. Distributed practice refers to studying the material to be learned at a specified time after the original learning event. Massed practice, on the other hand, refers to study sessions that happen right after the original learning event.
Research shows that distributed lessons improved elementary school children’s ability to generalize their learning 17 and that when faced with unique situations, college students who participated in a spaced review following the primary lecture adapted better than students who just received a massed online review. 18
Conspicuously missing from many current reports… are inquiries into whether both the training material content and its delivery are inherently flawed.
Distributed reviews of the same information make the technique effective. It is not the same as spreading different chunks of material over several sessions or days. Organizations that comprehend the advantages of distributed practice over massed practice may choose to drop the idea of holding annual or quarterly cybersecurity awareness training events—that is, cram sessions—that take all day or multiple days, usually with exercise sessions on learning objectives at the end. A better approach may be to opt for short sessions that introduce the idea of a single cybersecurity concept, say phishing, followed by defined, specific breaks of days or weeks before the same concept is revisited in the form of multiple follow-up sessions or a set of spaced-out exercises emailed to the participants. The examples in figure 4 illustrate the differences between the two approaches.

Massed practice, or the boot camp approach, may work to some extent for achieving a short-term goal such as passing an exam. However, for employees to achieve long-term retention of learned concepts—something that is of vital importance to organizations when it comes to cybersecurity—distributed practice is a superior method of learning.
Reconsolidation Tweaking a distributed practice approach to include memory reconsolidation can make training more effective. Although distributed practice involves presenting the same information, a small alteration of facts or measures reinforces the training. The key is to combine distributed practice with subtle changes in the follow-ups.
Making slight changes to the study material or task during practice sessions may help trainees master a skill much more quickly than they would without alteration. The results of a study by researchers at Johns Hopkins University, Baltimore, Maryland, USA, lends credence to the theory of reconsolidation by showing that motor skills are strengthened when existing memories are recalled and modified with new knowledge. 19 The researchers found that the gains in performance such as speedier and more accurate task completion nearly doubled in the experimental group given an altered second session, compared to a group that repeated the same task without any change. The researchers concluded that a trainee learns more and learns faster by practicing a subtly altered version of a task than by practicing the same thing multiple times in a row. However, the changes in the training must be subtle because if the modification renders the task noticeably different, trainees do not realize the desired gain.
The science behind reconsolidation is still subject to debate, but results so far offer a glimpse of the possibilities for using it to strengthen learning. Consolidation refers to how the human brain learns new material. Retrieving that material after first exposure but before the learner has had a chance to forget it reactivates the learning process. It theoretically gives the learner an opportunity to weaken or strengthen memory retention. It appears possible to disrupt or impair retention by providing conflicting or incorrect information after an initial learning event or to strengthen it by providing correct information with slight updates. The updates might help to close gaps in the initial learning experience, thereby strengthening it.
For example, when using the distributed practice approach to teach employees about phishing, it might be beneficial to use the principles of reconsolidation in the follow-up sessions by subtly changing the phishing scenarios in the exercises. Each social engineering red flag ( figure 5 ) in the set might be used to introduce a slight variation to the initial learning session to reinforce the main learning subject of phishing.

The Value of Case Studies
Nothing raises cybersecurity awareness more effectively than showing the aftermath of real breaches in targeted enterprises and highlighting how vulnerable all organizations are to cyberthreats. One well-known and effective training technique is the use of case studies in problem-based learning (PBL) scenarios. The results of multiple studies indicate that PBL has a significant positive effect on students’ skill development and knowledge retention. 20 The US National Center for Case Study Teaching in Science polled more than a hundred university faculty members who had been trained to use case studies and found that more than 90 percent reported that students who were taught using sample cases learned new ways to think about issues and took an active part in the learning process. 21
Key characteristics of a good discussion case include being concise; being somewhat controversial to grab attention, but maintaining balance and not getting carried away; having memorable characters act out the case study with dialogue; ensuring that the subject material is relevant to the learners; presenting a dilemma to be solved; being contemporary rather than purely historical; using real rather than fabricated scenarios and having clear learning objectives.
Additional research expands on the qualities that make a good case study, 22 including being pertinent to the class and learning objectives, 23 being connected to theory and practice 24 , 25 , 26 and telling a story containing some form of ambiguity. 27
Information security officers struggling to sell internal leadership and stakeholders on abstract concepts such as segregation of duties (SoD), change management and other internal IT controls might find that case studies based on events in the news are effective tools to get their message across.
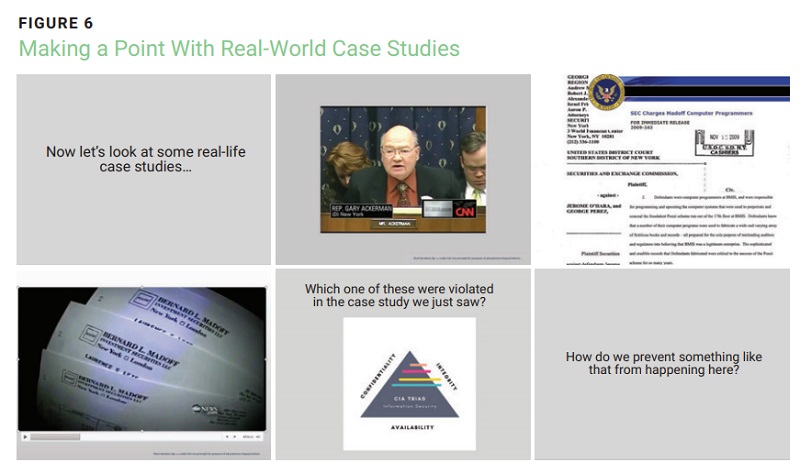
For example, a complete case study on the Bernard Madoff financial scam—complete with short news video clips and government press releases on IT personnel being charged with crimes—helped illustrate complex topics in an easy-to-understand format for the leadership at a not-for-profit and get its buy-in for implementing organizationwide checks and balances ( figure 6 ).
Learning From Incidents and Accidents Industrial accidents have been studied and analyzed over many decades, and learning from these incidents that inevitably occur in large systems—especially ones that pose a danger to human safety, such as those that occur with chemicals and other hazardous materials—has always been a top priority. By establishing a framework for learning from incidents, an organization can reduce risk and minimize loss and, thus, become a more reliable organization over time. Learning from incidents and accidents fosters a culture of continuous organizational improvement that will reduce incident severity and risk of disaster. Organizations that do not learn from past errors are doomed to repeat them, for example:
- The US National Aeronautics and Space Administration (NASA) lost two space shuttles, the Challenger in 1986 and the Columbia in 2003. The Columbia Accident Investigation Board noted that “[T]he causes of the institutional failure responsible for Challenger have not been fixed. Second, the Board strongly believes that if these persistent, systemic flaws are not resolved, the scene is set for another accident.” 28
- Failure to learn was among the causes for the Deep Water Horizon disaster. British Petroleum had experienced several major incidents before— specifically the Grangemouth refinery incident in Scotland, the Texas City refinery explosion in the US state of Texas, and the Prudhoe Bay leaks in the US state of Alaska. 29
Incidents, however, do not always have to end in disaster. 30 A system can be put in place to control their severity. It is important to recognize that, in most cases, a disaster results from a chain of events going undetected rather than from a standalone, spontaneous event. If an effective learning system could detect the incident, the chain of events could be broken and a disaster could be prevented.
By establishing a framework for learning from incidents, an organization can reduce risk and minimize loss and, thus, become a more reliable organization over time.
In addition to implementing systems that enable learning from incidents, technology organizations should investigate the use of mitigating systems, including a sort of kill switch that could potentially prevent an incident from becoming a disaster. One IT organization that suffered a series of ransomware events used data security software to study the data from the incidents and determined that all the attacks originated from end-user workstations and spread to network shares before showing up on assets of higher value. 31 A mitigating system using the data security platform was soon put in place so that ransomware activity detected at the end-user’s virtual local area network (VLAN) would automatically disable the user account the questionable activity was operating under and close ports to other parts of the network. Other examples of mitigating systems are automatic blocking of remote Internet Protocol (IP) addresses based on scanning activity detected by a security information and event management (SIEM) tool and automatic disabling of user accounts flagged as exhibiting unusual activity by other security tools.
In IT, especially cybersecurity, distilling the data collected from past incidents and accidents into actionable, effective training remains a challenge.
Organizations other than typical industrial factories have already adopted techniques to prevent incidents from descending into chaos and disaster. In the mid-1980s, researchers at the University of California, Berkeley, USA, began taking a closer look at why some organizations, despite their complex and risk-prone environments, continued to succeed in avoiding major safety incidents. 32 The term high reliability organizations (HRO) soon evolved to refer to this category of organizations. Researchers discovered that HROs use several tools and initiatives to learn from safety incidents, some of which could be adapted for use in healthcare, for example. 33 The researchers conducted a systematic review to identify effective learning tools that multidisciplinary teams in healthcare could adapt and use following a patient safety incident. IT-reliant organizations are on the cusp of facing major disasters; the attempted poisoning of city water in Oldsmar, Florida, USA, 34 and the Colonial Gas pipeline ransomware event are early warning signs. 35 If IT does not invest in learning systems championed by industries other than IT over the years, catastrophes will become inevitable.
Sometimes lessons are not learned. This can happen for various reasons, including the handling of information within and between organizations in a way that discourages dissemination of lessons learned from emergencies, training and educational programs, placing an unhealthy emphasis on what to learn rather than how to learn and ingrained organizational cultures preventing learning. 36
Recommendations for avoiding these traps include creating an official policy for identifying and learning lessons, developing techniques to identify and learn lessons from mock exercises and major emergencies, and engaging in an ongoing process of cross-training so that diverse teams can fully develop a broad understanding of how other teams think and operate under pressure. Data from the incident learning system can be applied in future training sessions. 37
Safety-conscious industrial organizations, often under the watchful eye of regulators, have long prioritized collecting data about accidents and feeding them into learning systems that are then converted to simulations used in training. Although the typical IT organization may not have as many situations that could affect human safety as other industry sectors, IT in general is known for having a culture of investigating failures and conducting root-cause analyses. However, in IT, especially cybersecurity, distilling the data collected from past incidents and accidents into actionable, effective training remains a challenge.
For example, one organization responded to the challenge by converting root-cause analysis of its actual cybersecurity incidents into animated training simulations that were then emailed out as quarterly or annual retrospectives (figure 7) . IT personnel received a more detailed tear-down of the incidents using the same animation medium.

Despite investing in training, technology and technical know-how and expanding their budgets to support ever-increasing information security operational costs, organizations are still falling victim to cyberattacks every day. These attacks show no sign of slowing down. Checkpoint research reported 900 weekly attacks per organization in 2021, a 50 percent jump compared with 2020. 38
Organization leaders need to realize that cybersecurity awareness is not just about training nontechnical employees about phishing and online scams and then arming them with better security practices. Cybersecurity awareness also plays a vital role in changing an organization’s culture for the better by changing certain behaviors (e.g., leaky change management practices; arming people with the data to make better decisions; providing the confidence and means to challenge unethical behavior, such as a senior manager falsifying disaster-recovery test results). The server left unpatched, the files left unprotected and the critical security feature, which took nine months to roll out, reflect organizational cultures that are in dire need of reform.
To create lasting change, organizations must not only build the components of an effective cyberawareness program, but also improve the quality of their content and the mechanisms for its delivery. Informed by research concerning how humans learn, organizations can adopt the most effective techniques to aid the developers of their training systems. With the right tools, developers can tailor content that improves employees’ learning speed and information retention and help employees adapt quickly to changing environments and situations, even during times of heavy workload and high pressure.
Author’s Note
The information and views expressed in this article are those of the author and do not constitute any official position, policy or pronouncement of his employer.
1 SonicWall, 2021 SonicWall Cyber Threat Report , USA, 2021, https://www.sonicwall.com/resources/white-papers/2021-sonicwall-cyber-threat-report/ 2 Ibid. 3 Morgan, S.; “Cybercrime to Cost the World $10.5 Trillion Annually by 2025,” Cybercrime Magazine , 13 November 2020, https://cybersecurityventures.com/hackerpocalypse-original-cybercrime-report-2016/ 4 KnowBe4 , 2021 State of Privacy and Security Awareness Report , USA, 2021, https://www.knowbe4.com/hubfs/2021-State-of-Privacy-Security-Awareness-Report-Research_EN-US.pdf 5 Malwarebytes, Enduring From Home: COVID-19’s Impact on Business Security , USA, 2020, https://www.malwarebytes.com/resources/files/2020/08/malwarebytes_enduringfromhome_report_final.pdf 6 Kaspersky, “The Human Factor in IT Security: How Employees Are Making Businesses Vulnerable From Within,” Kaspersky Daily, https://www.kaspersky.com/blog/the-human-factor-in-it-security/ 7 Verizon, 2021 Data Breach Investigations Report , USA, 2021, https://enterprise.verizon.com/content/verizon-enterprise/us/en/index/resources/reports/2021-data-breach-investigations-report.pdf 8 Willis Towers Watson, Cyber Claims Analysis Report , United Kingdom, 2020, https://www.wtwco.com/en-NZ/Insights/2020/07/cyber-claims-analysis-report 9 Ibid. 10 Osterman Research, Inc., The ROI of Security Awareness Training , USA, August 2019, https://www.mimecast.com/resources/analyst-reports/osterman-research---the-roi-of-security-awareness-training/ 11 Ibid. 12 Op cit KnowBe4 13 DeBeaubien, ; L. Spitzner; H. Xu; N. Zhang; 2021 SANS Security Awareness Report: Managing Human Cyber Risk , USA, 2021, https://www.sans.org/security-awareness-training/resources/reports/sareport-2021/ 14 SANS, “Measuring Program Maturity,” https://www.sans.org/security-awareness-training/resources/maturity-model/ 15 Carpenter, K.; N. J. Cepeda; D. Rohrer;H. K. Kang; H. Pashler; “Using Spacing to Enhance Diverse Forms of Learning: Review of Recent Research and Implications for Instruction,” Educational Psychology Review , vol. 24, iss. 3, http://www.jstor.org/stable/43546797 16 Francisco, A.; “Ask the Cognitive Scientist: Distributed Practice,” Digital Promise, 8 May 2019, https://digitalpromise.org/2019/05/08/ask-the-cognitive-scientist-distributed-practice/ 17 Vlach, H.; C. Sandhofer; “Distributing Learning Over Time: The Spacing Effect in Children’s Acquisition and Generalization of Science Concepts,” Child Development , 22 May 2012, https://ncbi.nlm.nih.gov/pmc/articles/PMC3399982/ncbi.nlm.nih.gov/pmc/articles/PMC3399982/ 18 Kapler, ; T. Weston; M. Wiseheart; “Spacing in a Simulated Undergraduate Classroom: Long-Term Benefits for Factual and Higher-Level Learning,” Learning and Instruction , April 2015, https://www.sciencedirect.com/science/article/abs/pii/S0959475214001042?via%3Dihub 19 Wymbs, N.; A. Bastian; P. Celnik; “Motor Skills Are Strengthened Through Reconsolidation,” Current Biology , 8 February 2016, https://www.sciencedirect.com/science/article/pii/S0960982215015146 20 Herreid, ; “Using Case Studies to Teach Science,” American Institute of Biological Sciences, 2005, https://files.eric.ed.gov/fulltext/ED501359.pdf 21 Herreid, ; “Case Studies in Science–A Novel Method of Science Education,” Journal of College Science Teaching , February 1994, https://eric.ed.gov/?id=EJ487069 22 Anderson, ; “Teaching Developmental Theory With Interrupted Video Case Studies,” Journal of the Scholarship of Teaching and Learning , December 2019, https://scholarworks.iu.edu/journals/index.php/josotl/article/view/25385/3711 23 McFarlane, D.; “Guidelines for Using Case Studies in the Teaching-Learning Process,” College Quarterly , Winter 2015, https://files.eric.ed.gov/fulltext/EJ1070008.pdf 24 Anderson, B.; S. Bradshaw; J. Banning; Using Interrupted Video Case Studies to Teach Developmental Theory: A Pilot Study , Gauisus, 2016, https://sotl.illinoisstate.edu/downloads/gauisus/AndersonVolume4.pdf 25 Penn, ; C. Currie; K. Hoad; F. O’Brien; “The Use of Case Studies in OR Teaching,” Higher Education Pedagogies, 8 March 2016, www.tandfonline.com/doi/full/10.1080/23752696.2015.1134201 26 Prud’homme-Généreux, A.; “Case Study: Formulating Questions That Address Student Misconceptions in a Case Study,” Journal of College Science Teaching , March 2017, https://eric.ed.gov/?id=EJ1136640 27 Boston University Center for Teaching and Learning, Massachusetts, USA, “Using Case Studies to Teach,” https://www.bu.edu/ctl/teaching-resources/using-case-studies-to-teach/ 28 Columbia Accident Investigation Board, Report Volume I, USA, August 2003, http://s3.amazonaws.com/akamai.netstorage/nasa-global/CAIB/CAIB_lowres_full.pdf 29 Dechy, N.; J. Rousseau; F. Jeffroy; “Learning Lessons From Accidents With a Human and Organisational Factors Perspective: Deficiencies and Failures of Operating Experience Feedback Systems,” EUROSAFE Forum 2011, researchgate.net/publication/233997934 30 Cooke, ; T. Rohleder; “Learning From Incidents: From Normal Accidents to High Reliability,” System Dynamics Review , September 2006, https://onlinelibrary.wiley.com/doi/10.1002/sdr.338 31 Varonis, Varonis Case Study: City of San Diego, USA, https://info.varonis.com/hubfs/docs/case_studies/en/Varonis_Case_Study_San_Diego.pdf 32 Roberts, K. H.; “HRO Has Prominent History,” Anesthesia Patient Safety Foundation Newslette r, 18, iss. 1, Spring 2003, https://www.apsf.org/article/hro-has-prominent-history/ 33 Serou, ; L. Sahota; A. Husband; S. Forrest; Slight; S. Slight; “Learning From Safety Incidents in High-Reliability Organizations: A Systematic Review of Learning Tools That Could Be Adapted and Used in Healthcare,” International Journal for Quality in Health Care , 17 March 2021, https://academic.oup.com/intqhc/article/33/1/mzab046/6174559 34 Staff, “‘A Matter of National Security: FBI, Secret Service Investigate After Hacker Tried to Poison a Florida City’s Water With Lye,” USA Today , 9 February 2021, https://www.usatoday.com/story/news/nation/2021/02/09/oldsmar-florida- water-hacker-lye-sodium-hydroxide/4444387001/ 35 Turton, W.; K. Mehrotra; “Hackers Breached Colonial Pipeline Using Compromised Password,” Bloomberg, 4 June 2021, https://www.bloomberg.com/news/articles/2021-06-04/hackers-breached-colonial- pipeline-using-compromised-password 36 Coles, E; “Learning the Lessons From Major Incidents: A Short Review of the Literature,” Emergency Planning College , June 2014 37 Ibid . 38 Check Point Research, “Check Point Research: Cyber Attacks Increased 50 Percent Year Over Year,” 2022, https://blog.checkpoint.com/2022/01/10/check-point-research-cyber- attacks-increased-50-year-over-year/
Ranjit Bhaskar, CISA, CISM, CISSP
Is a senior security architect at Texas Windstorm Insurance Association (TWIA). Bhaskar has 25 years of experience in enterprise architecture and is the author of the op-ed, “A Cybersecurity Culture Score.” He can be reached via LinkedIn at https://www.linkedin.com/in/ranjit-bhaskar-467877218 .
- Corpus ID: 1112703
The Impact of Information Security Awareness Training on Information Security Behaviour: The Case for Further Research
- Tony Stephanou , R. Dagada
- Published in Information Security for… 2008
- Computer Science
Figures and Tables from this paper

40 Citations
Information security training and awareness program: an investigation, a perspective on the intersection of information security policies and ia awareness, factoring in end-user behavior.
- Highly Influenced
An Empirical Study of SETA Program Sustaining Educational Sector’s Information Security vs. Information Systems Misuse
Information security awareness: an application of psychological factors – a study in malaysia, factors influencing information security compliance: an institutional perspective, a review of security awareness approach: ensuring communal learning, legal and policy aspects to consider when providing information security in the corporate environment, impact of education on security practices in ict, a qualitative investigation of bank employee experiences of information security and phishing, the impact of information security awareness training on information security behaviour, 45 references, a design theory for information security awareness.
- Highly Influential
A conceptual foundation for organizational information security awareness
Towards information security behavioural compliance, organisational learning models for information security education, "you are the key to security": establishing a successful security awareness program, a framework for evaluating ict security awareness, practical approaches to creating a security culture, security training and awareness - fitting a square peg in a round hole, employees' behavior towards is security policy compliance, five dimensions of information security awareness, related papers.
Showing 1 through 3 of 0 Related Papers
The Impact of Information Security Awareness on Compliance with Information Security Policies: a Phishing Perspective
PDF Version Also Available for Download.
Description
This research seeks to derive and examine a multidimensional definition of information security awareness, investigate its antecedents, and analyze its effects on compliance with organizational information security policies. The above research goals are tested through the theoretical lens of technology threat avoidance theory and protection motivation theory. Information security awareness is defined as a second-order construct composed of the elements of threat and coping appraisals supplemented by the responsibilities construct to account for organizational environment. The study is executed in two stages. First, the participants (employees of a municipality) are exposed to a series of phishing and spear-phishing messages to … continued below
Physical Description
viii, 153 pages : illustrations (some color)
Creation Information
Hanus, Bartlomiej T. August 2014.
This dissertation is part of the collection entitled: UNT Theses and Dissertations and was provided by the UNT Libraries to the UNT Digital Library , a digital repository hosted by the UNT Libraries . It has been viewed 2901 times, with 15 in the last month. More information about this dissertation can be viewed below.
People and organizations associated with either the creation of this dissertation or its content.
- Hanus, Bartlomiej T.
- Windsor, John C. (John Clayton), 1946- Major Professor
Committee Members
- Pavur, Robert J.
- Kim, Dan J.
- University of North Texas Publisher Info: www.unt.edu Place of Publication: Denton, Texas
Rights Holder
For guidance see Citations, Rights, Re-Use .
Provided By
Unt libraries.
The UNT Libraries serve the university and community by providing access to physical and online collections, fostering information literacy, supporting academic research, and much, much more.
Descriptive information to help identify this dissertation. Follow the links below to find similar items on the Digital Library.
Degree Information
- Department: Department of Information Technology and Decision Sciences
- Discipline: Business Computer Information Systems
- Level: Doctoral
- Name: Doctor of Philosophy
- Grantor: University of North Texas
- PublicationType: Doctoral Dissertation
This research seeks to derive and examine a multidimensional definition of information security awareness, investigate its antecedents, and analyze its effects on compliance with organizational information security policies. The above research goals are tested through the theoretical lens of technology threat avoidance theory and protection motivation theory. Information security awareness is defined as a second-order construct composed of the elements of threat and coping appraisals supplemented by the responsibilities construct to account for organizational environment. The study is executed in two stages. First, the participants (employees of a municipality) are exposed to a series of phishing and spear-phishing messages to assess if there are any common characteristics shared by the phishing victims. The differences between the phished and the not phished group are assessed through multiple discriminant analysis. Second, the same individuals are asked to participate in a survey designed to examine their security awareness. The research model is tested using PLS-SEM approach. The results indicate that security awareness is in fact a second-order formative construct composed of six components. There are significant differences in security awareness levels between the victims of the phishing experiment and the employees who maintain compliance with security policies. The study extends the theory by proposing and validating a universal definition of security awareness. It provides practitioners with an instrument to examine awareness in a plethora of settings and design customized security training activities.
- information security
- policy compliance
- security awareness
- threat avoidance
Library of Congress Subject Headings
- Computer networks -- Security measures.
- Data protection.
- Phishing -- Case studies.
- Thesis or Dissertation
Unique identifying numbers for this dissertation in the Digital Library or other systems.
- Archival Resource Key : ark:/67531/metadc699974
Collections
This dissertation is part of the following collection of related materials.
UNT Theses and Dissertations
Theses and dissertations represent a wealth of scholarly and artistic content created by masters and doctoral students in the degree-seeking process. Some ETDs in this collection are restricted to use by the UNT community .
What responsibilities do I have when using this dissertation?
Digital Files
- 162 image files available in multiple sizes
- 1 file (.pdf)
- Metadata API: descriptive and downloadable metadata available in other formats
Dates and time periods associated with this dissertation.

Creation Date
- August 2014
Added to The UNT Digital Library
- Aug. 21, 2015, 5:42 a.m.
Description Last Updated
- March 27, 2020, 9:48 a.m.
Usage Statistics
When was this dissertation last used?
Interact With This Dissertation
Here are some suggestions for what to do next.
Search Inside
- or search this site for other thesis or dissertations
Start Reading
- All Formats
Citations, Rights, Re-Use
- Citing this Dissertation
- Responsibilities of Use
- Licensing and Permissions
- Linking and Embedding
- Copies and Reproductions
International Image Interoperability Framework

We support the IIIF Presentation API
Print / Share
Links for robots.
Helpful links in machine-readable formats.
Archival Resource Key (ARK)
- ERC Record: /ark:/67531/metadc699974/?
- Persistence Statement: /ark:/67531/metadc699974/??
International Image Interoperability Framework (IIIF)
- IIIF Manifest: /ark:/67531/metadc699974/manifest/
Metadata Formats
- UNTL Format: /ark:/67531/metadc699974/metadata.untl.xml
- DC RDF: /ark:/67531/metadc699974/metadata.dc.rdf
- DC XML: /ark:/67531/metadc699974/metadata.dc.xml
- OAI_DC : /oai/?verb=GetRecord&metadataPrefix=oai_dc&identifier=info:ark/67531/metadc699974
- METS : /ark:/67531/metadc699974/metadata.mets.xml
- OpenSearch Document: /ark:/67531/metadc699974/opensearch.xml
- Thumbnail: /ark:/67531/metadc699974/thumbnail/
- Small Image: /ark:/67531/metadc699974/small/
- In-text: /ark:/67531/metadc699974/urls.txt
- Usage Stats: /stats/stats.json?ark=ark:/67531/metadc699974
Hanus, Bartlomiej T. The Impact of Information Security Awareness on Compliance with Information Security Policies: a Phishing Perspective , dissertation , August 2014; Denton, Texas . ( https://digital.library.unt.edu/ark:/67531/metadc699974/ : accessed June 21, 2024 ), University of North Texas Libraries, UNT Digital Library, https://digital.library.unt.edu ; .
Information Security - Science topic

- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
Enter the email address you signed up with and we'll email you a reset link.
- We're Hiring!
- Help Center

Effectiveness of information security awareness methods based on psychological theories
2011, AFRICAN JOURNAL OF BUSINESS MANAGEMENT
Related Papers
International Journal of Engineering Research and Technology (IJERT)
IJERT Journal
https://www.ijert.org/a-conceptual-model-to-understand-information-security-awareness https://www.ijert.org/research/a-conceptual-model-to-understand-information-security-awareness-IJERTV3IS080428.pdf Information technology plays an important role in everyday lives and it affects the status of information security. Commonly used meaning for information security in literature is the preservation of confidentiality, integrity and availability. The main aim of the research is to examine the information security awareness and influence information security culture through awareness before applying to any organization. Information security awareness provides some kind of safeguard for our information from outside attack. Most of the security incidents are occurred due to the negligence and unawareness of the users. It is important for all employees in society to keep the awareness of information security at higher level. Generally few users with poor awareness and many users with rich awareness of information security in society exist. End-users attitude and the evaluation of information security policy are the two important factors in raising information security awareness. The success of project management within organization requires security awareness. This paper proposes an information security awareness model (ISAM) which analyzes and identifies the most common events related to information security awareness and categorizes these events as low-level, mid-level, and high-level.
CAKRAWALA PENDIDIKAN
Iffah Budiningsih
The advancement of science and technology, especially in the field of Information Communication Technology (ICT) is characterized by the availability of information access faster, easier, convenient, but also vulnerable to try to steal (tap) and modify information. This study aims to determine the reletionship between organizational support perception, competence and motivation with information security awareness(ISA).The research method used survey from the population of 324 people affordable employee local government that handling information system in 33 provinces; the sample was taken 140 people by stratified proportional random sampling.The data were collected using a questionnaire; and data analysis using multiple regression. The results of the reserach show: (1) Information security awareness is influenced positively and significantly by the organizational support perception, competence and motivation. (2) The competence is the dominant factor that influences the information security awareness compared to the organizational support perception and motivation. (3) Information security awareness can improve by competencies i.e. knowladge, skill, attitude continuously and tiered; and the‘ model instructional awareness training’ developed by ‘Schultz’ can be used to improve the attitude or character of information security awareness. Keywords: information security awareness, organizational support perception, competence, motivation
Computers & Security
Hennie Kruger
Due to the intensified need for improved information security, many organisations have established information security awareness programs to ensure that their employees are informed and aware of security risks, thereby protecting themselves and their profitability. In order for a security awareness program to add value to an organisation and at the same time make a contribution to the field of information security, it is necessary to have a set of methods to study and measure its effect. The objective of this paper is to report on the development of a prototype model for measuring information security awareness in an international mining company. Following a description of the model, a brief discussion of the application results is presented.
Jurnal Cakrawala Pendidikan
Tjipto Dinarjo
The advancement of science and technology especially in the field of Information Communication Technology (ICT) is characterized by the availability of information access faster, easier, convenient, but also vulnerable to try to steal (tap) and modify information. This study aims to determine the relationship between organizational support perception, competence, and motivation with information security awareness. The survey involved a population of 324 people affordable employees in local government that handling information systems in 33 provinces. The sample was taken 140 people by stratified proportional random sampling. The data were collected using a questionnaire and analyzed using multiple regression. The results of the research show: (1) Information security awareness is influenced positively and significantly by the organizational support perception, competence and motivation, (2) The competence is the dominant factor that influences the information security awareness comp...
Selected Papers from the 1st International Conference on Islam, Science and Technology, ICONISTECH-1 2019, 11-12 July 2019, Bandung, Indonesia
Muharman Lubis
bilal Khan Muhammad
The destruction due to computer security incidents warns organizations to adopt security measures. In addition to technological measures, individual’s information security awareness is also necessary. Different psychological theories have been proposed to make an effective information security awareness campaign. These information security awareness campaigns are limited in their ability in raising awareness of the participants of the campaign. Although much research has been done in the area of information security awareness, however, this paper considers the applications of healthcare awareness and environmental awareness strategies to make an effective information security awareness campaign. In this paper, we study some of the useful research work conducted in the healthcare and environmental safety awareness domains. These researches have been carried out by well-known researchers in the field of psychology. Finally, we apply these healthcare and environmental awareness best practices to propose an effective information security awareness campaign.
International Journal of Computer Science & Information Technology (IJCSIT)
Increasingly, all kinds of organizations and institutions are adopting the E-business model to conduct their activities and provide E-Services for their customers. In the process, whether they know it or not, those organizations are also opening themselves up to the risk of information security breaches. Therefore protecting an organization’s ICT infrastructure, IT systems, and Data is a vital issue that is often underestimated. Research has shown that one of the most significant threats to information security comes not from external attack but rather from the system's users, because they are familiar with the infrastructure and have access to its resources, but may be unaware of the risks. Moreover, using only technological solutions to protect an organization’s assets is not enough; there is a need to consider the human factor by raising users’ security awareness. Our contribution to this problem is to propose an Information Security Awareness Program that aims at raising and maintaining the level of users’ security awareness. This paper puts forward a general model for an information security awareness program and describes how it could be incorporated into an organization’s website through the process of development life cycle.
Computers & Security
Cate Jerram
Shadi Al-Awawdeh
Educated and trained people are critical success factor in any IT work environment to minimize threats or misuse of the organizational assets that may damage the growth, excellence, and efficiency of any business. However, humans are always the weakest point in any security plan. Awareness is by far the most successful technique that does not cost much when compared with training and education and may reduce the total expenditure on security. Having a properly planned information security awareness program greatly impact the raising of the awareness level among the organization’s staff. Information Technology unit represents a critical success factor in knowledge management and plays a major role in the decision-making process within any organization. We assess that the initial step in delivering any security awareness plan to the business should start from within IT unit, and this is aligned with the perception that security is the sole responsibility of the IT department. Most of the former studies proposed general information security awareness programs and guidelines, but few of them targeted IT unit. The purpose of this research is to propose an information security awareness program (ISAP) to be used by IT unit to enhance the level of information security standard regardless of the organization type. Our research study differs from other studies in that we targeted the IT unit when building ISAP. Furthermore, we identify several awareness knowledge areas for each sub-division.
Loading Preview
Sorry, preview is currently unavailable. You can download the paper by clicking the button above.
RELATED PAPERS
International Journal of Commerce, IT & Management, Vol. 3 (8), 2013
Semiu Akanmu
adedayo williams
Information Security for South Africa
Mysore Ramaswamy
Information Security Journal: A Global Perspective
Maria Karyda
Advances in Science, Technology and Engineering Systems Journal
farid affan
Omar Zakaria
Elmarie Kritzinger
International Journal of Computer Science and Information Security (IJCSIS) Vol. 20 No. 2 FEBRUARY 2022
Journal of Computer Science IJCSIS , Amjad Mahfouth
Information Management & Computer Security
Behaviour & Information Technology
Jemal H Abawajy
mustopa husein lubis
2011 Information Security for South Africa
Stephen Flowerday , Hennie Kruger , Lynette Drevin
Salvatore Ammirato
Journal of Computer Science IJCSIS
International Journal of Applied Decision Sciences
Bilgin Metin
International Journal of Innovative Research in Computer and Communication Engineering
Tinotenda Zvavashe
RELATED TOPICS
- We're Hiring!
- Help Center
- Find new research papers in:
- Health Sciences
- Earth Sciences
- Cognitive Science
- Mathematics
- Computer Science
- Academia ©2024
IEEE Account
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu
- Subscribe SciFeed
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Advances in cybersecurity and reliability.

Acknowledgments
Conflicts of interest.
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Alazab, M.; Alazab, A. Advances in Cybersecurity and Reliability. Information 2024 , 15 , 361. https://doi.org/10.3390/info15060361
Alazab M, Alazab A. Advances in Cybersecurity and Reliability. Information . 2024; 15(6):361. https://doi.org/10.3390/info15060361
Alazab, Moutaz, and Ammar Alazab. 2024. "Advances in Cybersecurity and Reliability" Information 15, no. 6: 361. https://doi.org/10.3390/info15060361
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals

IMAGES
VIDEO
COMMENTS
Jaeger (2018) indicated that "research on information security awareness is still an evolving field with many uncharted areas to be ... or sequentially based on the situation to narrow down the number of papers and find and select the most relevant papers. Relevant keywords for the research questions were selected as mentioned in Table ...
Goodhue and Straub (1991) and, later, Straub and Welke (1998) evaluated the role of security managers' awareness in reducing incidents. After them, the predominant focus of studies has been on raising end-user awareness of security issues (Kruger and Kearney, 2006; Chen et al., 2006).Awareness of security professionals is different in context and concept from the general security awareness ...
Cetin & Hamdullah Nejat Basim (2020): Cyber Security Awareness, Knowledge and Behavior: A Comparative Study, Journal of Computer Information Systems, DOI: 10.1080/08874417.2020.1712269
Security Education Training and Awareness plays a dynamic role for organizations in endorsing resources' thoughtfulness and accessibility. This paper determines the importance of security ...
Information Security Awareness: Literature Review and Integrative Framework. Lennart Jaeger. Published in Hawaii International… 3 January 2018. Computer Science. TLDR. This study synthesizes the relationship between ISA and its antecedents and consequences and identifies consequences of ISA in terms of changes in beliefs, attitudes ...
This study aims to analyze the trends of cybersecurity awareness and the research gap in cybersecurity topics. Data was gathered starting from May 20 th , 2023, by searching it online on Scopus with the keywords "Cybersecurity", this study combines Articles, Reviews, Conference papers, Books, and Book chapters while utilizing VOSviewer to get ...
Better Cybersecurity Awareness Through Research. In the last few years, information security professionals have faced tremendous challenges. Just in 2021, there were more than two billion malware attacks and trillions of intrusion attempts. 1 Ransomware attacks alone have increased by 151 percent compared with 2020. 2 In fall of 2020 ...
This paper aims to summarize the current findings on cybersecurity awareness research for children and help guide future studies. We have performed a systematic literature review on cybersecurity awareness for children, analyzing 56 peer-reviewed studies that report in depth on various cybersecurity risks and awareness-raising approaches.
The paper identifies ambiguous aspects of current security awareness approaches and the proposed classification provides a guide to identify the range of options available to researchers and practitioners when they design their research and practice on information security awareness. ABSTRACT The aim of this survey is largely exploratory, namely, to discover patterns and trends in the way that ...
This paper reflects research in progress and discusses some of the problems with existing information security awareness research and proposes a model to be tested for examining the impact of information security Awareness training on information security behaviour. Information Security awareness initiatives are seen as critical to any information security programme.
Information exchange has become increasingly faster and efficient through the use of recent technological advances, such as instant messaging and social media platforms. Consequently, access to information has become easier. However, new types of cybersecurity threats that typically result in data loss and information misuse have emerged simultaneously. Therefore, maintaining data privacy in ...
Academia.edu is a platform for academics to share research papers. Investigating Information Security Awareness: Research and Practice Gaps ... Investigating information security awareness: research and practice gaps Authors Aggeliki Tsohou1, Spyros Kokolakis1, Maria Karyda1, Evangelos Kiountouzis2 1 University of the Aegean, Dept. of ...
A quantitative research approach with case study method is used. Findings showed that the information security awareness level of Enat Bank employees is unsatisfactory. One of the best ways to make sure employees will not make costly errors in regard to information security is to institute organization-wide security awareness initiatives.
This research seeks to derive and examine a multidimensional definition of information security awareness, investigate its antecedents, and analyze its effects on compliance with organizational information security policies. The above research goals are tested through the theoretical lens of technology threat avoidance theory and protection motivation theory. Information security awareness is ...
The simple economics of an external shock to a bug bounty platform. The cybersecurity of fairy tales. Journal of Cybersecurity is inviting submissions to a new special issue from the workshop on the economics of information security. Authors whose papers appeared at the workshop are invited to submit a revised version to the journal.
A case study in information security awareness improvement: a short description Isabella CORRADINI Themis Research Centre Roma, Italy and Enrico NARDELLI Univ. Roma "Tor Vergata" Roma, Italy ABSTRACT In this paper we provide a short description of a training experience aiming at improving information security awareness.
The results of the study will provide a mean score for security awareness for both faculty and staff, as well as individual items that could be classified as awareness or behavior. The results of the study provided an understanding of security awareness and behaviors. Implications of the findings are presented in this paper. The research
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on INFORMATION SECURITY. Find methods information, sources, references or conduct a literature review on ...
Effectiveness of information security awareness methods based on psychological theories . × ... 10.5897/AJBM11.067 ISSN 1993-8233 ©2011 Academic Journals Full Length Research Paper Effectiveness of information security awareness methods based on psychological theories Bilal Khan1, Khaled S. Alghathbar1, 2, Syed Irfan Nabi1,3 and Muhammad ...
Although prior information security research on PMT (e.g., [Citation 12, Citation 65]) has identified various personal and social factors that may affect individuals' protection motivation, there are inconsistent findings across these studies. Our study has theorized and empirically validated that the inconsistent findings may be due to an ...
In this paper, we illustrate the factors that impact information security in different fields; cyber security, Internet of Things and network security from various studies and outline the security requirements to reduce this impact. ... Information security is defined as protecting the information, the system, and the hardware that use, store ...
In addition, five scenarios can be considered for cyber warfare: (1) Government-sponsored cyber espionage to gather information to plan future cyber-attacks, (2) a cyber-attack aimed at laying the groundwork for any unrest and popular uprising, (3) Cyber-attack aimed at disabling equipment and facilitating physical aggression, (4) Cyber-attack as a complement to physical aggression, and (5 ...
Information Security Awareness Research Paper - Free download as PDF File (.pdf), Text File (.txt) or read online for free. information security awareness research paper
The paper "Countermeasure Strategies to Address Cybersecurity Challenges Amidst Major Crises in the Higher Education and Research Sector: An Organisational Learning Perspective" by Samreen Mahmood, Mehmood Chadhar, and Selena Firmin analyses counterstrategies to address cybersecurity challenges during major crises in the Higher Education and Research Sector (HERS); this is carried out ...