Demystifying the self Parameter: A Complete Guide to Using self in Python Classes
The self parameter is a special parameter that is passed to methods in Python classes. It binds the instance of the class to the method, allowing the method to access and modify the attributes and methods of the class instance. Properly utilizing self is key to writing effective Python classes. This guide will provide a deep dive into self - what it is, when it’s used, and how to leverage it to create well-designed class methods in Python.

Table of Contents
What is self , 1. instance methods, 2. constructor methods, how does self work, when is self not needed, getting attributes, setting attributes, calling methods, modifying multiple instances, caveats of using self, data classes, game characters, networking with sockets.
In Python, self refers to the instance of the class that a method is being called on. By convention, self is always the first parameter passed to methods in a class. For example:
Here, when greet() is called on the john instance, john gets passed automatically as the self argument. This allows greet() to access the name attribute to print the greeting message specific to the john instance.
In a nutshell, self allows a method to have access to the attributes and methods of the class instance it is called on. Without self , methods would not know which instance they are interacting with.
When is self used?
The self parameter is used in two primary cases:
In instance methods - methods that are called on an instance of a class.
In the __init__ constructor method to initialize instance attributes.
Essentially, any method defined inside a class declaration should have self as the first parameter if you want to access attributes and methods of the class instance.
Let’s expand on these two main use cases:
Instance methods are methods that are designed to be called on instances of a class. That is, they are not standalone functions, but rather behaviors that a class instance can exhibit.
Instance methods always take self as the first parameter. By convention, it is named self but could technically be named anything (though self is universally preferred).
When calling an instance method, Python binds the instance to self automatically so you do not need to pass it explicitly.
For example:
This allows area() to access the width and height of the rect instance through self.width and self.height .
Without self , the method would not know which rectangle instance to operate on.
The __init__ method is a special constructor method that is called automatically when an instance of a class is created. It is used to initialize the attributes of a class instance.
__init__ always takes self as the first parameter, along with any other parameters needed to instantiate the class.
Here, when creating the sam instance, __init__ is called automatically with sam passed as self and the name and breed passed as the other two parameters.
This allows the name and breed attributes to be initialized on the sam instance properly.
So in summary, self is utilized in __init__ to set up the new class instance.
Behind the scenes, when a method is called on an instance, Python automatically passes the instance as the first argument to the method.
Is equivalent to:
So self gives us a way to access the object instance via a parameter to the method call. This is what enables instance methods to operate on instance state.
Without the use of self , code inside a method would not be able to access or modify attributes of the instance it was called on. Attempting to access self.some_attr would raise an error about that attribute being undefined.
There are some cases in Python where self is not explicitly required as a method parameter:
Static methods - These behave like regular functions, not operating on an instance or its state. They have the @staticmethod decorator.
Class methods - These operate at the class level rather than instance level. They take cls as the first arg instead of self . Denoted with @classmethod .
Functions outside a class - Regular functions defined outside a class definition do not take self or any instance, they operate independently.
In these cases, self is not necessary because the method or function does not operate on an instance state.
Accessing Instance Attributes with self
Now that we understand what self represents, let’s explore how we can leverage it to access attributes and methods of a class instance:
We can access any attribute defined on an instance via self in a method.
This accesses the name and age attributes of the john instance using self.name and self.age
We can also set or update attributes using assignment via self :
Here birthday() increments john ’s age using self.age += 1 .
In addition to attributes, self allows a method to call other methods on the instance:
This allows methods to reuse behavior and operate on the instance.
A key benefit of using self is that we can define methods that uniformly operate on attributes across all instances of a class.
The increment() method will properly increment the counter for each instance it is called on. Without self , the counters would incorrectly share state and not work properly.
This allows us to write reusable methods that can operate on any instance of a class in a encapsulated manner.
While self is useful, there are some caveats to keep in mind:
Methods that use self can only be called on class instances, not the class itself. Attempting to call Class.method() will raise an error if self is used.
All attributes must be accessed via self . Code like count += 1 would modify a local variable, not the instance attribute.
It is easy to accidentally overwrite self in a method with a local variable, losing access to the instance. Avoid reassigning self .
Methods that do not need access to instance state should be made static or class methods to avoid unnecessary use of self .
self can be confusing for developers coming from other languages. Take time to properly learn Python instance methods and self usage.
With disciplined coding, self enables writing reusable classes that operate on encapsulated instance state. But it takes practice to use properly and effectively.
Example Use Cases
To illustrate practical applications of self in Python, let’s walk through some examples:
self allows custom data classes to store state and define constructors, string representations, and comparisons:
This provides convenient class functionality building on self .
In a game, self can be used to track character stats and call actions:
This keeps each character’s state encapsulated and reusable.
For network programming with sockets:
self is leveraged to track each connection and send/receive data accordingly.
The examples showcase just a fraction of how self can be utilized for clean class design across domains like data science, games, networking, and more.
To summarize proper usage of the self parameter in Python:
self refers to the instance a method is called on and is automatically passed by Python.
It provides access to attributes and methods on the instance via self.attr and self.method() .
self should be the first parameter in instance methods and __init__ constructors.
It enables read/write access to state across instances separately.
Avoid reassigning self accidentally inside a method definition.
Use self to write reusable, encapsulated classes in Python.
With this knowledge, you are now equipped to leverage self effectively in your own Python classes and unlock the full power of object-oriented programming in Python. The self parameter ties together key concepts like encapsulation, access control, and polymorphism. Mastering its use will level up your Python class design skills.
- python
- object-oriented-programming-oop
Understanding Python self Variable with Examples
Python self variable is used to bind the instance of the class to the instance method. We have to explicitly declare it as the first method argument to access the instance variables and methods. This variable is used only with the instance methods.
In most of the Object-Oriented programming languages, you can access the current object in a method without the need for explicitly having it as a method parameter. For example, we can use “ this ” keyword to access the current object in Java program. But, in Python we have to explicitly declare the object instance as “self” variable.
Python self is a keyword?
Python self variable is not a reserved keyword . But, it’s the best practice and convention to use the variable name as “self” to refer to the instance.
Python self variable Example
Let’s say we have a Dog class defined as below.
Output : Labrador is barking.
- The __init__() function is defined with two variables but when we are creating the Dog instance, we have to provide only one argument. The “self” is automatically assigned to the newly created instance of Dog class.
- The bark() method has only one argument – “self” – which gets bind to the Dog instance that calls this method. That’s why we are not passing any argument when calling the bark() method.
- If we have to access any instance variable in the function, we can use the dot operator.
Can we skip “self” variable?
What if the instance method doesn’t need to access instance variables. Can we skip the self variable in this case?
Let’s find out with a simple example.
If you will run the above code, there won’t be any error. But, we are not calling the bark() method. Let’s see what happens when we try to call the bark() method.

We are getting error as the bark() method accepts 0 argument but we provided 1. It’s because when we are calling d.bark() , the “d” instance is automatically passed as the first argument to the bark() instance method.
But, if we access the bark() instance method through class reference then it will work fine. So, calling Dog.bark() will not cause any errors.
Similar variables for Class Method and Static Method?
The same behavior is present with the Class methods too. The only difference is that the convention is to use “ cls ” as the variable name for the Class reference.
However, it’s not required with a static method. Because, the static methods are self sufficient functions and they can’t access any of the class variables or functions directly.
Let’s look at a complete example with self and cls variables and a static method without any arguments.
Quick Example to Break the Convention
This example is just to show you that it’s not mandatory to use the variable name as “self” and “cls”. In real programming, always stick to this convention.
The “self” variable is bound to the current instance
The self variable gives us access to the current instance properties. We can confirm this with a simple example by creating two different instances of the Dog class.
Why not make “self” variable implicit?
There had been a lot of suggestions to make the “self” variable a reserved keyword and implicitly available to the instance method. But, the suggestion was rejected by “Guido van Rossum”. You can read about them here and here .
Python Tutorial
File handling, python modules, python numpy, python pandas, python matplotlib, python scipy, machine learning, python mysql, python mongodb, python reference, module reference, python how to, python examples, python assignment operators.
Assignment operators are used to assign values to variables:
| Operator | Example | Same As | Try it |
|---|---|---|---|
| = | x = 5 | x = 5 | |
| += | x += 3 | x = x + 3 | |
| -= | x -= 3 | x = x - 3 | |
| *= | x *= 3 | x = x * 3 | |
| /= | x /= 3 | x = x / 3 | |
| %= | x %= 3 | x = x % 3 | |
| //= | x //= 3 | x = x // 3 | |
| **= | x **= 3 | x = x ** 3 | |
| &= | x &= 3 | x = x & 3 | |
| |= | x |= 3 | x = x | 3 | |
| ^= | x ^= 3 | x = x ^ 3 | |
| >>= | x >>= 3 | x = x >> 3 | |
| <<= | x <<= 3 | x = x << 3 |
Related Pages

COLOR PICKER

Contact Sales
If you want to use W3Schools services as an educational institution, team or enterprise, send us an e-mail: [email protected]
Report Error
If you want to report an error, or if you want to make a suggestion, send us an e-mail: [email protected]
Top Tutorials
Top references, top examples, get certified.
Member-only story
What Is Python’s “Self” Argument, Anyway?
A behind-the-scenes look into this well-known argument.
Martin Heinz
Better Programming
Every Python developer is familiar with the self argument, which is present in every* method declaration of every class. We all know how to use it, but do you really know what it is, why it's there, and how it works under the hood?
What We Already Know

Written by Martin Heinz
CKA | RHCE | DevOps Engineer | Working with Python, Kubernetes, Linux and more | https://martinheinz.dev/ | https://ko-fi.com/martinheinz
Text to speech
Python Enhancement Proposals
- Python »
- PEP Index »
PEP 572 – Assignment Expressions
The importance of real code, exceptional cases, scope of the target, relative precedence of :=, change to evaluation order, differences between assignment expressions and assignment statements, specification changes during implementation, _pydecimal.py, datetime.py, sysconfig.py, simplifying list comprehensions, capturing condition values, changing the scope rules for comprehensions, alternative spellings, special-casing conditional statements, special-casing comprehensions, lowering operator precedence, allowing commas to the right, always requiring parentheses, why not just turn existing assignment into an expression, with assignment expressions, why bother with assignment statements, why not use a sublocal scope and prevent namespace pollution, style guide recommendations, acknowledgements, a numeric example, appendix b: rough code translations for comprehensions, appendix c: no changes to scope semantics.
This is a proposal for creating a way to assign to variables within an expression using the notation NAME := expr .
As part of this change, there is also an update to dictionary comprehension evaluation order to ensure key expressions are executed before value expressions (allowing the key to be bound to a name and then re-used as part of calculating the corresponding value).
During discussion of this PEP, the operator became informally known as “the walrus operator”. The construct’s formal name is “Assignment Expressions” (as per the PEP title), but they may also be referred to as “Named Expressions” (e.g. the CPython reference implementation uses that name internally).
Naming the result of an expression is an important part of programming, allowing a descriptive name to be used in place of a longer expression, and permitting reuse. Currently, this feature is available only in statement form, making it unavailable in list comprehensions and other expression contexts.
Additionally, naming sub-parts of a large expression can assist an interactive debugger, providing useful display hooks and partial results. Without a way to capture sub-expressions inline, this would require refactoring of the original code; with assignment expressions, this merely requires the insertion of a few name := markers. Removing the need to refactor reduces the likelihood that the code be inadvertently changed as part of debugging (a common cause of Heisenbugs), and is easier to dictate to another programmer.
During the development of this PEP many people (supporters and critics both) have had a tendency to focus on toy examples on the one hand, and on overly complex examples on the other.
The danger of toy examples is twofold: they are often too abstract to make anyone go “ooh, that’s compelling”, and they are easily refuted with “I would never write it that way anyway”.
The danger of overly complex examples is that they provide a convenient strawman for critics of the proposal to shoot down (“that’s obfuscated”).
Yet there is some use for both extremely simple and extremely complex examples: they are helpful to clarify the intended semantics. Therefore, there will be some of each below.
However, in order to be compelling , examples should be rooted in real code, i.e. code that was written without any thought of this PEP, as part of a useful application, however large or small. Tim Peters has been extremely helpful by going over his own personal code repository and picking examples of code he had written that (in his view) would have been clearer if rewritten with (sparing) use of assignment expressions. His conclusion: the current proposal would have allowed a modest but clear improvement in quite a few bits of code.
Another use of real code is to observe indirectly how much value programmers place on compactness. Guido van Rossum searched through a Dropbox code base and discovered some evidence that programmers value writing fewer lines over shorter lines.
Case in point: Guido found several examples where a programmer repeated a subexpression, slowing down the program, in order to save one line of code, e.g. instead of writing:
they would write:
Another example illustrates that programmers sometimes do more work to save an extra level of indentation:
This code tries to match pattern2 even if pattern1 has a match (in which case the match on pattern2 is never used). The more efficient rewrite would have been:
Syntax and semantics
In most contexts where arbitrary Python expressions can be used, a named expression can appear. This is of the form NAME := expr where expr is any valid Python expression other than an unparenthesized tuple, and NAME is an identifier.
The value of such a named expression is the same as the incorporated expression, with the additional side-effect that the target is assigned that value:
There are a few places where assignment expressions are not allowed, in order to avoid ambiguities or user confusion:
This rule is included to simplify the choice for the user between an assignment statement and an assignment expression – there is no syntactic position where both are valid.
Again, this rule is included to avoid two visually similar ways of saying the same thing.
This rule is included to disallow excessively confusing code, and because parsing keyword arguments is complex enough already.
This rule is included to discourage side effects in a position whose exact semantics are already confusing to many users (cf. the common style recommendation against mutable default values), and also to echo the similar prohibition in calls (the previous bullet).
The reasoning here is similar to the two previous cases; this ungrouped assortment of symbols and operators composed of : and = is hard to read correctly.
This allows lambda to always bind less tightly than := ; having a name binding at the top level inside a lambda function is unlikely to be of value, as there is no way to make use of it. In cases where the name will be used more than once, the expression is likely to need parenthesizing anyway, so this prohibition will rarely affect code.
This shows that what looks like an assignment operator in an f-string is not always an assignment operator. The f-string parser uses : to indicate formatting options. To preserve backwards compatibility, assignment operator usage inside of f-strings must be parenthesized. As noted above, this usage of the assignment operator is not recommended.
An assignment expression does not introduce a new scope. In most cases the scope in which the target will be bound is self-explanatory: it is the current scope. If this scope contains a nonlocal or global declaration for the target, the assignment expression honors that. A lambda (being an explicit, if anonymous, function definition) counts as a scope for this purpose.
There is one special case: an assignment expression occurring in a list, set or dict comprehension or in a generator expression (below collectively referred to as “comprehensions”) binds the target in the containing scope, honoring a nonlocal or global declaration for the target in that scope, if one exists. For the purpose of this rule the containing scope of a nested comprehension is the scope that contains the outermost comprehension. A lambda counts as a containing scope.
The motivation for this special case is twofold. First, it allows us to conveniently capture a “witness” for an any() expression, or a counterexample for all() , for example:
Second, it allows a compact way of updating mutable state from a comprehension, for example:
However, an assignment expression target name cannot be the same as a for -target name appearing in any comprehension containing the assignment expression. The latter names are local to the comprehension in which they appear, so it would be contradictory for a contained use of the same name to refer to the scope containing the outermost comprehension instead.
For example, [i := i+1 for i in range(5)] is invalid: the for i part establishes that i is local to the comprehension, but the i := part insists that i is not local to the comprehension. The same reason makes these examples invalid too:
While it’s technically possible to assign consistent semantics to these cases, it’s difficult to determine whether those semantics actually make sense in the absence of real use cases. Accordingly, the reference implementation [1] will ensure that such cases raise SyntaxError , rather than executing with implementation defined behaviour.
This restriction applies even if the assignment expression is never executed:
For the comprehension body (the part before the first “for” keyword) and the filter expression (the part after “if” and before any nested “for”), this restriction applies solely to target names that are also used as iteration variables in the comprehension. Lambda expressions appearing in these positions introduce a new explicit function scope, and hence may use assignment expressions with no additional restrictions.
Due to design constraints in the reference implementation (the symbol table analyser cannot easily detect when names are re-used between the leftmost comprehension iterable expression and the rest of the comprehension), named expressions are disallowed entirely as part of comprehension iterable expressions (the part after each “in”, and before any subsequent “if” or “for” keyword):
A further exception applies when an assignment expression occurs in a comprehension whose containing scope is a class scope. If the rules above were to result in the target being assigned in that class’s scope, the assignment expression is expressly invalid. This case also raises SyntaxError :
(The reason for the latter exception is the implicit function scope created for comprehensions – there is currently no runtime mechanism for a function to refer to a variable in the containing class scope, and we do not want to add such a mechanism. If this issue ever gets resolved this special case may be removed from the specification of assignment expressions. Note that the problem already exists for using a variable defined in the class scope from a comprehension.)
See Appendix B for some examples of how the rules for targets in comprehensions translate to equivalent code.
The := operator groups more tightly than a comma in all syntactic positions where it is legal, but less tightly than all other operators, including or , and , not , and conditional expressions ( A if C else B ). As follows from section “Exceptional cases” above, it is never allowed at the same level as = . In case a different grouping is desired, parentheses should be used.
The := operator may be used directly in a positional function call argument; however it is invalid directly in a keyword argument.
Some examples to clarify what’s technically valid or invalid:
Most of the “valid” examples above are not recommended, since human readers of Python source code who are quickly glancing at some code may miss the distinction. But simple cases are not objectionable:
This PEP recommends always putting spaces around := , similar to PEP 8 ’s recommendation for = when used for assignment, whereas the latter disallows spaces around = used for keyword arguments.)
In order to have precisely defined semantics, the proposal requires evaluation order to be well-defined. This is technically not a new requirement, as function calls may already have side effects. Python already has a rule that subexpressions are generally evaluated from left to right. However, assignment expressions make these side effects more visible, and we propose a single change to the current evaluation order:
- In a dict comprehension {X: Y for ...} , Y is currently evaluated before X . We propose to change this so that X is evaluated before Y . (In a dict display like {X: Y} this is already the case, and also in dict((X, Y) for ...) which should clearly be equivalent to the dict comprehension.)
Most importantly, since := is an expression, it can be used in contexts where statements are illegal, including lambda functions and comprehensions.
Conversely, assignment expressions don’t support the advanced features found in assignment statements:
- Multiple targets are not directly supported: x = y = z = 0 # Equivalent: (z := (y := (x := 0)))
- Single assignment targets other than a single NAME are not supported: # No equivalent a [ i ] = x self . rest = []
- Priority around commas is different: x = 1 , 2 # Sets x to (1, 2) ( x := 1 , 2 ) # Sets x to 1
- Iterable packing and unpacking (both regular or extended forms) are not supported: # Equivalent needs extra parentheses loc = x , y # Use (loc := (x, y)) info = name , phone , * rest # Use (info := (name, phone, *rest)) # No equivalent px , py , pz = position name , phone , email , * other_info = contact
- Inline type annotations are not supported: # Closest equivalent is "p: Optional[int]" as a separate declaration p : Optional [ int ] = None
- Augmented assignment is not supported: total += tax # Equivalent: (total := total + tax)
The following changes have been made based on implementation experience and additional review after the PEP was first accepted and before Python 3.8 was released:
- for consistency with other similar exceptions, and to avoid locking in an exception name that is not necessarily going to improve clarity for end users, the originally proposed TargetScopeError subclass of SyntaxError was dropped in favour of just raising SyntaxError directly. [3]
- due to a limitation in CPython’s symbol table analysis process, the reference implementation raises SyntaxError for all uses of named expressions inside comprehension iterable expressions, rather than only raising them when the named expression target conflicts with one of the iteration variables in the comprehension. This could be revisited given sufficiently compelling examples, but the extra complexity needed to implement the more selective restriction doesn’t seem worthwhile for purely hypothetical use cases.
Examples from the Python standard library
env_base is only used on these lines, putting its assignment on the if moves it as the “header” of the block.
- Current: env_base = os . environ . get ( "PYTHONUSERBASE" , None ) if env_base : return env_base
- Improved: if env_base := os . environ . get ( "PYTHONUSERBASE" , None ): return env_base
Avoid nested if and remove one indentation level.
- Current: if self . _is_special : ans = self . _check_nans ( context = context ) if ans : return ans
- Improved: if self . _is_special and ( ans := self . _check_nans ( context = context )): return ans
Code looks more regular and avoid multiple nested if. (See Appendix A for the origin of this example.)
- Current: reductor = dispatch_table . get ( cls ) if reductor : rv = reductor ( x ) else : reductor = getattr ( x , "__reduce_ex__" , None ) if reductor : rv = reductor ( 4 ) else : reductor = getattr ( x , "__reduce__" , None ) if reductor : rv = reductor () else : raise Error ( "un(deep)copyable object of type %s " % cls )
- Improved: if reductor := dispatch_table . get ( cls ): rv = reductor ( x ) elif reductor := getattr ( x , "__reduce_ex__" , None ): rv = reductor ( 4 ) elif reductor := getattr ( x , "__reduce__" , None ): rv = reductor () else : raise Error ( "un(deep)copyable object of type %s " % cls )
tz is only used for s += tz , moving its assignment inside the if helps to show its scope.
- Current: s = _format_time ( self . _hour , self . _minute , self . _second , self . _microsecond , timespec ) tz = self . _tzstr () if tz : s += tz return s
- Improved: s = _format_time ( self . _hour , self . _minute , self . _second , self . _microsecond , timespec ) if tz := self . _tzstr (): s += tz return s
Calling fp.readline() in the while condition and calling .match() on the if lines make the code more compact without making it harder to understand.
- Current: while True : line = fp . readline () if not line : break m = define_rx . match ( line ) if m : n , v = m . group ( 1 , 2 ) try : v = int ( v ) except ValueError : pass vars [ n ] = v else : m = undef_rx . match ( line ) if m : vars [ m . group ( 1 )] = 0
- Improved: while line := fp . readline (): if m := define_rx . match ( line ): n , v = m . group ( 1 , 2 ) try : v = int ( v ) except ValueError : pass vars [ n ] = v elif m := undef_rx . match ( line ): vars [ m . group ( 1 )] = 0
A list comprehension can map and filter efficiently by capturing the condition:
Similarly, a subexpression can be reused within the main expression, by giving it a name on first use:
Note that in both cases the variable y is bound in the containing scope (i.e. at the same level as results or stuff ).
Assignment expressions can be used to good effect in the header of an if or while statement:
Particularly with the while loop, this can remove the need to have an infinite loop, an assignment, and a condition. It also creates a smooth parallel between a loop which simply uses a function call as its condition, and one which uses that as its condition but also uses the actual value.
An example from the low-level UNIX world:
Rejected alternative proposals
Proposals broadly similar to this one have come up frequently on python-ideas. Below are a number of alternative syntaxes, some of them specific to comprehensions, which have been rejected in favour of the one given above.
A previous version of this PEP proposed subtle changes to the scope rules for comprehensions, to make them more usable in class scope and to unify the scope of the “outermost iterable” and the rest of the comprehension. However, this part of the proposal would have caused backwards incompatibilities, and has been withdrawn so the PEP can focus on assignment expressions.
Broadly the same semantics as the current proposal, but spelled differently.
Since EXPR as NAME already has meaning in import , except and with statements (with different semantics), this would create unnecessary confusion or require special-casing (e.g. to forbid assignment within the headers of these statements).
(Note that with EXPR as VAR does not simply assign the value of EXPR to VAR – it calls EXPR.__enter__() and assigns the result of that to VAR .)
Additional reasons to prefer := over this spelling include:
- In if f(x) as y the assignment target doesn’t jump out at you – it just reads like if f x blah blah and it is too similar visually to if f(x) and y .
- import foo as bar
- except Exc as var
- with ctxmgr() as var
To the contrary, the assignment expression does not belong to the if or while that starts the line, and we intentionally allow assignment expressions in other contexts as well.
- NAME = EXPR
- if NAME := EXPR
reinforces the visual recognition of assignment expressions.
This syntax is inspired by languages such as R and Haskell, and some programmable calculators. (Note that a left-facing arrow y <- f(x) is not possible in Python, as it would be interpreted as less-than and unary minus.) This syntax has a slight advantage over ‘as’ in that it does not conflict with with , except and import , but otherwise is equivalent. But it is entirely unrelated to Python’s other use of -> (function return type annotations), and compared to := (which dates back to Algol-58) it has a much weaker tradition.
This has the advantage that leaked usage can be readily detected, removing some forms of syntactic ambiguity. However, this would be the only place in Python where a variable’s scope is encoded into its name, making refactoring harder.
Execution order is inverted (the indented body is performed first, followed by the “header”). This requires a new keyword, unless an existing keyword is repurposed (most likely with: ). See PEP 3150 for prior discussion on this subject (with the proposed keyword being given: ).
This syntax has fewer conflicts than as does (conflicting only with the raise Exc from Exc notation), but is otherwise comparable to it. Instead of paralleling with expr as target: (which can be useful but can also be confusing), this has no parallels, but is evocative.
One of the most popular use-cases is if and while statements. Instead of a more general solution, this proposal enhances the syntax of these two statements to add a means of capturing the compared value:
This works beautifully if and ONLY if the desired condition is based on the truthiness of the captured value. It is thus effective for specific use-cases (regex matches, socket reads that return '' when done), and completely useless in more complicated cases (e.g. where the condition is f(x) < 0 and you want to capture the value of f(x) ). It also has no benefit to list comprehensions.
Advantages: No syntactic ambiguities. Disadvantages: Answers only a fraction of possible use-cases, even in if / while statements.
Another common use-case is comprehensions (list/set/dict, and genexps). As above, proposals have been made for comprehension-specific solutions.
This brings the subexpression to a location in between the ‘for’ loop and the expression. It introduces an additional language keyword, which creates conflicts. Of the three, where reads the most cleanly, but also has the greatest potential for conflict (e.g. SQLAlchemy and numpy have where methods, as does tkinter.dnd.Icon in the standard library).
As above, but reusing the with keyword. Doesn’t read too badly, and needs no additional language keyword. Is restricted to comprehensions, though, and cannot as easily be transformed into “longhand” for-loop syntax. Has the C problem that an equals sign in an expression can now create a name binding, rather than performing a comparison. Would raise the question of why “with NAME = EXPR:” cannot be used as a statement on its own.
As per option 2, but using as rather than an equals sign. Aligns syntactically with other uses of as for name binding, but a simple transformation to for-loop longhand would create drastically different semantics; the meaning of with inside a comprehension would be completely different from the meaning as a stand-alone statement, while retaining identical syntax.
Regardless of the spelling chosen, this introduces a stark difference between comprehensions and the equivalent unrolled long-hand form of the loop. It is no longer possible to unwrap the loop into statement form without reworking any name bindings. The only keyword that can be repurposed to this task is with , thus giving it sneakily different semantics in a comprehension than in a statement; alternatively, a new keyword is needed, with all the costs therein.
There are two logical precedences for the := operator. Either it should bind as loosely as possible, as does statement-assignment; or it should bind more tightly than comparison operators. Placing its precedence between the comparison and arithmetic operators (to be precise: just lower than bitwise OR) allows most uses inside while and if conditions to be spelled without parentheses, as it is most likely that you wish to capture the value of something, then perform a comparison on it:
Once find() returns -1, the loop terminates. If := binds as loosely as = does, this would capture the result of the comparison (generally either True or False ), which is less useful.
While this behaviour would be convenient in many situations, it is also harder to explain than “the := operator behaves just like the assignment statement”, and as such, the precedence for := has been made as close as possible to that of = (with the exception that it binds tighter than comma).
Some critics have claimed that the assignment expressions should allow unparenthesized tuples on the right, so that these two would be equivalent:
(With the current version of the proposal, the latter would be equivalent to ((point := x), y) .)
However, adopting this stance would logically lead to the conclusion that when used in a function call, assignment expressions also bind less tight than comma, so we’d have the following confusing equivalence:
The less confusing option is to make := bind more tightly than comma.
It’s been proposed to just always require parentheses around an assignment expression. This would resolve many ambiguities, and indeed parentheses will frequently be needed to extract the desired subexpression. But in the following cases the extra parentheses feel redundant:
Frequently Raised Objections
C and its derivatives define the = operator as an expression, rather than a statement as is Python’s way. This allows assignments in more contexts, including contexts where comparisons are more common. The syntactic similarity between if (x == y) and if (x = y) belies their drastically different semantics. Thus this proposal uses := to clarify the distinction.
The two forms have different flexibilities. The := operator can be used inside a larger expression; the = statement can be augmented to += and its friends, can be chained, and can assign to attributes and subscripts.
Previous revisions of this proposal involved sublocal scope (restricted to a single statement), preventing name leakage and namespace pollution. While a definite advantage in a number of situations, this increases complexity in many others, and the costs are not justified by the benefits. In the interests of language simplicity, the name bindings created here are exactly equivalent to any other name bindings, including that usage at class or module scope will create externally-visible names. This is no different from for loops or other constructs, and can be solved the same way: del the name once it is no longer needed, or prefix it with an underscore.
(The author wishes to thank Guido van Rossum and Christoph Groth for their suggestions to move the proposal in this direction. [2] )
As expression assignments can sometimes be used equivalently to statement assignments, the question of which should be preferred will arise. For the benefit of style guides such as PEP 8 , two recommendations are suggested.
- If either assignment statements or assignment expressions can be used, prefer statements; they are a clear declaration of intent.
- If using assignment expressions would lead to ambiguity about execution order, restructure it to use statements instead.
The authors wish to thank Alyssa Coghlan and Steven D’Aprano for their considerable contributions to this proposal, and members of the core-mentorship mailing list for assistance with implementation.
Appendix A: Tim Peters’s findings
Here’s a brief essay Tim Peters wrote on the topic.
I dislike “busy” lines of code, and also dislike putting conceptually unrelated logic on a single line. So, for example, instead of:
instead. So I suspected I’d find few places I’d want to use assignment expressions. I didn’t even consider them for lines already stretching halfway across the screen. In other cases, “unrelated” ruled:
is a vast improvement over the briefer:
The original two statements are doing entirely different conceptual things, and slamming them together is conceptually insane.
In other cases, combining related logic made it harder to understand, such as rewriting:
as the briefer:
The while test there is too subtle, crucially relying on strict left-to-right evaluation in a non-short-circuiting or method-chaining context. My brain isn’t wired that way.
But cases like that were rare. Name binding is very frequent, and “sparse is better than dense” does not mean “almost empty is better than sparse”. For example, I have many functions that return None or 0 to communicate “I have nothing useful to return in this case, but since that’s expected often I’m not going to annoy you with an exception”. This is essentially the same as regular expression search functions returning None when there is no match. So there was lots of code of the form:
I find that clearer, and certainly a bit less typing and pattern-matching reading, as:
It’s also nice to trade away a small amount of horizontal whitespace to get another _line_ of surrounding code on screen. I didn’t give much weight to this at first, but it was so very frequent it added up, and I soon enough became annoyed that I couldn’t actually run the briefer code. That surprised me!
There are other cases where assignment expressions really shine. Rather than pick another from my code, Kirill Balunov gave a lovely example from the standard library’s copy() function in copy.py :
The ever-increasing indentation is semantically misleading: the logic is conceptually flat, “the first test that succeeds wins”:
Using easy assignment expressions allows the visual structure of the code to emphasize the conceptual flatness of the logic; ever-increasing indentation obscured it.
A smaller example from my code delighted me, both allowing to put inherently related logic in a single line, and allowing to remove an annoying “artificial” indentation level:
That if is about as long as I want my lines to get, but remains easy to follow.
So, in all, in most lines binding a name, I wouldn’t use assignment expressions, but because that construct is so very frequent, that leaves many places I would. In most of the latter, I found a small win that adds up due to how often it occurs, and in the rest I found a moderate to major win. I’d certainly use it more often than ternary if , but significantly less often than augmented assignment.
I have another example that quite impressed me at the time.
Where all variables are positive integers, and a is at least as large as the n’th root of x, this algorithm returns the floor of the n’th root of x (and roughly doubling the number of accurate bits per iteration):
It’s not obvious why that works, but is no more obvious in the “loop and a half” form. It’s hard to prove correctness without building on the right insight (the “arithmetic mean - geometric mean inequality”), and knowing some non-trivial things about how nested floor functions behave. That is, the challenges are in the math, not really in the coding.
If you do know all that, then the assignment-expression form is easily read as “while the current guess is too large, get a smaller guess”, where the “too large?” test and the new guess share an expensive sub-expression.
To my eyes, the original form is harder to understand:
This appendix attempts to clarify (though not specify) the rules when a target occurs in a comprehension or in a generator expression. For a number of illustrative examples we show the original code, containing a comprehension, and the translation, where the comprehension has been replaced by an equivalent generator function plus some scaffolding.
Since [x for ...] is equivalent to list(x for ...) these examples all use list comprehensions without loss of generality. And since these examples are meant to clarify edge cases of the rules, they aren’t trying to look like real code.
Note: comprehensions are already implemented via synthesizing nested generator functions like those in this appendix. The new part is adding appropriate declarations to establish the intended scope of assignment expression targets (the same scope they resolve to as if the assignment were performed in the block containing the outermost comprehension). For type inference purposes, these illustrative expansions do not imply that assignment expression targets are always Optional (but they do indicate the target binding scope).
Let’s start with a reminder of what code is generated for a generator expression without assignment expression.
- Original code (EXPR usually references VAR): def f (): a = [ EXPR for VAR in ITERABLE ]
- Translation (let’s not worry about name conflicts): def f (): def genexpr ( iterator ): for VAR in iterator : yield EXPR a = list ( genexpr ( iter ( ITERABLE )))
Let’s add a simple assignment expression.
- Original code: def f (): a = [ TARGET := EXPR for VAR in ITERABLE ]
- Translation: def f (): if False : TARGET = None # Dead code to ensure TARGET is a local variable def genexpr ( iterator ): nonlocal TARGET for VAR in iterator : TARGET = EXPR yield TARGET a = list ( genexpr ( iter ( ITERABLE )))
Let’s add a global TARGET declaration in f() .
- Original code: def f (): global TARGET a = [ TARGET := EXPR for VAR in ITERABLE ]
- Translation: def f (): global TARGET def genexpr ( iterator ): global TARGET for VAR in iterator : TARGET = EXPR yield TARGET a = list ( genexpr ( iter ( ITERABLE )))
Or instead let’s add a nonlocal TARGET declaration in f() .
- Original code: def g (): TARGET = ... def f (): nonlocal TARGET a = [ TARGET := EXPR for VAR in ITERABLE ]
- Translation: def g (): TARGET = ... def f (): nonlocal TARGET def genexpr ( iterator ): nonlocal TARGET for VAR in iterator : TARGET = EXPR yield TARGET a = list ( genexpr ( iter ( ITERABLE )))
Finally, let’s nest two comprehensions.
- Original code: def f (): a = [[ TARGET := i for i in range ( 3 )] for j in range ( 2 )] # I.e., a = [[0, 1, 2], [0, 1, 2]] print ( TARGET ) # prints 2
- Translation: def f (): if False : TARGET = None def outer_genexpr ( outer_iterator ): nonlocal TARGET def inner_generator ( inner_iterator ): nonlocal TARGET for i in inner_iterator : TARGET = i yield i for j in outer_iterator : yield list ( inner_generator ( range ( 3 ))) a = list ( outer_genexpr ( range ( 2 ))) print ( TARGET )
Because it has been a point of confusion, note that nothing about Python’s scoping semantics is changed. Function-local scopes continue to be resolved at compile time, and to have indefinite temporal extent at run time (“full closures”). Example:
This document has been placed in the public domain.
Source: https://github.com/python/peps/blob/main/peps/pep-0572.rst
Last modified: 2023-10-11 12:05:51 GMT
Python In-Place Assignment Operators
In-place assignment operators (also called compound assignment operators) perform an operation in-place on a variable provided as first operand. They overwrite the value of the first operand variable with the result of the operation when performing the operator without assignment. For example, x += 3 is the same as x = x + 3 of first calculating the result of x + 3 and then assigning it to the variable x.
| Operator | Short Example | Equivalent Long Example | |
|---|---|---|---|
| <<= |
You can watch me go over all of these operators in the following video:
![python assignment self [Overview] Python's In-Place Assignment Operators | Compound Operators](https://blog.finxter.com/wp-content/plugins/wp-youtube-lyte/lyteCache.php?origThumbUrl=https%3A%2F%2Fi.ytimg.com%2Fvi%2FzFQFJMJsACU%2F0.jpg)
We’ll rush over all in-place operators one-by-one next!
Python In-Place Addition
Python provides the operator x += y to add two objects in-place by calculating the sum x + y and assigning the result to the first operands variable name x . You can set up the in-place addition behavior for your own class by overriding the magic “dunder” method __iadd__(self, other) in your class definition.
The expression x += y is syntactical sugar for the longer-form x = x + y :
Related Tutorial: Python In-Place Addition
Python In-Place Subtraction
Python provides the operator x -= y to subtract two objects in-place by calculating the difference x - y and assigning the result to the first operands variable name x . You can set up the in-place subtraction behavior for your own class by overriding the magic “dunder” method __isub__(self, other) in your class definition.
The expression x -= y is syntactical sugar for the longer-form x = x - y :
Related Tutorial: Python In-Place Subtraction
Python In-Place Multiplication
Python provides the operator x *= y to multiply two objects in-place by calculating the product x * y and assigning the result to the first operands variable name x . You can set up the in-place multiplication behavior for your own class by overriding the magic “dunder” method __imul__(self, other) in your class definition.
The expression x *= y is syntactical sugar for the longer-form x = x * y :
Related Tutorial: Python In-Place Multiplication
Python In-Place Division
Python’s in-place division operator x /= y divides two objects in-place by calculating x / y and assigning the result to the first operands variable name x . Set up in-place division for your own class by overriding the magic “dunder” method __truediv__(self, other) in your class definition.
The expression x /= y is syntactical sugar for the longer-form x = x / y :
Related Tutorial: Python In-Place Division
Python In-Place Modulo
Python provides the operator x %= y to calculate the modulo operation x % y , and assign the result in-place to the first operands variable x . You can set up the in-place modulo behavior for your own class by overriding the magic “dunder” method __imod__(self, other) in your class definition.
The expression x %= y is syntactical sugar for the longer-form x = x % y :
Related Tutorial: Python In-Place Modulo
Python In-Place Integer Division
Python’s in-place integer division operator x //= y divides two objects in-place by calculating x // y and assigning the result to the first operands variable name x . Set up in-place integer (or floor) division for your own class by overriding the magic “dunder” method __floordiv__(self, other) in your class definition.
Related Tutorial: Python In-Place Integer Division
Python In-Place Exponentiation
Python provides the in-place exponentiation operator x **= y that raises x to the power of y using x ** y and assigns the result to the first operands variable name x . You can set up the in-place exponentiation behavior for your own class by overriding the magic “dunder” method __ipow__(self, other) in your class definition.
The expression x **= y is syntactical sugar for the longer-form x = x ** y :
Related Tutorial: Python In-Place Exponentiation
Python In-Place Bitwise AND
Python’s in-place bitwise AND operator x &= y calcualtes bitwise-and x & y and assigns the result to the first operand x . To set it up for your own class, override the magic “dunder” method __iand__(self, other) in your class definition.
The expression x &= y is syntactical sugar for the longer-form x = x & y :
Related Tutorial: Python In-Place Bitwise AND
Python In-Place Bitwise OR
Python’s A |= B applies the | operator in place. Thus, it is semantically identical to the longer-form version A = A | B of first performing the operation A | B and then assigning the result to the variable A .
The following minimal example creates two Boolean variables A and B and performs the in-place B |= A operation to perform a logical OR operation B | A and assigning the result to the first operand B that becomes True :
In this example, you’ve seen this in-place operation on Boolean operands. But the | operator is overloaded in Python. The three most frequent use cases for the | and |= operators are the following:
- Python Sets : set union operator
- Python Dictionaries : dictionary update operator
- Python Booleans : logical OR operator
Related Tutorial: Python In-Place Bitwise OR
Python In-Place Bitwise XOR
Python’s in-place bitwise XOR operator x ^= y calcualtes bitwise XOR x ^ y and assigns the result to the first operand x . To set this up for your own class, override the magic “dunder” method __ixor__(self, other) in your class definition.
The expression x ^ = y is syntactical sugar for the longer-form x = x ^ y :
Related Tutorial: Python In-Place Bitwise XOR
Python In-Place Bitwise Right-Shift
Python’s in-place bitwise right-shift operator x >>= y calculates the right-shift operation x >> y , and assigns the result to the first operands variable name x . You can set up the in-place right-shift behavior in your own class by overriding the magic “dunder” method __irshift__(self, other) in your class definition.
The expression x >>= y is syntactical sugar for the longer-form x = x >> y :
Related Tutorial: Python In-Place Bitwise Right-Shift
Python In-Place Bitwise Left-Shift
Python’s in-place bitwise left-shift operator x <<= y calculates the left-shift operation x << y , and assigns the result to the first operands variable name x . You can set up the in-place left-shift behavior in your own class by overriding the magic “dunder” method __ilshift__(self, other) in your class definition.
The expression x <<= y is syntactical sugar for the longer-form x = x << y :
Related Tutorial: Python In-Place Bitwise Left-Shift
Python In-Place Magic Methods
The following table provides the names of the magic methods you need to define to enable in-place operators on your custom class:
| Method Name | Description |
|---|---|
In the following code example, we create a custom class Data and define our “magic” double-underscore methods so that we can perform in-place computations on objects of this class.
Let’s try these out!
While working as a researcher in distributed systems, Dr. Christian Mayer found his love for teaching computer science students.
To help students reach higher levels of Python success, he founded the programming education website Finxter.com that has taught exponential skills to millions of coders worldwide. He’s the author of the best-selling programming books Python One-Liners (NoStarch 2020), The Art of Clean Code (NoStarch 2022), and The Book of Dash (NoStarch 2022). Chris also coauthored the Coffee Break Python series of self-published books. He’s a computer science enthusiast, freelancer , and owner of one of the top 10 largest Python blogs worldwide.
His passions are writing, reading, and coding. But his greatest passion is to serve aspiring coders through Finxter and help them to boost their skills. You can join his free email academy here.
- Python »
- 3.12.4 Documentation »
- The Python Standard Library »
- Development Tools »
- typing — Support for type hints
- Theme Auto Light Dark |
typing — Support for type hints ¶
Added in version 3.5.
Source code: Lib/typing.py
The Python runtime does not enforce function and variable type annotations. They can be used by third party tools such as type checkers , IDEs, linters, etc.
This module provides runtime support for type hints.
Consider the function below:
The function moon_weight takes an argument expected to be an instance of float , as indicated by the type hint earth_weight: float . The function is expected to return an instance of str , as indicated by the -> str hint.
While type hints can be simple classes like float or str , they can also be more complex. The typing module provides a vocabulary of more advanced type hints.
New features are frequently added to the typing module. The typing_extensions package provides backports of these new features to older versions of Python.
A quick overview of type hints (hosted at the mypy docs)
The Python typing system is standardised via PEPs, so this reference should broadly apply to most Python type checkers. (Some parts may still be specific to mypy.)
Type-checker-agnostic documentation written by the community detailing type system features, useful typing related tools and typing best practices.
Specification for the Python Type System ¶
The canonical, up-to-date specification of the Python type system can be found at “Specification for the Python type system” .
Type aliases ¶
A type alias is defined using the type statement, which creates an instance of TypeAliasType . In this example, Vector and list[float] will be treated equivalently by static type checkers:
Type aliases are useful for simplifying complex type signatures. For example:
The type statement is new in Python 3.12. For backwards compatibility, type aliases can also be created through simple assignment:
Or marked with TypeAlias to make it explicit that this is a type alias, not a normal variable assignment:
Use the NewType helper to create distinct types:
The static type checker will treat the new type as if it were a subclass of the original type. This is useful in helping catch logical errors:
You may still perform all int operations on a variable of type UserId , but the result will always be of type int . This lets you pass in a UserId wherever an int might be expected, but will prevent you from accidentally creating a UserId in an invalid way:
Note that these checks are enforced only by the static type checker. At runtime, the statement Derived = NewType('Derived', Base) will make Derived a callable that immediately returns whatever parameter you pass it. That means the expression Derived(some_value) does not create a new class or introduce much overhead beyond that of a regular function call.
More precisely, the expression some_value is Derived(some_value) is always true at runtime.
It is invalid to create a subtype of Derived :
However, it is possible to create a NewType based on a ‘derived’ NewType :
and typechecking for ProUserId will work as expected.
See PEP 484 for more details.
Recall that the use of a type alias declares two types to be equivalent to one another. Doing type Alias = Original will make the static type checker treat Alias as being exactly equivalent to Original in all cases. This is useful when you want to simplify complex type signatures.
In contrast, NewType declares one type to be a subtype of another. Doing Derived = NewType('Derived', Original) will make the static type checker treat Derived as a subclass of Original , which means a value of type Original cannot be used in places where a value of type Derived is expected. This is useful when you want to prevent logic errors with minimal runtime cost.
Added in version 3.5.2.
Changed in version 3.10: NewType is now a class rather than a function. As a result, there is some additional runtime cost when calling NewType over a regular function.
Changed in version 3.11: The performance of calling NewType has been restored to its level in Python 3.9.
Annotating callable objects ¶
Functions – or other callable objects – can be annotated using collections.abc.Callable or typing.Callable . Callable[[int], str] signifies a function that takes a single parameter of type int and returns a str .
For example:
The subscription syntax must always be used with exactly two values: the argument list and the return type. The argument list must be a list of types, a ParamSpec , Concatenate , or an ellipsis. The return type must be a single type.
If a literal ellipsis ... is given as the argument list, it indicates that a callable with any arbitrary parameter list would be acceptable:
Callable cannot express complex signatures such as functions that take a variadic number of arguments, overloaded functions , or functions that have keyword-only parameters. However, these signatures can be expressed by defining a Protocol class with a __call__() method:
Callables which take other callables as arguments may indicate that their parameter types are dependent on each other using ParamSpec . Additionally, if that callable adds or removes arguments from other callables, the Concatenate operator may be used. They take the form Callable[ParamSpecVariable, ReturnType] and Callable[Concatenate[Arg1Type, Arg2Type, ..., ParamSpecVariable], ReturnType] respectively.
Changed in version 3.10: Callable now supports ParamSpec and Concatenate . See PEP 612 for more details.
The documentation for ParamSpec and Concatenate provides examples of usage in Callable .
Since type information about objects kept in containers cannot be statically inferred in a generic way, many container classes in the standard library support subscription to denote the expected types of container elements.
Generic functions and classes can be parameterized by using type parameter syntax :
Or by using the TypeVar factory directly:
Changed in version 3.12: Syntactic support for generics is new in Python 3.12.
Annotating tuples ¶
For most containers in Python, the typing system assumes that all elements in the container will be of the same type. For example:
list only accepts one type argument, so a type checker would emit an error on the y assignment above. Similarly, Mapping only accepts two type arguments: the first indicates the type of the keys, and the second indicates the type of the values.
Unlike most other Python containers, however, it is common in idiomatic Python code for tuples to have elements which are not all of the same type. For this reason, tuples are special-cased in Python’s typing system. tuple accepts any number of type arguments:
To denote a tuple which could be of any length, and in which all elements are of the same type T , use tuple[T, ...] . To denote an empty tuple, use tuple[()] . Using plain tuple as an annotation is equivalent to using tuple[Any, ...] :
The type of class objects ¶
A variable annotated with C may accept a value of type C . In contrast, a variable annotated with type[C] (or typing.Type[C] ) may accept values that are classes themselves – specifically, it will accept the class object of C . For example:
Note that type[C] is covariant:
The only legal parameters for type are classes, Any , type variables , and unions of any of these types. For example:
type[Any] is equivalent to type , which is the root of Python’s metaclass hierarchy .
User-defined generic types ¶
A user-defined class can be defined as a generic class.
This syntax indicates that the class LoggedVar is parameterised around a single type variable T . This also makes T valid as a type within the class body.
Generic classes implicitly inherit from Generic . For compatibility with Python 3.11 and lower, it is also possible to inherit explicitly from Generic to indicate a generic class:
Generic classes have __class_getitem__() methods, meaning they can be parameterised at runtime (e.g. LoggedVar[int] below):
A generic type can have any number of type variables. All varieties of TypeVar are permissible as parameters for a generic type:
Each type variable argument to Generic must be distinct. This is thus invalid:
Generic classes can also inherit from other classes:
When inheriting from generic classes, some type parameters could be fixed:
In this case MyDict has a single parameter, T .
Using a generic class without specifying type parameters assumes Any for each position. In the following example, MyIterable is not generic but implicitly inherits from Iterable[Any] :
User-defined generic type aliases are also supported. Examples:
For backward compatibility, generic type aliases can also be created through a simple assignment:
Changed in version 3.7: Generic no longer has a custom metaclass.
Changed in version 3.12: Syntactic support for generics and type aliases is new in version 3.12. Previously, generic classes had to explicitly inherit from Generic or contain a type variable in one of their bases.
User-defined generics for parameter expressions are also supported via parameter specification variables in the form [**P] . The behavior is consistent with type variables’ described above as parameter specification variables are treated by the typing module as a specialized type variable. The one exception to this is that a list of types can be used to substitute a ParamSpec :
Classes generic over a ParamSpec can also be created using explicit inheritance from Generic . In this case, ** is not used:
Another difference between TypeVar and ParamSpec is that a generic with only one parameter specification variable will accept parameter lists in the forms X[[Type1, Type2, ...]] and also X[Type1, Type2, ...] for aesthetic reasons. Internally, the latter is converted to the former, so the following are equivalent:
Note that generics with ParamSpec may not have correct __parameters__ after substitution in some cases because they are intended primarily for static type checking.
Changed in version 3.10: Generic can now be parameterized over parameter expressions. See ParamSpec and PEP 612 for more details.
A user-defined generic class can have ABCs as base classes without a metaclass conflict. Generic metaclasses are not supported. The outcome of parameterizing generics is cached, and most types in the typing module are hashable and comparable for equality.
The Any type ¶
A special kind of type is Any . A static type checker will treat every type as being compatible with Any and Any as being compatible with every type.
This means that it is possible to perform any operation or method call on a value of type Any and assign it to any variable:
Notice that no type checking is performed when assigning a value of type Any to a more precise type. For example, the static type checker did not report an error when assigning a to s even though s was declared to be of type str and receives an int value at runtime!
Furthermore, all functions without a return type or parameter types will implicitly default to using Any :
This behavior allows Any to be used as an escape hatch when you need to mix dynamically and statically typed code.
Contrast the behavior of Any with the behavior of object . Similar to Any , every type is a subtype of object . However, unlike Any , the reverse is not true: object is not a subtype of every other type.
That means when the type of a value is object , a type checker will reject almost all operations on it, and assigning it to a variable (or using it as a return value) of a more specialized type is a type error. For example:
Use object to indicate that a value could be any type in a typesafe manner. Use Any to indicate that a value is dynamically typed.
Nominal vs structural subtyping ¶
Initially PEP 484 defined the Python static type system as using nominal subtyping . This means that a class A is allowed where a class B is expected if and only if A is a subclass of B .
This requirement previously also applied to abstract base classes, such as Iterable . The problem with this approach is that a class had to be explicitly marked to support them, which is unpythonic and unlike what one would normally do in idiomatic dynamically typed Python code. For example, this conforms to PEP 484 :
PEP 544 allows to solve this problem by allowing users to write the above code without explicit base classes in the class definition, allowing Bucket to be implicitly considered a subtype of both Sized and Iterable[int] by static type checkers. This is known as structural subtyping (or static duck-typing):
Moreover, by subclassing a special class Protocol , a user can define new custom protocols to fully enjoy structural subtyping (see examples below).
Module contents ¶
The typing module defines the following classes, functions and decorators.
Special typing primitives ¶
Special types ¶.
These can be used as types in annotations. They do not support subscription using [] .
Special type indicating an unconstrained type.
Every type is compatible with Any .
Any is compatible with every type.
Changed in version 3.11: Any can now be used as a base class. This can be useful for avoiding type checker errors with classes that can duck type anywhere or are highly dynamic.
A constrained type variable .
Definition:
AnyStr is meant to be used for functions that may accept str or bytes arguments but cannot allow the two to mix.
Note that, despite its name, AnyStr has nothing to do with the Any type, nor does it mean “any string”. In particular, AnyStr and str | bytes are different from each other and have different use cases:
Special type that includes only literal strings.
Any string literal is compatible with LiteralString , as is another LiteralString . However, an object typed as just str is not. A string created by composing LiteralString -typed objects is also acceptable as a LiteralString .
LiteralString is useful for sensitive APIs where arbitrary user-generated strings could generate problems. For example, the two cases above that generate type checker errors could be vulnerable to an SQL injection attack.
See PEP 675 for more details.
Added in version 3.11.
Never and NoReturn represent the bottom type , a type that has no members.
They can be used to indicate that a function never returns, such as sys.exit() :
Or to define a function that should never be called, as there are no valid arguments, such as assert_never() :
Never and NoReturn have the same meaning in the type system and static type checkers treat both equivalently.
Added in version 3.6.2: Added NoReturn .
Added in version 3.11: Added Never .
Special type to represent the current enclosed class.
This annotation is semantically equivalent to the following, albeit in a more succinct fashion:
In general, if something returns self , as in the above examples, you should use Self as the return annotation. If Foo.return_self was annotated as returning "Foo" , then the type checker would infer the object returned from SubclassOfFoo.return_self as being of type Foo rather than SubclassOfFoo .
Other common use cases include:
classmethod s that are used as alternative constructors and return instances of the cls parameter.
Annotating an __enter__() method which returns self.
You should not use Self as the return annotation if the method is not guaranteed to return an instance of a subclass when the class is subclassed:
See PEP 673 for more details.
Special annotation for explicitly declaring a type alias .
TypeAlias is particularly useful on older Python versions for annotating aliases that make use of forward references, as it can be hard for type checkers to distinguish these from normal variable assignments:
See PEP 613 for more details.
Added in version 3.10.
Deprecated since version 3.12: TypeAlias is deprecated in favor of the type statement, which creates instances of TypeAliasType and which natively supports forward references. Note that while TypeAlias and TypeAliasType serve similar purposes and have similar names, they are distinct and the latter is not the type of the former. Removal of TypeAlias is not currently planned, but users are encouraged to migrate to type statements.
Special forms ¶
These can be used as types in annotations. They all support subscription using [] , but each has a unique syntax.
Union type; Union[X, Y] is equivalent to X | Y and means either X or Y.
To define a union, use e.g. Union[int, str] or the shorthand int | str . Using that shorthand is recommended. Details:
The arguments must be types and there must be at least one.
Unions of unions are flattened, e.g.:
Unions of a single argument vanish, e.g.:
Redundant arguments are skipped, e.g.:
When comparing unions, the argument order is ignored, e.g.:
You cannot subclass or instantiate a Union .
You cannot write Union[X][Y] .
Changed in version 3.7: Don’t remove explicit subclasses from unions at runtime.
Changed in version 3.10: Unions can now be written as X | Y . See union type expressions .
Optional[X] is equivalent to X | None (or Union[X, None] ).
Note that this is not the same concept as an optional argument, which is one that has a default. An optional argument with a default does not require the Optional qualifier on its type annotation just because it is optional. For example:
On the other hand, if an explicit value of None is allowed, the use of Optional is appropriate, whether the argument is optional or not. For example:
Changed in version 3.10: Optional can now be written as X | None . See union type expressions .
Special form for annotating higher-order functions.
Concatenate can be used in conjunction with Callable and ParamSpec to annotate a higher-order callable which adds, removes, or transforms parameters of another callable. Usage is in the form Concatenate[Arg1Type, Arg2Type, ..., ParamSpecVariable] . Concatenate is currently only valid when used as the first argument to a Callable . The last parameter to Concatenate must be a ParamSpec or ellipsis ( ... ).
For example, to annotate a decorator with_lock which provides a threading.Lock to the decorated function, Concatenate can be used to indicate that with_lock expects a callable which takes in a Lock as the first argument, and returns a callable with a different type signature. In this case, the ParamSpec indicates that the returned callable’s parameter types are dependent on the parameter types of the callable being passed in:
PEP 612 – Parameter Specification Variables (the PEP which introduced ParamSpec and Concatenate )
- Annotating callable objects
Special typing form to define “literal types”.
Literal can be used to indicate to type checkers that the annotated object has a value equivalent to one of the provided literals.
Literal[...] cannot be subclassed. At runtime, an arbitrary value is allowed as type argument to Literal[...] , but type checkers may impose restrictions. See PEP 586 for more details about literal types.
Added in version 3.8.
Changed in version 3.9.1: Literal now de-duplicates parameters. Equality comparisons of Literal objects are no longer order dependent. Literal objects will now raise a TypeError exception during equality comparisons if one of their parameters are not hashable .
Special type construct to mark class variables.
As introduced in PEP 526 , a variable annotation wrapped in ClassVar indicates that a given attribute is intended to be used as a class variable and should not be set on instances of that class. Usage:
ClassVar accepts only types and cannot be further subscribed.
ClassVar is not a class itself, and should not be used with isinstance() or issubclass() . ClassVar does not change Python runtime behavior, but it can be used by third-party type checkers. For example, a type checker might flag the following code as an error:
Added in version 3.5.3.
Special typing construct to indicate final names to type checkers.
Final names cannot be reassigned in any scope. Final names declared in class scopes cannot be overridden in subclasses.
There is no runtime checking of these properties. See PEP 591 for more details.
Special typing construct to mark a TypedDict key as required.
This is mainly useful for total=False TypedDicts. See TypedDict and PEP 655 for more details.
Special typing construct to mark a TypedDict key as potentially missing.
See TypedDict and PEP 655 for more details.
Special typing form to add context-specific metadata to an annotation.
Add metadata x to a given type T by using the annotation Annotated[T, x] . Metadata added using Annotated can be used by static analysis tools or at runtime. At runtime, the metadata is stored in a __metadata__ attribute.
If a library or tool encounters an annotation Annotated[T, x] and has no special logic for the metadata, it should ignore the metadata and simply treat the annotation as T . As such, Annotated can be useful for code that wants to use annotations for purposes outside Python’s static typing system.
Using Annotated[T, x] as an annotation still allows for static typechecking of T , as type checkers will simply ignore the metadata x . In this way, Annotated differs from the @no_type_check decorator, which can also be used for adding annotations outside the scope of the typing system, but completely disables typechecking for a function or class.
The responsibility of how to interpret the metadata lies with the tool or library encountering an Annotated annotation. A tool or library encountering an Annotated type can scan through the metadata elements to determine if they are of interest (e.g., using isinstance() ).
Here is an example of how you might use Annotated to add metadata to type annotations if you were doing range analysis:
Details of the syntax:
The first argument to Annotated must be a valid type
Multiple metadata elements can be supplied ( Annotated supports variadic arguments):
It is up to the tool consuming the annotations to decide whether the client is allowed to add multiple metadata elements to one annotation and how to merge those annotations.
Annotated must be subscripted with at least two arguments ( Annotated[int] is not valid)
The order of the metadata elements is preserved and matters for equality checks:
Nested Annotated types are flattened. The order of the metadata elements starts with the innermost annotation:
Duplicated metadata elements are not removed:
Annotated can be used with nested and generic aliases:
Annotated cannot be used with an unpacked TypeVarTuple :
This would be equivalent to:
where T1 , T2 , etc. are TypeVars . This would be invalid: only one type should be passed to Annotated.
By default, get_type_hints() strips the metadata from annotations. Pass include_extras=True to have the metadata preserved:
At runtime, the metadata associated with an Annotated type can be retrieved via the __metadata__ attribute:
The PEP introducing Annotated to the standard library.
Added in version 3.9.
Special typing construct for marking user-defined type guard functions.
TypeGuard can be used to annotate the return type of a user-defined type guard function. TypeGuard only accepts a single type argument. At runtime, functions marked this way should return a boolean.
TypeGuard aims to benefit type narrowing – a technique used by static type checkers to determine a more precise type of an expression within a program’s code flow. Usually type narrowing is done by analyzing conditional code flow and applying the narrowing to a block of code. The conditional expression here is sometimes referred to as a “type guard”:
Sometimes it would be convenient to use a user-defined boolean function as a type guard. Such a function should use TypeGuard[...] as its return type to alert static type checkers to this intention.
Using -> TypeGuard tells the static type checker that for a given function:
The return value is a boolean.
If the return value is True , the type of its argument is the type inside TypeGuard .
If is_str_list is a class or instance method, then the type in TypeGuard maps to the type of the second parameter after cls or self .
In short, the form def foo(arg: TypeA) -> TypeGuard[TypeB]: ... , means that if foo(arg) returns True , then arg narrows from TypeA to TypeB .
TypeB need not be a narrower form of TypeA – it can even be a wider form. The main reason is to allow for things like narrowing list[object] to list[str] even though the latter is not a subtype of the former, since list is invariant. The responsibility of writing type-safe type guards is left to the user.
TypeGuard also works with type variables. See PEP 647 for more details.
Typing operator to conceptually mark an object as having been unpacked.
For example, using the unpack operator * on a type variable tuple is equivalent to using Unpack to mark the type variable tuple as having been unpacked:
In fact, Unpack can be used interchangeably with * in the context of typing.TypeVarTuple and builtins.tuple types. You might see Unpack being used explicitly in older versions of Python, where * couldn’t be used in certain places:
Unpack can also be used along with typing.TypedDict for typing **kwargs in a function signature:
See PEP 692 for more details on using Unpack for **kwargs typing.
Building generic types and type aliases ¶
The following classes should not be used directly as annotations. Their intended purpose is to be building blocks for creating generic types and type aliases.
These objects can be created through special syntax ( type parameter lists and the type statement). For compatibility with Python 3.11 and earlier, they can also be created without the dedicated syntax, as documented below.
Abstract base class for generic types.
A generic type is typically declared by adding a list of type parameters after the class name:
Such a class implicitly inherits from Generic . The runtime semantics of this syntax are discussed in the Language Reference .
This class can then be used as follows:
Here the brackets after the function name indicate a generic function .
For backwards compatibility, generic classes can also be declared by explicitly inheriting from Generic . In this case, the type parameters must be declared separately:
Type variable.
The preferred way to construct a type variable is via the dedicated syntax for generic functions , generic classes , and generic type aliases :
This syntax can also be used to create bound and constrained type variables:
However, if desired, reusable type variables can also be constructed manually, like so:
Type variables exist primarily for the benefit of static type checkers. They serve as the parameters for generic types as well as for generic function and type alias definitions. See Generic for more information on generic types. Generic functions work as follows:
Note that type variables can be bound , constrained , or neither, but cannot be both bound and constrained.
The variance of type variables is inferred by type checkers when they are created through the type parameter syntax or when infer_variance=True is passed. Manually created type variables may be explicitly marked covariant or contravariant by passing covariant=True or contravariant=True . By default, manually created type variables are invariant. See PEP 484 and PEP 695 for more details.
Bound type variables and constrained type variables have different semantics in several important ways. Using a bound type variable means that the TypeVar will be solved using the most specific type possible:
Type variables can be bound to concrete types, abstract types (ABCs or protocols), and even unions of types:
Using a constrained type variable, however, means that the TypeVar can only ever be solved as being exactly one of the constraints given:
At runtime, isinstance(x, T) will raise TypeError .
The name of the type variable.
Whether the type var has been explicitly marked as covariant.
Whether the type var has been explicitly marked as contravariant.
Whether the type variable’s variance should be inferred by type checkers.
Added in version 3.12.
The bound of the type variable, if any.
Changed in version 3.12: For type variables created through type parameter syntax , the bound is evaluated only when the attribute is accessed, not when the type variable is created (see Lazy evaluation ).
A tuple containing the constraints of the type variable, if any.
Changed in version 3.12: For type variables created through type parameter syntax , the constraints are evaluated only when the attribute is accessed, not when the type variable is created (see Lazy evaluation ).
Changed in version 3.12: Type variables can now be declared using the type parameter syntax introduced by PEP 695 . The infer_variance parameter was added.
Type variable tuple. A specialized form of type variable that enables variadic generics.
Type variable tuples can be declared in type parameter lists using a single asterisk ( * ) before the name:
Or by explicitly invoking the TypeVarTuple constructor:
A normal type variable enables parameterization with a single type. A type variable tuple, in contrast, allows parameterization with an arbitrary number of types by acting like an arbitrary number of type variables wrapped in a tuple. For example:
Note the use of the unpacking operator * in tuple[T, *Ts] . Conceptually, you can think of Ts as a tuple of type variables (T1, T2, ...) . tuple[T, *Ts] would then become tuple[T, *(T1, T2, ...)] , which is equivalent to tuple[T, T1, T2, ...] . (Note that in older versions of Python, you might see this written using Unpack instead, as Unpack[Ts] .)
Type variable tuples must always be unpacked. This helps distinguish type variable tuples from normal type variables:
Type variable tuples can be used in the same contexts as normal type variables. For example, in class definitions, arguments, and return types:
Type variable tuples can be happily combined with normal type variables:
However, note that at most one type variable tuple may appear in a single list of type arguments or type parameters:
Finally, an unpacked type variable tuple can be used as the type annotation of *args :
In contrast to non-unpacked annotations of *args - e.g. *args: int , which would specify that all arguments are int - *args: *Ts enables reference to the types of the individual arguments in *args . Here, this allows us to ensure the types of the *args passed to call_soon match the types of the (positional) arguments of callback .
See PEP 646 for more details on type variable tuples.
The name of the type variable tuple.
Changed in version 3.12: Type variable tuples can now be declared using the type parameter syntax introduced by PEP 695 .
Parameter specification variable. A specialized version of type variables .
In type parameter lists , parameter specifications can be declared with two asterisks ( ** ):
For compatibility with Python 3.11 and earlier, ParamSpec objects can also be created as follows:
Parameter specification variables exist primarily for the benefit of static type checkers. They are used to forward the parameter types of one callable to another callable – a pattern commonly found in higher order functions and decorators. They are only valid when used in Concatenate , or as the first argument to Callable , or as parameters for user-defined Generics. See Generic for more information on generic types.
For example, to add basic logging to a function, one can create a decorator add_logging to log function calls. The parameter specification variable tells the type checker that the callable passed into the decorator and the new callable returned by it have inter-dependent type parameters:
Without ParamSpec , the simplest way to annotate this previously was to use a TypeVar with bound Callable[..., Any] . However this causes two problems:
The type checker can’t type check the inner function because *args and **kwargs have to be typed Any .
cast() may be required in the body of the add_logging decorator when returning the inner function, or the static type checker must be told to ignore the return inner .
Since ParamSpec captures both positional and keyword parameters, P.args and P.kwargs can be used to split a ParamSpec into its components. P.args represents the tuple of positional parameters in a given call and should only be used to annotate *args . P.kwargs represents the mapping of keyword parameters to their values in a given call, and should be only be used to annotate **kwargs . Both attributes require the annotated parameter to be in scope. At runtime, P.args and P.kwargs are instances respectively of ParamSpecArgs and ParamSpecKwargs .
The name of the parameter specification.
Parameter specification variables created with covariant=True or contravariant=True can be used to declare covariant or contravariant generic types. The bound argument is also accepted, similar to TypeVar . However the actual semantics of these keywords are yet to be decided.
Changed in version 3.12: Parameter specifications can now be declared using the type parameter syntax introduced by PEP 695 .
Only parameter specification variables defined in global scope can be pickled.
Concatenate
Arguments and keyword arguments attributes of a ParamSpec . The P.args attribute of a ParamSpec is an instance of ParamSpecArgs , and P.kwargs is an instance of ParamSpecKwargs . They are intended for runtime introspection and have no special meaning to static type checkers.
Calling get_origin() on either of these objects will return the original ParamSpec :
The type of type aliases created through the type statement.
The name of the type alias:
The module in which the type alias was defined:
The type parameters of the type alias, or an empty tuple if the alias is not generic:
The type alias’s value. This is lazily evaluated , so names used in the definition of the alias are not resolved until the __value__ attribute is accessed:
Other special directives ¶
These functions and classes should not be used directly as annotations. Their intended purpose is to be building blocks for creating and declaring types.
Typed version of collections.namedtuple() .
This is equivalent to:
To give a field a default value, you can assign to it in the class body:
Fields with a default value must come after any fields without a default.
The resulting class has an extra attribute __annotations__ giving a dict that maps the field names to the field types. (The field names are in the _fields attribute and the default values are in the _field_defaults attribute, both of which are part of the namedtuple() API.)
NamedTuple subclasses can also have docstrings and methods:
NamedTuple subclasses can be generic:
Backward-compatible usage:
Changed in version 3.6: Added support for PEP 526 variable annotation syntax.
Changed in version 3.6.1: Added support for default values, methods, and docstrings.
Changed in version 3.8: The _field_types and __annotations__ attributes are now regular dictionaries instead of instances of OrderedDict .
Changed in version 3.9: Removed the _field_types attribute in favor of the more standard __annotations__ attribute which has the same information.
Changed in version 3.11: Added support for generic namedtuples.
Helper class to create low-overhead distinct types .
A NewType is considered a distinct type by a typechecker. At runtime, however, calling a NewType returns its argument unchanged.
The module in which the new type is defined.
The name of the new type.
The type that the new type is based on.
Changed in version 3.10: NewType is now a class rather than a function.
Base class for protocol classes.
Protocol classes are defined like this:
Such classes are primarily used with static type checkers that recognize structural subtyping (static duck-typing), for example:
See PEP 544 for more details. Protocol classes decorated with runtime_checkable() (described later) act as simple-minded runtime protocols that check only the presence of given attributes, ignoring their type signatures.
Protocol classes can be generic, for example:
In code that needs to be compatible with Python 3.11 or older, generic Protocols can be written as follows:
Mark a protocol class as a runtime protocol.
Such a protocol can be used with isinstance() and issubclass() . This raises TypeError when applied to a non-protocol class. This allows a simple-minded structural check, very similar to “one trick ponies” in collections.abc such as Iterable . For example:
runtime_checkable() will check only the presence of the required methods or attributes, not their type signatures or types. For example, ssl.SSLObject is a class, therefore it passes an issubclass() check against Callable . However, the ssl.SSLObject.__init__ method exists only to raise a TypeError with a more informative message, therefore making it impossible to call (instantiate) ssl.SSLObject .
An isinstance() check against a runtime-checkable protocol can be surprisingly slow compared to an isinstance() check against a non-protocol class. Consider using alternative idioms such as hasattr() calls for structural checks in performance-sensitive code.
Changed in version 3.12: The internal implementation of isinstance() checks against runtime-checkable protocols now uses inspect.getattr_static() to look up attributes (previously, hasattr() was used). As a result, some objects which used to be considered instances of a runtime-checkable protocol may no longer be considered instances of that protocol on Python 3.12+, and vice versa. Most users are unlikely to be affected by this change.
Changed in version 3.12: The members of a runtime-checkable protocol are now considered “frozen” at runtime as soon as the class has been created. Monkey-patching attributes onto a runtime-checkable protocol will still work, but will have no impact on isinstance() checks comparing objects to the protocol. See “What’s new in Python 3.12” for more details.
Special construct to add type hints to a dictionary. At runtime it is a plain dict .
TypedDict declares a dictionary type that expects all of its instances to have a certain set of keys, where each key is associated with a value of a consistent type. This expectation is not checked at runtime but is only enforced by type checkers. Usage:
To allow using this feature with older versions of Python that do not support PEP 526 , TypedDict supports two additional equivalent syntactic forms:
Using a literal dict as the second argument:
Using keyword arguments:
Deprecated since version 3.11, will be removed in version 3.13: The keyword-argument syntax is deprecated in 3.11 and will be removed in 3.13. It may also be unsupported by static type checkers.
The functional syntax should also be used when any of the keys are not valid identifiers , for example because they are keywords or contain hyphens. Example:
By default, all keys must be present in a TypedDict . It is possible to mark individual keys as non-required using NotRequired :
This means that a Point2D TypedDict can have the label key omitted.
It is also possible to mark all keys as non-required by default by specifying a totality of False :
This means that a Point2D TypedDict can have any of the keys omitted. A type checker is only expected to support a literal False or True as the value of the total argument. True is the default, and makes all items defined in the class body required.
Individual keys of a total=False TypedDict can be marked as required using Required :
It is possible for a TypedDict type to inherit from one or more other TypedDict types using the class-based syntax. Usage:
Point3D has three items: x , y and z . It is equivalent to this definition:
A TypedDict cannot inherit from a non- TypedDict class, except for Generic . For example:
A TypedDict can be generic:
To create a generic TypedDict that is compatible with Python 3.11 or lower, inherit from Generic explicitly:
A TypedDict can be introspected via annotations dicts (see Annotations Best Practices for more information on annotations best practices), __total__ , __required_keys__ , and __optional_keys__ .
Point2D.__total__ gives the value of the total argument. Example:
This attribute reflects only the value of the total argument to the current TypedDict class, not whether the class is semantically total. For example, a TypedDict with __total__ set to True may have keys marked with NotRequired , or it may inherit from another TypedDict with total=False . Therefore, it is generally better to use __required_keys__ and __optional_keys__ for introspection.
Point2D.__required_keys__ and Point2D.__optional_keys__ return frozenset objects containing required and non-required keys, respectively.
Keys marked with Required will always appear in __required_keys__ and keys marked with NotRequired will always appear in __optional_keys__ .
For backwards compatibility with Python 3.10 and below, it is also possible to use inheritance to declare both required and non-required keys in the same TypedDict . This is done by declaring a TypedDict with one value for the total argument and then inheriting from it in another TypedDict with a different value for total :
If from __future__ import annotations is used or if annotations are given as strings, annotations are not evaluated when the TypedDict is defined. Therefore, the runtime introspection that __required_keys__ and __optional_keys__ rely on may not work properly, and the values of the attributes may be incorrect.
See PEP 589 for more examples and detailed rules of using TypedDict .
Changed in version 3.11: Added support for marking individual keys as Required or NotRequired . See PEP 655 .
Changed in version 3.11: Added support for generic TypedDict s.
Protocols ¶
The following protocols are provided by the typing module. All are decorated with @runtime_checkable .
An ABC with one abstract method __abs__ that is covariant in its return type.
An ABC with one abstract method __bytes__ .
An ABC with one abstract method __complex__ .
An ABC with one abstract method __float__ .
An ABC with one abstract method __index__ .
An ABC with one abstract method __int__ .
An ABC with one abstract method __round__ that is covariant in its return type.
ABCs for working with IO ¶
Generic type IO[AnyStr] and its subclasses TextIO(IO[str]) and BinaryIO(IO[bytes]) represent the types of I/O streams such as returned by open() .
Functions and decorators ¶
Cast a value to a type.
This returns the value unchanged. To the type checker this signals that the return value has the designated type, but at runtime we intentionally don’t check anything (we want this to be as fast as possible).
Ask a static type checker to confirm that val has an inferred type of typ .
At runtime this does nothing: it returns the first argument unchanged with no checks or side effects, no matter the actual type of the argument.
When a static type checker encounters a call to assert_type() , it emits an error if the value is not of the specified type:
This function is useful for ensuring the type checker’s understanding of a script is in line with the developer’s intentions:
Ask a static type checker to confirm that a line of code is unreachable.
Here, the annotations allow the type checker to infer that the last case can never execute, because arg is either an int or a str , and both options are covered by earlier cases.
If a type checker finds that a call to assert_never() is reachable, it will emit an error. For example, if the type annotation for arg was instead int | str | float , the type checker would emit an error pointing out that unreachable is of type float . For a call to assert_never to pass type checking, the inferred type of the argument passed in must be the bottom type, Never , and nothing else.
At runtime, this throws an exception when called.
Unreachable Code and Exhaustiveness Checking has more information about exhaustiveness checking with static typing.
Ask a static type checker to reveal the inferred type of an expression.
When a static type checker encounters a call to this function, it emits a diagnostic with the inferred type of the argument. For example:
This can be useful when you want to debug how your type checker handles a particular piece of code.
At runtime, this function prints the runtime type of its argument to sys.stderr and returns the argument unchanged (allowing the call to be used within an expression):
Note that the runtime type may be different from (more or less specific than) the type statically inferred by a type checker.
Most type checkers support reveal_type() anywhere, even if the name is not imported from typing . Importing the name from typing , however, allows your code to run without runtime errors and communicates intent more clearly.
Decorator to mark an object as providing dataclass -like behavior.
dataclass_transform may be used to decorate a class, metaclass, or a function that is itself a decorator. The presence of @dataclass_transform() tells a static type checker that the decorated object performs runtime “magic” that transforms a class in a similar way to @dataclasses.dataclass .
Example usage with a decorator function:
On a base class:
On a metaclass:
The CustomerModel classes defined above will be treated by type checkers similarly to classes created with @dataclasses.dataclass . For example, type checkers will assume these classes have __init__ methods that accept id and name .
The decorated class, metaclass, or function may accept the following bool arguments which type checkers will assume have the same effect as they would have on the @dataclasses.dataclass decorator: init , eq , order , unsafe_hash , frozen , match_args , kw_only , and slots . It must be possible for the value of these arguments ( True or False ) to be statically evaluated.
The arguments to the dataclass_transform decorator can be used to customize the default behaviors of the decorated class, metaclass, or function:
eq_default ( bool ) – Indicates whether the eq parameter is assumed to be True or False if it is omitted by the caller. Defaults to True .
order_default ( bool ) – Indicates whether the order parameter is assumed to be True or False if it is omitted by the caller. Defaults to False .
kw_only_default ( bool ) – Indicates whether the kw_only parameter is assumed to be True or False if it is omitted by the caller. Defaults to False .
Indicates whether the frozen parameter is assumed to be True or False if it is omitted by the caller. Defaults to False .
field_specifiers ( tuple [ Callable [ ... , Any ] , ... ] ) – Specifies a static list of supported classes or functions that describe fields, similar to dataclasses.field() . Defaults to () .
**kwargs ( Any ) – Arbitrary other keyword arguments are accepted in order to allow for possible future extensions.
Type checkers recognize the following optional parameters on field specifiers:
Parameter name | Description |
|---|---|
| Indicates whether the field should be included in the synthesized method. If unspecified, defaults to . |
| Provides the default value for the field. |
| Provides a runtime callback that returns the default value for the field. If neither nor are specified, the field is assumed to have no default value and must be provided a value when the class is instantiated. |
| An alias for the parameter on field specifiers. |
| Indicates whether the field should be marked as keyword-only. If , the field will be keyword-only. If , it will not be keyword-only. If unspecified, the value of the parameter on the object decorated with will be used, or if that is unspecified, the value of on will be used. |
| Provides an alternative name for the field. This alternative name is used in the synthesized method. |
At runtime, this decorator records its arguments in the __dataclass_transform__ attribute on the decorated object. It has no other runtime effect.
See PEP 681 for more details.
Decorator for creating overloaded functions and methods.
The @overload decorator allows describing functions and methods that support multiple different combinations of argument types. A series of @overload -decorated definitions must be followed by exactly one non- @overload -decorated definition (for the same function/method).
@overload -decorated definitions are for the benefit of the type checker only, since they will be overwritten by the non- @overload -decorated definition. The non- @overload -decorated definition, meanwhile, will be used at runtime but should be ignored by a type checker. At runtime, calling an @overload -decorated function directly will raise NotImplementedError .
An example of overload that gives a more precise type than can be expressed using a union or a type variable:
See PEP 484 for more details and comparison with other typing semantics.
Changed in version 3.11: Overloaded functions can now be introspected at runtime using get_overloads() .
Return a sequence of @overload -decorated definitions for func .
func is the function object for the implementation of the overloaded function. For example, given the definition of process in the documentation for @overload , get_overloads(process) will return a sequence of three function objects for the three defined overloads. If called on a function with no overloads, get_overloads() returns an empty sequence.
get_overloads() can be used for introspecting an overloaded function at runtime.
Clear all registered overloads in the internal registry.
This can be used to reclaim the memory used by the registry.
Decorator to indicate final methods and final classes.
Decorating a method with @final indicates to a type checker that the method cannot be overridden in a subclass. Decorating a class with @final indicates that it cannot be subclassed.
Changed in version 3.11: The decorator will now attempt to set a __final__ attribute to True on the decorated object. Thus, a check like if getattr(obj, "__final__", False) can be used at runtime to determine whether an object obj has been marked as final. If the decorated object does not support setting attributes, the decorator returns the object unchanged without raising an exception.
Decorator to indicate that annotations are not type hints.
This works as a class or function decorator . With a class, it applies recursively to all methods and classes defined in that class (but not to methods defined in its superclasses or subclasses). Type checkers will ignore all annotations in a function or class with this decorator.
@no_type_check mutates the decorated object in place.
Decorator to give another decorator the no_type_check() effect.
This wraps the decorator with something that wraps the decorated function in no_type_check() .
Decorator to indicate that a method in a subclass is intended to override a method or attribute in a superclass.
Type checkers should emit an error if a method decorated with @override does not, in fact, override anything. This helps prevent bugs that may occur when a base class is changed without an equivalent change to a child class.
There is no runtime checking of this property.
The decorator will attempt to set an __override__ attribute to True on the decorated object. Thus, a check like if getattr(obj, "__override__", False) can be used at runtime to determine whether an object obj has been marked as an override. If the decorated object does not support setting attributes, the decorator returns the object unchanged without raising an exception.
See PEP 698 for more details.
Decorator to mark a class or function as unavailable at runtime.
This decorator is itself not available at runtime. It is mainly intended to mark classes that are defined in type stub files if an implementation returns an instance of a private class:
Note that returning instances of private classes is not recommended. It is usually preferable to make such classes public.
Introspection helpers ¶
Return a dictionary containing type hints for a function, method, module or class object.
This is often the same as obj.__annotations__ , but this function makes the following changes to the annotations dictionary:
Forward references encoded as string literals or ForwardRef objects are handled by evaluating them in globalns , localns , and (where applicable) obj ’s type parameter namespace. If globalns or localns is not given, appropriate namespace dictionaries are inferred from obj .
None is replaced with types.NoneType .
If @no_type_check has been applied to obj , an empty dictionary is returned.
If obj is a class C , the function returns a dictionary that merges annotations from C ’s base classes with those on C directly. This is done by traversing C.__mro__ and iteratively combining __annotations__ dictionaries. Annotations on classes appearing earlier in the method resolution order always take precedence over annotations on classes appearing later in the method resolution order.
The function recursively replaces all occurrences of Annotated[T, ...] with T , unless include_extras is set to True (see Annotated for more information).
See also inspect.get_annotations() , a lower-level function that returns annotations more directly.
If any forward references in the annotations of obj are not resolvable or are not valid Python code, this function will raise an exception such as NameError . For example, this can happen with imported type aliases that include forward references, or with names imported under if TYPE_CHECKING .
Changed in version 3.9: Added include_extras parameter as part of PEP 593 . See the documentation on Annotated for more information.
Changed in version 3.11: Previously, Optional[t] was added for function and method annotations if a default value equal to None was set. Now the annotation is returned unchanged.
Get the unsubscripted version of a type: for a typing object of the form X[Y, Z, ...] return X .
If X is a typing-module alias for a builtin or collections class, it will be normalized to the original class. If X is an instance of ParamSpecArgs or ParamSpecKwargs , return the underlying ParamSpec . Return None for unsupported objects.
Get type arguments with all substitutions performed: for a typing object of the form X[Y, Z, ...] return (Y, Z, ...) .
If X is a union or Literal contained in another generic type, the order of (Y, Z, ...) may be different from the order of the original arguments [Y, Z, ...] due to type caching. Return () for unsupported objects.
Check if a type is a TypedDict .
Class used for internal typing representation of string forward references.
For example, List["SomeClass"] is implicitly transformed into List[ForwardRef("SomeClass")] . ForwardRef should not be instantiated by a user, but may be used by introspection tools.
PEP 585 generic types such as list["SomeClass"] will not be implicitly transformed into list[ForwardRef("SomeClass")] and thus will not automatically resolve to list[SomeClass] .
Added in version 3.7.4.
A special constant that is assumed to be True by 3rd party static type checkers. It is False at runtime.
The first type annotation must be enclosed in quotes, making it a “forward reference”, to hide the expensive_mod reference from the interpreter runtime. Type annotations for local variables are not evaluated, so the second annotation does not need to be enclosed in quotes.
If from __future__ import annotations is used, annotations are not evaluated at function definition time. Instead, they are stored as strings in __annotations__ . This makes it unnecessary to use quotes around the annotation (see PEP 563 ).
Deprecated aliases ¶
This module defines several deprecated aliases to pre-existing standard library classes. These were originally included in the typing module in order to support parameterizing these generic classes using [] . However, the aliases became redundant in Python 3.9 when the corresponding pre-existing classes were enhanced to support [] (see PEP 585 ).
The redundant types are deprecated as of Python 3.9. However, while the aliases may be removed at some point, removal of these aliases is not currently planned. As such, no deprecation warnings are currently issued by the interpreter for these aliases.
If at some point it is decided to remove these deprecated aliases, a deprecation warning will be issued by the interpreter for at least two releases prior to removal. The aliases are guaranteed to remain in the typing module without deprecation warnings until at least Python 3.14.
Type checkers are encouraged to flag uses of the deprecated types if the program they are checking targets a minimum Python version of 3.9 or newer.
Aliases to built-in types ¶
Deprecated alias to dict .
Note that to annotate arguments, it is preferred to use an abstract collection type such as Mapping rather than to use dict or typing.Dict .
This type can be used as follows:
Deprecated since version 3.9: builtins.dict now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to list .
Note that to annotate arguments, it is preferred to use an abstract collection type such as Sequence or Iterable rather than to use list or typing.List .
This type may be used as follows:
Deprecated since version 3.9: builtins.list now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to builtins.set .
Note that to annotate arguments, it is preferred to use an abstract collection type such as AbstractSet rather than to use set or typing.Set .
Deprecated since version 3.9: builtins.set now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to builtins.frozenset .
Deprecated since version 3.9: builtins.frozenset now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias for tuple .
tuple and Tuple are special-cased in the type system; see Annotating tuples for more details.
Deprecated since version 3.9: builtins.tuple now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to type .
See The type of class objects for details on using type or typing.Type in type annotations.
Deprecated since version 3.9: builtins.type now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Aliases to types in collections ¶
Deprecated alias to collections.defaultdict .
Deprecated since version 3.9: collections.defaultdict now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.OrderedDict .
Added in version 3.7.2.
Deprecated since version 3.9: collections.OrderedDict now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.ChainMap .
Added in version 3.6.1.
Deprecated since version 3.9: collections.ChainMap now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.Counter .
Deprecated since version 3.9: collections.Counter now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.deque .
Deprecated since version 3.9: collections.deque now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Aliases to other concrete types ¶
Deprecated since version 3.8, will be removed in version 3.13: The typing.io namespace is deprecated and will be removed. These types should be directly imported from typing instead.
Deprecated aliases corresponding to the return types from re.compile() and re.match() .
These types (and the corresponding functions) are generic over AnyStr . Pattern can be specialised as Pattern[str] or Pattern[bytes] ; Match can be specialised as Match[str] or Match[bytes] .
Deprecated since version 3.8, will be removed in version 3.13: The typing.re namespace is deprecated and will be removed. These types should be directly imported from typing instead.
Deprecated since version 3.9: Classes Pattern and Match from re now support [] . See PEP 585 and Generic Alias Type .
Deprecated alias for str .
Text is provided to supply a forward compatible path for Python 2 code: in Python 2, Text is an alias for unicode .
Use Text to indicate that a value must contain a unicode string in a manner that is compatible with both Python 2 and Python 3:
Deprecated since version 3.11: Python 2 is no longer supported, and most type checkers also no longer support type checking Python 2 code. Removal of the alias is not currently planned, but users are encouraged to use str instead of Text .
Aliases to container ABCs in collections.abc ¶
Deprecated alias to collections.abc.Set .
Deprecated since version 3.9: collections.abc.Set now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
This type represents the types bytes , bytearray , and memoryview of byte sequences.
Deprecated since version 3.9, will be removed in version 3.14: Prefer collections.abc.Buffer , or a union like bytes | bytearray | memoryview .
Deprecated alias to collections.abc.Collection .
Added in version 3.6.
Deprecated since version 3.9: collections.abc.Collection now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Container .
Deprecated since version 3.9: collections.abc.Container now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.ItemsView .
Deprecated since version 3.9: collections.abc.ItemsView now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.KeysView .
Deprecated since version 3.9: collections.abc.KeysView now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Mapping .
Deprecated since version 3.9: collections.abc.Mapping now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.MappingView .
Deprecated since version 3.9: collections.abc.MappingView now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.MutableMapping .
Deprecated since version 3.9: collections.abc.MutableMapping now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.MutableSequence .
Deprecated since version 3.9: collections.abc.MutableSequence now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.MutableSet .
Deprecated since version 3.9: collections.abc.MutableSet now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Sequence .
Deprecated since version 3.9: collections.abc.Sequence now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.ValuesView .
Deprecated since version 3.9: collections.abc.ValuesView now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Aliases to asynchronous ABCs in collections.abc ¶
Deprecated alias to collections.abc.Coroutine .
The variance and order of type variables correspond to those of Generator , for example:
Deprecated since version 3.9: collections.abc.Coroutine now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.AsyncGenerator .
An async generator can be annotated by the generic type AsyncGenerator[YieldType, SendType] . For example:
Unlike normal generators, async generators cannot return a value, so there is no ReturnType type parameter. As with Generator , the SendType behaves contravariantly.
If your generator will only yield values, set the SendType to None :
Alternatively, annotate your generator as having a return type of either AsyncIterable[YieldType] or AsyncIterator[YieldType] :
Deprecated since version 3.9: collections.abc.AsyncGenerator now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.AsyncIterable .
Deprecated since version 3.9: collections.abc.AsyncIterable now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.AsyncIterator .
Deprecated since version 3.9: collections.abc.AsyncIterator now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Awaitable .
Deprecated since version 3.9: collections.abc.Awaitable now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Aliases to other ABCs in collections.abc ¶
Deprecated alias to collections.abc.Iterable .
Deprecated since version 3.9: collections.abc.Iterable now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Iterator .
Deprecated since version 3.9: collections.abc.Iterator now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Callable .
See Annotating callable objects for details on how to use collections.abc.Callable and typing.Callable in type annotations.
Deprecated since version 3.9: collections.abc.Callable now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Generator .
A generator can be annotated by the generic type Generator[YieldType, SendType, ReturnType] . For example:
Note that unlike many other generics in the typing module, the SendType of Generator behaves contravariantly, not covariantly or invariantly.
If your generator will only yield values, set the SendType and ReturnType to None :
Alternatively, annotate your generator as having a return type of either Iterable[YieldType] or Iterator[YieldType] :
Deprecated since version 3.9: collections.abc.Generator now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Hashable .
Deprecated since version 3.12: Use collections.abc.Hashable directly instead.
Deprecated alias to collections.abc.Reversible .
Deprecated since version 3.9: collections.abc.Reversible now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to collections.abc.Sized .
Deprecated since version 3.12: Use collections.abc.Sized directly instead.
Aliases to contextlib ABCs ¶
Deprecated alias to contextlib.AbstractContextManager .
Added in version 3.5.4.
Deprecated since version 3.9: contextlib.AbstractContextManager now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecated alias to contextlib.AbstractAsyncContextManager .
Added in version 3.6.2.
Deprecated since version 3.9: contextlib.AbstractAsyncContextManager now supports subscripting ( [] ). See PEP 585 and Generic Alias Type .
Deprecation Timeline of Major Features ¶
Certain features in typing are deprecated and may be removed in a future version of Python. The following table summarizes major deprecations for your convenience. This is subject to change, and not all deprecations are listed.
Feature | Deprecated in | Projected removal | PEP/issue |
|---|---|---|---|
and submodules | 3.8 | 3.13 |
|
versions of standard collections | 3.9 | Undecided (see for more information) |
|
| 3.9 | 3.14 |
|
| 3.11 | Undecided |
|
and | 3.12 | Undecided |
|
| 3.12 | Undecided |
|
Table of Contents
- Specification for the Python Type System
- Type aliases
- Annotating tuples
- The type of class objects
- User-defined generic types
- The Any type
- Nominal vs structural subtyping
- Special types
- Special forms
- Building generic types and type aliases
- Other special directives
- ABCs for working with IO
- Functions and decorators
- Introspection helpers
- Aliases to built-in types
- Aliases to types in collections
- Aliases to other concrete types
- Aliases to container ABCs in collections.abc
- Aliases to asynchronous ABCs in collections.abc
- Aliases to other ABCs in collections.abc
- Aliases to contextlib ABCs
- Deprecation Timeline of Major Features
Previous topic
Development Tools
pydoc — Documentation generator and online help system
- Report a Bug
- Show Source
Calling function on startup
hello, when I try to call the function getSingleRows(), I get the following error TypeError: Thirdwindow.getSingleRows() missing 1 required positional argument: ‘self’ please point out what I am missing
here are my files
crashcourse.kv
getSingleRows is an instance method of Thirdwindow (it has a parameter self that will refer to the instance/object), but you’re calling it as a plain method getSingleRows() , so no instance there.
if you want to call the method getSingleRows at start-up during an object instantiation, include an __init__ constructor method, and call the method in there, i.e:
If you want access to the attribute x in other parts of your class script, define it in the constructor so that it becomes an attribute of the instances that you create. I don’t think that there is a need for the global keyword here.
where should I add this function def init (self): self.getSingleRows()
please be patient because I am new to this
At the top of the class, as in:
For the x value, assign it to whatever value is required during initialization. I have set it to None in this example since I do not know its intended initial value. For all classes, if you need code to run during instantiation, include it in the __init__ constructor method.
Hope that helps.
Experiment. For example:
As you can see, if you assign a variable in the __init__ constructor method, you can access it by any instance method or instance object. There is no need for a global keyword. However, if you wish to have access to an attribute between many instance objects, then assign it as a class attribute.
thank you for your patience but when I edited my code with the code you provided it produced that says EXPECTED INDENTED BLOCK
The class word that defines Windowmanager(screen) has a red line unerneath and when I hover it, it says expected indented block
When experimenting with new code and concepts , always start small. That is, begin with the bare minimum so that you can test the proposition in isolation. Thereafter, slowly build out.
In the script that you provided, the method getSingleRows(self) is missing a body statement. You can’t declare a method and leave it blank.
add a statement to it:
Another way to think of this, is suppose that you are in a classroom. Your professor has a list/roster of all of the students that are attending that class. As he is taking roll call, he slowly looks at each name in the roster and links it to a student (a body). If at any point he comes upon a student that is missing (missing a body), he makes a note of it. This is essentially what is going on here. There is a method name that has been declared, but with a missing body. Anytime that you declare a method/function, it has to accompanied by a body statement. The same is true for classes.
thank you the error has gone, but what about the code that deals with the database? does it go inside def getSingleRows(self):? thank you again for your advice
Yes, it can go inside the method. However, this is where your creativity will have to come into play. How do YOU want to design your application? As I stated in a previous post, start small. Experiment with a concept/propostion. Don’t write 2-3 pages worth of code and then decide to test for verification. Test at every step of the development phase so that you verify that it is being developed according to your requirements. This also helps you understand your own code btw.
hello Paul again. I listed to your advice and started running the code for testing after adding print(“print something”), it produced this error
TypeError: Thirdwindow. init () got an unexpected keyword argument ‘__no_builder’
please, solve this problem
Related Topics
| Topic | Replies | Views | Activity | |
|---|---|---|---|---|
| Python Help | 3 | 1528 | March 31, 2022 | |
| Python Help | 5 | 471 | December 10, 2022 | |
| Python Help | 8 | 2096 | February 3, 2023 | |
| Python Help | 3 | 1829 | September 20, 2022 | |
| Python Help | 8 | 2181 | November 18, 2023 |
Join us and get access to thousands of tutorials and a community of expert Pythonistas.
This lesson is for members only. Join us and get access to thousands of tutorials and a community of expert Pythonistas.
Assignment Expression Syntax

- Discussion (1)
For more information on concepts covered in this lesson, you can check out:
- Python Scope & the LEGB Rule: Resolving Names in Your Code | Real Python Article
- PEP 572 – Assignment Expressions: Exceptional Cases | Python.org
00:00 Walrus operator syntax. One of the main reasons assignments were not expressions in Python from the beginning is the visual likeness of the assignment operator ( = ) and the equality comparison operator ( == ). This could potentially lead to bugs.
00:18 When introducing assignment expressions, a great deal of thought was put into how to avoid similar bugs with the walrus operator. As mentioned previously, one important feature is the walrus operator is never allowed as a direct replacement for the assignment operator, and vice versa.
00:35 As you saw at the beginning of the course, you can’t use a plain assignment expression to assign a value. It is syntactically legal to use an assignment expression to only assign a value, but only if you add parentheses.
00:57 Even though this is possible, this really is a prime example of where you should stay away from the walrus operator and use a traditional assignment statement instead.
01:07 There are several other examples where the walrus operator is either illegal or discouraged. All of these examples raise a SyntaxError .
01:40 In all of these cases, you would be better served using the assignment operator instead. The next examples are all similar and they are all legal code. However, the walrus operator doesn’t improve your code in any of these cases.
02:20 None of these examples make your code more readable. You should instead do the extra assignment separately by using a traditional assignment statement. If you want to look at this in more depth, take a look at the original PEP which created the assignment expression operator.
02:39 There’s one use case where the := character sequence is already valid Python. In f-strings, a colon ( : ) is used to separate values from their format specification.
02:56 The := in this case does look like a walrus operator, but the effect is quite different. To interpret x:=8 inside the f-string, the expression is broken into three parts: the x , the colon ( : ), and the =8 . Here, x is a value, the colon ( : ) acts as a separator, and =8 is a format specification.
03:21 In this context, equals ( = ) specifies an alignment option. In this case, the value is padded with spaces in a field width of 8 .
03:31 To use assignment expressions inside f-strings, you need to add parentheses.
03:44 This updates the value of x as expected. However, you’re probably better off using traditional assignments outside of your f-strings instead.
03:55 Let’s look at some other situations where assignment expressions are illegal. Attribute and item assignment: You can only assign to simple names, not dotted or index names.
04:22 As you can see, this fails with a descriptive error message, and there’s no straightforward workaround. Iterable unpacking: You can’t unpack when using the walrus operator.
04:45 Augmented assignment: You can’t use the walrus operator combined with augmented assignment operators like plus equals ( += ). This raises a SyntaxError .
05:01 The easiest workaround here would be to do the augmentation explicitly. When you’re using the walrus operator, it will behave similarly to traditional assignment statements in many respects.
05:14 The scope of the assignment target is the same as for assignments. It will follow the LEGB rule. Typically, the assignment will happen in the local scope, but if the target name is already declared global or non-local, that is honored.
05:33 For more information on this topic, check out this Real Python course, Python Scope & the LEGB Rule: Resolving Names in Your Code. The precedence of the walrus operator can cause some confusion.
05:47 It binds less tightly than all other operators except the comma, so you might need parentheses to delimit the expression that’s assigned. As an example, note what happens when you don’t use parentheses.
06:12 Here, square is bound to the whole expression number ** 2 > 5 . In other words, square gets the value True and not the value of number ** 2 , which was the intention. In this case, you can delimit the expression with parentheses.
06:38 The parentheses make the if statement both clearer and actually correct. There’s one final gotcha. When assigning a tuple using the walrus operator, you always need to use parentheses around the tuple.
06:53 Compare the following assignments.
07:21 Note that in the second example, walrus takes the value 3.8 and not the whole tuple of (3.8, True) . That’s because the walrus operator binds more tightly than the comma.
07:33 This may seem a bit annoying. However, if the walrus operator bound less tightly than the comma, it wouldn’t be possible to use the walrus operator in function calls with more than one argument.
07:45 The style recommendations for the walrus operator are mostly the same as for the assignment operator. First, always add spaces around the walrus operator in your code.
07:57 Second, use parentheses around the expression as necessary but avoid adding extra parentheses that are not needed. The general design of assignment expressions is to make them easy to use when they’re helpful but to avoid overusing them when they might clutter up your code.
08:15 Next up, a look at some of the pitfalls that may meet you when you use the walrus operator.
dar3232 on May 5, 2023
I took a step further the unpacking example… 🤯
Become a Member to join the conversation.
Python Programming
Practice Python Exercises and Challenges with Solutions
Free Coding Exercises for Python Developers. Exercises cover Python Basics , Data structure , to Data analytics . As of now, this page contains 18 Exercises.
What included in these Python Exercises?
Each exercise contains specific Python topic questions you need to practice and solve. These free exercises are nothing but Python assignments for the practice where you need to solve different programs and challenges.
- All exercises are tested on Python 3.
- Each exercise has 10-20 Questions.
- The solution is provided for every question.
- Practice each Exercise in Online Code Editor
These Python programming exercises are suitable for all Python developers. If you are a beginner, you will have a better understanding of Python after solving these exercises. Below is the list of exercises.
Select the exercise you want to solve .
Basic Exercise for Beginners
Practice and Quickly learn Python’s necessary skills by solving simple questions and problems.
Topics : Variables, Operators, Loops, String, Numbers, List
Python Input and Output Exercise
Solve input and output operations in Python. Also, we practice file handling.
Topics : print() and input() , File I/O
Python Loop Exercise
This Python loop exercise aims to help developers to practice branching and Looping techniques in Python.
Topics : If-else statements, loop, and while loop.
Python Functions Exercise
Practice how to create a function, nested functions, and use the function arguments effectively in Python by solving different questions.
Topics : Functions arguments, built-in functions.
Python String Exercise
Solve Python String exercise to learn and practice String operations and manipulations.
Python Data Structure Exercise
Practice widely used Python types such as List, Set, Dictionary, and Tuple operations in Python
Python List Exercise
This Python list exercise aims to help Python developers to learn and practice list operations.
Python Dictionary Exercise
This Python dictionary exercise aims to help Python developers to learn and practice dictionary operations.
Python Set Exercise
This exercise aims to help Python developers to learn and practice set operations.
Python Tuple Exercise
This exercise aims to help Python developers to learn and practice tuple operations.
Python Date and Time Exercise
This exercise aims to help Python developers to learn and practice DateTime and timestamp questions and problems.
Topics : Date, time, DateTime, Calendar.
Python OOP Exercise
This Python Object-oriented programming (OOP) exercise aims to help Python developers to learn and practice OOP concepts.
Topics : Object, Classes, Inheritance
Python JSON Exercise
Practice and Learn JSON creation, manipulation, Encoding, Decoding, and parsing using Python
Python NumPy Exercise
Practice NumPy questions such as Array manipulations, numeric ranges, Slicing, indexing, Searching, Sorting, and splitting, and more.
Python Pandas Exercise
Practice Data Analysis using Python Pandas. Practice Data-frame, Data selection, group-by, Series, sorting, searching, and statistics.
Python Matplotlib Exercise
Practice Data visualization using Python Matplotlib. Line plot, Style properties, multi-line plot, scatter plot, bar chart, histogram, Pie chart, Subplot, stack plot.
Random Data Generation Exercise
Practice and Learn the various techniques to generate random data in Python.
Topics : random module, secrets module, UUID module
Python Database Exercise
Practice Python database programming skills by solving the questions step by step.
Use any of the MySQL, PostgreSQL, SQLite to solve the exercise
Exercises for Intermediate developers
The following practice questions are for intermediate Python developers.
If you have not solved the above exercises, please complete them to understand and practice each topic in detail. After that, you can solve the below questions quickly.
Exercise 1: Reverse each word of a string
Expected Output
- Use the split() method to split a string into a list of words.
- Reverse each word from a list
- finally, use the join() function to convert a list into a string
Steps to solve this question :
- Split the given string into a list of words using the split() method
- Use a list comprehension to create a new list by reversing each word from a list.
- Use the join() function to convert the new list into a string
- Display the resultant string
Exercise 2: Read text file into a variable and replace all newlines with space
Given : Assume you have a following text file (sample.txt).
Expected Output :
- First, read a text file.
- Next, use string replace() function to replace all newlines ( \n ) with space ( ' ' ).
Steps to solve this question : -
- First, open the file in a read mode
- Next, read all content from a file using the read() function and assign it to a variable.
- Display final string
Exercise 3: Remove items from a list while iterating
Description :
In this question, You need to remove items from a list while iterating but without creating a different copy of a list.
Remove numbers greater than 50
Expected Output : -
- Get the list's size
- Iterate list using while loop
- Check if the number is greater than 50
- If yes, delete the item using a del keyword
- Reduce the list size
Solution 1: Using while loop
Solution 2: Using for loop and range()
Exercise 4: Reverse Dictionary mapping
Exercise 5: display all duplicate items from a list.
- Use the counter() method of the collection module.
- Create a dictionary that will maintain the count of each item of a list. Next, Fetch all keys whose value is greater than 2
Solution 1 : - Using collections.Counter()
Solution 2 : -
Exercise 6: Filter dictionary to contain keys present in the given list
Exercise 7: print the following number pattern.
Refer to Print patterns in Python to solve this question.
- Use two for loops
- The outer loop is reverse for loop from 5 to 0
- Increment value of x by 1 in each iteration of an outer loop
- The inner loop will iterate from 0 to the value of i of the outer loop
- Print value of x in each iteration of an inner loop
- Print newline at the end of each outer loop
Exercise 8: Create an inner function
Question description : -
- Create an outer function that will accept two strings, x and y . ( x= 'Emma' and y = 'Kelly' .
- Create an inner function inside an outer function that will concatenate x and y.
- At last, an outer function will join the word 'developer' to it.
Exercise 9: Modify the element of a nested list inside the following list
Change the element 35 to 3500

Exercise 10: Access the nested key increment from the following dictionary
Under Exercises: -
Python Object-Oriented Programming (OOP) Exercise: Classes and Objects Exercises
Updated on: December 8, 2021 | 51 Comments
Python Date and Time Exercise with Solutions
Updated on: December 8, 2021 | 11 Comments
Python Dictionary Exercise with Solutions
Updated on: May 6, 2023 | 57 Comments
Python Tuple Exercise with Solutions
Updated on: December 8, 2021 | 95 Comments
Python Set Exercise with Solutions
Updated on: October 20, 2022 | 27 Comments
Python if else, for loop, and range() Exercises with Solutions
Updated on: September 6, 2021 | 292 Comments
Updated on: August 2, 2022 | 153 Comments
Updated on: September 6, 2021 | 108 Comments
Python List Exercise with Solutions
Updated on: December 8, 2021 | 197 Comments
Updated on: December 8, 2021 | 7 Comments
Python Data Structure Exercise for Beginners
Updated on: December 8, 2021 | 116 Comments
Python String Exercise with Solutions
Updated on: October 6, 2021 | 220 Comments
Updated on: March 9, 2021 | 23 Comments
Updated on: March 9, 2021 | 50 Comments
Updated on: July 20, 2021 | 29 Comments
Python Basic Exercise for Beginners
Updated on: August 31, 2023 | 490 Comments
Useful Python Tips and Tricks Every Programmer Should Know
Updated on: May 17, 2021 | 23 Comments
Python random Data generation Exercise
Updated on: December 8, 2021 | 13 Comments
Python Database Programming Exercise
Updated on: March 9, 2021 | 17 Comments
- Online Python Code Editor
Updated on: June 1, 2022 |
About PYnative
PYnative.com is for Python lovers. Here, You can get Tutorials, Exercises, and Quizzes to practice and improve your Python skills .
Explore Python
- Learn Python
- Python Basics
- Python Databases
- Python Exercises
- Python Quizzes
- Python Tricks
To get New Python Tutorials, Exercises, and Quizzes
Legal Stuff
We use cookies to improve your experience. While using PYnative, you agree to have read and accepted our Terms Of Use , Cookie Policy , and Privacy Policy .
Copyright © 2018–2024 pynative.com
- Python Basics
- Interview Questions
- Python Quiz
- Popular Packages
- Python Projects
- Practice Python
- AI With Python
- Learn Python3
- Python Automation
- Python Web Dev
- DSA with Python
- Python OOPs
- Dictionaries
Python Operators
Precedence and associativity of operators in python.
- Python Arithmetic Operators
- Difference between / vs. // operator in Python
- Python - Star or Asterisk operator ( * )
- What does the Double Star operator mean in Python?
- Division Operators in Python
- Modulo operator (%) in Python
- Python Logical Operators
- Python OR Operator
- Difference between 'and' and '&' in Python
- not Operator in Python | Boolean Logic
Ternary Operator in Python
- Python Bitwise Operators
Python Assignment Operators
Assignment operators in python.
- Walrus Operator in Python 3.8
- Increment += and Decrement -= Assignment Operators in Python
- Merging and Updating Dictionary Operators in Python 3.9
- New '=' Operator in Python3.8 f-string
Python Relational Operators
- Comparison Operators in Python
- Python NOT EQUAL operator
- Difference between == and is operator in Python
- Chaining comparison operators in Python
- Python Membership and Identity Operators
- Difference between != and is not operator in Python
In Python programming, Operators in general are used to perform operations on values and variables. These are standard symbols used for logical and arithmetic operations. In this article, we will look into different types of Python operators.
- OPERATORS: These are the special symbols. Eg- + , * , /, etc.
- OPERAND: It is the value on which the operator is applied.
Types of Operators in Python
- Arithmetic Operators
- Comparison Operators
- Logical Operators
- Bitwise Operators
- Assignment Operators
- Identity Operators and Membership Operators
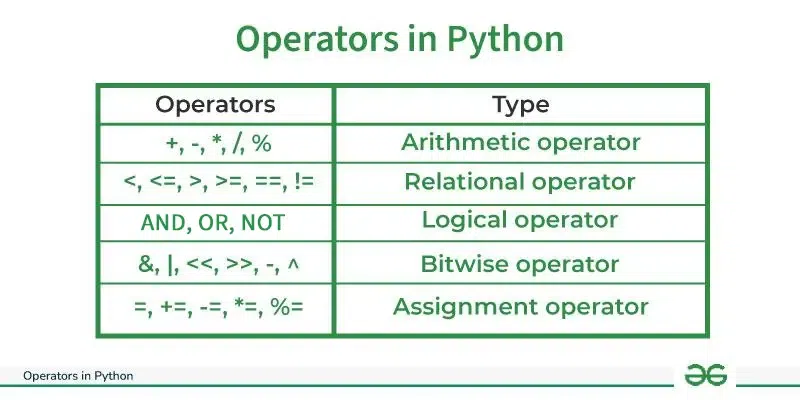
Arithmetic Operators in Python
Python Arithmetic operators are used to perform basic mathematical operations like addition, subtraction, multiplication , and division .
In Python 3.x the result of division is a floating-point while in Python 2.x division of 2 integers was an integer. To obtain an integer result in Python 3.x floored (// integer) is used.
| Operator | Description | Syntax |
|---|---|---|
| + | Addition: adds two operands | x + y |
| – | Subtraction: subtracts two operands | x – y |
| * | Multiplication: multiplies two operands | x * y |
| / | Division (float): divides the first operand by the second | x / y |
| // | Division (floor): divides the first operand by the second | x // y |
| % | Modulus: returns the remainder when the first operand is divided by the second | x % y |
| ** | Power: Returns first raised to power second | x ** y |
Example of Arithmetic Operators in Python
Division operators.
In Python programming language Division Operators allow you to divide two numbers and return a quotient, i.e., the first number or number at the left is divided by the second number or number at the right and returns the quotient.
There are two types of division operators:
Float division
- Floor division
The quotient returned by this operator is always a float number, no matter if two numbers are integers. For example:
Example: The code performs division operations and prints the results. It demonstrates that both integer and floating-point divisions return accurate results. For example, ’10/2′ results in ‘5.0’ , and ‘-10/2’ results in ‘-5.0’ .
Integer division( Floor division)
The quotient returned by this operator is dependent on the argument being passed. If any of the numbers is float, it returns output in float. It is also known as Floor division because, if any number is negative, then the output will be floored. For example:
Example: The code demonstrates integer (floor) division operations using the // in Python operators . It provides results as follows: ’10//3′ equals ‘3’ , ‘-5//2’ equals ‘-3’ , ‘ 5.0//2′ equals ‘2.0’ , and ‘-5.0//2’ equals ‘-3.0’ . Integer division returns the largest integer less than or equal to the division result.
Precedence of Arithmetic Operators in Python
The precedence of Arithmetic Operators in Python is as follows:
- P – Parentheses
- E – Exponentiation
- M – Multiplication (Multiplication and division have the same precedence)
- D – Division
- A – Addition (Addition and subtraction have the same precedence)
- S – Subtraction
The modulus of Python operators helps us extract the last digit/s of a number. For example:
- x % 10 -> yields the last digit
- x % 100 -> yield last two digits
Arithmetic Operators With Addition, Subtraction, Multiplication, Modulo and Power
Here is an example showing how different Arithmetic Operators in Python work:
Example: The code performs basic arithmetic operations with the values of ‘a’ and ‘b’ . It adds (‘+’) , subtracts (‘-‘) , multiplies (‘*’) , computes the remainder (‘%’) , and raises a to the power of ‘b (**)’ . The results of these operations are printed.
Note: Refer to Differences between / and // for some interesting facts about these two Python operators.
Comparison of Python Operators
In Python Comparison of Relational operators compares the values. It either returns True or False according to the condition.
| Operator | Description | Syntax |
|---|---|---|
| > | Greater than: True if the left operand is greater than the right | x > y |
| < | Less than: True if the left operand is less than the right | x < y |
| == | Equal to: True if both operands are equal | x == y |
| != | Not equal to – True if operands are not equal | x != y |
| >= | Greater than or equal to True if the left operand is greater than or equal to the right | x >= y |
| <= | Less than or equal to True if the left operand is less than or equal to the right | x <= y |
= is an assignment operator and == comparison operator.
Precedence of Comparison Operators in Python
In Python, the comparison operators have lower precedence than the arithmetic operators. All the operators within comparison operators have the same precedence order.
Example of Comparison Operators in Python
Let’s see an example of Comparison Operators in Python.
Example: The code compares the values of ‘a’ and ‘b’ using various comparison Python operators and prints the results. It checks if ‘a’ is greater than, less than, equal to, not equal to, greater than, or equal to, and less than or equal to ‘b’ .
Logical Operators in Python
Python Logical operators perform Logical AND , Logical OR , and Logical NOT operations. It is used to combine conditional statements.
| Operator | Description | Syntax |
|---|---|---|
| and | Logical AND: True if both the operands are true | x and y |
| or | Logical OR: True if either of the operands is true | x or y |
| not | Logical NOT: True if the operand is false | not x |
Precedence of Logical Operators in Python
The precedence of Logical Operators in Python is as follows:
- Logical not
- logical and
Example of Logical Operators in Python
The following code shows how to implement Logical Operators in Python:
Example: The code performs logical operations with Boolean values. It checks if both ‘a’ and ‘b’ are true ( ‘and’ ), if at least one of them is true ( ‘or’ ), and negates the value of ‘a’ using ‘not’ . The results are printed accordingly.
Bitwise Operators in Python
Python Bitwise operators act on bits and perform bit-by-bit operations. These are used to operate on binary numbers.
| Operator | Description | Syntax |
|---|---|---|
| & | Bitwise AND | x & y |
| | | Bitwise OR | x | y |
| ~ | Bitwise NOT | ~x |
| ^ | Bitwise XOR | x ^ y |
| >> | Bitwise right shift | x>> |
| << | Bitwise left shift | x<< |
Precedence of Bitwise Operators in Python
The precedence of Bitwise Operators in Python is as follows:
- Bitwise NOT
- Bitwise Shift
- Bitwise AND
- Bitwise XOR
Here is an example showing how Bitwise Operators in Python work:
Example: The code demonstrates various bitwise operations with the values of ‘a’ and ‘b’ . It performs bitwise AND (&) , OR (|) , NOT (~) , XOR (^) , right shift (>>) , and left shift (<<) operations and prints the results. These operations manipulate the binary representations of the numbers.
Python Assignment operators are used to assign values to the variables.
| Operator | Description | Syntax |
|---|---|---|
| = | Assign the value of the right side of the expression to the left side operand | x = y + z |
| += | Add AND: Add right-side operand with left-side operand and then assign to left operand | a+=b a=a+b |
| -= | Subtract AND: Subtract right operand from left operand and then assign to left operand | a-=b a=a-b |
| *= | Multiply AND: Multiply right operand with left operand and then assign to left operand | a*=b a=a*b |
| /= | Divide AND: Divide left operand with right operand and then assign to left operand | a/=b a=a/b |
| %= | Modulus AND: Takes modulus using left and right operands and assign the result to left operand | a%=b a=a%b |
| //= | Divide(floor) AND: Divide left operand with right operand and then assign the value(floor) to left operand | a//=b a=a//b |
| **= | Exponent AND: Calculate exponent(raise power) value using operands and assign value to left operand | a**=b a=a**b |
| &= | Performs Bitwise AND on operands and assign value to left operand | a&=b a=a&b |
| |= | Performs Bitwise OR on operands and assign value to left operand | a|=b a=a|b |
| ^= | Performs Bitwise xOR on operands and assign value to left operand | a^=b a=a^b |
| >>= | Performs Bitwise right shift on operands and assign value to left operand | a>>=b a=a>>b |
| <<= | Performs Bitwise left shift on operands and assign value to left operand | a <<= b a= a << b |
Let’s see an example of Assignment Operators in Python.
Example: The code starts with ‘a’ and ‘b’ both having the value 10. It then performs a series of operations: addition, subtraction, multiplication, and a left shift operation on ‘b’ . The results of each operation are printed, showing the impact of these operations on the value of ‘b’ .
Identity Operators in Python
In Python, is and is not are the identity operators both are used to check if two values are located on the same part of the memory. Two variables that are equal do not imply that they are identical.
Example Identity Operators in Python
Let’s see an example of Identity Operators in Python.
Example: The code uses identity operators to compare variables in Python. It checks if ‘a’ is not the same object as ‘b’ (which is true because they have different values) and if ‘a’ is the same object as ‘c’ (which is true because ‘c’ was assigned the value of ‘a’ ).
Membership Operators in Python
In Python, in and not in are the membership operators that are used to test whether a value or variable is in a sequence.
Examples of Membership Operators in Python
The following code shows how to implement Membership Operators in Python:
Example: The code checks for the presence of values ‘x’ and ‘y’ in the list. It prints whether or not each value is present in the list. ‘x’ is not in the list, and ‘y’ is present, as indicated by the printed messages. The code uses the ‘in’ and ‘not in’ Python operators to perform these checks.
in Python, Ternary operators also known as conditional expressions are operators that evaluate something based on a condition being true or false. It was added to Python in version 2.5.
It simply allows testing a condition in a single line replacing the multiline if-else making the code compact.
Syntax : [on_true] if [expression] else [on_false]
Examples of Ternary Operator in Python
The code assigns values to variables ‘a’ and ‘b’ (10 and 20, respectively). It then uses a conditional assignment to determine the smaller of the two values and assigns it to the variable ‘min’ . Finally, it prints the value of ‘min’ , which is 10 in this case.
In Python, Operator precedence and associativity determine the priorities of the operator.
Operator Precedence in Python
This is used in an expression with more than one operator with different precedence to determine which operation to perform first.
Let’s see an example of how Operator Precedence in Python works:
Example: The code first calculates and prints the value of the expression 10 + 20 * 30 , which is 610. Then, it checks a condition based on the values of the ‘name’ and ‘age’ variables. Since the name is “ Alex” and the condition is satisfied using the or operator, it prints “Hello! Welcome.”
Operator Associativity in Python
If an expression contains two or more operators with the same precedence then Operator Associativity is used to determine. It can either be Left to Right or from Right to Left.
The following code shows how Operator Associativity in Python works:
Example: The code showcases various mathematical operations. It calculates and prints the results of division and multiplication, addition and subtraction, subtraction within parentheses, and exponentiation. The code illustrates different mathematical calculations and their outcomes.
To try your knowledge of Python Operators, you can take out the quiz on Operators in Python .
Python Operator Exercise Questions
Below are two Exercise Questions on Python Operators. We have covered arithmetic operators and comparison operators in these exercise questions. For more exercises on Python Operators visit the page mentioned below.
Q1. Code to implement basic arithmetic operations on integers
Q2. Code to implement Comparison operations on integers
Explore more Exercises: Practice Exercise on Operators in Python
Please Login to comment...
Similar reads.
- python-basics
- Python-Operators
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Self-Attention Explained with Code
How large language models create rich, contextual embeddings.
Bradney Smith
Towards Data Science
Part 3 in the “LLMs from Scratch” series — a complete guide to understanding and building Large Language Models. If you are interested in learning more about how these models work I encourage you to read:
- Prelude: A Brief History of Large Language Models
- Part 1: Tokenization — A Complete Guide
- Part 2: Word Embeddings with word2vec from Scratch in Python
- Part 3: Self-Attention Explained with Code
- Part 4: A Complete Guide to BERT with Code
Introduction
The paper “Attention is All You Need” debuted perhaps the single largest advancement in Natural Language Processing (NLP) in the last 10 years: the Transformer [1]. This architecture massively simplified the complex designs of language models at the time while achieving unparalleled results. State-of-the-art (SOTA) models, such as those in the GPT, Claude, and Llama families, owe their success to this design, at the heart of which is self-attention. In this deep dive, we will explore how this mechanism works and how it is used by transformers to create contextually rich embeddings that enable these models to perform so well.
1 — Overview of the Transformer Embedding Process
2 — positional encoding, 3 — the self-attention mechanism, 4 — transformer embeddings in python, 5 — conclusion, 6 — further reading, 1.1 — recap on transformers.
In the prelude article of this series, we briefly explored the history of the Transformer and its impact on NLP. To recap: the Transformer is a deep neural network architecture that is the foundation for almost all LLMs today. Derivative models are often called Transformer-based models or transformers for short, and so these terms will be used interchangeably here. Like all machine learning models, transformers work with numbers and linear algebra rather than processing human language directly. Because of this, they must convert textual inputs from users into numerical representations through several steps. Perhaps the most important of these steps is applying the self-attention mechanism, which is the focus of this article. The process of representing text with vectors is called embedding (or encoding ), hence the numerical representations of the input text are known as transformer embeddings .
1.2 — The Issue with Static Embeddings
In Part 2 of this series , we explored static embeddings for language models using word2vec as an example. This embedding method predates transformers and suffers from one major drawback: the lack of contextual information. Words with multiple meanings (called polysemous words) are encoded with somewhat ambiguous representations since they lack the context needed for precise meaning. A classic example of a polysemous word is bank . Using a static embedding model, the word bank would be represented in vector space with some degree of similarity to words such as money and deposit and some degree of similarity to words such as river and nature . This is because the word will occur in many different contexts within the training data. This is the core problem with static embeddings: they do not change based on context — hence the term “static”.
1.3 — Fixing Static Embeddings
Transformers overcome the limitations of static embeddings by producing their own context-aware transformer embeddings. In this approach, fixed word embeddings are augmented with positional information (where the words occur in the input text) and contextual information (how the words are used). These two steps take place in distinct components in transformers, namely the positional encoder and the self-attention blocks, respectively. We will look at each of these in detail in the following sections. By incorporating this additional information, transformers can produce much more powerful vector representations of words based on their usage in the input sequence. Extending the vector representations beyond static embeddings is what enables Transformer-based models to handle polysemous words and gain a deeper understanding of language compared to previous models.
1.4 — Introducing Learned Embeddings
Much like the word2vec approach released four years prior, transformers store the initial vector representation for each token in the weights of a linear layer (a small neural network). In the word2vec model, these representations form the static embeddings, but in the Transformer context these are known as learned embeddings . In practice they are very similar, but using a different name emphasises that these representations are only a starting point for the transformer embeddings and not the final form.
The linear layer sits at the beginning of the Transformer architecture and contains only weights and no bias terms (bias = 0 for every neuron). The layer weights can be represented as a matrix of size V × d_model , where V is the vocabulary size (the number of unique words in the training data) and d_model is the number of embedding dimensions. In the previous article, we denoted d_model as N , in line with word2vec notation, but here we will use d_model which is more common in the Transformer context. The original Transformer was proposed with a d_model size of 512 dimensions, but in practice any reasonable value can be used.
1.5 — Creating Learned Embeddings
A key difference between static and learned embeddings is the way in which they are trained. Static embeddings are trained in a separate neural network (using the Skip-Gram or Continuous Bag of Words architectures) using a word prediction task within a given window size. Once trained, the embeddings are then extracted and used with a range of different language models. Learned embeddings, however, are integral to the transformer you are using and are stored as weights in the first linear layer of the model. These weights, and consequently the learned embedding for each token in the vocabulary, are trained in the same backpropagation steps as the rest of the model parameters. Below is a summary of the training process for learned embeddings.
Step 1: Initialisation
Randomly initialise the weights for each neuron in the linear layer at the beginning of the model, and set the bias terms to 0. This layer is also called the embedding layer, since it is the linear layer that will store the learned embeddings. The weights can be represented as a matrix of size V × d_model , where the word embedding for each word in the vocabulary is stored along the rows. For example, the embedding for the first word in the vocabulary is stored in the first row, the second word is stored in the second row, and so on.
Step 2: Training
At each training step, the Transformer receives an input word and the aim is to predict the next word in the sequence — a task known as Next Token Prediction (NTP). Initially, these predictions will be very poor, and so every weight and bias term in the network will be updated to improve performance against the loss function, including the embeddings. After many training iterations, the learned embeddings should provide a strong vector representation for each word in the vocabulary.
Step 3: Extract the Learned Embeddings
When new input sequences are given to the model, the words are converted into tokens with an associated token ID, which corresponds to the position of the token in the tokenizer’s vocabulary. For example, the word cat may lie at position 349 in the tokenizer’s vocabulary and so will take the ID 349 . Token IDs are used to create one-hot encoded vectors that extract the correct learned embeddings from the weights matrix (that is, V -dimensional vectors where every element is 0 except for the element at the token ID position, which is 1).
Note: PyTorch is a very popular deep learning library in Python that powers some of the most well-known machine learning packages, such as the HuggingFace Transformers library [2]. If you are familiar with PyTorch, you may have encountered the nn.Embedding class, which is often used to form the first layer of transformer networks (the nn denotes that the class belongs to the neural network package). This class returns a regular linear layer that is initialised with the identity function as the activation function and with no bias term. The weights are randomly initialised since they are parameters to be learned by the model during training. This essentially carries out the steps described above in one simple line of code. Remember, the nn.Embeddings layer does not provide pre-trained word embeddings out-of-the-box, but rather initialises a blank canvas of embeddings before training. This is to allow the transformer to learn its own embeddings during the training phase.
1.6 — Transformer Embedding Process
Once the learned embeddings have been trained, the weights in the embedding layer never change. That is, the learned embedding for each word (or more specifically, token) always provides the same starting point for a word’s vector representation. From here, the positional and contextual information will be added to produce a unique representation of the word that is reflective of its usage in the input sequence.
Transformer embeddings are created in a four-step process, which is demonstrated below using the example prompt: Write a poem about a man fishing on a river bank. . Note that the first two steps are the same as the word2vec approach we saw before. Steps 3 and 4 are the further processing that add contextual information to the embeddings.
Step 1) Tokenization:
Tokenization is the process of dividing a longer input sequence into individual words (and parts of words) called tokens. In this case, the sentence will be broken down into:
write , a , poem , about , a , man , fishing , on , a , river , bank
Next, the tokens are associated with their token IDs, which are integer values corresponding to the position of the token in the tokenizer’s vocabulary (see Part 1 of this series for an in-depth look at the tokenization process).
Step 2) Map the Tokens to Learned Embeddings:
Once the input sequence has been converted into a set of token IDs, the tokens are then mapped to their learned embedding vector representations, which were acquired during the transformer’s training. These learned embeddings have the “lookup table” behaviour as we saw in the word2vec example in Part 2 of this series . The mapping takes place by multiplying a one-hot encoded vector created from the token ID with the weights matrix, just as in the word2vec approach. The learned embeddings are denoted V in the image below.
Step 3) Add Positional Information with Positional Encoding:
Positional Encoding is then used to add positional information to the word embeddings. Whereas Recurrent Neural Networks (RNNs) process text sequentially (one word at a time), transformers process all words in parallel. This removes any implicit information about the position of each word in the sentence. For example, the sentences the cat ate the mouse and the mouse ate the cat use the same words but have very different meanings. To preserve the word order, positional encoding vectors are generated and added to the learned embedding for each word. In the image below, the positional encoding vectors are denoted P , and the sums of the learned embeddings and positional encodings are denoted X .
Step 4) Modify the Embeddings using Self-Attention:
The final step is to add contextual information using the self-attention mechanism. This determines which words give context to other words in the input sequence. In the image below, the transformer embeddings are denoted y .
2.1 — The Need for Positional Encoding
Before the self-attention mechanism is applied, positional encoding is used to add information about the order of tokens to the learned embeddings. This compensates for the loss of positional information caused by the parallel processing used by transformers described earlier. There are many feasible approaches for injecting this information, but all methods must adhere to a set of constraints. The functions used to generate positional information must produce values that are:
- Bounded — values should not explode in the positive or negative direction but be constrained (e.g. between 0 and 1, -1 and 1, etc)
- Periodic — the function should produce a repeating pattern that the model can learn to recognise and discern position from
- Predictable — positional information should be generated in such a way that the model can understand the position of words in sequence lengths it was not trained on. For example, even if the model has not seen a sequence length of exactly 412 tokens in its training, the transformer should be able to understand the position of each of the embeddings in the sequence.
These constraints ensure that the positional encoder produces positional information that allows words to attend to (gain context from) any other important word, regardless of their relative positions in the sequence. In theory, with a sufficiently powerful computer, words should be able to gain context from every relevant word in an infinitely long input sequence. The length of a sequence from which a model can derive context is called the context length . In chatbots like ChatGPT, the context includes the current prompt as well as all previous prompts and responses in the conversation (within the context length limit). This limit is typically in the range of a few thousand tokens, with GPT-3 supporting up to 4096 tokens and GPT-4 enterprise edition capping at around 128,000 tokens [3].
2.2 — Positional Encoding in “Attention is All You Need”
The original transformer model was proposed with the following positional encoding functions:
- pos is the position of the word in the input, where pos = 0 corresponds to the first word in the sequence
- i is the index of each embedding dimension, ranging from i=0 (for the first embedding dimension) up to d_model
- d_model is the number of embedding dimensions for each learned embedding vector (and therefore each positional encoding vector). This was previously denoted N in the article on word2vec.
The two proposed functions take arguments of 2i and 2i+1 , which in practice means that the sine function generates positional information for the even-numbered dimensions of each word vector ( i is even), and the cosine function does so for the odd-numbered dimensions ( i is odd). According to the authors of the transformer:
“The positional encoding corresponds to a sinusoid. The wavelengths form a geometric progression from 2π to 10000·2π. We chose this function because we hypothesised it would allow the model to easily learn to attend by relative positions, since for any fixed offset k , PE_pos+k can be represented as a linear function of PE_pos ”.
The value of the constant in the denominator being 10_000 was found to be suitable after some experimentation, but is a somewhat arbitrary choice by the authors.
2.3 — Other Positional Encoding Approaches
The positional encodings shown above are considered fixed because they are generated by a known function with deterministic (predictable) outputs. This represents the most simple form of positional encoding. It is also possible to use learned positional encodings by randomly initialising some positional encodings and training them with backpropagation. Derivatives of the BERT architecture are examples of models that take this learned encoding approach. More recently, the Rotary Positional Encoding (RoPE) method has gained popularity, finding use in models such as Llama 2 and PaLM, among other positional encoding methods.
2.4 — Implementing a Positional Encoder in Python
Creating a positional encoder class in Python is fairly straightforward. We can start by defining a function that accepts the number of embedding dimensions ( d_model ), the maximum length of the input sequence ( max_length ), and the number of decimal places to round each value in the vectors to ( rounding ). Note that transformers define a maximum input sequence length, and any sequence that has fewer tokens than this limit is appended with padding tokens until the limit is reached. To account for this behaviour in our positional encoder, we accept a max_length argument. In practice, this limit is typically thousands of characters long.
We can also exploit a mathematical trick to save computation. Instead of calculating the denominator for both PE_{pos, 2i} and PE_{pos, 2i} , we can note that the denominator is identical for consecutive pairs of i . For example, the denominators for i=0 and i=1 are the same, as are the denominators for i=2 and i=3 . Hence, we can perform the calculations to determine the denominators once for the even values of i and reuse them for the odd values of i .
2.5 — Visualising the Positional Encoding Matrix
Recall that the positional information generated must be bounded, periodic, and predictable. The outputs of the sinusoidal functions presented earlier can be collected into a matrix, which can then be easily combined with the learned embeddings using element-wise addition. Plotting this matrix gives a nice visualisation of the desired properties. In the plot below, curving bands of negative values (blue) emanate from the left edge of the matrix. These bands form a pattern that the transformer can easily learn to predict.
3.1 — Overview of Attention Mechanisms
Now that we have covered an overview of transformer embeddings and the positional encoding step, we can turn our focus to the self-attention mechanism itself. In short, self-attention modifies the vector representation of words to capture the context of their usage in an input sequence. The “self” in self-attention refers to the fact that the mechanism uses the surrounding words within a single sequence to provide context. As such, self-attention requires all words to be processed in parallel. This is actually one of the main benefits of transformers (especially compared to RNNs) since the models can leverage parallel processing for a significant performance boost. In recent times, there has been some rethinking around this approach, and in the future we may see this core mechanism being replaced [4].
Another form of attention used in transformers is cross-attention. Unlike self-attention, which operates within a single sequence, cross-attention compares each word in an output sequence to each word in an input sequence, crossing between the two embedding matrices. Note the difference here compared to self-attention, which focuses entirely within a single sequence.
3.2 — Visualising How Self-Attention Contextualises Embeddings
The plots below show a simplified set of learned embedding vectors in two dimensions. Words associated with nature and rivers are concentrated in the top right quadrant of the graph, while words associated with money are concentrated in the bottom left. The vector representing the word bank is positioned between the two clusters due to its polysemic nature. The objective of self-attention is to move the learned embedding vectors to regions of vector space that more accurately capture their meaning within the context of the input sequence. In the example input Write a poem about a man fishing on a river bank. , the aim is to move the vector for bank in such a way that captures more of the meaning of nature and rivers, and less of the meaning of money and deposits.
Note: More accurately, the goal of self-attention here is to update the vector for every word in the input, so that all embeddings better represent the context in which they were used. There is nothing special about the word bank here that transformers have some special knowledge of — self-attention is applied across all the words. We will look more at this shortly, but for now, considering solely how bank is affected by self-attention gives a good intuition for what is happening in the attention block. For the purpose of this visualisation, the positional encoding information has not been explicitly shown. The effect of this will be minimal, but note that the self-attention mechanism will technically operate on the sum of the learned embedding plus the positional information and not solely the learned embedding itself.
3.3 — The Self-Attention Algorithm
In the section above, we stated that the goal of self-attention is to move the embedding for each token to a region of vector space that better represents the context of its use in the input sequence. What we didn’t discuss is how this is done. Here we will show a step-by-step example of how the self-attention mechanism modifies the embedding for bank , by adding context from the surrounding tokens.
Step 1) Calculate the Similarity Between Words using the Dot Product:
The context of a token is given by the surrounding tokens in the sentence. Therefore, we can use the embeddings of all the tokens in the input sequence to update the embedding for any word, such as bank . Ideally, words that provide significant context (such as river ) will heavily influence the embedding, while words that provide less context (such as a ) will have minimal effect.
The degree of context one word contributes to another is measured by a similarity score. Tokens with similar learned embeddings are likely to provide more context than those with dissimilar embeddings. The similarity scores are calculated by taking the dot product of the current embedding for one token (its learned embedding plus positional information) with the current embeddings of every other token in the sequence. For clarity, the current embeddings have been termed s elf-attention inputs in this article and are denoted x .
There are several options for measuring the similarity between two vectors, which can be broadly categorised into: distance-based and angle-based metrics. Distance-based metrics characterise the similarity of vectors using the straight-line distance between them. This calculation is relatively simple and can be thought of as applying Pythagoras’s theorem in d_model -dimensional space. While intuitive, this approach is computationally expensive.
For angle-based similarity metrics, the two main candidates are: cosine similarity and dot-product similarity . Both of these characterise similarity using the cosine of the angle between the two vectors, θ. For orthogonal vectors (vectors that are at right angles to each other) cos(θ) = 0 , which represents no similarity. For parallel vectors, cos(θ) = 1 , which represents that the vectors are identical. Solely using the angle between vectors, as is the case with cosine similarity, is not ideal for two reasons. The first is that the magnitude of the vectors is not considered, so distant vectors that happen to be aligned will produce inflated similarity scores. The second is that cosine similarity requires first computing the dot product and then dividing by the product of the vectors’ magnitudes — making cosine similarity a computationally expensive metric. Therefore, the dot product is used to determine similarity. The dot product formula is given below for two vectors x_1 and x_2 .
The diagram below shows the dot product between the self-attention input vector for bank , x_bank, and the matrix of vector representations for every token in the input sequence, X^T . We can also write x_bank as x_11 to reflect its position in the input sequence. The matrix X stores the self-attention inputs for every token in the input sequence as rows. The number of columns in this matrix is given by L_max , the maximum sequence length of the model. In this example, we will assume that the maximum sequence length is equal to the number of words in the input prompt, removing the need for any padding tokens (see Part 4 in this series for more about padding). To compute the dot product directly, we can transpose X and calculate the vector of similarity scores, S_bank using S_bank = x_bank ⋅ X^T . The individual elements of S_bank represent the similarity scores between bank and each token in the input sequence.
Step 2) Scale the Similarity Scores:
The dot product approach lacks any form of normalisation (unlike cosine similarity), which can cause the similarity scores to become very large. This can pose computational challenges, so normalisation of some form becomes necessary. The most common method is to divide each score by √ d_model , resulting in scaled dot-product attention . Scaled dot-product attention is not restricted to self-attention and is also used for cross-attention in transformers.
Step 3) Calculate the Attention Weights using the Softmax Function:
The output of the previous step is the vector S_bank , which contains the similarity scores between bank and every token in the input sequence. These similarity scores are used as weights to construct a transformer embedding for bank from the weighted sum of embeddings for each surrounding token in the prompt. The weights, known as attention weights , are calculated by passing S_bank into the softmax function. The outputs are stored in a vector denoted W_bank . To see more about the softmax function, refer to the previous article on word2vec.
Step 4) Calculate the Transformer Embedding
Finally, the transformer embedding for bank is obtained by taking the weighted sum of write , a , prompt , …, bank . Of course, bank will have the highest similarity score with itself (and therefore the largest attention weight), so the output embedding after this process will remain similar to before. This behaviour is ideal since the initial embedding already occupies a region of vector space that encodes some meaning for bank. The goal is to nudge the embedding towards the words that provide more context. The weights for words that provide little context, such as a and man , are very small. Hence, their influence on the output embedding will be minimal. Words that provide significant context, such as river and fishing , will have higher weights, and therefore pull the output embedding closer to their regions of vector space. The end result is a new embedding, y_bank , that reflects the context of the entire input sequence.
3.4 — Expanding Self-Attention using Matrices
Above, we walked through the steps to calculate the transformer embedding for the singular word bank . The input consisted of the learned embedding vector for bank plus its positional information, which we denoted x_11 or x_bank . The key point here, is that we considered only one vector as the input. If we instead pass in the matrix X (with dimensions L_max × d_model ) to the self-attention block, we can calculate the transformer embedding for every token in the input prompt simultaneously. The output matrix, Y , contains the transformer embedding for every token along the rows of the matrix. This approach is what enables transformers to quickly process text.
3.5 — The Query, Key, and Value Matrices
The above description gives an overview of the core functionality of the self-attention block, but there is one more piece of the puzzle. The simple weighted sum above does not include any trainable parameters, but we can introduce some to the process. Without trainable parameters, the performance of the model may still be good, but by allowing the model to learn more intricate patterns and hidden features from the training data, we observe much stronger model performance.
The self-attention inputs are used three times to calculate the new embeddings, these include the x_bank vector, the X^T matrix in the dot product step, and the X^T matrix in the weighted sum step. These three sites are the perfect candidates to introduce some weights, which are added in the form of matrices (shown in red). When pre-multiplied by their respective inputs (shown in blue), these form the key , query , and value matrices, K , Q , and V (shown in purple). The number of columns in these weight matrices is an architectural choice by the user. Choosing a value for d_q , d_k , and d_v that is less than d_model will result in dimensionality reduction, which can improve model speed. Ultimately, these values are hyperparameters that can be changed based on the specific implementation of the model and the use-case, and are often all set equal to d_model if unsure [5].
3.6 — The Database Analogy
The names for these matrices come from an analogy with databases, which is explained briefly below.
- A query in a database is what you are looking for when performing a search. For example, “show me all the albums in the database that have sold more than 1,000,000 records”. In the self-attention block, we are essentially asking the same question, but phrased as “show me the transformer embedding for this vector (e.g. x_bank )”.
- The keys in the database are the attributes or columns that are being searched against. In the example given earlier, you can think of this as the “Albums Sold” column, which stores the information we are interested in. In self-attention, we are interested in the embeddings for every word in the input prompt, so we can compute a set of attention weights. Therefore, the key matrix is a collection of all the input embeddings.
- The values correspond to the actual data in the database, that is, the actual sale figures in our example (e.g. 2,300,000 copies). For self-attention, this is exactly the same as the input for the key matrix: a collection of all the input embeddings. Hence, the key and value matrices both take in the matrix X as the input.
3.7 — A Note on Multi-Head Attention
Distributing Computation Across Multiple Heads:
The “Attention is All You Need” paper expands self-attention into multi-head attention , which gives even richer representations of the input sequences. This method involves repeating the calculation of attention weights using different key, query, and value matrices which are learned independently within each head . A head is a section of the attention block dedicated to processing a fraction of the input embedding dimensions. For example, an input, x , with 512 dimensions will be divided by the number of heads, h , to create h chunks of size d_k (where d_k = d_model / h ). For a model with 8 heads ( h=8 ), each head will receive 64 dimensions of x ( d_k = 64). Each chunk is processed using the self-attention mechanism in its respective head, and at the end the outputs from all heads are combined using a linear layer to produce a single output with the original 512 dimensions.
The Benefits of Using Multiple Heads:
The core idea is to allow each head to learn different types of relationships between words in the input sequence, and to combine them to create deep text representations. For example, some heads might learn to capture long-term dependencies (relationships between words that are distant in the text), while others might focus on short-term dependencies (words that are close in text).
Building Intuition for Multi-Head Attention:
To build some intuition for the usefulness of multiple attention heads, consider words in a sentence that require a lot of context. For example, in the sentence I ate some of Bob’s chocolate cake , the word ate should attend to I, Bob’s and cake to gain full context. This is a rather simple example, but if you extend this concept to complex sequences spanning thousands of words, hopefully it seems reasonable that distributing the computational load across separate attention mechanisms will be beneficial.
Summary of Multi-Head Attention:
To summarise, multi-head attention involves repeating the self-attention mechanism h times and combining the results to distil the information into rich transformer embeddings. While this step is not strictly necessary, it has been found to produce more impressive results, and so is standard in transformer-based models.
4.1 — Extracting Learned Embeddings and Transformer Embeddings from Transformer Models
Python has many options for working with transformer models, but none are perhaps as well-known as Hugging Face. Hugging Face provides a centralised resource hub for NLP researchers and developers alike, including tools such as:
- transformers : The library at the core of Hugging Face, which provides an interface for using, training, and fine-tuning pre-trained transformer models.
- tokenizers : A library for working with tokenizers for many kinds of transformers, either using pre-built tokenizer models or constructing brand new ones from scratch.
- datasets : A collection of datasets to train models on a variety of tasks, not just restricted to NLP.
- Model Hub: A large repository of cutting-edge models from published papers, community-developed models, and everything in between. These are made freely available and can be easily imported into Python via the transformers API.
The code cell below shows how the transformers library can be used to load a transformer-based model into Python, and how to extract both the learned embeddings for words (without context) and the transformer embeddings (with context). The remainder of this article will break down the steps shown in this cell and describe additional functionalities available when working with embeddings.
4.2 — Import the Transformers Library
The first step to produce transformer embeddings is to choose a model from the Hugging Face transformers library. In this article, we will not use the model for inference but solely to examine the embeddings it produces. This is not a standard use-case, and so we will have to do some extra digging in order to access the embeddings. Since the transformers library is written in PyTorch (referred to as torch in the code), we can import torch to extract data from the inner workings of the models.
4.3 — Choose a Model
For this example, we will use DistilBERT, a smaller version of Google’s BERT model which was released by Hugging Face themselves in October 2019 [6]. According to the Hugging Face documentation [7]:
DistilBERT is a small, fast, cheap and light Transformer model trained by distilling BERT base. It has 40% less parameters than bert-base-uncased , runs 60% faster while preserving over 95% of BERT’s performances as measured on the GLUE language understanding benchmark .
We can import DistilBERT and its corresponding tokenizer into Python either directly from the transformers library or using the AutoModel and AutoTokenizer classes. There is very little difference between the two, although AutoModel and AutoTokenizer are often preferred since the model name can be parameterised and stored in a string, which makes it simpler to change the model being used.
After importing DistilBERT and its corresponding tokenizer, we can call the from_pretrained method for each to load in the specific version of the DistilBERT model and tokenizer we want to use. In this case, we have chosen distilbert-base-uncased , where base refers to the size of the model, and uncased indicates that the model was trained on uncased text (all text is converted to lowercase).
4.4 — Create Some Example Sentences
Next, we can create some sentences to give the model some words to embed. The two sentences, s1 and s2 , both contain the word bank but in different contexts. The goal here is to show that the word bank will begin with the same learned embedding in both sentences, then be modified by DistilBERT using self-attention to produce a unique, contextualised embedding for each input sequence.
4.5 — Tokenize an Input Sequence
The tokenizer class can be used to tokenize an input sequence (as shown below) and convert a string into a list of token IDs. Optionally, we can also pass a return_tensors argument to format the token IDs as a PyTorch tensor ( return_tensors=pt ) or as TensorFlow constants ( return_tensors=tf ). Leaving this argument empty will return the token IDs in a Python list. The return value is a dictionary that contains input_ids : the list-like object containing token IDs, and attention_mask which we will ignore for now.
Note: BERT-based models include a [CLS] token at the beginning of each sequence, and a [SEP] token to distinguish between two bodies of text in the input. These are present due to the tasks that BERT was originally trained on and can largely be ignored here. For a discussion on BERT special tokens, model sizes, cased vs uncased , and the attention mask, see Part 4 of this series .
4.6 — Extract the Learned Embeddings from a Model
Each transformer model provides access to its learned embeddings via the embeddings.word_embeddings method. This method accepts a token ID or collection of token IDs and returns the learned embedding(s) as a PyTorch tensor.
4.7 — Extract the Transformer Embeddings from a Model
Converting a context-lacking learned embedding into a context-aware transformer embedding requires a forward pass of the model. Since we are not updating the weights of the model here (i.e. training the model), we can use the torch.no_grad() context manager to save on memory. This allows us to pass the tokens directly into the model and compute the transformer embeddings without any unnecessary calculations. Once the tokens have been passed into the model, a BaseModelOutput is returned, which contains various information about the forward pass. The only data that is of interest here is the activations in the last hidden state, which form the transformer embeddings. These can be accessed using the last_hidden_state attribute, as shown below, which concludes the explanation for the code cell shown at the top of this section.
4.8 — Convert Token IDs to Tokens
It is possible to convert token IDs back into textual tokens, which shows exactly how the tokenizer divided the input sequence. This is useful when longer or rarer words are divided into multiple subwords when using subword tokenizers such as WordPiece (e.g. in BERT-based models) or Byte-Pair Encoding (e.g. in the GPT family of models).
The self-attention mechanism generates rich, context-aware transformer embeddings for text by processing each token in an input sequence simultaneously. These embeddings build on the foundations of static word embeddings (such as word2vec) and enable more capable language models such as BERT and GPT. Further work in this field will continue to improve the capabilities of LLMs and NLP as a whole.
[1] A. Vaswani, N. Shazeer, N. Parmar, J. Uszkoreit, L. Jones, A. N. Gomez, Ł. Kaiser, and I. Polosukhin, Attention is All You Need (2017), Advances in Neural Information Processing Systems 30 (NIPS 2017)
[2] Hugging Face, Transformers (2024), HuggingFace.co
[3] OpenAI, ChatGPT Pricing (2024), OpenAI.com
[4] A. Gu and T. Dao, Mamba: Linear-Time Sequence Modelling with Selective State Spaces (2023), ArXiv abs/2312.00752
[5] J. Alammar, The Illustrated Transformer (2018). GitHub
[6] V. Sanh, L. Debut, J. Chaumond, and T. Wolf, DistilBERT, a distilled version of BERT: smaller, faster, cheaper and lighter (2019), 5th Workshop on Energy Efficient Machine Learning and Cognitive Computing — NeurIPS 2019
[7] Hugging Face, DistilBERT Documentation (2024) HuggingFace.co
[8] Hugging Face, BERT Documentation (2024) HuggingFace.co

Written by Bradney Smith
Senior Machine Learning Engineer. My work focuses on Natural Language Processing (NLP) and data science communication. Check out my "LLMs from Scratch" series !
Text to speech
CS50: Introduction to Computer Science
An introduction to the intellectual enterprises of computer science and the art of programming.
Associated Schools

Harvard School of Engineering and Applied Sciences
What you'll learn.
A broad and robust understanding of computer science and programming
How to think algorithmically and solve programming problems efficiently
Concepts like abstraction, algorithms, data structures, encapsulation, resource management, security, software engineering, and web development
Familiarity with a number of languages, including C, Python, SQL, and JavaScript plus CSS and HTML
How to engage with a vibrant community of like-minded learners from all levels of experience
How to develop and present a final programming project to your peers
Course description
This is CS50x , Harvard University's introduction to the intellectual enterprises of computer science and the art of programming for majors and non-majors alike, with or without prior programming experience. An entry-level course taught by David J. Malan, CS50x teaches students how to think algorithmically and solve problems efficiently. Topics include abstraction, algorithms, data structures, encapsulation, resource management, security, software engineering, and web development. Languages include C, Python, SQL, and JavaScript plus CSS and HTML. Problem sets inspired by real-world domains of biology, cryptography, finance, forensics, and gaming. The on-campus version of CS50x , CS50, is Harvard's largest course.
Students who earn a satisfactory score on 9 problem sets (i.e., programming assignments) and a final project are eligible for a certificate. This is a self-paced course–you may take CS50x on your own schedule.
Instructors

David J. Malan

You may also like

CS50's Understanding Technology
This is CS50’s introduction to technology for students who don’t (yet!) consider themselves computer persons.

CS50 for Lawyers
This course is a variant of Harvard University's introduction to computer science, CS50, designed especially for lawyers (and law students).
Using Python for Research
Take your introductory knowledge of Python programming to the next level and learn how to use Python 3 for your research.
Join our list to learn more
Collectives™ on Stack Overflow
Find centralized, trusted content and collaborate around the technologies you use most.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Get early access and see previews of new features.
What is the best way to do automatic attribute assignment in Python, and is it a good idea?
Instead of writing code like this every time I define a class:
I could use this recipe for automatic attribute assignment .
Two questions :
- Are there drawbacks or pitfalls associated with this shortcut?
Is there a better way to achieve similar convenience?
- 4 +1 this is a recurrent pattern in Python. I don't see any drawback in using the autoassign decorator, as it lets you define a list of argument not to assign. – pberkes Sep 6, 2010 at 16:55
- 1 stackoverflow.com/questions/1389180/… – pmav99 May 24, 2014 at 12:32
9 Answers 9
There are some things about the autoassign code that bug me (mostly stylistic, but one more serious problem):
autoassign does not assign an 'args' attribute:
autoassign acts like a decorator. But autoassign(*argnames) calls a function which returns a decorator. To achieve this magic, autoassign needs to test the type of its first argument. If given a choice, I prefer functions not test the type of its arguments.
There seems to be a considerable amount of code devoted to setting up sieve , lambdas within lambdas, ifilters, and lots of conditions.
I think there might be a simpler way. (See below).
for _ in itertools.starmap(assigned.setdefault, defaults): pass . I don't think map or starmap was meant to call functions, whose only purpose is their side effects. It could have been written more clearly with the mundane:
Here is an alternative simpler implementation which has the same functionality as autoassign (e.g. can do includes and excludes), and which addresses the above points:
And here is the unit test I used to check its behavior:
PS. Using autoassign or autoargs is compatible with IPython code completion.
- 1 I also found your autoargs incredibly handy. One issue I noticed is that it seems to throw an error if defaults is None , because the call to reversed fails. Am I right in thinking that this should be fixable by adding an if defaults: in front of the line for attr,val in zip(reversed(attrs),reversed(defaults)): , or does that have unintended sideeffects? The unit test passes. – m01 Feb 12, 2014 at 9:32
- @m01: Sorry for the very belated response. Thanks for the correction! – unutbu Aug 2, 2017 at 15:38
- @unutbu Just a nit but in 3.10.x inspect.getargspec(func) getargspec is deprecated. you should use inspect.getfullargspec(func) instead – Frank C. Jan 10, 2023 at 20:46
From Python 3.7+ you can use a Data Class , which achieves what you want and more.
It allows you to define fields for your class, which are attributes automatically assigned.
It would look something like that:
The __init__ method will be automatically created in your class, and it will assign the arguments of instance creation to those attributes (and validate the arguments).
Note that here type hinting is required , that is why I have used int and str in the example. If you don't know the type of your field, you can use Any from the typing module .
- 1 Backport for Python 3.6 : The PEP 557 references a sample implementation ( permalink as of 2019-10-28 ) on GitHub which has a pypi/pip module as well. Therefore it can be installed by pip install dataclasses . – luckydonald Oct 28, 2019 at 21:19
I don't know if it is necessarily better, but you could do this:
Courtesy Peter Norvig's Python: Infrequently Answered Questions .
- 7 This is a quick solution to the problem, but it has two drawbacks: 1) you have to add much more code if you want to make sure that some arguments are passed to the function; 2) the signature of the function is completely opaque, and it cannot be used to understand how to call the function; one will need to rely on the docstring instead – pberkes Sep 6, 2010 at 16:57
One drawback: many IDEs parse __init__.py to discover an object's attributes. If you want automatic code completion in your IDE to be more functional, then you may be better off spelling it out the old-fashioned way.
If you have a lot of variables, you could pass one single configuration dict or object.
Similar to the above, though not the same... the following is very short, deals with args and kwargs :
Use like this:
This a simple implementation by judy2k :
In this package you can now find
- @autoargs inspired by answer-3653049
- @autoprops to transform the fields generated by @autoargs into @property , for use in combination with a validation library such as enforce or pycontracts .
Note that this has been validated for python 3.5+
You just can't use *args, but you can store in some instance list (like self.args, don't know)
Your Answer
Reminder: Answers generated by artificial intelligence tools are not allowed on Stack Overflow. Learn more
Sign up or log in
Post as a guest.
Required, but never shown
By clicking “Post Your Answer”, you agree to our terms of service and acknowledge you have read our privacy policy .
Not the answer you're looking for? Browse other questions tagged python attributes decorator or ask your own question .
- Featured on Meta
- The 2024 Developer Survey Is Live
- The return of Staging Ground to Stack Overflow
- The [tax] tag is being burninated
- Policy: Generative AI (e.g., ChatGPT) is banned
Hot Network Questions
- Book where the populace is split between two sects, that of the “hand” and that of the “mind"
- Was it known in ancient Rome and Greece that boiling water made it safe to drink and if so, what was the theory behind this?
- Why aren't tightly stitched commercial pcbs more common?
- Thought experiment regarding gravity
- Has a country ever by its own volition refused to join the United Nations?
- TikZ - how to draw ticks on circle perpendicularly with ellipses around?
- 1h 10m international > domestic transit at IST (Istanbul) on a single ticket
- Group with a translation invariant ultrafilter
- Have any countries managed to reduce immigration by a significant margin in the absence of economic problems?
- What happens when you target a dead creature with Scrying?
- Is there a phrase like "etymologically related" but for food?
- Why are we abbreviating Player's Handbook to PHB?
- Why is array access not an infix operator?
- siesta 5.0 compilation issues with spack
- What is the difference between Hof and Bauernhof?
- Yosemite national park availability
- For the square wave signal, why does a narrower square wave correspond to more spread in the frequency domain?
- Is it allowed to use patents for new inventions?
- How do Authenticators work?
- I need help in understanding the alternative solution provided to solve this geometry question of calculating area of quadrilateral
- Ubuntu Terminal with alternating colours for each line
- How can I use a transistor to control the segments on this 7-segment display?
- What does "far right tilt" actually mean in the context of the EU in 2024?
- What do humans do uniquely, that computers apparently will not be able to?

An official website of the United States government
Here’s how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
Free Cyber Services #protect2024 Secure Our World Shields Up Report A Cyber Issue
Vulnerability Summary for the Week of June 3, 2024
The CISA Vulnerability Bulletin provides a summary of new vulnerabilities that have been recorded by the National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD) in the past week. NVD is sponsored by CISA. In some cases, the vulnerabilities in the bulletin may not yet have assigned CVSS scores. Please visit NVD for updated vulnerability entries, which include CVSS scores once they are available.
Vulnerabilities are based on the Common Vulnerabilities and Exposures (CVE) vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores:
- High : vulnerabilities with a CVSS base score of 7.0–10.0
- Medium : vulnerabilities with a CVSS base score of 4.0–6.9
- Low : vulnerabilities with a CVSS base score of 0.0–3.9
Entries may include additional information provided by organizations and efforts sponsored by CISA. This information may include identifying information, values, definitions, and related links. Patch information is provided when available. Please note that some of the information in the bulletin is compiled from external, open-source reports and is not a direct result of CISA analysis.
High Vulnerabilities
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| 8theme--XStore Core | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in 8theme XStore Core allows PHP Local File Inclusion.This issue affects XStore Core: from n/a through 5.3.8. | 2024-06-04 | | |
| 8theme--XStore | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in 8theme XStore allows PHP Local File Inclusion.This issue affects XStore: from n/a through 9.3.8. | 2024-06-04 | | |
| ABB, Busch-Jaeger--2.4! Display 55, SD/U12.55.11-825 | FDSK Leak in ABB, Busch-Jaeger, FTS Display (version 1.00) and BCU (version 1.3.0.33) allows attacker to take control via access to local KNX Bus-System | 2024-06-05 | | |
| ABB, Busch-Jaeger--2.4! Display 55, SD/U12.55.11-825 | Replay Attack in ABB, Busch-Jaeger, FTS Display (version 1.00) and BCU (version 1.3.0.33) allows attacker to capture/replay KNX telegram to local KNX Bus-System | 2024-06-05 | | |
| BdThemes--Element Pack Pro | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal'), Deserialization of Untrusted Data vulnerability in BdThemes Element Pack Pro allows Path Traversal, Object Injection.This issue affects Element Pack Pro: from n/a through 7.7.4. | 2024-06-04 | | |
| BestWebSoft--Contact Form to DB by BestWebSoft | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in BestWebSoft Contact Form to DB by BestWebSoft.This issue affects Contact Form to DB by BestWebSoft: from n/a through 1.7.2. | 2024-06-08 | | |
| Bitdefender--GravityZone Console On-Premise | A host whitelist parser issue in the proxy service implemented in the GravityZone Update Server allows an attacker to cause a server-side request forgery. This issue only affects GravityZone Console versions before 6.38.1-2 that are running only on premise. | 2024-06-06 | | |
| bobbysmith007--WP-DB-Table-Editor | The WP-DB-Table-Editor plugin for WordPress is vulnerable to unauthorized access of data, modification of data, and loss of data due to lack of a default capability requirement on the 'dbte_render' function in all versions up to, and including, 1.8.4. This makes it possible for authenticated attackers, with contributor access and above, to modify database tables that the theme has been configured to use the plugin to edit. | 2024-06-04 | | |
| chainguard-dev--apko | apko is an apk-based OCI image builder. apko exposures HTTP basic auth credentials from repository and keyring URLs in log output. This vulnerability is fixed in v0.14.5. | 2024-06-03 | | |
| Chanjet--Smooth T+system | A vulnerability, which was classified as critical, has been found in Chanjet Smooth T+system 3.5. This issue affects some unknown processing of the file /tplus/UFAQD/keyEdit.aspx. The manipulation of the argument KeyID leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-267185 was assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-05 | | |
| chrisbadgett--LifterLMS WordPress LMS for eLearning | The LifterLMS - WordPress LMS Plugin for eLearning plugin for WordPress is vulnerable to SQL Injection via the orderBy attribute of the lifterlms_favorites shortcode in all versions up to, and including, 7.6.2 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for authenticated attackers, with Contributor-level access and above, to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-05 | | |
| Cisco--Cisco Unified Contact Center Enterprise | A vulnerability in the web-based management interface of Cisco Finesse could allow an unauthenticated, remote attacker to conduct an SSRF attack on an affected system. This vulnerability is due to insufficient validation of user-supplied input for specific HTTP requests that are sent to an affected system. An attacker could exploit this vulnerability by sending a crafted HTTP request to the affected device. A successful exploit could allow the attacker to obtain limited sensitive information for services that are associated to the affected device. | 2024-06-05 | | |
| Code for Recovery--12 Step Meeting List | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Code for Recovery 12 Step Meeting List allows Reflected XSS.This issue affects 12 Step Meeting List: from n/a through 3.14.33. | 2024-06-08 | | |
| Code Parrots--Easy Forms for Mailchimp | Insertion of Sensitive Information into Log File vulnerability in Code Parrots Easy Forms for Mailchimp.This issue affects Easy Forms for Mailchimp: from n/a through 6.9.0. | 2024-06-04 | | |
| Codeer Limited--Bricks Builder | Improper Control of Generation of Code ('Code Injection') vulnerability in Codeer Limited Bricks Builder allows Code Injection.This issue affects Bricks Builder: from n/a through 1.9.6. | 2024-06-04 | | |
| codelessthemes--Cowidgets Elementor Addons | The Cowidgets - Elementor Addons plugin for WordPress is vulnerable to Local File Inclusion in all versions up to, and including, 1.1.1 via the 'item_style' and 'style' parameters. This makes it possible for authenticated attackers, with Contributor-level access and above, to include and execute arbitrary files on the server, allowing the execution of any PHP code in those files. This can be used to bypass access controls, obtain sensitive data, or achieve code execution in cases where images and other "safe" file types can be uploaded and included. | 2024-06-06 | | |
| CodePeople--WP Time Slots Booking Form | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in CodePeople WP Time Slots Booking Form allows Stored XSS.This issue affects WP Time Slots Booking Form: from n/a through 1.2.10. | 2024-06-08 | | |
| CODESYS--CODESYS Control for BeagleBone SL | An unauthenticated remote attacker can use a malicious OPC UA client to send a crafted request to affected CODESYS products which can cause a DoS due to incorrect calculation of buffer size. | 2024-06-04 | | |
| CODESYS--CODESYS Control Win (SL) | A local attacker with low privileges can read and modify any users files and cause a DoS in the working directory of the affected products due to exposure of resource to wrong sphere. | 2024-06-04 | | |
| Dell--CPG BIOS | Dell BIOS contains a missing support for integrity check vulnerability. An attacker with physical access to the system could potentially bypass security mechanisms to run arbitrary code on the system. | 2024-06-07 | | |
| Dell--PowerScale OneFS | Dell PowerScale OneFS versions 8.2.x through 9.8.0.x contain a use of hard coded credentials vulnerability. An adjacent network unauthenticated attacker could potentially exploit this vulnerability, leading to information disclosure of network traffic and denial of service. | 2024-06-04 | | |
| denoland--deno | An issue in `.npmrc` support in Deno 1.44.0 was discovered where Deno would send `.npmrc` credentials for the scope to the tarball URL when the registry provided URLs for a tarball on a different domain. All users relying on .npmrc are potentially affected by this vulnerability if their private registry references tarball URLs at a different domain. This includes usage of deno install subcommand, auto-install for npm: specifiers and LSP usage. It is recommended to upgrade to Deno 1.44.1 and if your private registry ever serves tarballs at a different domain to rotate your registry credentials. | 2024-06-06 | | |
| dexta--Dextaz Ping | Improper Neutralization of Special Elements used in a Command ('Command Injection') vulnerability in dexta Dextaz Ping allows Command Injection.This issue affects Dextaz Ping: from n/a through 0.65. | 2024-06-04 | | |
| DigiWin--EasyFlow .NET | DigiWin EasyFlow .NET lacks validation for certain input parameters. An unauthenticated remote attacker can inject arbitrary SQL commands to read, modify, and delete database records. | 2024-06-03 | | |
| directus--directus | Directus is a real-time API and App dashboard for managing SQL database content. Prior to 10.11.2, providing a non-numeric length value to the random string generation utility will create a memory issue breaking the capability to generate random strings platform wide. This creates a denial of service situation where logged in sessions can no longer be refreshed as sessions depend on the capability to generate a random session ID. This vulnerability is fixed in 10.11.2. | 2024-06-03 | | |
| envoyproxy--envoy | Envoy is a cloud-native, open source edge and service proxy. Envoyproxy with a Brotli filter can get into an endless loop during decompression of Brotli data with extra input. | 2024-06-04 | | |
| envoyproxy--envoy | Envoy is a cloud-native, open source edge and service proxy. Due to how Envoy invoked the nlohmann JSON library, the library could throw an uncaught exception from downstream data if incomplete UTF-8 strings were serialized. The uncaught exception would cause Envoy to crash. | 2024-06-04 | | |
| evmos--evmos | Evmos is the Ethereum Virtual Machine (EVM) Hub on the Cosmos Network. There is an issue with how to liquid stake using Safe which itself is a contract. The bug only appears when there is a local state change together with an ICS20 transfer in the same function and uses the contract's balance, that is using the contract address as the sender parameter in an ICS20 transfer using the ICS20 precompile. This is in essence the "infinite money glitch" allowing contracts to double the supply of Evmos after each transaction.The issue has been patched in versions >=V18.1.0. | 2024-06-06 | | |
| expresstech--Quiz and Survey Master (QSM) Easy Quiz and Survey Maker | The Quiz And Survey Master - Best Quiz, Exam and Survey Plugin for WordPress plugin for WordPress is vulnerable to SQL Injection via the 'question_id' parameter in all versions up to, and including, 9.0.1 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for authenticated attackers, with contributor-level access and above, to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-07 | | |
| Fahad Mahmood--WP Docs | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Fahad Mahmood WP Docs allows Reflected XSS.This issue affects WP Docs: from n/a through 2.1.3. | 2024-06-08 | | |
| Foliovision--FV Flowplayer Video Player | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Foliovision FV Flowplayer Video Player allows Reflected XSS.This issue affects FV Flowplayer Video Player: from n/a through 7.5.45.7212. | 2024-06-03 | | |
| Fortinet--FortiWebManager | An improper authorization in Fortinet FortiWebManager version 7.2.0 and 7.0.0 through 7.0.4 and 6.3.0 and 6.2.3 through 6.2.4 and 6.0.2 allows attacker to execute unauthorized code or commands via HTTP requests or CLI. | 2024-06-03 | | |
| Fortinet--FortiWebManager | An improper authorization in Fortinet FortiWebManager version 7.2.0 and 7.0.0 through 7.0.4 and 6.3.0 and 6.2.3 through 6.2.4 and 6.0.2 allows attacker to execute unauthorized code or commands via HTTP requests or CLI. | 2024-06-03 | | |
| Fortinet--FortiWebManager | An improper authorization in Fortinet FortiWebManager version 7.2.0 and 7.0.0 through 7.0.4 and 6.3.0 and 6.2.3 through 6.2.4 and 6.0.2 allows attacker to execute unauthorized code or commands via HTTP requests or CLI. | 2024-06-03 | | |
| gelform--Social Link Pages: link-in-bio landing pages for your social media profiles | The Social Link Pages: link-in-bio landing pages for your social media profiles plugin for WordPress is vulnerable to unauthorized access due to a missing capability check on the import_link_pages() function in all versions up to, and including, 1.6.9. This makes it possible for unauthenticated attackers to inject arbitrary pages and malicious web scripts. | 2024-06-04 | | |
| GiveWP--GiveWP | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in GiveWP allows Reflected XSS.This issue affects GiveWP: from n/a through 3.12.0. | 2024-06-08 | | |
| Grafana--OnCall | Grafana OnCall is an easy-to-use on-call management tool that will help reduce toil in on-call management through simpler workflows and interfaces that are tailored specifically for engineers. Grafana OnCall, from version 1.1.37 before 1.5.2 are vulnerable to a Server Side Request Forgery (SSRF) vulnerability in the webhook functionallity. This issue was fixed in version 1.5.2 | 2024-06-05 | | |
| HCL Software--Domino Server | The Domino Catalog template is susceptible to a Stored Cross-Site Scripting (XSS) vulnerability. An attacker with the ability to edit documents in the catalog application/database created from this template can embed a cross site scripting attack. The attack would be activated by an end user clicking it. | 2024-06-06 | | |
| IBM--Engineering Requirements Management DOORS Next | IBM Engineering Requirements Management DOORS Next 7.0.2 and 7.0.3 is vulnerable to an XML External Entity Injection (XXE) attack when processing XML data. A remote attacker could exploit this vulnerability to expose sensitive information or consume memory resources. IBM X-Force ID: 268758. | 2024-06-06 | | |
| icegram--Email Subscribers by Icegram Express Email Marketing, Newsletters, Automation for WordPress & WooCommerce | The Email Subscribers by Icegram Express plugin for WordPress is vulnerable to SQL Injection via the 'hash' parameter in all versions up to, and including, 5.7.20 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for unauthenticated attackers to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-05 | | |
| idccms -- idccms | idccms V1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component admin/vpsClass_deal.php?mudi=add | 2024-06-04 | | |
| idccms -- idccms | idccms V1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via admin/vpsCompany_deal.php?mudi=del | 2024-06-04 | | |
| idccms -- idccms | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via /admin/vpsCompany_deal.php?mudi=rev&nohrefStr=close | 2024-06-04 | | |
| idccms -- idccms | idccms V1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via /admin/vpsCompany_deal.php?mudi=add&nohrefStr=close | 2024-06-04 | | |
| ifm--moneo appliance QVA200 | An unauthenticated remote attacker can change the admin password in a moneo appliance due to weak password recovery mechanism. | 2024-06-03 | | |
| itsourcecode--Bakery Online Ordering System | A vulnerability was found in itsourcecode Bakery Online Ordering System 1.0. It has been classified as critical. Affected is an unknown function of the file /admin/modules/product/controller.php?action=add. The manipulation of the argument image leads to unrestricted upload. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. VDB-267414 is the identifier assigned to this vulnerability. | 2024-06-07 | | |
| itsourcecode--Online Discussion Forum | A vulnerability was found in itsourcecode Online Discussion Forum 1.0. It has been rated as critical. This issue affects some unknown processing of the file register_me.php. The manipulation of the argument eaddress leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-267407. | 2024-06-07 | | |
| jupyter-server--jupyter_server | The Jupyter Server provides the backend for Jupyter web applications. Jupyter Server on Windows has a vulnerability that lets unauthenticated attackers leak the NTLMv2 password hash of the Windows user running the Jupyter server. An attacker can crack this password to gain access to the Windows machine hosting the Jupyter server, or access other network-accessible machines or 3rd party services using that credential. Or an attacker perform an NTLM relay attack without cracking the credential to gain access to other network-accessible machines. This vulnerability is fixed in 2.14.1. | 2024-06-06 | | |
| kanboard--kanboard | Kanboard is project management software that focuses on the Kanban methodology. The vuln is in app/Controller/ProjectPermissionController.php function addUser(). The users permission to add users to a project only get checked on the URL parameter project_id. If the user is authorized to add users to this project the request gets processed. The users permission for the POST BODY parameter project_id does not get checked again while processing. An attacker with the 'Project Manager' on a single project may take over any other project. The vulnerability is fixed in 1.2.37. | 2024-06-06 | | |
| litonice13--Master Addons Free Widgets, Hover Effects, Toggle, Conditions, Animations for Elementor | The Master Addons - Free Widgets, Hover Effects, Toggle, Conditions, Animations for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the Navigation Menu widget of the plugin's Mega Menu extension in all versions up to, and including, 2.0.6.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| LJ Apps--WP TripAdvisor Review Slider | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in LJ Apps WP TripAdvisor Review Slider allows Blind SQL Injection.This issue affects WP TripAdvisor Review Slider: from n/a through 12.6. | 2024-06-03 | | |
| Loopus--WP Visitors Tracker | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Loopus WP Visitors Tracker allows Reflected XSS.This issue affects WP Visitors Tracker: from n/a through 2.3. | 2024-06-08 | | |
| lvaudore--The Moneytizer | The The Moneytizer plugin for WordPress is vulnerable to unauthorized access of data, modification of data, and loss of data due to a missing capability check on multiple AJAX functions in the /core/core_ajax.php file in all versions up to, and including, 9.5.20. This makes it possible for authenticated attackers, with subscriber access and above, to update and retrieve billing and bank details, update and reset the plugin's settings, and update languages as well as other lower-severity actions. | 2024-06-06 | | |
| lvaudore--The Moneytizer | The The Moneytizer plugin for WordPress is vulnerable to Cross-Site Request Forgery in all versions up to, and including, 9.5.20. This is due to missing or incorrect nonce validation on multiple AJAX functions. This makes it possible for unauthenticated attackers to to update and retrieve billing and bank details, update and reset the plugin's settings, and update languages as well as other lower-severity actions via a forged request granted they can trick a site administrator into performing an action such as clicking on a link. | 2024-06-06 | | |
| misskey-dev--misskey | Misskey is an open source, decentralized microblogging platform. Misskey doesn't perform proper normalization on the JSON structures of incoming signed ActivityPub activity objects before processing them, allowing threat actors to spoof the contents of signed activities and impersonate the authors of the original activities. This vulnerability is fixed in 2024.5.0. | 2024-06-03 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 1.1.0 or newer, enabling a maliciously uploaded scikit-learn model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 1.1.0 or newer, enabling a maliciously uploaded scikit-learn model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 0.9.0 or newer, enabling a maliciously uploaded PyFunc model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 1.24.0 or newer, enabling a maliciously uploaded pmdarima model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 1.23.0 or newer, enabling a maliciously uploaded LightGBM scikit-learn model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 2.0.0rc0 or newer, enabling a maliciously uploaded Tensorflow model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 2.5.0 or newer, enabling a maliciously uploaded Langchain AgentExecutor model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 0.5.0 or newer, enabling a maliciously uploaded PyTorch model to run arbitrary code on an end user's system when interacted with. | 2024-06-04 | | |
| MLflow--MLflow | Deserialization of untrusted data can occur in versions of the MLflow platform running version 1.27.0 or newer, enabling a maliciously crafted Recipe to execute arbitrary code on an end user's system when run. | 2024-06-04 | | |
| MLflow--MLflow | Remote Code Execution can occur in versions of the MLflow platform running version 1.11.0 or newer, enabling a maliciously crafted MLproject to execute arbitrary code on an end user's system when run. | 2024-06-04 | | |
| n/a--Clash | A vulnerability was found in Clash up to 0.20.1 on Windows. It has been declared as critical. This vulnerability affects unknown code of the component Proxy Port. The manipulation leads to improper authentication. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. It is recommended to change the configuration settings. VDB-267406 is the identifier assigned to this vulnerability. | 2024-06-07 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 2200, Exynos 1480, Exynos 2400. It lacks a check for the validation of native handles, which can result in code execution. | 2024-06-07 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor and Wearable Processor Exynos 850, Exynos 1080, Exynos 2100, Exynos 1280, Exynos 1380, Exynos 1330, Exynos W920, Exynos W930. The mobile processor lacks proper reference count checking, which can result in a UAF (Use-After-Free) vulnerability. | 2024-06-07 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor and Wearable Processor Exynos 850, Exynos 1080, Exynos 2100, Exynos 1280, Exynos 1380, Exynos 1330, Exynos W920, Exynos W930. The mobile processor lacks proper memory deallocation checking, which can result in a UAF (Use-After-Free) vulnerability. | 2024-06-07 | | |
| Netgsm--Netgsm | Missing Authorization vulnerability in Netgsm.This issue affects Netgsm: from n/a through 2.9.16. | 2024-06-04 | | |
| open-telemetry--opentelemetry-collector | The OpenTelemetry Collector offers a vendor-agnostic implementation on how to receive, process and export telemetry data. An unsafe decompression vulnerability allows unauthenticated attackers to crash the collector via excessive memory consumption. OTel Collector version 0.102.1 fixes this issue. It is also fixed in the confighttp module version 0.102.0 and configgrpc module version 0.102.1. | 2024-06-05 | | |
| phoeniixx--Social Login Lite For WooCommerce | The Social Login Lite For WooCommerce plugin for WordPress is vulnerable to authentication bypass in versions up to, and including, 1.6.0. This is due to insufficient verification on the user being supplied during the social login through the plugin. This makes it possible for unauthenticated attackers to log in as any existing user on the site, such as an administrator, if they have access to the email. | 2024-06-04 | | |
| pimcore--pimcore | Pimcore is an Open Source Data & Experience Management Platform. The Pimcore thumbnail generation can be used to flood the server with large files. By changing the file extension or scaling factor of the requested thumbnail, attackers can create files that are much larger in file size than the original. This vulnerability is fixed in 11.2.4. | 2024-06-04 | | |
| pokornydavid--Frontend Registration Contact Form 7 | The Frontend Registration - Contact Form 7 plugin for WordPress is vulnerable to privilege escalation in versions up to, and including, 5.1 due to insufficient restriction on the '_cf7frr_' post meta. This makes it possible for authenticated attackers, with editor-level access and above, to modify the default user role in the registration form settings. | 2024-06-04 | | |
| PORTY Smart Tech Technology Joint Stock Company--PowerBank Application | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in PORTY Smart Tech Technology Joint Stock Company PowerBank Application allows Retrieve Embedded Sensitive Data.This issue affects PowerBank Application: before 2.02. | 2024-06-05 | | |
| PowerPack--PowerPack Pro for Elementor | The PowerPack Pro for Elementor plugin for WordPress is vulnerable to privilege escalation in all versions up to, and including, 2.10.17. This is due to the plugin not restricting low privileged users from setting a default role for a registration form. This makes it possible for authenticated attackers, with contributor-level access and above, to create a registration form with administrator set as the default role and then register as an administrator. | 2024-06-08 | | |
| qodeinteractive--Qi Addons For Elementor | The Qi Addons For Elementor plugin for WordPress is vulnerable to Remote File Inclusion in all versions up to, and including, 1.7.2 via the 'behavior' attributes found in the qi_addons_for_elementor_blog_list shortcode. This makes it possible for authenticated attackers, with Contributor-level access and above, to include remote files on the server, resulting in code execution. Please note that this requires an attacker to create a non-existent directory or target an instance where file_exists won't return false with a non-existent directory in the path, in order to successfully exploit. | 2024-06-07 | | |
| Qualcomm, Inc.--Snapdragon | Memory corruption in TZ Secure OS while Tunnel Invoke Manager initialization. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Cryptographic issue while performing attach with a LTE network, a rogue base station can skip the authentication phase and immediately send the Security Mode Command. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Memory corruption in Hypervisor when platform information mentioned is not aligned. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Information disclosure in Video while parsing mp2 clip with invalid section length. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Memory corruption while creating a LPAC client as LPAC engine was allowed to access GPU registers. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Memory corruption while copying a keyblob`s material when the key material`s size is not accurately checked. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Transient DOS while processing an improperly formatted Fine Time Measurement (FTM) management frame. | 2024-06-03 | | |
| realmag777--Active Products Tables for WooCommerce | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in realmag777 Active Products Tables for WooCommerce allows Reflected XSS.This issue affects Active Products Tables for WooCommerce: from n/a through 1.0.6.3. | 2024-06-08 | | |
| Red Hat--Logging Subsystem for Red Hat OpenShift | A flaw was found in OpenShift's Telemeter. If certain conditions are in place, an attacker can use a forged token to bypass the issue ("iss") check during JSON web token (JWT) authentication. | 2024-06-05 | | |
| Red Hat--Red Hat Build of Keycloak | A flaw was found in Keycloak in OAuth 2.0 Pushed Authorization Requests (PAR). Client-provided parameters were found to be included in plain text in the KC_RESTART cookie returned by the authorization server's HTTP response to a `request_uri` authorization request, possibly leading to an information disclosure vulnerability. | 2024-06-03 | | |
| Red Hat--Red Hat Enterprise Linux 8 | A flaw was found in Booth, a cluster ticket manager. If a specially-crafted hash is passed to gcry_md_get_algo_dlen(), it may allow an invalid HMAC to be accepted by the Booth server. | 2024-06-06 | | |
| Repute Infosystems--ARMember | Improper Privilege Management vulnerability in Repute Infosystems ARMember allows Privilege Escalation.This issue affects ARMember: from n/a through 4.0.10. | 2024-06-04 | | |
| RLDD--Auto Coupons for WooCommerce | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in RLDD Auto Coupons for WooCommerce allows Reflected XSS.This issue affects Auto Coupons for WooCommerce: from n/a through 3.0.14. | 2024-06-08 | | |
| Samsung Mobile--Samsung Mobile Devices | Improper access control vulnerability in SmartManagerCN prior to SMR Jun-2024 Release 1 allows local attackers to launch privileged activities. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Heap out-of-bound write vulnerability in parsing grid image header in libsavscmn.so prior to SMR Jun-2024 Release 1 allows local attackers to execute arbitrary code. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Heap out-of-bound write vulnerability in parsing grid image in libsavscmn.so prior to SMR June-2024 Release 1 allows local attackers to execute arbitrary code. | 2024-06-04 | | |
| Select-Themes--Stockholm Core | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Select-Themes Stockholm Core allows PHP Local File Inclusion.This issue affects Stockholm Core: from n/a through 2.4.1. | 2024-06-04 | | |
| Select-Themes--Stockholm | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Select-Themes Stockholm allows PHP Local File Inclusion.This issue affects Stockholm: from n/a through 9.6. | 2024-06-04 | | |
| Select-Themes--Stockholm | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Select-Themes Stockholm allows PHP Local File Inclusion.This issue affects Stockholm: from n/a through 9.6. | 2024-06-04 | | |
| Skops-dev--Skops | Deserialization of untrusted data can occur in versions 0.6 or newer of the skops python library, enabling a maliciously crafted model to run arbitrary code on an end user's system when loaded. | 2024-06-04 | | |
| softaculous--FileOrganizer Manage WordPress and Website Files | The FileOrganizer - Manage WordPress and Website Files plugin for WordPress is vulnerable to Sensitive Information Exposure in all versions up to, and including, 1.0.7 via the 'fileorganizer_ajax_handler' function. This makes it possible for unauthenticated attackers to extract sensitive data including backups or other sensitive information if the files have been moved to the built-in Trash folder. | 2024-06-07 | | |
| solarwinds -- solarwinds_platform | The SolarWinds Platform was determined to be affected by a SWQL Injection Vulnerability. Attack complexity is high for this vulnerability. | 2024-06-04 | | |
| solarwinds -- solarwinds_platform | The SolarWinds Platform was determined to be affected by a Race Condition Vulnerability affecting the web console. | 2024-06-04 | | |
| SolarWinds --SolarWinds Serv-U | SolarWinds Serv-U was susceptible to a directory transversal vulnerability that would allow access to read sensitive files on the host machine. | 2024-06-06 | | |
| sonalsinha21--SKT Addons for Elementor | The SKT Addons for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Age Gate and Creative Slider widgets in all versions up to, and including, 2.0 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-08 | | |
| Summar Software--Mentor Employee Portal | Untrusted data deserialization vulnerability has been found in Mentor - Employee Portal, affecting version 3.83.35. This vulnerability could allow an attacker to execute arbitrary code, by injecting a malicious payload into the "ViewState" field. | 2024-06-06 | | |
| Sysaid--SysAid | SysAid - CWE-89: Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') | 2024-06-06 | | |
| Sysaid--SysAid | SysAid - CWE-78: Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection') | 2024-06-06 | | |
| Tainacan.org--Tainacan | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Tainacan.Org Tainacan allows Reflected XSS.This issue affects Tainacan: from n/a through 0.21.3. | 2024-06-03 | | |
| Team Heateor--Heateor Social Login | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Team Heateor Heateor Social Login allows Cross-Site Scripting (XSS).This issue affects Heateor Social Login: from n/a through 1.1.32. | 2024-06-08 | | |
| Themeisle--Visualizer | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in Themeisle Visualizer.This issue affects Visualizer: from n/a through 3.11.1. | 2024-06-08 | | |
| themeum--Tutor LMS eLearning and online course solution | The Tutor LMS - eLearning and online course solution plugin for WordPress is vulnerable to time-based SQL Injection via the 'course_id' parameter in all versions up to, and including, 2.7.1 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for authenticated attackers, with admin access and above, to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-07 | | |
| ThimPress--Eduma | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in ThimPress Eduma allows Reflected XSS.This issue affects Eduma: from n/a through 5.4.7. | 2024-06-08 | | |
| Tribulant--Newsletters | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Tribulant Newsletters allows Reflected XSS.This issue affects Newsletters: from n/a through 4.9.5. | 2024-06-08 | | |
| unitecms--Unlimited Elements For Elementor (Free Widgets, Addons, Templates) | The Unlimited Elements For Elementor (Free Widgets, Addons, Templates) plugin for WordPress is vulnerable to blind SQL Injection via the 'data[addonID]' parameter in all versions up to, and including, 1.5.109 due to insufficient escaping on the user supplied parameter and lack of sufficient preparation on the existing SQL query. This makes it possible for authenticated attackers, with Contributor-level access and above, to append additional SQL queries into already existing queries that can be used to extract sensitive information from the database. | 2024-06-06 | | |
| Unlimited Elements--Unlimited Elements For Elementor (Free Widgets, Addons, Templates) | Unrestricted Upload of File with Dangerous Type vulnerability in Unlimited Elements Unlimited Elements For Elementor (Free Widgets, Addons, Templates) allows Code Injection.This issue affects Unlimited Elements For Elementor (Free Widgets, Addons, Templates): from n/a through 1.5.66. | 2024-06-04 | | |
| userproplugin -- userpro | Improper Privilege Management vulnerability in DeluxeThemes Userpro allows Privilege Escalation.This issue affects Userpro: from n/a through 5.1.8. | 2024-06-04 | | |
| vanyukov--Market Exporter | The Market Exporter plugin for WordPress is vulnerable to unauthorized loss of data due to a missing capability check on the 'remove_files' function in all versions up to, and including, 2.0.19. This makes it possible for authenticated attackers, with Subscriber-level access and above, to use path traversal to delete arbitrary files on the server. | 2024-06-07 | | |
| viz-rs--nano-id | nano-id is a unique string ID generator for Rust. Affected versions of the nano-id crate incorrectly generated IDs using a reduced character set in the `nano_id::base62` and `nano_id::base58` functions. Specifically, the `base62` function used a character set of 32 symbols instead of the intended 62 symbols, and the `base58` function used a character set of 16 symbols instead of the intended 58 symbols. Additionally, the `nano_id::gen` macro is also affected when a custom character set that is not a power of 2 in size is specified. It should be noted that `nano_id::base64` is not affected by this vulnerability. This can result in a significant reduction in entropy, making the generated IDs predictable and vulnerable to brute-force attacks when the IDs are used in security-sensitive contexts such as session tokens or unique identifiers. The vulnerability is fixed in 0.4.0. | 2024-06-04 | | |
| Wow-Company--Easy Digital Downloads Recent Purchases | Improper Control of Filename for Include/Require Statement in PHP Program ('PHP Remote File Inclusion') vulnerability in Wow-Company Easy Digital Downloads - Recent Purchases allows PHP Remote File Inclusion.This issue affects Easy Digital Downloads - Recent Purchases: from n/a through 1.0.2. | 2024-06-04 | | |
| wpase--Admin and Site Enhancements (ASE) | Improper Authentication vulnerability in wpase Admin and Site Enhancements (ASE) allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Admin and Site Enhancements (ASE): from n/a through 5.7.1. | 2024-06-04 | | |
| wpdevart--Responsive Image Gallery, Gallery Album | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in wpdevart Responsive Image Gallery, Gallery Album.This issue affects Responsive Image Gallery, Gallery Album: from n/a through 2.0.3. | 2024-06-08 | | |
| WPMobile.App--WPMobile.App | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in WPMobile.App allows Reflected XSS.This issue affects WPMobile.App: from n/a through 11.41. | 2024-06-08 | | |
| wshberlin--Startklar Elementor Addons | The Startklar Elementor Addons plugin for WordPress is vulnerable to Directory Traversal in all versions up to, and including, 1.7.15 via the 'dropzone_hash' parameter. This makes it possible for unauthenticated attackers to copy the contents of arbitrary files on the server, which can contain sensitive information, and to delete arbitrary directories, including the root WordPress directory. | 2024-06-06 | | |
| XforWooCommerce--XforWooCommerce | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in XforWooCommerce allows PHP Local File Inclusion.This issue affects XforWooCommerce: from n/a through 2.0.2. | 2024-06-04 | | |
| xootix--Login/Signup Popup ( Inline Form + Woocommerce ) | The Login/Signup Popup ( Inline Form + Woocommerce ) plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the 'import_settings' function in versions 2.7.1 to 2.7.2. This makes it possible for authenticated attackers, with Subscriber-level access and above, to change arbitrary options on affected sites. This can be used to enable new user registration and set the default role for new users to Administrator. | 2024-06-06 | | |
| Yannick Lefebvre--Link Library | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Yannick Lefebvre Link Library link-library allows Reflected XSS.This issue affects Link Library: from n/a through 7.6.3. | 2024-06-08 | | |
| YdataAI--ydata-profiling | Deserialization of untrusted data can occur in versions 3.7.0 or newer of Ydata's ydata-profiling open-source library, enabling a malicously crafted report to run arbitrary code on an end user's system when loaded. | 2024-06-04 | | |
| YdataAI--ydata-profiling | A cross-site scripting (XSS) vulnerability in versions 3.7.0 or newer of Ydata's ydata-profiling open-source library allows for payloads to be run when a maliocusly crafted report is viewed in the browser. | 2024-06-04 | | |
| YdataAI--ydata-profiling | Deseriliazation of untrusted data can occur in versions 3.7.0 or newer of Ydata's ydata-profiling open-source library, enabling a maliciously crafted dataset to run arbitrary code on an end user's system when loaded. | 2024-06-04 | |
Back to top
Medium Vulnerabilities
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| 10up--ElasticPress | Cross-Site Request Forgery (CSRF) vulnerability in 10up ElasticPress.This issue affects ElasticPress: from n/a through 5.1.0. | 2024-06-08 | | |
| 10up--Restricted Site Access | Authentication Bypass by Spoofing vulnerability in 10up Restricted Site Access allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Restricted Site Access: from n/a through 7.4.1. | 2024-06-04 | | |
| 10Web Form Builder Team--Form Maker by 10Web | Improper Restriction of Excessive Authentication Attempts vulnerability in 10Web Form Builder Team Form Maker by 10Web allows Functionality Bypass.This issue affects Form Maker by 10Web: from n/a through 1.15.20. | 2024-06-04 | | |
| 10web--Photo Gallery by 10Web Mobile-Friendly Image Gallery | The Photo Gallery by 10Web - Mobile-Friendly Image Gallery plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'svg' parameter in all versions up to, and including, 1.8.23 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. By default, this can only be exploited by administrators, but the ability to use and configure Photo Gallery can be extended to contributors on pro versions of the plugin. | 2024-06-07 | | |
| 10web--Photo Gallery by 10Web Mobile-Friendly Image Gallery | The Photo Gallery by 10Web - Mobile-Friendly Image Gallery plugin for WordPress is vulnerable to Path Traversal in all versions up to, and including, 1.8.23 via the esc_dir function. This makes it possible for authenticated attackers to cut and paste (copy) the contents of arbitrary files on the server, which can contain sensitive information, and to cut (delete) arbitrary directories, including the root WordPress directory. By default this can be exploited by administrators only. In the premium version of the plugin, administrators can give gallery edit permissions to lower level users, which might make this exploitable by users as low as contributors. | 2024-06-07 | | |
| A WP Life--Contact Form Widget | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in A WP Life Contact Form Widget.This issue affects Contact Form Widget: from n/a through 1.3.9. | 2024-06-03 | | |
| AccessAlly--PopupAlly | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in AccessAlly PopupAlly allows Stored XSS.This issue affects PopupAlly: from n/a through 2.1.1. | 2024-06-03 | | |
| adamskaat--Countdown, Coming Soon, Maintenance Countdown & Clock | The Countdown, Coming Soon, Maintenance - Countdown & Clock plugin for WordPress is vulnerable to unauthorized access due to a missing capability check on the conditionsRow and switchCountdown functions in all versions up to, and including, 2.7.8. This makes it possible for authenticated attackers, with subscriber-level access and above, to inject PHP Objects and modify the status of countdowns. | 2024-06-06 | | |
| Analytify--Analytify | Cross-Site Request Forgery (CSRF) vulnerability in Analytify.This issue affects Analytify: from n/a through 5.2.3. | 2024-06-08 | | |
| apollo13themes--Rife Free | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in apollo13themes Rife Free allows Stored XSS.This issue affects Rife Free: from n/a through 2.4.19. | 2024-06-08 | | |
| argoproj--argo-cd | Argo CD is a declarative, GitOps continuous delivery tool for Kubernetes. The vulnerability allows unauthorized access to the sensitive settings exposed by /api/v1/settings endpoint without authentication. All sensitive settings are hidden except passwordPattern. This vulnerability is fixed in 2.11.3, 2.10.12, and 2.9.17. | 2024-06-06 | | |
| argoproj--argo-cd | Argo CD is a declarative, GitOps continuous delivery tool for Kubernetes. It's possible for authenticated users to enumerate clusters by name by inspecting error messages. It's also possible to enumerate the names of projects with project-scoped clusters if you know the names of the clusters. This vulnerability is fixed in 2.11.3, 2.10.12, and 2.9.17. | 2024-06-06 | | |
| ARI Soft--ARI Stream Quiz | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in ARI Soft ARI Stream Quiz allows Code Injection.This issue affects ARI Stream Quiz: from n/a through 1.3.2. | 2024-06-04 | | |
| artbees--SellKit Funnel builder and checkout optimizer for WooCommerce to sell more, faster | The SellKit - Funnel builder and checkout optimizer for WooCommerce to sell more, faster plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'id' parameter in all versions up to, and including, 1.9.8 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| Automattic--ChaosTheory | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Automattic ChaosTheory allows Stored XSS.This issue affects ChaosTheory: from n/a through 1.3. | 2024-06-03 | | |
| awordpresslife--Formula | The Formula theme for WordPress is vulnerable to Reflected Cross-Site Scripting via the 'id' parameter in the 'quality_customizer_notify_dismiss_action' AJAX action in all versions up to, and including, 0.5.1 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-08 | | |
| awordpresslife--Formula | The Formula theme for WordPress is vulnerable to Reflected Cross-Site Scripting via the 'id' parameter in the 'ti_customizer_notify_dismiss_recommended_plugins' AJAX action in all versions up to, and including, 0.5.1 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-08 | | |
| bdthemes--Prime Slider Addons For Elementor (Revolution of a slider, Hero Slider, Ecommerce Slider) | The Prime Slider - Addons For Elementor (Revolution of a slider, Hero Slider, Ecommerce Slider) plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'id' attribute within the Pacific widget in all versions up to, and including, 3.14.7 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| Benoit Mercusot--Simple Popup Manager | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Benoit Mercusot Simple Popup Manager allows Stored XSS.This issue affects Simple Popup Manager: from n/a through 1.3.5. | 2024-06-03 | | |
| BetterAddons--Better Elementor Addons | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in BetterAddons Better Elementor Addons allows PHP Local File Inclusion.This issue affects Better Elementor Addons: from n/a through 1.4.1. | 2024-06-04 | | |
| BeyondTrust--BeyondInsight | Prior to 23.2, it is possible to perform arbitrary Server-Side requests via HTTP-based connectors within BeyondInsight, resulting in a server-side request forgery vulnerability. | 2024-06-04 | | |
| BeyondTrust--BeyondInsight | Prior to 23.1, an information disclosure vulnerability exists within BeyondInsight which can allow an attacker to enumerate usernames. | 2024-06-04 | | |
| biplob018--Image Hover Effects for Elementor with Lightbox and Flipbox | The Image Hover Effects for Elementor with Lightbox and Flipbox plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the '_id', 'oxi_addons_f_title_tag', and 'content_description_tag' parameters in all versions up to, and including, 3.0.2 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| Born05--CraftCMS Plugin - Two-Factor Authentication | The CraftCMS plugin Two-Factor Authentication through 3.3.3 allows reuse of TOTP tokens multiple times within the validity period. | 2024-06-06 | | |
| Brainstorm Force--Spectra | Improper Restriction of Excessive Authentication Attempts vulnerability in Brainstorm Force Spectra allows Functionality Bypass.This issue affects Spectra: from n/a through 2.3.0. | 2024-06-03 | | |
| Brainstorm Force--Spectra | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in Brainstorm Force Spectra allows Code Injection.This issue affects Spectra: from n/a through 2.3.0. | 2024-06-03 | | |
| Brainstorm Force--Spectra | Improper Neutralization of Special Elements in Output Used by a Downstream Component ('Injection') vulnerability in Brainstorm Force Spectra allows Content Spoofing, Phishing.This issue affects Spectra: from n/a through 2.3.0. | 2024-06-03 | | |
| brainstormforce--Cards for Beaver Builder | The Cards for Beaver Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Cards widget in all versions up to, and including, 1.1.3 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-08 | | |
| brainstormforce--SureTriggers Connect All Your Plugins, Apps, Tools & Automate Everything! | The SureTriggers - Connect All Your Plugins, Apps, Tools & Automate Everything! plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Trigger Link shortcode in all versions up to, and including, 1.0.47 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-04 | | |
| brizy -- brizy-page_builder | The Brizy - Page Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the form name values in all versions up to, and including, 2.4.43 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| brizy -- brizy-page_builder | The Brizy - Page Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Custom Attributes for blocks in all versions up to, and including, 2.4.43 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers with contributor-level and above permissions to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| brizy -- brizy-page_builder | The Brizy - Page Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via post content in all versions up to, and including, 2.4.41 due to insufficient input sanitization performed only on the client side and insufficient output escaping. This makes it possible for authenticated attackers, with contributor access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| brizy -- brizy-page_builder | The Brizy - Page Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'Link To' field of multiple widgets in all versions up to, and including, 2.4.43 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| Bryan Hadaway--Site Favicon | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Bryan Hadaway Site Favicon allows Stored XSS.This issue affects Site Favicon: from n/a through 0.2. | 2024-06-03 | | |
| Canonical Ltd.--Netplan | netplan leaks the private key of wireguard to local users. A security fix will be released soon. | 2024-06-07 | | |
| cartpauj--Cartpauj Register Captcha | : Improper Control of Interaction Frequency vulnerability in cartpauj Cartpauj Register Captcha allows Functionality Misuse.This issue affects Cartpauj Register Captcha: from n/a through 1.0.02. | 2024-06-04 | | |
| CeiKay--Tooltip CK | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in CeiKay Tooltip CK tooltip-ck allows Stored XSS.This issue affects Tooltip CK: from n/a through 2.2.15. | 2024-06-08 | | |
| Ciprian Popescu--Block for Font Awesome | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Ciprian Popescu Block for Font Awesome allows Stored XSS.This issue affects Block for Font Awesome: from n/a through 1.4.4. | 2024-06-08 | | |
| Cisco--Cisco Unified Contact Center Enterprise | A vulnerability in the web-based management interface of Cisco Finesse could allow an unauthenticated, remote attacker to conduct a stored XSS attack by exploiting an RFI vulnerability. This vulnerability is due to insufficient validation of user-supplied input for specific HTTP requests that are sent to an affected device. An attacker could exploit this vulnerability by persuading a user to click a crafted link. A successful exploit could allow the attacker to execute arbitrary script code in the context of the affected interface or access sensitive information on the affected device. | 2024-06-05 | | |
| claudiosanches--Claudio Sanches Checkout Cielo for WooCommerce | The Claudio Sanches - Checkout Cielo for WooCommerce plugin for WordPress is vulnerable to unauthorized modification of data due to insufficient payment validation in the update_order_status() function in all versions up to, and including, 1.1.0. This makes it possible for unauthenticated attackers to update the status of orders to paid bypassing payment. | 2024-06-04 | | |
| Codection--Import and export users and customers | Missing Authorization vulnerability in Codection Import and export users and customers.This issue affects Import and export users and customers: from n/a through 1.24.6. | 2024-06-08 | | |
| codeless -- cowidgets_-_elementor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Codeless Cowidgets - Elementor Addons allows Stored XSS.This issue affects Cowidgets - Elementor Addons: from n/a through 1.1.1. | 2024-06-04 | | |
| codelessthemes--Cowidgets Elementor Addons | The Cowidgets - Elementor Addons plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'heading_tag' parameter in all versions up to, and including, 1.1.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-04 | | |
| codename065--Download Manager | The Download Manager plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's 'wpdm_modal_login_form' shortcode in all versions up to, and including, 3.2.93 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| CodePeople, paypaldev--CP Contact Form with Paypal | Missing Authorization vulnerability in CodePeople, paypaldev CP Contact Form with Paypal allows Functionality Misuse.This issue affects CP Contact Form with Paypal: from n/a through 1.3.34. | 2024-06-03 | | |
| CodePeople--Calculated Fields Form | Missing Authorization vulnerability in CodePeople Calculated Fields Form allows Functionality Misuse.This issue affects Calculated Fields Form: from n/a through 1.1.120. | 2024-06-03 | | |
| CodePeople--Contact Form Email | Improper Restriction of Excessive Authentication Attempts vulnerability in CodePeople Contact Form Email allows Functionality Bypass.This issue affects Contact Form Email: from n/a through 1.3.41. | 2024-06-04 | | |
| CodePeople--Contact Form Email | Missing Authorization vulnerability in CodePeople Contact Form Email allows Functionality Misuse.This issue affects Contact Form Email: from n/a through 1.3.31. | 2024-06-04 | | |
| CodePeople--CP Multi View Event Calendar | Missing Authorization vulnerability in CodePeople CP Multi View Event Calendar allows Functionality Misuse.This issue affects CP Multi View Event Calendar: from n/a through 1.4.10. | 2024-06-03 | | |
| CodePeople--Search in Place | Missing Authorization vulnerability in CodePeople Search in Place allows Functionality Misuse.This issue affects Search in Place: from n/a through 1.0.104. | 2024-06-03 | | |
| Creative Motion, Will Bontrager Software, LLC--Woody ad snippets | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Creative Motion, Will Bontrager Software, LLC Woody ad snippets allows Stored XSS.This issue affects Woody ad snippets: from n/a through 2.4.10. | 2024-06-08 | | |
| CreativeThemes--Blocksy Companion | Server-Side Request Forgery (SSRF) vulnerability in CreativeThemes Blocksy Companion.This issue affects Blocksy Companion: from n/a through 2.0.42. | 2024-06-03 | | |
| creativethemeshq--Blocksy | The Blocksy theme for WordPress is vulnerable to Reflected Cross-Site Scripting via the custom_url parameter in all versions up to, and including, 2.0.50 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-05 | | |
| CRM Perks.--Integration for Contact Form 7 and Constant Contact | Cross-Site Request Forgery (CSRF) vulnerability in CRM Perks. Integration for Contact Form 7 and Constant Contact.This issue affects Integration for Contact Form 7 and Constant Contact: from n/a through 1.1.5. | 2024-06-03 | | |
| cyberchimps--Responsive Addons Starter Templates, Advanced Features and Customizer Settings for Responsive Theme. | The Responsive Addons - Starter Templates, Advanced Features and Customizer Settings for Responsive Theme. plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's file uploader in all versions up to, and including, 3.0.5 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Author-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| CyberChimps--Responsive | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in CyberChimps Responsive allows Stored XSS.This issue affects Responsive: from n/a through 5.0.3. | 2024-06-04 | | |
| cyclonetheme--Elegant Blocks | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in cyclonetheme Elegant Blocks allows Stored XSS.This issue affects Elegant Blocks: from n/a through 1.7. | 2024-06-03 | | |
| dain--snappy | iq80 Snappy is a compression/decompression library. When uncompressing certain data, Snappy tries to read outside the bounds of the given byte arrays. Because Snappy uses the JDK class `sun.misc.Unsafe` to speed up memory access, no additional bounds checks are performed and this has similar security consequences as out-of-bounds access in C or C++, namely it can lead to non-deterministic behavior or crash the JVM. iq80 Snappy is not actively maintained anymore. As quick fix users can upgrade to version 0.5. | 2024-06-03 | | |
| Devnath verma--WP Captcha | Improper Restriction of Excessive Authentication Attempts vulnerability in Devnath verma WP Captcha allows Functionality Bypass.This issue affects WP Captcha: from n/a through 2.0.0. | 2024-06-04 | | |
| dextorlobo--Custom Dash | The Custom Dash plugin for WordPress is vulnerable to Stored Cross-Site Scripting via admin settings in all versions up to, and including, 1.0.2 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with administrator-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. This only affects multi-site installations and installations where unfiltered_html has been disabled. | 2024-06-06 | | |
| dfactory--Download Attachments | The Download Attachments plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's 'download-attachments' shortcode in all versions up to, and including, 1.3 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-04 | | |
| Dulldusk--PHP File Manager | Vulnerability in Dulldusk's PHP File Manager affecting version 1.7.8. This vulnerability consists of an XSS through the fm_current_dir parameter of index.php. An attacker could send a specially crafted JavaScript payload to an authenticated user and partially hijack their browser session. | 2024-06-06 | | |
| duongancol--Boostify Header Footer Builder for Elementor | The Boostify Header Footer Builder for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'size' parameter in all versions up to, and including, 1.3.2 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| duongancol--Boostify Header Footer Builder for Elementor | The Boostify Header Footer Builder for Elementor plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the create_bhf_post function in all versions up to, and including, 1.3.3. This makes it possible for authenticated attackers, with subscriber-level access and above, to create pages or posts with arbitrary content. | 2024-06-06 | | |
| El tiempo--Weather Widget Pro | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in El tiempo Weather Widget Pro allows Stored XSS.This issue affects Weather Widget Pro: from n/a through 1.1.40. | 2024-06-08 | | |
| elearningfreak -- insert_or_embed_articulate_content | The Insert or Embed Articulate Content into WordPress plugin through 4.3000000023 lacks validation of URLs when adding iframes, allowing attackers to inject an iFrame in the page and thus load arbitrary content from any page. | 2024-06-04 | | |
| EmailGPT--EmailGPT | The EmailGPT service contains a prompt injection vulnerability. The service uses an API service that allows a malicious user to inject a direct prompt and take over the service logic. Attackers can exploit the issue by forcing the AI service to leak the standard hard-coded system prompts and/or execute unwanted prompts. When engaging with EmailGPT by submitting a malicious prompt that requests harmful information, the system will respond by providing the requested data. This vulnerability can be exploited by any individual with access to the service. | 2024-06-05 | | |
| Enea Overclokk--Stellissimo Text Box | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Enea Overclokk Stellissimo Text Box allows Stored XSS.This issue affects Stellissimo Text Box: from n/a through 1.1.4. | 2024-06-08 | | |
| envothemes--Envo Extra | The Envo Extra plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'button_css_id' parameter within the Button widget in all versions up to, and including, 1.8.23 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| envoyproxy--envoy | Envoy is a cloud-native, open source edge and service proxy. A theoretical request smuggling vulnerability exists through Envoy if a server can be tricked into adding an upgrade header into a response. Per RFC https://www.rfc-editor.org/rfc/rfc7230#section-6.7 a server sends 101 when switching protocols. Envoy incorrectly accepts a 200 response from a server when requesting a protocol upgrade, but 200 does not indicate protocol switch. This opens up the possibility of request smuggling through Envoy if the server can be tricked into adding the upgrade header to the response. | 2024-06-04 | | |
| envoyproxy--envoy | Envoy is a cloud-native, open source edge and service proxy. A crash was observed in `EnvoyQuicServerStream::OnInitialHeadersComplete()` with following call stack. It is a use-after-free caused by QUICHE continuing push request headers after `StopReading()` being called on the stream. As after `StopReading()`, the HCM's `ActiveStream` might have already be destroyed and any up calls from QUICHE could potentially cause use after free. | 2024-06-04 | | |
| envoyproxy--envoy | Envoy is a cloud-native, open source edge and service proxy. There is a crash at `QuicheDataReader::PeekVarInt62Length()`. It is caused by integer underflow in the `QuicStreamSequencerBuffer::PeekRegion()` implementation. | 2024-06-04 | | |
| envoyproxy--envoy | Envoy is a cloud-native, open source edge and service proxy. There is a use-after-free in `HttpConnectionManager` (HCM) with `EnvoyQuicServerStream` that can crash Envoy. An attacker can exploit this vulnerability by sending a request without `FIN`, then a `RESET_STREAM` frame, and then after receiving the response, closing the connection. | 2024-06-04 | | |
| envoyproxy--envoy | Envoy is a cloud-native, open source edge and service proxy. Envoy exposed an out-of-memory (OOM) vector from the mirror response, since async HTTP client will buffer the response with an unbounded buffer. | 2024-06-04 | | |
| Essential Addons--Essential Addons for Elementor Pro | The Essential Addons for Elementor Pro plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'eael_lightbox_open_btn_icon' parameter within the Lightbox & Modal widget in all versions up to, and including, 5.8.15 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| evmos--evmos | Evmos is the Ethereum Virtual Machine (EVM) Hub on the Cosmos Network. Users are able to delegate tokens that have not yet been vested. This affects employees and grantees who have funds managed via `ClawbackVestingAccount`. This affects 18.1.0 and earlier. | 2024-06-06 | | |
| extendthemes--Colibri Page Builder | The Colibri Page Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's colibri_video_player shortcode in all versions up to, and including, 1.0.276 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| extendthemes--Colibri Page Builder | The Colibri Page Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's shortcode(s) in all versions up to, and including, 1.0.276 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| Fahad Mahmood--WP Docs | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Fahad Mahmood WP Docs allows Stored XSS.This issue affects WP Docs: from n/a through 2.1.3. | 2024-06-08 | | |
| Fastly--Fastly | Missing Authorization vulnerability in Fastly.This issue affects Fastly: from n/a through 1.2.25. | 2024-06-03 | | |
| FeedbackWP--Rate my Post WP Rating System | Authentication Bypass by Spoofing vulnerability in FeedbackWP Rate my Post - WP Rating System allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Rate my Post - WP Rating System: from n/a through 3.4.2. | 2024-06-04 | | |
| flowdee--EasyAzon Amazon Associates Affiliate Plugin | The EasyAzon - Amazon Associates Affiliate Plugin plugin for WordPress is vulnerable to Reflected Cross-Site Scripting via the 'easyazon-cloaking-locale' parameter in all versions up to, and including, 5.1.0 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-06 | | |
| Forge12 Interactive GmbH--Captcha/Honeypot for Contact Form 7 | Improper Restriction of Excessive Authentication Attempts vulnerability in Forge12 Interactive GmbH Captcha/Honeypot for Contact Form 7 allows Functionality Bypass.This issue affects Captcha/Honeypot for Contact Form 7: from n/a through 1.11.3. | 2024-06-04 | | |
| Fortinet--FortiAuthenticator | A URL redirection to untrusted site ('open redirect') in Fortinet FortiAuthenticator version 6.6.0, version 6.5.3 and below, version 6.4.9 and below may allow an attacker to to redirect users to an arbitrary website via a crafted URL. | 2024-06-03 | | |
| Fortinet--FortiPortal | A client-side enforcement of server-side security in Fortinet FortiPortal version 6.0.0 through 6.0.14 allows attacker to improper access control via crafted HTTP requests. | 2024-06-03 | | |
| Fortinet--FortiSOAR | An improper removal of sensitive information before storage or transfer vulnerability [CWE-212] in FortiSOAR version 7.3.0, version 7.2.2 and below, version 7.0.3 and below may allow an authenticated low privileged user to read Connector passwords in plain-text via HTTP responses. | 2024-06-03 | | |
| Fortinet--FortiWebManager | An improper authorization in Fortinet FortiWebManager version 7.2.0 and 7.0.0 through 7.0.4 and 6.3.0 and 6.2.3 through 6.2.4 and 6.0.2 allows attacker to execute unauthorized code or commands via HTTP requests or CLI. | 2024-06-05 | | |
| Fortinet--FortiWeb | An exposure of sensitive information to an unauthorized actor vulnerability [CWE-200] in FortiWeb version 7.4.0, version 7.2.4 and below, version 7.0.8 and below, 6.3 all versions may allow an authenticated attacker to read password hashes of other administrators via CLI commands. | 2024-06-03 | | |
| Fortinet--FortiWeb | Multiple improper authorization vulnerabilities [CWE-285] in FortiWeb version 7.4.2 and below, version 7.2.7 and below, version 7.0.10 and below, version 6.4.3 and below, version 6.3.23 and below may allow an authenticated attacker to perform unauthorized ADOM operations via crafted requests. | 2024-06-03 | | |
| freephp-1--Nafeza Prayer Time | The Nafeza Prayer Time plugin for WordPress is vulnerable to Stored Cross-Site Scripting via admin settings in all versions up to, and including, 1.2.9 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with administrator-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. This only affects multi-site installations and installations where unfiltered_html has been disabled. | 2024-06-04 | | |
| g5theme--Essential Real Estate | The Essential Real Estate plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's 'ere_property_map' shortcode in all versions up to, and including, 4.4.2 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-04 | | |
| g5theme--Essential Real Estate | The Essential Real Estate plugin for WordPress is vulnerable to unauthorized loss of data due to insufficient validation on the remove_property_attachment_ajax() function in all versions up to, and including, 4.4.2. This makes it possible for authenticated attackers, with subscriber-level access and above, to delete arbitrary attachments. | 2024-06-04 | | |
| GeneratePress--GP Premium | The GP Premium plugin for WordPress is vulnerable to Reflected Cross-Site Scripting via the message parameter in all versions up to, and including, 2.4.0 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that execute if they can successfully trick a user into performing an action such as clicking on a link. | 2024-06-05 | | |
| getbrave -- brave | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Brave Brave Popup Builder allows Stored XSS.This issue affects Brave Popup Builder: from n/a through 0.6.8. | 2024-06-04 | | |
| getformwork--formwork | Formwork is a flat file-based Content Management System (CMS). An attackers (requires administrator privilege) to execute arbitrary web scripts by modifying site options via /panel/options/site. This type of attack is suitable for persistence, affecting visitors across all pages (except the dashboard). This vulnerability is fixed in 1.13.1. | 2024-06-07 | | |
| gn_themes--WP Shortcodes Plugin Shortcodes Ultimate | The WP Shortcodes Plugin - Shortcodes Ultimate plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's su_lightbox shortcode in all versions up to, and including, 7.1.6 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| GregRoss--Just Writing Statistics | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in GregRoss Just Writing Statistics allows Stored XSS.This issue affects Just Writing Statistics: from n/a through 4.5. | 2024-06-03 | | |
| gVectors Team--wpDiscuz | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in gVectors Team wpDiscuz allows Stored XSS.This issue affects wpDiscuz: from n/a through 7.6.18. | 2024-06-08 | | |
| gVectors Team--wpDiscuz | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in gVectors Team wpDiscuz allows Code Injection.This issue affects wpDiscuz: from n/a through 7.6.10. | 2024-06-04 | | |
| Hans van Eijsden,niwreg--ImageMagick Sharpen Resized Images | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Hans van Eijsden,niwreg ImageMagick Sharpen Resized Images allows Stored XSS.This issue affects ImageMagick Sharpen Resized Images: from n/a through 1.1.7. | 2024-06-03 | | |
| HasThemes--HT Feed | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in HasThemes HT Feed allows Stored XSS.This issue affects HT Feed: from n/a through 1.2.8. | 2024-06-08 | | |
| HasThemes--ShopLentor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in HasThemes ShopLentor allows Stored XSS.This issue affects ShopLentor: from n/a through 2.8.7. | 2024-06-03 | | |
| HCL Software--Connections Docs | HCL Connections Docs is vulnerable to a cross-site scripting attack where an attacker may leverage this issue to execute arbitrary code. This may lead to credentials disclosure and possibly launch additional attacks. | 2024-06-08 | | |
| horearadu--Materialis Companion | The Materialis Companion plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's materialis_contact_form shortcode in all versions up to, and including, 1.3.41 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| horearadu--One Page Express Companion | The One Page Express Companion plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's one_page_express_contact_form shortcode in all versions up to, and including, 1.6.37 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| ibabar--WordPress prettyPhoto | The WordPress prettyPhoto plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' parameter in all versions up to, and including, 1.2.3 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| IBM--i | IBM i 7.2, 7.3, 7.4, and 7.5 Service Tools Server (SST) is vulnerable to SST user enumeration by a remote attacker. This vulnerability can be used by a malicious actor to gather information about SST users that can be targeted in further attacks. IBM X-Force ID: 287538. | 2024-06-07 | | |
| IBM--System Storage DS8900F | IBM System Storage DS8900F 89.22.19.0, 89.30.68.0, 89.32.40.0, 89.33.48.0, 89.40.83.0, and 89.40.93.0 could allow a remote user to create an LDAP connection with a valid username and empty password to establish an anonymous connection. IBM X-Force ID: 279518. | 2024-06-06 | | |
| Icegram--Icegram | Missing Authorization vulnerability in Icegram.This issue affects Icegram: from n/a through 3.1.21. | 2024-06-08 | | |
| IdoPesok--zsa | zsa is a library for building typesafe server actions in Next.js. All users are impacted. The zsa application transfers the parse error stack from the server to the client in production build mode. This can potentially reveal sensitive information about the server environment, such as the machine username and directory paths. An attacker could exploit this vulnerability to gain unauthorized access to sensitive server information. This information could be used to plan further attacks or gain a deeper understanding of the server infrastructure. This has been patched on `0.3.3`. | 2024-06-07 | | |
| ILLID--Advanced Woo Labels | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in ILLID Advanced Woo Labels allows Cross-Site Scripting (XSS).This issue affects Advanced Woo Labels: from n/a through 1.93. | 2024-06-08 | | |
| IP2Location--Download IP2Location Country Blocker | Authentication Bypass by Spoofing vulnerability in IP2Location Download IP2Location Country Blocker allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Download IP2Location Country Blocker: from n/a through 2.29.1. | 2024-06-04 | | |
| ishanverma--Authorize.net Payment Gateway For WooCommerce | The Authorize.net Payment Gateway For WooCommerce plugin for WordPress is vulnerable to payment bypass in all versions up to, and including, 8.0. This is due to the plugin not properly verifying the authenticity of the request that updates a orders payment status. This makes it possible for unauthenticated attackers to update order payment statuses to paid bypassing any payment. | 2024-06-04 | | |
| itsourcecode--Bakery Online Ordering System | A vulnerability was found in itsourcecode Bakery Online Ordering System 1.0. It has been declared as critical. Affected by this vulnerability is an unknown functionality of the file index.php. The manipulation of the argument txtsearch leads to sql injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-267091. | 2024-06-04 | | |
| itsourcecode--Bakery Online Ordering System | A vulnerability was found in itsourcecode Bakery Online Ordering System 1.0. It has been rated as critical. Affected by this issue is some unknown functionality of the file report/index.php. The manipulation of the argument procduct leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-267092. | 2024-06-05 | | |
| itsourcecode--Online Discussion Forum | A vulnerability classified as critical has been found in itsourcecode Online Discussion Forum 1.0. Affected is an unknown function of the file /members/poster.php. The manipulation of the argument image leads to unrestricted upload. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-267408. | 2024-06-07 | | |
| J.N. Breetvelt a.k.a. OpaJaap--WP Photo Album Plus | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in J.N. Breetvelt a.K.A. OpaJaap WP Photo Album Plus allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects WP Photo Album Plus: from n/a through 8.5.02.005. | 2024-06-04 | | |
| j0hnsmith--Testimonials Widget | The Testimonials Widget plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's testimonials shortcode in all versions up to, and including, 4.0.4 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| Jewel Theme--Master Addons for Elementor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Jewel Theme Master Addons for Elementor allows Stored XSS.This issue affects Master Addons for Elementor: from n/a through 2.0.5.9. | 2024-06-08 | | |
| Jewel Theme--Master Addons for Elementor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Jewel Theme Master Addons for Elementor allows Stored XSS.This issue affects Master Addons for Elementor: from n/a through 2.0.6.0. | 2024-06-08 | | |
| johnnash1975--Easy Social Like Box Popup Sidebar Widget | The Easy Social Like Box - Popup - Sidebar Widget plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's 'cardoza_facebook_like_box' shortcode in all versions up to, and including, 4.0 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| JumpDEMAND Inc.--ActiveDEMAND | Cross-Site Request Forgery (CSRF) vulnerability in JumpDEMAND Inc. ActiveDEMAND.This issue affects ActiveDEMAND: from n/a through 0.2.43. | 2024-06-03 | | |
| Kharim Tomlinson--WP Next Post Navi | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Kharim Tomlinson WP Next Post Navi allows Stored XSS.This issue affects WP Next Post Navi: from n/a through 1.8.3. | 2024-06-03 | | |
| Kognetiks--Kognetiks Chatbot for WordPress | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Kognetiks Kognetiks Chatbot for WordPress allows Stored XSS.This issue affects Kognetiks Chatbot for WordPress: from n/a through 1.9.8. | 2024-06-08 | | |
| LabVantage--LIMS | A vulnerability classified as critical was found in LabVantage LIMS 2017. This vulnerability affects unknown code of the file /labvantage/rc?command=page&page=SampleList&_iframename=list of the component POST Request Handler. The manipulation of the argument param1 leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. VDB-267454 is the identifier assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-08 | | |
| Lester GaMerZ Chan--WP-PostRatings | Improper Control of Interaction Frequency vulnerability in Lester 'GaMerZ' Chan WP-PostRatings allows Functionality Misuse.This issue affects WP-PostRatings: from n/a through 1.91. | 2024-06-04 | | |
| litonice13--Master Addons Free Widgets, Hover Effects, Toggle, Conditions, Animations for Elementor | The Master Addons - Free Widgets, Hover Effects, Toggle, Conditions, Animations for Elementor plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the 'ma-template' REST API route in all versions up to, and including, 2.0.6.1. This makes it possible for unauthenticated attackers to create or modify existing Master Addons templates or make settings modifications related to these templates. | 2024-06-07 | | |
| Lukman Nakib--Debug Log Manger Tool | Insertion of Sensitive Information into Log File vulnerability in Lukman Nakib Debug Log - Manger Tool.This issue affects Debug Log - Manger Tool: from n/a through 1.4.5. | 2024-06-03 | | |
| MagniGenie--RestroPress | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in MagniGenie RestroPress allows Stored XSS.This issue affects RestroPress: from n/a through 3.1.2.1. | 2024-06-08 | | |
| Marketing Fire, LLC--Widget Options - Extended | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in Marketing Fire, LLC Widget Options - Extended.This issue affects Widget Options - Extended: from n/a through 5.1.0. | 2024-06-08 | | |
| melapress--Admin Notices Manager | The Admin Notices Manager plugin for WordPress is vulnerable to unauthorized access of data due to a missing capability check on the handle_ajax_call() function in all versions up to, and including, 1.4.0. This makes it possible for authenticated attackers, with subscriber-level access and above, to retrieve a list of registered user emails. | 2024-06-04 | | |
| Menno Luitjes--Foyer | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in Menno Luitjes Foyer allows Code Injection.This issue affects Foyer: from n/a through 1.7.5. | 2024-06-04 | | |
| Mervin Praison--Praison SEO WordPress | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Mervin Praison Praison SEO WordPress allows Stored XSS.This issue affects Praison SEO WordPress: from n/a through 4.0.15. | 2024-06-03 | | |
| metagauss--ProfileGrid User Profiles, Groups and Communities | The ProfileGrid - User Profiles, Groups and Communities plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the pm_dismissible_notice and pm_wizard_update_group_icon functions in all versions up to, and including, 5.8.6. This makes it possible for authenticated attackers, with Subscriber-level access and above, to change arbitrary options to the value '1' or change group icons. | 2024-06-05 | | |
| Metagauss--RegistrationMagic | Authentication Bypass by Spoofing vulnerability in Metagauss RegistrationMagic allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects RegistrationMagic: from n/a through 5.2.5.0. | 2024-06-04 | | |
| Metagauss--RegistrationMagic | Improper Control of Interaction Frequency vulnerability in Metagauss RegistrationMagic allows Functionality Misuse.This issue affects RegistrationMagic: from n/a through 5.2.5.0. | 2024-06-04 | | |
| miniorange--Malware Scanner | Authentication Bypass by Spoofing vulnerability in miniorange Malware Scanner allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Malware Scanner: from n/a through 4.7.1. | 2024-06-04 | | |
| MongoDB Inc--PyMongo | An out-of-bounds read in the 'bson' module of PyMongo 4.6.2 or earlier allows deserialization of malformed BSON provided by a Server to raise an exception which may contain arbitrary application memory. | 2024-06-05 | | |
| moveaddons--Move Addons for Elementor | Missing Authorization vulnerability in moveaddons Move Addons for Elementor.This issue affects Move Addons for Elementor: from n/a through 1.2.9. | 2024-06-04 | | |
| mpntod--Rotating Tweets (Twitter widget and shortcode) | The Rotating Tweets (Twitter widget and shortcode) plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's' 'rotatingtweets' in all versions up to, and including, 1.9.10 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| N/A--Church Admin | Server-Side Request Forgery (SSRF) vulnerability in Church Admin.This issue affects Church Admin: from n/a through 4.3.6. | 2024-06-03 | | |
| N/A--KiviCare | Authorization Bypass Through User-Controlled Key vulnerability in KiviCare.This issue affects KiviCare: from n/a through 3.6.2. | 2024-06-08 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_config_get_nl_params(), there is no input validation check on hal_req->num_config_discovery_attr coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_followup_get_nl_params(), there is no input validation check on hal_req->service_specific_info_len coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_config_get_nl_params(), there is no input validation check on disc_attr->infrastructure_ssid_len coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_config_get_nl_params(), there is no input validation check on disc_attr->mesh_id_len coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_publish_get_nl_params(), there is no input validation check on hal_req->service_specific_info_len coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_followup_get_nl_params(), there is no input validation check on hal_req->sdea_service_specific_info_len coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_subscribe_get_nl_params(), there is no input validation check on hal_req->rx_match_filter_len coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_get_security_info_nl(), there is no input validation check on sec_info->key_info.body.pmk_info.pmk_len coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_send_action_frame_cert(), there is no input validation check on len coming from userspace, which can lead to a heap over-read. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_nan_subscribe_get_nl_params(), there is no input validation check on hal_req->num_intf_addr_present coming from userspace, which can lead to a heap overwrite. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_set_delayed_wakeup_type(), there is no input validation check on a length of ioctl_args->args[i] coming from userspace, which can lead to a heap over-read. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_send_action_frame_ut(), there is no input validation check on len coming from userspace, which can lead to a heap over-read. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor Exynos 980, Exynos 850, Exynos 1280, Exynos 1380, and Exynos 1330. In the function slsi_send_action_frame(), there is no input validation check on len coming from userspace, which can lead to a heap over-read. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor EExynos 2200, Exynos 1480, Exynos 2400. It lacks a check for the validation of native handles, which can result in an Out-of-Bounds Write. | 2024-06-07 | | |
| n/a--n/a | Ariane Allegro Scenario Player through 2024-03-05, when Ariane Duo kiosk mode is used, allows physically proximate attackers to obtain sensitive information (such as hotel invoice content with PII), and potentially create unauthorized room keys, by entering a guest-search quote character and then accessing the underlying Windows OS. | 2024-06-06 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor, Automotive Processor, Wearable Processor, and Modem Exynos 980, 990, 850, 1080, 2100, 2200, 1280, 1380, 1330, 9110, W920, Exynos Modem 5123, Exynos Modem 5300, and Exynos Auto T5123. The baseband software does not properly check format types specified by the RRC. This can lead to a lack of encryption. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor, Wearable Processor, Automotive Processor, and Modem Exynos 980, 990, 850, 1080, 2100, 2200, 1280, 1380, 1330, 2400, 9110, W920, W930, Modem 5123, Modem 5300, and Auto T5123. The baseband software does not properly check states specified by the RRC (Radio Resource Control) module. This can lead to disclosure of sensitive information. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor, Wearable Processor, Automotive Processor, and Modem Exynos 980, 990, 850, 1080, 2100, 2200, 1280, 1380, 1330, 2400, 9110, W920, W930, Modem 5123, Modem 5300, and Auto T5123. The baseband software does not properly check states specified by the RRC (Radio Resource Control) Reconfiguration message. This can lead to disclosure of sensitive information. | 2024-06-04 | | |
| N/A--RT Easy Builder Advanced addons for Elementor | Missing Authorization vulnerability in RT Easy Builder - Advanced addons for Elementor.This issue affects RT Easy Builder - Advanced addons for Elementor: from n/a through 2.0. | 2024-06-04 | | |
| nalam-1--Magical Addons For Elementor ( Header Footer Builder, Free Elementor Widgets, Elementor Templates Library ) | The Magical Addons For Elementor ( Header Footer Builder, Free Elementor Widgets, Elementor Templates Library ) plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the '_id' parameter in all versions up to, and including, 1.1.39 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| nayrathemes--Clever Fox | The Clever Fox plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's info box block in all versions up to, and including, 25.2.0 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers with contributor-level and above permissions to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| nayrathemes--Clever Fox | The Clever Fox - One Click Website Importer by Nayra Themes plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the 'clever-fox-activate-theme' function in all versions up to, and including, 25.2.0. This makes it possible for authenticated attackers, with subscriber access and above, to modify the active theme, including to an invalid value which can take down the site. | 2024-06-07 | | |
| ndijkstra--Mollie Forms | The Mollie Forms plugin for WordPress is vulnerable to Cross-Site Request Forgery in all versions up to, and including, 2.6.13. This is due to missing or incorrect nonce validation on the duplicateForm() function. This makes it possible for unauthenticated attackers to duplicate forms via a forged request granted they can trick a site administrator into performing an action such as clicking on a link. | 2024-06-05 | | |
| Netentsec--NS-ASG Application Security Gateway | A vulnerability was found in Netentsec NS-ASG Application Security Gateway 6.3. It has been classified as critical. This affects an unknown part of the file /admin/config_MT.php?action=delete. The manipulation of the argument Mid leads to sql injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-266847. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-03 | | |
| Netentsec--NS-ASG Application Security Gateway | A vulnerability was found in Netentsec NS-ASG Application Security Gateway 6.3. It has been declared as critical. This vulnerability affects unknown code of the file /protocol/iscuser/uploadiscuser.php of the component JSON Content Handler. The manipulation of the argument messagecontent leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-266848. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-03 | | |
| netty--netty-incubator-codec-ohttp | netty-incubator-codec-ohttp is the OHTTP implementation for netty. BoringSSLAEADContext keeps track of how many OHTTP responses have been sent and uses this sequence number to calculate the appropriate nonce to use with the encryption algorithm. Unfortunately, two separate errors combine which would allow an attacker to cause the sequence number to overflow and thus the nonce to repeat. | 2024-06-04 | | |
| Nitin Rathod--WP Forms Puzzle Captcha | Improper Restriction of Excessive Authentication Attempts vulnerability in Nitin Rathod WP Forms Puzzle Captcha allows Functionality Bypass.This issue affects WP Forms Puzzle Captcha: from n/a through 4.1. | 2024-06-04 | | |
| oslabs-beta--SkyScraper | SkyScrape is a GUI Dashboard for AWS Infrastructure and Managing Resources and Usage Costs. SkyScrape's API requests are currently unsecured HTTP requests, leading to potential vulnerabilities for the user's temporary credentials and data. This affects version 1.0.0. | 2024-06-07 | | |
| OTRS AG--OTRS | The file upload feature in OTRS and ((OTRS)) Community Edition has a path traversal vulnerability. This issue permits authenticated agents or customer users to upload potentially harmful files to directories accessible by the web server, potentially leading to the execution of local code like Perl scripts. This issue affects OTRS: from 7.0.X through 7.0.49, 8.0.X, 2023.X, from 2024.X through 2024.3.2; ((OTRS)) Community Edition: from 6.0.1 through 6.0.34. | 2024-06-06 | | |
| pandaboxwp--WP jQuery Lightbox | The WP jQuery Lightbox plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'title' attribute in all versions up to, and including, 1.5.4 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| pdfcrowd -- save_as_pdf_plugin | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Pdfcrowd Save as PDF plugin by Pdfcrowd allows Stored XSS.This issue affects Save as PDF plugin by Pdfcrowd: from n/a through 3.2.3. | 2024-06-04 | | |
| Peregrine themes--Bloglo | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Peregrine themes Bloglo allows Stored XSS.This issue affects Bloglo: from n/a through 1.1.3. | 2024-06-08 | | |
| pickplugins--Gutenberg Blocks, Page Builder ComboBlocks | The Post Grid, Form Maker, Popup Maker, WooCommerce Blocks, Post Blocks, Post Carousel - Combo Blocks plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'tag' attribute in blocks in all versions up to, and including, 2.2.80 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| pickplugins--Gutenberg Blocks, Page Builder ComboBlocks | The Post Grid, Form Maker, Popup Maker, WooCommerce Blocks, Post Blocks, Post Carousel - Combo Blocks plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'class' attribute of the menu-wrap-item block in all versions up to, and including, 2.2.80 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| PickPlugins--Tabs & Accordion | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in PickPlugins Tabs & Accordion allows Code Injection.This issue affects Tabs & Accordion: from n/a through 1.3.10. | 2024-06-04 | | |
| PINPOINT.WORLD--Pinpoint Booking System | External Control of Assumed-Immutable Web Parameter vulnerability in PINPOINT.WORLD Pinpoint Booking System allows Functionality Misuse.This issue affects Pinpoint Booking System: from n/a through 2.9.9.3.4. | 2024-06-04 | | |
| Plechev Andrey--WP-Recall | Cross-Site Request Forgery (CSRF) vulnerability in Plechev Andrey WP-Recall.This issue affects WP-Recall: from n/a through 16.26.6. | 2024-06-08 | | |
| Pluggabl LLC--Booster Elite for WooCommerce | Improper Authentication vulnerability in Pluggabl LLC Booster Elite for WooCommerce allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Booster Elite for WooCommerce: from n/a before 7.1.3. | 2024-06-04 | | |
| Pluggabl LLC--Booster for WooCommerce | Improper Authentication vulnerability in Pluggabl LLC Booster for WooCommerce allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Booster for WooCommerce: from n/a through 7.1.2. | 2024-06-04 | | |
| pluginever--WP Content Pilot Autoblogging & Affiliate Marketing Plugin | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in pluginever WP Content Pilot - Autoblogging & Affiliate Marketing Plugin allows Code Injection.This issue affects WP Content Pilot - Autoblogging & Affiliate Marketing Plugin: from n/a through 1.3.3. | 2024-06-04 | | |
| pluginkollektiv--Antispam Bee | Authentication Bypass by Spoofing vulnerability in pluginkollektiv Antispam Bee allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Antispam Bee: from n/a through 2.11.3. | 2024-06-04 | | |
| Podlove--Podlove Web Player | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in Podlove Podlove Web Player.This issue affects Podlove Web Player: from n/a through 5.7.3. | 2024-06-08 | | |
| Popup Maker--Popup Maker WP | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Popup Maker Popup Maker WP allows Stored XSS.This issue affects Popup Maker WP: from n/a through 1.2.8. | 2024-06-03 | | |
| POSIMYTH--The Plus Addons for Elementor Page Builder Lite | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in POSIMYTH The Plus Addons for Elementor Page Builder Lite allows Stored XSS.This issue affects The Plus Addons for Elementor Page Builder Lite: from n/a through 5.5.4. | 2024-06-08 | | |
| PropertyHive--PropertyHive | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in PropertyHive allows Stored XSS.This issue affects PropertyHive: from n/a through 2.0.13. | 2024-06-08 | | |
| ptz0n--Google CSE | The Google CSE plugin for WordPress is vulnerable to Stored Cross-Site Scripting via admin settings in all versions up to, and including, 1.0.7 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with administrator-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. This only affects multi-site installations and installations where unfiltered_html has been disabled. | 2024-06-06 | | |
| Pure Chat by Ruby--Pure Chat | Cross-Site Request Forgery (CSRF) vulnerability in Pure Chat by Ruby Pure Chat.This issue affects Pure Chat: from n/a through 2.22. | 2024-06-05 | | |
| purvabathe--Simple Image Popup Shortcode | The Simple Image Popup Shortcode plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's 'sips_popup' shortcode in all versions up to, and including, 1.0 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| qodeinteractive--Qi Addons For Elementor | The Qi Addons For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's button widgets in all versions up to, and including, 1.7.2 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| qodeinteractive--Qi Blocks | The Qi Blocks plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's file uploader in all versions up to, and including, 1.2.9 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Author-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| Qualcomm, Inc.--Snapdragon | Information disclosure while handling T2LM Action Frame in WLAN Host. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Memory corruption in Audio during a playback or a recording due to race condition between allocation and deallocation of graph object. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Memory corruption when IPC callback handle is used after it has been released during register callback by another thread. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | Memory corruption when more scan frequency list or channels are sent from the user space. | 2024-06-03 | | |
| Qualcomm, Inc.--Snapdragon | transient DOS when setting up a fence callback to free a KGSL memory entry object during DMA. | 2024-06-03 | | |
| quomodosoft--ElementsReady Addons for Elementor | The ElementsReady Addons for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the '_id' parameter in all versions up to, and including, 6.1.0 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| RadiusTheme--The Post Grid | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in RadiusTheme The Post Grid allows Stored XSS.This issue affects The Post Grid: from n/a through 7.7.1. | 2024-06-08 | | |
| rails--rails | Action Text brings rich text content and editing to Rails. Instances of ActionText::Attachable::ContentAttachment included within a rich_text_area tag could potentially contain unsanitized HTML. This vulnerability is fixed in 7.1.3.4 and 7.2.0.beta2. | 2024-06-04 | | |
| rails--rails | Action Pack is a framework for handling and responding to web requests. Since 6.1.0, the application configurable Permissions-Policy is only served on responses with an HTML related Content-Type. This vulnerability is fixed in 6.1.7.8, 7.0.8.2, and 7.1.3.3. | 2024-06-04 | | |
| Red Hat--Red Hat Satellite 6 | A flaw was found in foreman-installer when puppet-candlepin is invoked cpdb with the --password parameter. This issue leaks the password in the process list and allows an attacker to take advantage and obtain the password. | 2024-06-05 | | |
| Red Hat--Red Hat Satellite 6 | A flaw was found in the Katello plugin for Foreman, where it is possible to store malicious JavaScript code in the "Description" field of a user. This code can be executed when opening certain pages, for example, Host Collections. | 2024-06-05 | | |
| restrict--Restrict for Elementor | The Restrict for Elementor plugin for WordPress is vulnerable to Sensitive Information Exposure in all versions up to, and including, 1.0.6 due to improper restrictions on hidden data that make it accessible through the REST API. This makes it possible for unauthenticated attackers to extract potentially sensitive data from post content. | 2024-06-06 | | |
| Revolution Slider--Slider Revolution | The Slider Revolution plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's Add Layer widget in all versions up to, and including, 6.7.11 due to insufficient input sanitization and output escaping on the user supplied 'class', 'id', and 'title' attributes. This makes it possible for authenticated attackers, with author-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. NOTE: Successful exploitation of this vulnerability requires an Administrator to give Slider Creation privileges to Author-level users. | 2024-06-04 | | |
| Revolution Slider--Slider Revolution | The Slider Revolution plugin for WordPress is vulnerable to Stored Cross-Site Scripting in all versions up to, and including, 6.7.10 due to insufficient input sanitization and output escaping on the user supplied Elementor 'wrapperid' and 'zindex' display attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-04 | | |
| rubengc--GamiPress Link | The GamiPress - Link plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's gamipress_link shortcode in all versions up to, and including, 1.1.4 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| rustaurius--Five Star Restaurant Menu and Food Ordering | The Restaurant Menu and Food Ordering plugin for WordPress is vulnerable to unauthorized creation of data due to a missing capability check on 'add_section', 'add_menu', 'add_menu_item', and 'add_menu_page' functions in all versions up to, and including, 2.4.16. This makes it possible for authenticated attackers, with Subscriber-level access and above, to create menu sections, menus, food items, and new menu pages. | 2024-06-05 | | |
| Samsung Mobile--GalaxyBudsManager PC | Arbitrary directory creation in GalaxyBudsManager PC prior to version 2.1.240315.51 allows attacker to create arbitrary directory. | 2024-06-04 | | |
| Samsung Mobile--Samsung Live Wallpaper PC | Arbitrary directory creation in Samsung Live Wallpaper PC prior to version 3.3.8.0 allows attacker to create arbitrary directory. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Improper input validation in libsheifdecadapter.so prior to SMR Jun-2024 Release 1 allows local attackers to lead to memory corruption. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Stack-based buffer overflow vulnerability in bootloader prior to SMR Jun-2024 Release 1 allows physical attackers to overwrite memory. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Improper input validation vulnerability in chnactiv TA prior to SMR Jun-2024 Release 1 allows local privileged attackers lead to potential arbitrary code execution. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Incorrect use of privileged API vulnerability in registerBatteryStatsCallback in BatteryStatsService prior to SMR Jun-2024 Release 1 allows local attackers to use privileged API. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Incorrect use of privileged API vulnerability in getSemBatteryUsageStats in BatteryStatsService prior to SMR Jun-2024 Release 1 allows local attackers to use privileged API. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Improper component protection vulnerability in Samsung Dialer prior to SMR May-2024 Release 1 allows local attackers to make a call without proper permission. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Improper input validation vulnerability in caminfo driver prior to SMR Jun-2024 Release 1 allows local privileged attackers to write out-of-bounds memory. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Improper caller verification vulnerability in SemClipboard prior to SMR June-2024 Release 1 allows local attackers to access arbitrary files. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Improper input validation vulnerability in libsavscmn.so prior to SMR Jun-2024 Release 1 allows local attackers to write out-of-bounds memory. | 2024-06-04 | | |
| Samsung Mobile--Samsung Mobile Devices | Out-of-bounds read vulnerability in bootloader prior to SMR June-2024 Release 1 allows physical attackers to arbitrary data access. | 2024-06-04 | | |
| satollo--Newsletter Send awesome emails from WordPress | The Newsletter plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'np1' parameter in all versions up to, and including, 8.3.4 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| sendinblue -- newsletter\,_smtp\,_email_marketing_and_subscribe | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Brevo Newsletter, SMTP, Email marketing and Subscribe forms by Sendinblue allows Reflected XSS.This issue affects Newsletter, SMTP, Email marketing and Subscribe forms by Sendinblue: from n/a through 3.1.77. | 2024-06-04 | | |
| Sensei--Sensei Pro (WC Paid Courses) | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Sensei Sensei Pro (WC Paid Courses) allows Stored XSS.This issue affects Sensei Pro (WC Paid Courses): from n/a through 4.23.1.1.23.1. | 2024-06-08 | | |
| shafayat-alam--Gutenberg Blocks and Page Layouts Attire Blocks | The Gutenberg Blocks and Page Layouts - Attire Blocks plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the disable_fe_assets function in all versions up to, and including, 1.9.2. This makes it possible for authenticated attackers, with subscriber access or above, to change the plugin's settings. Additionally, no nonce check is performed resulting in a CSRF vulnerability. | 2024-06-05 | | |
| shrinitech--Fluid Notification Bar | The Fluid Notification Bar plugin for WordPress is vulnerable to Stored Cross-Site Scripting via admin settings in all versions up to, and including, 3.2.3 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with administrator-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. This only affects multi-site installations and installations where unfiltered_html has been disabled. | 2024-06-04 | | |
| silabs.com--Gecko SDK | A bug exists in the API, mesh_node_power_off(), which fails to copy the contents of the Replay Protection List (RPL) from RAM to NVM before powering down, resulting in the ability to replay unsaved messages. Note that as of June 2024, the Gecko SDK was renamed to the Simplicity SDK, and the versioning scheme was changed from Gecko SDK vX.Y.Z to Simplicity SDK YYYY.MM.Patch#. | 2024-06-06 | | |
| SinaExtra--Sina Extension for Elementor | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in SinaExtra Sina Extension for Elementor allows PHP Local File Inclusion.This issue affects Sina Extension for Elementor: from n/a through 3.5.1. | 2024-06-04 | | |
| SinaExtra--Sina Extension for Elementor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in SinaExtra Sina Extension for Elementor allows Stored XSS.This issue affects Sina Extension for Elementor: from n/a through 3.5.3. | 2024-06-08 | | |
| SoftLab--Integrate Google Drive | Broken Authentication vulnerability in SoftLab Integrate Google Drive.This issue affects Integrate Google Drive: from n/a through 1.3.93. | 2024-06-04 | | |
| solarwinds -- solarwinds_platform | The SolarWinds Platform was determined to be affected by a stored cross-site scripting vulnerability affecting the web console. A high-privileged user and user interaction is required to exploit this vulnerability. | 2024-06-04 | | |
| Spiffy Plugins--Spiffy Calendar | Missing Authorization vulnerability in Spiffy Plugins Spiffy Calendar.This issue affects Spiffy Calendar: from n/a through 4.9.10. | 2024-06-04 | | |
| spiffyplugins -- wp_flow_plus | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Spiffy Plugins WP Flow Plus allows Stored XSS.This issue affects WP Flow Plus: from n/a through 5.2.2. | 2024-06-04 | | |
| StarCitizenTools--mediawiki-skins-Citizen | Citizen is a MediaWiki skin that makes extensions part of the cohesive experience. The page `MediaWiki:Tagline` has its contents used unescaped, so custom HTML (including Javascript) can be injected by someone with the ability to edit the MediaWiki namespace (typically those with the `editinterface` permission, or sysops). This vulnerability is fixed in 2.16.0. | 2024-06-03 | | |
| sulu--SuluFormBundle | The SuluFormBundle adds support for creating dynamic forms in Sulu Admin. The TokenController get parameter formName is not sanitized in the returned input field which leads to XSS. This vulnerability is fixed in 2.5.3. | 2024-06-06 | | |
| Synology--Camera Firmware | A vulnerability regarding buffer copy without checking the size of input ('Classic Buffer Overflow') has been found in the login component. This allows remote attackers to conduct denial-of-service attacks via unspecified vectors. This attack only affects the login service which will automatically restart. The following models with Synology Camera Firmware versions before 1.1.1-0383 may be affected: BC500 and TC500. | 2024-06-04 | | |
| tagDiv--tagDiv Composer | The tagDiv Composer plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's button shortcode in all versions up to, and including, 4.8 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. NOTE: The vulnerable code in this plugin is specifically tied to the tagDiv Newspaper theme. If another theme is installed (e.g., NewsMag), this code may not be present. | 2024-06-04 | | |
| Tainacan.org--Tainacan | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Tainacan.Org Tainacan allows Stored XSS.This issue affects Tainacan: from n/a through 0.21.3. | 2024-06-03 | | |
| takanakui--WP Mobile Menu The Mobile-Friendly Responsive Menu | The WP Mobile Menu - The Mobile-Friendly Responsive Menu plugin for WordPress is vulnerable to Stored Cross-Site Scripting via image alt text in all versions up to, and including, 2.8.4.2 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with author-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| Team Heateor--Heateor Social Login | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Team Heateor Heateor Social Login allows Stored XSS.This issue affects Heateor Social Login: from n/a through 1.1.32. | 2024-06-08 | | |
| TemplatesNext--TemplatesNext OnePager | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in TemplatesNext TemplatesNext OnePager allows Stored XSS.This issue affects TemplatesNext OnePager: from n/a through 1.3.3. | 2024-06-08 | | |
| Theme Freesia--Event | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Theme Freesia Event allows Stored XSS.This issue affects Event: from n/a through 1.2.2. | 2024-06-08 | | |
| Theme Freesia--Idyllic | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Theme Freesia Idyllic allows Stored XSS.This issue affects Idyllic: from n/a through 1.1.8. | 2024-06-08 | | |
| Theme Freesia--Pixgraphy | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Theme Freesia Pixgraphy allows Stored XSS.This issue affects Pixgraphy: from n/a through 1.3.8. | 2024-06-08 | | |
| themefarmer--WooCommerce Tools | The WooCommerce Tools plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the woocommerce_tool_toggle_module() function in all versions up to, and including, 1.2.9. This makes it possible for authenticated attackers, with subscriber-level access and above, to deactivate arbitrary plugin modules. | 2024-06-07 | | |
| themefusecom--Brizy Page Builder | The Brizy - Page Builder plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's contact form widget error message and redirect URL in all versions up to, and including, 2.4.43 due to insufficient input sanitization and output escaping on user supplied error messages. This makes it possible for authenticated attackers with contributor-level and above permissions to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| Themeisle--Otter Blocks PRO | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in Themeisle Otter Blocks PRO.This issue affects Otter Blocks PRO: from n/a through 2.6.11. | 2024-06-08 | | |
| themekraft -- buddyforms | The BuddyForms plugin for WordPress is vulnerable to Email Verification Bypass in all versions up to, and including, 2.8.9 via the use of an insufficiently random activation code. This makes it possible for unauthenticated attackers to bypass the email verification. | 2024-06-05 | | |
| themesflat -- themesflat_addons_for_elementor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Themesflat Themesflat Addons For Elementor allows Stored XSS.This issue affects Themesflat Addons For Elementor: from n/a through 2.1.2. | 2024-06-04 | | |
| themesflat--Themesflat Addons For Elementor | The Themesflat Addons For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via widget tags in all versions up to, and including, 2.1.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| themesflat--Themesflat Addons For Elementor | The Themesflat Addons For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's TF Group Image, TF Nav Menu, TF Posts, TF Woo Product Grid, TF Accordion, and TF Image Box widgets in all versions up to, and including, 2.1.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| themesflat--Themesflat Addons For Elementor | The Themesflat Addons For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting in several widgets via URL parameters in all versions up to, and including, 2.1.1 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| themesflat--Themesflat Addons For Elementor | The Themesflat Addons For Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's widget's titles in all versions up to, and including, 2.1.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| themeum--Tutor LMS eLearning and online course solution | The Tutor LMS - eLearning and online course solution plugin for WordPress is vulnerable to Insecure Direct Object Reference in all versions up to, and including, 2.7.1 via the 'attempt_delete' function due to missing validation on a user controlled key. This makes it possible for authenticated attackers, with Instructor-level access and above, to delete arbitrary quiz attempts. | 2024-06-07 | | |
| thimpress--LearnPress WordPress LMS Plugin | The LearnPress - WordPress LMS Plugin plugin for WordPress is vulnerable to Sensitive Information Exposure in all versions up to, and including, 4.2.6.8 due to incorrect implementation of get_items_permissions_check function. This makes it possible for unauthenticated attackers to extract basic information about website users, including their emails | 2024-06-05 | | |
| Tips and Tricks HQ--Stripe Payments | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in Tips and Tricks HQ Stripe Payments allows Code Injection.This issue affects Stripe Payments: from n/a through 2.0.79. | 2024-06-04 | | |
| TNB Mobile Solutions--Cockpit Software | Inclusion of Sensitive Information in Source Code vulnerability in TNB Mobile Solutions Cockpit Software allows Retrieve Embedded Sensitive Data.This issue affects Cockpit Software: before v0.251.1. | 2024-06-05 | | |
| tobiasbg--TablePress Tables in WordPress made easy | The TablePress - Tables in WordPress made easy plugin for WordPress is vulnerable to Server-Side Request Forgery in all versions up to, and including, 2.3 via the get_files_to_import() function. This makes it possible for authenticated attackers, with author-level access and above, to make web requests to arbitrary locations originating from the web application and can be used to query and modify information from internal services. Due to the complex nature of protecting against DNS rebind attacks in WordPress software, we settled on the developer simply restricting the usage of the URL import functionality to just administrators. While this is not optimal, we feel this poses a minimal risk to most site owners and ideally WordPress core would correct this issue in wp_safe_remote_get() and other functions. | 2024-06-07 | | |
| Tomas Cordero--Safety Exit | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Tomas Cordero Safety Exit allows Stored XSS.This issue affects Safety Exit: from n/a through 1.7.0. | 2024-06-03 | | |
| UAPP GROUP--Testimonial Carousel For Elementor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in UAPP GROUP Testimonial Carousel For Elementor allows Stored XSS.This issue affects Testimonial Carousel For Elementor: from n/a through 10.1.1. | 2024-06-08 | | |
| Unlimited Elements--Unlimited Elements For Elementor (Free Widgets, Addons, Templates) | Missing Authorization vulnerability in Unlimited Elements Unlimited Elements For Elementor (Free Widgets, Addons, Templates).This issue affects Unlimited Elements For Elementor (Free Widgets, Addons, Templates): from n/a through 1.5.109. | 2024-06-05 | | |
| victorfreitas--WPUpper Share Buttons | The WPUpper Share Buttons plugin for WordPress is vulnerable to unauthorized access of data when preparing sharing links for posts and pages in all versions up to, and including, 3.43. This makes it possible for unauthenticated attackers to obtain the contents of password protected posts and pages. | 2024-06-04 | | |
| VideoWhisper--Picture Gallery | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in VideoWhisper Picture Gallery allows Stored XSS.This issue affects Picture Gallery: from n/a through 1.5.11. | 2024-06-04 | | |
| visualcomposer -- visual_composer_website_builder | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in visualcomposer.Com Visual Composer Website Builder allows Stored XSS.This issue affects Visual Composer Website Builder: from n/a through 45.8.0. | 2024-06-04 | | |
| Volkswagen Group Charging GmbH - Elli, EVBox--ID Charger Connect & Pro | An attacker with access to the private network (the charger is connected to) or local access to the Ethernet-Interface can exploit a faulty implementation of the JWT-library in order to bypass the password authentication to the web configuration interface and then has full access as the user would have. However, an attacker will not have developer or admin rights. If the implementation of the JWT-library is wrongly configured to accept "none"-algorithms, the server will pass insecure JWT. A local, unauthenticated attacker can exploit this vulnerability to bypass the authentication mechanism. | 2024-06-06 | | |
| vollstart -- event_tickets_with_ticket_scanner | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Saso Nikolov Event Tickets with Ticket Scanner allows Reflected XSS.This issue affects Event Tickets with Ticket Scanner: from n/a through 2.3.1. | 2024-06-04 | | |
| Vsourz Digital--Responsive Slick Slider WordPress | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in Vsourz Digital Responsive Slick Slider WordPress allows Code Injection.This issue affects Responsive Slick Slider WordPress: from n/a through 1.4. | 2024-06-04 | | |
| wbcomdesigns--Wbcom Designs Custom Font Uploader | The Wbcom Designs - Custom Font Uploader plugin for WordPress is vulnerable to unauthorized loss of data due to a missing capability check on the 'cfu_delete_customfont' function in all versions up to, and including, 2.3.4. This makes it possible for authenticated attackers, with Subscriber-level access and above, to delete any custom font. | 2024-06-06 | | |
| wcmp--MultiVendorX Marketplace WooCommerce MultiVendor Marketplace Solution | The MultiVendorX Marketplace - WooCommerce MultiVendor Marketplace Solution plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'hover_animation' parameter in all versions up to, and including, 4.1.11 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| web-audimex -- audimexee | Cross Site Scripting vulnerability in audimex audimexEE v.15.1.2 and fixed in 15.1.3.9 allows a remote attacker to execute arbitrary code via the service, method, widget_type, request_id, payload parameters. | 2024-06-04 | | |
| WebFactory Ltd--Captcha Code | Improper Restriction of Excessive Authentication Attempts vulnerability in WebFactory Ltd Captcha Code allows Functionality Bypass.This issue affects Captcha Code: from n/a through 2.9. | 2024-06-04 | | |
| webfactory--Minimal Coming Soon Coming Soon Page | The Minimal Coming Soon - Coming Soon Page plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the validate_ajax, deactivate_ajax, and save_ajax functions in all versions up to, and including, 2.38. This makes it possible for authenticated attackers, with Subscriber-level access and above, to edit the license key, which could disable features of the plugin. | 2024-06-08 | | |
| webfactory--WP Force SSL & HTTPS SSL Redirect | The WP Force SSL & HTTPS SSL Redirect plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the 'ajax_save_setting' function in versions up to, and including, 1.66. This makes it possible for authenticated attackers, subscriber-level permissions and above, to update the plugin settings. | 2024-06-08 | | |
| webfactory--WP Reset Most Advanced WordPress Reset Tool | The WP Reset plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the save_ajax function in all versions up to, and including, 2.02. This makes it possible for authenticated attackers, with subscriber-level access and above, to modify the value fo the 'License Key' field for the 'Activate Pro License' setting. | 2024-06-08 | | |
| Webliberty--Simple Spoiler | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Webliberty Simple Spoiler allows Stored XSS.This issue affects Simple Spoiler: from n/a through 1.2. | 2024-06-03 | | |
| westerndeal--CF7 Google Sheets Connector | The CF7 Google Sheets Connector plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the 'execute_post_data_cg7_free' function in all versions up to, and including, 5.0.9. This makes it possible for unauthenticated attackers to toggle site configuration settings, including WP_DEBUG, WP_DEBUG_LOG, SCRIPT_DEBUG, and SAVEQUERIES. | 2024-06-08 | | |
| westguard--WS Form LITE Drag & Drop Contact Form Builder for WordPress | The WS Form LITE plugin for WordPress is vulnerable to CSV Injection in versions up to, and including, 1.9.217. This allows unauthenticated attackers to embed untrusted input into exported CSV files, which can result in code execution when these files are downloaded and opened on a local system with a vulnerable configuration. | 2024-06-07 | | |
| willnorris--Open Graph | The Open Graph plugin for WordPress is vulnerable to Sensitive Information Exposure in all versions up to, and including, 1.11.2 via the 'opengraph_default_description' function. This makes it possible for unauthenticated attackers to extract sensitive data including partial content of password-protected blog posts. | 2024-06-06 | | |
| wordpresschef--Salon Booking System | The Salon booking system plugin for WordPress is vulnerable to unauthorized access and modification of data due to a missing capability check on several functions hooked into admin_init in all versions up to, and including, 9.9. This makes it possible for authenticated attackers with subscriber access or higher to modify plugin settings and view discount codes intended for other users. | 2024-06-08 | | |
| Wow-Company--Woocommerce Recent Purchases | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Wow-Company Woocommerce - Recent Purchases allows PHP Local File Inclusion.This issue affects Woocommerce - Recent Purchases: from n/a through 1.0.1. | 2024-06-04 | | |
| WP Darko--Responsive Tabs | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in WP Darko Responsive Tabs allows Code Injection.This issue affects Responsive Tabs: from n/a before 4.0.6. | 2024-06-04 | | |
| WP Discussion Board--Discussion Board | Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) vulnerability in WP Discussion Board Discussion Board allows Content Spoofing, Cross-Site Scripting (XSS).This issue affects Discussion Board: from n/a through 2.4.8. | 2024-06-04 | | |
| WP Hait--Post Grid Elementor Addon | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in WP Hait Post Grid Elementor Addon allows Stored XSS.This issue affects Post Grid Elementor Addon: from n/a through 2.0.16. | 2024-06-03 | | |
| WP Moose--Kenta Gutenberg Blocks Responsive Blocks and block templates library for Gutenberg Editor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in WP Moose Kenta Gutenberg Blocks Responsive Blocks and block templates library for Gutenberg Editor allows Stored XSS.This issue affects Kenta Gutenberg Blocks Responsive Blocks and block templates library for Gutenberg Editor: from n/a through 1.3.9. | 2024-06-08 | | |
| wpbean--WPB Elementor Addons | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in wpbean WPB Elementor Addons allows Stored XSS.This issue affects WPB Elementor Addons: from n/a through 1.0.9. | 2024-06-03 | | |
| WPBlockArt--BlockArt Blocks | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in WPBlockArt BlockArt Blocks allows Stored XSS.This issue affects BlockArt Blocks: from n/a through 2.1.5. | 2024-06-08 | | |
| wpchill--Strong Testimonials | The Strong Testimonials plugin for WordPress is vulnerable to unauthorized modification of data due to an improper capability check on the wpmtst_save_view_sticky function in all versions up to, and including, 3.1.12. This makes it possible for authenticated attackers, with contributor access and above, to modify favorite views. | 2024-06-07 | | |
| WPDeveloper--Essential Addons for Elementor | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in WPDeveloper Essential Addons for Elementor allows Stored XSS.This issue affects Essential Addons for Elementor: from n/a through 5.9.15. | 2024-06-03 | | |
| wpdevteam--EmbedPress Embed PDF, Google Docs, Vimeo, Wistia, Embed YouTube Videos, Audios, Maps & Embed Any Documents in Gutenberg & Elementor | The EmbedPress - Embed PDF, Google Docs, Vimeo, Wistia, Embed YouTube Videos, Audios, Maps & Embed Any Documents in Gutenberg & Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'url' attribute within the plugin's EmbedPress PDF widget in all versions up to, and including, 4.0.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| wpdevteam--Essential Addons for Elementor Best Elementor Templates, Widgets, Kits & WooCommerce Builders | The Essential Addons for Elementor - Best Elementor Templates, Widgets, Kits & WooCommerce Builders plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'get_manual_calendar_events' function in all versions up to, and including, 5.9.22 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
| wpecommerce--Recurring PayPal Donations | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in wpecommerce Recurring PayPal Donations allows Stored XSS.This issue affects Recurring PayPal Donations: from n/a through 1.7. | 2024-06-08 | | |
| WPManageNinja LLC--Ninja Tables | Server-Side Request Forgery (SSRF) vulnerability in WPManageNinja LLC Ninja Tables.This issue affects Ninja Tables: from n/a through 5.0.9. | 2024-06-03 | | |
| WPMU DEV--Branda | Authentication Bypass by Spoofing vulnerability in WPMU DEV Branda allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Branda: from n/a through 3.4.14. | 2024-06-04 | | |
| WPMU DEV--Defender Security | Improper Authentication vulnerability in WPMU DEV Defender Security allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Defender Security: from n/a through 4.2.0. | 2024-06-04 | | |
| wponlinesupport--Album and Image Gallery plus Lightbox | The The Album and Image Gallery plus Lightbox plugin for WordPress is vulnerable to arbitrary shortcode execution in all versions up to, and including, 2.0. This is due to the software allowing users to execute an action that does not properly validate a value before running do_shortcode. This makes it possible for unauthenticated attackers to execute arbitrary shortcodes. | 2024-06-06 | | |
| WPPlugins WordPress Security Plugins--Hide My WP Ghost | Improper Restriction of Excessive Authentication Attempts vulnerability in WPPlugins - WordPress Security Plugins Hide My WP Ghost allows Functionality Bypass.This issue affects Hide My WP Ghost: from n/a through 5.0.25. | 2024-06-04 | | |
| wppool--WP Dark Mode WordPress Dark Mode Plugin for Improved Accessibility, Dark Theme, Night Mode, and Social Sharing | The WP Dark Mode - WordPress Dark Mode Plugin for Improved Accessibility, Dark Theme, Night Mode, and Social Sharing plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on the wpdm_social_share_save_options function in all versions up to, and including, 5.0.4. This makes it possible for authenticated attackers, with Subscriber-level access and above, to update the plugin's settings. | 2024-06-06 | | |
| wppost--WP-Recall Registration, Profile, Commerce & More | The WP-Recall - Registration, Profile, Commerce & More plugin for WordPress is vulnerable to unauthorized loss of data due to a missing capability check on the 'delete_payment' function in all versions up to, and including, 16.26.6. This makes it possible for unauthenticated attackers to delete arbitrary payments. | 2024-06-06 | | |
| wproyal--Royal Elementor Addons and Templates | The Royal Elementor Addons and Templates for WordPress is vulnerable to Stored Cross-Site Scripting via the 'inline_list' parameter in versions up to, and including, 1.3.976 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| wproyal--Royal Elementor Addons and Templates | The Royal Elementor Addons and Templates plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'custom_upload_mimes' function in versions up to, and including, 1.3.976 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level permissions and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-07 | | |
| wpvivid -- wpvivid_backup_for_mainwp | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in WPvivid Team WPvivid Backup for MainWP allows Reflected XSS.This issue affects WPvivid Backup for MainWP: from n/a through 0.9.32. | 2024-06-04 | | |
| wpweaver--Weaver Xtreme Theme Support | The Weaver Xtreme Theme Support plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the plugin's div shortcode in all versions up to, and including, 6.4 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-05 | | |
| wpxpo--Post Grid Gutenberg Blocks and WordPress Blog Plugin PostX | The Post Grid Gutenberg Blocks and WordPress Blog Plugin - PostX plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the filterMobileText parameter in all versions up to, and including, 4.0.4 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with Contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-08 | | |
| Xabier Miranda--WP Back Button | Cross Site Scripting (XSS) vulnerability in Xabier Miranda WP Back Button allows Stored XSS.This issue affects WP Back Button: from n/a through 1.1.3. | 2024-06-03 | | |
| xootix--Login/Signup Popup ( Inline Form + Woocommerce ) | The Login/Signup Popup ( Inline Form + Woocommerce ) plugin for WordPress is vulnerable to unauthorized access of data due to a missing capability check on the 'export_settings' function in versions 2.7.1 to 2.7.2. This makes it possible for authenticated attackers, with Subscriber-level access and above, to read arbitrary options on affected sites. | 2024-06-06 | | |
| YITH--YITH Custom Login | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in YITH YITH Custom Login allows Stored XSS.This issue affects YITH Custom Login: from n/a through 1.7.0. | 2024-06-08 | | |
| YITH--YITH WooCommerce Tab Manager | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in YITH YITH WooCommerce Tab Manager allows Stored XSS.This issue affects YITH WooCommerce Tab Manager: from n/a through 1.35.0. | 2024-06-08 | | |
| YITH--YITH WooCommerce Wishlist | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in YITH YITH WooCommerce Wishlist allows Stored XSS.This issue affects YITH WooCommerce Wishlist: from n/a through 3.32.0. | 2024-06-03 | | |
| yonifre--Maspik Spam blacklist | Authentication Bypass by Spoofing vulnerability in yonifre Maspik - Spam blacklist allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Maspik - Spam blacklist: from n/a through 0.10.3. | 2024-06-04 | | |
| zhuyi--BuddyPress Members Only | The BuddyPress Members Only plugin for WordPress is vulnerable to Sensitive Information Exposure in all versions up to, and including, 3.3.5 via the REST API. This makes it possible for unauthenticated attackers to bypass the plugin's "All Other Sections On Your Site Will be Opened to Guest" feature (when unset) and view restricted page and post content. | 2024-06-06 | | |
| zootemplate--Clever Addons for Elementor | The Clever Addons for Elementor plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the CAFE Icon, CAFE Team Member, and CAFE Slider widgets in all versions up to, and including, 2.1.9 due to insufficient input sanitization and output escaping. This makes it possible for authenticated attackers, with contributor-level access and above, to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | 2024-06-06 | | |
ninjateam--GDPR CCPA Compliance & Cookie Consent Banner | The GDPR CCPA Compliance & Cookie Consent Banner plugin for WordPress is vulnerable to unauthorized modification of data due to a missing capability check on several functions named ajaxUpdateSettings() in all versions up to, and including, 2.7.0. This makes it possible for authenticated attackers, with Subscriber-level access and above, to modify the plugin's settings, update page content, send arbitrary emails and inject malicious web scripts. | 2024-06-07 | |
Low Vulnerabilities
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| All In One WP Security & Firewall Team--All In One WP Security & Firewall | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in All In One WP Security & Firewall Team All In One WP Security & Firewall allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects All In One WP Security & Firewall: from n/a through 5.2.4. | 2024-06-04 | | |
| Born05--CraftCMS Plugin - Two-Factor Authentication | The CraftCMS plugin Two-Factor Authentication in versions 3.3.1, 3.3.2 and 3.3.3 discloses the password hash of the currently authenticated user after submitting a valid TOTP. | 2024-06-06 | | |
| David Vongries--Ultimate Dashboard | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in David Vongries Ultimate Dashboard allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Ultimate Dashboard: from n/a through 3.7.10. | 2024-06-04 | | |
| Event Espresso--Event Espresso 4 Decaf | Missing Authorization vulnerability in Event Espresso Event Espresso 4 Decaf allows Functionality Misuse.This issue affects Event Espresso 4 Decaf: from n/a through 4.10.44.Decaf. | 2024-06-03 | | |
| evmos--evmos | Evmos is the Ethereum Virtual Machine (EVM) Hub on the Cosmos Network. The spendable balance is not updated properly when delegating vested tokens. The issue allows a clawback vesting account to anticipate the release of unvested tokens. This vulnerability is fixed in 18.0.0. | 2024-06-06 | | |
| Florent Maillefaud--WP Maintenance | Authentication Bypass by Spoofing vulnerability in WP Maintenance allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects WP Maintenance: from n/a through 6.1.3. | 2024-06-04 | | |
| LWS--LWS Hide Login | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in LWS LWS Hide Login allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects LWS Hide Login: from n/a through 2.1.8. | 2024-06-04 | | |
| n/a--Likeshop | A vulnerability was found in Likeshop up to 2.5.7 and classified as problematic. This issue affects some unknown processing of the file /admin of the component Merchandise Handler. The manipulation leads to cross site scripting. The attack may be initiated remotely. The identifier VDB-267449 was assigned to this vulnerability. | 2024-06-08 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor, Automotive Processor, and Modem Exynos 9820, 9825, 980, 990, 850, 1080, 2100, 2200, 1280, 1380, 1330, Modem 5123, Modem 5300, and Auto T5123. The baseband software does not properly check replay protection specified by the NAS (Non-Access-Stratum) module. This can lead to denial of service. | 2024-06-05 | | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor, Automotive Processor, and Modem Exynos 9820, 9825, 980, 990, 850, 1080, 2100, 2200, 1280, 1380, 1330, Modem 5123, Modem 5300, and Auto T5123. The baseband software does not properly check format types specified by the NAS (Non-Access-Stratum) module. This can lead to bypass of authentication. | 2024-06-05 | | |
| Webcraftic--Hide login page | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in Webcraftic Hide login page allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Hide login page: from n/a through 1.1.9. | 2024-06-04 | | |
| WpDevArt--Booking calendar, Appointment Booking System | External Control of Assumed-Immutable Web Parameter vulnerability in WpDevArt Booking calendar, Appointment Booking System allows Manipulating Hidden Fields.This issue affects Booking calendar, Appointment Booking System: from n/a through 3.2.3. | 2024-06-03 | | |
| wpdevart--Coming soon and Maintenance mode | Authentication Bypass by Spoofing vulnerability in wpdevart Coming soon and Maintenance mode allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects Coming soon and Maintenance mode: from n/a through 3.7.3. | 2024-06-04 | | |
| WPServeur, NicolasKulka, wpformation--WPS Hide Login | Exposure of Sensitive Information to an Unauthorized Actor vulnerability in WPServeur, NicolasKulka, wpformation WPS Hide Login allows Accessing Functionality Not Properly Constrained by ACLs.This issue affects WPS Hide Login: from n/a through 1.9.11. | 2024-06-04 | |
Severity Not Yet Assigned
| Primary Vendor -- Product | Description | Published | CVSS Score | Source & Patch Info |
|---|---|---|---|---|
| A10--Thunder ADC | A10 Thunder ADC CsrRequestView Command Injection Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of A10 Thunder ADC. Authentication is required to exploit this vulnerability. The specific flaw exists within the CsrRequestView class. The issue results from the lack of proper validation of a user-supplied string before using it to execute a system call. An attacker can leverage this vulnerability to execute code in the context of a10user. Was ZDI-CAN-22517. | 2024-06-06 | not yet calculated | |
| A10--Thunder ADC | A10 Thunder ADC Incorrect Permission Assignment Local Privilege Escalation Vulnerability. This vulnerability allows local attackers to escalate privileges on affected installations of A10 Thunder ADC. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit this vulnerability. The specific flaw exists within the installer. The issue results from incorrect permissions on a file. An attacker can leverage this vulnerability to escalate privileges and execute arbitrary code in the context of root. Was ZDI-CAN-22754. | 2024-06-06 | not yet calculated | |
| Apache Software Foundation--Apache OFBiz | Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal') vulnerability in Apache OFBiz. This issue affects Apache OFBiz: before 18.12.14. Users are recommended to upgrade to version 18.12.14, which fixes the issue. | 2024-06-04 | not yet calculated | |
| Arm Ltd--Bifrost GPU Kernel Driver | Use After Free vulnerability in Arm Ltd Bifrost GPU Kernel Driver, Arm Ltd Valhall GPU Kernel Driver allows a local non-privileged user to make improper GPU memory processing operations to gain access to already freed memory.This issue affects Bifrost GPU Kernel Driver: from r34p0 through r40p0; Valhall GPU Kernel Driver: from r34p0 through r40p0. | 2024-06-07 | not yet calculated | |
| berriai--berriai/litellm | BerriAI's litellm, in its latest version, is vulnerable to arbitrary file deletion due to improper input validation on the `/audio/transcriptions` endpoint. An attacker can exploit this vulnerability by sending a specially crafted request that includes a file path to the server, which then deletes the specified file without proper authorization or validation. This vulnerability is present in the code where `os.remove(file.filename)` is used to delete a file, allowing any user to delete critical files on the server such as SSH keys, SQLite databases, or configuration files. | 2024-06-06 | not yet calculated | |
| berriai--berriai/litellm | A code injection vulnerability exists in the berriai/litellm application, version 1.34.6, due to the use of unvalidated input in the eval function within the secret management system. This vulnerability requires a valid Google KMS configuration file to be exploitable. Specifically, by setting the `UI_LOGO_PATH` variable to a remote server address in the `get_image` function, an attacker can write a malicious Google KMS configuration file to the `cached_logo.jpg` file. This file can then be used to execute arbitrary code by assigning malicious code to the `SAVE_CONFIG_TO_DB` environment variable, leading to full system control. The vulnerability is contingent upon the use of the Google KMS feature. | 2024-06-06 | not yet calculated | |
| berriai--berriai/litellm | A blind SQL injection vulnerability exists in the berriai/litellm application, specifically within the '/team/update' process. The vulnerability arises due to the improper handling of the 'user_id' parameter in the raw SQL query used for deleting users. An attacker can exploit this vulnerability by injecting malicious SQL commands through the 'user_id' parameter, leading to potential unauthorized access to sensitive information such as API keys, user information, and tokens stored in the database. The affected version is 1.27.14. | 2024-06-06 | not yet calculated | |
| berriai--berriai/litellm | An SQL Injection vulnerability exists in the berriai/litellm repository, specifically within the `/global/spend/logs` endpoint. The vulnerability arises due to improper neutralization of special elements used in an SQL command. The affected code constructs an SQL query by concatenating an unvalidated `api_key` parameter directly into the query, making it susceptible to SQL Injection if the `api_key` contains malicious data. This issue affects the latest version of the repository. Successful exploitation of this vulnerability could lead to unauthorized access, data manipulation, exposure of confidential information, and denial of service (DoS). | 2024-06-06 | not yet calculated | |
| Canonical Ltd.--Apport | There is a race condition in the 'replaced executable' detection that, with the correct local configuration, allow an attacker to execute arbitrary code as root. | 2024-06-03 | not yet calculated | |
| Canonical Ltd.--Apport | Apport can be tricked into connecting to arbitrary sockets as the root user | 2024-06-03 | not yet calculated | |
| Canonical Ltd.--Apport | ~/.config/apport/settings parsing is vulnerable to "billion laughs" attack | 2024-06-04 | not yet calculated | |
| Canonical Ltd.--Apport | is_closing_session() allows users to fill up apport.log | 2024-06-04 | not yet calculated | |
| Canonical Ltd.--Apport | is_closing_session() allows users to create arbitrary tcp dbus connections | 2024-06-04 | not yet calculated | |
| Canonical Ltd.--Apport | is_closing_session() allows users to consume RAM in the Apport process | 2024-06-04 | not yet calculated | |
| Canonical Ltd.--Apport | Apport does not disable python crash handler before entering chroot | 2024-06-04 | not yet calculated | |
| Canonical Ltd.--Apport | Apport argument parsing mishandles filename splitting on older kernels resulting in argument spoofing | 2024-06-04 | not yet calculated | |
| Canonical Ltd.--subiquity | Subiquity Shows Guided Storage Passphrase in Plaintext with Read-all Permissions | 2024-06-03 | not yet calculated | |
| Chromium--libvpx | There exists interger overflows in libvpx in versions prior to 1.14.1. Calling vpx_img_alloc() with a large value of the d_w, d_h, or align parameter may result in integer overflows in the calculations of buffer sizes and offsets and some fields of the returned vpx_image_t struct may be invalid. Calling vpx_img_wrap() with a large value of the d_w, d_h, or stride_align parameter may result in integer overflows in the calculations of buffer sizes and offsets and some fields of the returned vpx_image_t struct may be invalid. We recommend upgrading to version 1.14.1 or beyond | 2024-06-03 | not yet calculated | |
| CodePeople--Music Store - WordPress eCommerce | SQL injection vulnerability in Music Store - WordPress eCommerce versions prior to 1.1.14 allows a remote authenticated attacker with an administrative privilege to execute arbitrary SQL commands. Information stored in the database may be obtained or altered by the attacker. | 2024-06-07 | not yet calculated | |
| deepjavalibrary--deepjavalibrary/djl | A TarSlip vulnerability exists in the deepjavalibrary/djl, affecting version 0.26.0 and fixed in version 0.27.0. This vulnerability allows an attacker to manipulate file paths within tar archives to overwrite arbitrary files on the target system. Exploitation of this vulnerability could lead to remote code execution, privilege escalation, data theft or manipulation, and denial of service. The vulnerability is due to improper validation of file paths during the extraction of tar files, as demonstrated in multiple occurrences within the library's codebase, including but not limited to the files_util.py and extract_imagenet.py scripts. | 2024-06-06 | not yet calculated | |
| EMTA Grup--PDKS | Improper Access Control vulnerability in EMTA Grup PDKS allows Exploiting Incorrectly Configured Access Control Security Levels.This issue affects PDKS: before 20240603. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | 2024-06-03 | not yet calculated | |
| Fortra--Tripwire Enterprise | An authentication bypass vulnerability has been identified in the REST and SOAP API components of Tripwire Enterprise (TE) 9.1.0 when TE is configured to use LDAP/Active Directory SAML authentication and its optional "Auto-synchronize LDAP Users, Roles, and Groups" feature is enabled. This vulnerability allows unauthenticated attackers to bypass authentication if a valid username is known. Exploitation of this vulnerability could allow remote attackers to gain privileged access to the APIs and lead to unauthorized information disclosure or modification. | 2024-06-03 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | The gaizhenbiao/chuanhuchatgpt application is vulnerable to a path traversal attack due to its use of an outdated gradio component. The application is designed to restrict user access to resources within the `web_assets` folder. However, the outdated version of gradio it employs is susceptible to path traversal, as identified in CVE-2023-51449. This vulnerability allows unauthorized users to bypass the intended restrictions and access sensitive files, such as `config.json`, which contains API keys. The issue affects the latest version of chuanhuchatgpt prior to the fixed version released on 20240305. | 2024-06-06 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | A stored Cross-Site Scripting (XSS) vulnerability existed in version (20240121) of gaizhenbiao/chuanhuchatgpt due to inadequate sanitization and validation of model output data. Despite user-input validation efforts, the application fails to properly sanitize or validate the output from the model, allowing for the injection and execution of malicious JavaScript code within the context of a user's browser. This vulnerability can lead to the execution of arbitrary JavaScript code in the context of other users' browsers, potentially resulting in the hijacking of victims' browsers. | 2024-06-06 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | In gaizhenbiao/chuanhuchatgpt, specifically the version tagged as 20240121, there exists a vulnerability due to improper access control mechanisms. This flaw allows an authenticated attacker to bypass intended access restrictions and read the `history` files of other users, potentially leading to unauthorized access to sensitive information. The vulnerability is present in the application's handling of access control for the `history` path, where no adequate mechanism is in place to prevent an authenticated user from accessing another user's chat history files. This issue poses a significant risk as it could allow attackers to obtain sensitive information from the chat history of other users. | 2024-06-06 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | An improper access control vulnerability exists in the gaizhenbiao/chuanhuchatgpt application, specifically in version 20240410. This vulnerability allows any user on the server to access the chat history of any other user without requiring any form of interaction between the users. Exploitation of this vulnerability could lead to data breaches, including the exposure of sensitive personal details, financial data, or confidential conversations. Additionally, it could facilitate identity theft and manipulation or fraud through the unauthorized access to users' chat histories. This issue is due to insufficient access control mechanisms in the application's handling of chat history data. | 2024-06-04 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | A timing attack vulnerability exists in the gaizhenbiao/chuanhuchatgpt repository, specifically within the password comparison logic. The vulnerability is present in version 20240310 of the software, where passwords are compared using the '=' operator in Python. This method of comparison allows an attacker to guess passwords based on the timing of each character's comparison. The issue arises from the code segment that checks a password for a particular username, which can lead to the exposure of sensitive information to an unauthorized actor. An attacker exploiting this vulnerability could potentially guess user passwords, compromising the security of the system. | 2024-06-06 | not yet calculated | |
| gaizhenbiao--gaizhenbiao/chuanhuchatgpt | gaizhenbiao/chuanhuchatgpt is vulnerable to an unrestricted file upload vulnerability due to insufficient validation of uploaded file types in its `/upload` endpoint. Specifically, the `handle_file_upload` function does not sanitize or validate the file extension or content type of uploaded files, allowing attackers to upload files with arbitrary extensions, including HTML files containing XSS payloads and Python files. This vulnerability, present in the latest version as of 20240310, could lead to stored XSS attacks and potentially result in remote code execution (RCE) on the server hosting the application. | 2024-06-06 | not yet calculated | |
| Go standard library--archive/zip | The archive/zip package's handling of certain types of invalid zip files differs from the behavior of most zip implementations. This misalignment could be exploited to create an zip file with contents that vary depending on the implementation reading the file. The archive/zip package now rejects files containing these errors. | 2024-06-05 | not yet calculated | |
| Go standard library--net/netip | The various Is methods (IsPrivate, IsLoopback, etc) did not work as expected for IPv4-mapped IPv6 addresses, returning false for addresses which would return true in their traditional IPv4 forms. | 2024-06-05 | not yet calculated | |
| Google--Omaha | Inappropriate implementation in Google Updator prior to 1.3.36.351 in Google Chrome allowed a local attacker to perform privilege escalation via a malicious file. (Chromium security severity: High) | 2024-06-07 | not yet calculated | |
| Google--Omaha | Inappropriate implementation in Google Updator prior to 1.3.36.351 in Google Chrome allowed a local attacker to bypass discretionary access control via a malicious file. (Chromium security severity: High) | 2024-06-07 | not yet calculated | |
| gradio-app--gradio-app/gradio | A command injection vulnerability exists in the gradio-app/gradio repository, specifically within the 'test-functional.yml' workflow. The vulnerability arises due to improper neutralization of special elements used in a command, allowing for unauthorized modification of the base repository or secrets exfiltration. The issue affects versions up to and including '@gradio/[email protected]'. The flaw is present in the workflow's handling of GitHub context information, where it echoes the full name of the head repository, the head branch, and the workflow reference without adequate sanitization. This could potentially lead to the exfiltration of sensitive secrets such as 'GITHUB_TOKEN', 'COMMENT_TOKEN', and 'CHROMATIC_PROJECT_TOKEN'. | 2024-06-04 | not yet calculated | |
| gradio-app--gradio-app/gradio | The 'deploy-website.yml' workflow in the gradio-app/gradio repository, specifically in the 'main' branch, is vulnerable to secrets exfiltration due to improper authorization. The vulnerability arises from the workflow's explicit checkout and execution of code from a fork, which is unsafe as it allows the running of untrusted code in an environment with access to push to the base repository and access secrets. This flaw could lead to the exfiltration of sensitive secrets such as GITHUB_TOKEN, HF_TOKEN, VERCEL_ORG_ID, VERCEL_PROJECT_ID, COMMENT_TOKEN, AWSACCESSKEYID, AWSSECRETKEY, and VERCEL_TOKEN. The vulnerability is present in the workflow file located at https://github.com/gradio-app/gradio/blob/72f4ca88ab569aae47941b3fb0609e57f2e13a27/.github/workflows/deploy-website.yml. | 2024-06-04 | not yet calculated | |
| gradio-app--gradio-app/gradio | A Server-Side Request Forgery (SSRF) vulnerability exists in the gradio-app/gradio version 4.21.0, specifically within the `/queue/join` endpoint and the `save_url_to_cache` function. The vulnerability arises when the `path` value, obtained from the user and expected to be a URL, is used to make an HTTP request without sufficient validation checks. This flaw allows an attacker to send crafted requests that could lead to unauthorized access to the local network or the AWS metadata endpoint, thereby compromising the security of internal servers. | 2024-06-06 | not yet calculated | |
| gradio-app--gradio-app/gradio | A local file inclusion vulnerability exists in the JSON component of gradio-app/gradio version 4.25. The vulnerability arises from improper input validation in the `postprocess()` function within `gradio/components/json_component.py`, where a user-controlled string is parsed as JSON. If the parsed JSON object contains a `path` key, the specified file is moved to a temporary directory, making it possible to retrieve it later via the `/file=..` endpoint. This issue is due to the `processing_utils.move_files_to_cache()` function traversing any object passed to it, looking for a dictionary with a `path` key, and then copying the specified file to a temporary directory. The vulnerability can be exploited by an attacker to read files on the remote system, posing a significant security risk. | 2024-06-06 | not yet calculated | |
| GStreamer--GStreamer | GStreamer AV1 Video Parsing Stack-based Buffer Overflow Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of GStreamer. Interaction with this library is required to exploit this vulnerability but attack vectors may vary depending on the implementation. The specific flaw exists within the parsing of tile list data within AV1-encoded video files. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length stack-based buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22873. | 2024-06-07 | not yet calculated | |
| h2oai--h2oai/h2o-3 | In h2oai/h2o-3 version 3.40.0.4, an exposure of sensitive information vulnerability exists due to an arbitrary system path lookup feature. This vulnerability allows any remote user to view full paths in the entire file system where h2o-3 is hosted. Specifically, the issue resides in the Typeahead API call, which when requested with a typeahead lookup of '/', exposes the root filesystem including directories such as /home, /usr, /bin, among others. This vulnerability could allow attackers to explore the entire filesystem, and when combined with a Local File Inclusion (LFI) vulnerability, could make exploitation of the server trivial. | 2024-06-06 | not yet calculated | |
| imartinez--imartinez/privategpt | A Server-Side Request Forgery (SSRF) vulnerability exists in the file upload section of imartinez/privategpt version 0.5.0. This vulnerability allows attackers to send crafted requests that could result in unauthorized access to the local network and potentially sensitive information. Specifically, by manipulating the 'path' parameter in a file upload request, an attacker can cause the application to make arbitrary requests to internal services, including the AWS metadata endpoint. This issue could lead to the exposure of internal servers and sensitive data. | 2024-06-06 | not yet calculated | |
| Japan System Techniques Co., Ltd.--UNIVERSAL PASSPORT RX | Cross-site scripting vulnerability exists in UNIVERSAL PASSPORT RX versions 1.0.0 to 1.0.7, which may allow a remote authenticated attacker to execute an arbitrary script on the web browser of the user who is using the product. | 2024-06-03 | not yet calculated | |
| Japan System Techniques Co., Ltd.--UNIVERSAL PASSPORT RX | Cross-site scripting vulnerability exists in UNIVERSAL PASSPORT RX versions 1.0.0 to 1.0.8, which may allow a remote authenticated attacker with an administrative privilege to execute an arbitrary script on the web browser of the user who is using the product. | 2024-06-03 | not yet calculated | |
| Johnson Controls--Software House CCURE 9000 | Under certain circumstances the Microsoft® Internet Information Server (IIS) used to host the C•CURE 9000 Web Server will log Microsoft Windows credential details within logs. There is no impact to non-web service interfaces C•CURE 9000 or prior versions | 2024-06-06 | not yet calculated | |
| Johnson Controls--Software House iSTAR Pro, ICU | Under certain circumstances communications between the ICU tool and an iSTAR Pro door controller is susceptible to Machine-in-the-Middle attacks which could impact door control and configuration. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF JPF File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of JPF files. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated object. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22092. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF PSD File Parsing Heap-based Buffer Overflow Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of PSD files. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length heap-based buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22917. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF PDF File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of PDF files. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22918. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF PSD File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of PSD files. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22919. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF TGA File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of TGA files. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22920. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF PDF File Parsing Stack-based Buffer Overflow Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of PDF files. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a fixed-length stack-based buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22921. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF PDF File Parsing Memory Corruption Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of PDF files. The issue results from the lack of proper validation of user-supplied data, which can result in a memory corruption condition. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22930. | 2024-06-06 | not yet calculated | |
| Kofax--Power PDF | Kofax Power PDF AcroForm Annotation Out-Of-Bounds Read Information Disclosure Vulnerability. This vulnerability allows remote attackers to disclose sensitive information on affected installations of Kofax Power PDF. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the handling of Annotation objects in AcroForms. The issue results from the lack of proper validation of user-supplied data, which can result in a read past the end of an allocated buffer. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of the current process. Was ZDI-CAN-22933. | 2024-06-06 | not yet calculated | |
| kubeflow--kubeflow/kubeflow | kubeflow/kubeflow is vulnerable to a Regular Expression Denial of Service (ReDoS) attack due to inefficient regular expression complexity in its email validation mechanism. An attacker can remotely exploit this vulnerability without authentication by providing specially crafted input that causes the application to consume an excessive amount of CPU resources. This vulnerability affects the latest version of kubeflow/kubeflow, specifically within the centraldashboard-angular backend component. The impact of exploiting this vulnerability includes resource exhaustion, and service disruption. | 2024-06-06 | not yet calculated | |
| langchain-ai--langchain-ai/langchain | A Denial-of-Service (DoS) vulnerability exists in the `SitemapLoader` class of the `langchain-ai/langchain` repository, affecting all versions. The `parse_sitemap` method, responsible for parsing sitemaps and extracting URLs, lacks a mechanism to prevent infinite recursion when a sitemap URL refers to the current sitemap itself. This oversight allows for the possibility of an infinite loop, leading to a crash by exceeding the maximum recursion depth in Python. This vulnerability can be exploited to occupy server socket/port resources and crash the Python process, impacting the availability of services relying on this functionality. | 2024-06-06 | not yet calculated | |
| langchain-ai--langchain-ai/langchain | A Server-Side Request Forgery (SSRF) vulnerability exists in the Web Research Retriever component of langchain-ai/langchain version 0.1.5. The vulnerability arises because the Web Research Retriever does not restrict requests to remote internet addresses, allowing it to reach local addresses. This flaw enables attackers to execute port scans, access local services, and in some scenarios, read instance metadata from cloud environments. The vulnerability is particularly concerning as it can be exploited to abuse the Web Explorer server as a proxy for web attacks on third parties and interact with servers in the local network, including reading their response data. This could potentially lead to arbitrary code execution, depending on the nature of the local services. The vulnerability is limited to GET requests, as POST requests are not possible, but the impact on confidentiality, integrity, and availability is significant due to the potential for stolen credentials and state-changing interactions with internal APIs. | 2024-06-06 | not yet calculated | |
| libaom--libaom | Integer overflow in libaom internal function img_alloc_helper can lead to heap buffer overflow. This function can be reached via 3 callers: * Calling aom_img_alloc() with a large value of the d_w, d_h, or align parameter may result in integer overflows in the calculations of buffer sizes and offsets and some fields of the returned aom_image_t struct may be invalid. * Calling aom_img_wrap() with a large value of the d_w, d_h, or align parameter may result in integer overflows in the calculations of buffer sizes and offsets and some fields of the returned aom_image_t struct may be invalid. * Calling aom_img_alloc_with_border() with a large value of the d_w, d_h, align, size_align, or border parameter may result in integer overflows in the calculations of buffer sizes and offsets and some fields of the returned aom_image_t struct may be invalid. | 2024-06-05 | not yet calculated | |
| lightning-ai--lightning-ai/pytorch-lightning | A remote code execution (RCE) vulnerability exists in the lightning-ai/pytorch-lightning library version 2.2.1 due to improper handling of deserialized user input and mismanagement of dunder attributes by the `deepdiff` library. The library uses `deepdiff.Delta` objects to modify application state based on frontend actions. However, it is possible to bypass the intended restrictions on modifying dunder attributes, allowing an attacker to construct a serialized delta that passes the deserializer whitelist and contains dunder attributes. When processed, this can be exploited to access other modules, classes, and instances, leading to arbitrary attribute write and total RCE on any self-hosted pytorch-lightning application in its default configuration, as the delta endpoint is enabled by default. | 2024-06-06 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: drm/vmwgfx: Fix invalid reads in fence signaled events Correctly set the length of the drm_event to the size of the structure that's actually used. The length of the drm_event was set to the parent structure instead of to the drm_vmw_event_fence which is supposed to be read. drm_read uses the length parameter to copy the event to the user space thus resuling in oob reads. | 2024-06-03 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: thermal/debugfs: Fix two locking issues with thermal zone debug With the current thermal zone locking arrangement in the debugfs code, user space can open the "mitigations" file for a thermal zone before the zone's debugfs pointer is set which will result in a NULL pointer dereference in tze_seq_start(). Moreover, thermal_debug_tz_remove() is not called under the thermal zone lock, so it can run in parallel with the other functions accessing the thermal zone's struct thermal_debugfs object. Then, it may clear tz->debugfs after one of those functions has checked it and the struct thermal_debugfs object may be freed prematurely. To address the first problem, pass a pointer to the thermal zone's struct thermal_debugfs object to debugfs_create_file() in thermal_debug_tz_add() and make tze_seq_start(), tze_seq_next(), tze_seq_stop(), and tze_seq_show() retrieve it from s->private instead of a pointer to the thermal zone object. This will ensure that tz_debugfs will be valid across the "mitigations" file accesses until thermal_debugfs_remove_id() called by thermal_debug_tz_remove() removes that file. To address the second problem, use tz->lock in thermal_debug_tz_remove() around the tz->debugfs value check (in case the same thermal zone is removed at the same time in two different threads) and its reset to NULL. Cc :6.8+ <[email protected]> # 6.8+ | 2024-06-03 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: net: ks8851: Queue RX packets in IRQ handler instead of disabling BHs Currently the driver uses local_bh_disable()/local_bh_enable() in its IRQ handler to avoid triggering net_rx_action() softirq on exit from netif_rx(). The net_rx_action() could trigger this driver .start_xmit callback, which is protected by the same lock as the IRQ handler, so calling the .start_xmit from netif_rx() from the IRQ handler critical section protected by the lock could lead to an attempt to claim the already claimed lock, and a hang. The local_bh_disable()/local_bh_enable() approach works only in case the IRQ handler is protected by a spinlock, but does not work if the IRQ handler is protected by mutex, i.e. this works for KS8851 with Parallel bus interface, but not for KS8851 with SPI bus interface. Remove the BH manipulation and instead of calling netif_rx() inside the IRQ handler code protected by the lock, queue all the received SKBs in the IRQ handler into a queue first, and once the IRQ handler exits the critical section protected by the lock, dequeue all the queued SKBs and push them all into netif_rx(). At this point, it is safe to trigger the net_rx_action() softirq, since the netif_rx() call is outside of the lock that protects the IRQ handler. | 2024-06-03 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: tracefs: Reset permissions on remount if permissions are options There's an inconsistency with the way permissions are handled in tracefs. Because the permissions are generated when accessed, they default to the root inode's permission if they were never set by the user. If the user sets the permissions, then a flag is set and the permissions are saved via the inode (for tracefs files) or an internal attribute field (for eventfs). But if a remount happens that specify the permissions, all the files that were not changed by the user gets updated, but the ones that were are not. If the user were to remount the file system with a given permission, then all files and directories within that file system should be updated. This can cause security issues if a file's permission was updated but the admin forgot about it. They could incorrectly think that remounting with permissions set would update all files, but miss some. For example: # cd /sys/kernel/tracing # chgrp 1002 current_tracer # ls -l [..] -rw-r----- 1 root root 0 May 1 21:25 buffer_size_kb -rw-r----- 1 root root 0 May 1 21:25 buffer_subbuf_size_kb -r--r----- 1 root root 0 May 1 21:25 buffer_total_size_kb -rw-r----- 1 root lkp 0 May 1 21:25 current_tracer -rw-r----- 1 root root 0 May 1 21:25 dynamic_events -r--r----- 1 root root 0 May 1 21:25 dyn_ftrace_total_info -r--r----- 1 root root 0 May 1 21:25 enabled_functions Where current_tracer now has group "lkp". # mount -o remount,gid=1001 . # ls -l -rw-r----- 1 root tracing 0 May 1 21:25 buffer_size_kb -rw-r----- 1 root tracing 0 May 1 21:25 buffer_subbuf_size_kb -r--r----- 1 root tracing 0 May 1 21:25 buffer_total_size_kb -rw-r----- 1 root lkp 0 May 1 21:25 current_tracer -rw-r----- 1 root tracing 0 May 1 21:25 dynamic_events -r--r----- 1 root tracing 0 May 1 21:25 dyn_ftrace_total_info -r--r----- 1 root tracing 0 May 1 21:25 enabled_functions Everything changed but the "current_tracer". Add a new link list that keeps track of all the tracefs_inodes which has the permission flags that tell if the file/dir should use the root inode's permission or not. Then on remount, clear all the flags so that the default behavior of using the root inode's permission is done for all files and directories. | 2024-06-03 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: fs/9p: only translate RWX permissions for plain 9P2000 Garbage in plain 9P2000's perm bits is allowed through, which causes it to be able to set (among others) the suid bit. This was presumably not the intent since the unix extended bits are handled explicitly and conditionally on .u. | 2024-06-03 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: remoteproc: mediatek: Make sure IPI buffer fits in L2TCM The IPI buffer location is read from the firmware that we load to the System Companion Processor, and it's not granted that both the SRAM (L2TCM) size that is defined in the devicetree node is large enough for that, and while this is especially true for multi-core SCP, it's still useful to check on single-core variants as well. Failing to perform this check may make this driver perform R/W operations out of the L2TCM boundary, resulting (at best) in a kernel panic. To fix that, check that the IPI buffer fits, otherwise return a failure and refuse to boot the relevant SCP core (or the SCP at all, if this is single core). | 2024-06-08 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: erofs: reliably distinguish block based and fscache mode When erofs_kill_sb() is called in block dev based mode, s_bdev may not have been initialised yet, and if CONFIG_EROFS_FS_ONDEMAND is enabled, it will be mistaken for fscache mode, and then attempt to free an anon_dev that has never been allocated, triggering the following warning: ============================================ ida_free called for id=0 which is not allocated. WARNING: CPU: 14 PID: 926 at lib/idr.c:525 ida_free+0x134/0x140 Modules linked in: CPU: 14 PID: 926 Comm: mount Not tainted 6.9.0-rc3-dirty #630 RIP: 0010:ida_free+0x134/0x140 Call Trace: <TASK> erofs_kill_sb+0x81/0x90 deactivate_locked_super+0x35/0x80 get_tree_bdev+0x136/0x1e0 vfs_get_tree+0x2c/0xf0 do_new_mount+0x190/0x2f0 [...] ============================================ Now when erofs_kill_sb() is called, erofs_sb_info must have been initialised, so use sbi->fsid to distinguish between the two modes. | 2024-06-08 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: KEYS: trusted: Fix memory leak in tpm2_key_encode() 'scratch' is never freed. Fix this by calling kfree() in the success, and in the error case. | 2024-06-08 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: Bluetooth: L2CAP: Fix div-by-zero in l2cap_le_flowctl_init() l2cap_le_flowctl_init() can cause both div-by-zero and an integer overflow since hdev->le_mtu may not fall in the valid range. Move MTU from hci_dev to hci_conn to validate MTU and stop the connection process earlier if MTU is invalid. Also, add a missing validation in read_buffer_size() and make it return an error value if the validation fails. Now hci_conn_add() returns ERR_PTR() as it can fail due to the both a kzalloc failure and invalid MTU value. divide error: 0000 [#1] PREEMPT SMP KASAN NOPTI CPU: 0 PID: 67 Comm: kworker/u5:0 Tainted: G W 6.9.0-rc5+ #20 Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS 1.15.0-1 04/01/2014 Workqueue: hci0 hci_rx_work RIP: 0010:l2cap_le_flowctl_init+0x19e/0x3f0 net/bluetooth/l2cap_core.c:547 Code: e8 17 17 0c 00 66 41 89 9f 84 00 00 00 bf 01 00 00 00 41 b8 02 00 00 00 4c 89 fe 4c 89 e2 89 d9 e8 27 17 0c 00 44 89 f0 31 d2 <66> f7 f3 89 c3 ff c3 4d 8d b7 88 00 00 00 4c 89 f0 48 c1 e8 03 42 RSP: 0018:ffff88810bc0f858 EFLAGS: 00010246 RAX: 00000000000002a0 RBX: 0000000000000000 RCX: dffffc0000000000 RDX: 0000000000000000 RSI: ffff88810bc0f7c0 RDI: ffffc90002dcb66f RBP: ffff88810bc0f880 R08: aa69db2dda70ff01 R09: 0000ffaaaaaaaaaa R10: 0084000000ffaaaa R11: 0000000000000000 R12: ffff88810d65a084 R13: dffffc0000000000 R14: 00000000000002a0 R15: ffff88810d65a000 FS: 0000000000000000(0000) GS:ffff88811ac00000(0000) knlGS:0000000000000000 CS: 0010 DS: 0000 ES: 0000 CR0: 0000000080050033 CR2: 0000000020000100 CR3: 0000000103268003 CR4: 0000000000770ef0 PKRU: 55555554 Call Trace: <TASK> l2cap_le_connect_req net/bluetooth/l2cap_core.c:4902 [inline] l2cap_le_sig_cmd net/bluetooth/l2cap_core.c:5420 [inline] l2cap_le_sig_channel net/bluetooth/l2cap_core.c:5486 [inline] l2cap_recv_frame+0xe59d/0x11710 net/bluetooth/l2cap_core.c:6809 l2cap_recv_acldata+0x544/0x10a0 net/bluetooth/l2cap_core.c:7506 hci_acldata_packet net/bluetooth/hci_core.c:3939 [inline] hci_rx_work+0x5e5/0xb20 net/bluetooth/hci_core.c:4176 process_one_work kernel/workqueue.c:3254 [inline] process_scheduled_works+0x90f/0x1530 kernel/workqueue.c:3335 worker_thread+0x926/0xe70 kernel/workqueue.c:3416 kthread+0x2e3/0x380 kernel/kthread.c:388 ret_from_fork+0x5c/0x90 arch/x86/kernel/process.c:147 ret_from_fork_asm+0x1a/0x30 arch/x86/entry/entry_64.S:244 </TASK> Modules linked in: ---[ end trace 0000000000000000 ]--- | 2024-06-08 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: drm/amd/display: Fix division by zero in setup_dsc_config When slice_height is 0, the division by slice_height in the calculation of the number of slices will cause a division by zero driver crash. This leaves the kernel in a state that requires a reboot. This patch adds a check to avoid the division by zero. The stack trace below is for the 6.8.4 Kernel. I reproduced the issue on a Z16 Gen 2 Lenovo Thinkpad with a Apple Studio Display monitor connected via Thunderbolt. The amdgpu driver crashed with this exception when I rebooted the system with the monitor connected. kernel: ? die (arch/x86/kernel/dumpstack.c:421 arch/x86/kernel/dumpstack.c:434 arch/x86/kernel/dumpstack.c:447) kernel: ? do_trap (arch/x86/kernel/traps.c:113 arch/x86/kernel/traps.c:154) kernel: ? setup_dsc_config (drivers/gpu/drm/amd/amdgpu/../display/dc/dsc/dc_dsc.c:1053) amdgpu kernel: ? do_error_trap (./arch/x86/include/asm/traps.h:58 arch/x86/kernel/traps.c:175) kernel: ? setup_dsc_config (drivers/gpu/drm/amd/amdgpu/../display/dc/dsc/dc_dsc.c:1053) amdgpu kernel: ? exc_divide_error (arch/x86/kernel/traps.c:194 (discriminator 2)) kernel: ? setup_dsc_config (drivers/gpu/drm/amd/amdgpu/../display/dc/dsc/dc_dsc.c:1053) amdgpu kernel: ? asm_exc_divide_error (./arch/x86/include/asm/idtentry.h:548) kernel: ? setup_dsc_config (drivers/gpu/drm/amd/amdgpu/../display/dc/dsc/dc_dsc.c:1053) amdgpu kernel: dc_dsc_compute_config (drivers/gpu/drm/amd/amdgpu/../display/dc/dsc/dc_dsc.c:1109) amdgpu After applying this patch, the driver no longer crashes when the monitor is connected and the system is rebooted. I believe this is the same issue reported for 3113. | 2024-06-08 | not yet calculated | |
| Linux--Linux | In the Linux kernel, the following vulnerability has been resolved: wifi: iwlwifi: Use request_module_nowait This appears to work around a deadlock regression that came in with the LED merge in 6.9. The deadlock happens on my system with 24 iwlwifi radios, so maybe it something like all worker threads are busy and some work that needs to complete cannot complete. [also remove unnecessary "load_module" var and now-wrong comment] | 2024-06-08 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | An improper access control vulnerability exists in lunary-ai/lunary versions up to and including 1.2.2, where an admin can update any organization user to the organization owner. This vulnerability allows the elevated user to delete projects within the organization. The issue is resolved in version 1.2.7. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In lunary-ai/lunary version v1.2.13, an improper authorization vulnerability exists that allows unauthorized users to access and manipulate projects within an organization they should not have access to. Specifically, the vulnerability is located in the `checkProjectAccess` method within the authorization middleware, which fails to adequately verify if a user has the correct permissions to access a specific project. Instead, it only checks if the user is part of the organization owning the project, overlooking the necessary check against the `account_project` table for explicit project access rights. This flaw enables attackers to gain complete control over all resources within a project, including the ability to create, update, read, and delete any resource, compromising the privacy and security of sensitive information. | 2024-06-08 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | An improper access control vulnerability exists in the lunary-ai/lunary repository, specifically within the versions.patch functionality for updating prompts. Affected versions include 1.2.2 up to but not including 1.2.25. The vulnerability allows unauthorized users to update prompt details due to insufficient access control checks. This issue was addressed and fixed in version 1.2.25. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In lunary-ai/lunary versions 1.2.2 through 1.2.25, an improper access control vulnerability allows users on the Free plan to invite other members and assign them any role, including those intended for Paid and Enterprise plans only. This issue arises due to insufficient backend validation of roles and permissions, enabling unauthorized users to join a project and potentially exploit roles and permissions not intended for their use. The vulnerability specifically affects the Team feature, where the backend fails to validate whether a user has paid for a plan before allowing them to send invite links with any role assigned. This could lead to unauthorized access and manipulation of project settings or data. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | An Insecure Direct Object Reference (IDOR) vulnerability was identified in lunary-ai/lunary, affecting versions up to and including 1.2.2. This vulnerability allows unauthorized users to view, update, or delete any dataset_prompt or dataset_prompt_variation within any dataset or project. The issue stems from improper access control checks in the dataset management endpoints, where direct references to object IDs are not adequately secured against unauthorized access. This vulnerability was fixed in version 1.2.25. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | A Privilege Escalation Vulnerability exists in lunary-ai/lunary version 1.2.2, where any user can delete any datasets due to missing authorization checks. The vulnerability is present in the dataset deletion functionality, where the application fails to verify if the user requesting the deletion has the appropriate permissions. This allows unauthorized users to send a DELETE request to the server and delete any dataset by specifying its ID. The issue is located in the datasets.delete function within the datasets index file. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | An Incorrect Authorization vulnerability exists in lunary-ai/lunary versions up to and including 1.2.2, which allows unauthenticated users to delete any dataset. The vulnerability is due to the lack of proper authorization checks in the dataset deletion endpoint. Specifically, the endpoint does not verify if the provided project ID belongs to the current user, thereby allowing any dataset to be deleted without proper authentication. This issue was fixed in version 1.2.8. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | An Improper Access Control vulnerability exists in the lunary-ai/lunary repository, affecting versions up to and including 1.2.2. The vulnerability allows unauthorized users to view any prompts in any projects by supplying a specific prompt ID to an endpoint that does not adequately verify the ownership of the prompt ID. This issue was fixed in version 1.2.25. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In lunary-ai/lunary version 1.2.4, an account takeover vulnerability exists due to the exposure of password recovery tokens in API responses. Specifically, when a user initiates the password reset process, the recovery token is included in the response of the `GET /v1/users/me/org` endpoint, which lists all users in a team. This allows any authenticated user to capture the recovery token of another user and subsequently change that user's password without consent, effectively taking over the account. The issue lies in the inclusion of the `recovery_token` attribute in the users object returned by the API. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In lunary-ai/lunary version 1.2.5, an improper access control vulnerability exists due to a missing permission check in the `GET /v1/users/me/org` endpoint. The platform's role definitions restrict the `Prompt Editor` role to prompt management and project viewing/listing capabilities, explicitly excluding access to user information. However, the endpoint fails to enforce this restriction, allowing users with the `Prompt Editor` role to access the full list of users in the organization. This vulnerability allows unauthorized access to sensitive user information, violating the intended access controls. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | In lunary-ai/lunary version 1.2.4, a vulnerability exists in the password recovery mechanism where the reset password token is not invalidated after use. This allows an attacker who compromises the recovery token to repeatedly change the password of a victim's account. The issue lies in the backend's handling of the reset password process, where the token, once used, is not discarded or invalidated, enabling its reuse. This vulnerability could lead to unauthorized account access if an attacker obtains the recovery token. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | A Server-Side Request Forgery (SSRF) vulnerability exists in the lunary-ai/lunary application, specifically within the endpoint '/auth/saml/tto/download-idp-xml'. The vulnerability arises due to the application's failure to validate user-supplied URLs before using them in server-side requests. An attacker can exploit this vulnerability by sending a specially crafted request to the affected endpoint, allowing them to make unauthorized requests to internal or external resources. This could lead to the disclosure of sensitive information, service disruption, or further attacks against the network infrastructure. The issue affects the latest version of the application as of the report. | 2024-06-06 | not yet calculated | |
| lunary-ai--lunary-ai/lunary | A Cross-site Scripting (XSS) vulnerability exists in the SAML metadata endpoint `/auth/saml/${org?.id}/metadata` of lunary-ai/lunary version 1.2.7. The vulnerability arises due to the application's failure to escape or validate the `orgId` parameter supplied by the user before incorporating it into the generated response. Specifically, the endpoint generates XML responses for SAML metadata, where the `orgId` parameter is directly embedded into the XML structure without proper sanitization or validation. This flaw allows an attacker to inject arbitrary JavaScript code into the generated SAML metadata page, leading to potential theft of user cookies or authentication tokens. | 2024-06-06 | not yet calculated | |
| Luxion--KeyShot Viewer | Luxion KeyShot Viewer KSP File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Luxion KeyShot Viewer. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of KSP files. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22449. | 2024-06-06 | not yet calculated | |
| Luxion--KeyShot Viewer | Luxion KeyShot Viewer KSP File Parsing Use-After-Free Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Luxion KeyShot Viewer. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of KSP files. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22515. | 2024-06-06 | not yet calculated | |
| Luxion--KeyShot Viewer | Luxion KeyShot Viewer KSP File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Luxion KeyShot Viewer. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of KSP files. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22514. | 2024-06-06 | not yet calculated | |
| Luxion--KeyShot Viewer | Luxion KeyShot Viewer KSP File Parsing Stack-based Buffer Overflow Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Luxion KeyShot Viewer. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of KSP files. The issue results from the lack of proper validation of the length of user-supplied data prior to copying it to a stack-based buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22266. | 2024-06-06 | not yet calculated | |
| Luxion--KeyShot Viewer | Luxion KeyShot Viewer KSP File Parsing Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Luxion KeyShot Viewer. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of KSP files. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22267. | 2024-06-06 | not yet calculated | |
| Luxion--KeyShot | Luxion KeyShot BIP File Parsing Uncontrolled Search Path Element Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of Luxion KeyShot. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the parsing of BIP files. The issue results from loading a library from an unsecured location. An attacker can leverage this vulnerability to execute code in the context of the current process. Was ZDI-CAN-22738. | 2024-06-06 | not yet calculated | |
| man-group--man-group/dtale | man-group/dtale version 3.10.0 is vulnerable to an authentication bypass and remote code execution (RCE) due to improper input validation. The vulnerability arises from a hardcoded `SECRET_KEY` in the flask configuration, allowing attackers to forge a session cookie if authentication is enabled. Additionally, the application fails to properly restrict custom filter queries, enabling attackers to execute arbitrary code on the server by bypassing the restriction on the `/update-settings` endpoint, even when `enable_custom_filters` is not enabled. This vulnerability allows attackers to bypass authentication mechanisms and execute remote code on the server. | 2024-06-06 | not yet calculated | |
| MediaTek, Inc.--MT6298, MT6813, MT6815, MT6833, MT6835, MT6853, MT6855, MT6873, MT6875, MT6875T, MT6877, MT6878, MT6879, MT6883, MT6885, MT6889, MT6891, MT6893, MT6895, MT6895T, MT6896, MT6897, MT6980, MT6980D, MT6983, MT6990, MT8673, MT8675, MT8765, MT8766, MT8768, MT8771, MT8786, MT8791T, MT8792, MT8797, MT8798 | In modem, there is a possible information disclosure due to using risky cryptographic algorithm during connection establishment negotiation. This could lead to remote information disclosure, when weak encryption algorithm is used, with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: MOLY00942482; Issue ID: MSV-1469. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6298, MT6813, MT6815, MT6835, MT6878, MT6879, MT6895, MT6895T, MT6896, MT6897, MT6899, MT6980, MT6980D, MT6983, MT6986, MT6986D, MT6990, MT6991, MT8673, MT8675, MT8771, MT8791T, MT8792, MT8797, MT8798 | In modem, there is a possible system crash due to improper input validation. This could lead to remote denial of service with no additional execution privileges needed. User interaction is no needed for exploitation. Patch ID: MOLY01270721; Issue ID: MSV-1479. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6298, MT6813, MT6815, MT6835, MT6878, MT6879, MT6895, MT6895T, MT6896, MT6897, MT6899, MT6980, MT6980D, MT6983, MT6986, MT6986D, MT6990, MT6991, MT8673, MT8792, MT8798 | In modem, there is a possible out of bounds write due to an incorrect bounds check. This could lead to remote denial of service with no additional execution privileges needed. User interaction is no needed for exploitation. Patch ID: MOLY01267281; Issue ID: MSV-1477. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6580, MT6739, MT6761, MT6765, MT6768, MT6779, MT6781, MT6785, MT6789, MT6833, MT6835, MT6853, MT6855, MT6873, MT6877, MT6879, MT6883, MT6885, MT6886, MT6889, MT6893, MT6895, MT6897, MT6983, MT6985, MT6989, MT8666, MT8667, MT8673, MT8676 | In dmc, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS08668110; Issue ID: MSV-1333. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6768, MT6781, MT6835, MT6853, MT6855, MT6877, MT6879, MT6885, MT6886, MT6893, MT6983, MT6985, MT6989 | In telephony, there is a possible information disclosure due to a missing permission check. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS08698617; Issue ID: MSV-1394. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6813, MT6815, MT6835, MT6878, MT6897, MT6899, MT6986, MT6986D, MT6991, MT8792 | In modem, there is a possible out of bounds write due to improper input invalidation. This could lead to remote denial of service with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: MOLY01267285; Issue ID: MSV-1462. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6833, MT6853, MT6855, MT6873, MT6875, MT6875T, MT6877, MT6883, MT6885, MT6889, MT6891, MT6893, MT8675, MT8771, MT8791T, MT8797 | In modem, there is a possible selection of less-secure algorithm during the VoWiFi IKE due to a missing DH downgrade check. This could lead to remote information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation. Patch ID: MOLY01286330; Issue ID: MSV-1430. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6833, MT6853, MT6873, MT6877, MT6885, MT6893, MT8185, MT8675, MT8786, MT8789 | In eemgpu, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS08713302; Issue ID: MSV-1393. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6890, MT6990, MT7622 | In wlan driver, there is a possible out of bounds read due to improper input validation. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: WCNCR00364733; Issue ID: MSV-1331. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6890, MT6990, MT7622 | In wlan driver, there is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: WCNCR00364732; Issue ID: MSV-1332. | 2024-06-03 | not yet calculated | |
| MediaTek, Inc.--MT6890, MT7622 | In wlan service, there is a possible out of bounds write due to improper input validation. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: WCNCR00367704; Issue ID: MSV-1411. | 2024-06-03 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | An improper authorization vulnerability exists in the mintplex-labs/anything-llm application, specifically within the '/api/v/' endpoint and its sub-routes. This flaw allows unauthenticated users to perform destructive actions on the VectorDB, including resetting the database and deleting specific namespaces, without requiring any authorization or permissions. The issue affects all versions up to and including the latest version, with a fix introduced in version 1.0.0. Exploitation of this vulnerability can lead to complete data loss of document embeddings across all workspaces, rendering workspace chats and embeddable chat widgets non-functional. Additionally, attackers can list all namespaces, potentially exposing private workspace names. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | A JSON Injection vulnerability exists in the `mintplex-labs/anything-llm` application, specifically within the username parameter during the login process at the `/api/request-token` endpoint. The vulnerability arises from improper handling of values, allowing attackers to perform brute force attacks without prior knowledge of the username. Once the password is known, attackers can conduct blind attacks to ascertain the full username, significantly compromising system security. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | A remote code execution vulnerability exists in mintplex-labs/anything-llm due to improper handling of environment variables. Attackers can exploit this vulnerability by injecting arbitrary environment variables via the `POST /api/system/update-env` endpoint, which allows for the execution of arbitrary code on the host running anything-llm. The vulnerability is present in the latest version of anything-llm, with the latest commit identified as fde905aac1812b84066ff72e5f2f90b56d4c3a59. This issue has been fixed in version 1.0.0. Successful exploitation could lead to code execution on the host, enabling attackers to read and modify data accessible to the user running the service, potentially leading to a denial of service. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | A stored Cross-Site Scripting (XSS) vulnerability exists in the mintplex-labs/anything-llm application, affecting versions up to and including the latest before 1.0.0. The vulnerability arises from the application's failure to properly sanitize and validate user-supplied URLs before embedding them into the application UI as external links with custom icons. Specifically, the application does not prevent the inclusion of 'javascript:' protocol payloads in URLs, which can be exploited by a user with manager role to execute arbitrary JavaScript code in the context of another user's session. This flaw can be leveraged to steal the admin's authorization token by crafting malicious URLs that, when clicked by the admin, send the token to an attacker-controlled server. The attacker can then use this token to perform unauthorized actions, escalate privileges to admin, or directly take over the admin account. The vulnerability is triggered when the malicious link is opened in a new tab using either the CTRL + left mouse button click or the mouse scroll wheel click, or in some non-updated versions of modern browsers, by directly clicking on the link. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | A Server-Side Request Forgery (SSRF) vulnerability exists in the upload link feature of mintplex-labs/anything-llm. This feature, intended for users with manager or admin roles, processes uploaded links through an internal Collector API using a headless browser. An attacker can exploit this by hosting a malicious website and using it to perform actions such as internal port scanning, accessing internal web applications not exposed externally, and interacting with the Collector API. This interaction can lead to unauthorized actions such as arbitrary file deletion and limited Local File Inclusion (LFI), including accessing NGINX access logs which may contain sensitive information. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | In mintplex-labs/anything-llm, a vulnerability exists in the thread update process that allows users with Default or Manager roles to escalate their privileges to Administrator. The issue arises from improper input validation when handling HTTP POST requests to the endpoint `/workspace/:slug/thread/:threadSlug/update`. Specifically, the application fails to validate or check user input before passing it to the `workspace_thread` Prisma model for execution. This oversight allows attackers to craft a Prisma relation query operation that manipulates the `users` model to change a user's role to admin. Successful exploitation grants attackers the highest level of user privileges, enabling them to see and perform all actions within the system. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | mintplex-labs/anything-llm is vulnerable to multiple security issues due to improper input validation in several endpoints. An attacker can exploit these vulnerabilities to escalate privileges from a default user role to an admin role, read and delete arbitrary files on the system, and perform Server-Side Request Forgery (SSRF) attacks. The vulnerabilities are present in the `/request-token`, `/workspace/:slug/thread/:threadSlug/update`, `/system/remove-logo`, `/system/logo`, and collector's `/process` endpoints. These issues are due to the application's failure to properly validate user input before passing it to `prisma` functions and other critical operations. Affected versions include the latest version prior to 1.0.0. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | mintplex-labs/anything-llm is affected by an uncontrolled resource consumption vulnerability in its upload file endpoint, leading to a denial of service (DOS) condition. Specifically, the server can be shut down by sending an invalid upload request. An attacker with the ability to upload documents can exploit this vulnerability to cause a DOS condition by manipulating the upload request. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | A Cross-Site Scripting (XSS) vulnerability exists in mintplex-labs/anything-llm, affecting both the desktop application version 1.2.0 and the latest version of the web application. The vulnerability arises from the application's feature to fetch and embed content from websites into workspaces, which can be exploited to execute arbitrary JavaScript code. In the desktop application, this flaw can be escalated to Remote Code Execution (RCE) due to insecure application settings, specifically the enabling of 'nodeIntegration' and the disabling of 'contextIsolation' in Electron's webPreferences. The issue has been addressed in version 1.4.2 of the desktop application. | 2024-06-06 | not yet calculated | |
| mintplex-labs--mintplex-labs/anything-llm | A Server-Side Request Forgery (SSRF) vulnerability exists in the latest version of mintplex-labs/anything-llm, allowing attackers to bypass the official fix intended to restrict access to intranet IP addresses and protocols. Despite efforts to filter out intranet IP addresses starting with 192, 172, 10, and 127 through regular expressions and limit access protocols to HTTP and HTTPS, attackers can still bypass these restrictions using alternative representations of IP addresses and accessing other ports running on localhost. This vulnerability enables attackers to access any asset on the internal network, attack web services on the internal network, scan hosts on the internal network, and potentially access AWS metadata endpoints. The vulnerability is due to insufficient validation of user-supplied URLs, which can be exploited to perform SSRF attacks. | 2024-06-05 | not yet calculated | |
| mlflow--mlflow/mlflow | A vulnerability in mlflow/mlflow version 8.2.1 allows for remote code execution due to improper neutralization of special elements used in an OS command ('Command Injection') within the `mlflow.data.http_dataset_source.py` module. Specifically, when loading a dataset from a source URL with an HTTP scheme, the filename extracted from the `Content-Disposition` header or the URL path is used to generate the final file path without proper sanitization. This flaw enables an attacker to control the file path fully by utilizing path traversal or absolute path techniques, such as '../../tmp/poc.txt' or '/tmp/poc.txt', leading to arbitrary file write. Exploiting this vulnerability could allow a malicious user to execute commands on the vulnerable machine, potentially gaining access to data and model information. The issue is fixed in version 2.9.0. | 2024-06-06 | not yet calculated | |
| mlflow--mlflow/mlflow | A Local File Inclusion (LFI) vulnerability was identified in mlflow/mlflow, specifically in version 2.9.2, which was fixed in version 2.11.3. This vulnerability arises from the application's failure to properly validate URI fragments for directory traversal sequences such as '../'. An attacker can exploit this flaw by manipulating the fragment part of the URI to read arbitrary files on the local file system, including sensitive files like '/etc/passwd'. The vulnerability is a bypass to a previous patch that only addressed similar manipulation within the URI's query string, highlighting the need for comprehensive validation of all parts of a URI to prevent LFI attacks. | 2024-06-06 | not yet calculated | |
| mlflow--mlflow/mlflow | A vulnerability in mlflow/mlflow version 2.11.1 allows attackers to create multiple models with the same name by exploiting URL encoding. This flaw can lead to Denial of Service (DoS) as an authenticated user might not be able to use the intended model, as it will open a different model each time. Additionally, an attacker can exploit this vulnerability to perform data model poisoning by creating a model with the same name, potentially causing an authenticated user to become a victim by using the poisoned model. The issue stems from inadequate validation of model names, allowing for the creation of models with URL-encoded names that are treated as distinct from their URL-decoded counterparts. | 2024-06-06 | not yet calculated | |
| n/a--n/a | Precor touchscreen console P62, P80, and P82 could allow a remote attacker (within the local network) to bypass security restrictions, and access the service menu, because there is a hard-coded service code. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Precor touchscreen console P82 contains a private SSH key that corresponds to a default public key. A remote attacker could exploit this to gain root privileges. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Precor touchscreen console P62, P80, and P82 could allow a remote attacker to obtain sensitive information because the root password is stored in /etc/passwd. An attacker could exploit this to extract files and obtain sensitive information. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Precor touchscreen console P62, P80, and P82 contains a default SSH public key in the authorized_keys file. A remote attacker could use this key to gain root privileges. | 2024-06-07 | not yet calculated | |
| n/a--n/a | dnsmasq 2.9 is vulnerable to Integer Overflow via forward_query. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An issue was discovered in Samsung Mobile Processor, Automotive Processor, Wearable Processor, and Modem Exynos 980, 990, 850, 1080, 2100, 2200, 1280, 1380, 1330, 9110, W920, Exynos Modem 5123, Exynos Modem 5300, and Exynos Auto T5123. The baseband software does not properly check states specified by the RRC. This can lead to disclosure of sensitive information. | 2024-06-05 | not yet calculated | |
| n/a--n/a | A deep link validation issue in KakaoTalk 10.4.3 allowed a remote adversary to direct users to run any attacker-controller JavaScript within a WebView. The impact was further escalated by triggering another WebView that leaked its access token in a HTTP request header. Ultimately, this access token could be used to takeover another user's account and read her/his chat messages. | 2024-06-03 | not yet calculated | |
| n/a--n/a | An issue in obgm and Libcoap v.a3ed466 allows a remote attacker to cause a denial of service via thecoap_context_t function in the src/coap_threadsafe.c:297:3 component. | 2024-06-06 | not yet calculated | |
| n/a--n/a | Mercusys MW325R EU V3 (Firmware MW325R(EU)_V3_1.11.0 Build 221019) is vulnerable to a stack-based buffer overflow, which could allow an attacker to execute arbitrary code. Exploiting the vulnerability requires authentication. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Dynamsoft Service 1.8.1025 through 1.8.2013, 1.7.0330 through 1.7.2531, 1.6.0428 through 1.6.1112, 1.5.0625 through 1.5.3116, 1.4.0618 through 1.4.1230, and 1.0.516 through 1.3.0115 has Incorrect Access Control. This is fixed in 1.8.2014, 1.7.4212, 1.6.3212, 1.5.31212, 1.4.3212, and 1.3.3212. | 2024-06-06 | not yet calculated | |
| n/a--n/a | dnspod-sr 0dfbd37 is vulnerable to buffer overflow. | 2024-06-06 | not yet calculated | |
| n/a--n/a | dnspod-sr 0dfbd37 contains a SEGV. | 2024-06-06 | not yet calculated | |
| n/a--n/a | robdns commit d76d2e6 was discovered to contain a heap overflow via the component block->filename at /src/zonefile-insertion.c. | 2024-06-06 | not yet calculated | |
| n/a--n/a | robdns commit d76d2e6 was discovered to contain a NULL pointer dereference via the item->tokens component at /src/conf-parse.c. | 2024-06-06 | not yet calculated | |
| n/a--n/a | robdns commit d76d2e6 was discovered to contain a misaligned address at /src/zonefile-insertion.c. | 2024-06-06 | not yet calculated | |
| n/a--n/a | smartdns commit 54b4dc was discovered to contain a misaligned address at smartdns/src/util.c. | 2024-06-06 | not yet calculated | |
| n/a--n/a | smartdns commit 54b4dc was discovered to contain a misaligned address at smartdns/src/dns.c. | 2024-06-06 | not yet calculated | |
| n/a--n/a | Invision Community through 4.7.16 allows remote code execution via the applications/core/modules/admin/editor/toolbar.php IPS\core\modules\admin\editor\_toolbar::addPlugin() method. This method handles uploaded ZIP files that are extracted into the applications/core/interface/ckeditor/ckeditor/plugins/ directory without properly verifying their content. This can be exploited by admin users (with the toolbar_manage permission) to write arbitrary PHP files into that directory, leading to execution of arbitrary PHP code in the context of the web server user. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Invision Community before 4.7.16 allow SQL injection via the applications/nexus/modules/front/store/store.php IPS\nexus\modules\front\store\_store::_categoryView() method, where user input passed through the filter request parameter is not properly sanitized before being used to execute SQL queries. This can be exploited by unauthenticated attackers to carry out Blind SQL Injection attacks. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Incorrect access control in the fingerprint authentication mechanism of Phone Cleaner: Boost & Clean v2.2.0 allows attackers to bypass fingerprint authentication due to the use of a deprecated API. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Incorrect access control in the fingerprint authentication mechanism of Bitdefender Mobile Security v4.11.3-gms allows attackers to bypass fingerprint authentication due to the use of a deprecated API. | 2024-06-03 | not yet calculated | |
| n/a--n/a | The DNS protocol in RFC 1035 and updates allows remote attackers to cause a denial of service (resource consumption) by arranging for DNS queries to be accumulated for seconds, such that responses are later sent in a pulsing burst (which can be considered traffic amplification in some cases), aka the "DNSBomb" issue. | 2024-06-06 | not yet calculated | |
| n/a--n/a | A Reflected Cross-site scripting (XSS) vulnerability located in htdocs/compta/paiement/card.php of Dolibarr before 19.0.2 allows remote attackers to inject arbitrary web script or HTML via a crafted payload injected into the facid parameter. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Cyrus IMAP before 3.8.3 and 3.10.x before 3.10.0-rc1 allows authenticated attackers to cause unbounded memory allocation by sending many LITERALs in a single command. | 2024-06-05 | not yet calculated | |
| n/a--n/a | Directory Traversal vulnerability in CubeCart v.6.5.5 and before allows an attacker to execute arbitrary code via a crafted file uploaded to the _g and node parameters. | 2024-06-06 | not yet calculated | |
| n/a--n/a | A SQL Injection vulnerability exists in the `ofrs/admin/index.php` script of PHPGurukul Online Fire Reporting System 1.2. The vulnerability allows attackers to bypass authentication and gain unauthorized access by injecting SQL commands into the username input field during the login process. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Silverpeas before 6.3.5 allows authentication bypass by omitting the Password field to AuthenticationServlet, often providing an unauthenticated user with superadmin access. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Sourcecodester Gas Agency Management System v1.0 is vulnerable to SQL Injection via /gasmark/editbrand.php?id=. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Sourcecodester Gas Agency Management System v1.0 is vulnerable to arbitrary code execution via editClientImage.php. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Tenda O3V2 v1.0.0.12(3880) was discovered to contain a Blind Command Injection via stpEn parameter in the SetStp function. This vulnerability allows attackers to execute arbitrary commands with root privileges. | 2024-06-04 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component /admin/idcProType_deal.php?mudi=add&nohrefStr=close | 2024-06-05 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component admin/type_deal.php?mudi=del | 2024-06-05 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component admin/type_deal.php?mudi=add. | 2024-06-05 | not yet calculated | |
| n/a--n/a | idccms v1.35 was discovered to contain a Cross-Site Request Forgery (CSRF) via the component admin/vpsClass_deal.php?mudi=del | 2024-06-05 | not yet calculated | |
| n/a--n/a | Sourcecodester Pharmacy/Medical Store Point of Sale System 1.0 is vulnerable SQL Injection via login.php. This vulnerability stems from inadequate validation of user inputs for the email and password parameters, allowing attackers to inject malicious SQL queries. | 2024-06-07 | not yet calculated | |
| n/a--n/a | LyLme_spage v1.9.5 is vulnerable to Cross Site Scripting (XSS) via admin/link.php. | 2024-06-03 | not yet calculated | |
| n/a--n/a | LyLme_spage v1.9.5 is vulnerable to Server-Side Request Forgery (SSRF) via the get_head function. | 2024-06-04 | not yet calculated | |
| n/a--n/a | TRENDnet TEW-827DRU devices through 2.06B04 contain a stack-based buffer overflow in the ssi binary. The overflow allows an authenticated user to execute arbitrary code by POSTing to apply.cgi via the action vlan_setting with a sufficiently long dns1 or dns 2 key. | 2024-06-03 | not yet calculated | |
| n/a--n/a | TRENDnet TEW-827DRU devices through 2.06B04 contain a stack-based buffer overflow in the ssi binary. The overflow allows an authenticated user to execute arbitrary code by POSTing to apply.cgi via the action wizard_ipv6 with a sufficiently long reboot_type key. | 2024-06-03 | not yet calculated | |
| n/a--n/a | Improper input validation in OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) via inputting negative values into the oneflow.zeros/ones parameter. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An issue in OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) when an empty array is processed with oneflow.tensordot. | 2024-06-06 | not yet calculated | |
| n/a--n/a | Improper input validation in OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) via inputting a negative value into the dim parameter. | 2024-06-06 | not yet calculated | |
| n/a--n/a | OneFlow-Inc. Oneflow v0.9.1 does not display an error or warning when the oneflow.eye parameter is floating. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An issue in the oneflow.permute component of OneFlow-Inc. Oneflow v0.9.1 causes an incorrect calculation when the same dimension operation is performed. | 2024-06-06 | not yet calculated | |
| n/a--n/a | Improper input validation in OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) via inputting a negative value into the oneflow.full parameter. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An issue in OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) when index as a negative number exceeds the range of size. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An issue in the oneflow.scatter_nd parameter OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) when index parameter exceeds the range of shape. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An issue in OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) when an empty array is processed with oneflow.dot. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An issue in OneFlow-Inc. Oneflow v0.9.1 allows attackers to cause a Denial of Service (DoS) via inputting a negative value into the oneflow.index_select parameter. | 2024-06-06 | not yet calculated | |
| n/a--n/a | A cross-site scripting (XSS) vulnerability in Monstra CMS v3.0.4 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the Themes parameter at index.php. | 2024-06-07 | not yet calculated | |
| n/a--n/a | An arbitrary file upload vulnerability in Monstra CMS v3.0.4 allows attackers to execute arbitrary code via uploading a crafted PHP file. | 2024-06-06 | not yet calculated | |
| n/a--n/a | A cross-site scripting (XSS) vulnerability in Monstra CMS v3.0.4 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the About Me parameter in the Edit Profile page. | 2024-06-06 | not yet calculated | |
| n/a--n/a | Sourcecodester Stock Management System v1.0 is vulnerable to SQL Injection via editCategories.php. | 2024-06-06 | not yet calculated | |
| n/a--n/a | TOTOLINK CP300 V2.0.4-B20201102 was discovered to contain a hardcoded password vulnerability in /etc/shadow.sample, which allows attackers to log in as root. | 2024-06-03 | not yet calculated | |
| n/a--n/a | TOTOLINK LR350 V9.3.5u.6369_B20220309 was discovered to contain a command injection via the host_time parameter in the NTPSyncWithHost function. | 2024-06-03 | not yet calculated | |
| n/a--n/a | An issue in Netgear WNR614 JNR1010V2 N300-V1.1.0.54_1.0.1 allows attackers to bypass authentication and access the administrative interface via unspecified vectors. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Netgear WNR614 JNR1010V2 N300-V1.1.0.54_1.0.1 does not properly set the HTTPOnly flag for cookies. This allows attackers to possibly intercept and access sensitive communications between the router and connected devices. | 2024-06-07 | not yet calculated | |
| n/a--n/a | An issue in Netgear WNR614 JNR1010V2/N300-V1.1.0.54_1.0.1 allows attackers to create passwords that do not conform to defined security standards. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Netgear WNR614 JNR1010V2/N300-V1.1.0.54_1.0.1 was discovered to store credentials in plaintext. | 2024-06-07 | not yet calculated | |
| n/a--n/a | An issue in the implementation of the WPS in Netgear WNR614 JNR1010V2/N300-V1.1.0.54_1.0.1 allows attackers to gain access to the router's pin. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Insecure permissions in Netgear WNR614 JNR1010V2/N300-V1.1.0.54_1.0.1 allows attackers to access URLs and directories embedded within the firmware via unspecified vectors. | 2024-06-06 | not yet calculated | |
| n/a--n/a | A SQL injection vulnerability in SEMCMS v.4.8, allows a remote attacker to obtain sensitive information via the ID parameter in Download.php. | 2024-06-04 | not yet calculated | |
| n/a--n/a | A SQL injection vulnerability in SEMCMS v.4.8, allows a remote attacker to obtain sensitive information via the lgid parameter in Download.php. | 2024-06-04 | not yet calculated | |
| n/a--n/a | An arbitrary file upload vulnerability in the image upload function of aimeos-core v2024.04 allows attackers to execute arbitrary code via uploading a crafted PHP file. | 2024-06-07 | not yet calculated | |
| n/a--n/a | The encrypt() function of Ninja Core v7.0.0 was discovered to use a weak cryptographic algorithm, leading to a possible leakage of sensitive information. | 2024-06-06 | not yet calculated | |
| n/a--n/a | An XML External Entity (XXE) vulnerability in the ebookmeta.get_metadata function of ebookmeta before v1.2.8 allows attackers to access sensitive information or cause a Denial of Service (DoS) via crafted XML input. | 2024-06-07 | not yet calculated | |
| n/a--n/a | SQL Injection vulnerability in CRMEB v.5.2.2 allows a remote attacker to obtain sensitive information via the getProductList function in the ProductController.php file. | 2024-06-05 | not yet calculated | |
| n/a--n/a | Jan v0.4.12 was discovered to contain an arbitrary file read vulnerability via the /v1/app/readFileSync interface. | 2024-06-04 | not yet calculated | |
| n/a--n/a | An arbitrary file upload vulnerability in the /v1/app/writeFileSync interface of Jan v0.4.12 allows attackers to execute arbitrary code via uploading a crafted file. | 2024-06-04 | not yet calculated | |
| n/a--n/a | Northern.tech Mender Enterprise before 3.6.4 and 3.7.x before 3.7.4 has Weak Authentication. | 2024-06-03 | not yet calculated | |
| n/a--n/a | The Active Admin (aka activeadmin) framework before 3.2.2 for Ruby on Rails allows stored XSS in certain situations where users can create entities (to be later edited in forms) with arbitrary names, aka a "dynamic form legends" issue. 4.0.0.beta7 is also a fixed version. | 2024-06-03 | not yet calculated | |
| n/a--n/a | An arbitrary file upload vulnerability in the /v1/app/appendFileSync interface of Jan v0.4.12 allows attackers to execute arbitrary code via uploading a crafted file. | 2024-06-04 | not yet calculated | |
| n/a--n/a | Roundcube Webmail before 1.5.7 and 1.6.x before 1.6.7 allows XSS via SVG animate attributes. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Roundcube Webmail before 1.5.7 and 1.6.x before 1.6.7 allows XSS via list columns from user preferences. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Roundcube Webmail before 1.5.7 and 1.6.x before 1.6.7 on Windows allows command injection via im_convert_path and im_identify_path. NOTE: this issue exists because of an incomplete fix for CVE-2020-12641. | 2024-06-07 | not yet calculated | |
| n/a--n/a | An XML External Entity (XXE) vulnerability in the ebookmeta.get_metadata function of lxml before v4.9.1 allows attackers to access sensitive information or cause a Denial of Service (DoS) via crafted XML input. | 2024-06-07 | not yet calculated | |
| n/a--n/a | Libarchive before 3.7.4 allows name out-of-bounds access when a ZIP archive has an empty-name file and mac-ext is enabled. This occurs in slurp_central_directory in archive_read_support_format_zip.c. | 2024-06-08 | not yet calculated | |
| n/a--n/a | fprintd through 1.94.3 lacks a security attention mechanism, and thus unexpected actions might be authorized by "auth sufficient pam_fprintd.so" for Sudo. | 2024-06-08 | not yet calculated | |
| NETGEAR--ProSAFE Network Management System | NETGEAR ProSAFE Network Management System UpLoadServlet Directory Traversal Remote Code Execution Vulnerability. This vulnerability allows remote attackers to execute arbitrary code on affected installations of NETGEAR ProSAFE Network Management System. Authentication is required to exploit this vulnerability. The specific flaw exists within the UpLoadServlet class. The issue results from the lack of proper validation of a user-supplied path prior to using it in file operations. An attacker can leverage this vulnerability to execute code in the context of SYSTEM. Was ZDI-CAN-22724. | 2024-06-06 | not yet calculated | |
| onnx--onnx/onnx | A vulnerability in the `download_model_with_test_data` function of the onnx/onnx framework, version 1.16.0, allows for arbitrary file overwrite due to inadequate prevention of path traversal attacks in malicious tar files. This vulnerability enables attackers to overwrite any file on the system, potentially leading to remote code execution, deletion of system, personal, or application files, thus impacting the integrity and availability of the system. The issue arises from the function's handling of tar file extraction without performing security checks on the paths within the tar file, as demonstrated by the ability to overwrite the `/home/kali/.ssh/authorized_keys` file by specifying an absolute path in the malicious tar file. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | parisneo/lollms-webui is vulnerable to path traversal and denial of service attacks due to an exposed `/select_database` endpoint in version a9d16b0. The endpoint improperly handles file paths, allowing attackers to specify absolute paths when interacting with the `DiscussionsDB` instance. This flaw enables attackers to create directories anywhere on the system where the application has permissions, potentially leading to denial of service by creating directories with names of critical files, such as HTTPS certificate files, causing server startup failures. Additionally, attackers can manipulate the database path, resulting in the loss of client data by constantly changing the file location to an attacker-controlled location, scattering the data across the filesystem and making recovery difficult. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A Cross-Site Request Forgery (CSRF) vulnerability exists in the profile picture upload functionality of the Lollms application, specifically in the parisneo/lollms-webui repository, affecting versions up to 7.3.0. This vulnerability allows attackers to change a victim's profile picture without their consent, potentially leading to a denial of service by overloading the filesystem with files. Additionally, this flaw can be exploited to perform a stored cross-site scripting (XSS) attack, enabling attackers to execute arbitrary JavaScript in the context of the victim's browser session. The issue is resolved in version 9.3. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A vulnerability in the parisneo/lollms-webui version 9.3 allows attackers to bypass intended access restrictions and execute arbitrary code. The issue arises from the application's handling of the `/execute_code` endpoint, which is intended to be blocked from external access by default. However, attackers can exploit the `/update_setting` endpoint, which lacks proper access control, to modify the `host` configuration at runtime. By changing the `host` setting to an attacker-controlled value, the restriction on the `/execute_code` endpoint can be bypassed, leading to remote code execution. This vulnerability is due to improper neutralization of special elements used in an OS command (`Improper Neutralization of Special Elements used in an OS Command`). | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | parisneo/lollms-webui is vulnerable to path traversal attacks that can lead to remote code execution due to insufficient sanitization of user-supplied input in the 'Database path' and 'PDF LaTeX path' settings. An attacker can exploit this vulnerability by manipulating these settings to execute arbitrary code on the targeted server. The issue affects the latest version of the software. The vulnerability stems from the application's handling of the 'discussion_db_name' and 'pdf_latex_path' parameters, which do not properly validate file paths, allowing for directory traversal. This vulnerability can also lead to further file exposure and other attack vectors by manipulating the 'discussion_db_name' parameter. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A path traversal vulnerability exists in the parisneo/lollms-webui version 9.3 on the Windows platform. Due to improper validation of file paths between Windows and Linux environments, an attacker can exploit this vulnerability to delete any file on the system. The issue arises from the lack of adequate sanitization of user-supplied input in the 'del_preset' endpoint, where the application fails to prevent the use of absolute paths or directory traversal sequences ('..'). As a result, an attacker can send a specially crafted request to the 'del_preset' endpoint to delete files outside of the intended directory. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A path traversal vulnerability exists in the parisneo/lollms-webui application, specifically within the `lollms_core/lollms/server/endpoints/lollms_binding_files_server.py` and `lollms_core/lollms/security.py` files. Due to inadequate validation of file paths between Windows and Linux environments using `Path(path).is_absolute()`, attackers can exploit this flaw to read any file on the system. This issue affects the latest version of LoLLMs running on the Windows platform. The vulnerability is triggered when an attacker sends a specially crafted request to the `/user_infos/{path:path}` endpoint, allowing the reading of arbitrary files, as demonstrated with the `win.ini` file. The issue has been addressed in version 9.5 of the software. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A path traversal and arbitrary file upload vulnerability exists in the parisneo/lollms-webui application, specifically within the `@router.get("/switch_personal_path")` endpoint in `./lollms-webui/lollms_core/lollms/server/endpoints/lollms_user.py`. The vulnerability arises due to insufficient sanitization of user-supplied input for the `path` parameter, allowing an attacker to specify arbitrary file system paths. This flaw enables direct arbitrary file uploads, leakage of `personal_data`, and overwriting of configurations in `lollms-webui`->`configs` by exploiting the same named directory in `personal_data`. The issue affects the latest version of the application and is fixed in version 9.4. Successful exploitation could lead to sensitive information disclosure, unauthorized file uploads, and potentially remote code execution by overwriting critical configuration files. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A path traversal vulnerability exists in the 'cyber_security/codeguard' native personality of the parisneo/lollms-webui, affecting versions up to 9.5. The vulnerability arises from the improper limitation of a pathname to a restricted directory in the 'process_folder' function within 'lollms-webui/zoos/personalities_zoo/cyber_security/codeguard/scripts/processor.py'. Specifically, the function fails to properly sanitize user-supplied input for the 'code_folder_path', allowing an attacker to specify arbitrary paths using '../' or absolute paths. This flaw leads to arbitrary file read and overwrite capabilities in specified directories without limitations, posing a significant risk of sensitive information disclosure and unauthorized file manipulation. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A remote code execution (RCE) vulnerability exists in the '/install_extension' endpoint of the parisneo/lollms-webui application, specifically within the `@router.post("/install_extension")` route handler. The vulnerability arises due to improper handling of the `name` parameter in the `ExtensionBuilder().build_extension()` method, which allows for local file inclusion (LFI) leading to arbitrary code execution. An attacker can exploit this vulnerability by crafting a malicious `name` parameter that causes the server to load and execute a `__init__.py` file from an arbitrary location, such as the upload directory for discussions. This vulnerability affects the latest version of parisneo/lollms-webui and can lead to remote code execution without requiring user interaction, especially when the application is exposed to an external endpoint or operated in headless mode. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms-webui | A Server-Side Request Forgery (SSRF) vulnerability exists in the 'add_webpage' endpoint of the parisneo/lollms-webui application, affecting the latest version. The vulnerability arises because the application does not adequately validate URLs entered by users, allowing them to input arbitrary URLs, including those that target internal resources such as 'localhost' or '127.0.0.1'. This flaw enables attackers to make unauthorized requests to internal or external systems, potentially leading to access to sensitive data, service disruption, network integrity compromise, business logic manipulation, and abuse of third-party resources. The issue is critical and requires immediate attention to maintain the application's security and integrity. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms | A path traversal vulnerability exists in the parisneo/lollms application, specifically within the `sanitize_path_from_endpoint` and `sanitize_path` functions in `lollms_core\lollms\security.py`. This vulnerability allows for arbitrary file reading when the application is running on Windows. The issue arises due to insufficient sanitization of user-supplied input, enabling attackers to bypass the path traversal protection mechanisms by crafting malicious input. Successful exploitation could lead to unauthorized access to sensitive files, information disclosure, and potentially a denial of service (DoS) condition by including numerous large or resource-intensive files. This vulnerability affects the latest version prior to 9.6. | 2024-06-06 | not yet calculated | |
| parisneo--parisneo/lollms | A path traversal vulnerability exists in the parisneo/lollms application, affecting version 9.4.0 and potentially earlier versions, but fixed in version 5.9.0. The vulnerability arises due to improper validation of file paths between Windows and Linux environments, allowing attackers to traverse beyond the intended directory and read any file on the Windows system. Specifically, the application fails to adequately sanitize file paths containing backslashes (`\`), which can be exploited to access the root directory and read, or even delete, sensitive files. This issue was discovered in the context of the `/user_infos` endpoint, where a crafted request using backslashes to reference a file (e.g., `\windows\win.ini`) could result in unauthorized file access. The impact of this vulnerability includes the potential for attackers to access sensitive information such as environment variables, database files, and configuration files, which could lead to further compromise of the system. | 2024-06-06 | not yet calculated | |
| ProjectDiscovery--Interactsh | Files or Directories Accessible to External Parties vulnerability in smb server in ProjectDiscovery Interactsh allows remote attackers to read/write any files in the directory and subdirectories of where the victim runs interactsh-server via anonymous login. | 2024-06-05 | not yet calculated | |
| pytorch--pytorch/pytorch | A vulnerability in the PyTorch's torch.distributed.rpc framework, specifically in versions prior to 2.2.2, allows for remote code execution (RCE). The framework, which is used in distributed training scenarios, does not properly verify the functions being called during RPC (Remote Procedure Call) operations. This oversight permits attackers to execute arbitrary commands by leveraging built-in Python functions such as eval during multi-cpu RPC communication. The vulnerability arises from the lack of restriction on function calls when a worker node serializes and sends a PythonUDF (User Defined Function) to the master node, which then deserializes and executes the function without validation. This flaw can be exploited to compromise master nodes initiating distributed training, potentially leading to the theft of sensitive AI-related data. | 2024-06-06 | not yet calculated | |
| qdrant--qdrant/qdrant | qdrant/qdrant version 1.9.0-dev is vulnerable to arbitrary file read and write during the snapshot recovery process. Attackers can exploit this vulnerability by manipulating snapshot files to include symlinks, leading to arbitrary file read by adding a symlink that points to a desired file on the filesystem and arbitrary file write by including a symlink and a payload file in the snapshot's directory structure. This vulnerability allows for the reading and writing of arbitrary files on the server, which could potentially lead to a full takeover of the system. The issue is fixed in version v1.9.0. | 2024-06-03 | not yet calculated | |
| scikit-learn--scikit-learn/scikit-learn | A sensitive data leakage vulnerability was identified in scikit-learn's TfidfVectorizer, specifically in versions up to and including 1.4.1.post1, which was fixed in version 1.5.0. The vulnerability arises from the unexpected storage of all tokens present in the training data within the `stop_words_` attribute, rather than only storing the subset of tokens required for the TF-IDF technique to function. This behavior leads to the potential leakage of sensitive information, as the `stop_words_` attribute could contain tokens that were meant to be discarded and not stored, such as passwords or keys. The impact of this vulnerability varies based on the nature of the data being processed by the vectorizer. | 2024-06-06 | not yet calculated | |
| SEH Computertechnik--utnserver Pro | Missing input validation in the SEH Computertechnik utnserver Pro, SEH Computertechnik utnserver ProMAX, SEH Computertechnik INU-100 web-interface allows stored Cross-Site Scripting (XSS)..This issue affects utnserver Pro, utnserver ProMAX, INU-100 version 20.1.22 and below. | 2024-06-04 | not yet calculated | |
| SEH Computertechnik--utnserver Pro | Missing input validation and OS command integration of the input in the utnserver Pro, utnserver ProMAX, INU-100 web-interface allows authenticated command injection.This issue affects utnserver Pro, utnserver ProMAX, INU-100 version 20.1.22 and below. | 2024-06-04 | not yet calculated | |
| SEH Computertechnik--utnserver Pro | An uncontrolled resource consumption of file descriptors in SEH Computertechnik utnserver Pro, SEH Computertechnik utnserver ProMAX, SEH Computertechnik INU-100 allows DoS via HTTP.This issue affects utnserver Pro, utnserver ProMAX, INU-100 version 20.1.22 and below. | 2024-06-04 | not yet calculated | |
| significant-gravitas--significant-gravitas/autogpt | A Cross-Site Request Forgery (CSRF) vulnerability in significant-gravitas/autogpt version v0.5.0 allows attackers to execute arbitrary commands on the AutoGPT server. The vulnerability stems from the lack of protections on the API endpoint receiving instructions, enabling an attacker to direct a user running AutoGPT in their local network to a malicious website. This site can then send crafted requests to the AutoGPT server, leading to command execution. The issue is exacerbated by CORS being enabled for arbitrary origins by default, allowing the attacker to read the response of all cross-site queries. This vulnerability was addressed in version 5.1. | 2024-06-06 | not yet calculated | |
| significant-gravitas--significant-gravitas/autogpt | An OS command injection vulnerability exists in the MacOS Text-To-Speech class MacOSTTS of the significant-gravitas/autogpt project, affecting versions up to v0.5.0. The vulnerability arises from the improper neutralization of special elements used in an OS command within the `_speech` method of the MacOSTTS class. Specifically, the use of `os.system` to execute the `say` command with user-supplied text allows for arbitrary code execution if an attacker can inject shell commands. This issue is triggered when the AutoGPT instance is run with the `--speak` option enabled and configured with `TEXT_TO_SPEECH_PROVIDER=macos`, reflecting back a shell injection snippet. The impact of this vulnerability is the potential execution of arbitrary code on the instance running AutoGPT. The issue was addressed in version 5.1.0. | 2024-06-06 | not yet calculated | |
| significant-gravitas--significant-gravitas/autogpt | AutoGPT, a component of significant-gravitas/autogpt, is vulnerable to an improper neutralization of special elements used in an OS command ('OS Command Injection') due to a flaw in its shell command validation function. Specifically, the vulnerability exists in versions v0.5.0 up to but not including 5.1.0. The issue arises from the application's method of validating shell commands against an allowlist or denylist, where it only checks the first word of the command. This allows an attacker to bypass the intended restrictions by crafting commands that are executed despite not being on the allowlist or by including malicious commands not present in the denylist. Successful exploitation of this vulnerability could allow an attacker to execute arbitrary shell commands. | 2024-06-06 | not yet calculated | |
| Sonos--Era 100 | Sonos Era 100 SMB2 Message Handling Integer Underflow Information Disclosure Vulnerability. This vulnerability allows network-adjacent attackers to disclose sensitive information on affected installations of Sonos Era 100 smart speakers. Authentication is not required to exploit this vulnerability. The specific flaw exists within the handling of SMB2 messages. The issue results from the lack of proper validation of user-supplied data, which can result in an integer underflow before reading from memory. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of root. Was ZDI-CAN-22336. | 2024-06-06 | not yet calculated | |
| Sonos--Era 100 | Sonos Era 100 SMB2 Message Handling Out-Of-Bounds Write Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected installations of Sonos Era 100 smart speakers. Authentication is not required to exploit this vulnerability. The specific flaw exists within the handling of SMB2 messages. The issue results from the lack of proper validation of user-supplied data, which can result in a write past the end of an allocated buffer. An attacker can leverage this vulnerability to execute code in the context of root. Was ZDI-CAN-22384. | 2024-06-06 | not yet calculated | |
| Sonos--Era 100 | Sonos Era 100 SMB2 Message Handling Out-Of-Bounds Read Information Disclosure Vulnerability. This vulnerability allows network-adjacent attackers to disclose sensitive information on affected installations of Sonos Era 100 smart speakers. Authentication is not required to exploit this vulnerability. The specific flaw exists within the handling of SMB2 messages. The issue results from the lack of proper validation of user-supplied data, which can result in a read past the end of an allocated buffer. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of root. Was ZDI-CAN-22428. | 2024-06-06 | not yet calculated | |
| Sonos--Era 100 | Sonos Era 100 SMB2 Message Handling Use-After-Free Remote Code Execution Vulnerability. This vulnerability allows network-adjacent attackers to execute arbitrary code on affected installations of Sonos Era 100 smart speakers. Authentication is not required to exploit this vulnerability. The specific flaw exists within the handling of SMB2 messages. The issue results from the lack of validating the existence of an object prior to performing operations on the object. An attacker can leverage this vulnerability to execute code in the context of root. Was ZDI-CAN-22459. | 2024-06-06 | not yet calculated | |
| stangirard--stangirard/quivr | A Server-Side Request Forgery (SSRF) vulnerability exists in the stangirard/quivr application, version 0.0.204, which allows attackers to access internal networks. The vulnerability is present in the crawl endpoint where the 'url' parameter can be manipulated to send HTTP requests to arbitrary URLs, thereby facilitating SSRF attacks. The affected code is located in the backend/routes/crawl_routes.py file, specifically within the crawl_endpoint function. This issue could allow attackers to interact with internal services that are accessible from the server hosting the application. | 2024-06-06 | not yet calculated | |
| Unknown--ARForms - Premium WordPress Form Builder Plugin | The ARForms - Premium WordPress Form Builder Plugin WordPress plugin before 6.6 allows unauthenticated users to modify uploaded files in such a way that PHP code can be uploaded when an upload file input is included on a form | 2024-06-07 | not yet calculated | |
| Unknown--ARForms - Premium WordPress Form Builder Plugin | The ARForms - Premium WordPress Form Builder Plugin WordPress plugin before 6.6 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup) | 2024-06-07 | not yet calculated | |
| Unknown--buddyboss-platform | The buddyboss-platform WordPress plugin before 2.6.0 contains an IDOR vulnerability that allows a user to like a private post by manipulating the ID included in the request | 2024-06-04 | not yet calculated | |
| Unknown--buddyboss-platform | The contains an IDOR vulnerability that allows a user to comment on a private post by manipulating the ID included in the request | 2024-06-05 | not yet calculated | |
| Unknown--FS Product Inquiry | The FS Product Inquiry WordPress plugin through 1.1.1 does not sanitise and escape a parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting which could be used against high privilege users such as admin or unauthenticated users | 2024-06-04 | not yet calculated | |
| Unknown--FS Product Inquiry | The FS Product Inquiry WordPress plugin through 1.1.1 does not sanitise and escape some form submissions, which could allow unauthenticated users to perform Stored Cross-Site Scripting attacks | 2024-06-04 | not yet calculated | |
| Unknown--Gutenberg Blocks with AI by Kadence WP | The Gutenberg Blocks with AI by Kadence WP WordPress plugin before 3.2.37 does not validate and escape some of its block attributes before outputting them back in a page/post where the block is embed, which could allow users with the contributor role and above to perform Stored Cross-Site Scripting attacks | 2024-06-04 | not yet calculated | |
| Unknown--Insert or Embed Articulate Content into WordPress | The Insert or Embed Articulate Content into WordPress plugin through 4.3000000023 is not properly filtering which file extensions are allowed to be imported on the server, allowing the uploading of malicious code within zip files | 2024-06-04 | not yet calculated | |
| Unknown--Logo Slider | The Logo Slider WordPress plugin before 4.0.0 does not validate and escape some of its Slider Settings before outputting them back in attributes, which could allow users with the contributor role and above to perform Stored Cross-Site Scripting attacks | 2024-06-07 | not yet calculated | |
| Unknown--Simple Ajax Chat | The Simple Ajax Chat WordPress plugin before 20240412 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup) | 2024-06-04 | not yet calculated | |
| Unknown--The Events Calendar | The Events Calendar WordPress plugin before 6.4.0.1 does not properly sanitize user-submitted content when rendering some views via AJAX. | 2024-06-04 | not yet calculated | |
| Unknown--WP Backpack | The WP Backpack WordPress plugin through 2.1 does not sanitise and escape some of its settings, which could allow high privilege users such as admin to perform Stored Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed (for example in multisite setup) | 2024-06-07 | not yet calculated | |
| Unknown--WP Stacker | The WP Stacker WordPress plugin through 1.8.5 does not have CSRF check in some places, and is missing sanitisation as well as escaping, which could allow attackers to make logged in admin add Stored XSS payloads via a CSRF attack | 2024-06-07 | not yet calculated | |
| Unknown--wp-eMember | The wp-eMember WordPress plugin before 10.3.9 does not sanitize and escape the "fieldId" parameter before outputting it back in the page, leading to a Reflected Cross-Site Scripting. | 2024-06-04 | not yet calculated | |
| zenml-io--zenml-io/zenml | A race condition vulnerability exists in zenml-io/zenml versions up to and including 0.55.3, which allows for the creation of multiple users with the same username when requests are sent in parallel. This issue was fixed in version 0.55.5. The vulnerability arises due to insufficient handling of concurrent user creation requests, leading to data inconsistencies and potential authentication problems. Specifically, concurrent processes may overwrite or corrupt user data, complicating user identification and posing security risks. This issue is particularly concerning for APIs that rely on usernames as input parameters, such as PUT /api/v1/users/test_race, where it could lead to further complications. | 2024-06-06 | not yet calculated | |
| zenml-io--zenml-io/zenml | An improper authorization vulnerability exists in the zenml-io/zenml repository, specifically within the API PUT /api/v1/users/id endpoint. This vulnerability allows any authenticated user to modify the information of other users, including changing the `active` status of user accounts to false, effectively deactivating them. This issue affects version 0.55.3 and was fixed in version 0.56.2. The impact of this vulnerability is significant as it allows for the deactivation of admin accounts, potentially disrupting the functionality and security of the application. | 2024-06-06 | not yet calculated | |
| zenml-io--zenml-io/zenml | A stored Cross-Site Scripting (XSS) vulnerability was identified in the zenml-io/zenml repository, specifically within the 'logo_url' field. By injecting malicious payloads into this field, an attacker could send harmful messages to other users, potentially compromising their accounts. The vulnerability affects version 0.55.3 and was fixed in version 0.56.2. The impact of exploiting this vulnerability could lead to user account compromise. | 2024-06-06 | not yet calculated | |
| zenml-io--zenml-io/zenml | An issue was discovered in zenml-io/zenml versions up to and including 0.55.4. Due to improper authentication mechanisms, an attacker with access to an active user session can change the account password without needing to know the current password. This vulnerability allows for unauthorized account takeover by bypassing the standard password change verification process. The issue was fixed in version 0.56.3. | 2024-06-06 | not yet calculated | |
| zenml-io--zenml-io/zenml | A clickjacking vulnerability exists in zenml-io/zenml versions up to and including 0.55.5 due to the application's failure to set appropriate X-Frame-Options or Content-Security-Policy HTTP headers. This vulnerability allows an attacker to embed the application UI within an iframe on a malicious page, potentially leading to unauthorized actions by tricking users into interacting with the interface under the attacker's control. The issue was addressed in version 0.56.3. | 2024-06-06 | not yet calculated | |
| zenml-io--zenml-io/zenml | A vulnerability in zenml-io/zenml version 0.56.3 allows attackers to reuse old session credentials or session IDs due to insufficient session expiration. Specifically, the session does not expire after a password change, enabling an attacker to maintain access to a compromised account without the victim's ability to revoke this access. This issue was observed in a self-hosted ZenML deployment via Docker, where after changing the password from one browser, the session remained active and usable in another browser without requiring re-authentication. | 2024-06-08 | not yet calculated | |
Please share your thoughts
We recently updated our anonymous product survey ; we’d welcome your feedback.

IMAGES
VIDEO
COMMENTS
30. I've noticed that a common pattern I use is to assign SomeClass.__init__() arguments to self attributes of the same name. Example: class SomeClass(): def __init__(self, a, b, c): self.a = a. self.b = b. self.c = c. In fact it must be a common task for others as well as PyDev has a shortcut for this - if you place the cursor on the parameter ...
Learning about the Python assignment operator and its use for writing assignment statements will arm you with powerful tools for writing better and more robust Python code. ... Another example of implicit assignments is the current instance of a class, which in Python is called self by convention. This name implicitly gets a reference to the ...
The self parameter is a special parameter that is passed to methods in Python classes. It binds the instance of the class to the method, allowing the method to access and modify the attributes and methods of the class instance. Properly utilizing self is key to writing effective Python classes. This guide will provide a deep dive into self ...
Due to its intuitive and concise syntax, as defined by PEP 673, the Self type is the preferred annotation for methods that return an instance of their class. The Self type can be imported directly from Python's typing module in version 3.11 and beyond. For Python versions less than 3.11, the Self type is available in typing_extensions.
The explicit self is not unique to Python. This idea was borrowed from Modula-3. Following is a use case where it becomes helpful. There is no explicit variable declaration in Python. They spring into action on the first assignment. The use of self makes it easier to distinguish between instance attributes (and methods) from local variables.
Understanding Python self Variable with Examples. Python self variable is used to bind the instance of the class to the instance method. We have to explicitly declare it as the first method argument to access the instance variables and methods. This variable is used only with the instance methods. In most of the Object-Oriented programming ...
Python Assignment Operators. Assignment operators are used to assign values to variables: Operator. Example. Same As. Try it. =. x = 5. x = 5.
Python's self is the embodiment of the "worse is better" design philosophy — described here. The priority of this design philosophy is "simplicity" defined as: The design must be simple, both in implementation and interface. It is more important for the implementation to be simple than the interface…. That's exactly the case ...
Assignment Operator. Assignment Operators are used to assign values to variables. This operator is used to assign the value of the right side of the expression to the left side operand. Python. # Assigning values using # Assignment Operator a = 3 b = 5 c = a + b # Output print(c) Output. 8.
Unparenthesized assignment expressions are prohibited for the value of a keyword argument in a call. Example: foo(x = y := f(x)) # INVALID foo(x=(y := f(x))) # Valid, though probably confusing. This rule is included to disallow excessively confusing code, and because parsing keyword arguments is complex enough already.
As far as Python is concerned, you can use any name for the first parameter of a method. But we recommend everyone use these names so that when we read each others' code, we won't have to remember what variable refers to the current object in each method.
In this lesson, you'll learn about the biggest change in Python 3.8: the introduction of assignment expressions.Assignment expression are written with a new notation (:=).This operator is often called the walrus operator as it resembles the eyes and tusks of a walrus on its side.. Assignment expressions allow you to assign and return a value in the same expression.
Note how the local assignment (which is default) didn't change scope_test's binding of spam.The nonlocal assignment changed scope_test's binding of spam, and the global assignment changed the module-level binding.. You can also see that there was no previous binding for spam before the global assignment.. 9.3. A First Look at Classes¶. Classes introduce a little bit of new syntax, three new ...
Python provides the operator x *= y to multiply two objects in-place by calculating the product x * y and assigning the result to the first operands variable name x. You can set up the in-place multiplication behavior for your own class by overriding the magic "dunder" method __imul__(self, other) in your class definition. >>> x = 2. >>> x ...
The function moon_weight takes an argument expected to be an instance of float, as indicated by the type hint earth_weight: float.The function is expected to return an instance of str, as indicated by the -> str hint.. While type hints can be simple classes like float or str, they can also be more complex.The typing module provides a vocabulary of more advanced type hints.
Hi, if you want to call the method getSingleRows at start-up during an object instantiation, include an __init__ constructor method, and call the method in there, i.e:. def __init__(self): self.getSingleRows() If you want access to the attribute x in other parts of your class script, define it in the constructor so that it becomes an attribute of the instances that you create.
If we have an object say a1 of type Array and if we have a line like a1 = a1 somewhere, the program results in unpredictable behavior because there is no self assignment check in the above code. To avoid the above issue, self assignment check must be there while overloading assignment operator. For example, following code does self assignment check.
self is just an argument that is passed to your function. It's a name that points to the instance the method was called on. "Assigning to self " is equivalent to: def fn(a): a = 2. a = 1. fn(a) # a is still equal to 1. Assigning to self changes what the self name points to (from one Table instance to a new Table instance here).
Assignment Expression Syntax. For more information on concepts covered in this lesson, you can check out: Walrus operator syntax. One of the main reasons assignments were not expressions in Python from the beginning is the visual likeness of the assignment operator (=) and the equality comparison operator (==). This could potentially lead to bugs.
These free exercises are nothing but Python assignments for the practice where you need to solve different programs and challenges. All exercises are tested on Python 3. Each exercise has 10-20 Questions. The solution is provided for every question. These Python programming exercises are suitable for all Python developers.
Assignment Operators in Python. Let's see an example of Assignment Operators in Python. Example: The code starts with 'a' and 'b' both having the value 10. It then performs a series of operations: addition, subtraction, multiplication, and a left shift operation on 'b'.
If you are interested in learning more about how these models work I encourage you to read: Prelude: A Brief History of Large Language Models. Part 1: Tokenization — A Complete Guide. Part 2: Word Embeddings with word2vec from Scratch in Python. Part 3: Self-Attention Explained with Code. Part 4: A Complete Guide to BERT with Code.
This is CS50x , Harvard University's introduction to the intellectual enterprises of computer science and the art of programming for majors and non-majors alike, with or without prior programming experience. An entry-level course taught by David J. Malan, CS50x teaches students how to think algorithmically and solve problems efficiently.
self is a reference to an object. If you assign to it, you change which object the variable self is referring to, but it does not modify anything outside that method. The functionality is similar to the following code: def change(a): a = 10. print(a) # prints 10. x = 5. change(x) print(x) # prints 5.
Недавно в Python появился класс для хранения данных (dataclass). В примере 5.7 показано, как все эти self-выражения исчезают при использовании классов данных. Пример 5.7. Применение класса данных dataclass
From Python 3.7+ you can use a Data Class, which achieves what you want and more.. It allows you to define fields for your class, which are attributes automatically assigned.. It would look something like that: @dataclass class Foo: a: str b: int c: str ... The __init__ method will be automatically created in your class, and it will assign the arguments of instance creation to those attributes ...
Deserialization of untrusted data can occur in versions 0.6 or newer of the skops python library, enabling a maliciously crafted model to run arbitrary code on an end user's system when loaded. 2024-06-04: 7.8: CVE-2024-37065 6f8de1f0-f67e-45a6-b68f-98777fdb759c: softaculous--FileOrganizer Manage WordPress and Website Files