- A t tachments (0)
- Page History
- Page Information
- Resolved comments
- View in Hierarchy
- View Source
- Export to PDF
- Export to Word

CRS1xx/2xx series switches
The Cloud Router Switch series are highly integrated switches with high-performance MIPS CPU and feature-rich packet processors. The CRS switches can be designed into various Ethernet applications including unmanaged switch, Layer 2 managed switch, carrier switch, and wireless/wired unified packet processing. See Cloud Router Switch configuration examples
This article applies to CRS1xx and CRS2xx series switches and not to CRS3xx series switches. For CRS3xx series devices, read the CRS3xx, CRS5xx series switches and CCR2116, CCR2216 routers manual.
Cloud Router Switch models
This table clarifies the main differences between Cloud Router Switch models.
Abbreviations and Explanations
CVID - Customer VLAN id: inner VLAN tag id of the IEEE 802.1ad frame
SVID - Service VLAN id: outer VLAN tag id of the IEEE 802.1ad frame
IVL - Independent VLAN learning - learning/lookup is based on both MAC addresses and VLAN IDs.
SVL - Shared VLAN learning - learning/lookup is based on MAC addresses - not on VLAN IDs.
TPID - Tag Protocol Identifier
PCP - Priority Code Point: a 3-bit field which refers to the IEEE 802.1p priority
DEI - Drop Eligible Indicator
DSCP - Differentiated services Code Point
Drop precedence - internal CRS switch QoS attribute used for packet enqueuing or dropping.
Port Switching
To set up port switching on CRS1xx/2xx series switches, check the Bridge Hardware Offloading page.
Dynamic reserved VLAN entries (VLAN4091; VLAN4090; VLAN4089; etc.) are created in the CRS switch when switched port groups are added when a hardware offloaded bridge is created. These VLANs are necessary for internal operation and have lower precedence than user-configured VLANs.
Multiple switch groups
The CRS1xx/2xx series switches allow you to use multiple bridges with hardware offloading, this allows you to easily isolate multiple switch groups. This can be done by simply creating multiple bridges and enabling hardware offloading.
Multiple hardware offloaded bridge configuration is designed as a fast and simple port isolation solution, but it limits a part of the VLAN functionality supported by the CRS switch chip. For advanced configurations use one bridge within the CRS switch chip for all ports, configure VLANs, and isolate port groups with port isolation profile configuration.
CRS1xx/2xx series switches can run multiple hardware offloaded bridges with (R)STP enabled, but it is not recommended since the device is not designed to run multiple (R)STP instances on a hardware level. To isolate multiple switch groups and have (R)STP enabled you should isolate port groups with port isolation profile configuration.
Global Settings
The CRS switch chip is configurable from the /interface ethernet switch console menu.
Sub-menu: /interface ethernet switch
Port Settings
Sub-menu: /interface ethernet switch port
Forwarding Databases
Unicast fdb.
The unicast forwarding database supports up to 16318 MAC entries.
Sub-menu: /interface ethernet switch unicast-fdb
Multicast FDB
CRS125 switch-chip supports up to 1024 entries in MFDB for multicast forwarding. For each multicast packet, destination MAC or destination IP lookup is performed in MFDB. MFDB entries are not automatically learned and can only be configured.
Sub-menu: /interface ethernet switch multicast-fdb
Reserved FDB
Cloud Router Switch supports 256 RFDB entries. Each RFDB entry can store either Layer2 unicast or multicast MAC address with specific commands.
Sub-menu: /interface ethernet switch reserved-fdb
The VLAN table supports 4096 VLAN entries for storing VLAN member information as well as other VLAN information such as QoS, isolation, forced VLAN, learning, and mirroring.
Sub-menu: /interface ethernet switch vlan
Egress VLAN Tag
Egress packets can be assigned different VLAN tag formats. The VLAN tags can be removed, added, or remained as is when the packet is sent to the egress port (destination port). Each port has dedicated control of the egress VLAN tag format. The tag formats include:
The Egress VLAN Tag table includes 4096 entries for VLAN tagging selection.
Sub-menu: /interface ethernet switch egress-vlan-tag
Ingress/Egress VLAN Translation
The Ingress VLAN Translation table allows for up to 15 entries for each port. One or multiple fields can be selected from the packet header for lookup in the Ingress VLAN Translation table. The S-VLAN or C-VLAN or both configured in the first matched entry are assigned to the packet.
Sub-menu: /interface ethernet switch ingress-vlan-translation
Sub-menu: /interface ethernet switch egress-vlan-translation
Below is a table of traffic that triggers a rule that has a certain VLAN format set, note that traffic that is tagged with VLAN ID 0 is a special case that is also taken into account.
If VLAN-format is set to any , then customer-vid / service-vid set to 0 will trigger the switch rule with VLAN 0 traffic. In this case, the switch rule will be looking for untagged traffic or traffic with a VLAN 0 tag, and only untagged-or-tagged will filter out VLAN 0 traffic in this case.
Protocol Based VLAN
Protocol Based VLAN table is used to assign VID and QoS attributes to related protocol packets per port.
Sub-menu: /interface ethernet switch protocol-based-vlan
MAC Based VLAN
MAC Based VLAN table is used to assign VLAN based on the source MAC.
Sub-menu: /interface ethernet switch mac-based-vlan
All CRS1xx/2xx series switches support up to 1024 MAC Based VLAN table entries.
1:1 VLAN Switching
1:1 VLAN switching can be used to replace the regular L2 bridging for matched packets. When a packet hits a 1:1 VLAN switching table entry, the destination port information in the entry is assigned to the packet. The matched destination information in the UFDB and MFDB entry no longer applies to the packet.
Sub-menu: /interface ethernet switch one2one-vlan-switching
Port Isolation/Leakage
The CRS switches support flexible multi-level isolation features, which can be used for user access control, traffic engineering and advanced security and network management. The isolation features provide an organized fabric structure allowing user to easily program and control the access by port, MAC address, VLAN, protocol, flow, and frame type. The following isolation and leakage features are supported:
- Port-level isolation
- MAC-level isolation
- VLAN-level isolation
- Protocol-level isolation
- Flow-level isolation
- Free combination of the above
Port-level isolation supports different control schemes on the source port and destination port. Each entry can be programmed with access control for either the source port or the destination port.
- When the entry is programmed with source port access control, the entry is
applied to the ingress packets.
- When the entry is programmed with destination port access control, the entry
is applied to the egress packets.
Port leakage allows bypassing egress VLAN filtering on the port. A leaky port is allowed to access other ports for various applications such as security, network control, and management. Note: When both isolation and leakage are applied to the same port, the port is isolated.
Sub-menu: /interface ethernet switch port-isolation
Sub-menu: /interface ethernet switch port-leakage
The Trunking in the Cloud Router Switches provides static link aggregation groups with hardware automatic failover and load balancing. IEEE802.3ad and IEEE802.1ax compatible Link Aggregation Control Protocol is not supported. Up to 8 Trunk groups are supported with up to 8 Trunk member ports per Trunk group. CRS Port Trunking calculates transmit-hash based on all following parameters: L2 src-dst MAC + L3 src-dst IP + L4 src-dst Port.
Sub-menu: /interface ethernet switch trunk
Quality of Service
Traffic shaping restricts the rate and burst size of the flow which is transmitted out from the interface. The shaper is implemented by a token bucket. If the packet exceeds the maximum rate or the burst size, which means not enough token for the packet, the packet is stored to buffer until there is enough token to transmit it.
Sub-menu: /interface ethernet switch shaper
Ingress Port Policer
Sub-menu: /interface ethernet switch ingress-port-policer
The global QoS group table is used for VLAN-based, Protocol-based, and MAC-based QoS group assignment configuration.
Sub-menu: /interface ethernet switch qos-group
DSCP QoS Map
The global DSCP to QOS mapping table is used for mapping from the DSCP of the packet to new QoS attributes configured in the table.
Sub-menu: /interface ethernet switch dscp-qos-map
DSCP To DSCP Map
The global DSCP to DSCP mapping table is used for mapping from the packet's original DSCP to the new DSCP value configured in the table.
Sub-menu: /interface ethernet switch dscp-to-dscp
Policer QoS Map
Sub-menu: /interface ethernet switch policer-qos-map
Access Control List
Access Control List contains of ingress policy and egress policy engines and allows configuration of up to 128 policy rules (limited by RouterOS). It is an advanced tool for wire-speed packet filtering, forwarding, shaping, and modifying based on Layer2, Layer3, and Layer4 protocol header field conditions.
See the Summary section for Access Control List supported Cloud Router Switch devices.
Due to hardware limitations, it is not possible to match broadcast/multicast traffic on specific ports. You should use port isolation, drop traffic on ingress ports, or use VLAN filtering to prevent certain broadcast/multicast traffic from being forwarded.
Sub-menu: /interface ethernet switch acl
ACL condition part for MAC-related fields of packets.
ACL condition part for VLAN-related fields of packets.
ACL condition part for IPv4 and IPv6 related fields of packets.
ACL rule action part.
Filter bypassing part for ACL packets.
ACL Policer
Sub-menu: /interface ethernet switch acl policer
- CRS1xx/2xx series switches examples
- CRS1xx/2xx VLANs with Trunks
- Basic VLAN switching
- Bridge Hardware Offloading
- Spanning Tree Protocol
- IGMP Snooping
- DHCP Snooping and Option 82
- MTU on RouterBOARD
- Layer2 misconfiguration
- Powered by Atlassian Confluence 8.9.1
- Printed by Atlassian Confluence 8.9.1
- Report a bug
- Atlassian News
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
Unable to remove a port from default VLAN
I am unable to remove a port from my default VLAN .
I've tried:
It has no errors but when I check it using:
Then the port I try to remove is still in vlan 1.
I'm using a Cisco Catalyst 3550 .
- Is it possible to remove a port from this VLAN?
- 1 AFAIK, It cannot not be a member of any VLAN. If you don't want the port in VLAN 1 then you need to assign it to another VLAN. A port cannot be removed from the Native/Default VLAN without being assigned to another VLAN. – joeqwerty Dec 17, 2014 at 15:42
- Like Joe says...if you don't want it in any vlan then just disable the port, it'll still be a member of VLAN 1 but won't pass traffic. – TheCleaner Dec 17, 2014 at 15:45
A port must have a VLAN assignment. If you need it to be completely disconnected, set it to a nonexistent VLAN and shut down the port.
(I'm not sure if the "no" is required. Don't have a switch at my fingers with an open port to test).
That said, shutdown should be sufficient in and of itself.
- Depending on the switch you could set the interface to no switchport , but you would need to remember to set it back when configuring as a L2 interface. Also the no switchport access vlan 1 is not required, as you have set it do a different vlan already. – cpt_fink Dec 23, 2014 at 4:29
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged cisco port switch vlan ..
- The Overflow Blog
- An open-source development paradigm
- Developers get by with a little help from AI: Stack Overflow Knows code...
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
- What deliverables would you like to see out of a working group?
Hot Network Questions
- Gap between F22 ailerons and flaperons
- What is a "rapid changes in gravitational force"
- Waking up in the middle of a dream
- Why are my benchmark times not repeatable, even for a CPU-bound task?
- Break a word into vowels and consonants
- What ways can a pure martial get find familiar at level 1?
- Do you agree with ChatGPT’s answer to question : Is vedana a Sankhara?
- Make two disks just touch
- “Do you love Me more than these?”
- What types of observations necessitate postulating more complex theories without violating Occam's Razor?
- I just ordered a 26 by 1.95 tube but my tire is marked 26 by 2.10. Will the 1.95 tube fit the 2.10 tire?
- They would/will have been married forty years come this June
- Is the Rocket Lab launch scheduled for May 31 only launching a tiny cubesat?
- How many individual extrasolar "shiny" objects has humanity identified?
- what orders to be triggered after a stock splits?
- Compare two strings, with NaC
- When we classify a polynomial as binomial, trinomial, etc., do we have to simplify it first?
- Is probability physical or idealistic? Is probability an inherent part of nature/reality?
- My MTB has slightly longer reach for my size
- Changing file permissions from 777 to 755 or changing the owner doesn't do anything
- What is "Arduino Optocoupler Disease"?
- Poul Anderson short story about a communitarian town with two curmudgeons who have conflicting views
- Second floor thermostat, battery powered, does absolutely nothing and appears to not be connected to anything
- How to select all intersecting vertices like a boolean?

- CCNA 200-301
- CCNA 200-301 Labs
- CCNP 350-401 ENCOR
- CCNP 350-401 ENCOR Labs
- CCNP 300-410 ENARSI
CCIE Enterprise Infrastructure
- Cisco Packet Tracer Lab Course
- NRS II IRP Course
- NRS II MPLS Course
- NRS II Service Architecture
- Nokia Configuration Course
- Nokia SRC Program
- JNCIA Junos
- HCIA (HCNA)
- HCIA Configuration Course
- What is Huawei R&S Certification?
- Huawei ICT Certifications
- Python Course
- IPv6 Course
- IP Multicast Course
- NRS I Configuration Course
- Cisco Packet Tracer How To Guide
- Online Courses
- Udemy Courses
- CCNA Flashcard Questions
- Protocol Cheat Sheets
- Subnetting Cheat Sheet
- Linux Cheat Sheet
- Python Cheat Sheet
- CLI Commands Cheat Sheets
- Miscellaneous Cheat Sheets
- Cisco Packet Tracer Labs
- Cisco GNS3 Labs
- Huawei eNSP Labs
- Nokia GNS3 Labs
- Short Config Videos
- Network Tools
- IPCisco on Social Media
- Network Engineer Interview Questions
- Personality Interview Training
- Sign In/Up | Members
- Lost password
- Sign In/Sign Up
- ENROLL HERE

- VLAN Port Types and Port Assignment
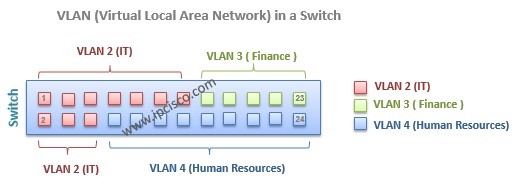
In this lesson, we will focus on some of the key lessons of VLANs. We will learn how to assign ports to VLAN, VLAN Port types and VLAn Tagging.
Table of Contents
Static and Dynamic VLAN Assignments
VLANs can be assigned statically and dynamically . Static configuration is more common, but dynamic is also used.
Static VLAN assignment is like its name. You will statically assign the ports to the VLAN.
Dynamic VLAN assignment can be done by VLAN Membership Policy Server(VMPS) . VMPS needs VLAN-MAC address relationship database. Here, we will use the static one, like many network engineer.
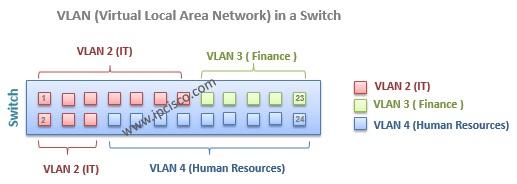
VLAN Port Types
There are two type port used in VLANs. These are: – Access Ports, – Trunk Ports
Access ports are the ports that are member of a single VLAN . Host devices are connected to it. This is also default Cisco switch port type.
Trunk ports are the ports that are member of more than one VLAN or all VLANs . This ports are used between switches. To span VLANs between more than one switch, some ports are needed to carry VLAN information accross the switches. These ports are trunk ports. You can also carry each VLAN without using any trunk port. But this way is not efficient and not common.
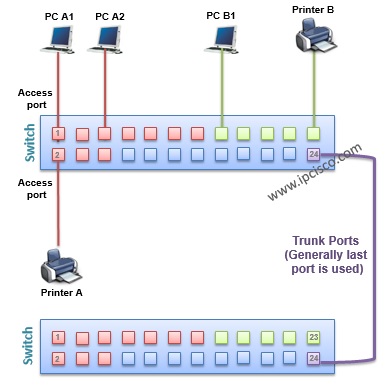
VLAN Frame Tagging
While carrying the frames between VLANs across multiple swithes, frame tagging is required. Because the other end switch need to understand that where the frame will go ( to which VLAN) on the other end. And tagging is used only for the frames going out a trunk port. This is not used for access ports, and anyway this is not necessary.
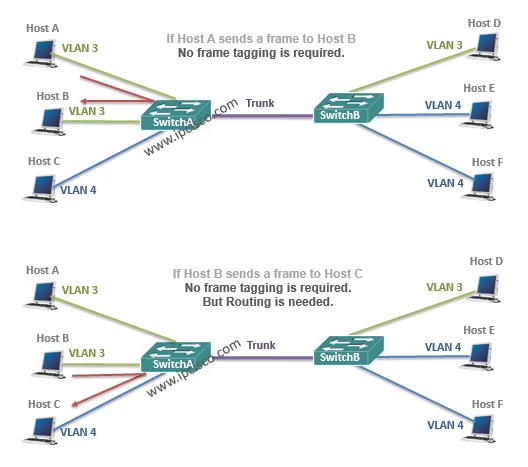
No VLAN Frame Tagging Require
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
- IPv6 Configuration on Cisco
- IPv6 Link Local Address Type
- Subnetting IPv6
- TACACS+ Configuration on Packet Tracer
Access-Lists (ACLs)
- Extended Access List Configuration
- Standard ACL Configuration With Packet Tracer
- Access Control Lists for Traffic Control
- OSPF Virtual-Link Configuration On Packet Tracer
- OSPF SPF and Cost
- OSPF Overview
- OSPF Adjacency Mechanims
- OSPF Packet Types
- OSPF LSA Types
- OSPF Area Types
- OSPF Network Types
- OSPF Miscellenaous
- Single Area OSPF Configuration on Cisco IOS
- OSPFv3 Configuration on Cisco IOS
- OSPF Standard Area and Backbone Area
- OSPF External Routes
- OSPF Stub Area and Totally-Stub Area
- OSPF NSSA and Totally NSSA
Link Aggregation
- PAgP Configuration
- Link Aggregation on Cisco IOS XR
- LACP Configuration
- VLAN Configuration Example 2
- VLAN Configuration Example
- VLAN Frame Tagging Protocols
- RIP Configuration Example
- RIPng Configuration Example
Neighbor Discovery
- IPv6 NDP (Neighbour Discovery Protocol)
- CDP Configuration Example
- LLDP Configuration Example
- Neighbour Discovery Protocols
Routing Fundamentals
- CIR and PIR
- IPv6 Static and Default Route Configuration
- Static Route Configuration
- Dynamic Routing Protocols
- BFD (Bidirectional Forwarding Detection)
- EIGRP For IPv6 Configuration Example
- EIGRP for IPv6
- EIGRP Configuration Example
- EIGRP Miscellenaous
- EIGRP Packet Types and Neighbourship Establishment
- EIGRP Tables Types
- Inter VLAN Routing
- SVI Configuration Example
- Inter VLAN Routing Configuration Example
- Frame-Relay Configuration with both Inverse-ARP and Frame-Relay Map
- Multipoint Frame Relay Configuration
- Frame Relay Point-to-Point Configuration
- Metro Ethernet
First Hop Redundancy
- HSRP Configuration Example
- First Hop Redundancy Protocols
- VRRP Configuration Example
- GLBP Configuration Example
- Cisco BGP Route Reflector Config on GNS3
- BGP Confederation
- BGP Route Reflector
- BGP Community
- Path Attributes: MED
- Path Attributes: Origin
- Path Attributes: AS Path
- Path Attributes : Local Preference
- Path Attributes: Weight
- BGP Next Hop Self
- BGP Configuration Example
- BGP Path Attributes
- IBGP versus EBGP
- BGP Peers, BGP Sessions and BGP Messages
- ISIS for IPv6
- ISIS For IPv6 Configuration on Cisco IOS
- ISIS Configuration Example on Cisco IOS
- IS-IS versus OSPF
- IS-IS Adjacency
- IS-IS Packet Types
- IS-IS Addresses
- SNMP Configuration Example
- Private VLANs
- Private VLAN Configuration on Cisco
- DHCP Snooping Configuration on Packet Tracer
- DHCP Option 82
- DHCP Operation
- How to Configure DHCP on Cisco Routers?
- What is DHCP?
- What is DHCP Snooping?
- Gratuitous ARP
- SCTP (Stream Control Transmission Protocol)
- TCP Header Flags
- TCP Window Size, Checksum and Urgent Pointer
- TCP Header Options
- TCP Header Overview
- TCP Sequence & Acknowledgement Number
- TCP versus UDP
Switch Security
- Switch Port Security
- Switch Port Security Configuration Example
- What is Protected Port ?
VTP, GVRP, MVRP
- MVRP Configuration on Cisco
- GVRP Configuration on Cisco
- VTP Configuration Example
- PVST+ and Rapid PVST+Configuration on Packet Tracer
- PVST+ and Rapid PVST+
- MST (Multiple Spanning Tree)
- MST Configuration on Cisco
- Portfast, Root Guard, BPDU Filter and BPDU Guard
- Loop Guard, Uplink Fast, Backbone Fast and UDLD
- STP Operation
- STP Configuration Example
- RSTP Configuration Example
- STP Portfast Configuration Example
- SDN Components
- New Features Coming with SDN
- Traditional Networks Versus SDN
- SDN Overview
IGMP and MLD
- CGMP (Cisco Group Management Protocol)
- IGMP Snooping
- Cisco IGMP Configuration Example
- MLD Snooping Configuration Example
- MLD Operations
- MLD Configuration Example
- Unicast, Broadcast, Multicast, Anycast
- IGMPv3 Overview
- Multicast IP Addressing
- Multicast MAC Addresses
- QoS Policing and Shaping
- QoS Classification and Marking
- MPSL Label Distribution
- Enabling MPLS On Cisco Routers
- Cisco VPLS Configuration
- MPLS Label Switching Mechanims
- MPLS Basics
- MPLS VPN Labelling
LDP and RSVP
- LDP Label Distribution
IPv4 and IPv6
- IPv4 Subnetting
- IPv4 Addressing
- IPv6 Addressing
- IPv6 Address Types
Traffic Capture
- ERSPAN Configuration on Packet Tracer
- Remote SPAN Configuration on Packet Tracer
- Cisco SPAN Overview
- Local SPAN Configuration on Packet Tracer
Cisco SD-WAN
- Cisco SD-WAN Verification
- Cisco vSmart Controller Configuration
- Cisco vBond Initial Configuration
- Cisco SD-WAN Components
- SD-WAN Architecture
Network Security
- Access Control Lists
- 802.1x (Port Based Network Access Control)
- EAPoL (Extensible Authentication Protocol over LAN)
Network Time Protocol
- NTP (Network Time Protocol)
- Cisco NTP Configuration

Route Redistribution
- Route Redistribution: OSPF and EIGRP
- Connected Networks and Static Routes Redistribution
Other Lessons
- VPN Types and Protocols of VPN
- Configuration Register
- Ethernet Collisions and Troubleshooting
Latest Lessons
- VLSM Subnetting Part of: CCNA 200-301
- Coaxial Cable Details Part of: CCNA 200-301
- IPv4 vs IPv6 Comparison Part of: CCNA 200-301
- IGMPv3 Overview Part of: IP Multicast Course
- IGMPv3 Overview Part of: CCIE Enterprise Infrastructure
- Subnetting IPv6 Part of: CCIE Enterprise Infrastructure
- IPv6 and Subnetting Part of: CCNP Enterprise 350-401 ENCOR
- IPv6 Link Local Address Type Part of: CCIE Enterprise Infrastructure
- Cisco Switch Configuration on Cisco Packet Tracer Part of: CCNA 200-301
- Switch Configuration on Cisco Packet Tracer Part of: Cisco Packet Tracer Lab Course
- More Lessons
Latest Blog Posts
WHAT YOU WILL FIND?
- 250.000+ Students All Over The World
- 8.000+ Questions & Answers
- 100+ Lab Files & Cheat Sheets
- 30+ IT/Network Courses
- A Real Desire To Help You
- Daily Social Media Shares
- %100 Satisfaction
- CISCO Courses
- NOKIA Courses
- HUAWEI Courses
- JUNIPER Courses
- PYTHON Course
- KEY Courses
- VIDEO Courses
- UDEMY Courses
- Cheat Sheets
- Configuration Files
- Interview Questions
- IPCisco On Social Media
- Pärnu mnt. 139c – 14, 11317, Tallinn, Estonia
- [email protected]
Manual:CRS1xx/2xx series switches
Applies to RouterOS: v6.12 +
Warning: This manual is moved to [ CRS1xx/2xx series switches ]
- 2 Cloud Router Switch models
- 3 Cloud Router Switch configuration examples
- 4 Abbreviations and Explanations
- 5.1 Multiple switch groups
- 6 Global Settings
- 7 Port Settings
- 8.1 Unicast FDB
- 8.2 Multicast FDB
- 8.3 Reserved FDB
- 9.1 VLAN Table
- 9.2 Egress VLAN Tag
- 9.3 Ingress/Egress VLAN Translation
- 9.4 Protocol Based VLAN
- 9.5 MAC Based VLAN
- 9.6 1:1 VLAN Switching
- 10 Port Isolation/Leakage
- 11 Trunking
- 12.1 Shaper
- 12.2 Ingress Port Policer
- 12.3 QoS Group
- 12.4 DSCP QoS Map
- 12.5 DSCP To DSCP Map
- 12.6 Policer QoS Map
- 13.2 ACL Policer
- 14 See also
The Cloud Router Switch series are highly integrated switches with high performance MIPS CPU and feature-rich packet processor. The CRS switches can be designed into various Ethernet applications including unmanaged switch, Layer 2 managed switch, carrier switch and wireless/wired unified packet processing.
Warning: This article applies to CRS1xx and CRS2xx series switches and not to CRS3xx series switches. For CRS3xx series devices read the CRS3xx series switches manual.
Cloud Router Switch models
This table clarifies main differences between Cloud Router Switch models.
Cloud Router Switch configuration examples
Abbreviations and explanations.
CVID - Customer VLAN id: inner VLAN tag id of the IEEE 802.1ad frame
SVID - Service VLAN id: outer VLAN tag id of the IEEE 802.1ad frame
IVL - Independent VLAN learning - learning/lookup is based on both MAC addresses and VLAN IDs.
SVL - Shared VLAN learning - learning/lookup is based on MAC addresses - not on VLAN IDs.
TPID - Tag Protocol Identifier
PCP - Priority Code Point: a 3-bit field which refers to the IEEE 802.1p priority
DEI - Drop Eligible Indicator
DSCP - Differentiated services Code Point
Drop precedence - internal CRS switch QoS attribute used for packet enqueuing or dropping.
Port Switching
In order to setup port switching on CRS1xx/2xx series switches, check the Bridge Hardware Offloading page.
Note: Dynamic reserved VLAN entries (VLAN4091; VLAN4090; VLAN4089; etc.) are created in CRS switch when switched port groups are added when a hardware offloaded bridge is created. These VLANs are necessary for internal operation and have lower precedence than user configured VLANs.
Multiple switch groups
The CRS1xx/2xx series switches allow you to use multiple bridges with hardware offloading, this allows you to easily isolate multiple switch groups. This can be done by simply creating multiple bridges and enabling hardware offloading.
Note: Multiple hardware offloaded bridge configuration is designed as fast and simple port isolation solution, but it limits a part of VLAN functionality supported by CRS switch-chip. For advanced configurations use one bridge within CRS switch chip for all ports, configure VLANs and isolate port groups with port isolation profile configuration.
Warning: CRS1xx/2xx series switches are capable of running multiple hardware offloaded bridges with (R)STP enabled, but it is not recommended since the device is not designed to run multiple (R)STP instances on a hardware level. To isolate multiple switch groups and have (R)STP enabled you should isolate port groups with port isolation profile configuration.
Global Settings
Sub-menu: /interface ethernet switch
CRS switch chip is configurable from the /interface ethernet switch console menu.
Port Settings
Sub-menu: /interface ethernet switch port
Forwarding Databases
Unicast fdb.
Sub-menu: /interface ethernet switch unicast-fdb
The unicast forwarding database supports up to 16318 MAC entries.
Multicast FDB
Sub-menu: /interface ethernet switch multicast-fdb
CRS125 switch-chip supports up to 1024 entries in MFDB for multicast forwarding. For each multicast packet, destination MAC or destination IP lookup is performed in MFDB. MFDB entries are not automatically learnt and can only be configured.
Reserved FDB
Sub-menu: /interface ethernet switch reserved-fdb
Cloud Router Switch supports 256 RFDB entries. Each RFDB entry can store either Layer2 unicast or multicast MAC address with specific commands.
Sub-menu: /interface ethernet switch vlan
The VLAN table supports 4096 VLAN entries for storing VLAN member information as well as other VLAN information such as QoS, isolation, forced VLAN, learning, and mirroring.
Egress VLAN Tag
Sub-menu: /interface ethernet switch egress-vlan-tag
Egress packets can be assigned different VLAN tag format. The VLAN tags can be removed, added, or remained as is when the packet is sent to the egress port (destination port). Each port has dedicated control on the egress VLAN tag format. The tag formats include:
The Egress VLAN Tag table includes 4096 entries for VLAN tagging selection.
Ingress/Egress VLAN Translation
The Ingress VLAN Translation table allows for up to 15 entries for each port. One or multiple fields can be selected from packet header for lookup in the Ingress VLAN Translation table. The S-VLAN or C-VLAN or both configured in the first matched entry is assigned to the packet.
Sub-menu: /interface ethernet switch ingress-vlan-translation
Sub-menu: /interface ethernet switch egress-vlan-translation
Below is a table of traffic that triggers a rule that has a certain VLAN format set, note that traffic that is tagged with VLAN ID 0 is a special case that is also taken into account.
Warning: If VLAN-format is set to any , then customer-vid/service-vid set to 0 will trigger the switch rule with VLAN 0 traffic. In this case the switch rule will be looking for untagged traffic or traffic with VLAN 0 tag, only untagged-or-tagged will filter out VLAN 0 traffic in this case.
Protocol Based VLAN
Sub-menu: /interface ethernet switch protocol-based-vlan
Protocol Based VLAN table is used to assign VID and QoS attributes to related protocol packet per port.
MAC Based VLAN
Sub-menu: /interface ethernet switch mac-based-vlan
MAC Based VLAN table is used to assign VLAN based on source MAC.
Note: All CRS1xx/2xx series switches support up to 1024 MAC Based VLAN table entries.
1:1 VLAN Switching
Sub-menu: /interface ethernet switch one2one-vlan-switching
1:1 VLAN switching can be used to replace the regular L2 bridging for matched packets. When a packet hits an 1:1 VLAN switching table entry, the destination port information in the entry is assigned to the packet. The matched destination information in UFDB and MFDB entry no longer applies to the packet.
Port Isolation/Leakage
Sub-menu: /interface ethernet switch port-isolation
Sub-menu: /interface ethernet switch port-leakage
The CRS switches support flexible multi-level isolation features, which can be used for user access control, traffic engineering and advanced security and network management. The isolation features provide an organized fabric structure allowing user to easily program and control the access by port, MAC address, VLAN, protocol, flow and frame type. The following isolation and leakage features are supported:
- Port-level isolation
- MAC-level isolation
- VLAN-level isolation
- Protocol-level isolation
- Flow-level isolation
- Free combination of the above
Port-level isolation supports different control schemes on source port and destination port. Each entry can be programmed with access control for either source port or destination port.
- When the entry is programmed with source port access control, the entry is
applied to the ingress packets.
- When the entry is programmed with destination port access control, the entry
is applied to the egress packets.
Port leakage allows bypassing egress VLAN filtering on the port. Leaky port is allowed to access other ports for various applications such as security, network control and management. Note: When both isolation and leakage is applied to the same port, the port is isolated.
Sub-menu: /interface ethernet switch trunk
The Trunking in the Cloud Router Switches provides static link aggregation groups with hardware automatic failover and load balancing. IEEE802.3ad and IEEE802.1ax compatible Link Aggregation Control Protocol is not supported. Up to 8 Trunk groups are supported with up to 8 Trunk member ports per Trunk group. CRS Port Trunking calculates transmit-hash based on all following parameters: L2 src-dst MAC + L3 src-dst IP + L4 src-dst Port.
Quality of Service
Sub-menu: /interface ethernet switch shaper
Traffic shaping restricts the rate and burst size of the flow which is transmitted out from the interface. The shaper is implemented by a token bucket. If the packet exceeds the maximum rate or the burst size, which means no enough token for the packet, the packet is stored to buffer until there is enough token to transmit it.
Ingress Port Policer
Sub-menu: /interface ethernet switch ingress-port-policer
Sub-menu: /interface ethernet switch qos-group
The global QoS group table is used for VLAN-based, Protocol-based and MAC-based QoS group assignment configuration.
DSCP QoS Map
Sub-menu: /interface ethernet switch dscp-qos-map
The global DSCP to QOS mapping table is used for mapping from DSCP of the packet to new QoS attributes configured in the table.
DSCP To DSCP Map
Sub-menu: /interface ethernet switch dscp-to-dscp
The global DSCP to DSCP mapping table is used for mapping from the packet's original DSCP to new DSCP value configured in the table.
Policer QoS Map
Sub-menu: /interface ethernet switch policer-qos-map
Access Control List
Note: See Summary section for Access Control List supported Cloud Router Switch devices.
Access Control List contains of ingress policy and egress policy engines and allows to configure up to 128 policy rules (limited by RouterOS). It is advanced tool for wire-speed packet filtering, forwarding, shaping and modifying based on Layer2, Layer3 and Layer4 protocol header field conditions.
Warning: Due to hardware limitation it is not possible to match broadcast/multicast traffic on specific ports. You should use port isolation, drop traffic on ingress ports or use VLAN filtering to prevent certain broadcast/multicast traffic from being forwarded.
Sub-menu: /interface ethernet switch acl
ACL condition part for MAC related fields of packets.
ACL condition part for VLAN related fields of packets.
ACL condition part for IPv4 and IPv6 related fields of packets.
ACL rule action part.
Filter bypassing part for ACL packets.
ACL Policer
Sub-menu: /interface ethernet switch acl policer
- CRS1xx/2xx series switches examples
- CRS1xx/2xx VLANs with Trunks
- Basic VLAN switching
- Bridge Hardware Offloading
- Spanning Tree Protocol
- IGMP Snooping
- DHCP Snooping and Option 82
- MTU on RouterBOARD
- Layer2 misconfiguration
- Master-port
[ Top | Back to Content ]
- Bridging and switching
- Routerboard
Navigation menu
- Skip to content
- Skip to search
- Skip to footer
Dynamic VLAN Assignment and Auto Smartport Configuration on a SG350X and SG550X
Available languages, download options.
- PDF (4.0 MB) View with Adobe Reader on a variety of devices
- ePub (3.9 MB) View in various apps on iPhone, iPad, Android, Sony Reader, or Windows Phone
- Mobi (Kindle) (3.7 MB) View on Kindle device or Kindle app on multiple devices
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
This document provides instructions on how to configure the Generic VLAN Registration Protocol (GVRP) settings and Auto Smartport on your switches.
If you are unfamiliar with some terms in this document, check out Cisco Business: Glossary of New Terms .
Introduction
Generic Attribute Registration Protocol (GARP) VLAN Registration Protocol or Generic VLAN Registration Protocol (GVRP) allows devices to dynamically exchange Virtual Local Area Network (VLAN) configuration information to make configuration of VLANs easier. When GVRP is globally enabled, the manually/statically created VLANs will automatically propagate the VLAN ID to interconnecting switches and interfaces. Dynamic VLAN Assignment is used to eliminate the chance for error when configuring VLANs when working with large networks. When the switch receives VLAN information through GVRP and GVRP Registration, the receiving interface joins that VLAN. If an interface attempts to join a VLAN that does not exist and Dynamic VLAN creation is enabled, the switch automatically creates the VLAN.
It is important to note that in order for this to work on an access port, the end device has to be GVRP enabled (GVRP enabled NICs if they are servers or PCs).
Smartport is an interface to which a built-in or user-defined macro may be applied. These macros are designed to provide a means of quickly configuring the device to support the communication requirements and utilize the features of various types of network devices. The network access and QoS requirements vary if the interface is connected to an IP phone, a printer, a router, and/or Access Point (AP).
Applicable Devices
- SG350X Series
- SG550X Series
Software Version
To configure Dynamic VLAN Assignment and Auto Smartport Configuration, follow the guideline below:
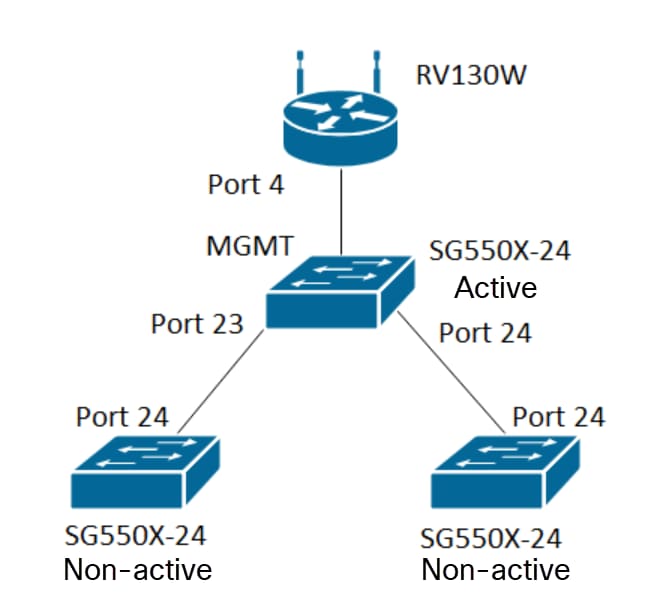
Note: The 2 non-active switches are not connected to the active switch until the conclusion.
The port that is being configured with GVRP must be configured in truck mode or general mode as GVRP requires support for tagging. When the VLAN's propagate from the active switch to the non-active switches via GVRP, it would be considered as dynamic VLANs.
Note : If there is an error "vlan not created by user", then only static VLANs (manually created) can be added to a port configured as an access port. GVRP does not work the same as VTP (Server – Client).
The steps below are configured in Advanced mode in the Display Mode field at the top of the web configuration page .
Table of Contents
- Configuring Auto Smartports on the SG350XG and SG550XG
- Configure GVRP settings on the SG550X-24 (active)
- Setting up VLAN settings on the SG550X-24 (active)
- How to Configure Interface settings on SG550X-24 (active)
- How to Set Up Port VLAN Membership on the active Switch
- Configuring GVRP on the Non-active switch
- Setting up Interface settings on the Non-active switch
Verification
Configure gvrp settings on the sg550x-24 (active).
To learn more about configuring GVRP Settings on a switch, click here .
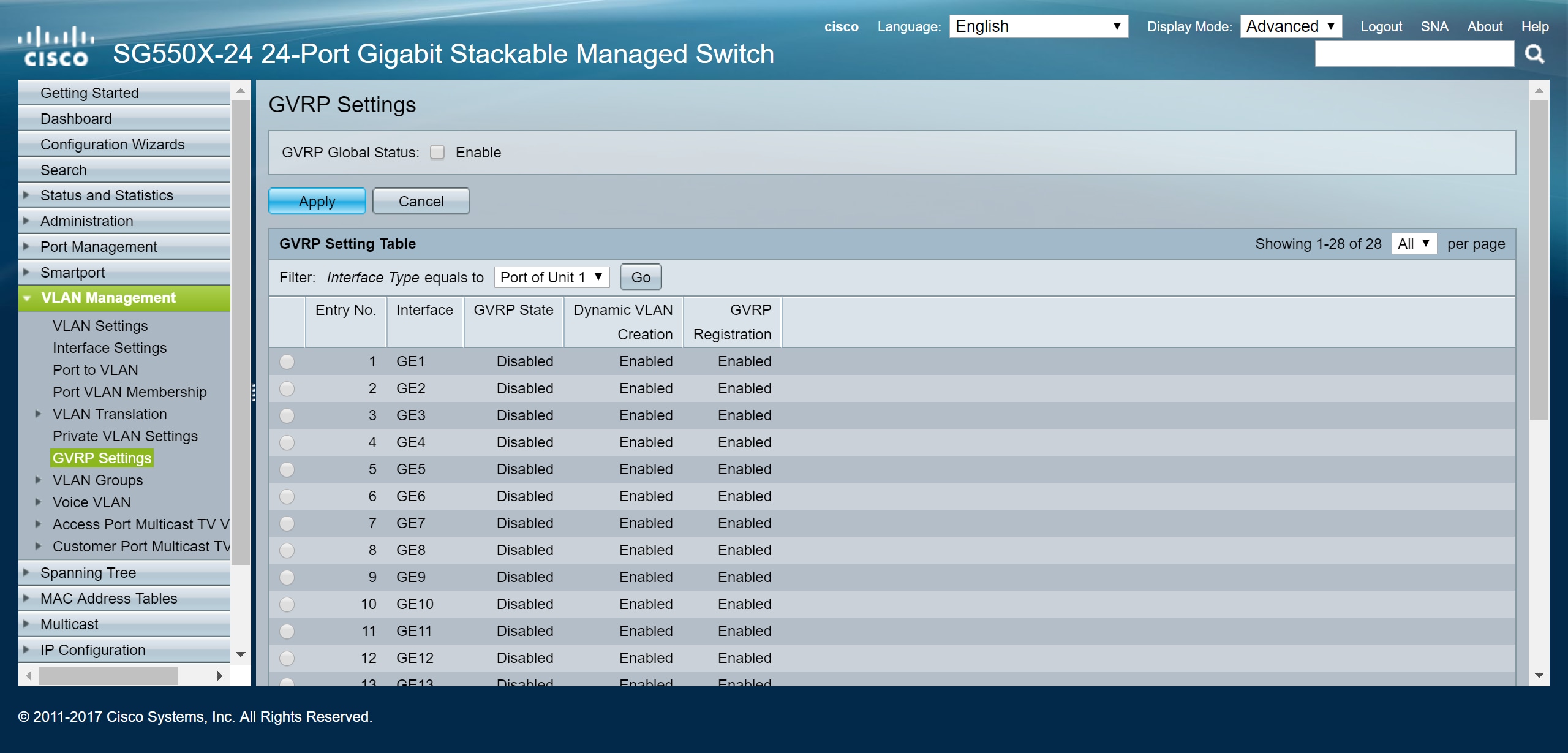
Step 1. Log in to the web-based utility of your active switch and navigate to VLAN Management > GVRP Settings .
Note: In this example, one of the SG550X-24 will be the active switch.
Step 2. Check the Enable checkbox to enable GVRP Global Status to globally enable GVRP on the switch.
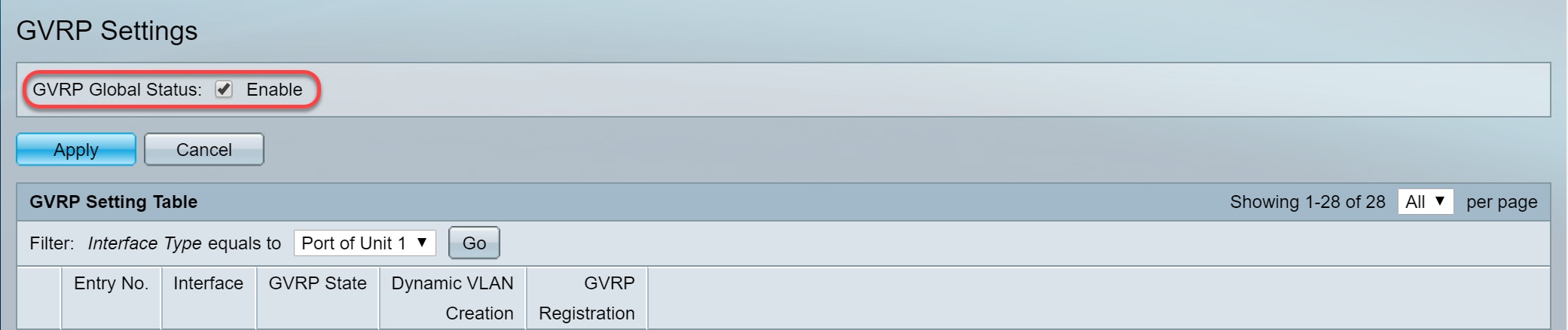
Step 3. Click Apply to enable GVRP features.
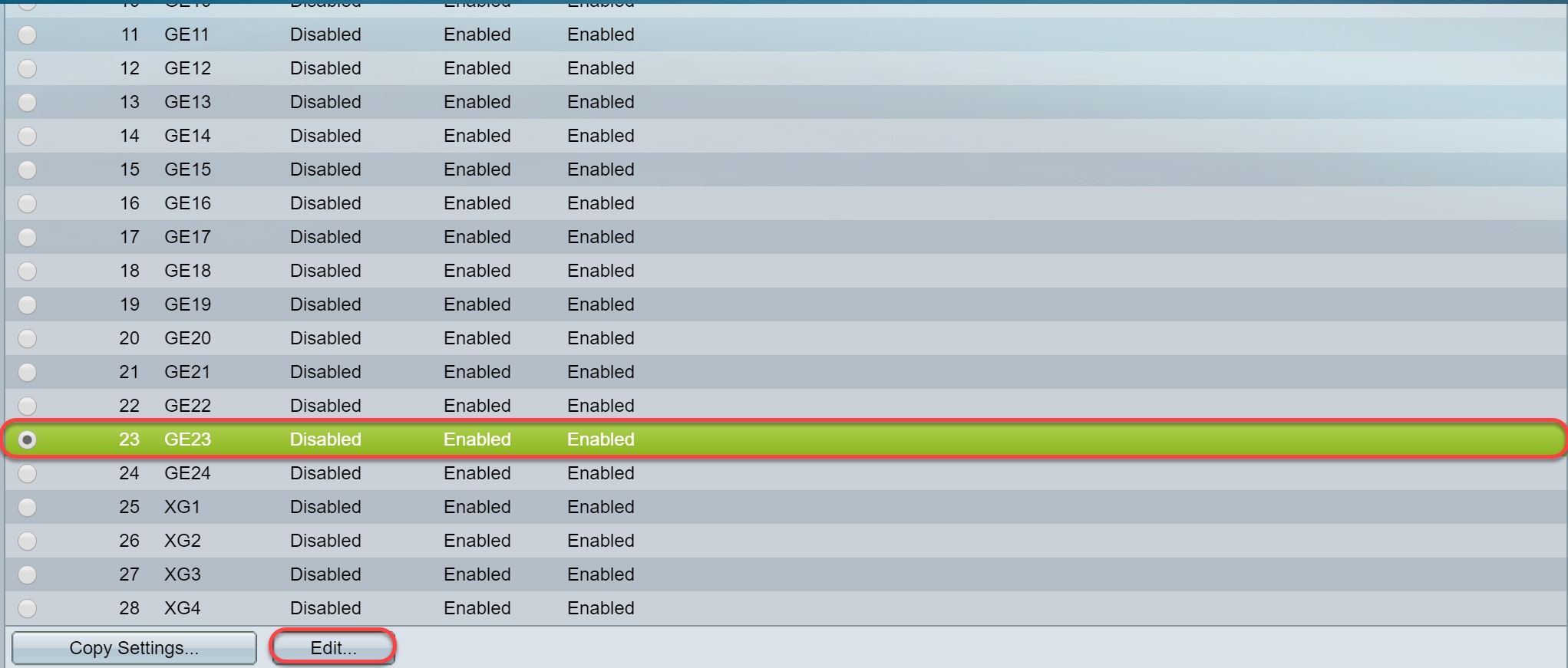
Step 4. Click the radio button of the interface on which you would like to configure GVRP. Then click Edit... to modify the GVRP settings for the selected interface.
Note: In this example, we will be configuring GE23 and GE24.
Step 5. The Edit GVRP Setting window appears.
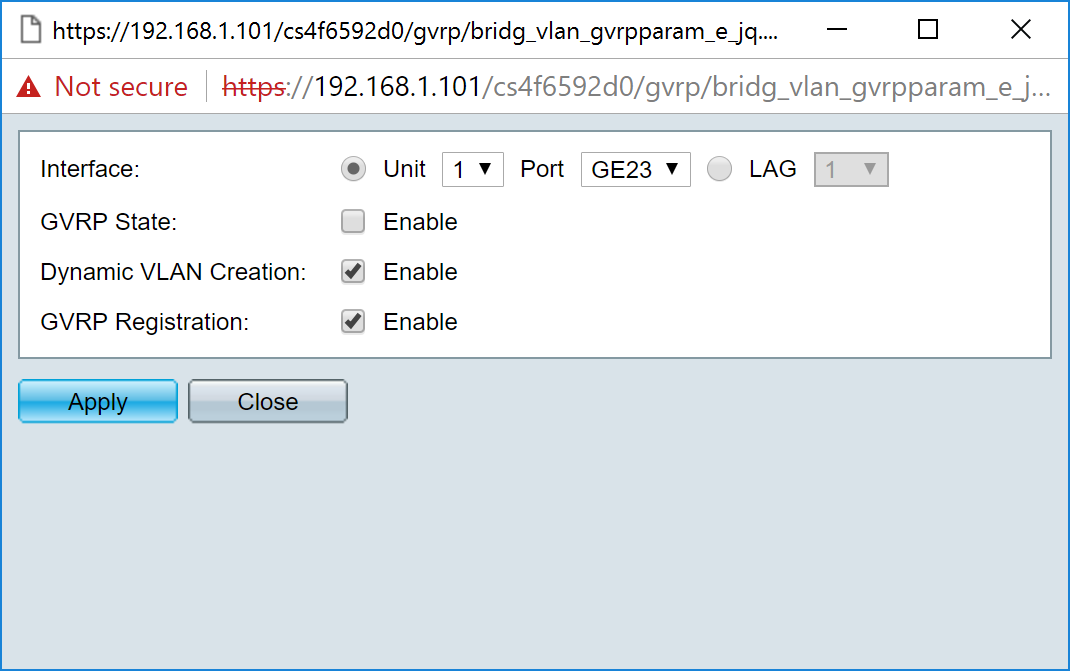
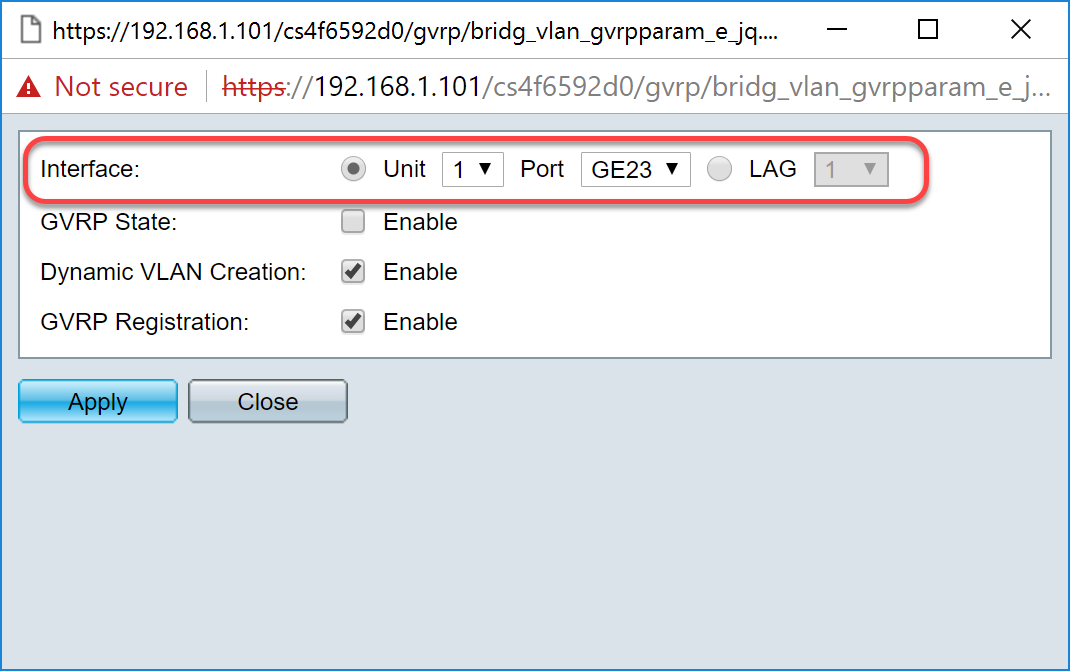
Step 6. (Optional) Click the appropriate radio button and choose a new interface from the Port or Link Aggregation Group (LAG) drop-down list to change the interface whose settings you want to change. LAG bundles individual Ethernet links into a single logical link that can increase the throughput further than a single connection can support.
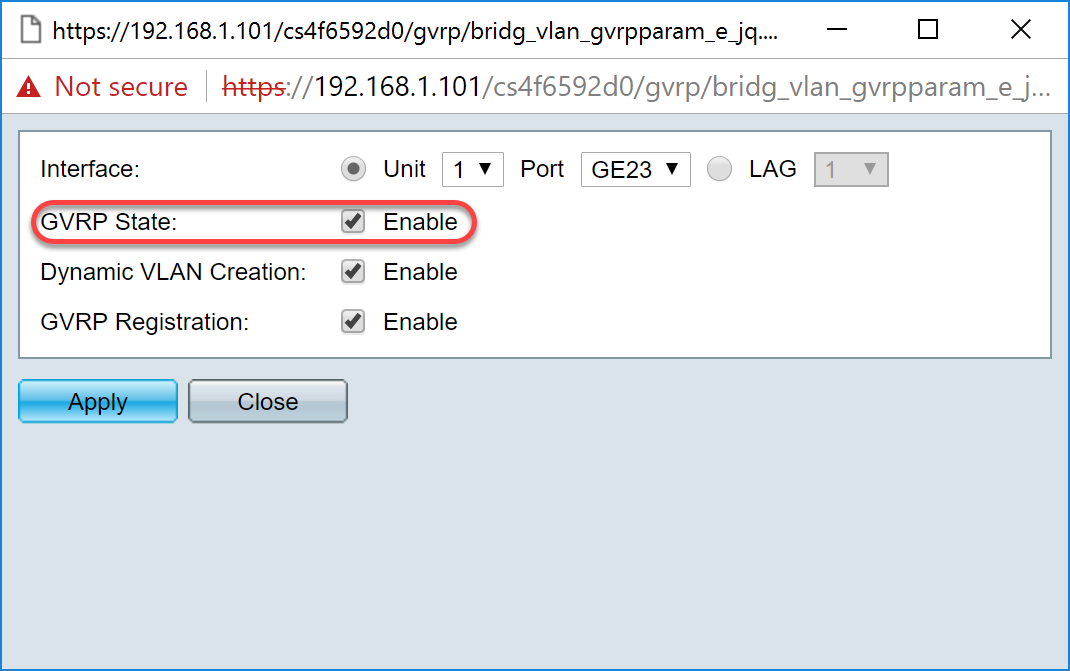
Step 7. Check the Enable checkbox in the GVRP State field to enable GVRP features on this interface.
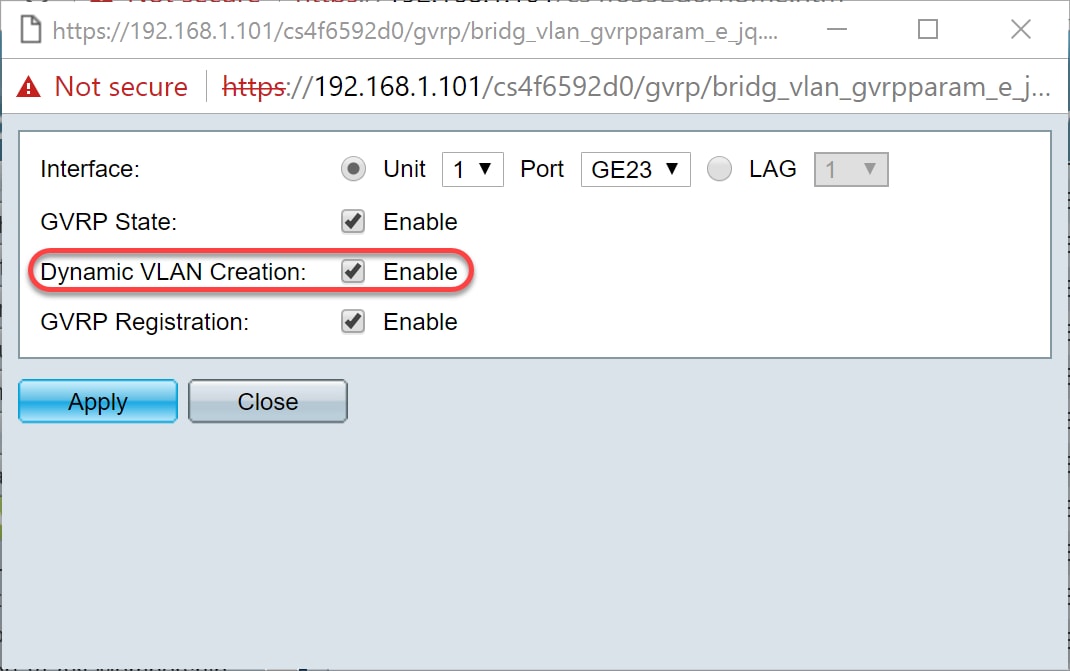
Step 8. Check the Enable check box in the Dynamic VLAN Creation field to have a VLAN dynamically created if it does not exist when GVRP information is received for that VLAN on the selected interface. If Dynamic VLAN Creation is disabled, the switch only recognizes VLANs that have been manually created.
Note: This is enabled by default.
Step 9. (Optional) Check the Enable check box in the GVRP Registration field to have the selected interface join a VLAN when GVRP information is received for that VLAN on the selected interface. If GVRP registration is disabled, an interface only associates with a VLAN that it is manually configured to be on.
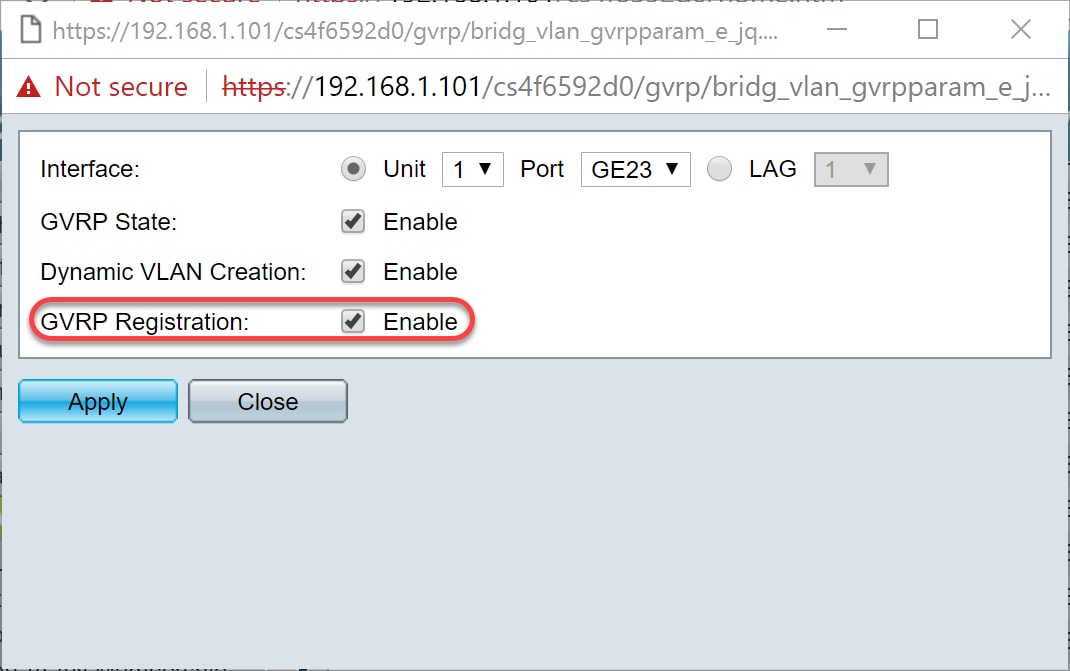
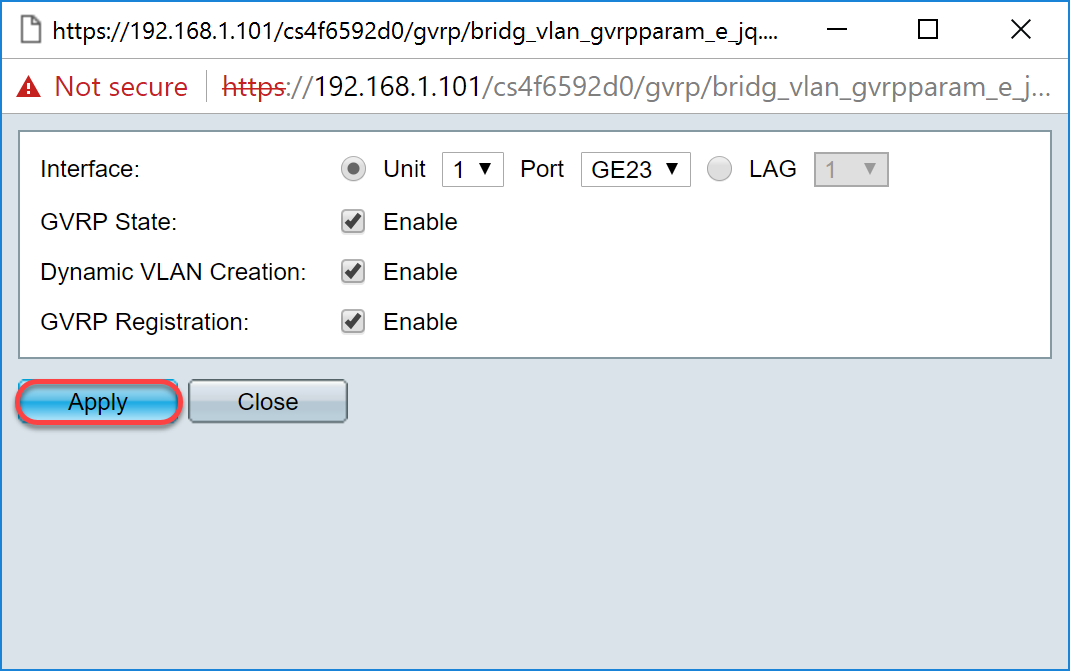
Step 10. Click Apply to save the updated GVRP settings for the selected interface and then click Close to exit the Edit GVRP Setting window.
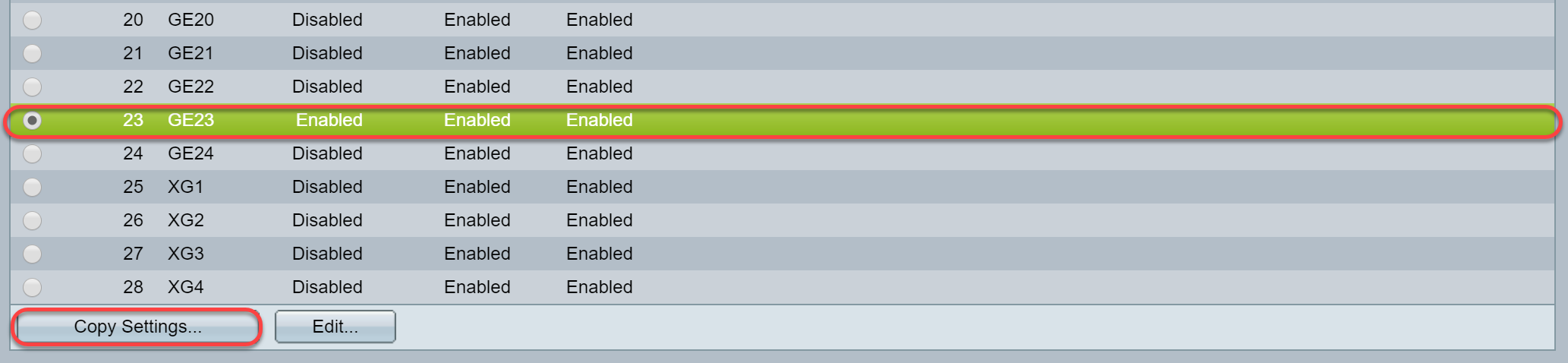
Step 11. (Optional) To copy the GVRP settings of one interface to several other interfaces, click the radio button of the desired interface and click Copy Settings . The Copy Settings window appears.
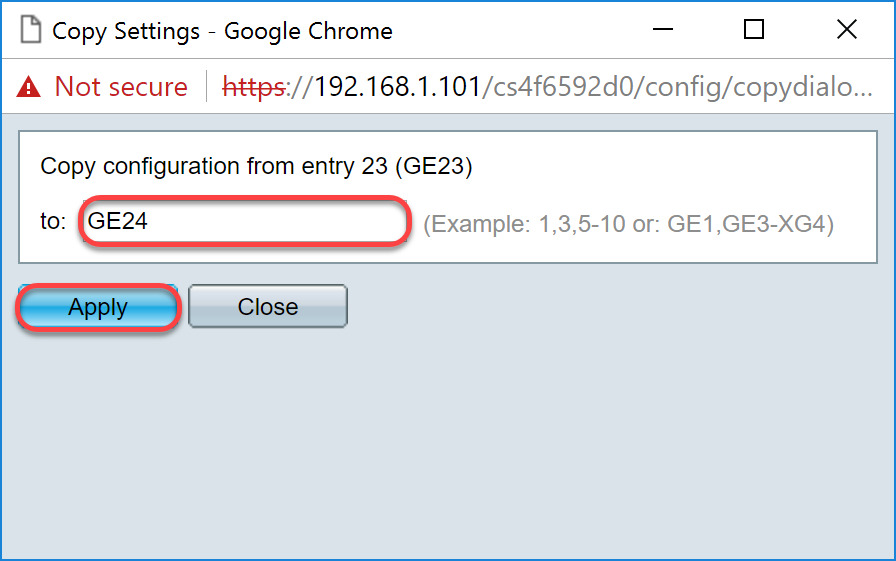
Step 12. (Optional) Enter the interface number(s) or interface name(s) of the interface(s) to which you wish to copy the settings of the chosen interface in the provided field. Then click Apply to save your changes or click Close to cancel your changes.
Setting Up VLAN Settings on the SG550X-24 (active)
Step 1. Navigate to VLAN Management > VLAN Settings .
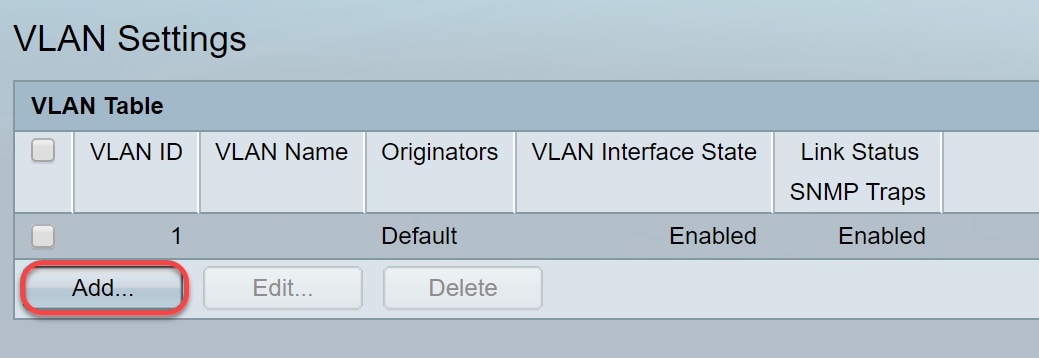
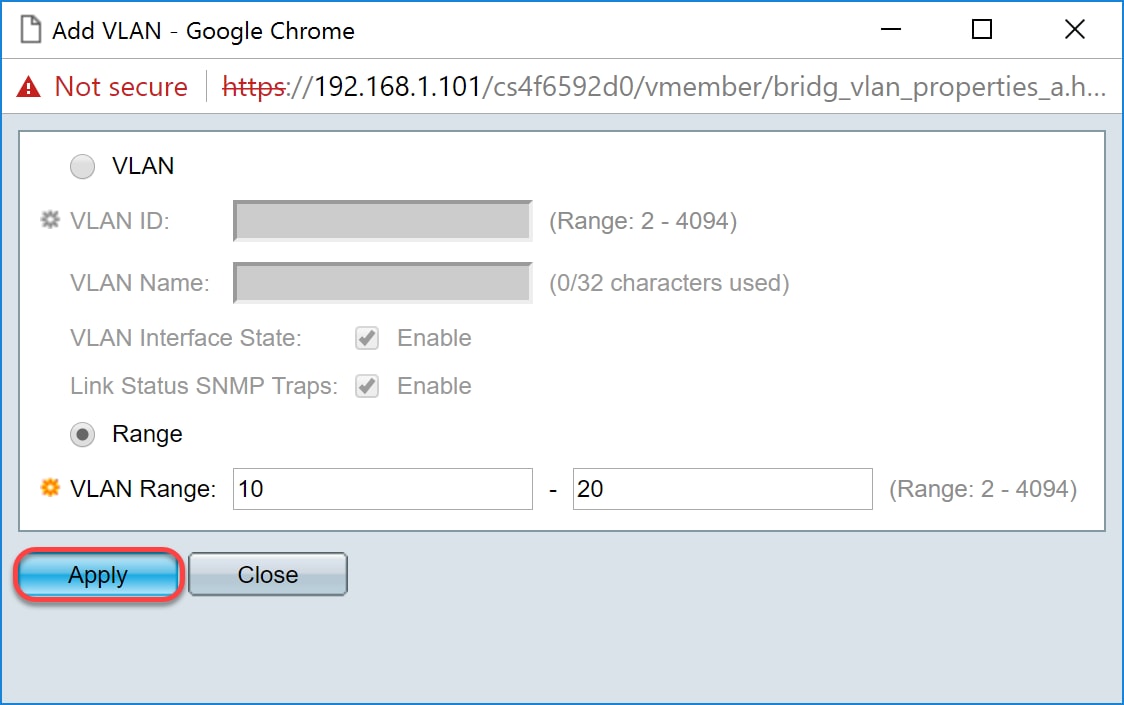
Step 2. Click Add... to create new VLANs. The Add VLAN window appears.
Note: There are two ways to create a VLAN. You can create a single VLAN or you can set a range of new VLANs. In this example, we will be creating a range of VLANs.
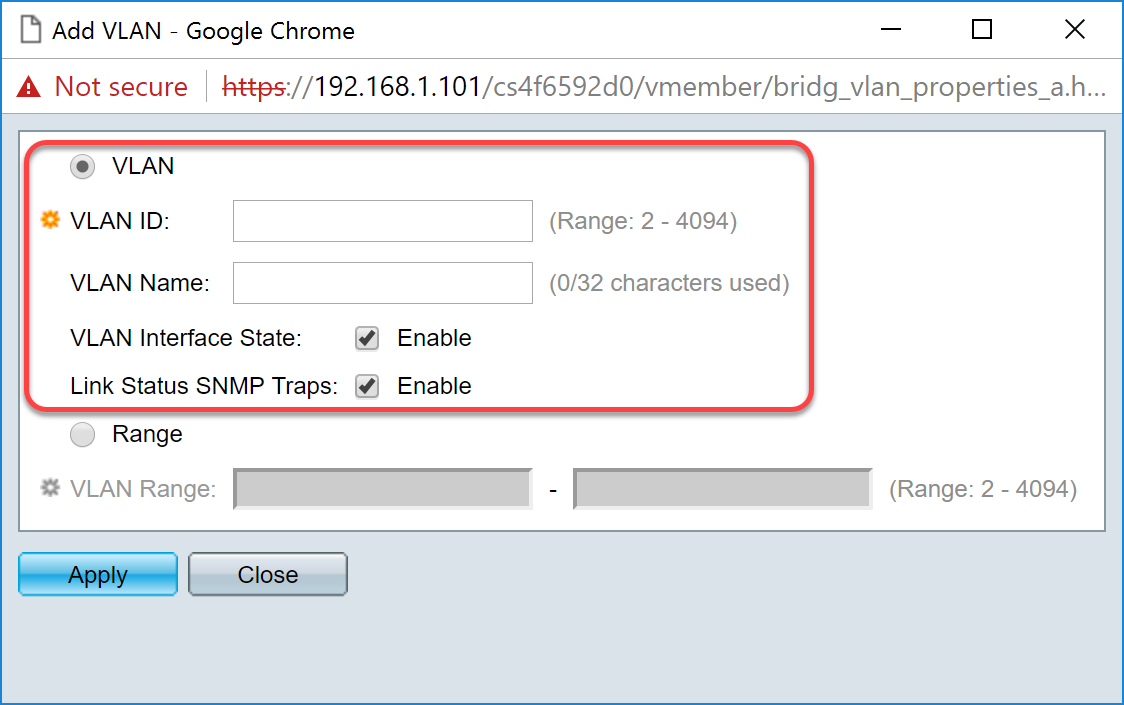
Step 3. To create a single VLAN, click the VLAN radio button. Then enter the following information:
- VLAN ID — The ID of the new VLAN.
- VLAN Name — The name of the new VLAN
Step 4. To create a range of VLANs, click the Range radio button. Then enter the following information:
- VLAN Range — The range, according to the number of VLANs you want to create. For example, if you want to create 10 VLANs, then enter a range that will fit your needs. In this example, we will create VLAN 10 to 20.
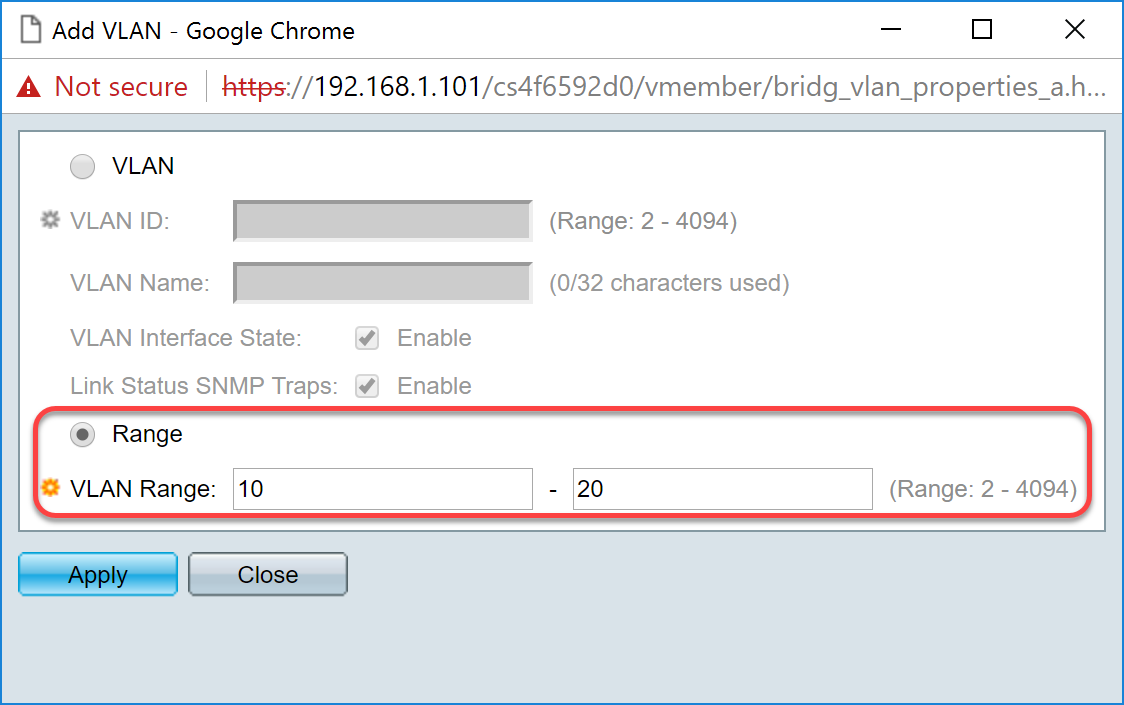
Step 5. Click Apply to save your configuration.
How to Configure Interface Settings on the SG550X-24 (active)
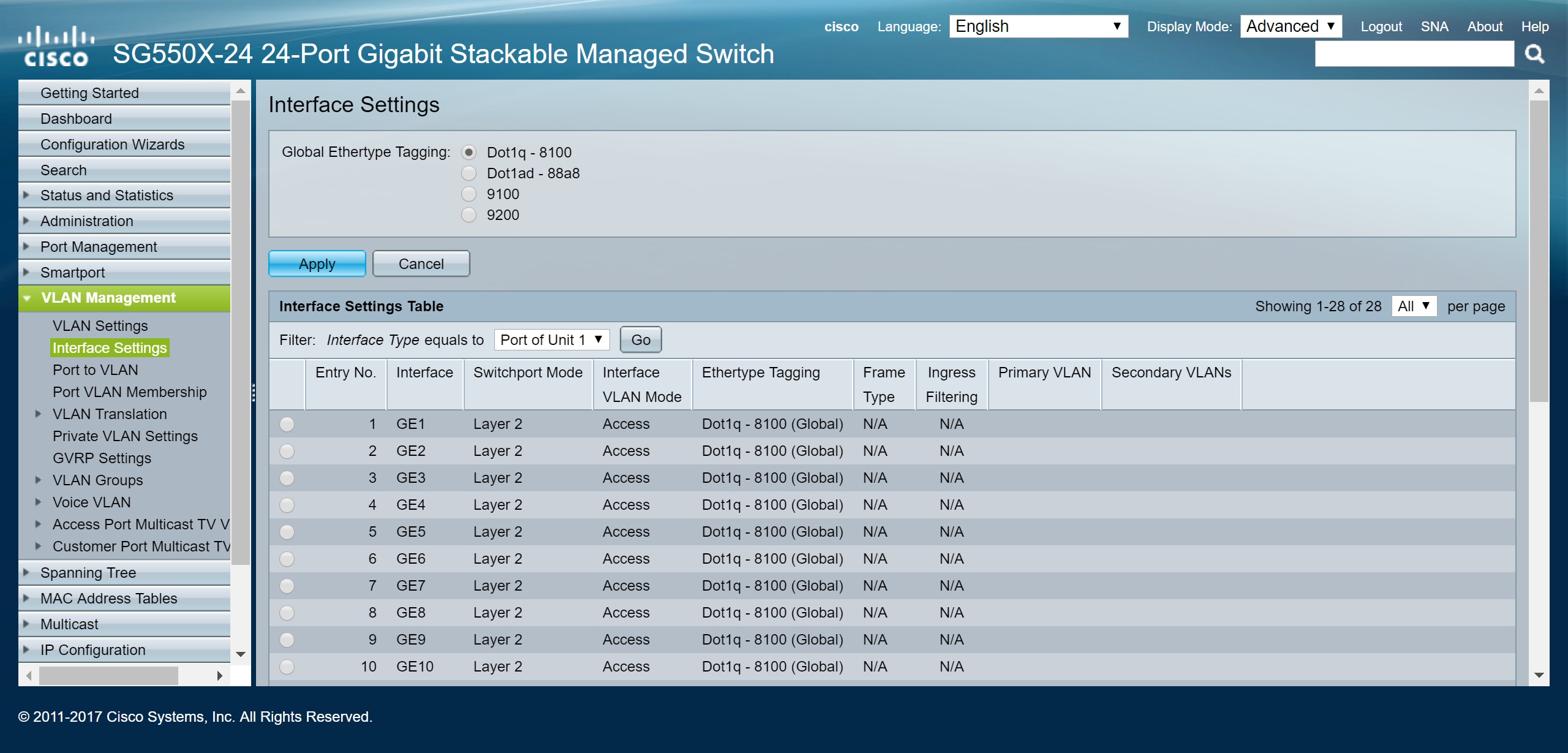
Step 1. Navigate to VLAN Management > Interface Settings .
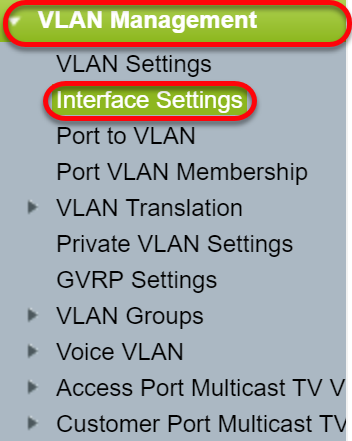
Step 2. Select a Global Ethertype Tagging method. The options are:
- Dot1q-8100 — Also known as IEEE 802.1Q. It is the standard for tagging frames on a trunk and supports up to 4096 VLANs. The TPID is usually set to 0x8100 to identify the frame as an IEEE802.1Q frame.
- Dot1ad-88a8 — implements a standard protocol for double tagging of data by using a feature called QinQ. Data traffic coming from the customer side are double tagged in the provider network where the inner tag is the customer-tag (C-tag) and the outer tag is provider-tag (S-tag). S-VLAN tag or S-tag is known as Service tag which is used to forward packets into the provider network. The S-tag segregate traffic between various customers, while preservice the customer VLAN tags. This is done with QinQ which provides isolation between service provider networks and customers' networks. The device is a provider bridge that supports port-based c-tagged service interface.
- 9100 — Non-standard QinQ ethertype
- 9200 — Non-standard tagging.
Note: In this example, we used the default Dot1q-8100 for the Global Ethertype Tagging.
Step 3. Click Apply .
Step 4. Click the radio button of the interface that you have configured GVRP. Ports that are configured with GVRP needs to be configured as trunk ports.
Note: In this example, we will be configuring GE23 and GE24 as trunk ports.
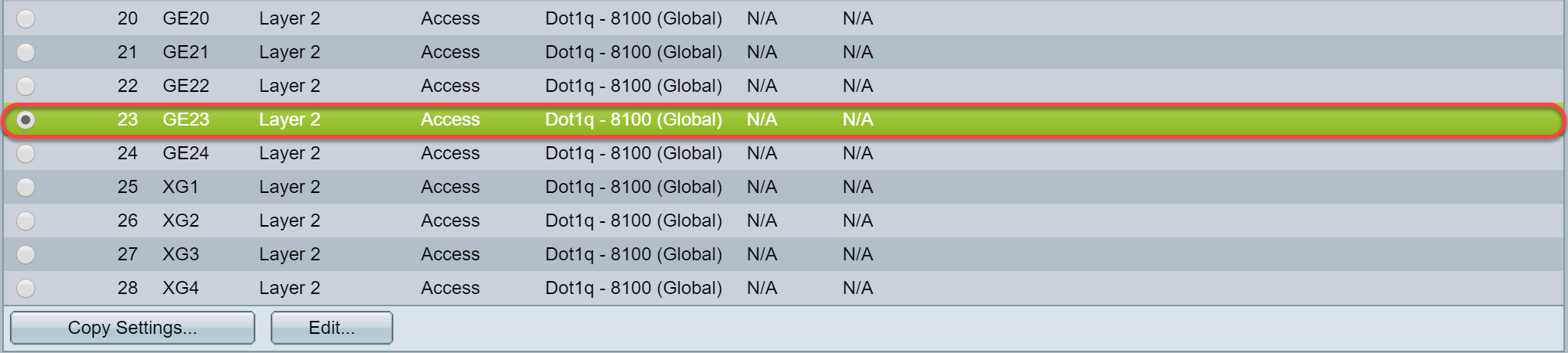
Step 5. Click Edit... to edit the interface. The Edit Interface Settings windows opens.
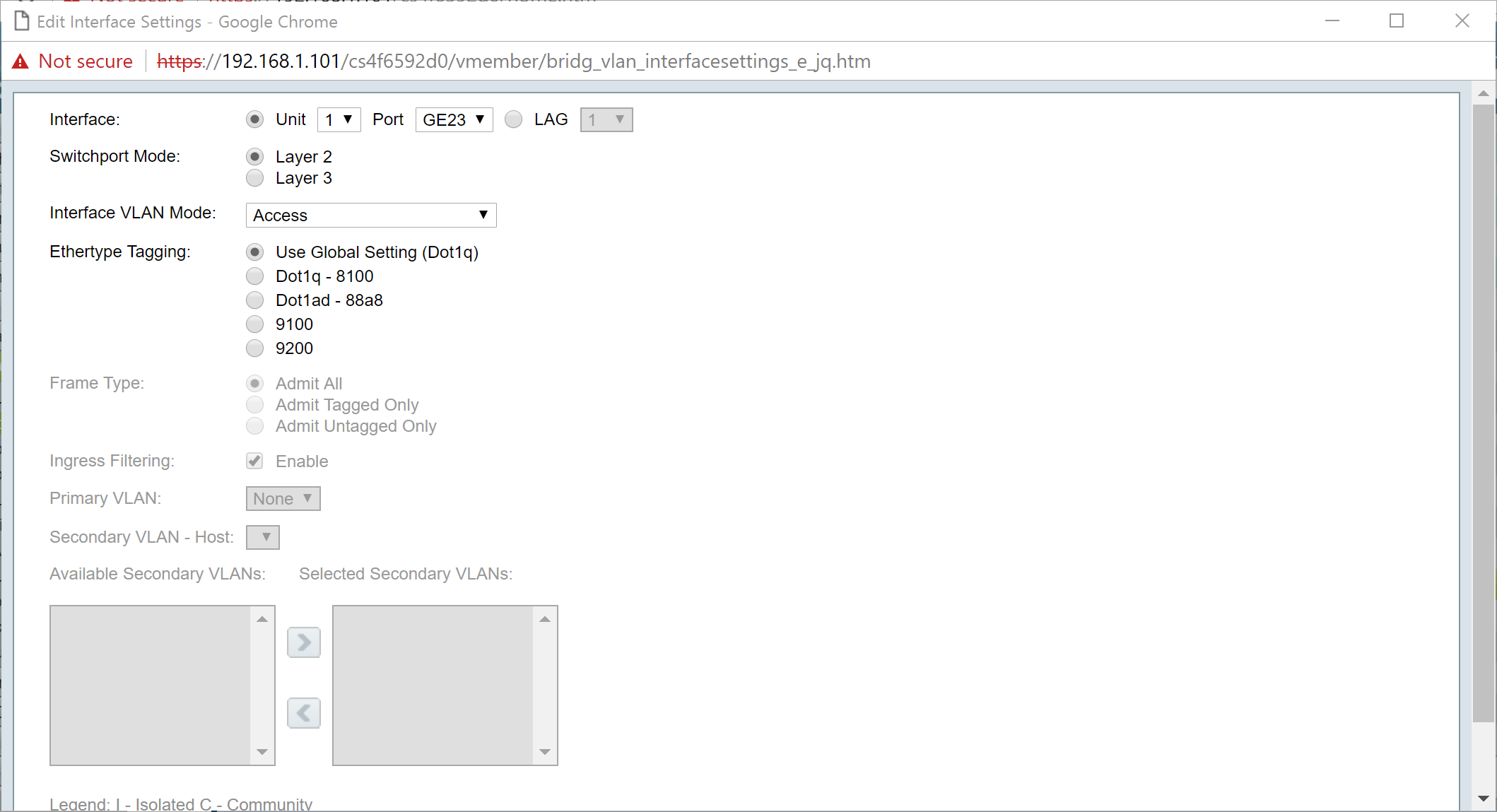
Step 6. (Optional) Click the appropriate radio button and choose a new interface from the Port or LAG drop-down list to change the interface whose settings you want to change.
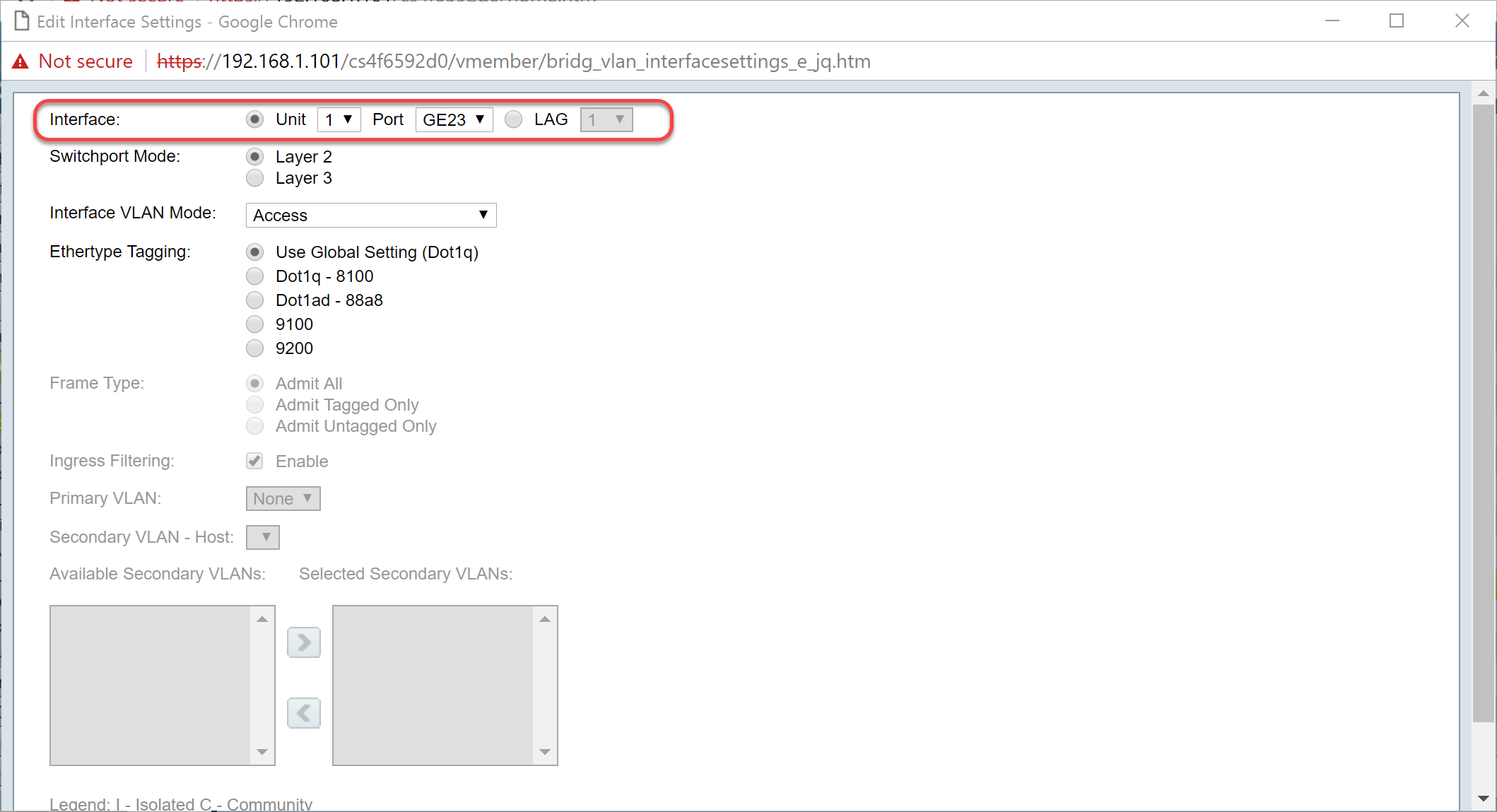
Step 7. Select either Layer 2 or Layer 3 in the Switchport Mode field.
Note: In this example, the default (Layer 2) was selected.
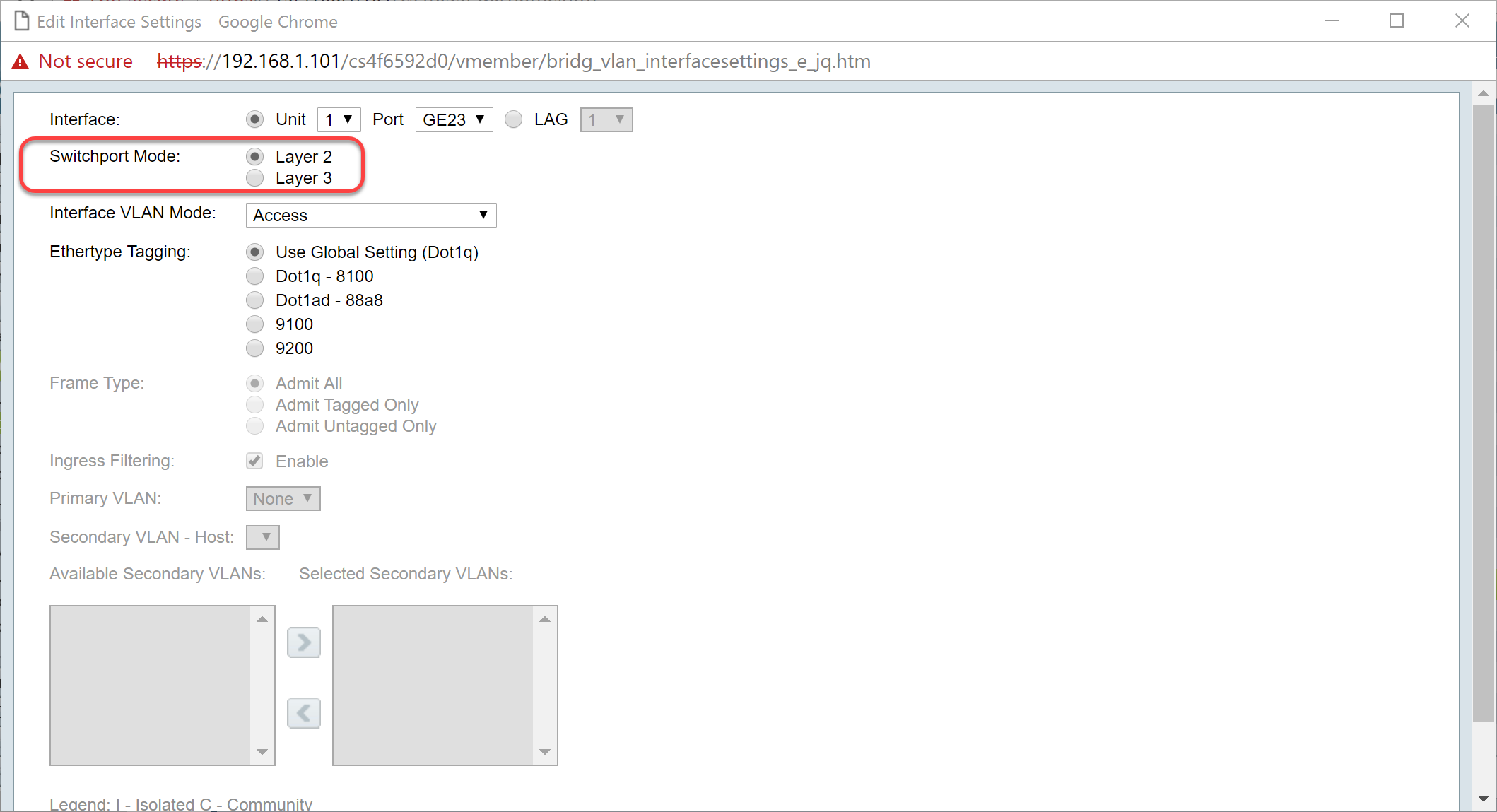
Step 8. Select Trunk in the Interface VLAN Mode drop-down list. The interface is an untagged member of one VLAN at most, and is a tagged member of zero or more VLANs.
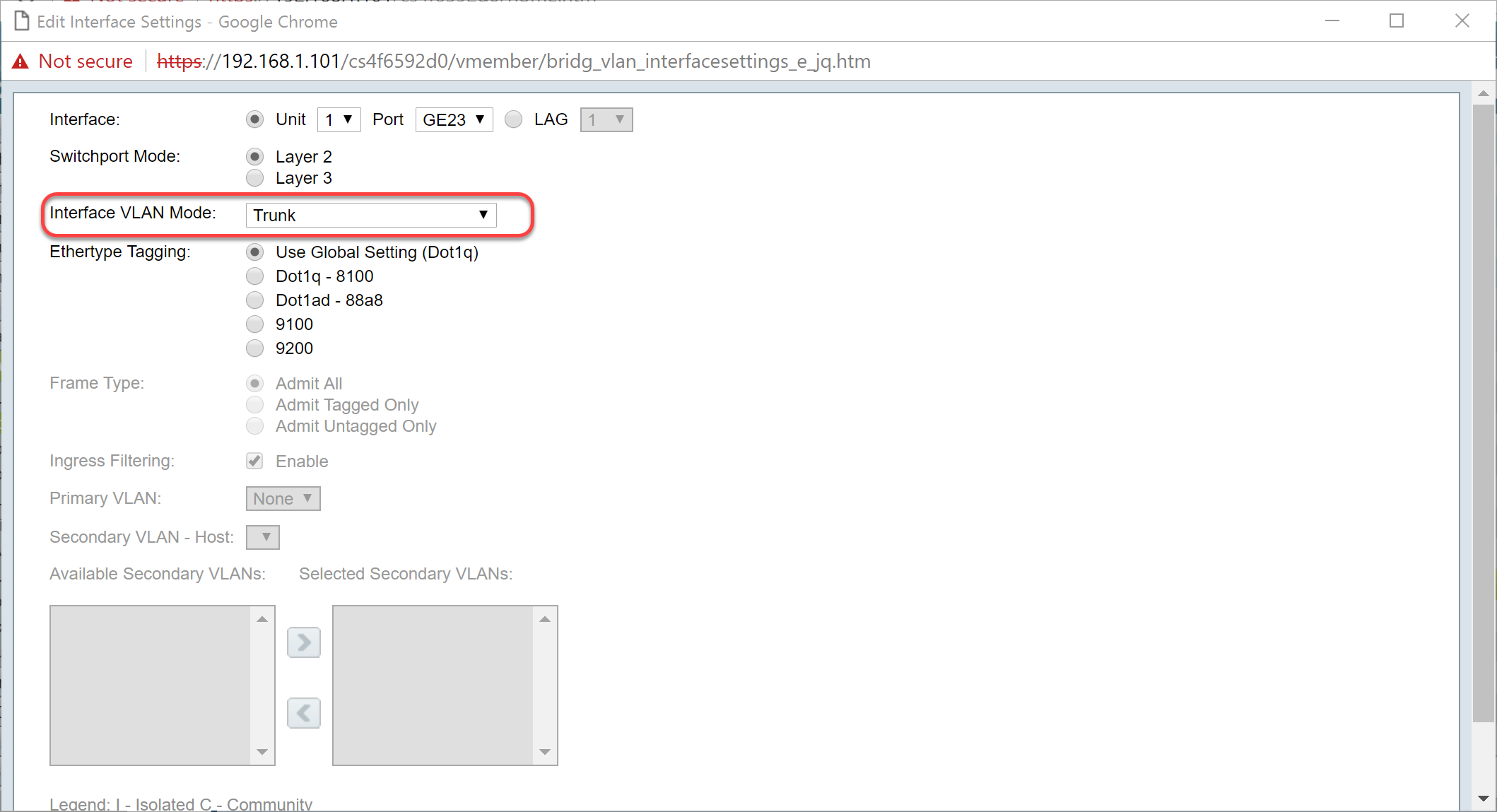
Step 9. Select an Ethertype Tagging method for the S-VLAN tag. The options are:
- Use Global Setting (Dot1q)
- Dot1q - 8100
- Dot1ad - 88a8
Note: In this example, we used the default value: Use Global Setting (Dot1q) .
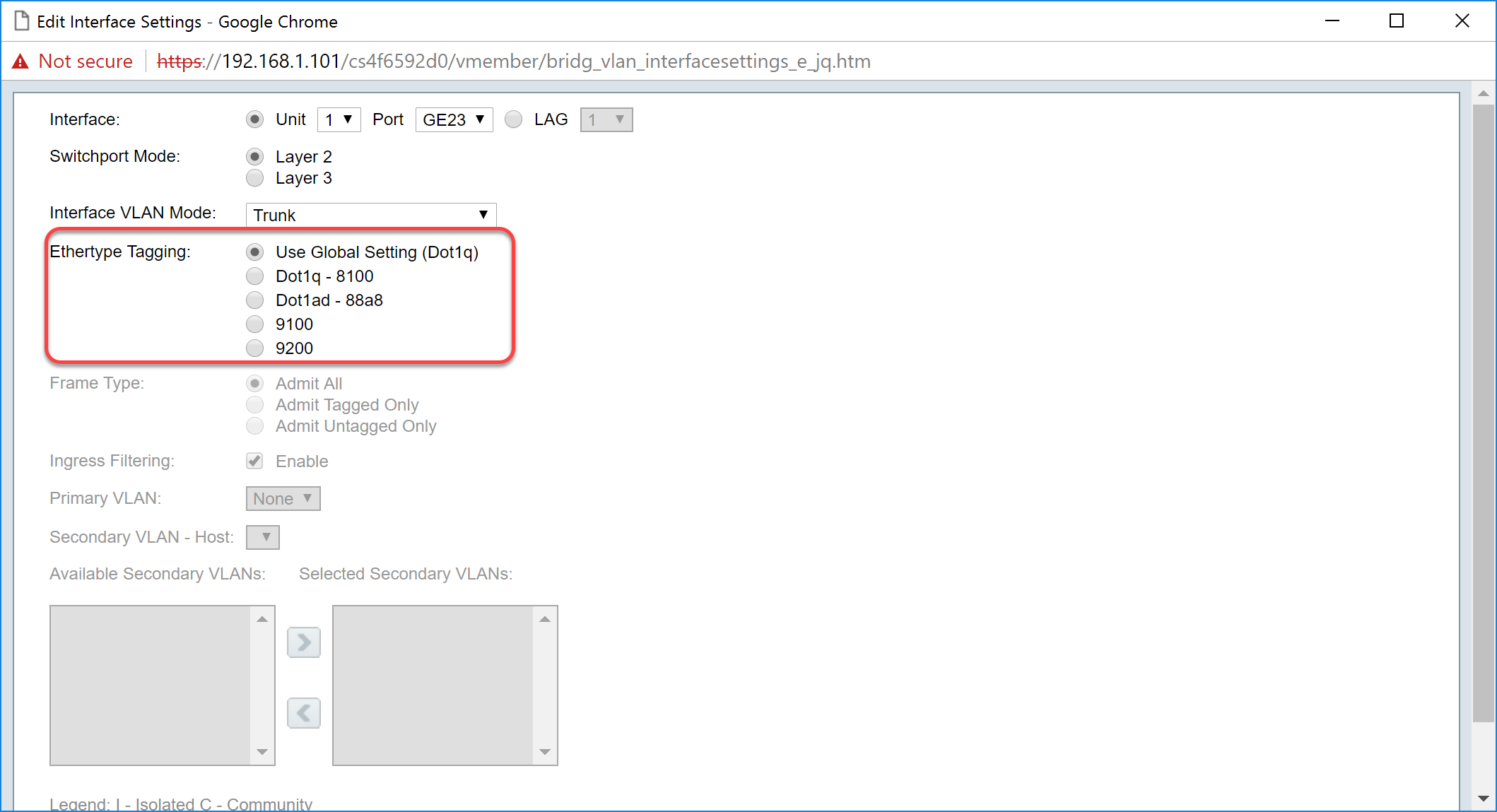
Step 10. Then click Apply to save the changes.
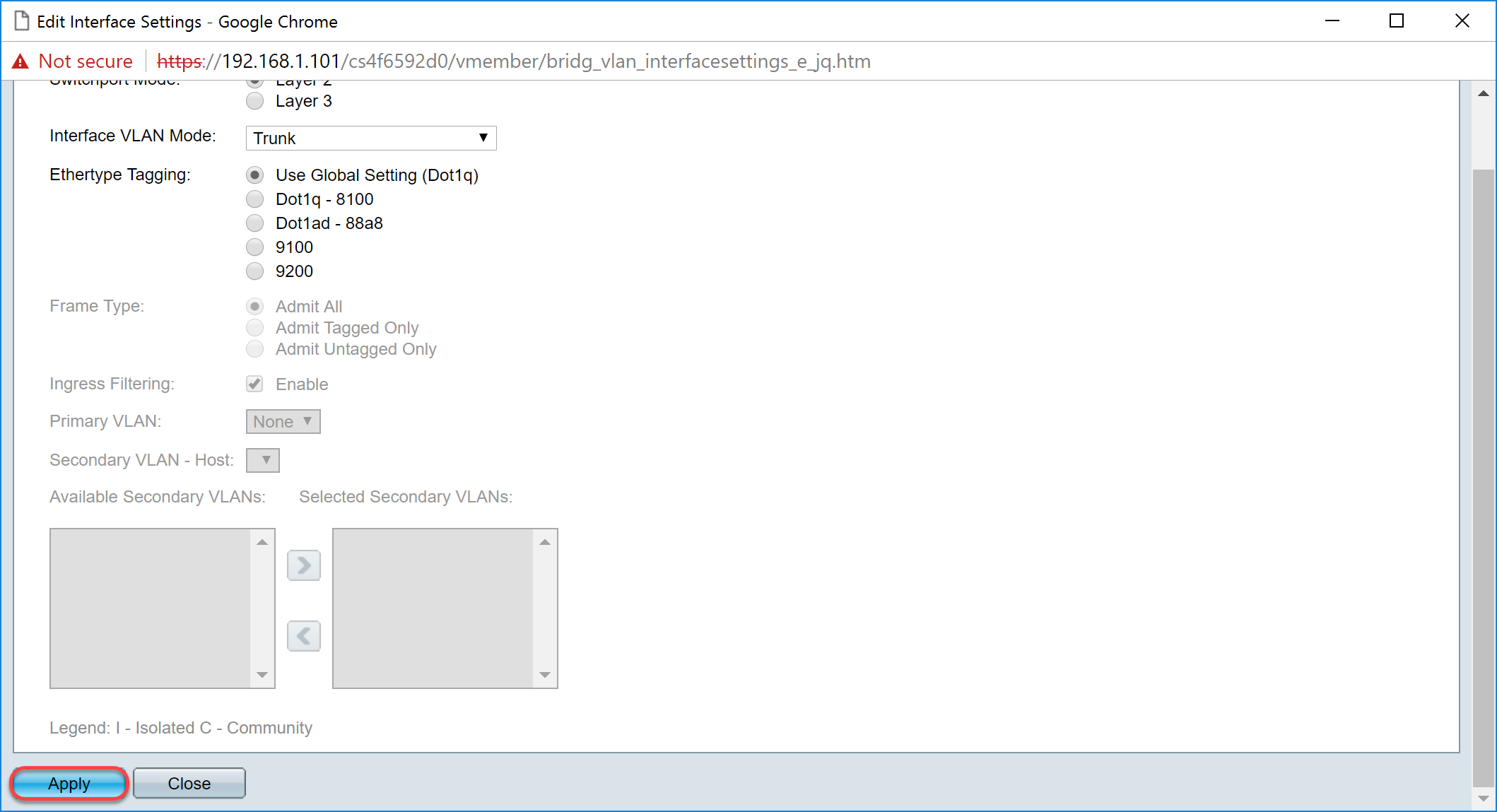
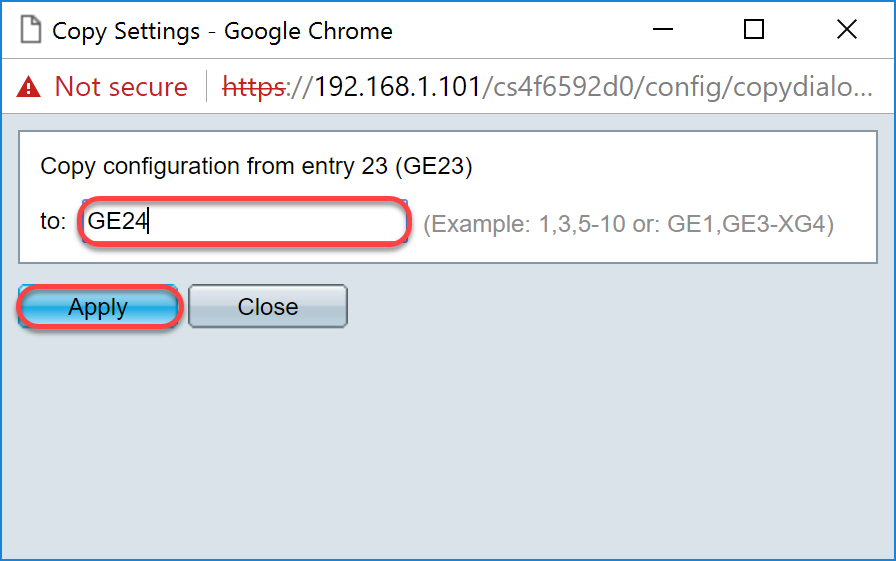
Step 11. (Optional) If you have configured GVRP on more than one interface then you can select the interface that you have just configured and click Copy Settings... . This will allow you to copy the configuration that you have just configured to other interfaces.
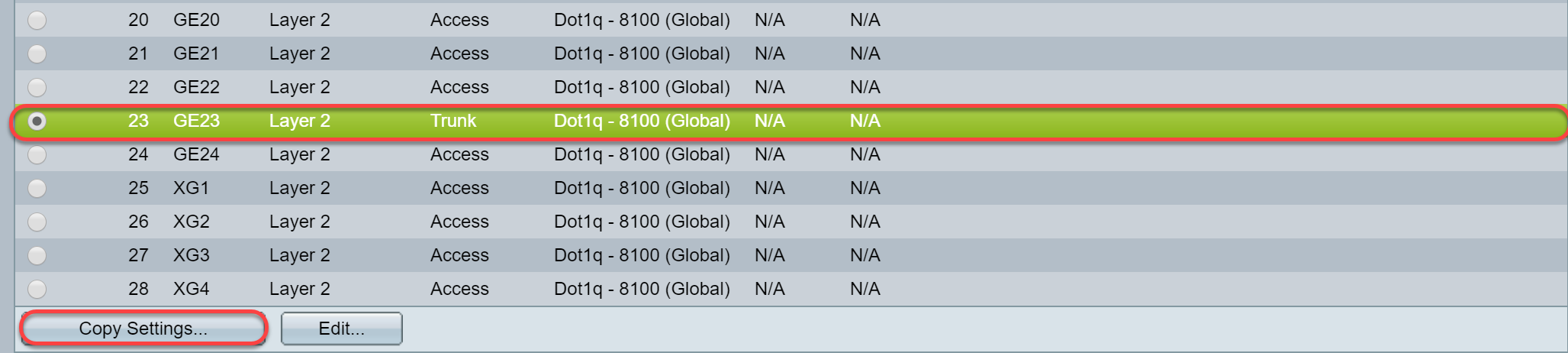
Step 12. (Optional) In the pop-up window that appears, enter the port where you wish to apply the same settings and click Apply .
Note: In this example, the settings from GE23 are going to be copied to GE24 only.
How to Set Up Port VLAN Membership Settings on the active Switch
Step 1. Navigate to VLAN Management > Port VLAN Membership .
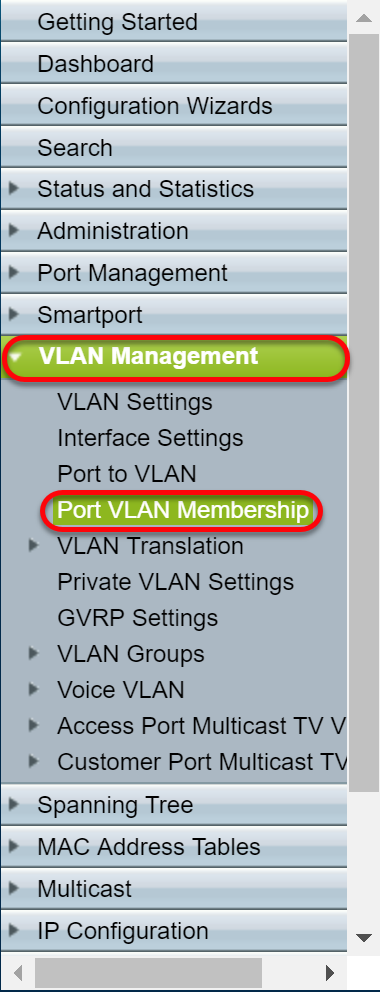
Step 2. Click the radio button of the interfaces that you have configured as trunk port.Then click Join VLAN... to edit the VLAN membership of that interface.

Step 3. (Optional) Click the appropriate radio button and choose a new interface from the Port or LAG drop-down list to change the interface whose settings you want to change.
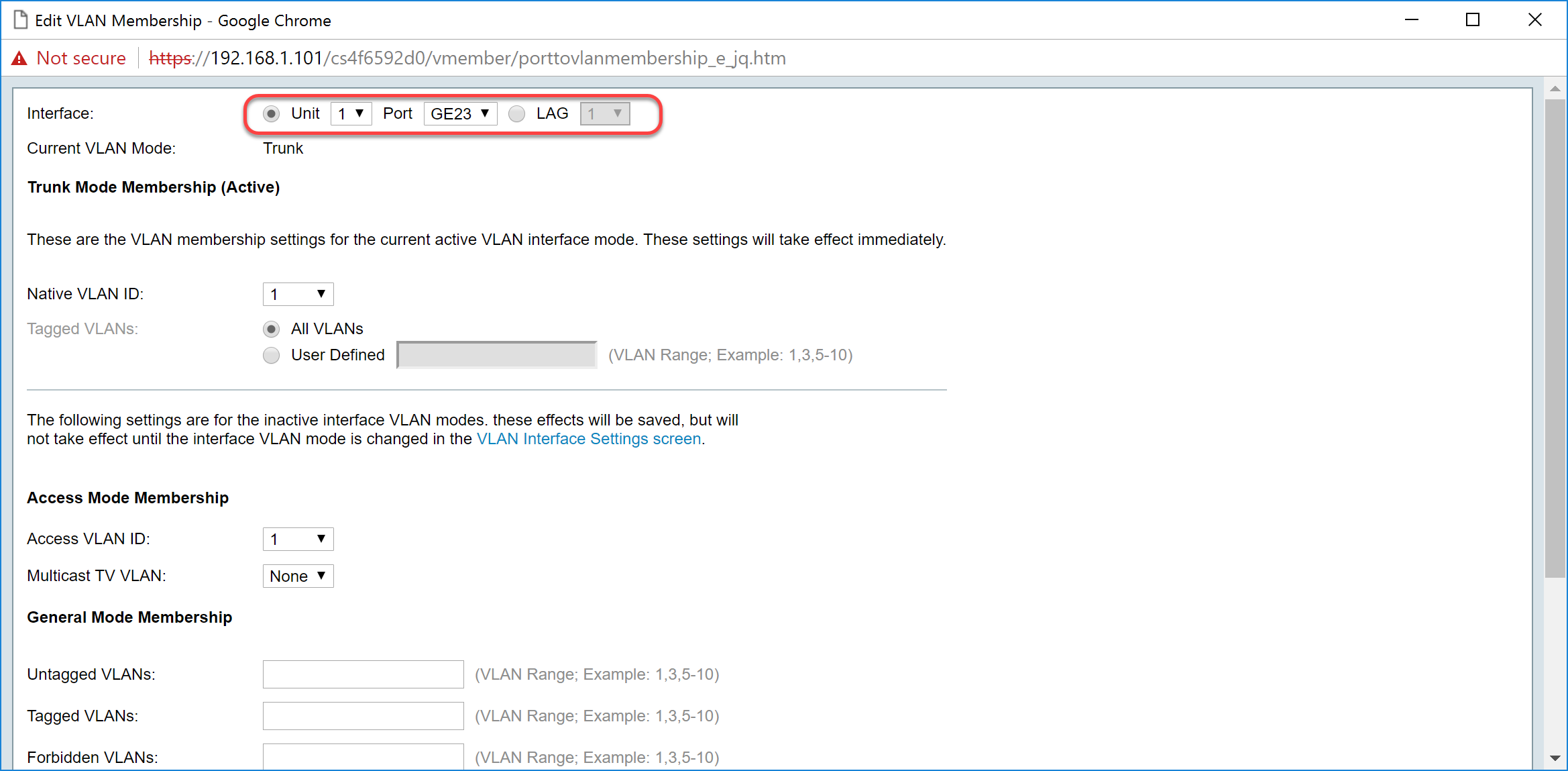
Step 4. When the port is in Trunk mode, it will be a member of this VLAN. Select the Native VLAN ID in the Native VLAN ID drop-down list.
Note: In this example, we will be using VLAN 1 as the native VLAN ID.
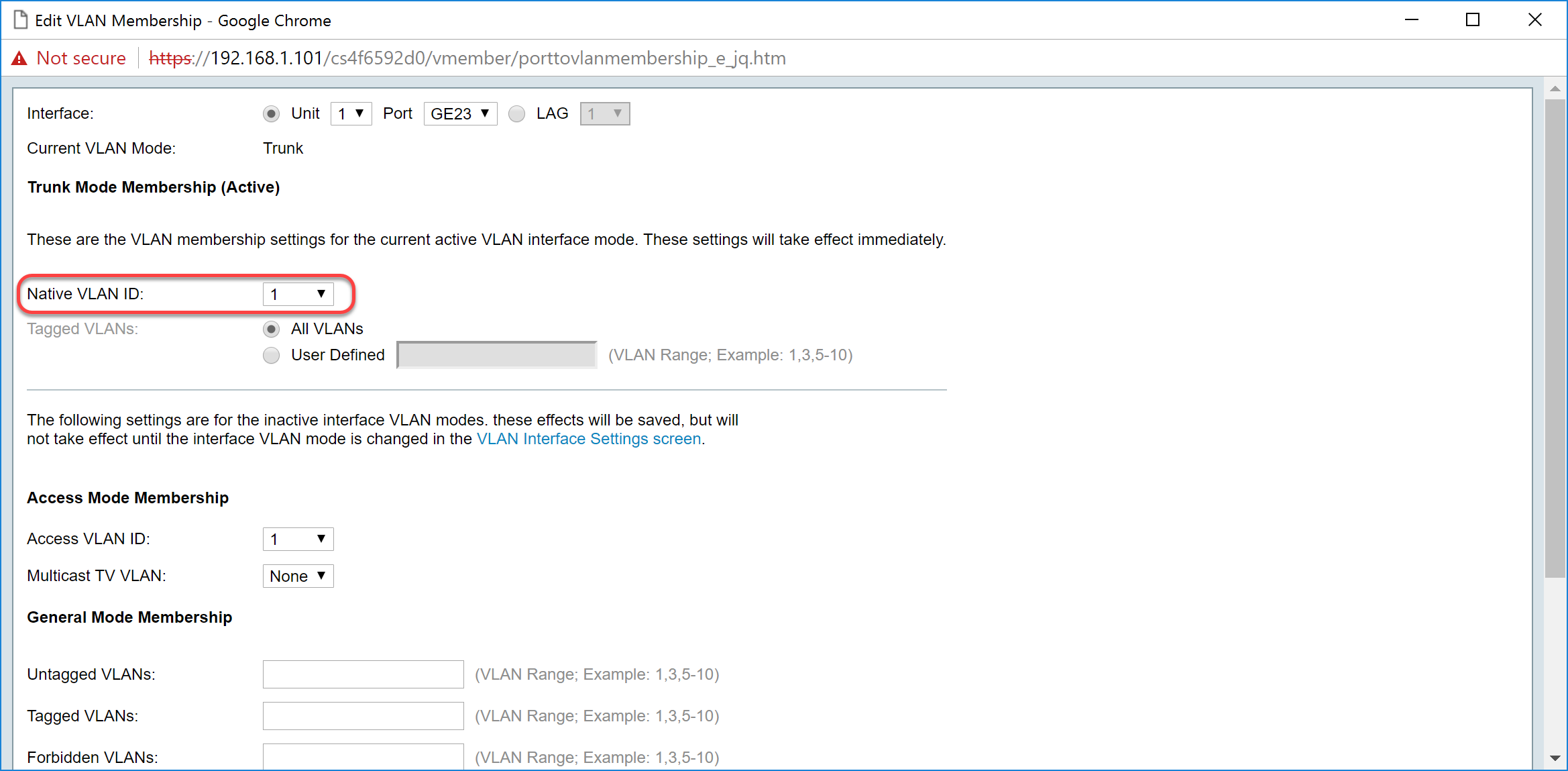
Step 5. Select User Defined radio button in the Tagged VLANs field. Then enter the VLAN ID's that you want this port to be a member of.
Note: In this example, we will be using VLAN: 1, 10-20 for GE23 and GE24.
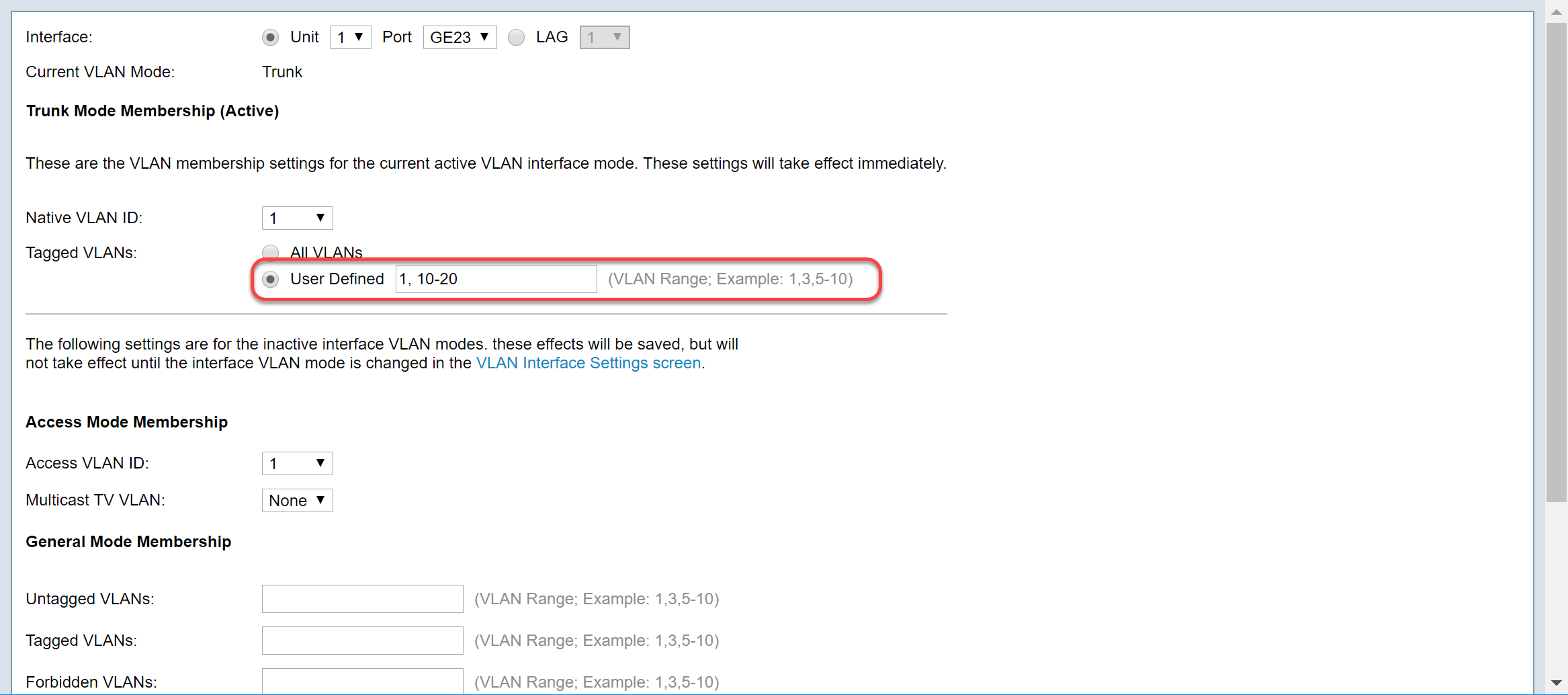
Step 6. Then click Apply to save your changes.
Note: Repeat steps 2-6 if you have more interfaces that needs to be configured.
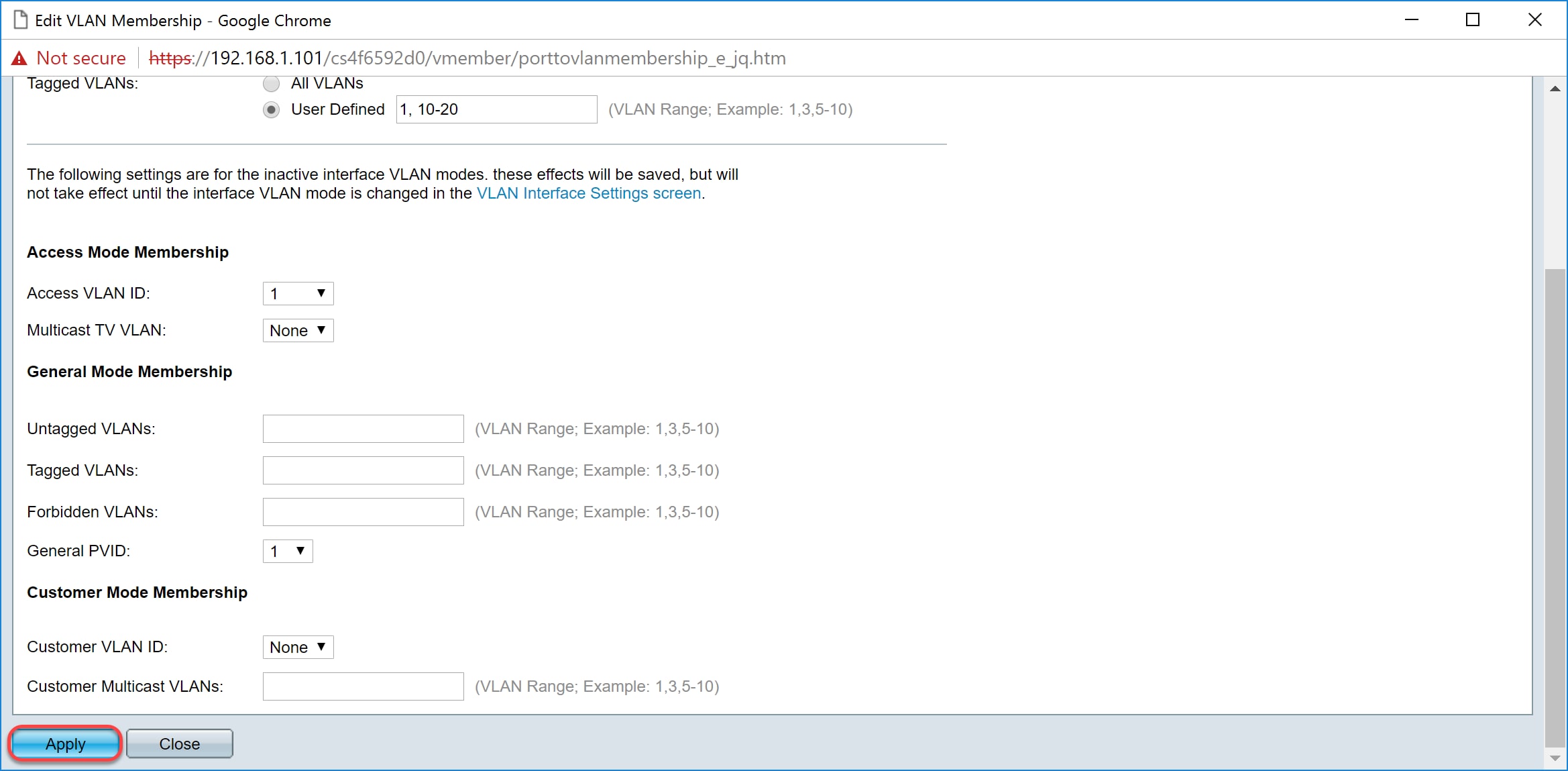
Step 7. Press the Save button on the top to save your configuration to the startup configuration file.

Configuring GVRP Settings on the Non-active Switch
Step 1. Log into the web configuration page of the non-active switch and navigate to VLAN Management > GVRP Settings . The GVRP Settings page opens.
Note: Since the non-active switches is not connected to the active switch, the default IP address is 192.168.1.254. You would have to put your PC to have a static IP address in that network in order to connect to it.
Proceed to configure the same way as the section: Configure GVRP Settings on SG550X-24 (active) for both of the non-switches. Configure only the port that is going to be connected to the active SG550X-24 switch. In this example, both of the non-active switch is using port 24 to connect to the active switch.
Setting Up Interface Settings on SG550X-24 Non-active Switch
Step 1. Navigate to VLAN Management > Interface Settings . The Interface Settings page opens.
Proceed to configure the same way as: How to Configure Interface Settings on the SG550X-24 (active) for both of the non-switches. Configure only the port that is connected to the active switch as trunk port. In this example, GE24 is configured as trunk for both of the switches.
Before we can verify that GVRP is working, there is a few more steps that needs to be done. Follow the last few steps below:
Step 1. Connect the cable from your non-active switch to the active switch.
Note: In this example, we will be connecting one of the non-active SG550X-24 (port 24) to the active SG550X-24 (port 23).
Step 2. Connect the cable from your second non-active switch to the active switch.
Note: In this example, we will be connecting the other non-active SG550X-24(port 24) to the active SG550X-24 (port 24).
Note: If you don't see any VLANs created by GVRP automatically in the VLAN Management > Create VLAN. A reboot may be required for your switches.
Step 3. Navigate to VLAN Management > Create VLAN on the non-active switch to see if VLAN 10-20 has been created.
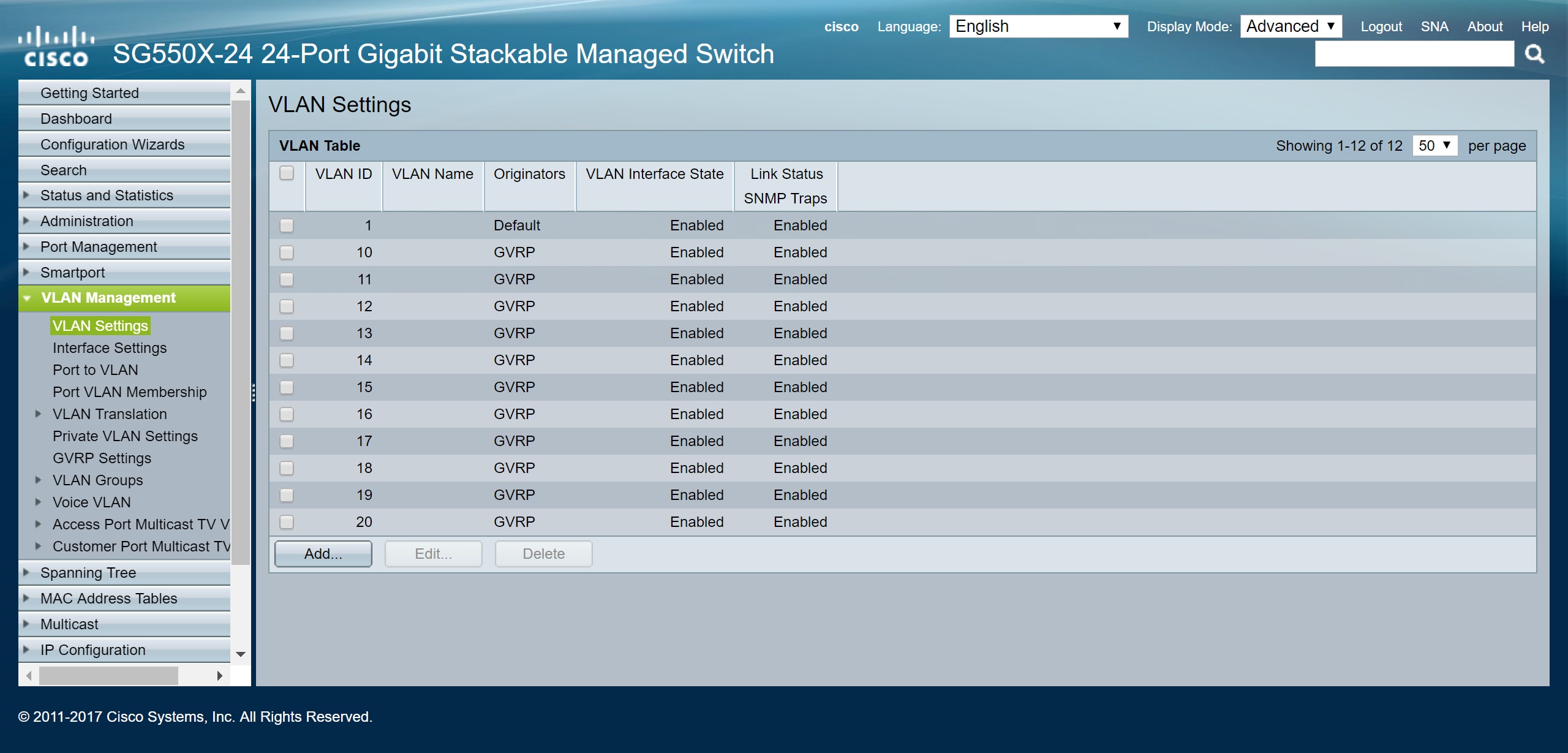
Step 4. Navigate to Status and Statistics > View Log > RAM Memory and check to see if GVRP has created VLAN 10-20 for both of the non-active switches.
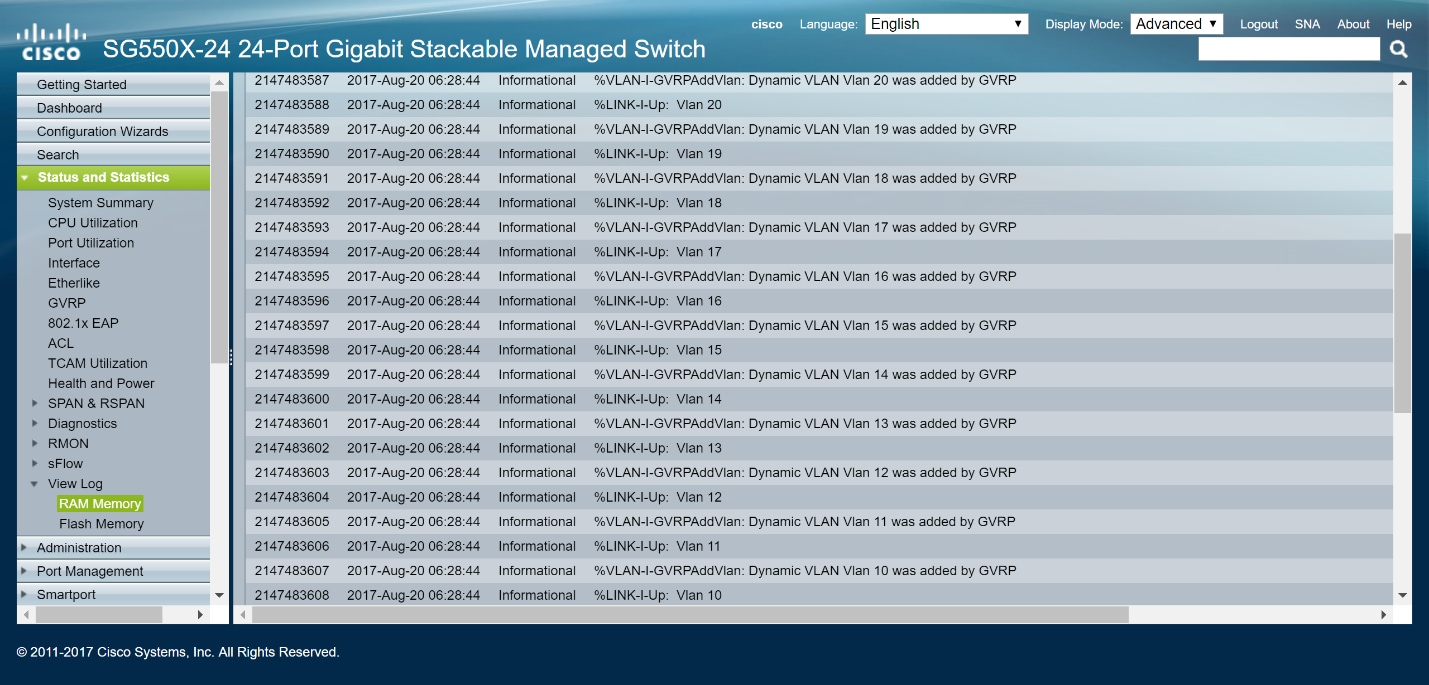
You have now successfully configured Dynamic VLANs and Auto Smartport configuration.
Check out the following links to view related videos:
Configuring Generic VLAN Registration Protocol (GVRP) on Cisco RV345
Smartport Configuration
Was this Document Helpful?

Contact Cisco
- (Requires a Cisco Service Contract )
Voice VLAN assignment modes
A port can be assigned to a voice VLAN in automatic mode or manual mode.
Automatic mode
Automatic mode is suitable for scenarios where PCs and IP phones connected in series access the network through the device and ports on the device transmit both voice traffic and data traffic, as shown in Figure 55 .
The system matches the source MAC address carried in the protocol packets sent when an IP phone is powered on against the device's OUI addresses. If the system finds a match, it automatically assigns the receiving port to the voice VLAN, issues ACL rules, and configures the packet precedence. You can configure a voice VLAN aging time on the device. The system will remove a port from the voice VLAN if no packet is received from the port during the aging time. The system automatically assigns ports to, or removes ports from, a voice VLAN. When the voice VLAN works correctly, when the system reboots, the system reassigns ports in automatic voice VLAN assignment mode to the voice VLAN after the reboot, ensuring that existing voice connections can work correctly. In this case, voice traffic streams do not trigger port assignment to the voice VLAN.
Manual mode
Manual mode is suitable for scenarios where only IP phones access the network through the device and ports on the device transmit only voice traffic, as shown in Figure 56 . In this mode, ports assigned to a voice VLAN transmit voice traffic exclusively, which prevents the impact of data traffic on the transmission of voice traffic.
You must manually assign an IP phone accessing port to a voice VLAN. Then, the system matches the source MAC addresses carried in the packets against the device’s OUI addresses. If the system finds a match, it issues ACL rules and configures the packet precedence. In this mode, you must manually assign ports to, or remove ports from, a voice VLAN.
Cooperation of voice VLAN assignment modes and IP phones
Both modes forward tagged packets sent out of IP phones according to their tags. Some IP phones can send out VLAN-tagged packets, and some IP phones can send out only untagged packets. Table 18 and Table 19 list the configurations required for ports of different link types to support tagged or untagged voice traffic sent from IP phones when different voice VLAN assignment modes are configured.
When IP phones send untagged voice traffic, you can only configure the voice traffic receiving ports on the device to operate in manual voice VLAN assignment mode.
Table 18: Required configurations on ports of different link types for them to support tagged voice traffic
Table 19: Required configurations on ports of different link types for them to support tagged voice traffic
When you configure the voice VLAN assignment modes, follow these guidelines:
If an IP phone sends tagged voice traffic and its accessing port is configured with 802.1X authentication and any of the guest VLAN, Auth-Fail VLAN, and critical VLAN features, assign different VLAN IDs to the voice VLAN, PVID of the connecting port, and 802.1X guest, Auth-Fail, or critical VLAN.
If an IP phone sends untagged voice traffic, to implement the voice VLAN feature, you must configure the PVID of the IP phone's accessing port as the voice VLAN. As a result, you cannot implement 802.1X authentication.
© Copyright 2016 Hewlett Packard Enterprise Development LP

IMAGES
VIDEO
COMMENTS
vlan-id - Specifies the VLAN to which the port is configured. none - Specifies that the access port cannot belong to any VLAN. Note: In this example, the range of ports is assigned to VLAN 30. Step 7. (Optional) To return the port or range of ports to the default VLAN, enter the following: SG350X(config-if-range)#no switchport access vlan. Step 8.
After creating a VLAN, you can manually assign a port to that VLAN and it will be able to communicate only with or through other devices in the VLAN. Configure the switch port for membership in a given VLAN as follows: Statically assign a VLAN: COS. set vlan number mod/port. IOS. (global) interface type mod/port.
Ports which drop frames if no MAC-based, Protocol-based VLAN assignment or Ingress VLAN Translation is applied. drop-if-invalid-or-src-port- -not-member-of-vlan-on-ports ( ports ; Default: none ) Ports that drop invalid and other port VLAN ID frames.
Step 1. Log in to the web configuration utility and choose VLAN Management > Interface Settings. The Interface Settings page opens: Step 2. Chose an interface from the Interface Type drop-down list and then click Go. Port — A single physical port on the switch. LAG — A group of ports used to increase link reliability.
VLAN Port Assignment is an application that displays device, port, and related VLAN information for an associated VTP domain in a tabular format and helps you manage ports on your network's VLANs. Use VLAN Port Assignment to: • Assign or move ports to a VLAN. • View port, device, and trunk attributes. • View and find port information in a ...
1. A port must have a VLAN assignment. If you need it to be completely disconnected, set it to a nonexistent VLAN and shut down the port. interface fa0/1. switchport access vlan 901. no switchport access vlan 1. shutdown. (I'm not sure if the "no" is required. Don't have a switch at my fingers with an open port to test).
VLAN Port Types. There are two type port used in VLANs. These are: - Access Ports, - Trunk Ports. Access ports are the ports that are member of a single VLAN. Host devices are connected to it. This is also default Cisco switch port type. Trunk ports are the ports that are member of more than one VLAN or all VLANs.
Private VLAN-Promiscuous - Select to set the interface as promiscuous. VLAN Mapping-Tunnel - Select to set the interface as a VLAN tunnel edge port. VLAN Mapping-One to One - Select to set the interface as to be used as a VLAN mapping one to one edge port. Note: For this example, Trunk was chosen. Step 5. Click€Apply. Step 6.
3. Add VLAN 40 as a trunked/tagged VLAN on the uplink port of the switch. This will make it active (since it has an active interface) and allow you to reach it in the first place if you are coming from a remote switch. Share. Improve this answer. answered Aug 14, 2016 at 5:02.
VLAN Port Types. There are two type port used in VLANs. These are: - Access Ports, - Trunk Ports. Access ports are the ports that are member of a single VLAN. Host devices are connected to it. This is also default Cisco switch port type. Trunk ports are the ports that are member of more than one VLAN or all VLANs.
Interface Settings. Step 1. Log in to the web-based utility and chooseVLAN Management > Interface Settings. Step 2. In the Interface Settings Table, choose an interface from the Interface Type equals to drop-down list and then click Go. The options are: Port - Choose Port if only a single port needs to be configured.
To change a port's VLAN assignment: Press E (for Edit). Use the arrow keys to select a VLAN assignment you want to change. Press the Space bar to make your assignment selection ( No, Tagged, Untagged , or Forbid. If you are finished assigning ports to VLANs, press Enter and then S (for Save) to activate the changes and return to the ...
Flexible VLAN assignment: Port based VLAN Protocol based VLAN MAC based VLAN From any to any VLAN translation and swapping 1:1 VLAN switching - VLAN to port mapping ... Ports which drop frames if no MAC-based, Protocol-based VLAN assignment or Ingress VLAN Translation is applied. drop-if-invalid-or-src-port--not-member-of-vlan-on-ports
Step 4. When the port is in Trunk mode, it will be a member of this VLAN. Select the Native VLAN ID in the Native VLAN ID drop-down list. Note: In this example, we will be using VLAN 1 as the native VLAN ID. Step 5. Select User Defined radio button in the Tagged VLANs field. Then enter the VLAN ID's that you want this port to be a member of.
In this mode, ports assigned to a voice VLAN transmit voice traffic exclusively, which prevents the impact of data traffic on the transmission of voice traffic. You must manually assign an IP phone accessing port to a voice VLAN. Then, the system matches the source MAC addresses carried in the packets against the device's OUI addresses.