A Complete Guide to Managing Technology Risk at the Enterprise Level
Safeguarding your organization from technological risks is an ongoing challenge. Whether you’re looking to identify, prevent, or combat these risks, this comprehensive guide covers everything you need to know about technology risk management to improve the safety, availability, and confidentiality of your systems and data.

What is technology risk?
Technology risk, or information technology risk, refers to the possibility of technology failures that can severely compromise business operations. This risk comes in many forms, such as information security breaches, cyberattacks, service outages, and unauthorized access to sensitive data like passwords.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial .
Technology risk examples
Even though technology risks differ based on the industry and the type of infrastructure, some of the most common types include:
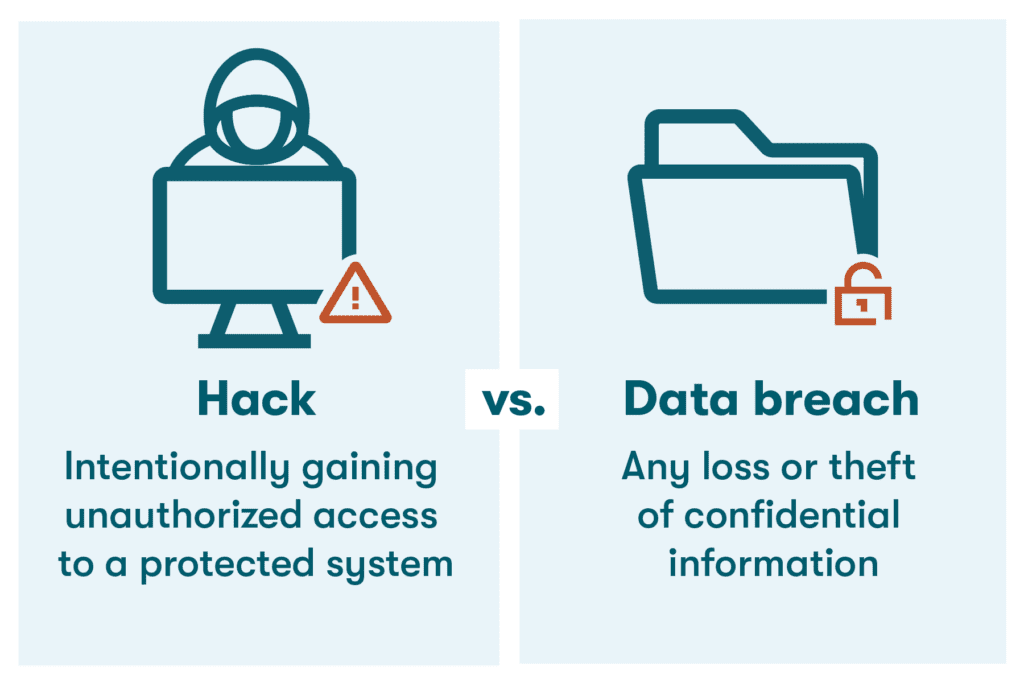
- Hacks. Hacking can be malicious (in the case of cybercrime) or non-malicious (for example, white-hat hackers who help test systems.) On the malicious side, hacking refers to a multitude of cybersecurity threats designed to gain unauthorized access, disrupt operations, steal sensitive information, or cause harm. Businesses frequently encounter these threats , particularly in the form of phishing and malware attacks. — Phishing. This cyberattack relies on fraudulent messages, particularly emails, containing embedded links to trick individuals into revealing sensitive information like passwords or financial details. — Malware. Short for ”malicious software,” malware refers to any type of software designed to harm or exploit computer systems or networks. Malware, such as computer viruses, causes harm by damaging programs or deleting files, while ransomware locks a user's computer or files until a ransom is paid.
- Data breaches. Data breaches occur when confidential information is accessed or exposed to unauthorized individuals. External security threats such as hacking, malware, and phishing can expose sensitive data to outsiders. Disgruntled employees, former employees with a working company login, or those lacking proper training can also accidentally or purposefully contribute to data breaches.
- Personal devices. Personal devices often lack data encryption or get misplaced, making them highly susceptible to data loss or theft. Since IT teams have limited control over the security of personal devices, businesses must take the necessary steps to secure them by implementing password managers, antivirus software, and security patches.
- Unsecured Wi-Fi. Inadequate Wi-Fi security, remote access through unsecured servers, and connecting to spoofed Wi-Fi networks in public places increases the risk of unauthorized access and data theft. One way to prevent potential information exposure is to use a virtual private network (VPN) .
- System failure. This technology risk arises when the tools, equipment, or systems supporting business operations encounter major disruptions or malfunctions. Such risks can result in an inability to perform crucial functions, as well as data loss, downtime, and significant financial and operational repercussions. It's important to have robust monitoring mechanisms, backup measures , and disaster recovery plans in place to minimize the impact of system failures and maintain uninterrupted operations.
- Third-party risks. Many organizations rely on external service providers or third-party software. If these partners lack strong internet security, your business may fall prey to data breaches or operational disruptions through them. You should review your provider agreements, as they may state that the provider is not liable for business interruption losses.
From big enterprises to recently funded startups, every business faces the ever-present threat of security breaches. Learn how Dashlane fortifies your defenses and protects against security threats .
Why is technology risk management important?
Despite several advancements in modern technology, various technology risks continue to impact workplaces. A technology risk management strategy can help effectively prepare and protect business data in the following ways:
- Identify and address potential technology risks before they occur
Outdated software in IT infrastructure can introduce compatibility issues and lead to bottlenecks, causing delays and prolonged system downtime. Regular technology risk assessments enable managers to quickly identify and address potential risks, ensuring smooth and uninterrupted operations.
- Monitor and protect data in real time
Real-time data and reliable statistics eliminate time delays, enabling prompt action in the event of a cyber incident. Utilizing the right tools streamlines the reporting process, making it easier to track and manage risks.
- Reduce costs associated with reputational and financial losses
Implementing a risk assessment schedule enables proactive identification and resolution of technological issues, preventing reputational damage and unnecessary recovery expenses. Businesses should also conduct timely assessments of IT systems, including personnel, investment, and IT infrastructure, to ensure efficient allocation and optimization of resources.
- Manage threats swiftly without losing business continuity
24/7 monitoring of IT systems is essential for uninterrupted business operations and preventing unnecessary stress for employees. A robust technology risk management strategy enables businesses to respond more swiftly to disruptions, minimizing downtime and ensuring business continuity.
- Gain trust from employees and clients
Creating a low-risk IT environment for employees fosters a strong working relationship, demonstrating a commitment to their security and well-being. Building trust with customers and stakeholders is essential, and risk management in technology provides reassurance that investments are protected even in emergencies.
5 steps to implement a technology risk management policy
A technology risk management policy includes a detailed step-by-step plan, starting from risk assessment to routine monitoring, to ensure your organization is a step ahead when combating technological risks. Implementing such a policy usually consists of the following steps:
- Conduct a technology risk assessment
Begin by evaluating your organization's digital infrastructure, systems, and processes to identify potential risks and vulnerabilities. This assessment involves conducting thorough audits, vulnerability scans, and analyses of existing controls to help you understand your business's specific technology risks.
- Develop a technology risk management policy
Next, create a comprehensive policy that outlines the objectives, principles, and guidelines for managing technology risks within your organization. This policy should address areas such as data security, incident response, access controls, employee training, and risk mitigation strategies. By clearly defining expectations and procedures, the policy ensures consistency and promotes a culture of security throughout the organization.
- Establish roles and responsibilities
Establish distinct roles and responsibilities for the individuals involved in the technology risk management process. Assigning specific responsibilities ensures that everyone understands their role in managing technology risks and can work together to mitigate potential threats effectively.
- Implement the framework
Now it's time to put your technology risk management framework into action and implement the necessary controls, procedures, and safeguards. This involves deploying security measures (like firewalls, encryption, and access controls) and establishing incident response protocols, employee awareness programs, and ongoing monitoring processes.
- Monitor progress and reassess
Keep an eye on your system logs, conduct periodic vulnerability assessments, and stay updated on emerging threats and industry best practices. By monitoring progress and reassessing risks, you can identify any new risks or changes in the technology landscape and make necessary adjustments to your risk management strategy to maintain robust protection.
How to perform a technology risk assessment
As noted above, the first step in implementing an effective technology risk management policy is to perform a technology risk assessment or a security audit . Follow these steps to risk-assess your business:
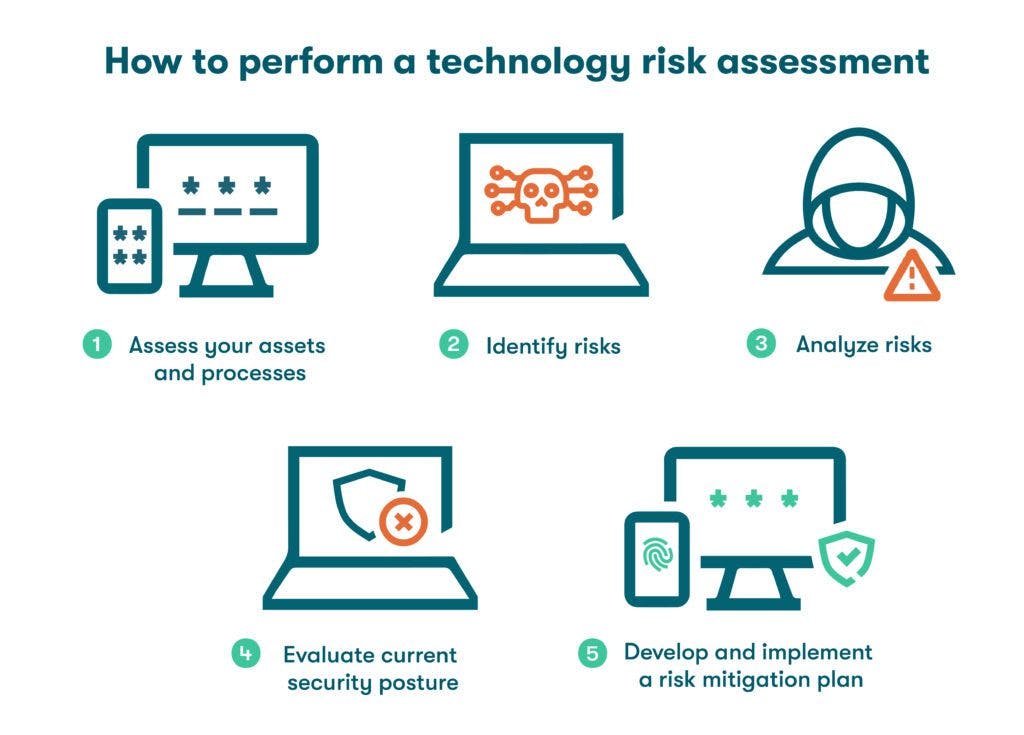
- Assess your assets and processes
Identify valuable assets of the business, such as servers, client contact information, and trade secrets. Since it’s impossible to go through each and every asset, focus on those that are mission-critical by establishing criteria, such as monetary value and organizational importance.
- Identify risks
After prioritizing your assets, conduct a thorough examination to identify potential threats associated with each one. A threat refers to any factor that can cause harm to your organization. Be vigilant for signs of hardware failure and suspicious or malicious activities, such as data breaches, theft of sensitive information, and employee impersonation.
- Analyze risks
Thoroughly examine the identified risks to better understand their potential impact on your organization. Consider factors such as financial loss, operational disruption, reputational damage, and regulatory compliance. This analysis helps prioritize risks based on their severity and provides insights for effective risk mitigation strategies.
- Evaluate your current security posture
Assess your organization's existing security measures to identify strengths and weaknesses. Identify any gaps or areas for improvement that need to be addressed to enhance your overall security posture and reduce vulnerabilities.
- Develop and implement a risk mitigation plan
Based on the risk analysis and security evaluation, create a comprehensive plan outlining specific actions and measures to mitigate identified risks. Implement the risk mitigation plan systematically, allocate resources effectively, and regularly monitor and update it to adapt to evolving threats.
The challenges of manual technology risk assessments
When you follow the above steps to conduct a technology risk assessment, it’s essential to use modern tools to streamline the process, maintain accuracy, and avoid human error.
Ongoing technology-based assessments come equipped with automated data collection, analysis, and reporting tools. Manual workflows pose several challenges, some of which are:
- Inefficient data management. Carrying out assessments manually makes it challenging to organize and analyze data effectively, resulting in incomplete or fragmented risk assessments.
- Time-consuming process. Manual assessments require significant time and effort to gather and analyze data, leading to delays in identifying and addressing risks.
- Human error. Depending solely on manual processes increases the risk of human error, such as overlooking critical information or misinterpreting data.
- Lack of standardization. Manual assessments often lack standardized processes and criteria, making it challenging to compare and prioritize risks consistently.
Old technology must be removed and replaced with newer, more advanced tools.
Technology retirement vs. new technologies
Technology retirement refers to replacing outdated technology to keep your business running efficiently. By embracing modern technology solutions, organizations can enhance productivity, streamline operations, upgrade security systems, and assess technological risks more efficiently and accurately.
Problems of using outdated technology:
- Data security risks. Using outdated technologies exposes your business to increased data security risks. Outdated tech lacks updates and security measures, making it more vulnerable to hacks. This increases your risk of experiencing security breaches and unauthorized access.
- Less compatibility. Technology that has gone obsolete often lacks compatibility with modern systems and software, limiting your ability to collaborate and integrate safely and effectively with partners and clients.
- Potential data loss. The risk of potential data loss is higher with outdated technology, as it may lack reliable backup mechanisms or fail to handle data storage efficiently.
- Lower productivity. Older technology can lower productivity due to slow performance, frequent system crashes, and compatibility issues that hinder efficient workflows.
Benefits of using newer technology:
- Latest security features. Modern technology is loaded with advanced security features. Reliable password managers and endpoint security platforms like Cloudflare and Crowdstrike help protect your data, devices, and systems from evolving cyber threats.
- Enhanced flexibility. Upgraded technology improves compatibility with a wide range of systems and workflows, enabling seamless collaboration and data exchange.
- Remote work support. Newer technology is better equipped to handle challenges posed by remote work. It provides enhanced connectivity, cloud-based collaboration tools, and remote access capabilities without compromising security .
- Improved efficiency. Upgrading to newer technology improves efficiency by streamlining processes, automating tasks, and providing faster and more reliable performance.
- Competitive edge. With modern technology, you can leverage advanced tools and innovations to get a competitive edge and drive growth for your business.
Periodic technological risk assessments, coupled with comprehensive policies and modern IT systems, provide 360-degree defense against cybersecurity threats. While the initial process may take a bit of work, completing the assessment and getting proper systems in place will go a long way in helping to safeguard business operations.
Need help convincing management to invest in your organization’s IT security? Read our comprehensive guide to building the case for a password manager in 8 steps .
- RiskOptics, “ What is Technology Risk? ” June 2022.
- Netwrix, “ Beginner’s Guide to IT Risk Management ,” March 2023.
- Netwrix, “ How to Perform IT Risk Assessment ,” March 2023.
- AnyConnector, “ What Is Technology Risk? How to Manage Business Threats ,” March 2021.
- Thales, “ 2022 Thales Data Threat Report ,” 2022.
- eSecurity Planet, “ Automating Security Risk Assessments for Better Protection ,” January 2021.
- Shi, “ The importance of modernizing old technology — and how to do it ,” April 2023.
- ERMA, “ 4 Types of Beneficial Risk Management Technology ,” July 2022.
- Dashlane, “ Why Do You Need a VPN? Don’t Miss These 3 Key Benefits ,” December 2022.
- Dashlane, “ How to Create a Culture of Security ,” March 2022.
- Dashlane, “ 11 Cyber Threats To Be Aware of & Defend Against ,” April 2023.
- Cobalt, “ Cybersecurity Statistics for 2023 ,” December 2022.
- Dashlane, “ How Businesses with a BYOD Policy Can Secure Employee Devices ,” January 2023.
- Dashlane, “ Putting Security First: How Dashlane Protects Your Data ,” January 2023.
- Dashlane, “ Are Password Managers Safe for Businesses? ” January 2023.
- Dashlane, “ How To Maintain Security When Employees Work Remotely ,” October 2022.
Sign up to receive news and updates about Dashlane
Thanks! You're subscribed. Be on the lookout for updates straight to your inbox.

Dashlane is a web and mobile app that simplifies password management for people and businesses. We empower organizations to protect company and employee data, while helping everyone easily log in to the accounts they need—anytime, anywhere.
Please note: We use cookies on our site to give you the best experience. Please accept these cookies, or change your settings here: Cookie preferences.
Build and transform technology landscapes to support evolving business strategies and operationalize innovation.
1,300+ LeanIX Customers
A growing list of industry leaders who trust in LeanIX
Maximize market potential through a partner program offering LeanIX solutions tailored to your business model.
The Complete Guide to Technology Risk Management

Technology risk management itself is not a new concept, but its requirements have evolved alongside the actual technologies we now use to run businesses. Decentralized systems, rapid software implementations, larger application portfolios — all of this and more makes IT risk and security management a priority not only for IT teams but business leaders across the enterprise.
Today, a single negative security event can cost millions of dollars to recover from. And while security breaches are never totally avoidable, a solid technology risk management strategy can reduce its adverse impact on a business.
This post offers a guide on technology risk management, what it means in practice, and how connecting enterprise architecture to your strategy can have real security benefits.
Quick Takeaways
- Technologies like cloud computing, microservices, and IoT have increased the potential that companies will experience IT security events.
- A technology risk management strategy typically includes assessment , evaluation, and maintenance of security risks.
- Enterprise architecture management can support technology risk management through increased visibility, better end-of-life management capabilities, and processes for IT standardization.
The State of Technology Risk in 2022
The implementation of any technology always comes with a certain level of risk. That risk, however, has become increasingly complex as technologies like cloud computing, microservices, and IoT devices have created decentralized IT infrastructures and broader attack surfaces for cyberthreats.
Data breaches increased significantly for both small and large businesses in the U.S. and Canada between 2020 and 2021 (shown in the graph below) — and this is only one type of IT security event. Consider also the threat of malware attacks, outages, and misconfigurations and it’s clear why technology risk management is a priority for businesses of all sizes.
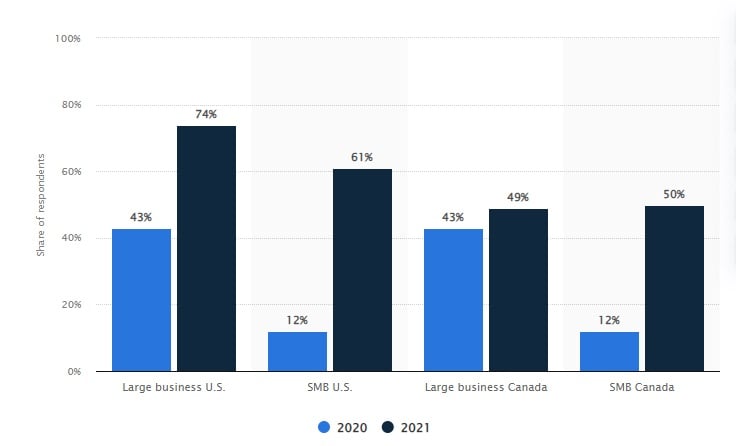
Data breaches, a common technology risk today, rose significantly between 2020 and 2021 for both small and large businesses ( source ).
At the same time, more traditional security concerns like internal compliance and end-of-life technology management have become more challenging as enterprises use more applications (as many as 650 for the average large enterprise and up to 3400 for the largest 10%) and other IT components.
Companies must think more proactively and strategically about technology risk management, implementing collaborative approaches to its execution that secure the enterprise and allow it to operate with necessary levels of agility.
What does technology risk management actually mean?
Given its importance to business success, it is worth defining technology risk management more specifically and outlining exactly what’s involved in its execution.
In general, technology risk management activities can be grouped into one of the following three categories:
- Assessment - The initial step in any technology risk management strategy, which includes listing all IT assets (software, hardware, networks, etc.) and associated risks.
- Prioritization - Evaluating risks to understand their urgency and level of importance, then prioritizing the order and/or extent to which they’ll be addressed
- Maintenance - Ensuring that ongoing security best practices – like access control or data privacy compliance – are being followed
All three activities are important to maintaining needed levels of security in the modern enterprise, and they all require collaboration between risk and IT teams as well as other stakeholders (end users, department managers, and legal/compliance teams to name a few).
The Benefits of an EA-Driven Approach to Technology Risk Management
A less commonly mentioned but critical contributor to effective technology risk management is the enterprise architecture team . EA teams possess both a global and a granular perspective on critical infrastructure, with the ability to zoom in or out as needed to assess risk and determine the best course of action to address it.
Further, EA teams manage powerful data resources that can be shared with risk managers across the enterprise to drive better IT management and lower overall risk. Let’s look at 4 ways an EA-driven approach to technology risk management can benefit organizations.
Risk visibility
As mentioned before, the first step in a technology risk assessment is to list IT assets and fully understand your current state architecture . EA platforms typically hold this information and make it available for teams who need it. Even better, these platforms can make it available in the form of landscape maps, diagrams, business capability maps, or other visualized formats so it’s easily digestible and analyzable.
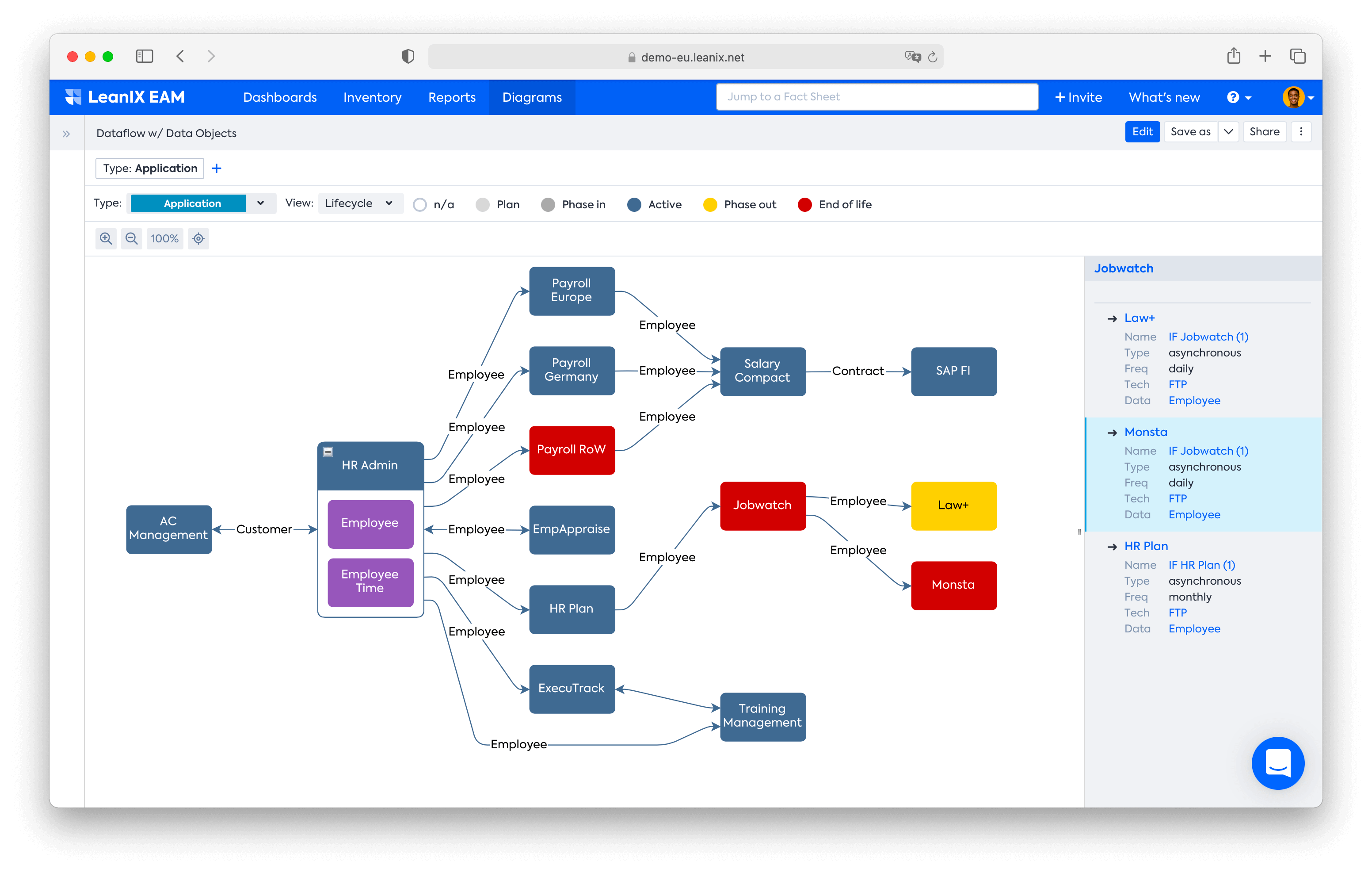
Dataflow Diagram example created in the LeanIX platform.
Better end-of-life asset management
Technology assets approaching obsolescence present a higher risk for security vulnerability. In fact, more than a third of security breaches are caused by outdated technologies . An enterprise unequipped to manage the technology lifecycle ( end-of-life assets) opens itself up to higher security risk, especially from threat actors seeking out old systems.
Enterprise architecture tools give you continual, real-time insight into which applications and assets are nearing obsolescence so that enterprises can proactively plan to phase them out and replace them.
As you can see in the LeanIX Application Landscape report below, it’s easy to spot end-of-life applications (red) and/or those that need to be phased out (yellow).
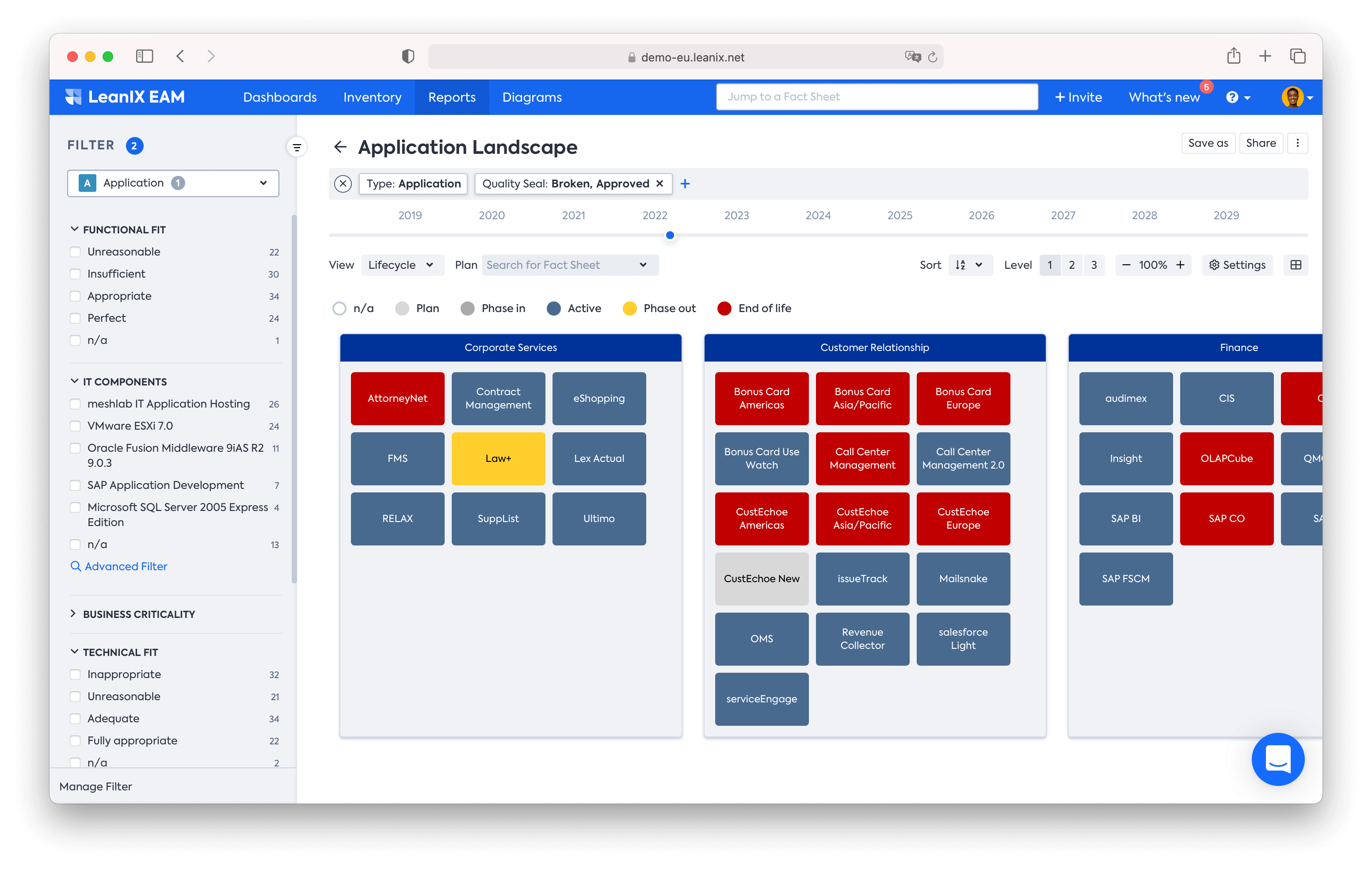
Application Landscape Reports boost technology risk management capabilities with real-time visualizations.
Standardization
It’s generally said in the IT world that more than half of IT security breaches come from insider threats — employees or other internal stakeholders who (intentionally or not) put a company at risk by compromising data, breaking access control rules, or similar action.
It’s critical, then, to pursue standardization when it comes to application access, data access, and sharing information. EA tools inform standardization by serving as a central source of truth for information regarding application ownership, licenses, approved users, use cases, process standards and more. The data EAs collect plays an essential role in efforts aimed at lowering the risk of an insider security threat.
Increased agility through informed decision making
Real-time access to application portfolio information — including dependencies and other relationship paths — allows business leaders at an organization to make technology decisions with a full understanding of their security implications.
This prevents business leaders from creating inadvertent risk when turning systems on and off. And by exposing potential threats that would otherwise go unnoticed, it elevates overall security awareness at the leadership level.
Manage technology risks with confidence using LeanIX
LeanIX can help you identify, evaluate, and mitigate risk using reports purposed specifically for technology risk management. Using the LeanIX platform, you can:
- Build a technology inventory as a foundation for effective risk management
- Synchronize data with ServiceNow or other ITSM solutions
- Use LeanIX’s built-in lifecycle catalog for lifecycle maintenance
- Uncover and evaluate obsolescence risk
- Plan and track risk mitigation
Schedule a call with us to get started.
Related Posts
Related resources.

Navigating the Digital Frontier: Fireside Chat on Technology ...
/EN/Reports/Thumbnail-Obsolescence-Gartner.png?width=140&height=100&name=Thumbnail-Obsolescence-Gartner.png)
Gartner® Report: How to Improve Infrastructure Fitness and ...
/EN/White-Paper/EN-IDC-Inforbrief-Application-Rationalization-Portfolio-Management-Thumbnail_v2.png?width=140&height=99&name=EN-IDC-Inforbrief-Application-Rationalization-Portfolio-Management-Thumbnail_v2.png)
Setting the Stage for Growth with Data-Driven Application ...
2023 Gartner® Magic Quadrant™ for Enterprise Architecture Tools
LeanIX named a Leader in the 2023 Gartner® Magic Quadrant™ for Enterprise Architecture Tools for third consecutive year
Get your complimentary report

How to Conduct a Technology Assessment: A Four-Step Guide
Posted / 12 August, 2021
Author / Enginess

Posted in digital transformation
If selected correctly, technologies can create competitive advantages for organizations. However, this selection process can be one of the most challenging decisions businesses face. Technology assessment done prior to the technology adoption reduces the risk of ineffective investment decisions.
We often forget a fundamental truth: software is a tool. It’s something that’s designed to help you do a job better, faster and more efficiently.
But like any tool, if you use the wrong one, you’re not going to get the results you want. You can have the fanciest screwdriver in the world, but it’s never going to be very good at hammering in nails.
That’s why it’s absolutely critical to conduct a thorough technology assessment, so you know you have the right tool to get the job done.
Here’s how you do it.
Why Bother With a Technology Assessment?
First, a technology assessment makes it much more likely to get a solution that suits your requirements and environment. We often know we have a problem and can visualize the ideal state we want our technology solution to get us to. However, it is challenging to know how to get there because it’s easy to confuse the symptoms with the cause of a problem. Thus, you end up solving the "symptom" with a (potentially expensive) piece of technology that is ill-equipped to address the underlying cause.
A structured process to assess and select a technology solution helps you get around this problem, reduce risks, and achieve your true objective, by forcing you to both identify the right problem and solve it in the right way.
Now that we know why we should do a formal technology assessment, how do you actually do it?
Step 1: Discovery
The first step towards picking the right technology is discovery. The purpose of the discovery phase is to deeply understand your existing reality, the problem you’re solving, and who you’re solving it for.
Understanding your current technology eco-system
You need to discover your current technology environment. This includes both the solutions you’re currently using as well as the systems and processes used to connect those systems. A good way to look at this is to look at it through the lens of a business process, and looking at what data is moved along the way, where that data is stored / what’s the source of truth, and how it gets from point A to point B.
A few questions to consider in this phase are:
- What data is important here?
- Who’s owning each system?
- What’s the source of truth for this process?
Understanding the problem
Next, you need to understand the problem, both in terms of the business and in terms of your end-user experience.
For example, say you are a sales organization struggling to hit your targets. Your business problem might be that you are not generating enough new business, and you are not sure why, what to do about it, or where to improve. In the same instance, your end-user problem might be that they don’t know what works and what doesn’t, so your sales reps just guess.
So your problem might boil down to documenting and sharing data readily throughout the sales organization so you can make better decisions and drive more revenue.
By combining both a business problem and the end-user problem, you can get a better sense of what the actual problem is, and begin to devise a way to solve it.
Understanding your people
Finally, you need to understand your people. That end-user insight isn’t going to come unless you take the time to really understand what your end users are struggling with and link this back to the high-level business problem. Shadowing of how people do their jobs, reviewing the existing usage data, user interviews, and rapid prototype testing are all excellent ways to uncover this information.
Once you have a holistic understanding of your technology environment, you can move on to the next step: analysis.

Step 2: Analysis
By the end of the discovery stage, you should be armed with information about where you are now and where you want to go. Ideally, you’ll have the beginnings of requirements to get there.
Next, you need to analyze the precise functionality that you have internally and how it’s currently being applied.
Since you have a good understanding of the problem, the goal, and the environment and systems, a good place to start is to look at what your existing tech stack can do.
You need to look at how the technology is being applied at a granular level. What’s more, you want to look at how it’s being worked around or misused. Are end-users avoiding features and functions? If so, why?
The reason you want to poke into these problems is that you might not need as complex a solution as you thought. Far more often, organizations are misusing their existing stack rather than using it to its full potential and still running into problems.
That said, you will find some gaps and holes. That’s where your technology assessment should focus, especially as you flesh out the requirements for what to buy to achieve your business objectives. The end state of the Assess and Analysis stage is an understanding of credible and prioritized options to fill your gaps with the pros and cons of each option.
Step 3: Define & Develop
Next comes to define and develop. You have a high-level business goal and a good understanding of the problem, environment, and the holes you’re trying to plug.
Next, you need to build out your vision for the end state. It’s not just about what problem you’re looking to solve, but more granular; what is your technology solution going to do/drive the business forward?
One common problem we see in this stage is a misalignment between the business, ops teams, and overall technology strategies. The challenge is that early research is often completed by technology teams (IT, etc…) but in reality, the entire project needs to be rallied around the business and operational requirements.
To do so, you need to develop and define your technology vision through the lens of the business and operational requirements. Ask yourself: does this feature/function/vendor solve the problem that the company has?
Naturally, there’s going to be some give and take here. Every decision or option you present will have tradeoffs. Defining and developing is about refining your vision down to be laser-focused on the business problem, and using the criteria you’ve built so far to hone in on exactly what you need.

Step 4: Document
The final step is to put all your work down on paper in a well-documents plan. Your final document should include:
- A high-level overview
- A crisp explanation of what you are solving and what you are asking for
- All the details of the implementation and deployment
- Details on project timelines and ownership.
One final piece of documentation is verbal communication. Make sure that the whole team knows the “elevator story”—that is, the high-level messaging to capture the interest and attention of key executives. You will also need to schedule the meetings with the executive decision-makers to gain buy-in. Ideally, these should be done one on one and then collectively, so there is both individual and group support. Finally, be ready to iterate as required based on executive feedback. Don’t assume just because it’s in your master plan its fact. Remember to be flexible, because it’s much better to tweak the project now than end up with technology you’re unhappy with.
As businesses get more complex, manual processes and systems become increasingly error-prone and risky, not to mention expensive and slow. Technology can help automate, streamline, and refine, giving valuable team members the space they need to do meaningful, high-value work.
Getting buy-in for it, buying the right tool, and then seeing that business impact, though, is far from simple.
Hopefully though, with these four steps, you will move toward your business goals by building and then executing your technology assessment plan. From here, your next steps are to pursue the specific technology you need to procure, document detailed requirements, evaluate vendors, and negotiate the paperwork. Once you select a vendor, embark on a consultative, collaborative approach to design and other steps for implementation. Remember that successful technology implementation requires a broader focus on process and organizational design. To achieve business value, consider how the technology change will drive changes in your metrics and support models.
Then implement, integrate, maintain… and repeat!

- accessibiity
- accessibility
- adaptive design
- artificial intelligence
- associations
- business intelligence
- business process engineering
- business process management
- business process managmenent
- business process reengineering
- business processes
- business processess
- change management
- collaboration
- colour theory
- consumer behaviour
- content management
- content management system
- content management systems
- content marketing
- content strategy
- conversion optimization
- conversions
- copywriting
- corporate website
- custom web applications
- customer engagement
- customer experience
- customer service
- customer success
- data security
- design of everyday things
- design sprint
- design thinking
- digital accessibility
- digital accessibiloty
- digital asset management
- digital business
- digital marketing
- digital platform
- digital strategy
- digital strategy roadmaps
- digital transformation
- digital trends
- employee portal
- enterprise applications
- fixed price
- flat design
- fullfillment
- gesture control
- google analytics
- google home
- health care
- hr processes
- infographic
- interactive design
- intersectionality
- iterative design
- jakob neilson
- learning management system
- machine learning
- micro interactions
- microservices
- mobile applications
- mobile health
- mobile optimization
- mobile strategy
- mobile websites
- multi-experience
- native apps
- online annual reports
- online shopping
- personalization
- pricing model
- process automation
- product development
- product management
- product strategy
- project management
- remote employees
- remote learning
- remote work
- responsive design
- roadmapping
- section 508
- service design
- social media
- software development
- sprint planning
- technology procurement
- telecommunications
- time and material
- usability testing
- user experience
- user experience design
- user research
- web accessibility
- web applications
- web content management
- web design trends
- web development
- web industry trends
- website content management
- website development
Subscribe to Enginess Digital Insights
Related articles.

Business Plan Risk Analysis - What You Need to Know
The business plan risk analysis is a crucial and often overlooked part of a robust business plan. In the ever-changing world of business knowing potential pitfalls and how to mitigate them could be the difference between success and failure. A well-crafted business plan acts as a guiding star for every venture, be it a startup finding its footing or a multinational corporation planning an expansion. However, amidst financial forecasts, marketing strategies, and operational logistics, the element of risk analysis frequently gets relegated to the back burner. In this blog, we will dissect the anatomy of the risk analysis section, show you exactly why it is important and provide you with guidelines and tips. We will also delve into real-life case studies to bring to life your learning your learning.
Table of Contents
- Risk Analysis - What is it?
- Types of Risks
- Components of Risk Analysis
- Real-Life Case Studies
- Tips & Best Practices
- Final Thoughts
Business Plan Risk Analysis - What Exactly Is It?
Risk analysis is like the radar system of a ship, scanning the unseen waters ahead for potential obstacles. It can forecast possible challenges that may occur in the business landscape and plan for their eventuality. Ignoring this can be equivalent to sailing blind into a storm. The business plan risk analysis section is a strategic tool used in business planning to identify and assess potential threats that could negatively impact the organisation's operations or assets. Taking the time to properly think about the risks your business faces or may face in the future will enable you to identify strategies to mitigate these issues.

Types of Business Risks
There are various types of risks that a business may face, which can be categorised into some broader groups:
- Operational Risks: These risks involve loss due to inadequate or failed internal processes, people, or systems. Examples could include equipment failure, theft, or employee misconduct.
- Financial Risks: These risks are associated with the financial structure of the company, transactions the company makes, and the company's ability to meet its financial obligations. For instance, currency fluctuations, increase in costs, or a decline in cash flow.
- Market Risks: These risks are external to the company and involve changes in the market. For example, new competitors entering the market changes in customer preferences, or regulatory changes.
- Strategic Risks: These risks relate to the strategic decisions made by the management team. Examples include the entry into a new market, the launch of a new product, or mergers and acquisitions.
- Compliance Risks: These risks occur when a company must comply with laws and regulations to stay in operation. They could involve changes in laws and regulations or non-compliance with existing ones.
The business risk analysis section is not a crystal ball predicting the future with absolute certainty, but it provides a foresighted approach that enables businesses to navigate a world full of uncertainties with informed confidence. In the next section, we will dissect the integral components of risk analysis in a business plan.

Components of a Risk Analysis Section
Risk analysis, while a critical component of a business plan, is not a one-size-fits-all approach. Each business has unique risks tied to its operations, industry, market, and even geographical location. A thorough risk analysis process, however, typically involves four main steps:
- Identification of Potential Risks: The first step in risk analysis is to identify potential risks that your business may face. This process should be exhaustive, including risks from various categories mentioned in the section above. You might use brainstorming sessions, expert consultations, industry research, or tools like a SWOT analysis to help identify these risks.
- Risk Assessment: Once you've identified potential risks, the next step is to assess them. This involves evaluating the likelihood of each risk occurring and the potential impact it could have on your business. Some risks might be unlikely but would have a significant impact if they did occur, while others might be likely but with a minor impact. Tools like a risk matrix can be helpful here to visualise and prioritise your risks.
- Risk Mitigation Strategies: After assessing the risks, you need to develop strategies to manage them. This could involve preventing the risk, reducing the impact or likelihood of the risk, transferring the risk, or accepting the risk and developing a contingency plan. Your strategies will be highly dependent on the nature of the risk and your business's ability to absorb or mitigate it.
- Monitoring and Review: Risk analysis is not a one-time task, but an ongoing process. The business landscape is dynamic, and new risks can emerge while old ones can change or even disappear. Regular monitoring and review of your risks and the effectiveness of your mitigation strategies is crucial. This should be an integral part of your business planning process.
Through these four steps, you can create a risk analysis section in your business plan that not only identifies and assesses potential threats but also outlines clear strategies to manage and mitigate these risks. This will demonstrate to stakeholders that your business is prepared and resilient, able to handle whatever challenges come its way.

Business Plan Risk Analysis - Real-Life Examples
To fully grasp the importance of risk analysis, it can be beneficial to examine some real-life scenarios. The following are two contrasting case studies - one demonstrating a successful risk analysis and another highlighting the repercussions when risk analysis fails.
Case Study 1: Google's Strategic Risk Mitigation
Consider Google's entry into the mobile operating system market with Android. Google identified a strategic risk : the growth of mobile internet use might outpace traditional desktop use, and if they didn't have a presence in the mobile market, they risked losing out on search traffic. They also recognised the risk of being too dependent on another company's (Apple's) platform for mobile traffic. Google mitigated this risk by developing and distributing its mobile operating system, Android. They offered it as an open-source platform, which encouraged adoption by various smartphone manufacturers and quickly expanded their mobile presence. This risk mitigation strategy helped Google maintain its dominance in the search market as internet usage shifted towards mobile.
Case Study 2: The Fallout of Lehman Brothers
On the flip side, Lehman Brothers, a global financial services firm, failed to adequately analyse and manage its risks, leading to its downfall during the 2008 financial crisis. The company had significant exposure to subprime mortgages and had failed to recognise the potential risk these risky loans posed. When the housing market collapsed, the value of these subprime mortgages plummeted, leading to significant financial losses. The company's failure to conduct a robust risk analysis and develop appropriate risk mitigation strategies eventually led to its bankruptcy. The takeaway from these case studies is clear - effective risk analysis can serve as an essential tool to navigate through uncertainty and secure a competitive advantage, while failure to analyse and mitigate potential risks can have dire consequences. As we move forward, we'll share some valuable tips and best practices to ensure your risk analysis is comprehensive and effective.
Business Plan Risk Analysis Tips and Best Practices
While the concept of risk analysis can seem overwhelming, following these tips and best practices can streamline the process and ensure that your risk management plan is both comprehensive and effective.
- Be Thorough: When identifying potential risks, aim to be as thorough as possible. It’s crucial not to ignore risk because it seems minor or unlikely; even small risks can have significant impacts if not managed properly.
- Involve the Right People: Diverse perspectives can help identify potential risks that might otherwise be overlooked. Include people from different departments or areas of expertise in your risk identification and assessment process. They will bring different perspectives and insights, leading to a more comprehensive risk analysis.
- Keep it Dynamic: The business environment is continually changing, and so are the risks. Hence, risk analysis should be an ongoing process, not a one-time event. Regularly review and update your risk analysis to account for new risks and changes in previously identified risks.
- Be Proactive, Not Reactive: Use your risk analysis to develop mitigation strategies in advance, rather than reacting to crises as they occur. Proactive risk management can help prevent crises, reduce their impact, and ensure that you're prepared when they do occur.
- Quantify When Possible: Wherever possible, use statistical analysis and financial projections to evaluate the potential impact of a risk. While not all risks can be quantified, putting numbers to the potential costs can provide a clearer picture of the risk and help prioritise your mitigation efforts.
Implementing these tips and best practices will strengthen your risk analysis, providing a more accurate picture of the potential risks and more effective strategies to manage them. Remember, the goal of risk analysis isn't to eliminate all risks—that's impossible—but to understand them better so you can manage them effectively and build a more resilient business.
In the ever-changing landscape of business, where uncertainty is a constant companion, the risk analysis section of a business plan serves as a guiding compass, illuminating potential threats and charting a course toward success. Throughout this blog, we have explored the critical role of risk analysis and the key components involved in its implementation. We learned that risk analysis is not just about identifying risks but also about assessing their potential impact and likelihood. It involves developing proactive strategies to manage and mitigate those risks, thereby safeguarding the business against potential pitfalls. In conclusion, a well-crafted business plan risk analysis section is not just a formality but a strategic asset that empowers your business to thrive in an unpredictable world. As you finalise your business plan, keep in mind that risk analysis is not a one-time task but an ongoing practice. Revisit and update your risk analysis regularly to stay ahead of changing business conditions. By embracing risk with a thoughtful and proactive approach, you will position your business for growth, resilience, and success in an increasingly dynamic and competitive landscape. Want more help with your business plan? Check out our Learning Zone for more in-depth guides on each specific section of your plan.
BreachSight
Vendor risk, trust exchange, product features, vendor risk assessments, security questionnaires.
- Security Ratings
Data Leaks Detection
- Integrations
AI Autofill
- Financial Services
eBooks, Reports, & more
What is it risk management strategies and processes.

Edward Kost
IT risk management is the process of managing cybersecurity risks through systems, policies, and technology. This process consists of three primary stages - identification, assessment, and control to mitigate vulnerabilities threatening sensitive resources.
The terms IT risk and information risk are often used interchangeably. They both refer to risk that threatens the protection of sensitive data and intellectual property.
Information Technology risks, both inherent and residual , are present in every organization. IT risk management is, therefore, an essential practice for every business.
What is the Difference Between Risk and Uncertainty?
Risk refers to decision-making situations where all potential outcomes, and their likelihood of occurrence, are known. On the other hand, uncertainty refers to decision-making situations where nothing is known - neither their potential outcomes nor their likelihood of occurrence.
A successful IT risk management plan reduces uncertainly and empowers decision-makers to be completely aware of all information risks in their digital landscape.
Why is IT risk Management Important?
An IT risk management program minimizes the impact of data breaches, which could translate to considerable costs savings. The global average cost of a data breach in 2020 was US$3.86 million.
In addition to cost savings, an IT risk management plan has the following benefits:
- It helps organizations increase their resilience to cyberattacks .
- It stabilizes business operators.
- It could decrease legal liability.
- It could reduce insurance premiums.
- It protects staff from potential harm.
- It facilitates the achievement of business objectives and business continuity

Example of a Successful IT Risk Management Plan
The Virginia Mason Medical Center in Seattle, Washington secured their patient safety department with an IT Risk Management plan in 2006. The resulting program was called the Virginia Mason Production System (VMPS) .
Since implementing VMPS, Virginia Mason has increased transparency in patient risk mitigation, disclosure, and reporting. This resulted in a significant drop in hospital professional premiums.
The 7 Best IT Risk Management Strategies and Processes
An IT risk management (IRM) framework must account for an evolving threat landscape . As a result, a single set of policies or strategies will not suffice. Because cyberattack tactics are constantly changing , risk management frameworks must be capable of addressing multiple cyber threats through a combination of different control strategies.
When used harmoniously, these strategies should help decision-makers confidently answer the following questions:
- What could go wrong?
- How will this outcome impact the organization?
- How will this outcome impact the achievement of business objectives?
- What can be done to prevent this outcome?
- What can be done to remedy this outcome after it has occurred?
- What are the potential costs of this outcome?
The essential requirement of an IRM program that will help answer the above questions include:
- The ability to continuously monitor the entire attack surface
- The ability to track cybersecurity posture strengthening efforts
- The ability to identify the location of all information
- Remediation management tools capable of prioritizing critical responses
- The ability to evaluate the risk tolerance for all assets
These essential requirements can be met with the following 7 risk management strategies
1. Risk Identification
All risks that could be potentially detrimental to processes and information security must be identified. Digital transformation has made this task exceedingly difficult since most company data is now stored in the cloud.
The inexorable proliferation of digital solutions obfuscates digital footprints making it difficult to identify assets and map their relationship to specific processes. This lack of transparency results in many attack vectors being overlooked, placing cloud-based platforms at a higher risk of cyberattacks.
The first step to unmitigated risk transparency is to identify all of your assets and their locations. This can be achieved through digital footprint mapping .
An attack surface monitoring solution could also identify all of your corporate assets and surface potential risks and vulnerabilities.
2. Identify Risk Levels and the Odds of Each Risk Being Exploited
After identifying all assets and their locations, the level of risk of the data stored in them needs to be quantified.
Not all sensitive data is equal in the eye of a cybercriminal, some categories are more coveted than others.
A study by IBM and Ponemon found that 80% of assessed data breaches involved customer Personal Identifiable Information (PII) .

Sensitive data that offers compounding financial returns to cyber criminals are at the highest risk of being targeted. When customer data is stolen, each victim is targeted in phishing attacks . Each phishing campaign then uncovers new victims that can then be targeted in new phishing attacks, extending the pernicious attack cycle.
The level of risk for each data type can then be calculated with a risk formula .
A simple formula for calculating risk levels is as follows:
Risk Level = Likelihood of a data breach X Financial impact of a data breach.
Probability analysis is used to then calculate the potential of each identified risk occurring. This is can be evaluated with a risk matrix .
3. Prioritize Each Identified Information Security Risk
To keep the costs of internal security operations lean, response efforts must be efficiently distributed so that the most critical IT risk are addressed first.
This can only be achieved if critical risks are correctly classified. Though some risk calculations are quite accurate, their evaluation involves a lengthy manual process.
Besides accuracy, speed is another critical variable in IT rIsk analysis because it affects the impact level of a data breach if risks are exploited by cybercriminals.
Victims that respond to data breaches in less than 200 days save an average of $1.12 million .
The idea solution should be capable of correctly classifying security vulnerabilities and prioritizing them for efficient remediation.
The UpGuard platform meets these two requirements. Users can see a list of all unaddressed vulnerabilities (both internally and in the vendor network) ordered by criticality. Each risk can then be rapidly addressed through the platform's remediation management feature.
4. Establish a Risk Appetite
With all IT risk and their likelihood of exploitation known, a risk appetite needs to be established. Risk appetites help organizations decide which control measures should be assigned to each risk factor. There are 5 control options:
- Risk acceptance
- Risk avoidance
- Mitigate risk
- Transfer risk
- Monitor risk
.png)
A risk appetite (or risk tolerance) sets the maximum level of risk that can be accepted before mitigation efforts are implemented.
Learn how to calculate the risk appetite for your Third-Party Risk Management program.
5. Mitigate Risks
MIitgation controls should be implemented for each type of risk that surprises the risk threshold. These controls should assess the highest-ranked IT risk first.
These controls should be supported with Incident Response Plans (IRP) to help security teams respond to threats in a timely and controlled manner.
IT risk mitigation controls include:
- Data encryption
- Keeping software updated
- Keeping antivirus updated
- Installing the latest software patches
- Backing up critical data
- Implementing Multi-Factor Authentication (MFA)
- Securing privileged access account s
- Implementing resilient cybersecurity frameworks
Risk can also be mitigated through a cybersecurity framework. There are many information security risk management frameworks available. The most reputable are listed below.
- COBIT - This framework helps organizations develop an Enterprise RIsk Management (ERM) strategy.
- Essential Eight - This is the recommended cybersecurity framework for all Australian businesses.
- COSO (Committee of Sponsoring Organizations of the Treadway Commission) - This framework facilitates secure network operations.
- Factor Analysis of Information Risk (FAIR) - This framework evaluates the. relationship between different risks and facilitates compliance with international regulations.
6. Transfer IT Risks
In many instances, it's more efficient and less burdensome for internal security teams to transfer critical risks to either an outside party or a cyber insurance entity.
Partnering with data storage, or backup, solutions will transfer and mitigate the risk of service interruption in the event of a data breach . Such a partnership also mitigates the risk of internal threats since employees will not have access to all data resources; and natural disasters because there's little chance that the same environmental damage will occur at two dispersed locations.
7. Monitor IT Risks and Compliance
IT monitoring methodologies should be implemented to track the progression of both mitigated risks and ignored risks within the risk appetite.
An example of an IT risk monitoring control is an attack surface monitor solution capable of scanning both in the internal and third-party network . Such a wide and deep level of transparency keeps organizations aware of the state of each risk, any related risk, and which vulnerabilities surpass the risk appetite.
Monitoring controls should also assess the effectiveness of mitigation controls. Cyberattackers are always adjusting their tactics to evade security defenses and mitigation strategies. A recent example the use of ransom software in a supply chain attack by cybercriminal group REvil.
Security ratings give security teams and stakeholders insight into the security posture of their organization, all of its subsidiaries, and vendors. This feature also instantly confirms the effectiveness of all remediation efforts .
When the immediate feedback functionality of security ratings is combined with attack surface monitoring controls, organizations are confidently aware of the likelihood of a data breach occurring, at any point in their IT environment, at any time.
Cybersecurity KPIs are the biding agents that ensure all IT risk monitoring efforts are supporting overall security objectives. They also facilitate meaningful reports for IT security teams and stakeholders.
Here are 14 important metrics that should be implemented in your IT risk management program.
1. Level of preparedness
2. Unidentified devices on internal networks
3. Intrusion attempts
4. Security incidents
5. Mean Time to Detect (MTTD)
6. Mean Time to Resolve (MTTR)
7. Mean Time to Contain (MTTC)
8. First party security ratings
9. Average vendor security rating
10. Patching cadence
11. Access management
12. Company vs peer performance
13. Vendor patching cadence
14. Mean time for vendors incident response
Learn more about cybersecurity KPIs
Risk Management Process and Standards
The proliferation of data breaches has placed a greater responsibility on organizations to secure their networks and protect customer data. These best security practices are enforced through regulatory compliance.
Industries at the highest risk of cyberattacks, such as financial services and healthcare, are bound to regulatory laws and the security frameworks that facilitate regulatory compliance.
Some examples of regulatory compliance standards are the General Data Protection Regulation (GDPR) for residents in the European Union and CPS 234 for APRA-Regulated organizations .
The chart below demonstrates the top 4 industries being targeted by cybercriminals in Australia. This also reflects global data breach trends.

Industries that are not regulated will still benefit from implementing regulatory frameworks to benefit from their advanced data breach protection controls.
The International Organization for Standardization (ISO) consists of a range of standards to suit all organizations and sectors. The most popular ISO standards for IT security are ISO 27001 and ISO 3100.
The ISO 27001 family offers requirements for data security management systems, and the ISO 3100 family can provide guidance of internal risk audits.
ISO has published over 22,700 standards to meet almost every information security requirement. The video below will provide some guidance on which ISO family is suitable for your business risk requirements.
The National Institue of Standards and Technology (NIST) has
Ensuring vendor compliance with regulatory standards is an essential component IT risk management since third-party breaches account for almost 60% of data breach events.
This can be achieved through risk assessments and security questionnaires. To support the efficient risk management of information systems, vendor security questionnaires should be managed via a security solution such as UpGuard. This will
This will alleviate the logistical nightmare of manually tracking the status of multiple risk assessments in spreadsheets.
The UpGuard platform supports the following security questionnaires:
- CyberRisk Questionnaire: Provides a comprehensive assessment of an organization's security posture, from their policy framework right down to their technical controls.
- ISO 27001 Questionnaire: Assesses an organization's security posture against the ISO 27001 standard with risks mapped against ISO 27001 domains. It is also suitable for the assessment of APRA CPS 234 requirements.
- Short Form Questionnaire: A condensed version of the CyberRisk Questionnaire, designed to be sent to smaller organizations.
- NIST Cybersecurity Framework Questionnaire: Assesses an organization's security posture against the NIST Cybersecurity Framework.
- PCI DSS Questionnaire: assess an organization's adherence to the twelve requirements of PCI DSS.
- California Consumer Privacy Act (CCPA) Questionnaire: Assesses whether a vendor is compliant with the personal information disclosure requirements outlined in CCPA.
- Modern Slavery Questionnaire: designed to identify modern slavery risks, address identified risks, and highlight areas requiring further due diligence.
- Pandemic Questionnaire: designed to help you assess the negative impact of any current or future pandemics.
- Security and Privacy Program Questionnaire: focuses solely on an organization's security and privacy program.
- Web Application Security Questionnaire: focuses solely on an organization's web application security controls.
- Infrastructure Security Questionnaire: focuses solely on an organization's infrastructure security controls.
- Physical and Data Centre Security Questionnaire: focuses solely on an organization's physical and data centre security controls.
- COBIT 5 Security Standard Questionnaire: Assesses compliance against the Control Objectives for Information and Related Technologies Framework created by ISACA.
- ISA 62443-2-1:2009 Security Standard Questionnaire: Assesses compliance against the ISA 62443-2-1:2009 standard for industrial automation and control systems.
- ISA 62443-3-3:2013 Security Standard Questionnaire: Assesses compliance against technical control system requirements associated with the seven foundational requirements (FRs) described in IEC 62443-1-1.
- GDPR Security Standard Questionnaire: Assesses compliance against the personal information disclosure requirements outlined in the European Union's General Data Protection Regulation (GPDR).
- CIS Controls 7.1 Security Standard Questionnaire: Assesses compliance against the best practice guidelines for cybersecurity outlined in 20 CIS Controls.
- NIST SP 800-53 Rev. 4 Security Standard Questionnaire: Assesses compliance against the security and privacy controls required for all U.S. federal information systems except those related to national security.
- SolarWinds Questionnaire: Designed to help you assess your vendors that may use SolarWinds.
- Kaseya Questionnaire: To help you determine if you or your vendors were exposed to the sophisticated supply chain ransomware attack
For highly specific IT risks assessments UpGuard offers a custom security questionnaire builder . that allows existing questionnaires to be edited or completely custom questionnaires to be created.
Reviewed by

Kaushik Sen
Ready to see upguard in action, ready to save time and streamline your trust management process, join 27,000+ cybersecurity newsletter subscribers.
Related posts
The top cybersecurity websites and blogs of 2024.

14 Cybersecurity Metrics + KPIs You Must Track in 2024
What are security ratings cyber performance scoring explained, why is cybersecurity important, what is typosquatting (and how to prevent it), introducing upguard's new sig lite questionnaire.

- UpGuard Vendor Risk
- UpGuard BreachSight
- Product Video
- Release notes
- SecurityScorecard
- All comparisons
- Security Reports
- Instant Security Score
- Third-Party Risk Management
- Attack Surface Management
- Cybersecurity
What is business risk?

You know about death and taxes. What about risk? Yes, risk is just as much a part of life as the other two inevitabilities. This became all the more apparent during COVID-19, as each of us had to assess and reassess our personal risk calculations as each new wave of the pandemic— and pandemic-related disruptions —washed over us. It’s the same in business: executives and organizations have different comfort levels with risk and ways to prepare against it.
Where does business risk come from? To start with, external factors can wreak havoc on an organization’s best-laid plans. These can include things like inflation , supply chain disruptions, geopolitical upheavals , unpredictable force majeure events like a global pandemic or climate disaster, competitors, reputational issues, or even cyberattacks .
But sometimes, the call is coming from inside the house. Companies can be imperiled by their own executives’ decisions or by leaks of privileged information, but most damaging of all, perhaps, is the risk of missed opportunities. We’ve seen it often: when companies choose not to adopt disruptive innovation, they risk losing out to more nimble competitors.
The modern era is rife with increasingly frequent sociopolitical, economic, and climate-related shocks. In 2019 alone, for example, 40 weather disasters caused damages exceeding $1 billion each . To stay competitive, organizations should develop dynamic approaches to risk and resilience. That means predicting new threats, perceiving changes in existing threats, and developing comprehensive response plans. There’s no magic formula that can guarantee safe passage through a crisis. But in situations of threat, sometimes only a robust risk-management plan can protect an organization from interruptions to critical business processes. For more on how to assess and prepare for the inevitability of risk, read on.
Learn more about McKinsey’s Risk and Resilience Practice.
What is risk control?
Risk controls are measures taken to identify, manage, and eliminate threats. Companies can create these controls through a range of risk management strategies and exercises. Once a risk is identified and analyzed, risk controls can be designed to reduce the potential consequences. Eliminating a risk—always the preferable solution—is one method of risk control. Loss prevention and reduction are other risk controls that accept the risk but seek to minimize the potential loss (insurance is one method of loss prevention). A final method of risk control is duplication (also called redundancy). Backup servers or generators are a common example of duplication, ensuring that if a power outage occurs no data or productivity is lost.
But in order to develop appropriate risk controls, an organization should first understand the potential threats.
What are the three components to a robust risk management strategy?
A dynamic risk management plan can be broken down into three components : detecting potential new risks and weaknesses in existing risk controls, determining the organization’s appetite for risk taking, and deciding on the appropriate risk management approach. Here’s more information about each step and how to undertake them.
1. Detecting risks and controlling weaknesses
A static approach to risk is not an option, since an organization can be caught unprepared when an unlikely event, like a pandemic, strikes. So it pays to always be proactive. To keep pace with changing environments, companies should answer the following three questions for each of the risks that are relevant to their business.
- How will a risk play out over time? Risks can be slow moving or fast moving. They can be cyclical or permanent. Companies should analyze how known risks are likely to play out and reevaluate them on a regular basis.
- Are we prepared to respond to systemic risks? Increasingly, risks have longer-term reputational or regulatory consequences, with broad implications for an industry, the economy, or society at large. A risk management strategy should incorporate all risks, including systemic ones.
- What new risks lurk in the future? Organizations should develop new methods of identifying future risks. Traditional approaches that rely on reviews and assessments of historical realities are no longer sufficient.
2. Assessing risk appetite
How can companies develop a systematic way of deciding which risks to accept and which to avoid? Companies should set appetites for risk that align with their own values, strategies, capabilities, and competitive environments—as well as those of society as a whole. To that end, here are three questions companies should consider.
- How much risk should we take on? Companies should reevaluate their risk profiles frequently according to shifting customer behaviors, digital capabilities, competitive landscapes, and global trends.
- Are there any risks we should avoid entirely? Some risks are clear: companies should not tolerate criminal activity or sexual harassment. Others are murkier. How companies respond to risks like economic turmoil and climate change depend on their particular business, industry, and levels of risk tolerance.
- Does our risk appetite adequately reflect the effectiveness of our controls? Companies are typically more comfortable taking risks for which they have strong controls in place. But the increased threat of severe risks challenges traditional assumptions about risk control effectiveness. For instance, many businesses have relied on automation to increase speed and reduce manual error. But increased data breaches and privacy concerns can increase the risk of large-scale failures. Organizations, therefore, should evolve their risk profiles accordingly.
3. Deciding on a risk management approach
Finally, organizations should decide how they will respond when a new risk is identified. This decision-making process should be flexible and fast, actively engaging leaders from across the organization and honestly assessing what has and hasn’t worked in past scenarios. Here are three questions organizations should be able to answer.
- How should we mitigate the risks we are taking? Ultimately, people need to make these decisions and assess how their controls are working. But automated control systems should buttress human efforts. Controls guided, for example, by advanced analytics can help guard against quantifiable risks and minimize false positives.
- How would we respond if a risk event or control breakdown happens? If (or more likely, when) a threat occurs, companies should be able to switch to crisis management mode quickly, guided by an established playbook. Companies with well-rehearsed crisis management capabilities weather shocks better, as we saw with the COVID-19 pandemic.
- How can we build true resilience? Resilient companies not only better withstand threats—they emerge stronger. The most resilient firms can turn fallout from crises into a competitive advantage. True resilience stems from a diversity of skills and experience, innovation, creative problem solving, and the basic psychological safety that enables peak performance.
Change is constant. Just because a risk control plan made sense last year doesn’t mean it will next year. In addition to the above points, a good risk management strategy involves not only developing plans based on potential risk scenarios but also evaluating those plans on a regular basis.
Learn more about McKinsey’s Risk and Resilience Practice.
What are five actions organizations can take to build dynamic risk management?
In the past, some organizations have viewed risk management as a dull, dreary topic, uninteresting for the executive looking to create competitive advantage. But when the risk is particularly severe or sudden, a good risk strategy is about more than competitiveness—it can mean survival. Here are five actions leaders can take to establish risk management capabilities .
- Reset the aspiration for risk management. This requires clear objectives and clarity on risk levels and appetite. Risk managers should establish dialogues with business leaders to understand how people across the business think about risk, and share possible strategies to nurture informed risk-versus-return decision making—as well as the capabilities available for implementation.
- Establish agile risk management practices. As the risk environment becomes more unpredictable, the need for agile risk management grows. In practice, that means putting in place cross-functional teams empowered to make quick decisions about innovating and managing risk.
- Harness the power of data and analytics. The tools of the digital revolution can help companies improve risk management. Data streams from traditional and nontraditional sources can broaden and deepen companies’ understandings of risk, and algorithms can boost error detection and drive more accurate predictions.
- Develop risk talent for the future. Risk managers who are equipped to meet the challenges of the future will need new capabilities and expanded domain knowledge in model risk management , data, analytics, and technology. This will help support a true understanding of the changing risk landscape , which risk leaders can use to effectively counsel their organizations.
- Fortify risk culture. Risk culture includes the mindsets and behavioral norms that determine an organization’s relationship with risk. A good risk culture allows an organization to respond quickly when threats emerge.
How do scenarios help business leaders understand uncertainty?
Done properly, scenario planning prompts business leaders to convert abstract hypotheses about uncertainties into narratives about realistic visions of the future. Good scenario planning can help decision makers experience new realities in ways that are intellectual and sensory, as well as rational and emotional. Scenarios have four main features that can help organizations navigate uncertain times.
- Scenarios expand your thinking. By developing a range of possible outcomes, each backed with a sequence of events that could lead to them, it’s possible to broaden our thinking. This helps us become ready for the range of possibilities the future might hold—and accept the possibility that change might come more quickly than we expect.
- Scenarios uncover inevitable or likely futures. A broad scenario-building effort can also point to powerful drivers of change, which can help to predict potential outcomes. In other words, by illuminating critical events from the past, scenario building can point to outcomes that are very likely to happen in the future.
- Scenarios protect against groupthink. In some large corporations, employees can feel unsafe offering contrarian points of view for fear that they’ll be penalized by management. Scenarios can help companies break out of this trap by providing a “safe haven” for opinions that differ from those of senior leadership and that may run counter to established strategy.
- Scenarios allow people to challenge conventional wisdom. In large corporations in particular, there’s frequently a strong bias toward the status quo. Scenarios are a nonthreatening way to lay out alternative futures in which assumptions underpinning today’s strategy can be challenged.
Learn more about McKinsey’s Strategy & Corporate Finance Practice.
What’s the latest thinking on risk for financial institutions?
In late 2021, McKinsey conducted survey-based research with more than 30 chief risk officers (CROs), asking about the current banking environment, risk management practices, and priorities for the future.
According to CROs, banks in the current environment are especially exposed to accelerating market dynamics, climate change, and cybercrime . Sixty-seven percent of CROs surveyed cited the pandemic as having significant impact on employees and in the area of nonfinancial risk. Most believed that these effects would diminish in three years’ time.

Introducing McKinsey Explainers : Direct answers to complex questions
Climate change, on the other hand, is expected to become a larger issue over time. Nearly all respondents cited climate regulation as one of the five most important forces in the financial industry in the coming three years. And 75 percent were concerned about climate-related transition risk: financial and other risks arising from the transformation away from carbon-based energy systems.
And finally, cybercrime was assessed as one of the top risks by most executives, both now and in the future.
Learn more about the risk priorities of banking CROs here .
What is cyber risk?
Cyber risk is a form of business risk. More specifically, it’s the potential for business losses of all kinds in the digital domain—financial, reputational, operational, productivity related, and regulatory related. While cyber risk originates from threats in the digital realm, it can also cause losses in the physical world, such as damage to operational equipment.
Cyber risk is not the same as a cyberthreat. Cyberthreats are the particular dangers that create the potential for cyber risk. These include privilege escalation (the exploitation of a flaw in a system for the purpose of gaining unauthorized access to resources), vulnerability exploitation (an attack that uses detected vulnerabilities to exploit the host system), or phishing. The risk impact of cyberthreats includes loss of confidentiality, integrity, and availability of digital assets, as well as fraud, financial crime, data loss, or loss of system availability.
In the past, organizations have relied on maturity-based cybersecurity approaches to manage cyber risk. These approaches focus on achieving a particular level of cybersecurity maturity by building capabilities, like establishing a security operations center or implementing multifactor authentication across the organization. A maturity-based approach can still be helpful in some situations, such as for brand-new organizations. But for most institutions, a maturity-based approach can turn into an unmanageably large project, demanding that all aspects of an organization be monitored and analyzed. The reality is that, since some applications are more vulnerable than others, organizations would do better to measure and manage only their most critical vulnerabilities.
What is a risk-based cybersecurity approach?
A risk-based approach is a distinct evolution from a maturity-based approach. For one thing, a risk-based approach identifies risk reduction as the primary goal. This means an organization prioritizes investment based on a cybersecurity program’s effectiveness in reducing risk. Also, a risk-based approach breaks down risk-reduction targets into precise implementation programs with clear alignment all the way up and down an organization. Rather than building controls everywhere, a company can focus on building controls for the worst vulnerabilities.
Here are eight actions that comprise a best practice for developing a risk-based cybersecurity approach:
- fully embed cybersecurity in the enterprise-risk-management framework
- define the sources of enterprise value across teams, processes, and technologies
- understand the organization’s enterprise-wide vulnerabilities—among people, processes, and technology—internally and for third parties
- understand the relevant “threat actors,” their capabilities, and their intent
- link the controls in “run” activities and “change” programs to the vulnerabilities that they address and determine what new efforts are needed
- map the enterprise risks from the enterprise-risk-management framework, accounting for the threat actors and their capabilities, the enterprise vulnerabilities they seek to exploit, and the security controls of the organization’s cybersecurity run activities and change program
- plot risks against the enterprise-risk appetite; report on how cyber efforts have reduced enterprise risk
- monitor risks and cyber efforts against risk appetite, key cyber risk indicators, and key performance indicators
How can leaders make the right investments in risk management?
Ignoring high-consequence, low-likelihood risks can be catastrophic to an organization—but preparing for everything is too costly. In the case of the COVID-19 crisis, the danger of a global pandemic on this scale was foreseeable, if unexpected. Nevertheless, the vast majority of companies were unprepared: among billion-dollar companies in the United States, more than 50 filed for bankruptcy in 2020.
McKinsey has described the decisions to act on these high-consequence, low-likelihood risks as “ big bets .” The number of these risks is far too large for decision makers to make big bets on all of them. To narrow the list down, the first thing a company can do is to determine which risks could hurt the business versus the risks that could destroy the company. Decision makers should prioritize the potential threats that would cause an existential crisis for their organization.
To identify these risks, McKinsey recommends using a two-by-two risk grid, situating the potential impact of an event on the whole company against the level of certainty about the impact. This way, risks can be measured against each other, rather than on an absolute scale.
Organizations sometimes survive existential crises. But it can’t be ignored that crises—and missed opportunities—can cause organizations to fail. By measuring the impact of high-impact, low-likelihood risks on core business, leaders can identify and mitigate risks that could imperil the company. What’s more, investing in protecting their value propositions can improve an organization’s overall resilience.
Articles referenced:
- “ Seizing the momentum to build resilience for a future of sustainable inclusive growth ,” February 23, 2023, Børge Brende and Bob Sternfels
- “ Data and analytics innovations to address emerging challenges in credit portfolio management ,” December 23, 2022, Abhishek Anand , Arvind Govindarajan , Luis Nario and Kirtiman Pathak
- “ Risk and resilience priorities, as told by chief risk officers ,” December 8, 2022, Marc Chiapolino , Filippo Mazzetto, Thomas Poppensieker , Cécile Prinsen, and Dan Williams
- “ What matters most? Six priorities for CEOs in turbulent times ,” November 17, 2022, Homayoun Hatami and Liz Hilton Segel
- “ Model risk management 2.0 evolves to address continued uncertainty of risk-related events ,” March 9, 2022, Pankaj Kumar, Marie-Paule Laurent, Christophe Rougeaux, and Maribel Tejada
- “ The disaster you could have stopped: Preparing for extraordinary risks ,” December 15, 2020, Fritz Nauck , Ophelia Usher, and Leigh Weiss
- “ Meeting the future: Dynamic risk management for uncertain times ,” November 17, 2020, Ritesh Jain, Fritz Nauck , Thomas Poppensieker , and Olivia White
- “ Risk, resilience, and rebalancing in global value chains ,” August 6, 2020, Susan Lund, James Manyika , Jonathan Woetzel , Edward Barriball , Mekala Krishnan , Knut Alicke , Michael Birshan , Katy George , Sven Smit , Daniel Swan , and Kyle Hutzler
- “ The risk-based approach to cybersecurity ,” October 8, 2019, Jim Boehm , Nick Curcio, Peter Merrath, Lucy Shenton, and Tobias Stähle
- “ Value and resilience through better risk management ,” October 1, 2018, Daniela Gius, Jean-Christophe Mieszala , Ernestos Panayiotou, and Thomas Poppensieker

Want to know more about business risk?
Related articles.

What matters most? Six priorities for CEOs in turbulent times

Creating a technology risk and cyber risk appetite framework

Risk and resilience priorities, as told by chief risk officers
VMware by Broadcom Dramatically Simplifies Offer Lineup and Licensing Model
- Share "VMware by Broadcom Dramatically Simplifies Offer Lineup and Licensing Model" on Twitter
- Share "VMware by Broadcom Dramatically Simplifies Offer Lineup and Licensing Model" on Facebook
- Share "VMware by Broadcom Dramatically Simplifies Offer Lineup and Licensing Model" on LinkedIn
By Krish Prasad, Senior Vice President and General Manager, VMware Cloud Foundation Division
Broadcom’s close of the VMware acquisition has brought together two engineering-first, innovation-centric teams to help build the world's leading infrastructure technology company. Together, we are well-positioned to enable global enterprises to embrace private, hybrid and multi-cloud environments. And we are committed to driving customer success through faster innovation, a simpler portfolio and a robust ecosystem.
Over the past two years, VMware has been on a journey to simplify its portfolio and transition from a perpetual to a subscription model to better serve customers with continuous innovation, faster time to value, and predictable investments.
Today, VMware by Broadcom has reached a new milestone with the announcement of the following:
- A dramatic simplification of our product portfolio that allows customers of all sizes to gain more value for their investments in VMware solutions. The portfolio simplification across all VMware by Broadcom divisions stems from customer and partner feedback over the years telling us our offers and go-to-market are too complex.
- Complete the transition of all VMware by Broadcom solutions to subscription licenses, with the end of sale of perpetual licenses, Support and Subscription (SnS) renewals for perpetual offerings, and hybrid purchase program/subscription purchase program (HPP/SPP) credits beginning today (effective dates will vary). Additionally, we are introducing a bring-your-own-subscription license option, providing license portability to VMware validated hybrid cloud endpoints running VMware Cloud Foundation.
Portfolio Simplification
Today, we’re announcing specific changes coming to the VMware Cloud Foundation division portfolio. Going forward, the division will feature two primary offers:
- VMware Cloud Foundation , our flagship enterprise-class hybrid cloud solution for customers to run their business critical and modern applications – in a secure, resilient and cost efficient manner. To allow more customers to benefit from this solution, we’ve reduced the previous subscription list price by half and added higher support service levels including enhanced support for activating the solution and lifecycle management.
- The new VMware vSphere Foundation delivers a more simplified enterprise-grade workload platform for our mid-sized to smaller customers. This solution integrates vSphere with our intelligent operations management to provide the best performance, availability, and efficiency with greater visibility and insights.
Both VMware Cloud Foundation and VMware vSphere Foundation will have optional advanced add-on offers. Our storage offering, ransomware and disaster recovery service, and application platform services are available on both offers. And Application Network and Security offerings are available for VMware Cloud Foundation. Additional advanced services and offerings, including Private AI, will be available soon.
Subscription Licenses
VMware has been on a journey to transition to a subscription model for more than a year now, and the industry has already embraced subscription as the standard for cloud consumption. With a simplified portfolio in place, we’re completing our transition to subscription offerings. Offerings will solely be available as subscriptions or as term licenses following the end of sale of perpetual licenses and Support and Subscription (SnS) renewals beginning today.
The subscription model helps us deliver what customers want:
- Continuous innovation.
- Faster time to value.
- Predictable investments.
Customers may continue using perpetual licenses with active support contracts. We will continue to provide support as defined in contractual commitments. We encourage customers to review their inventory of perpetual licenses, including Support Services renewal and expiration dates. Broadcom will work with customers to help them “trade in” their perpetual products in exchange for the new subscription products, with upgrade pricing incentives. (For additional details, see FAQ).
The simplification of our portfolio and shift to subscription and term offerings are a culmination of our multi-year business transformation efforts. The steps we’re taking today will further enable customer and partner success by delivering the innovation, simplicity and flexibility they need as they undertake their digital transformations.
Frequently Asked Questions
Q: what is vmware by broadcom announcing.
A: Today, VMware by Broadcom has reached a new milestone in its journey and announced the following:
- Complete the transition of all VMware by Broadcom solutions to subscription licenses, with the end of sale of perpetual licenses, Support and Subscription (SnS) renewals for perpetual offerings, and HPP/SPP (generic) credits beginning today. Additionally, we are introducing a bring-your-own-subscription license option, providing license portability to VMware validated hybrid cloud endpoints running VMware Cloud Foundation.
Q: How do these changes benefit customers?
A: Over the past two years, VMware has been on a journey to simplify its portfolio and transition to a subscription model, the industry standard for cloud consumption, and to better serve customers with continuous innovation, faster time to value, and predictable investments. We’re also helping more customers benefit from VMware Cloud Foundation by reducing the list price by half and including higher support service levels including enhanced support for activating the solution and lifecycle management.
Q: Why is this good for partners?
A: The industry has already widely embraced subscription and SaaS, and many partners in our ecosystem have already developed success practices in this area. Subscription and SaaS models provide an opportunity for partners to engage more strategically with customers and deliver higher-value services that drive customer success. It also helps accelerate their own transition to a business model focused on annual recurring revenue.
Q: What are the changes to perpetual licenses?
A: As part of our transition to subscription and a simplified portfolio, beginning today, we will no longer sell perpetual licenses. All offerings will continue to be available as subscriptions going forward. Additionally, we are ending the sale of Support and Subscription (SnS) renewals for perpetual offerings beginning today.
Q: Why make this change from perpetual licenses to subscription?
A: This shift is the natural next step in our multi-year strategy to make it easier for customers to consume both our existing offerings and new innovations. VMware believes that a subscription model supports our customers with the innovation and flexibility they need as they undertake their digital transformations.
Q: Can customers continue to use their perpetual licenses?
A: Yes, customers can continue to use perpetual licenses that they’ve purchased for products.
Q: Can customers still purchase and add additional perpetual licenses after today?
A: After a customer’s effective date for the end of availability of perpetual licenses, customers will not be able to purchase new perpetual licenses. Customers will be able to purchase subscription software or term licenses to supplement or replace their current perpetual-licensed install base.
Q: Can customers renew their Service and Support (SnS) contracts after today?
A: No, customers cannot renew their SnS contracts for perpetual licensed products after today. Broadcom will work with customers to help them “trade in” their perpetual products in exchange for the new subscription products, with upgrade pricing incentives. Customers can contact their VMware account or partner representative to learn more.
Q: Do customers have to collect and submit their perpetual licenses to Broadcom when they “trade-in” their products for subscription?
A: No, Broadcom does not require customers to submit their perpetual licenses to Broadcom when they “trade in” their products for subscription.
Q: Will VMware by Broadcom continue to provide support for active Service and Support (SnS) contracts?
A: We will continue to provide support as defined in contractual commitments.
Q: What will happen to customers’ existing perpetual licenses with active SnS contracts when they are up for renewal?
A: Customers should contact their VMware account or partner representative for upgrade pricing from perpetual to subscription.
Q: What can customers with perpetual licenses do now to prepare?
A: This is an excellent time for customers to assess their current state with VMware infrastructure and management products. We encourage customers to review their inventory of perpetual licenses, including refresh cycles and renewal dates, and become more familiar with VMware's available subscription offers. Customers should also contact their VMware or partner representative for more information.
Q: What VMware Cloud Foundation division offerings are available for purchase?
A: The product simplification across the VMware Cloud Foundation division stems from customer and partner feedback requesting we reduce the complexity of our offers and go-to-market. Going forward, the VMware Cloud Foundation division will feature two primary offers: VMware Cloud Foundation, the new VMware vSphere Foundation and our Hybrid Cloud services and offers. Additionally, we offer VMware vSphere Standard and VMware vSphere Essentials Plus for deployments with more limited requirements.
Q: What is VMware vSphere Foundation?
A: VMware vSphere Foundation is a new solution that combines our full-featured server virtualization platform, vSphere with intelligent operations management to deliver the best performance, availability, and efficiency with greater visibility and insights. For customers seeking an HCI solution, we offer VMware vSAN as an add-on to vSphere Foundation, which includes all the capabilities of vSAN including vSAN Max.
Q: What happens to customers that have purchased HPP/EPP credits and still have an outstanding balance of unredeemed credits?
A: We are honoring existing agreements and will work with our customers to help with the redemption of credits on our new offerings.
Q: What products and bundles are impacted by this new policy?
A: Here is a list of products impacted by the new licensing policy:
- VMware Cloud Foundation
- VMware vSphere
- VMware vSAN
- VMware Site Recovery Manager
- VMware vCloud Suite
- VMware Aria Suite
- VMware Aria Universal
- VMware Aria Automation
- VMware Aria Operations
- VMware Aria Operations for Logs
- VMware Aria Operations for Networks
- multi-cloud

IMAGES
VIDEO
COMMENTS
IT risk assessment is a subset of technology risk assessment, primarily concentrating on the information technology infrastructure of an organization. It involves evaluating risks related to IT systems, networks, and data management processes. The assessment aims to ensure the reliability, availability, and security of IT resources, addressing ...
Performing Risk Assessments of Emerging Technologies. Emerging technologies represent a major source of risk, and their complexities make those risk areas especially difficult to assess. Practitioners must consider the whole system view of the emerging technology, its use, its interplay with other technologies, and the combination of parties ...
1. New Technology Assessment 2. Risk Assessment 3. Barrier Assessment The new technology assessment step helps determine if the submission involves new technology, new operating conditions, or both, and categorizes the new technology for further evaluation. There are four categories to consider in the first part of the new technology assessment: 1.
The first reaction is often to use the organization's existing risk approach and shoehorn the new technology into the approach. For emerging technology especially, this can be daunting given the ambiguity across the technology itself, the business model associated with it and the processes and third parties that may be involved for the ...
In many banks, technology-risk management is disconnected from enterprise risk management (ERM) and even from the operational-risk team. That inhibits the bank's ability to prioritize the risks that are of critical importance and deploy the resources to remediate them. A contributing factor is often the absence of a common risk-management ...
A technology risk management policy includes a detailed step-by-step plan, starting from risk assessment to routine monitoring, to ensure your organization is a step ahead when combating technological risks. Implementing such a policy usually consists of the following steps: Conduct a technology risk assessment.
There are options on the tools and techniques that can be seamlessly incorporated into a business' process. The four common risk assessment tools are: risk matrix, decision tree, failure modes and effects analysis (FMEA), and bowtie model. Other risk assessment techniques include the what-if analysis, failure tree analysis, and hazard ...
Published: 09 April 2020 Summary. A set of new risk assessment principles is necessary to support digital business, which functions best at scale and speed. Security and risk management leaders can apply these principles to ensure the success of digital business through effective risk management.
In general, technology risk management activities can be grouped into one of the following three categories: Assessment - The initial step in any technology risk management strategy, which includes listing all IT assets (software, hardware, networks, etc.) and associated risks. Prioritization - Evaluating risks to understand their urgency and ...
A risk assessment determines the likelihood, consequences and tolerances of possible incidents. "Risk assessment is an inherent part of a broader risk management strategy to introduce control measures to eliminate or reduce any potential risk- related consequences." 1 The main purpose of risk assessment is to avoid negative consequences related to risk or to evaluate possible opportunities.
Hopefully though, with these four steps, you will move toward your business goals by building and then executing your technology assessment plan. From here, your next steps are to pursue the specific technology you need to procure, document detailed requirements, evaluate vendors, and negotiate the paperwork.
The fourth trend is related to emerging and evolving risk types that arise from new business models. For instance, digital channels present new kinds of risk (including the greater exposure of digital assets). The rise of analytics requires risk managers to pay close attention to model risk, and the greater level of interconnectedness among ...
1. Identify. At the heart of this process is the task of identifying risks. This involves recognizing and describing potential pitfalls that a business might face. Recognizing these risks early ...
The key goal for building a risk management plan is to write, develop and practice the plan. Practical and realistic risk management needs to be written and documented, or it will remain only an idea and set of abstract strategies. The goal should be to put risk management principles to work for the organization.
The business plan risk analysis section is a strategic tool used in business planning to identify and assess potential threats that could negatively impact the organisation's operations or assets. Taking the time to properly think about the risks your business faces or may face in the future will enable you to identify strategies to mitigate ...
Free trial. IT risk management is the process of managing cybersecurity risks through systems, policies, and technology. This process consists of three primary stages - identification, assessment, and control to mitigate vulnerabilities threatening sensitive resources. The terms IT risk and information risk are often used interchangeably.
Technology has come to play such a large role in day-to-day business operations that it can be a challenge to develop a comprehensive technology risk-management plan. Below, 16 industry experts ...
Risk assessment in business intelligence is vital for companies to protect themselves. It offers businesses a way to secure finances and protect the company's reputation, employees, and customers. Proactively, risk assessment prepares you for financial, physical, or technical issues that may arise. Using business intelligence tools helps with ...
TRRA. technology readiness and risk assessment. 1. Introduction. Effectively evaluating and managing science and technology risk and the maturation of critical new technologies are critical to the success of advanced technology systems development projects. Systems that depend upon the application of new technologies inevitably face three major ...
Cyber risk is a form of business risk. More specifically, it's the potential for business losses of all kinds in the digital domain—financial, reputational, operational, productivity related, and regulatory related. While cyber risk originates from threats in the digital realm, it can also cause losses in the physical world, such as damage ...
4. Calculate the probability and impact of different cyber risks. Two other important considerations for the risk assessment are: The probability of an attack, or the likelihood that an actor will exploit the vulnerability. The outcome of a potential attack, or the impact such an event will have on the organization.
Broadcom will work with customers to help them "trade in" their perpetual products in exchange for the new subscription products, with upgrade pricing incentives. (For additional details, see FAQ). The simplification of our portfolio and shift to subscription and term offerings are a culmination of our multi-year business transformation ...