Applied Cryptography in Network Systems Security for Cyberattack Prevention
Ieee account.
- Change Username/Password
- Update Address

Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Published: 15 June 2020
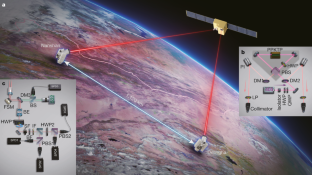
Entanglement-based secure quantum cryptography over 1,120 kilometres
- Juan Yin ORCID: orcid.org/0000-0002-9909-6211 1 , 2 , 3 ,
- Yu-Huai Li 1 , 2 , 3 ,
- Sheng-Kai Liao ORCID: orcid.org/0000-0002-4184-9583 1 , 2 , 3 ,
- Meng Yang 1 , 2 , 3 ,
- Yuan Cao ORCID: orcid.org/0000-0002-0354-2855 1 , 2 , 3 ,
- Liang Zhang 2 , 3 , 4 ,
- Ji-Gang Ren 1 , 2 , 3 ,
- Wen-Qi Cai 1 , 2 , 3 ,
- Wei-Yue Liu 1 , 2 , 3 ,
- Shuang-Lin Li 1 , 2 , 3 ,
- Rong Shu 2 , 3 , 4 ,
- Yong-Mei Huang 5 ,
- Lei Deng 6 ,
- Li Li 1 , 2 , 3 ,
- Qiang Zhang ORCID: orcid.org/0000-0003-3482-3091 1 , 2 , 3 ,
- Nai-Le Liu 1 , 2 , 3 ,
- Yu-Ao Chen ORCID: orcid.org/0000-0002-2309-2281 1 , 2 , 3 ,
- Chao-Yang Lu ORCID: orcid.org/0000-0002-8227-9177 1 , 2 , 3 ,
- Xiang-Bin Wang 2 ,
- Feihu Xu ORCID: orcid.org/0000-0002-1643-225X 1 , 2 , 3 ,
- Jian-Yu Wang 2 , 3 , 4 ,
- Cheng-Zhi Peng ORCID: orcid.org/0000-0002-4753-5243 1 , 2 , 3 ,
- Artur K. Ekert ORCID: orcid.org/0000-0002-1504-5039 7 , 8 &
- Jian-Wei Pan ORCID: orcid.org/0000-0002-6100-5142 1 , 2 , 3
Nature volume 582 , pages 501–505 ( 2020 ) Cite this article
32k Accesses
338 Citations
606 Altmetric
Metrics details
- Quantum information
- Single photons and quantum effects
Quantum key distribution (QKD) 1 , 2 , 3 is a theoretically secure way of sharing secret keys between remote users. It has been demonstrated in a laboratory over a coiled optical fibre up to 404 kilometres long 4 , 5 , 6 , 7 . In the field, point-to-point QKD has been achieved from a satellite to a ground station up to 1,200 kilometres away 8 , 9 , 10 . However, real-world QKD-based cryptography targets physically separated users on the Earth, for which the maximum distance has been about 100 kilometres 11 , 12 . The use of trusted relays can extend these distances from across a typical metropolitan area 13 , 14 , 15 , 16 to intercity 17 and even intercontinental distances 18 . However, relays pose security risks, which can be avoided by using entanglement-based QKD, which has inherent source-independent security 19 , 20 . Long-distance entanglement distribution can be realized using quantum repeaters 21 , but the related technology is still immature for practical implementations 22 . The obvious alternative for extending the range of quantum communication without compromising its security is satellite-based QKD, but so far satellite-based entanglement distribution has not been efficient 23 enough to support QKD. Here we demonstrate entanglement-based QKD between two ground stations separated by 1,120 kilometres at a finite secret-key rate of 0.12 bits per second, without the need for trusted relays. Entangled photon pairs were distributed via two bidirectional downlinks from the Micius satellite to two ground observatories in Delingha and Nanshan in China. The development of a high-efficiency telescope and follow-up optics crucially improved the link efficiency. The generated keys are secure for realistic devices, because our ground receivers were carefully designed to guarantee fair sampling and immunity to all known side channels 24 , 25 . Our method not only increases the secure distance on the ground tenfold but also increases the practical security of QKD to an unprecedented level.
This is a preview of subscription content, access via your institution
Access options
Access Nature and 54 other Nature Portfolio journals
Get Nature+, our best-value online-access subscription
24,99 € / 30 days
cancel any time
Subscribe to this journal
Receive 51 print issues and online access
185,98 € per year
only 3,65 € per issue
Rent or buy this article
Prices vary by article type
Prices may be subject to local taxes which are calculated during checkout
Similar content being viewed by others
Continuous entanglement distribution over a transnational 248 km fiber link
Sebastian Philipp Neumann, Alexander Buchner, … Rupert Ursin
A 15-user quantum secure direct communication network
Zhantong Qi, Yuanhua Li, … Xianfeng Chen

Strategies for achieving high key rates in satellite-based QKD
Sebastian Ecker, Bo Liu, … Rupert Ursin
Data availability
The data that support the findings of this study are available from the corresponding authors on reasonable request.
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. In Proc. Int. Conf. on Computers, Systems and Signal Processing 175–179 (1984).
Ekert, A. K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett . 67 , 661 (1991).
ADS MathSciNet CAS PubMed MATH Google Scholar
Bennett, C. H., Brassard, G. & Mermin, N. D. Quantum cryptography without Bell’s theorem. Phys. Rev. Lett . 68 , 557 (1992).
Peng, C.-Z. et al. Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Phys. Rev. Lett . 98 , 010505 (2007).
ADS PubMed Google Scholar
Rosenberg, D. et al. Long-distance decoy-state quantum key distribution in optical fiber. Phys. Rev. Lett . 98 , 010503 (2007).
Yin, H.-L. et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett . 117 , 190501 (2016).
Boaron, A. et al. Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett . 121 , 190502 (2018).
ADS CAS PubMed Google Scholar
Liao, S.-K. et al. Satellite-to-ground quantum key distribution. Nature 549 , 43 (2017).
Liao, S.-K. et al. Space-to-ground quantum key distribution using a small-sized payload on Tiangong-2 Space Lab. Chin. Phys. Lett . 34 , 090302 (2017).
ADS Google Scholar
Yin, J. et al. Satellite-to-ground entanglement-based quantum key distribution. Phys. Rev. Lett . 119 , 200501 (2017).
Schmitt-Manderbach, T. et al. Experimental demonstration of free-space decoy-state quantum key distribution over 144 km. Phys. Rev. Lett . 98 , 010504 (2007).
Ursin, R. et al. Entanglement-based quantum communication over 144 km. Nat. Phys . 3 , 481 (2007).
CAS Google Scholar
Elliott, C. et al. Current status of the DARPA quantum network. In Quantum Information and Computation III Vol. 5815, 138–150 (International Society for Optics and Photonics, 2005).
Peev, M. et al. The SECOQC quantum key distribution network in Vienna. New J. Phys . 11 , 075001 (2009).
Chen, T.-Y. et al. Field test of a practical secure communication network with decoy-state quantum cryptography. Opt. Express 17 , 6540 (2009).
Sasaki, M. et al. Field test of quantum key distribution in the Tokyo QKD network. Opt. Express 19 , 10387–10409 (2011).
Qiu, J. et al. Quantum communications leap out of the lab. Nature 508 , 441 (2014).
Liao, S.-K. et al. Satellite-relayed intercontinental quantum network. Phys. Rev. Lett . 120 , 030501 (2018).
Koashi, M. & Preskill, J. Secure quantum key distribution with an uncharacterized source. Phys. Rev. Lett . 90 , 057902 (2003).
Ma, X., Fung, C.-H. F. & Lo, H.-K. Quantum key distribution with entangled photon sources. Phys. Rev. A 76 , 012307 (2007).
Briegel, H.-J., Dur, W., Cirac, J. I. & Zoller, P. Quantum repeaters: the role of imperfect local operations in quantum communication. Phys. Rev. Lett . 81 , 5932–5935 (1998).
ADS CAS Google Scholar
Yang, S.-J., Wang, X.-J., Bao, X.-H. & Pan, J.-W. An efficient quantum light–matter interface with sub-second lifetime. Nat. Photon . 10 , 381 (2016).
Yin, J. et al. Satellite-based entanglement distribution over 1200 kilometers. Science 356 , 1140 (2017).
CAS PubMed Google Scholar
Lo, H.-K., Curty, M. & Tamaki, K. Secure quantum key distribution. Nat. Photon . 8 , 595 (2014).
Xu, F., Ma, X., Zhang, Q., Lo, H.-K. & Pan, J.-W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys . 92 , 025002 (2020).
Lydersen, L. et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photon . 4 , 686 (2010).
Zhao, Y., Fung, C.-H., Qi, B., Chen, C. & Lo, H.-K. Quantum hacking: experimental demonstration of time-shift attack against practical quantum-key-distribution systems. Phys. Rev. A 78 , 042333 (2008).
Weier, H. et al. Quantum eavesdropping without interception: an attack exploiting the dead time of single-photon detectors. New J. Phys . 13 , 073024 (2011).
Li, H.-W. et al. Attacking a practical quantum-key-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys. Rev. A 84 , 062308 (2011).
Sajeed, S. et al. Security loophole in free-space quantum key distribution due to spatial-mode detector-efficiency mismatch. Phys. Rev. A 91 , 062301 (2015).
Clauser, J. F., Horne, M. A., Shimony, A. & Holt, R. A. Proposed experiment to test local hidden-variable theories. Phys. Rev. Lett . 23 , 880 (1969).
ADS MATH Google Scholar
Koashi, M. Simple security proof of quantum key distribution based on complementarity. New J. Phys . 11 , 045018 (2009).
ADS MathSciNet Google Scholar
Tomamichel, M., Lim, C. C. W., Gisin, N. & Renner, R. Tight finite-key analysis for quantum cryptography. Nat. Commun . 3 , 634 (2012).
ADS PubMed PubMed Central Google Scholar
Peng, C.-Z. et al. Experimental free-space distribution of entangled photon pairs over 13 km: towards satellite-based global quantum communication. Phys. Rev. Lett . 94 , 150501 (2005).
Cao, Y. et al. Bell test over extremely high-loss channels: towards distributing entangled photon pairs between earth and the moon. Phys. Rev. Lett . 120 , 140405 (2018).
Ladd, T. D. et al. Quantum computers. Nature 464 , 45–53 (2010).
Makarov, V., Anisimov, A. & Skaar, J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys. Rev. A 74 , 022313 (2006).
Qi, B., Fung, C.-H.F., Lo, H.-K. & Ma, X. Time-shift attack in practical quantum cryptosystems. Quantum Inf. Comput . 7 , 73 (2007).
MathSciNet MATH Google Scholar
Gerhardt, I. et al. Experimentally faking the violation of Bell’s inequalities. Phys. Rev. Lett . 107 , 170404 (2011).
Bugge, A. N. et al. Laser damage helps the eavesdropper in quantum cryptography. Phys. Rev. Lett . 112 , 070503 (2014).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett . 108 , 130503 (2012).
Scarani, V. et al. The security of practical quantum key distribution. Rev. Mod. Phys . 81 , 1301–1350 (2009).
Shor, P. & Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett . 85 , 441 (2000).
Gottesman, D., Lo, H.-K., Lütkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices. Quantum Inf. Comput . 4 , 325 (2004).
Mayers, D. J. Unconditional security in quantum cryptography. J. Assoc. Comput. Mach . 48 , 351–406 (2001).
Lo, H. K. & Chau, H. F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 283 , 2050 (1999).
Ben-Or, M., Horodecki, M., Leung, D. W., Mayers, D. & Oppenheim, J. In Proc. 2nd Int. Conf. on Theory of Cryptography (TCC'05) 386–406 (Springer, 2005).
Renner, R. Security of quantum key distribution. PhD thesis , ETH Zurich (2005); preprint at https://arxiv.org/abs/quant-ph/0512258 .
Tsurumaru, T. Leftover hashing from quantum error correction: unifying the two approaches to the security proof of quantum key distribution. Preprint at https://arxiv.org/abs/1809.05479 (2018).
Serfling, R. J. Probability inequalities for the sum in sampling without replacement. Ann. Stat . 2 , 39–48 (1974).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun . 5 , 3732 (2014).
Fung, C.-H. F., Tamaki, K., Qi, B., Lo, H.-K. & Ma, X. Security proof of quantum key distribution with detection efficiency mismatch. Quantum Inf. Comput . 9 , 131–165 (2009).
Marøy, Ø., Lydersen, L. & Skaar, J. Security of quantum key distribution with arbitrary individual imperfections. Phys. Rev. A 82 , 032337 (2010).
Download references
Acknowledgements
We acknowledge discussions with X. Ma and C. Jiang. We thank colleagues at the National Space Science Center, China Xi’an Satellite Control Center, National Astronomical Observatories, Xinjiang Astronomical Observatory, Purple Mountain Observatory, and Qinghai Station for their management and coordination. We thank G.-B. Li, L.-L. Ma, Z. Wang, Y. Jiang, H.-B. Li, S.-J. Xu, Y.-Y. Yin, W.-C. Sun and Y. Wang for their long-term assistance in observation. This work was supported by the National Key R&D Program of China (grant number 2017YFA0303900), the Shanghai Municipal Science and Technology Major Project (grant number 2019SHZDZX01), the Anhui Initiative in Quantum Information Technologies, Science and Technological Fund of Anhui Province for Outstanding Youth (grant number 1808085J18) and the National Natural Science Foundation of China (grant numbers U1738201, 61625503, 11822409, 11674309, 11654005 and 61771443).
Author information
Authors and affiliations.
Hefei National Laboratory for Physical Sciences at the Microscale and Department of Modern Physics, University of Science and Technology of China, Hefei, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Feihu Xu, Cheng-Zhi Peng & Jian-Wei Pan
Shanghai Branch, CAS Center for Excellence in Quantum Information and Quantum Physics, University of Science and Technology of China, Shanghai, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Liang Zhang, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Rong Shu, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Xiang-Bin Wang, Feihu Xu, Jian-Yu Wang, Cheng-Zhi Peng & Jian-Wei Pan
Shanghai Research Center for Quantum Science, Shanghai, China
Juan Yin, Yu-Huai Li, Sheng-Kai Liao, Meng Yang, Yuan Cao, Liang Zhang, Ji-Gang Ren, Wen-Qi Cai, Wei-Yue Liu, Shuang-Lin Li, Rong Shu, Li Li, Qiang Zhang, Nai-Le Liu, Yu-Ao Chen, Chao-Yang Lu, Feihu Xu, Jian-Yu Wang, Cheng-Zhi Peng & Jian-Wei Pan
Key Laboratory of Space Active Opto-Electronic Technology, Shanghai Institute of Technical Physics, Chinese Academy of Sciences, Shanghai, China
Liang Zhang, Rong Shu & Jian-Yu Wang
The Institute of Optics and Electronics, Chinese Academy of Sciences, Chengdu, China
Yong-Mei Huang
Shanghai Engineering Center for Microsatellites, Shanghai, China
Mathematical Institute, University of Oxford, Oxford, UK
Artur K. Ekert
Centre for Quantum Technologies, National University of Singapore, Singapore, Singapore
You can also search for this author in PubMed Google Scholar
Contributions
C.-Z.P., A.K.E. and J.-W.P. conceived the research. J.Y., C.-Z.P. and J.-W.P. designed the experiments. J.Y., Y.-H.L., S.-K.L., M.Y., Y.C., J.-G.R., S.-L.L., C.-Z.P. and J.-W.P. developed the follow-up optics and monitoring circuit. J.Y., Y.-M.H., C.-Z.P. and J.-W.P. developed the efficiency telescopes. J.Y., S.-K.L., Y.C., L.Z., W.-Q.C., R.S., L.D., J.-Y.W., C.-Z.P. and J.-W.P. designed and developed the satellite and payloads. J.Y., L.Z., W.-Q.C., W.-Y.L. and C.-Z.P. developed the software. F.X., X.-B.W., A.K.E. and J.-W.P. performed the security proof and analysis. L.L., Q.Z., N.-L.L., Y.-A.C., X.-B.W., F.X., C.-Z.P., A.K.E. and J.-W.P. contributed to the theoretical study and implementation against device imperfections. F.X., C.-Y.L., C.-Z.P. and J.-W.P. analysed the data and wrote the manuscript, with input from J.Y., Y.-H.L., M.Y., Y.C. and A.K.E. All authors contributed to the data collection, discussed the results and reviewed the manuscript. J.-W.P. supervised the whole project.
Corresponding authors
Correspondence to Cheng-Zhi Peng or Jian-Wei Pan .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Extended data figures and tables
Extended data fig. 1 satellite-to-delingha link efficiencies under different weather conditions..
a , The data in previous work 23 was taken in different orbits during the period of 7 December 2016 to 22 December 2016. b , The data in current work was taken in different orbits during the period of 6 September 2018 to 22 October 2018. Here the change of link efficiencies on different days was caused by the weather conditions.
Extended Data Fig. 2 Multiple orbits of satellite-to-Delingha link efficiencies under good weather conditions.
Stable and high collection efficiencies were observed during the period of October 2018 to April 2019.
Extended Data Fig. 3 The comparison of satellite-to-Delingha link efficiency under the best-orbit condition.
a , After improving the link efficiency with high-efficiency telescopes and follow-up optics, on average, the current work shows a 3-dB enhancement in the collection efficiency over that of ref. 23 . The lines are linear fits to the data. b , Some representative values.
Extended Data Fig. 4 The finite-key secret key rate R versus the QBER.
For the 3,100 s of data collected in our experiment, a QBER of below about 6.0% is required to produce a positive key. The previous work 23 demonstrated a QBER of 8.1%, which is not sufficient to generate a secret key. In this work, a QBER of 4.5% and a secret key rate of 0.12 bits per second are demonstrated over 1,120 km. If one ignores the important finite-key effect, the QBER in ref. 23 is slightly lower than the well known asymptotic limit of 11% (ref. 43 ).
Extended Data Fig. 5 Schematics of the detection and blinding-attack monitoring circuit.
The biased voltage (HV) is applied to an avalanche photodiode through a passive quenching resistance ( R q = 500 kΩ) and a sampling resistance ( R s = 10 kΩ). The avalanche signals are read out as click or no-click events through a signal-discrimination circuit. The blinding signal monitor is shown in the dot-dash diagram. A resistor-capacitor filter and a voltage follower are used to smooth and minimize the impact on the signals. The outputs of an analogue to digital converter (ADC), at a sampling rate of 250 kHz, are registered by computer data acquisition (PC-DAQ). R1, resistor; C1, capacitor; OA, operational amplifier.
Extended Data Fig. 6
The transmission of the beam splitter within the selected bandwidth of wavelength.
Rights and permissions
Reprints and permissions
About this article
Cite this article.
Yin, J., Li, YH., Liao, SK. et al. Entanglement-based secure quantum cryptography over 1,120 kilometres. Nature 582 , 501–505 (2020). https://doi.org/10.1038/s41586-020-2401-y
Download citation
Received : 15 July 2019
Accepted : 13 May 2020
Published : 15 June 2020
Issue Date : 25 June 2020
DOI : https://doi.org/10.1038/s41586-020-2401-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Quantum-secured time transfer between precise timing facilities: a field trial with simulated satellite links.
- Francesco Picciariello
- Francesco Vedovato
- Florian Moll
GPS Solutions (2024)
Enhanced Performance of Measurement-device-independent Quantum Key Distribution over Turbulent Channels through Adaptive Optics
- Guoqi Huang
- Rongzhen Jiao
Quantum Information Processing (2024)
Polarization bases compensation towards advantages in satellite-based QKD without active feedback
- Sourav Chatterjee
- Kaumudibikash Goswami
- Urbasi Sinha
Communications Physics (2023)
Finite key performance of satellite quantum key distribution under practical constraints
- Jasminder S. Sidhu
- Thomas Brougham
- Daniel K. L. Oi
Demonstration of quantum-digital payments
- Peter Schiansky
- Philip Walther
Nature Communications (2023)
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
Academia.edu no longer supports Internet Explorer.
To browse Academia.edu and the wider internet faster and more securely, please take a few seconds to upgrade your browser .
- We're Hiring!
- Help Center
Applied Cryptography
- Most Cited Papers
- Most Downloaded Papers
- Newest Papers
- Save to Library
Advertisement
A systematic review of homomorphic encryption and its contributions in healthcare industry
- Original Article
- Open access
- Published: 03 May 2022
- Volume 9 , pages 3759–3786, ( 2023 )
Cite this article
You have full access to this open access article
- Kundan Munjal 1 , 2 &
- Rekha Bhatia 3
15k Accesses
25 Citations
3 Altmetric
Explore all metrics
Cloud computing and cloud storage have contributed to a big shift in data processing and its use. Availability and accessibility of resources with the reduction of substantial work is one of the main reasons for the cloud revolution. With this cloud computing revolution, outsourcing applications are in great demand. The client uses the service by uploading their data to the cloud and finally gets the result by processing it. It benefits users greatly, but it also exposes sensitive data to third-party service providers. In the healthcare industry, patient health records are digital records of a patient’s medical history kept by hospitals or health care providers. Patient health records are stored in data centers for storage and processing. Before doing computations on data, traditional encryption techniques decrypt the data in their original form. As a result, sensitive medical information is lost. Homomorphic encryption can protect sensitive information by allowing data to be processed in an encrypted form such that only encrypted data is accessible to service providers. In this paper, an attempt is made to present a systematic review of homomorphic cryptosystems with its categorization and evolution over time. In addition, this paper also includes a review of homomorphic cryptosystem contributions in healthcare.
Similar content being viewed by others

Homomorphic Cryptosystems for Securing Data in Public Cloud Computing

A Survey of Various Cryptographic Techniques: From Traditional Cryptography to Fully Homomorphic Encryption

- Homomorphic Encryption
Avoid common mistakes on your manuscript.
Introduction
Encryption approaches usually do not allow processing on encrypted data which implies every time data are processed in its original form. On the other hand, homomorphic encryption allows computation on encrypted data and provides encrypted results to the user. Homomorphic encryption not only allows the processing of encrypted data but also preserves privacy in the process. Classic public-key encryption consists of three algorithms: Key generation , Encryption , and Decryption ; however, in addition to these three conventional approaches, a homomorphic encryption property is required. Homomorphic property \(\varepsilon \) has an efficient algorithm \(Eval_{\varepsilon }\) with input as \(p_k\) encryption key, C is circuit generated from set \( C_\varepsilon \) and ciphertexts \(C_p = (c_{p1},c_{p2},....c_{pt})\) encrypted under public key \(p_k\) then \(Eval_{\varepsilon }(p_k,C,C_p)\) encrypts \(C( m_1,m_2,....,m_t)\) under \(p_k\) where \(C( m_1,m_2,....,m_t)\) is output of C on inputs \((m_1,m_2,....,m_t)\) . Consider a scenario with respect to healthcare where a doctor or patient send sensitive information to cloud for predicting some results as illustrated in Fig. 1 .
Step 1: Client (Patient or Doctor) sends data to third party service provider for performing a query/operation. Before sending, client encrypts the data.
Step 2: The client then asks the cloud service provider to perform a certain function on the data and provide the results.
Step 3: Cloud service provider then performs operations using homomorphic encryption property with some function f(). Noise is produced with arbitrary large number of operations. Every addition operation adds to the noise, and every multiplication operation double the noise. High computation on encrypted data results in excessive noise and there are several noise reduction methods. One of the most popular methods are bootstrapping and squashing. Both of these methods are a self-reliant process that progresses without external help. Modulus switching is another prominent strategy for achieving better asymptotic performance than bootstrapping.
Step 4: Encrypted results are provided to client.
Step 5: Client at its end computes decryption using decryption function and recovers f(message).
As a result no information is lost by getting encrypted results and decryption at its own end.
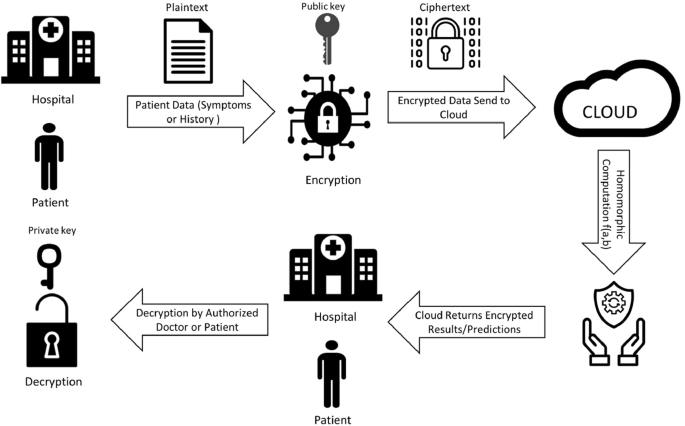

Homomorphic encryption in healthcare
Security is the key concern in cloud computing. Data provided to third-party service providers for processing and automation are a big issue. Every single business or organization wishes for the personal and sensitive data of the user. Every organization whether government, private, healthcare, academia requires data for policy formation, research purposes, planning new marketing strategies, or launching innovative products. Our main concern is with healthcare privacy as according to a survey by acumen research and consulting [ 1 ] healthcare cloud computing market will pass US$ 40 billion by the year 2026. Cloud computing in health care not only increases efficiency but also reduces cost. It is fast but protection of patient-sensitive data is the prime concern as it will not only promote patient confidence but also help in economic development. The digitization of a patient’s medical records is supposed to improve care quality and efficiency while reducing costs. On the other hand, patient records include a considerable quantity of sensitive information. As a result, patients must be able to swiftly allow a range of medical affiliates to access their sensitive information using a simple, trustworthy, efficient, and secure approach. Therefore, it is vital to look at the usage of homomorphic encryption in healthcare and compare various homomorphic algorithms for illness prediction as well as data querying while protecting the privacy of patient information.
The rest of this article is organized as follows: the next section contains review methods, planning, inclusion and exclusion criterion, research questions with motivation. The subsequent section compares and analyzes homomorphic encryption starting with partial and somewhat homomorphic encryption approaches followed by fully homomorphic encryption approaches. Techniques to fully homomorphic encryption were classified into four categories, with significant approaches in each category were compared. The next section focuses on homomorphic encryption in the healthcare sector. Homomorphic encryption techniques were compared on the basis of communication and computation overhead for securely identifying LQTC, cancer, average heart rate, cardiovascular problems, and a secure query generating system in healthcare. Finally, conclusion is presented.
Review method
The systematic review process may be considered as a means of solving a specific research problem. Presently no systematic reviews are focusing on homomorphic cryptosystems in healthcare and bioinformatics, therefore a systematic review research methodology was chosen. As a result, the systematic review aims to close this significant research gap. Kitchenham and Brereton [ 2 ] recommendations were selected to evaluate and explain all homomorphic encryption research questions. Our work is motivated by the revolutionary work of Craig Gentry [ 3 , 4 ]. Additionally, the fact that fully homomorphic encryption will act as a boon to the healthcare industry as it will preserve complete privacy of patient health data is also a path of motivation. Reviewing the processes outlined in Fig. 2 will give a basic understanding of the systematic review process:
Define research/review question: After reading various research/Journal articles and magazines and consulting with the expertise in the area of homomorphic encryption. Various research questions were identified.
Develop Review Protocol: Pre-define the kind of research that will be included, as well as the procedures for collecting, evaluating, and analysing data.
Identification of Research: After, Gentry’s revolutionary work in homomorphic encryption, a number of homomorphic encryption methodologies in healthcare and bioinformatics were published. Despite tremendous research in homomorphic encryption there is no systematic review that considers quality of research and development.
Extraction: Relevant research articles were included and irrelevant were excluded.
Study Quality Assessment: Research articles were selected from popular repositories with keywords as homomorphic encryption to review basic homomorphic approaches.
Data Synthesis: This phase entailed presenting data in descriptive and graphical form. It will help to make the overall evaluation of outcomes easier.
Knowledge Translation: The findings and details of the review will be distributed to relevant target groups in a variety of media.
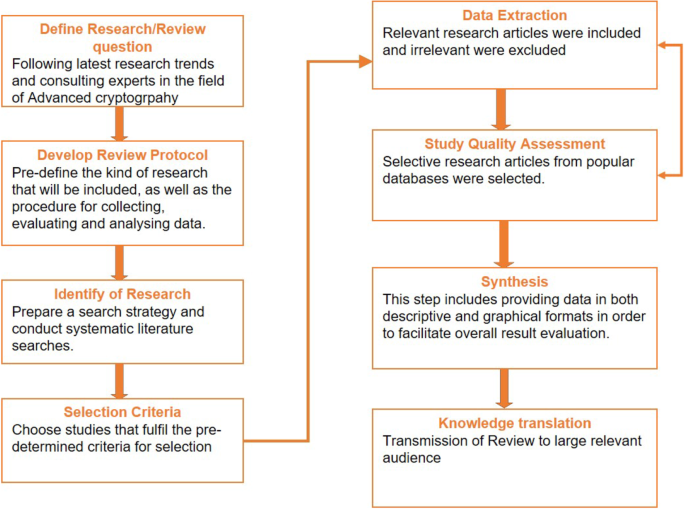
Steps in systematic review
Review planning
The accomplishment behind each review depends on the selection of good-quality papers with unique work and genuine references. Thus, recognized journals, conference proceedings, and databases were investigated and explored in the area of homomorphic encryption. Scientific publications from Scopus, ACM Digital library, Springer Link, Sciencedirect, Google Scholar were selected based upon research questions given in Table 1 . Fundamental studies in PHE, SWHE that function as cornerstones of homomorphic encryption were chosen first, followed by publications focused only on fully homomorphic encryption. A total of 1815 scientific papers were obtained using a database search with Keywords used for search as ’homomorphic encryption’, and ’homomorphic encryption’ or “medical” OR “healthcare” OR “bioinformatics” OR “EHR” OR “patient” OR “health” OR “medicine”. Following the removal of duplicate documents, a total of 857 records were evaluated for title screening. After screening title total 194 articles were selected for abstract screening. In abstract screening 69 papers that were focused on homomorphic encryption based upon LWE, NTRU, Lattices, Integers, and HE papers focused mainly on healthcare and bioinformatics were selected. Other than that 19 important papers in PHE and SWHE (consider Fig. 4 ) were chosen for better understanding the concept of homomorphic encryption.
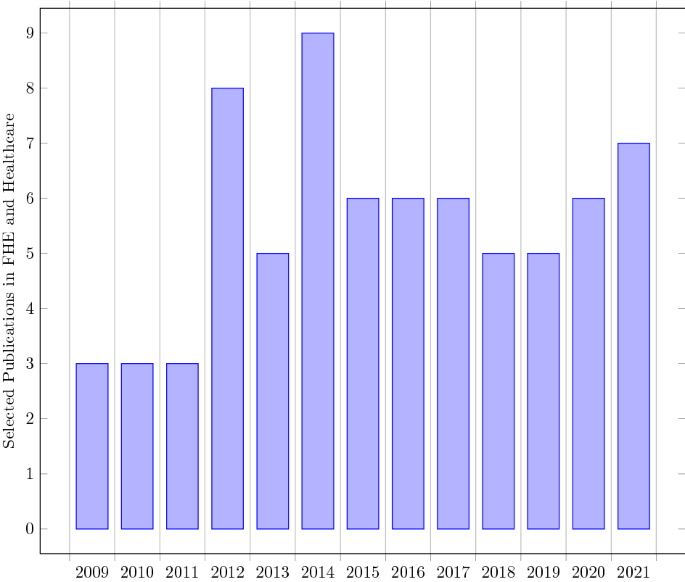
Scientific Articles from year 2009 to 2021
Inclusion and exclusion criteria
Scientific articles in journals, conferences proceedings, workshops published in the year range from Jan 2009 to Dec 2021 (Fig. 3 ) were considered. Other than that, Partial and Somewhat homomorphic encryption papers of the old era were also included to better understand the concept of homomorphic encryption. All quality research publications of fully homomorphic encryption after the Gentry FHE scheme were considered. Articles that were focused on the applicability of homomorphic encryption other than healthcare or bioinformatics were excluded.
Research questions
Prime objective of this review writing is to categorize the current literature on homomorphic encryption with its contributions in health informatics. This research study’s end result is the identification and examination of homomorphic encryption methods in healthcare. A set of research questions are formulated for this systematic literature review in Table 1 .
The medical services industry is experiencing a digital revolution. Modernizing medical care has prompted another time of computerized wellbeing and health. Medical services information is gathered from different sources (e.g., sensors associated with patients) and stored in unique medical services clouds (e.g., private and public clouds). Also, the volume of agglomerated medical information is sufficiently enormous to qualify as “Big Data”. As cloud medical services become a well-defined component in the medical services industry, there is a more critical requirement for safely sharing patient data across such dissimilar medical services clouds. Besides, with Accountable Treatment Organizations (ACOs) (e.g., medical service providers, specialists, clinics, and protection providers) collaborate to provide top-notch care, with demand for constant availability across cloud medical services higher than at any point in recent times. A disentangled patient-driven paradigm, in which patients can switch suppliers while still providing their data in a useful way for better diagnosis and treatment, and, in the long term, for enhanced global health, is appealing. As of now, medical care suppliers who have delicate patient information in private medical care clouds across the globe are reluctant to share that data on account of security and protection issues. As medical care suppliers move to the local area and public cloud-based administrations, a requirement for a secure connection between divergent medical care cloud increments. Moreover, security guidelines forced by Health Insurance Portability and Accountability Act (HIPAA) [ 6 ] and Health Information Technology for Economic and Clinical Health (HITECH) [ 7 ] place a cumbersome undertaking on medical care Information Technology (IT) framework to be agreeable with protection and security guidelines. Moreover, with arising Internet of Things (IoT) market and its mix in the vast information cloud stage, there is expanded worry about security and protection with the medical services cloud worldview. Many researchers contributed with their study in homomorphic encryption. Homomorphic encryption has three types: partial homomorphic encryption (PHE), somewhat homomorphic encryption (SWHE), and fully homomorphic encryption Fig. 5 . PHE supports either addition or multiplication i.e. one operation over encrypted data. SWHE supports a finite number of operations, i.e., it evaluates the circuit up to some limit or depth. FHE supports both operations infinite number of times over encrypted data.
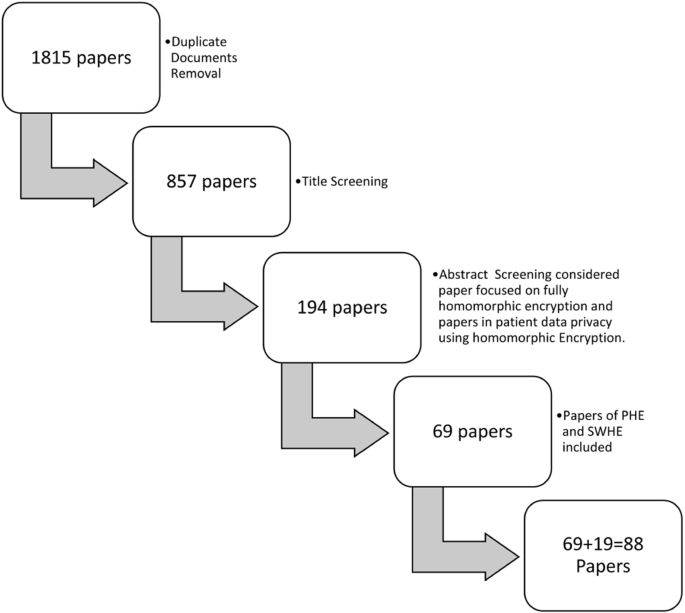
Research articles selection procedure
Partial homomorphic encryption schemes
There are various partial homomorphic encryption schemes available. It all started by Rivest, Adleman and Dertouzos [ 8 ] with an asymmetric encrypted system that supports multiply operation over ciphertext and first time they uses the term “privacy homomorphism”. It was based upon hardness of prime factoring problem. Goldwasser-Micali [ 9 ] proposed first scheme with semantic security proof. It was based upon the hardness of quadratic residuosity assumption [ 10 ] which states that if \(q\in Z_N ^*\) , is q \(\equiv \) \(x^2 mod N\) where
is solvable then q is quadratic residue mod N otherwise q is quadratic non-residue N . In, 1985 Tahar Elgamal [ 11 ] proposed a better public key cryptosystem which was an improvement over Diffie-Hellman[ 12 ] key exchange algorithm. In this public-key cryptography, security depends upon the hardness of discrete algorithms over finite fields. In discrete algorithm, consider a prime number p . let \(\alpha \) and \(\beta \) be integers which cannot be divided by p then find x such that \(\alpha ^x\) \(\equiv \) \( \beta \) ( modp ). Dense probabilistic encryption by Benaloh [ 13 ] is a homomorphic encryption scheme over addition operator with an improved expansion factor as compared to Goldwasser-Micali. The proposal was based upon higher residuosity problem[ 14 ] \(x^n\) as compared to quadratic residuosity problem, which is \(x^n\) in GM cryptosystem. Benaloh approach has a homomorphic property which shows that encrypted text multiplicative operation is the same as plain text addition operation. As encryption was applied after messages were added, encrypted messages \(Enc(m_1)\) and \(Enc(m_2)\) may be directly assessed. As a result, one can deduce that Benaloh’s method was additive homomorphic. Paillier [ 15 ] in 1999 proposed a trapdoor approach compared to prime residuosity, Paillier approach was based upon composite residuosity classes, which believed to be kind of boon to public-key cryptosystems. Initially, the nature of Paillier cryptosystem allows addition operation over encrypted data but later improvements in the approach proved that multiplications can also be performed over encrypted data. There are other partial homomorphic schemes [ 16 , 17 , 18 ] that were based upon previous work by Elgamal, Benaloh and Paillier, which improves computational performance while maintaining homomorphic property. In [ 19 ], due to hardness of the lattice problems, the author, proposed homomorphic cryptosystem with addition operation over vast cyclic group. Authors called their proposed scheme’s homomorphic attribute pseudohomomorphic . Galbraith [ 20 ] proposed a more natural generalization of Paillier’s cryptography approach, which he applied to elliptic curves while keeping the Paillier’s cryptosystem’s additional homomorphic property. Various partial homomorphic encryption (Table 2 ) approaches are compared based upon encryption, decryption, hardness, and homomorphic property.
Somewhat homomorphic encryption schemes
SWHE schemes [ 22 , 23 , 24 , 25 , 26 ] support an arbitrary number of operations, but with each operation, a noise is generated and after a limit the underlying encrypted value is lost. As a result, SWHE systems support arbitrary operations but only for a finite number of times. Each addition operation increases noise and every multiplication operation causes noise to multiply. SWHE is a unique but not complete solution like fully homomorphic encryption. FHE supports an unlimited number of arbitrary operations over ciphertext. Boneh-Goh-Nissim [ 23 ] proposed a semantically safe technique for adding and multiplying encrypted data. It supports an arbitrary number of addition with a single multiplication operation on ciphertext with a specified length. BGN enables evaluation of quadratic formulas over ciphertexts, i.e., 2-DNF ( Disjunctive Normal Form ). BGN approach hardness was dependent upon the subgroup decision problem [ 27 ], which states that whether a given element \(g_1\) of a finite group G is a member of subgroup \(G_1\) . Yao [ 22 ] study is an early effort for performing functions operations on the ciphertext. As a solution to the Millionaires’ Problem, Yao developed a two-party communication protocol, which compares the wealth of two wealthy persons without disclosing the precise amount.
Furthermore, in this approach, the ciphertext size grows linearly at a minimum as every gate in the circuit is computed. Yuval Ishai and Anat Paskin (IP) [ 24 ] proposed a scheme based upon a branching program evaluation on encrypted data. In [ 26 ] author proposed first SWHE scheme over a semi-group and NC1 is a complexity class covering circuits with poly-logarithmic depth and polynomial dimension. With one OR/NOT gate, the suggested technique allowed for polynomially many ANDing of ciphertexts. With each multiplication size of ciphertext increases.
Key generation:
Consider \(C_G\) and \(C_{G_1}\) as multiplicative cyclic groups of order n with \(n=q_1q_2\) . let g be a generator of \(C_G\) with \(e:C_G \times C_G \rightarrow C_{G_1}\) is a bilinear map, public key is \( (n,C_G,C_{G_1},e,g,h)\) with a as generator of \(C_G\) \(g,a\xleftarrow {\text {R}}\) and set \(h=a^{q_2}h\) being random generator of subgroup of \(C_G\) of order \(q_1\) .
Encryption:
\(c_{p1}=E_{msg_1}=g^{msg_1}h^r mod n\) , where r being random number \(\in \) {0,1,.,.,.n-1}.
Decryption:
\(msg_1=D(c_{p1})=\log _{g'}c'\)
Homomorphic Property under addition:
Where, \(r_1+r_2+r=r\)
Homomorphic property under multiplication: Consider \(g_1\) and \(h_1\) with order n and \(q_1\) , respectively. set \(g_1=e(g,g)\) and \(h_1=e(g,h)\) . Also consider \(h=g^{\alpha q_2}\) , \(\alpha \in \mathbb {Z}\) .
with \(r'=msg_1r_2+r_2msg_1+\alpha q_2r_1r_2+r\) ,uniformly distributed in \(\mathbb {Z}\) and ciphertext is uniformly distributed in \(C_{G_1}\) instead of \(C_G\) .
Fully homomorphic encryption schemes
An encryption scheme is fully homomorphic if it supports two operations, i.e., addition and multiplication, an infinite number of times over encrypted data. Ciphertext contains noise that increases with operations in all the fully homomorphic encryption schemes. In particular, a multiplication operation increases more noise than an addition operation. The noise level gets too high at a certain threshold, preventing additional homomorphic procedures from resulting in accuracy. At this point, a refreshing procedure is required, which makes the performance highly unsatisfactory.
Preliminaries for FHE
In this section, the FHE scheme is classified into four categories (Fig. 5 ). These advanced cryptographic approaches act as preliminaries for fully homomorphic encryption schemes. A review of research papers based on these criteria is also conducted.
Lattice based cryptography
Learning with errors (LWE/RLWE)
Integer based
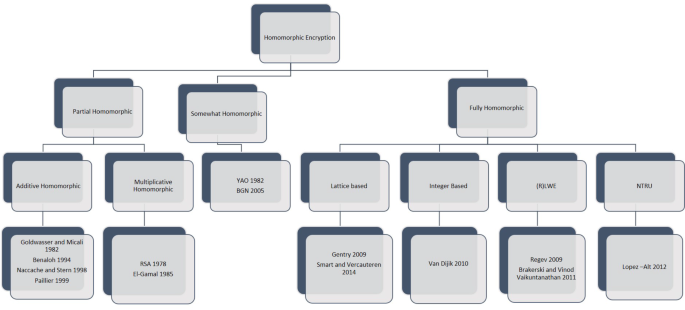
Classification of homomorphic encryption
Lattice-based cryptography
Lattice-based cryptography is an advanced cryptosystem. It holds first place in the advanced post-quantum cryptosystem, i.e., Cryptography based on lattices is thought to be safe against superfast quantum computers. Lattice-based cryptosystems are based upon hard problems like Shortest Vector Problem to find the shortest non-zero vector in the lat and Closest Vector Problem with the goal of finding the closest lattice vector with the given vector. In n-dimensional space, a lattice is any regularly spaced grid of points. Formally, n independent vectors known as basis of the lattice \(b_1,b_2,b_3,\dots \) , \(b_n\) are generated as a set of vectors
\(\mathcal {L}\) ( \(b_1,b_2,b_3,\dots ,b_n)= \sum _{j=1}^{n} x_jb_j \) , \(x_j \in \mathbb {Z}\) .
In 2009 Gentry [ 3 ] proposed a fully homomorphic encryption scheme, which was the first fully homomorphic encryption scheme. The solution comprises three steps. In the first step it provides general result that can evaluate its own decryption circuit i.e. bootstrappable . In the Second step, a public key encryption approach was suggested. This approach uses the concept of ideal lattices with having a bootstrappable property. It is represented as the lattice FHE technique that allows both homomorphic addition and multiplication computations on encrypted data. Former HE approaches provide either of the two operations as in Table 2 ; therefore, those schemes were partial homomorphic. The challenge of FHE is noise which increases as number of homomorphic operations increase. If the noise becomes too large, it becomes challenging to decrypt correctly.
Gentry’s approach is somewhat homomorphic (SHE) which means it can handle homomorphic operations up to a limit and to make it for unlimited operations ciphertext needs to be refreshed using bootstraping procedure. This procedure is a recrypting process, and inefficient. Initially, the encryption was bitwise, meaning that each bit of data was encrypted independently, and the result was ciphertext. Bit addition and multiplication (modulo 2) correspond to XOR and AND bitwise operations, allowing any Boolean circuit to be evaluated, i.e., any calculation to be done by first defining the computation in XOR and AND gates. However, immediately breaking down a calculation into bit operations results in complex and deep computation circuits, which SWHE cannot handle and requires encryption, i.e., Bootstrapping.
Bootstrapping and squashing
If a scheme is homomorphic enough to evaluate its circuit of decryption, it can be transformed into fully homomorphic encryption capable of evaluating any function. High computation on encrypted data results in high noise. It is necessary to refresh encrypted data regularly, but this must be done without needing a secret key, which is accomplished by bootstrapping. Bootstrapping is a self-reliant process that progresses without external help. Suppose SWHE can handle a circuit up to a certain threshold depth, D . If the augmented decrypt circuit has depth \(\le D\) , then the system is bootstrappable, i.e., the ciphertext can be refreshed through recryption. The idea behind recryption is:
Consider two secret key pairs. \((sk_1,pk_1)\) and \((sk_2,pk_2)\) and \(Decrypt_E(sk_1, Encrypt_E(pk_1,m))=m\) for message say m and same for second pair. Suppose E is homomorphic with respect to decryption circuit. Encryption of \(sk_1\) under \(pk_2\) will be \(Encrypt_E(pk_2,sk_1)\) . Encryption of initial ciphertext with public key
\(pk_2:\) \(Encrypt_E(pk_2, Encrypt_E(pk_1,m))\)
\(Decrypt_E(Encrypt_E(pk_2,sk_1),Encrypt_E(pk_1,m))\) \(=Encrypt_E(pk_2,m)\)
and it is to be done bitwise. In this way inner encryption is removed by creating a newly encrypted ciphertext with \(pk_2\) and the scheme can homomorphically evaluated.
\(Decrypt_E(sk,c_1) + Decrypt_E(sk,c_2)\) or,
\(Decrypt_E(sk,c_1) * Decrypt_E(sk,c_2)\) .
Bootstrapping is valid in decryption algorithms with lesser circuit depths. But if the circuit depth is high, bootstrapping is not possible due to performance issues. As a result, an improved technique is applied known as squashing , which reduces decryption algorithm complexity. According to this scheme, initially, a set of vectors are selected. The sum of these vectors is the same as the multiplicative inverse of the private key. Set elements are then multiplied with the encrypted text. As a result, polynomial degree of the circuit is reduced to an acceptable level. Retrieving private keys depends upon the assumption of SSSP (Sparse Subset Sum Problem) mentioned in [ 28 ]. Craig Gentry and Shai Halevi [ 29 ] proposed an FHE scheme that is hybrid of SWHE and MHE, i.e., Multiplicative homomorphic encryption. The approach still depends upon bootstrapping step, but it avoids squashing as it does not rely on the assumed hardness of SSSP. A new method in which sparse subset sum problem was replaced with Decision-Diffie Hellman [ 30 ]. This approach additionally substitutes MHE with AHE (additively homomorphic encryption), which encrypts discrete logarithms and creates a leveled FHE whose difficulty is determined by the shortest independent vector problem over ideal lattices [ 31 ]. At PKC 2010, a modified Gentry’s fully homomorphic public-key encryption scheme was presented by Smart and Vercauteren [ 32 ] that can support SIMD style operations. Gentry and Halevi followed the slow key generation process of smart and Vercauteren but still lacks SIMD style operation. A realization of achieving Single instruction multiple data operations using homomorphic evaluation of AES was given by smart and Vercauteren in 2011. BDDD, i.e., bounded distance decoding problem for somewhat homomorphic, ensured the encryption scheme’s security and sparse subset sum problem for bootstrapping procedure.
Integer-based FHE schemes
A SWHE was presented [ 33 ] based upon integers with the hardness of algorithm depending upon Approximate Greatest Common Divisor problem [ 34 ]. Although the scheme was symmetric, It was also demonstrated basic symmetric homomorphic encryption technique that may be transformed to an asymmetric homomorphic encryption technique [ 33 ]. At Eurocrypt 2013, an extended version of fully homomorphic encryption over integers was presented with batch FHE scheme over integers [ 35 ].Using the renowned Chinese Remainder Theorem, the DGHV method was extended by packing l plaintexts \(m_0,m_1,\cdots ,m_l\) into a single ciphertext. It allows not only encrypting bits but also elements from rings of the form \(\mathbb {Z}_Q\) . There are also some additional FHE schemes proposed over integers. A novel FHE over integers that is scale-invariant [ 36 ], an approach with integers plaintext [ 37 ], a symmetric FHE scheme that does not require bootstrapping [ 38 ], a SWHE method for performing arithmetic operations on huge integer values without converting them to bits [ 39 ]. In their names imply, all of these approaches enhanced FHEs over integers.
Learning with errors
Learning with errors (LWE) is a key concept that serves as a building block of advanced cryptographic algorithms. LWE is a generalization of LPN ( Learning parity with noise ) problem. LWE can be thought of as two sub-problems closely related to each other. Search LWE and Decision LWE . LWE is a powerful cryptography tool as its hardness is the same as lattice problems, i.e., shortest vector problem and closest vector problem.
Consider a matrix with n rows and m columns with uniform random entries from space of integers modulo q . let Z be a vector of length n with uniform random entries from the same space and let b be a vector of length m with entries drawn from \(\chi \) distribution. Compute s (all arithmetic operations are performed mod q )
\(a^TZ + b^T =s^T\)
In [ 40 ] the hardness of worst-case lattice issues was decreased from SVP to LWE problems, implying that if an algorithm can solve the LWE problem in an acceptable period, it can also solve the SVP problem. In [ 41 ] a significant improvement to the LWE problem by developing the ring-LWE (RLWE) problem was proposed, which leads to new applications. It was also proved that RLWE issues could be reduced to worst-case problems on ideal lattices, which polynomial-time quantum algorithms struggle to do. Another practical RLWE [ 42 ] to obtain an FHE scheme was proposed which, employs Gentry’s squashing and bootstrapping techniques. Polynomial-LWE (PLWE), a simpler variant of RLWE, was employed. PLWE can likewise be reduced to worst-case scenarios like SVP on ideal lattices. To reduce the noise growth concerning each operation, Brakerski, Gentry, and Vaikuntanathan introduced a leveled homomorphic encryption approach [ 43 ]. The growth of the noise is linear in contrast with the multiplicative depth of the circuit. The scheme was based upon a modulus switching technique known as the BGV scheme. BGV scheme was also used with AES to perform homomorphically in [ 44 ], but it requires different versions of public key, thus requiring a large amount of memory machine. Brakerski proposed a new approach invariance, at Crypto 2012 for leveled for leveled homomorphic encryption schemes. In contrast to modulus switching, ciphertext retains the same modulus throughout the homomorphic evaluation. As s result, just a single copy of the scale-invariant evaluation key must be maintained. In [ 46 ] Brakerski’s FHE scheme transformed from LWE to RLWE with detailed analysis of various subroutines, including multiplication, bootstrapping, and relinearization. No implementation of this scheme is available, but there is a proof-of-concept execution in computer algebra system which is used in [ 47 ]. In [ 48 ], a relinearization technique was introduced that obtains a SWHE without requiring hardness assumption on ideals. A dimensional-modulus reduction was also presented with the goal of converting SWHE to FHE without using the squashing and SSSP . Other schemes are based upon Learning with Error problem . In previous LWE schemes multiplication step was complicated and expensive due to relinearization but in [ 49 ] author suggested a novel approach for FHE, i.e., approximate eigenvector method. All addition and matrix operations in this approach are through matrices resulting in an asymptotically faster approach and easier to understand. The relinearization step was eliminated, and matrices were added and multiplied simply.
NTRU-based FHE scheme
NTRU-based encryption is an old encryption technique proposed by [ 50 ] in 1998. NTRU was the earliest encryption attempt on lattice problems. In [ 51 ] author uses on-the-fly MPC in which each user is involved in sending encrypted data to the cloud and decrypting, i.e., when outputs are received. A new type of encryption was used, i.e., multikey FHE with the capability of operating on inputs that are encrypted under multiple different and unrelated keys. The multikey FHE scheme was based upon NTRU, an efficient public-key encryption scheme. Although initially, NTRU was not fully homomorphic, transforming it into fully homomorphic reduces its efficiency but increases its capability. However, an additional assumption related to public key uniformity is needed, known as decisional small polynomial ratio (DSPR) assumption. This additional assumption is avoided by Stehle and Steinfield [ 52 ] and a secured FHE scheme was proposed [ 53 ] under RLWE with circular security assumptions only. A FHE technique was proposed based on the power-of-prime cyclotomic [ 54 ] ring. The method is based on the RLWE assumption does not need the use of the DSPR (decision small polynomial ratio) assumption. The approach’s efficacy leads to improved noise control, resulting in improved ciphertext storage, computation, and communication. In table 3 , important FHE schemes based on their category and hard problem used are classified.
Homomorphic encryption libraries
Research in HE has resulted in effective, freely accessible HE libraries and software. Custom implementations require a high level of programming and cryptography skill since noise should be carefully controlled to preserve accuracy upon decryption, and security settings must be explicitly specified. Table 4 gives an overview of the implementations, including the software’s name, inventor, language, license, and a brief synopsis of the schemes implemented.
This section covers all homomorphic approaches beginning from PHE followed by SHE and FHE approaches. All these approaches based upon various factors like hard problems, nature of homomorphism are compared. FHE systems are also categorized, and they have improved and changed through time. Finally, the technique and programming language utilised in HE-implemented libraries are compared. The publications on homomorphic encryption that are explicitly focused on healthcare data are explored in the next section.
In the healthcare industry, patient health records are referred to as Electronic health records (EHR), a digital record of a patient’s medical history kept by hospitals or health care providers. It includes clinical data, demographics, medical history, and medical reports. Electronic health records (EHRs) are official health information records generated by any healthcare provider. Digitizing patients’ health care information is likely to improve the quality of care and effectiveness and reduce costs. It also facilitate the access of patients’ healthcare records whenever and wherever possible. The main goal of EHR’s is to reduce the communication gap between health care providers for a better quality cure and that too with reduced costs. However, Electronic health records (EHRs) contain a large amount of sensitive data, which is not only accessible to the doctor but also accessible to several different sources like insurance companies and staff members, so effective management of electronic health records is essential for concerns related to data security. The three fundamental and main goals of security is (CIA), i.e., Confidentiality, Integrity, and availability.
Confidentiality: Only an authorized person should have access to the information.
Integrity: Information should be correct, and an unauthorized person should not alter it.
Availability: Information should be accessible, available, and usable at any time but only by an authorized entity.
A shared EHR comprises a complex and challenging layout of sensitive data, including laboratory tests, patient demographic information, medical history, radiology records like ECG, X-RAYS, and CTs. There is a requirement for a complete secured model that should meet the terms and conditions of legal and regulatory bodies. A secure model ensures access to sensitive information limited only to those entities who have a justifiable need-to-know privilege assigned by the patient. Sometimes, a patient chooses to deliberately hide his health information related to an HIV/AIDS treatment unless and until a specific treatment alternative is included. Therefore, it is necessary to have a simple, reliable, efficient, and secure mechanism in which patients can quickly authorize the number of medical affiliates for accessing their full or partial sensitive information. There are various techniques for data protection, including pseudonymisation and anonymization. Both of these techniques can be used to protect the individual’s health record.
Anonymisation is the processing of data to prevent identifying the person to whom it belongs permanently. Anonymized data never allow the identification of an individual to whom it belongs. It is not even possible that any person could be known from the data by any advanced processing of the data. On the other hand, Pseudonymisation replaces any identifiable characteristics of data with a pseudonym. The only difference between pseudonymization and anonymization techniques is that it is possible that an individual can be identified by analyzing the related data in pseudonymization. In various cases, it is not possible to use an anonymization technique either because of the nature of data perspective. Pseudonymized data are very much suitable for processing and analyzing. However, anonymizing data while maintaining its value is a complex undertaking due to the inclusion of quasi-identifier components other than direct identifiers (e.g., name, address) that may be used alone or in conjunction with other data to re-identify it. The most common problems associated with Electronic health records are privacy, security, and confidentiality. Privacy of digital health records can be achieved in three different ways: Acquisition , Storage and Computation . Although first two are achievable, but the third condition, i.e. computation, also needs to be addressed to get complete privacy. There exists no system to enable processing in the cloud with privacy. FHE permits computation on encrypted data in the cloud. Various approaches satisfy homomorphic property on medical data. Multiple approaches are studied from 2009 till 2021 and focused on preserving patient privacy using homomorphic encryption. All of these approaches will be presented in the remaining parts of this section.
A decentralized system was proposed in [ 71 ] that authenticate users using verifiable attributes while maintaining attribute and identity privacy. Furthermore, an authentication system was designed with progressive privacy constraints in diverse interactions among involved entities. In [ 72 ]author has described a cloud-based approach using FHE to review ECG. Authors formulated FHE as the core of this idea and identified challenges to make it possible for ECG-Monitoring. Data obtained from THEW [ 73 ] standard ECG database that contains data of 24 hrs and took average heart rate calculation. Acquisition devices are capable of transferring data in AES format wirelessly. Encrypted data will only be stored in the cloud. However, to operate on some of the data, AES encrypted data first must be converted into FHE encrypted format. AES to FHE conversion done by the method described in [ 44 ]. Implementation was done with two algorithms one was gentry’s original [ 3 ] FHE scheme, and the other was BGV [ 43 ] scheme. In gentry scheme, recryption operation was costly and took \(99.9 \%\) more time than homomorphic addition and multiplication. In BGV implementation, recrypt operation is avoided by defining multiplicative depth.
In [ 74 ], author presented an approach that predicts heart attack probability based upon few body measurements. They use a client application that collects health data and sends it in encrypted form and used Microsoft Windows Azure cloud service. A practical variant of a homomorphic encryption scheme was used. The method works with a ring where n is a power of 2, implying that polynomials with integer coefficients of degree less than N are the objects.
R = \(\frac{\mathbb {Z}[\,X\,]}{X^n+1}\)
Specifically plaintexts as well as ciphertext are all polynomials. An element \(x \in R\) has the form
\(x= \sum _{i=0}^{n-1}x_iX^i\) , \(x_i \in \mathbb {Z}.\)
Key generation and encryption process uses two probability distributions \(\chi _{key}\) and \(\chi _{err}\) on R , where \(\chi _{key}\) is used in key generation, i.e. uniformly distributed over polynomials with {-1,0,1} as coefficients in.
KeyGen \((N,q,t,\chi _{key},\chi _{err})\) : With degree N and modulus q and t this algorithm samples small polynomials f ’, g \(\leftarrow \) \(\chi _{key}\) and sets \(f=[1+tf\) ’ \(]_q\) if f is inverted modulo it computes \(f^{-1}\) of f \(\in \) R , otherwise it chooses new f ’ and set \(h=[tgf^{-1}]_q\) and output public and private key pair as \((p_k,s_k)\) =( h , k ) \(\in \) \(R^2\) .
Encryption ( h , m ): It samples small error polynomials \(s,e \leftarrow \chi _{err}\) . Cipher text generated is
\(c=[\lfloor {\frac{q}{t}\rfloor } [m]_t + e + hs]_q\) \(\in \) R
Decryption ( f , c ): With ciphertext c and private decryption key f , message m can be computed using decryption algorithm as:
\(m=[\lfloor \frac{t}{q}\cdot [fc]_q\rceil ]_t\)
In [ 75 ], FHE encrypted ECG data are uploaded from a patient to the cloud for detecting LQTC (Long QT Syndrome). Cloud will receive two values, QT and RR. These values are encrypted homomorphically at the patient’s end. Initially, recordings are taken from THEW database [ 73 ], and then patient \(QT_c\) is computed homomorphically as
\(QT_c = \frac{QT}{\sqrt{\frac{RR}{sec}}}\)
\(QT_c\) values are then compared with threshold value of 500 ms .
\(f(QT,RR)=[QT^3 > (500)^3 (RR/sec)]\) .
After converting this equation into matrix, its performance is evaluated by comparing the Naive and Matrix approach results and found that the matrix approach is consistently more efficient than naive approach by a factor of 20. As in the naive approach, the depth of computation is higher, and cost increases with depth.
A secure computation [ 76 ] in personalized medicine using Paillier cryptosystem [ 15 ] was proposed, which allows a personal mobile device with sensitive data to compute tests (e.g., Warfarin dosage) while keeping personal data and test specifics private. Details of a partial implementation of this protocol were also revealed. In [ 77 ] author used the BGV [ 43 ] scheme and its practical implementation HElib [ 55 ] for calculating average heart rate, calculation of minimum and maximum heart rate, and detection of LQTS (Long QT Syndrome). As BGV scheme uses leveled FHE which eliminates expensive recryption operation. Leveled FHE uses a better technique for handline noise, i.e., modulus switching . In this scheme, plain texts are represented as polynomial rings \(GF(p^d\) with p as a prime number, i.e., the range of polynomial coefficients and degree d of the polynomial. As plaint text are represented with polynomial rings which allow multiple message packing by partitioning them into independent slots [ 32 ] resulting into SIMD Single Instruction Multiple Data fashions.
The authors [ 78 ] developed evaluation techniques to compute securely over minor allele frequencies (MAF) and the \(\chi \) statistic in genome-wide association studies. It was also explained how to calculate the Hamming distance and Edit distance between encrypted DNA sequences safely. Finally, the performance of two widely used homomorphic encryption algorithms [ 44 ] and [ 53 ] were examined. Another approach [ 79 ] proposed a data division homomorphic encryption scheme in wireless sensor networks. The algorithm divides whole data into two or three parts for safer communication and data storage. Forwarding nodes within the network upload encrypted sensor data without the actual need of decrypting it. In a worse case, if the forwarding node is attacked, the attacker will not eavesdrop original data. The algorithm is divided into five phases: data preprocessing, encryption, data transfer, data fusion, and decryption. Consider D as the sensed data and N as a random integer. The data division scheme will divide the data into D / N , N . It is both additive and multiplicative homomorphic as shown in equation 1 and 2 .
\(m=D/N\) or \(m=n\) where \(m\in [0,M-1]\) where M is large integer
\(c=ENC(m,k,M)\) where e \(k\in [0,M-1]\)
In the Data Transfer phase, encapsulation of packets take place with \(\{E(D/N),k\}\) or \(\{E(N),k\}\) , packets are then sent to forwarding nodes randomly and finally forwarding nodes stores and uploads the packet on the server. In the Data fusion phase integrity of the data is verified, based upon the number of packets received, i.e 2 for multiplication and 3 for addition central server fusion node fuse them with multiplication and addition and finally, in decryption phase central server, after fusion decrypt the data with Dec ( c , k , M ).
Multiplicative homomorphism: due to homomorphism E ( D ) is the final result as:
Additive homomorphism: due to homomorphism \(E2(D+M)\)
In [ 80 ], author proposed a fully homomorphic encryption algorithm for encrypting and decrypting medical images. It uses DICOM as the input image. They analyzed keyspace analysis, correlation analysis, histogram analysis, key sensitivity analysis, PSNR , MSE and noise analysis. The author divided the whole process into fifteen steps. They used a probabilistic algorithm for a key generation as well as for encryption described in, and a deterministic algorithm for decryption [ 81 ]. This scheme supports unlimited additions (Eq. 4 ) and limited multiplications (Eq. 5 ) and uses a probabilistic algorithm for a key generation as well as for encryption and a deterministic algorithm for decryption. Perfect encrypted image results into uniform distributed histogram image according to histogram analysis of image pixel distribution was uniform. Larger PSNR values were identified, and in correlation analysis between two adjacent pixels, it was concluded that the algorithm provides good security. In key space analysis, \(150-bit\) size key is considered, which has total \(2^{150}\) values. Key size is sufficient, which is not affected by brute force attacks.
Homomorphic property:
\(M_1\) and \(M_2\) are plain texts and \(C_1\) and \(C_2\) ( equation 3 ) as respective ciphertexts. Parameter \(S_1\) and \(S_2\) are two small positive integers and \(B_1\) and \(B_2\) are big random positive integers. P and Q be two big prime numbers with \(P>>Q\) .
where a is any random number under P
Multiplicative Homomorphism:
Additive homomorphism:
Another approach [ 82 ] performs privacy-preserving linkage of records in healthcare sectors. A secondary contribution of this research is the creation of an API for the El-Gamal cryptosystem [ 11 ] that enables for the use of the cryptosystem’s multiplicative homomorphic feature. In [ 83 ] a secure privacy-preserving data aggregation technique was developed using a Bi-linear ElGamal cryptosystem and aggregate signature. According to security analysis, the proposed system protects data confidentiality, authenticity, and privacy while also resisting passive eavesdropping and replay assaults from malicious adversaries. Because of the use of privacy homomorphism, this approach can be implemented in a cloud-assisted Wireless Body Area Network (WBAN). The [ 84 ] solution is built on the hybrid framework Chimera, which allows migration between distinct families of fully homomorphic schemes TFHE [ 58 ] and HEAAN [ 57 ]. It was the only bootstrapped solution in idash 2018 competition that may be used for a variety of parameters without requiring a recryption of the genomic database
In [ 85 ] author proposed and implemented an optimized NTRU-based homomorphic encryption scheme resulting in much slower growth of noise. The encryption scheme includes d as degree of number field, modulus q , \( \sigma _k\) and \(\sigma _c\) is standard deviation of discrete Gaussian error distribution in key and ciphertext space, \(\lambda \) is the security level that can be 80 or 128 bits. There is a bit decomposition function BD () BD( integer ) takes a \(l-\) bit integer and output bit decomposition of integer as a row vector of size l . BD ( polynomial ) with input as n being polynomial size with l bit integer as each coefficient and outputs l \(\times \) n . BD( MatrixofPolynomials ) with input as polynomial matrix of size x \(\times \) y and outputs a matrix of size x \(\times \) yl . There is also bit decompose inverse function BDI which is an inverse of BD .
KeyGen \((1^\lambda )\) : consider two polynomials \(f_{1 \times 1},g_{1 \times 1} \leftarrow D_{\mathbb {Z}^n, \sigma _k}\) with condition f is invertible in ring \(R_q\) and f \(\equiv \) 1( mod 2). Public key \(p_k\) and secret key \(s_k\) can be computed as:
Enc \((p_k,m)\) : \(R_q\) is the message space and \(\mu \in R_q\)
\(C_{l \times 1}=\mu \cdot BDI(I_{l \times l}) + S_{l \times 1} \cdot h_{1 \times 1} + E_{l \times 1}\) , with \(S_{l \times 1}, E_{l \times 1} \leftarrow D_{R_q^{l \times 1},\sigma _c}\)
Dec \((s_k, C)\) :
Decrypted ciphertext can be reformulated as \(l \times 1\) polynomial vectors (Eq. 6 ) like \(\mu f, 2\mu f,\cdot \cdot \cdot \cdot , 2^{l-1}\mu f\) along with some error vector. In [ 86 ] author uses the medical cyber-physical system to target remote health monitoring system for patients that sends ECG data from patient’s home to the cloud. Patient data is encrypted using Paillier [ 15 ] and BGV [ 43 ] scheme. Paillier scheme is used to detect Average heart rate as it is only additive homomorphic, but BGV is used to detect LTQS (Long QT syndrome). THEW [ 73 ] (which is 24 − hour anonymized ECG recordings of real patients), with a sampling rate of 1000 Hz. 128-bit security for recommending encrypted data was used. LQTS implementation was compared based on bit-length of toc values in the dataset. Encryption and Decryption time using both Paillier and BGV is almost the same, but when it comes to evaluation Paillier becomes 3100 \(\times \) faster. However, Paillier is a partial homomorphic scheme, i.e., only additive homomorphic. In [ 87 ] author proposed a four-layer architecture of the mobile health network, including wearable area, pre-processing area, cloud server area, and physical diagnosis area, followed by safe average heart rate calculation, long QT syndrome, and chi-square detection. Dowlin’s protocol is used to determine the average heart rate and long QT syndrome and uses chi-square tests to check the relation between varicose veins and overweight patients. Dowlin FHE scheme [ 88 ] consists of:
n as security parameter = \(2^k\) where k \(\in \) , q is large prime number with \(q mod n \equiv 1 \) , t is small plain text modulus where \(1<t<q \) , \(\chi _{key}\) and \(\chi _{err}\) are randomly chosen from \(\overline{\psi \beta }\) , params=(n,q,t, \(\chi _{key}\) and \(\chi _{err}\) )
KeyGen(params) keygeneration sample polynomial f ’ g \(\leftarrow \) \(\chi _{key}\)
\(f=[1+tf\) ’ \(]_q\) if f is inverted modulo it computes \(f^{-1}\) of f in \(R_q\) , otherwise it chooses new f ’.
Generate vectors e and s \(\in \) \(R^l\) randomly, in which every component selected from \(\chi _{err}\) .
\(\gamma \) = \([Powersof2(f)+e+hs]_q\)
\(h=[tgf^{-1}]_q\) public key \(p_k=h\) , secret key \( s_k=f\) and evaluation key \(ev_k\) = \(\gamma \)
Enc \((p_k,m \in R_t)\) :
\(c=[\lfloor q/t \rfloor m +e_2 +hs_2]_q\)
Dec \((s_k,c)\) :
\(m=[\lfloor t/q \cdot [fc]_q \rceil ]_q\) .
In [ 89 ], author demonstrated efficient use of homomorphic encryption for computing aggregate queries on ciphertext and also provides confidentiality of aggregate-level data from i 2 b 2 data model. A privacy-preserving data sharing approach based upon El Gamal cryptosystem [ 11 ] which is additive homomorphic. It includes three phases, first is Initialization Phase to generate public and private keys for EL Gamal Cryptosystem followed by ETL Phase for encrypting i2b2 aggregate-level. After that, there is a Querying Phase . A query can be generated after, the encrypted data are stored on the storage server. With every query fresh temporary pair of keys are generated. After receiving the query, the server fetches the records encrypted under the public key and uses the crypto engine for homomorphically aggregating them. It also includes an interactive two-party encryption protocol with a proxy server for switching encryption of results. In [ 90 ], a SafeBioMetrics system architecture was proposed that enables secure cloud storage and processing of medical data using BGV [ 43 ] fully homomorphic encryption scheme. The Polar H7 device was applied as an experimental population sample to 45 individuals, and additionally dataset of 500 patients was used to detect DRHS (Delayed Polarization of Heart Syndrome) medical condition. Another i2b2 data privacy and security approach were proposed [ 91 ]. Privacy solution is integrated on top of the i2b2 framework using homomorphic encryption and differential privacy. Proposed solution was based upon Fan and Vercauteren cryptosystem [ 46 ], which is lattice based leveled homomorphic scheme with RLWE (Ring Learning with errors) enabling privacy based queries on the genomic data. The implementation of genomic cohorts in a real-world scenario took place at a hospital. Performance was evaluated with 707 MB of data that includes nearly 18.5 crore genotypes with each genotype of 4 bytes. The BGN [ 23 ] homomorphic cryptosystem has been used [ 92 ] as a cloud-based online medical prediagnosis approach that is both efficient and private. It enables the system’s online prediagnosis function, which may instantly be executed on the ciphertext. In [ 93 ], a medical encryption algorithm was proposed based upon elliptic curve cryptography combined with homomorphic encryption. Traditional ECC was expensive due to inversion operation, which is ignored in its improved version. The effectiveness of the algorithm was verified upon two medical images which show better keyspace and higher key sensitivity.
In [ 94 ], a privacy-preserving query model system was proposed, and put into use in a real-world medical side effect inquiry system. To reduce the size of database, a filtering technique was applied before query model deployment. Multi-threading was used for fast searching. The effectiveness of the approach was verified 10,000 times with a random query, using a database including 40,000 records of simulation data. Nearly about 99% of the queries are completed within 60 s. In [ 95 ], homomorphic encryption by Fan and Vercauteren [ 46 ] was implemented using R language on a simulated dataset of 5000 cancer patients with a security level of 128 bit. Identification of exceptional survivors is made with the identification of total drug exposure.
In [ 96 ] study adds security mechanisms into the architecture of a patient-oriented edge-cloud-based healthcare system. For secure processing and filtering of insensitive data processing in the edge layer, an edge-level additive homomorphic encryption is presented. In [ 97 ], using contrast-enhancement RDH and homomorphic encryption, a safe and high-visual-quality framework for medical pictures was created. The proposed algorithm was homomorphic encryption based upon a chaotic map. It was a partial homomorphic scheme with the additive homomorphic property. The correlation between encrypted and marked photos is found to be lower, as well as the unpredictability in encrypted images is fairly high. It implies that the proposed encryption approach can enhance image security by safeguarding image content. In [ 98 ], proposed a computational model and developed an algorithm for contract tracing with COVID-19 pandemic. The proposed algorithm was simulated using ElGamal [ 11 ] encryption algorithm. Simulation was done using a synthetic spatiotemporal geolocation dataset. It was generated with timestamped locations. It consists of all location-oriented information for more than 24 h. It also includes ten COVID-19 positive patients and one querying person. It covers region \(400\,Km^2\) within 24 hrs duration. Threshold distance of 2 m and Threshold time duration of 15 min with a threshold time difference of 12 h. According to simulation findings, the proposed approach effectively ensures security while also meeting the computing requirements for contact tracing. MHE allows for flexible, secure processing by seamlessly switching between HE-encrypted local computation and interactive protocols (SMC). It can be used to determine the most efficient strategy for each phase in a workflow, making use of one technique’s features to avoid the bottlenecks of the other. A self-serviced medical diagnosis system based upon homomorphic encryption (HE) and privacy-preserving access control was described [ 99 ], which may protect patient medical health data while keeping hospital diagnosis mode secret. Following a thorough security investigation, it was discovered that the scheme could withstand a variety of known security risks. To [ 100 ] handle medical data privacy problems in smart health, the author tackled two major issues in the adversarial model. First, it created Derepo to decentralize access control and encryption of data without losing computability. Static structures and dynamic processes are formalized as part of the double-layered architecture. Internal and external adversaries pose privacy problems. Thus the FHE method is employed to maintain secrecy and handle them. The author classifies data-sharing models into three groups and examines the major technical difficulties faced. Medical sites (i.e., data providers) that are willing to share data must pool their individual-level patient data into a single repository under the centralized approach. Unlike the centralized data-sharing approach, the decentralized model does not necessitate the physical transfer of patient-level data from medical locations’ IT infrastructure. For calculating average heart rate, computing minimum and maximum heart rates, and detecting LQTS, the author [ 101 ] employed the BGV [ 43 ] scheme and its practical implementation HElib [ 55 ]. Because the BGV system employs leveled FHE, it avoids the need for a costly recryption procedure. For handline noise, leveled FHE employs a better technique known as modulus switching. Numerous ways that are primarily concerned with the privacy of healthcare data using Homomorphic Encryption are compared in (Table 5 and Table 6 ), and it was determined that, despite performance concerns owing to large computation, homomorphic encryption is feasible and important for preserving patient data privacy. In [ 102 ], authors introduced a FAMHE scheme, which is a federated analytics system based on multiparity homomorphic encryption that integrates the strength of HE for executing computations on encrypted data without requiring communication between the parties. Safe computing and learning involve combining federated learning approaches with cryptographic frameworks. The technique was demonstrated to provide stringent privacy protection, but the accuracy of the approach was sacrificed in favor of performance. In [ 103 ], authors proposed two schemes CTHE ( Carmichael’s Theorem-based Homomorphic Encryption) and MEHE (Modified Enhanced Homomorphic Encryption ) . The hardness of integer factorization, the discrete logarithmic approach, and quadratic residuosity were employed in both techniques. It also makes use of modulus switching to decrease noise. Although the overall number of computations in MEHE was not decreased, the approach is still superior since it decreases noise without impacting security. In [ 104 ], authors presented a privacy-preserving framework CFHET-PPF. It combines three FHE approaches resulting in the prevention of false data injection. It is presented as a way to make it easier for fog nodes to categorize shared data based on illness risks, which is necessary for health data analysis. Because it prevents irrelevant computing during the transmission of sensitive data disseminated in the fog computing environment, it reduces encrypting time.
Privacy of data is essential than ever before in this internet world. Outsourcing applications are in high demand due to the cloud computing revolution. Clients use the service by uploading their data to the cloud, which is then evaluated to get a result. It benefits the consumer and exposes critical data to third-party service providers. Although data are encrypted, the difficulty with encrypted data is that it must be decrypted before being used. As a result of decrypting, it becomes vulnerable to all the things that were trying to secure it. Homomorphic encryption, which processes data while maintaining privacy and security, maybe the greatest solution for this problem in the future. The concept of HE has been around for more than three decades, but rapid development in the subject of fully homomorphic encryption advanced the field swiftly from Gentry’s innovative research to today’s efficient implementations. Digitizing a patient’s medical records is anticipated to increase the quality and effectiveness of care while also lowering expenses. However, because electronic health records (EHRs) include a vast quantity of sensitive data available not just to doctors but also to a range of other sources such as insurance companies and staff members. EHR administration is essential for data security issues. As a result, we surveyed and compared the HE and FHE schemes in this paper. Initially going with the fundamentals of HE, the concepts of Partial Homomorphic Encryption (PHE) and Somewhat Homomorphic Encryption (SHE) were examined, which are prime aspects in achieving Fully Homomorphic Encryption, followed by FHE. FHE approaches were divided into four distinct groups, and significant approaches in each group were compared. Finally, in the domains of healthcare and bioinformatics, HE techniques were retrieved and compared for securely identifying LQTC, cancer, average heart rate, cardiovascular problems, and a secure query generating system in healthcare. Overall, homomorphic encryption will be a boon to the healthcare business as the performance and utility of FHE improve.
Healthcare-Cloud computing Market. https://www.acumenresearchandconsulting.com/healthcare-cloud-computing-market . Accessed 1st May 2021
Kitchenham Barbara (2004) Procedures for performing systematic reviews. Keele, UK, Keele University 33(2004):1–26
Craig Gentry (2009) Fully homomorphic encryption using ideal lattices. In: Proceedings of the forty-first annual ACM symposium on Theory of computing, pp. 169–178
Craig Gentry (2009) A fully homomorphic encryption scheme. PhD thesis, Stanford University. www.crypto.stanford.edu/craig
Zhigang C, Gang H, Mengce Z, Xinxia S, Liqun C (2021) Bibliometrics of machine learning research using homomorphic encryption. Mathematics 9:2792, 11
Act A (1996) Health insurance portability and accountability act of 1996. Public Law 104:191
Google Scholar
US Congress (2009) Health information technology for economic and clinical health (hitech) act, title xiii of division a and title iv of division b of the American recovery and reinvestment act of 2009 (arra)
Ronald L. Rivest, Len Adleman, and Michael L. Dertouzos. On data banks and privacy homomorphisms. pages 165–179
Shaft G, Silvio M (1982) Probabilistic encryption & how to play mental poker keeping secret all partial information. In: Proceedings of the annual ACM symposium on theory of computing, pp 365–377
Kaliski B (2005) Quadratic Residuosity problem. Springer, Boston, MA, p 493
Elgamal T (1985) A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans Inf Theory 31(4):469–472
Article MathSciNet MATH Google Scholar
Diffie W, Hellman M (1976) New directions in cryptography. IEEE Trans Inf Theory 22(6):644–654
Josh B. Dense probabilistic encryption. In Proceedings of the workshop on selected areas of cryptography , pp 120–128
Yuliang Z, Tsutomu M, Hideki I Cryptographic applications of 7th-residuosity problem with 7 an odd integer
Pascal P (1999) Public-key cryptosystems based on composite degree residuosity classes. In Jacques S (ed), Advances in Cryptology — EUROCRYPT ’99, pages 223–238. Springer Berlin
Tatsuaki O, Shigenori U (1998) A new public-key cryptosystem as secure as factoring. In: International conference on the theory and applications of cryptographic techniques, pp 308–318. Springer
David N, Jacques S (1998) A new public key cryptosystem based on higher residues. In: Proceedings of the 5th ACM conference on computer and communications security, pp 59–66
Ivan D, Mads J (2001) A generalisation, a simpli. cation and some applications of paillier’s probabilistic public-key system. In International workshop on public key cryptography, pp 119–136. Springer, New York
Akinori K, Keisuke T, Keita X (2007) Multi-bit cryptosystems based on lattice problems. In: International Workshop on Public Key Cryptography, pp 315–329. Springer, New York
Steven DG (2002) Elliptic curve paillier schemes. J Cryptol 15(2):129–138
R[onald] LR, Adi S, Leonard MA () A method for obtaining digital signatures and public-key cryptosystems. CACM 26(1):96–99
Andrew CY (1982) Protocols for secure computations. In: 23rd annual symposium on foundations of computer science (sfcs 1982), pp 160–164. IEEE
Dan B, Eu-Jin G, Kobbi N (2005) Evaluating 2-dnf formulas on ciphertexts. In: Theory of cryptography conference , pp 325–341. Springer, New York
Yuval I, Anat P (2007) Evaluating branching programs on encrypted data. In Theory of Cryptography Conference , pp 575–594. Springer, New York
Michael F, Neal K (1994) Combinatorial cryptosystems galore! Contemp Math 168:51
Tomas Sander, Adam Young, and Moti Yung. Non-interactive cryptocomputing for nc1. In Proceedings of the 40th Annual Symposium on Foundations of Computer Science , FOCS ’99, page 554, USA, 1999. IEEE Computer Society
Kristian Gjøsteen. Subgroup membership problems and public key cryptosystems. 2004
Jeffrey Hoffstein, Jill Pipher, Joseph H Silverman, and Joseph H Silverman. An introduction to mathematical cryptography , volume 1. Springer, 2008
Craig G, Shai H (2011) Fully homomorphic encryption without squashing using depth-3 arithmetic circuits. In: 2011 IEEE 52nd annual symposium on foundations of computer science, pp 107–109. IEEE
Dan B (1998) The decision diffie-hellman problem. In: International algorithmic number theory symposium, pp 48–63. Springer, New York
Peikert C (2016) A decade of lattice cryptography. Found Trends Theor Comput Sci 10(4):283–424
Nigel PS, Frederik V (2014) Fully homomorphic simd operations. Des Codes Cryptogr 71(1):57–81
Marten Van D, Craig G, Shai H, Vinod V (2010) Fully homomorphic encryption over the integers. In: Annual international conference on the theory and applications of cryptographic techniques , pages 24–43. Springer, New York
Steven DG, Shishay WG, Sean M (2016) Algorithms for the approximate common divisor problem. LMS J Comput Math 19(A):58–72
Jung Hee Cheon, Jean-Sébastien Coron, Jinsu Kim, Moon Sung Lee, Tancrede Lepoint, Mehdi Tibouchi, and Aaram Yun. Batch fully homomorphic encryption over the integers. In Annual International Conference on the Theory and Applications of Cryptographic Techniques , pages 315–335. Springer, 2013
Jean-Sébastien Coron, Tancrede Lepoint, and Mehdi Tibouchi. Scale-invariant fully homomorphic encryption over the integers. In International Workshop on Public Key Cryptography , pages 311–328. Springer, 2014
Y Govinda Ramaiah and G Vijaya Kumari. Efficient public key homomorphic encryption over integer plaintexts. In 2012 International Conference on Information Security and Intelligent Control , pages 123–128. IEEE, 2012
Nitesh Aggarwal, CP Gupta, and Iti Sharma. Fully homomorphic symmetric scheme without bootstrapping. In Proceedings of 2014 International Conference on Cloud Computing and Internet of Things , pages 14–17. IEEE, 2014
Pedro Silveira Pisa, Michel Abdalla, and Otto Carlos Muniz Bandeira Duarte. Somewhat homomorphic encryption scheme for arithmetic operations on large integers. In 2012 Global Information Infrastructure and Networking Symposium (GIIS) , pages 1–8. IEEE, 2012
Regev O (2009) On lattices, learning with errors, random linear codes, and cryptography. Journal of the ACM (JACM) 56(6):1–40
Vadim Lyubashevsky, Chris Peikert, and Oded Regev. On ideal lattices and learning with errors over rings. In Annual International Conference on the Theory and Applications of Cryptographic Techniques , pages 1–23. Springer, 2010
Zvika Brakerski and Vinod Vaikuntanathan. Fully homomorphic encryption from ring-lwe and security for key dependent messages. In Annual cryptology conference , pages 505–524. Springer, 2011
Brakerski Z, Gentry C, Vaikuntanathan V (2014) (leveled) fully homomorphic encryption without bootstrapping. ACM Transactions on Computation Theory (TOCT) 6(3):1–36
Craig Gentry, Shai Halevi, and Nigel P Smart. Homomorphic evaluation of the aes circuit. In Annual Cryptology Conference , pages 850–867. Springer, 2012
Zvika Brakerski. Fully homomorphic encryption without modulus switching from classical gapsvp. In Annual Cryptology Conference , pages 868–886. Springer, 2012
Fan J, Vercauteren F (2012) Somewhat practical fully homomorphic encryption. IACR Cryptol. ePrint Arch. 2012:144
Thore Graepel, Kristin Lauter, and Michael Naehrig. Ml confidential: Machine learning on encrypted data. In International Conference on Information Security and Cryptology , pages 1–21. Springer, 2012
Brakerski Z, Vaikuntanathan V (2014) Efficient fully homomorphic encryption from (standard) lwe. SIAM J Comput 43(2):831–871
Craig Gentry, Amit Sahai, and Brent Waters. Homomorphic encryption from learning with errors: Conceptually-simpler, asymptotically-faster, attribute-based. In Annual Cryptology Conference , pages 75–92. Springer, 2013
Jeffrey Hoffstein, Jill Pipher, and Joseph H Silverman. Ntru: A ring-based public key cryptosystem. In International Algorithmic Number Theory Symposium , pages 267–288. Springer, 1998
Adriana López-Alt, Eran Tromer, and Vinod Vaikuntanathan. On-the-fly multiparty computation on the cloud via multikey fully homomorphic encryption. In Proceedings of the forty-fourth annual ACM symposium on Theory of computing , pages 1219–1234, 2012
Damien Stehlé and Ron Steinfeld. Making ntru as secure as worst-case problems over ideal lattices. In Annual International Conference on the Theory and Applications of Cryptographic Techniques , pages 27–47. Springer, 2011
Joppe W Bos, Kristin Lauter, Jake Loftus, and Michael Naehrig. Improved security for a ring-based fully homomorphic encryption scheme. In IMA International Conference on Cryptography and Coding , pages 45–64. Springer, 2013
Qin X, Huang R, Fan H (2021) An effective NTRU-based fully homomorphic encryption scheme. Math Probl Eng 2021:1–9
S Halevi and V Shoup. Helib. url: https://github.com/shaih
Zvika B, Craig G, Vinod V (2011) Fully homomorphic encryption without bootstrapping. Cryptology ePrint Archive, Report 2011/277. https://eprint.iacr.org/2011/277
Jung Hee Cheon, Andrey Kim, Miran Kim, and Yongsoo Song. Homomorphic encryption for arithmetic of approximate numbers. In International Conference on the Theory and Application of Cryptology and Information Security , pages 409–437. Springer, 2017
Chillotti I, Gama N, Georgieva M (2019) and Malika Izabachène. Fast fully homomorphic encryption library, Tfhe
Ilaria Chillotti, Nicolas Gama, Mariya Georgieva, and Malika Izabachene. Faster fully homomorphic encryption: Bootstrapping in less than \(0.1\) seconds. In international conference on the theory and application of cryptology and information security , pages 3–33. Springer, 2016
Microsoft SEAL (release 3.6). https://github.com/Microsoft/SEAL, November 2020. Microsoft Research, Redmond, WA
“FHEW Library”. https://github.com/lducas/FHEW/, Accessed 21st May 2021
Léo Ducas and Daniele Micciancio. Fhew: bootstrapping homomorphic encryption in less than a second. In Annual International Conference on the Theory and Applications of Cryptographic Techniques , pages 617–640. Springer, 2015
HEAAN Software Library. Cryptolab inc. 2018. https://github.com/snucrypto/HEAAN Accessed 21st May 2021
“NTT based Fast Lattice library”. https://github.com/CryptoExperts/FV-NFLlib, Accessed 22nd May 2021
PALISADE Lattice Cryptography Library. https://github.com/holybao/PALISADE, Accessed 22nd May 2021
Cingulata Library. https://github.com/CEA-LIST/Cingulata#cingulata, Accessed 22nd May 2021
Lattigo: lattice-based multiparty homomorphic encryption library in Go. https://github.com/ldsec/lattigo, Accessed 23rd May 2021
Pyfhel: PYthon For Homomorphic Encryption Libraries. https://github.com/ibarrond/Pyfhel , Accessed 23rd May 2021
\(\wedge \) \(\circ \) \(\lambda \) :Functional Lattice Cryptography. https://github.com/cpeikert/Loll, Accessed 23rd May 2021
Pedro G. M. R. Alves and Diego F. Aranha. Efficient GPGPU implementation of the Leveled Fully Homomorphic Encryption scheme YASHE. Master’s thesis, Institute of Computing, University of Campinas, Brazil, 2016. (In Portuguese)
Guo L, Zhang C, Sun J, Fang Y (2014) A privacy-preserving attribute-based authentication system for mobile health networks. IEEE Trans Mob Comput 13(9):1927–1941
Article Google Scholar
Ovunc Kocabas, Tolga Soyata, Jean Philippe Couderc, Mehmet Aktas, Jean Xia, and Michael Huang. Assessment of cloud-based health monitoring using homomorphic encryption. 2013 IEEE 31st International Conference on Computer Design, ICCD 2013 , pages 443–446, 2013
Jean-Philippe Couderc. The telemetric and holter ecg warehouse initiative (thew): a data repository for the design, implementation and validation of ecg-related technologies. In 2010 Annual International Conference of the IEEE Engineering in Medicine and Biology , pages 6252–6255. IEEE, 2010
Bos JW, Lauter K, Naehrig M (2014) Private predictive analysis on encrypted medical data. J Biomed Inform 50(May):234–243
Alex Page, Ovunc Kocabas, Scott Ames, Muthuramakrishnan Venkitasubramaniam, and Tolga Soyata. Cloud-based secure health monitoring: Optimizing fully-homomorphic encryption for streaming algorithms. 2014 IEEE Globecom Workshops, GC Wkshps 2014 , pages 48–52, 2014
Mentari Djatmiko, Arik Friedman, Roksana Boreli, Felix Lawrence, Brian Thorne, and Stephen Hardy. Secure evaluation protocol for personalized medicine. In Proceedings of the 13th Workshop on Privacy in the Electronic Society , WPES ’14, page 159–162, New York, NY, USA, 2014. Association for Computing Machinery
Ovunc Kocabas and Tolga Soyata. Utilizing Homomorphic Encryption to Implement Secure and Private Medical Cloud Computing. Proceedings - 2015 IEEE 8th International Conference on Cloud Computing, CLOUD 2015 , pages 540–547, 2015
Miran Kim and Kristin Lauter. Private genome analysis through homomorphic encryption. In BMC medical informatics and decision making , volume 15, pages 1–12. BioMed Central, 2015
Wang X, Zhang Z (2015) Data Division Scheme Based on Homomorphic Encryption in WSNs for Health Care. J Med Syst 39(12):1–7
Vengadapurvaja AM, Nisha G, Aarthy R, Sasikaladevi N (2017) An Efficient Homomorphic Medical Image Encryption Algorithm for Cloud Storage Security. Procedia Computer Science 115:643–650
Lichun Li, Rongxing Lu, Kim-Kwang Raymond Choo, Anwitaman Datta, and Jun Shao. Privacy-preserving-outsourced association rule mining on vertically partitioned databases. IEEE Transactions on Information Forensics and Security , 11(8):1847–1861, 2016
Diptendu Mohan Kar, Ibrahim Lazrig, Indrajit Ray, and Indrakshi Ray. Poster: Priremat: A distributed tool for privacy preserving record linking in healthcare. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security , CCS ’17, page 2507–2509, New York, NY, USA, 2017. Association for Computing Machinery
Ara A, Al-Rodhaan M, Tian Y, Al-Dhelaan A (2017) A secure privacy-preserving data aggregation scheme based on bilinear elgamal cryptosystem for remote health monitoring systems. IEEE Access 5:12601–12617
Sergiu Carpov, Nicolas Gama, Mariya Georgieva, and Juan Ramon Troncoso-Pastoriza. Privacy-preserving semi-parallel logistic regression training with fully homomorphic encryption. BMC Medical Genomics , 13(7):1–10, 2020
Khedr A, Gulak G (2018) SecureMed: Secure Medical Computation Using GPU-Accelerated Homomorphic Encryption Scheme. IEEE J Biomed Health Inform 22(2):597–606
Kocabas O, Soyata T, Aktas MK (2016) Emerging Security Mechanisms for Medical Cyber Physical Systems. IEEE/ACM Trans Comput Biol Bioinf 13(3):401–416
Sun X, Zhang P, Sookhak M, Jianping Yu, Xie W (2017) Utilizing fully homomorphic encryption to implement secure medical computation in smart cities. Pers Ubiquit Comput 21(5):831–839
Dowlin N, Gilad-Bachrach R, Laine K, Lauter K, Naehrig M, Wernsing J (2017) Manual for using homomorphic encryption for bioinformatics. Proc IEEE 105(3):552–567
Jean Louis Raisaro, Jeffrey G Klann, Kavishwar B Wagholikar, Hossein Estiri, Jean-Pierre Hubaux, and Shawn N Murphy. Feasibility of homomorphic encryption for sharing i2b2 aggregate-level data in the cloud. AMIA Summits on Translational Science Proceedings , 2018:176, 2018
Bocu R, Costache C (2018) A homomorphic encryption-based system for securely managing personal health metrics data. IBM J Res Dev 62(1):1–10
Jean Louis Raisaro, Gwangbae Choi, Sylvain Pradervand, Raphael Colsenet, Nathalie Jacquemont, Nicolas Rosat, Vincent Mooser, and Jean-Pierre Hubaux. Protecting privacy and security of genomic data in i2b2 with homomorphic encryption and differential privacy. IEEE/ACM transactions on computational biology and bioinformatics , 15(5):1413–1426, 2018
Wei Guo, Jun Shao, Rongxing Lu, Yining Liu, and Ali A. Ghorbani. A privacy-preserving online medical prediagnosis scheme for cloud environment, 2018
Yin S, Liu J, Teng L (2019) Improved Elliptic Curve Cryptography with Homomorphic Encryption for Medical Image Encryption. 2019:1–6
Yusheng Jiang, Tamotsu Noguchi, Nobuyuki Kanno, Yoshiko Yasumura, Takuya Suzuki, Yu Ishimaki, and Hayato Yamana. A privacy-preserving query system using fully homomorphic encryption with real-world implementation for medicine-side effect search. ACM International Conference Proceeding Series , 2019
Paddock S, Abedtash H, Zummo J, Thomas S (2019) Proof-of-concept study: Homomorphically encrypted data can support real-time learning in personalized cancer medicine. BMC Med Inform Decis Mak 19(1):1–10
Ramaprabha Jayaram and S. Prabakaran. Onboard disease prediction and rehabilitation monitoring on secure edge-cloud integrated privacy preserving healthcare system. Egyptian Informatics Journal , 2020
Yang Y, Xiao X, Cai X, Zhang W (2019) A secure and high visual-quality framework for medical images by contrast-enhancement reversible data hiding and homomorphic encryption. IEEE Access 7:96900–96911
Koushik Sinha, Pratham Majumder, and Subhas K. Ghosh. Fully Homomorphic Encryption based Privacy-Preserving Data Acquisition and Computation for Contact Tracing. International Symposium on Advanced Networks and Telecommunication Systems, ANTS , 2020-Decem:3–8, 2020
Li D, Liao X, Xiang T, Jiahui W, Le J (2020) Privacy-preserving self-serviced medical diagnosis scheme based on secure multi-party computation. Computers & Security 90:101701
Yepeng Ding and Hiroyuki Sato. Derepo: A distributed privacy-preserving data repository with decentralized access control for smart health. In 2020 7th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2020 6th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom) , pages 29–35, 2020
Ovunc Kocabas and Tolga Soyata. Towards privacy-preserving medical cloud computing using homomorphic encryption. Enabling Real-Time Mobile Cloud Computing through Emerging Technologies , pages 213–246, 2015
David Froelicher, Juan R. Troncoso-Pastoriza, Jean Louis Raisaro, Michel A. Cuendet, Joao Sa Sousa, Hyunghoon Cho, Bonnie Berger, Jacques Fellay, and Jean-Pierre Hubaux. Truly privacy-preserving federated analytics for precision medicine with multiparty homomorphic encryption. Nature Communications , 12(1), October 2021
K. Anitha Kumari, Avinash Sharma, Chinmay Chakraborty, and M. Ananyaa. Preserving health care data security and privacy using carmichael’s theorem-based homomorphic encryption and modified enhanced homomorphic encryption schemes in edge computing systems. Big Data , 10(1):1–17, 2022. PMID: 34375143
Sendhil R, Amuthan A (2021) Contextual fully homomorphic encryption schemes-based privacy preserving framework for securing fog-assisted healthcare data exchanging applications. Int J Inf Technol 13(4):1545–1553
Doröz Y, Sunar B (2016) Flattening ntru for evaluation key free homomorphic encryption. Journal of Mathematical Cryptology 14(1):66–83
Download references
Author information
Authors and affiliations.
Department of Computer Science and Engineering, Punjabi University, Patiala, 147002, India
Kundan Munjal
AIT CSE, Chandigarh University, Gharuan, Mohali, 140413, India
Department of Computer Science, Punjabi University, Patiala, 147002, India
Rekha Bhatia
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Kundan Munjal .
Ethics declarations
Conflict of interest.
On behalf of all authors, the corresponding author states that there is no conflict of interest.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Munjal, K., Bhatia, R. A systematic review of homomorphic encryption and its contributions in healthcare industry. Complex Intell. Syst. 9 , 3759–3786 (2023). https://doi.org/10.1007/s40747-022-00756-z
Download citation
Received : 08 July 2021
Accepted : 15 April 2022
Published : 03 May 2022
Issue Date : August 2023
DOI : https://doi.org/10.1007/s40747-022-00756-z
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Fully Homomorphic Encryption
- Health Informatics
- Secure Learning
- Find a journal
- Publish with us
- Track your research
Help | Advanced Search
Computer Science > Cryptography and Security
Title: large language models for blockchain security: a systematic literature review.
Abstract: Large Language Models (LLMs) have emerged as powerful tools in various domains involving blockchain security (BS). Several recent studies are exploring LLMs applied to BS. However, there remains a gap in our understanding regarding the full scope of applications, impacts, and potential constraints of LLMs on blockchain security. To fill this gap, we conduct a literature review on LLM4BS. As the first review of LLM's application on blockchain security, our study aims to comprehensively analyze existing research and elucidate how LLMs contribute to enhancing the security of blockchain systems. Through a thorough examination of scholarly works, we delve into the integration of LLMs into various aspects of blockchain security. We explore the mechanisms through which LLMs can bolster blockchain security, including their applications in smart contract auditing, identity verification, anomaly detection, vulnerable repair, and so on. Furthermore, we critically assess the challenges and limitations associated with leveraging LLMs for blockchain security, considering factors such as scalability, privacy concerns, and adversarial attacks. Our review sheds light on the opportunities and potential risks inherent in this convergence, providing valuable insights for researchers, practitioners, and policymakers alike.
Submission history
Access paper:.
- Download PDF
- HTML (experimental)
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
BibTeX formatted citation
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
Microsoft Research Blog
Research focus: week of march 18, 2024.
Published March 20, 2024
Share this page
- Share on Facebook
- Share on Twitter
- Share on LinkedIn
- Share on Reddit
- Subscribe to our RSS feed
Welcome to Research Focus, a series of blog posts that highlights notable publications, events, code/datasets, new hires and other milestones from across the research community at Microsoft.

NEW RESEARCH
Fewer is more: boosting llm reasoning with reinforced context pruning.
Large language models (LLMs) have shown impressive capabilities, yet they still struggle with math reasoning. In a recent paper: Fewer is More: Boosting LLM Reasoning with Reinforced Context Pruning , researchers from Microsoft propose CoT-Influx, a novel approach that pushes the boundary of few-shot chain-of-Thought (CoT) learning to improve LLM mathematical reasoning.
Given that adding more concise CoT examples in the prompt can improve LLM reasoning performance, CoT-Influx employs a coarse-to-fine pruner to maximize the input of effective and concise CoT examples. The pruner first selects as many crucial CoT examples as possible and then prunes unimportant tokens to fit the context window. A math reasoning dataset with diverse difficulty levels and reasoning steps is used to train the pruner, along with a math-specialized reinforcement learning approach. As a result, by enabling more CoT examples with double the context window size in tokens, CoT-Influx significantly outperforms various prompting baselines across various LLMs (LLaMA2-7B, 13B, 70B) and 5 math datasets, achieving up to 4.55% absolute improvements. Remarkably, without any fine-tuning, LLaMA2-70B with CoT-Influx surpasses GPT-3.5 and a wide range of larger LLMs (PaLM, Minerva 540B, etc.) on the GSM8K. CoT-Influx serves as a plug-and-play module for LLMs and is compatible with most existing reasoning prompting techniques, such as self-consistency and self-verification.
Microsoft Research Podcast

Collaborators: Renewable energy storage with Bichlien Nguyen and David Kwabi
Dr. Bichlien Nguyen and Dr. David Kwabi explore their work in flow batteries and how machine learning can help more effectively search the vast organic chemistry space to identify compounds with properties just right for storing waterpower and other renewables.
From User Surveys to Telemetry-Driven Agents: Exploring the Potential of Personalized Productivity Solutions
Organizations and individuals continuously strive to enhance their efficiency, improve time management, and optimize their work processes. Rapid advancements in AI, natural language processing, and machine learning technologies create new opportunities to develop tools that boost productivity.
In a recent paper: From User Surveys to Telemetry-Driven Agents: Exploring the Potential of Personalized Productivity Solutions , researchers from Microsoft present a comprehensive, user-centric approach to understand preferences in AI-based productivity agents and develop personalized solutions. The research began with a survey of 363 participants, seeking to reveal users’ specific needs and preferences for productivity agents such as relevant productivity challenges of information workers, preferred communication style and approach towards solving problems, and privacy expectations. With the survey insights, the researchers then developed a GPT-4 powered personalized productivity agent that uses telemetry data gathered from information workers via Viva Insights to provide tailored assistance. The agent’s performance was compared with alternative productivity-assistive tools, such as the traditional dashboard and AI-enabled summaries, in a study involving 40 participants. The findings highlight the importance of user-centric design, adaptability, and the balance between personalization and privacy in AI-assisted productivity tools. The insights distilled from this study could support future research to further enhance productivity solutions, ultimately leading to optimized efficiency and user experiences for information workers.
LongRoPE: Extending LLM Context Window Beyond 2 Million Tokens
The size of the context window of a large language model (LLM) determines the amount of text that can be entered for processing to generate responses. The window size is specifically measured by a number of tokens—larger windows are more desirable. However, due to high fine-tuning costs, scarcity of long texts, and catastrophic values introduced by new token positions, current extended context windows are limited to around 128k tokens.
In a recent paper: LongRoPE: Extending LLM Context Window Beyond 2 Million Tokens , researchers from Microsoft introduce a new method that extends the context window of pre-trained LLMs to an impressive 2.048 million tokens, without requiring direct fine-tuning on texts with extremely long lengths, which are scarce, while maintaining performance at the level of the original short context window. Extensive experiments on LLaMA2 and Mistral across various tasks demonstrate the effectiveness of this method. Models extended via LongRoPE retain the original architecture with minor modifications to the positional embedding and can reuse most pre-existing optimizations.
Exploring Interaction Patterns for Debugging: Enhancing Conversational Capabilities of AI-assistants
Conversational interactions with large language models (LLMs) enable programmers to obtain natural language explanations for various software development tasks. However, LLMs often leap to action without sufficient context, giving rise to implicit assumptions and inaccurate responses. Conversations between developers and LLMs are primarily structured as question-answer pairs, where the developer is responsible for asking the right questions and sustaining conversations across multiple turns.
In a recent paper: Exploring Interaction Patterns for Debugging: Enhancing Conversational Capabilities of AI-assistants , researchers from Microsoft draw inspiration from interaction patterns and conversation analysis to design Robin, an enhanced conversational AI-assistant for debugging. Robin works with the developer collaboratively, creating hypotheses about the bug’s root cause, testing them using IDE debugging features such as breakpoints and watches, and then proposing fixes. A user study with 12 industry professionals shows that equipping the LLM-driven debugging assistant to (1) leverage the insert expansion interaction pattern; (2) facilitate turn-taking; and (3) utilize debugging workflows, leads to lowered conversation barriers, effective fault localization, and 5x improvement in bug resolution rates.
Ironies of Generative AI: Understanding and mitigating productivity loss in human-AI interactions
Generative AI (GenAI) systems, which can produce new content based on input like code, images, speech, video, and more, offer opportunities to increase user productivity in many tasks, such as programming and writing. However, while they boost productivity in some studies, many others show that users are working ineffectively with GenAI systems and actually losing productivity. These ‘ironies of automation’ have been observed for over three decades in human factors research on automation in aviation, automated driving, and intelligence.
In a recent paper: Ironies of Generative AI: Understanding and mitigating productivity loss in human-AI interactions , researchers from Microsoft draw on this extensive research alongside recent GenAI user studies to outline four key reasons for why productivity loss can occur with GenAI systems: 1) a shift in users’ roles from production to evaluation; 2) unhelpful restructuring of workflows; 3) interruptions; and 4) a tendency for automation to make easy tasks easier and hard tasks harder. We then suggest how human factors research can also inform GenAI system design to mitigate productivity loss by using approaches such as continuous feedback, system personalization, ecological interface design, task stabilization, and clear task allocation. Grounding developments in GenAI system usability in decades of research aims to ensure that the design of human-AI interactions in this rapidly moving field learns from history instead of repeating it.
Related publications
Continue reading.

Research Focus: Week of March 4, 2024

Research Focus: Week of January 22, 2024

Research Focus: Week of December 18, 2023

Research Focus: Week of July 3, 2023
Research areas.
Research Groups
- Systems and Networking Research Group (Asia)
- HUE: Human Understanding and Empathy
- Collaborative Intelligence
Related projects
- Blended Reality for Effective Workflows
Related labs
- Microsoft Research Lab - Asia
- Microsoft Research Lab - Cambridge
- Microsoft Research Lab - Redmond
- Follow on Twitter
- Like on Facebook
- Follow on LinkedIn
- Subscribe on Youtube
- Follow on Instagram
Share this page:

IMAGES
VIDEO
COMMENTS
Explore the latest full-text research PDFs, articles, conference papers, preprints and more on APPLIED CRYPTOGRAPHY. Find methods information, sources, references or conduct a literature review on ...
The paper explores applied cryptography concepts in information and network systems security to prevent cyberattacks and improve secure communications. The contribution of the paper is threefold: First, we consider the various cyberattacks on the different cryptography algorithms in symmetric, asymmetric, and hashing functions. ...
Hybrid cryptography takes the advantage of integrating more than one cryptographic algorithms to enhance the overall security and performance. In our research, we have proposed a comparative study for two-tier versus three-tier hybrid cryptographic models applied to secure data on the cloud.
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... Applied Cryptography, Network ...
There exists a great divide between many government officials, security researchers and academics and the hacking community (which are more accurately defined as either white hat or cybercriminals). Whilst it is difficult to point to a research paper, the influence of Jeff Moss on cybersecurity and applied cryptography should not be understated.
The 44 full papers together with 5 short papers presented in this proceeding were carefully reviewed and selected from a total of 185 submissions. They were organized in topical sections as follows: Encryption, Attacks, Cryptographic Protocols, System Security., Cryptographic Primitives, MPC, Blockchain, Block-Cyphers, and Post-Quantum ...
IJACT provides a public forum to help cyber security academics, researchers and engineers working in the fields of cryptography and information security to disseminate state-of-the-art information and to discuss the new advances in applied cryptography. Contents. IJACT publishes original research papers. Special issues devoted to important ...
The ACNS 2020 proceedings volume presents papers focusing on current developments that advance the areas of applied cryptography and its application to systems and network security. The goal is to represent both academic research works as well as developments in industrial and technical frontiers.
This paper presents an updated survey of applications of machine learning techniques in cryptography and cryptanalysis. The paper summarizes the research done in these areas and provides suggestions for future directions in research. Additional Key Words and Phrases: cryptography, cryptanalysis, machine learning.
Feature papers represent the most advanced research with significant potential for high impact in the field. ... to ensure the confidentiality, integrity, and authenticity of digital data. Additionally, we examine post-quantum cryptography, a vital area of research in the face of the impending arrival of quantum computers. ... Applied Sciences ...
Applied Cryptography Knowledge Area Version 1.0.0 ... Moreover, since the boom in public research in cryptography starting in the late 1970s, re-searchers have been incredibly fecund in inventing new types of cryptography to solve seem-ingly impossible tasks. Whilst many of these new cryptographic gadgets were initially of purely
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications. ... Applied cryptography; Side ...
The 3-volume set LNCS 14583-14585 constitutes the proceedings of the 22nd International Conference on Applied Cryptography and Network Security, ACNS 2024, which took place in Abu Dhabi, UAE, in March 2024. The 54 full papers included in these proceedings were carefully reviewed and selected from 230 submissions.
Encryption turns an input (i.e., plain-text) into an encrypted output using an algorithm and a key (i.e., cipher-text). The type of cryptography includes symmetric key encryption methods with two forms (a) Block cipher and (b) Stream cipher. A block cipher uses a single data block.
Quantum key distribution (QKD) 1, 2, 3 is a theoretically secure way of sharing secret keys between remote users. It has been demonstrated in a laboratory over a coiled optical fibre up to 404 ...
This paper discusses cryptography research and algorithms. Cryptography will anonymize financial, personal, e-commerce, ... Applied Homomorphic Cryptography pp. 57-68, (2019).
International Journal on Cryptography and Information Security ( IJCIS) is an open access peer reviewed journal that focuses on cutting-edge results in applied cryptography and Information security. It aims to bring together scientists, researchers and students to exchange novel ideas and results in all aspects of cryptography, coding and ...
In this paper, an attempt is made to present a systematic review of homomorphic cryptosystems with its categorization and evolution over time. ... Define research/review question: ... Galbraith proposed a more natural generalization of Paillier's cryptography approach, which he applied to elliptic curves while keeping the Paillier's ...
Cryptography. , Volume 7, Issue 1 (March 2023) - 15 articles. Cover Story ( view full-size image ): Traditional password authentication methods have raised many issues in the past, including insecure practices, so it comes as no surprise that the evolution of authentication should arrive in the form of password-less solutions.
Large Language Models (LLMs) have emerged as powerful tools in various domains involving blockchain security (BS). Several recent studies are exploring LLMs applied to BS. However, there remains a gap in our understanding regarding the full scope of applications, impacts, and potential constraints of LLMs on blockchain security. To fill this gap, we conduct a literature review on LLM4BS. As ...
In a recent paper: Ironies of Generative AI: Understanding and mitigating productivity loss in human-AI interactions, researchers from Microsoft draw on this extensive research alongside recent GenAI user studies to outline four key reasons for why productivity loss can occur with GenAI systems: 1) a shift in users' roles from production to ...
Cryptography, an international, peer-reviewed Open Access journal. Next Issue Volume 6, September ... Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future ...
Cryptography is an international, scientific, peer-reviewed, open access journal on cryptography published quarterly online by MDPI.. Open Access — free for readers, with article processing charges (APC) paid by authors or their institutions.; High Visibility: indexed within Scopus, ESCI (Web of Science), dblp, and other databases. Journal Rank: CiteScore - Q2 (Applied Mathematics)