Essay on Mobile Phone
Here we have shared the Essay on Mobile Phone in detail so you can use it in your exam or assignment of 150, 250, 400, 500, or 1000 words.
You can use this Essay on Mobile Phone in any assignment or project whether you are in school (class 10th or 12th), college, or preparing for answer writing in competitive exams.
Topics covered in this article.

Essay on Mobile Phone in 150-250 words
Essay on mobile phone in 300-400 words, essay on mobile phone in 500-1000 words.
Mobile phones have become an integral part of modern life, revolutionizing the way we communicate, access information, and conduct daily activities. These portable devices have transformed from simple communication tools to powerful devices that offer a range of functions.
Mobile phones enable instant communication, allowing people to connect with others around the world through voice calls, text messages, and various messaging applications. They have also expanded the concept of social networking, providing platforms for individuals to connect, share experiences, and build communities.
Moreover, mobile phones have become multifunctional devices that offer internet access, multimedia capabilities, and a wide range of applications. They provide easy access to information, entertainment, and services such as online banking, shopping, and navigation.
However, the prevalence of mobile phones also raises concerns. Excessive use of mobile phones can lead to addiction, affecting productivity, social interactions, and overall well-being. It is crucial to strike a balance between utilizing the benefits of mobile phones and maintaining healthy boundaries.
In conclusion, mobile phones have transformed the way we communicate, access information, and engage with the world. They offer convenience, connectivity, and a range of functionalities. However, responsible use is necessary to avoid the negative impacts of excessive reliance on mobile phones.
Mobile phones have revolutionized the way we communicate and connect with others. These portable devices have evolved from simple communication tools to powerful devices offering a wide range of functionalities. This essay explores the impact of mobile phones on communication, social interaction, and daily life.
Communication and Connectivity
Mobile phones have transformed communication by providing instant and convenient access to others. Voice calls, text messaging, and various messaging applications allow individuals to connect with people around the world. The advent of smartphones has further expanded communication capabilities with features like video calls and social media platforms. Mobile phones have bridged geographical barriers and fostered global connectivity, allowing individuals to stay in touch regardless of distance.
Access to Information and Services
Mobile phones have become a gateway to a vast amount of information and services. With internet connectivity, users can access news, research, educational resources, and online platforms for entertainment and leisure. Mobile apps provide convenient access to various services such as banking, shopping, transportation, and navigation. This accessibility has transformed the way we access and interact with information, making our lives more efficient and convenient.
Social Impact
Mobile phones have had a significant impact on social interactions and relationships. They enable individuals to stay connected with friends, family, and colleagues. Social media platforms have expanded our social networks, allowing us to share experiences, photos, and thoughts instantly. However, the overuse of mobile phones can also lead to reduced face-to-face interactions and dependency on virtual connections. It is crucial to strike a balance between virtual and real-life interactions to maintain healthy social relationships.
Challenges and Considerations
While mobile phones offer numerous benefits, they also present challenges. Excessive use of mobile phones can lead to addiction, affecting productivity, mental health, and personal relationships. Additionally, concerns over privacy, cybersecurity, and the potential negative impact on children’s development require attention and responsible usage.
Mobile phones have revolutionized communication and connectivity, offering convenience, information access, and social interaction. While they bring numerous benefits, responsible usage is essential to mitigate the challenges associated with excessive reliance on mobile phones. By harnessing the power of mobile technology while maintaining a healthy balance, we can fully embrace the advantages offered by these remarkable devices.
Title: Mobile Phone – The Transformation of Communication and Connectivity
Introduction:
Mobile phones have emerged as an indispensable aspect of modern life, revolutionizing the way we communicate, access information, and conduct daily activities. These portable devices have evolved from simple communication tools to powerful devices that offer a wide range of functionalities. This essay explores the profound impact of mobile phones on communication, social interaction, and daily life, highlighting their advantages and challenges.
Evolution of Mobile Phones
Mobile phones have come a long way since their inception. From the bulky, limited-functionality devices of the past, mobile phones have transformed into sleek, multifunctional smartphones. The integration of advanced technologies such as high-speed internet connectivity, touchscreens, and powerful processors has propelled the capabilities of mobile phones to new heights.
Communication Revolution
Mobile phones have revolutionized communication by enabling instant connectivity with people around the world. Voice calls and text messages were just the beginning, as smartphones now offer a plethora of communication channels, including video calls, instant messaging applications, and social media platforms. These features have eliminated the constraints of geographical distance and time zones, allowing individuals to stay connected with loved ones and conduct business remotely.
Mobile phones have become the gateway to vast amounts of information and a wide range of services. With internet connectivity at our fingertips, we can access news, research, educational resources, and entertainment platforms anytime, anywhere. Mobile applications provide convenient access to services such as online banking, shopping, transportation, and navigation. Mobile phones have transformed the way we access and interact with information, making our lives more efficient and convenient.
Mobile phones have had a profound impact on social interactions and relationships. They have expanded our social networks beyond geographical boundaries, allowing us to connect with people from different cultures and backgrounds. Social media platforms have become integral to our daily lives, enabling us to share experiences, thoughts, and photos instantly. However, the rise of virtual connections has also raised concerns about the quality of real-life interactions and the potential for addiction to social media.
Productivity and Efficiency
Mobile phones have significantly enhanced productivity and efficiency in various aspects of life. They serve as personal organizers, allowing us to manage calendars, set reminders, and access productivity apps. Mobile email and document editing applications enable us to work remotely and stay connected to work-related tasks. Additionally, mobile banking and payment apps streamline financial transactions, reducing the need for physical visits to banks.
While mobile phones bring numerous benefits, they also present challenges. The overuse of mobile phones can lead to addiction, affecting productivity, mental health, and personal relationships. Excessive screen time can contribute to sedentary lifestyles and health issues such as eye strain and musculoskeletal problems. Concerns about privacy, cybersecurity, and the impact of mobile phone usage on children’s development require careful consideration and responsible usage.
Conclusion :
Mobile phones have transformed communication, connectivity, and daily life. They offer unparalleled convenience, connectivity, and a wide range of functionalities. However, responsible usage is essential to mitigate the challenges associated with excessive reliance on mobile phones. By harnessing the power of mobile technology while maintaining a healthy balance, we can fully embrace the advantages offered by these remarkable devices. As mobile phone technology continues to evolve, it is crucial to adapt our habits and practices to ensure that mobile phones enhance our lives without compromising our well-being and social connections.
Related Posts

Essential Elements of Valid Contract (Explained With Examples)

What is World Population? Main Causes, Effects, Top 20 Countries
Home — Essay Samples — Information Science and Technology — Mobile Phone — Evolution Of Mobile Communication
Evolution of Mobile Communication
- Categories: Cell Phones Digital Communication Mobile Phone
About this sample

Words: 2445 |
13 min read
Published: Jul 30, 2019
Words: 2445 | Pages: 5 | 13 min read
Table of contents
Cellular system, cordless telephone (ct) system, wide area paging systems, trends in cellular radio and personal communications.
- RF circuit fabrication
- Large scale circuit integration
- Digital circuit design
- Miniaturization technologies
- Cellular telephone system.
- Cordless Telephone (CT) system.
- Paging system.
- Forward Control Channels (FCC)
- Reverse Control Channels (RCC)
- Forward Voice Channels (FVC) and
- Reverse Voice Channels (RVC).
- Poor call qualities
- Interference
- Voice signal is digitized through 32 kb/sec Adaptive Differential Pulse Code Modulation (ADPCM) technique.
- Bit stream compression facility.
- Final bit stream transmission at a rate of 72 kb/sec through Gaussian Frequency Shift Keying (GFSK).
- Immune to errors.
- Supports data transmissions effectively up to 32 kb/sec.
- Traffic can be separated with the Time Division Duplex (TDD) access technique.
- Probability of call blocking
- Probability of call dropping
- Probability of call completion
- Handoff delay
- Rate of handoff
- Probability of an incomplete handoff
- Probability of handoff blocking
- Interruption time duration
- Handoff probability.
- Relative signal strength method.
- Relative signal strength with hysteris method.
- Relative signal strength with threshold method.
- Prediction techniques.
- Cell: It is smallest geographical area considered for cellular mobile communication.
- Base station (BS): Base station provides functionalities between mobile unit and Mobile Switching Center (MSC). The base station is located in each cell and it links the subscriber mobile unit with the MSC.
- Cell Splitting: In high cellular traffic regions, a larger cell is divided into smaller cells to have complete radio coverage.
- Handoff: When mobile unit moves from one cell to another cell the call in progress will be handed over form one base transceiver to the base transceiver of the new cell where the mobile unit enters so that the call in progress is not disturbed and such a process is called as “Handoff”.
- Cell sectoring: A cell can be divided into many sectors. For example, from 3 sectors to 6 sectors in a hexagonal cell. The directional antenna should focus on each sector.
- Umbrella cell pattern: A single large cell (Macro cell) consists of many small cells (Micro cells) and there will be interaction between the micro and macro cells.
- Control Channel: They are used for necessary exchange of information related to setting up and establishing cell base stations and the mobile units.
- Traffic Channels: They are used for carrying data or voice connections between different users.
- Frequency Reuse: It is a concept followed in cellular communication for efficient spectrum utilization. The same carrier frequency is reused by many cells in a cellular cluster and it is known as 'frequency reuse scheme.
- Fading: Fading is an effect in mobile radio propagation. It is common in multipath mobile signaling environment.
- Mobile Telecommunication Switching Office/Mobile Switching Center (MTSO/MSO): It is the main unit that connects the base transceiver station and the Public Switched Telephone Network (PSTN) in mobile communication.
- Global compatibility.
- Integrate paging, cordless and the cellular mobile system and LEO satellites as a single mobile system.
- Supports multi-function.

Cite this Essay
Let us write you an essay from scratch
- 450+ experts on 30 subjects ready to help
- Custom essay delivered in as few as 3 hours
Get high-quality help

Verified writer
- Expert in: Information Science and Technology Sociology

+ 120 experts online
By clicking “Check Writers’ Offers”, you agree to our terms of service and privacy policy . We’ll occasionally send you promo and account related email
No need to pay just yet!
Related Essays
5 pages / 2111 words
2 pages / 1073 words
2 pages / 1077 words
6 pages / 2892 words
Remember! This is just a sample.
You can get your custom paper by one of our expert writers.
121 writers online
Still can’t find what you need?
Browse our vast selection of original essay samples, each expertly formatted and styled
Related Essays on Mobile Phone
The debate over whether mobile phones should be banned in schools underscores the need for a nuanced and informed approach. While concerns about distractions and misuse are valid, the advantages of incorporating mobile phones [...]
The pros and cons of using mobile phones essay explores the ubiquitous presence of mobile devices in our lives and their impact on various aspects of society. Mobile phones have revolutionized communication, providing [...]
Mobile phones have become an indispensable part of our daily lives, and teenagers are no exception. In today's digital age, mobile phones have revolutionized the way we communicate, access information, and navigate the world. [...]
Samsung Galaxy S9 price, specifications, features, release date. What will the Samsung Galaxy S9 price be?Samsung Galaxy S9 price may be approx £639 / $725 / AU$1200 based on rumors, as the Galaxy S9 is likely to come at the [...]
The expansion of 5G wireless is 5th generation wireless technology. This will complete wireless communication with almost no limitations. It can be called REAL wireless world. It has incrediable transmission speed. A 5G network [...]
In this new era of globalization, the technologies are an ever-changing aspect of this day and age. New gadgets and many new and fresh ideas are always trying to makes life’s easier than before and bring people closer together. [...]
Related Topics
By clicking “Send”, you agree to our Terms of service and Privacy statement . We will occasionally send you account related emails.
Where do you want us to send this sample?
By clicking “Continue”, you agree to our terms of service and privacy policy.
Be careful. This essay is not unique
This essay was donated by a student and is likely to have been used and submitted before
Download this Sample
Free samples may contain mistakes and not unique parts
Sorry, we could not paraphrase this essay. Our professional writers can rewrite it and get you a unique paper.
Please check your inbox.
We can write you a custom essay that will follow your exact instructions and meet the deadlines. Let's fix your grades together!
Get Your Personalized Essay in 3 Hours or Less!
We use cookies to personalyze your web-site experience. By continuing we’ll assume you board with our cookie policy .
- Instructions Followed To The Letter
- Deadlines Met At Every Stage
- Unique And Plagiarism Free
- Mobile Phones
Essay on Mobile Phones
500 + words uses of mobile phones essay.
Mobile phones, chiefly used to make voice calls to people, are also popular as cell/cellular phones. The current technological developments have made our lives more comfortable. We are becoming more and more dependent on mobile phones for our communication. From calling to emailing or texting and even making purchases online, the uses of mobile phones are numerous. For this reason, mobile phones are also known as “smartphones” now.
Mobile Phones Essay
The fact that we should also avoid overdependence on mobile phones is also discussed in this essay on the mobile phone. This mobile phone essay in English discusses the advantages and disadvantages of mobile phones. Learn from this essay how to write a persuasive essay on mobile phones for students and help them ace essay writing.
Advantages of Mobile Phones Essay
This section of the mobile essay talks about the advantages of mobile phones. See here what this mobile phone paragraph has to say.
- Stay connected: – Mobile phones are the best way to stay connected with your friends and family living away from you. Voice calls, video calls, emails, messages and texts- thus, the communication modes via cell phones are multitude.
- Mode of entertainment: – As technology advances, you can now find the entire entertainment industry at your fingertips on your mobile. There are apps on mobiles to watch films, series/ shows, documentaries, news, read books, listen to music and much more.
- Managing office work :- With working from home becoming more popular now due to the Covid-19 pandemic, mobile phones can also simplify our work. From creating and getting reminders about meeting schedules, online meetings, sending and receiving emails/ files, giving presentations, setting alarms and applying for jobs to setting up a calendar to do jobs, mobile phones are beneficial for working people. Instant messaging and official emails via mobile phones also flow forth to connect with office people.
Disadvantages of Mobile Phones Essay
There are also cons to using mobile phones. Find here the disadvantages of mobile phones.
- Become overdependent on mobile phones :- It is seen that people tend to become overdependent on mobile phones, thus wasting their time. With technological advancement, the use of mobile phones has increased, making people addicted to them.
- People become more non-communicable :- They use mobile phones more as a mode of communication or to entertain themselves, thus meeting people less or talking less. As time goes by, they become rather incommunicable.
- Privacy loss:- Loss of privacy is another primary concern on the rise due to over usage of mobile phones. It is now possible to get personal details like where you live, details of your friends and family, job and education and so on via mobile phones.
Thus, see how there are pros and cons to using a mobile phone, from these advantages and disadvantages of mobile phones essay. Seeing as how mobile phones are now an integral part of our lives, it’s up to us to know how to use them properly to lead a hassle-free life without misusing them.
Also Read: Social Media Essay | Essay on Health is Wealth | Essay On Constitution of India
Frequently Asked Questions on Mobile Phones Essay
Who invented the mobile.
The mobile phone was invented in the year 1973 by Martin Cooper.
What is the role of mobile phones in our lives?
Mobile phones are a part of our lives now. Some of its main roles are storing data, instant communicative purposes, digital cameras, etc.
How can a mobile phone be of use to the student?
Students can use mobile phones for various study and research purposes. An abundant amount of information which is useful for students can be accessed through mobile phones.
Leave a Comment Cancel reply
Your Mobile number and Email id will not be published. Required fields are marked *
Request OTP on Voice Call
Post My Comment
Register with BYJU'S & Download Free PDFs
Register with byju's & watch live videos.
The Evolution of Mobile Communications
- Open Access
- First Online: 18 October 2023
Cite this chapter
You have full access to this open access chapter

- Seppo Yrjölä 3 , 4 ,
- Marja Matinmikko-Blue 5 &
- Petri Ahokangas 6
4721 Accesses
2 Citations
This chapter introduces the evolution of mobile communications. As the mobile communications’ context is expected to become increasingly platform-based and ecosystemic, it is important to distinguish relevant perspectives and map the developments in the field. This chapter provides an outlook from the first (1G) to fifth (5G) generation of mobile communications by looking at technology and standardization, relevant regulatory developments and contents, and specifically characterizes the business ecosystems toward the sixth generation of mobile communications (6G). The purpose of the chapter is to provide a contextual setting for the discussions presented in the subsequent chapters by showing the emergence and evolutionary continuum of mobile communications from 1 to 6G.
You have full access to this open access chapter, Download chapter PDF
Similar content being viewed by others

Long-Term Evolution

Generations of Wireless Mobile Networks: An Overview
Metis research advances towards the 5g mobile and wireless system definition.
- Technology generations
Standardization
- Business model.
Natural selection will not remove ignorance from future generations. (Richard Dawkins)
The Historical Development of Mobile Communications
Worldwide digitalization has been enabled by the successive mobile communications generations over the past three decades. Each generation has introduced new use cases and technical capabilities, while optimizing the use cases of the previous generation. Overall, technology can be seen to serve an enabling role in mobile communications. In this historical development, the commercialization cycle of mobile communications has followed three steps: (1) definition, (2) standardization and implementation, and (3) deployment and use. At the definition stage, the innovation from companies and research organizations is mediated together with national authorities in the global ITU-R (International Telecommunication Union Radiocommunication sector) to form a framework and develop usage scenarios for the radio aspects of mobile communications technology. After the definition of the requirements for the radio interface at the ITU-R, standardization bodies and firms negotiate standardization and implementation via standard releases that are the basis for the implementations by different technology vendors. As the technical systems and solutions needed in a technology generation have been developed, they are deployed and utilized by the mobile operators in different business implementations (Ahokangas et al., 2023 ). This deployment and use are, however, delimited by regulation as the telecommunications is a highly regulated field.
This chapter provides an overview and brief introduction to the mobile communications industry. The chapter will start with a brief description of technological development in the field in different technology generations from the first to sixth generation and discuss the role of standardization in this development. Next, the chapter will provide a short introduction to the role of regulation in mobile communications. The chapter will conclude with a characterization of the mobile communications business. This chapter serves as a starting point for the discussions presented in the subsequent chapters.
Technological Developments from 1G to 5G
From the first generation, the mobile network system architecture has been defined by the radio access technology, access and core network routing, and the associated services related to voice, messaging, data transfer, mobility, authentication, and access control. After the first generation (1G) analog voice only service, the second generation (2G) introduced a digital mobile system with text messaging and mobile phones as a personal portable device in addition to a voice service. The third generation (3G) with mobile broadband data brought access to mobile multimedia and significantly lowered the cost of the voice service. The fourth generation (4G) expanded the multimedia service offering across digital industries built around smart phones. 4G lowered the cost of data while introducing video to consumers and machine-type communications to serve vertical industries. The ongoing deployment of the fifth generation (5G) has drastically increased the number of communicating objects (David & Berndt, 2018 ). For consumers interactive low-cost video and for enterprises the industrial IoT (Internet of Things) are paving the way toward human augmentation and digital-physical fusion. Up to 4G mobile communications, the connectivity business has remained surprisingly unchanged allowing the incumbent mobile network operators (MNOs) to dominate the market, although they have been seriously challenged by the content-owning, cloud-based over-the-top (OTT) Internet giants (Ahokangas et al., 2013 ).
For 5G, the ITU-R vision framework for international mobile telecommunications IMT-2020 and beyond presented in (ITU-R, 2020 ) adopted a service-centric approach to the 5G use case definition. The IMT-2020 vision identified three services classes, enhanced mobile broadband (eMBB) targeted at consumers, ultra-reliable low-latency communications (URLLC) for mission-critical services for organizations such as factories, and massive machine-type communications (mMTC) to connect IoT. The fifth generation mobile network 5G new radio (NR) solution was standardized by 3GPP in release 15 and commercially deployed in 2019 based on the non-standalone (NSA) architecture where a 5G radio access network (RAN) operates on a legacy 4G LTE core network. Innovations in a new user equipment (UE), radio access network (RAN), and 5G core (5GC) designs enable substantial improvements across the main service domains eMBB, URLLC, and mMTC. In particular, the new active antenna beam-based physical layer RAN design allows operation in higher frequencies up to mmWaves with wider bandwidths. The 5G system architecture including the 5GC became available from 2020 as standalone (SA) enabling the deployment of private enterprise and industrial 5G networks (Parkvall et al., 2017 ).
The 5G standard evolution in releases 16 and 17, as depicted in Fig. 2.1 , expands the 5G ecosystem particularly for industrial domain via innovations such as time sensitive communication, small data transmission, and UE energy saving. 3GPP work on release 18 5G-Advanced (5GA) is due in 2024 and the first deployments are expected around 2025 (Chen et al., 2022 ). 5GA will provide an intelligent network platform utilizing machine learning (ML) to adapt to its environment, new classes of devices and enhance support for novel applications such as truly mobile extended reality (XR) services. Furthermore, 5GA will embed high-precision location, presence and timing technologies, and device innovations will make drone optimized and non-terrestrial networks (NTN) such as satellite connectivity a commonplace feature. For the Industrial Internet of things (IIoT) ecosystem, the release will offer connections from low-cost and low-data rate to extremely low latency with pinpoint accuracy (Lin, 2022 ).

Expected 3GPP standardization timeline and ITU-R process for IMT systems
In previous generations, the end-to-end network provided the same service to all users and the only option to offer guaranteed provision for a critical application, e.g., for public safety or critical infrastructure services was to deploy a dedicated physical network. In the 5GC network, network slicing allows operators to create thousands of virtual, independent networks within the same physical network infrastructure that connect from the device through to the application. Network slicing enables operators to efficiently package novel 5G network capabilities into differentiated, guaranteed service level agreement-based (SLA) services in a cost-effective way.
The 5GA platform is visioned to introduce and extend a variety of novel applications and use cases across industries in 2025, and beyond (see, e.g., Ghosh et al., 2019 ; Nakamura, 2020 ).
Extended mobile reality and ubiquitously available cloud gaming requires compact power-efficient devices supported by time critical communication capabilities.
Wearable technology and devices demand a small form factor, efficiency, and high battery life.
Industrial process monitoring and quality control are based on a massive volume of small data that should be transmitted frequently and efficiently to support network performance.
Critical infrastructures such as public safety, railways and utilities with ultra-reliable low-latency communication combined with security and privacy requirements.
Asset tracing and tracking in logistics demands extremely low energy consumption.
Tele-operation of autonomous vehicles, robots, and drones demands reliable and secure communications both for the control and payload data.
Location applications of connected devices with centimeter-level accuracy is enabled by advanced indoor and outdoor positioning technologies.
Resilient, deterministic, and more stringent timing of 5G networks will be made affordably available and leveraged, e.g., in industrial automation to real-time financial transactions.
For 6G, ITU-R is working to publish the global framework for IMT toward 2030 and beyond in 2023 that will provide the basis for defining the future 6G.
The worldwide success of mobile communications from the first generation onward can be seen to be largely founded on the initially proprietary technologies that have subsequently been transferred into a series of standards. Each new technology generation has required a decade of billions of euros investment in research and development to formalize technological innovations into standards and further into hardware and software products and services. Technology standardization has helped to generate foundational innovation platforms upon which emerging technology vendors have developed their products and services. From 1G onward, a similar standard release process has been followed providing standard blueprints for stakeholders to contribute and develop products and network solutions. The stakeholder community for the development has been well defined and stable consisting of a limited number of technology vendors, mobile network operators, system integrators, as well as academia and regulators.
With 5G, the technology ecosystem has been expanded particularly toward enterprises and industries introducing an unprecedented number of use cases and related novel stakeholder groups. Moreover, it should be acknowledged that 5G standardization deviates from previous generations having a coordinated single worldwide major approach to the IMT-2020 requirements. 3G (IMT-2000) was defined by three alternative paths (3GPP UMTS, 3GPP2 CDMA2000 and IEEE mobile WIMAX) and 4G (IMT-Advanced) with 3GPP LTE and IEEE mobile WIMAX alternatives that initially did not have an obvious single winner. Furthermore, 5G service-based architecture with open interfaces, the convergence of communication, information technology and data (ICDT), and user developer centricity will challenge the establish 3GPP grounded IMT process. Recent geopolitical and societal changes—especially related to discussions on data colonialization, user rights, and the use of artificial intelligence, and the digitalization of society and critical infrastructures—have given rise to discussions on the role of nations in standardization. The ongoing technology battle has specifically concerned the leadership in 5G regarding semiconductors, and concerns over sovereignty regarding AI and digital technologies have become an issue (Moerel & Timmers, 2021 ). As a recent example, the US “Clean network initiative” in 2020 addressed the long-term threat to data privacy, security, human rights, and principled collaboration to free the world from authoritarian malign actors (US Government, 2020 ). These developments raise the question of the possible fragmentation of the 6G standardization.
Role of Patents and Licensing
For a half-century, all major mobile communications technology providers have relied on patent licensing as their main value capture mechanism. The European telecommunications standards institute (ETSI) has orchestrated the development and governance of standards, controlling the technology contributors to make licenses available on a fair, reasonable, and non-discriminatory (FRAND) basis for a wide variety of implementers globally. The unique combination of technology co-development and widespread global adoption have been enabled by a nonexclusive licensing model. In addition to standard essential patent (SEP) royalties which have created a continuous incentive for standard contributions, technology vendors have leveraged complementarities via adjacent intellectual property (Teece, 2019 ).
The collaborative approach has empowered a downstream innovation and a mobile technology and application ecosystem. The standards-compliant ecosystem comprises dedicated technology/chipset firms, infrastructure equipment providers, mobile network operators, device manufacturers, operating system software providers, application developers, and content providers. Many specialized technology firms and vertically integrated companies in the mobile communications industry increasingly engage with two or more roles. Contrary to the single company-owned web-scale “winner-takes-all” digital platforms, harmonized common standards in mobile communications have helped define platforms with many stacked software layers.
A detailed look at the ETSI IPR online database (ETSI IPR) reveals that most 5G patents were declared between 2017 and 2019, and 25% of them were evolutionarily declared already for 4G. The database indicates that radio access networks (RAN), comprising the radio performance, physical layer, radio resource management specification, specification of the access network interfaces, the definition of the operations, and management requirements and conformance testing for user equipment and base stations encompasses about 84% of the SEPs. Physical layers 1 and layer 2 alone add up to 70% of SEPs. Services and systems aspects (SA) covering the overall architecture encompasses approximately only 11% of SEPs despite their leading role in security, management, orchestration, charging, and mission-critical applications areas. The remaining approximately 5% of SEPs are encompassed in the core network and terminals (CT) domain where differentiation and user experience have traditionally been implemented via technology system integration and overall network design, management, and orchestration. All in all, what matters is the device relevance found to be 80–90% of all the SEPs, which is in line with the distribution of licensing royalties (Yrjölä et al., 2022 ).
With a massive diffusion into new application areas and expanding the circle of stakeholders and licensees in the 6G era, firms may increasingly cooperate vertically in open dynamic multi-layered architectures while competing horizontally to capture value across services. The resulting complex licensing landscape will necessitate more precise rules for FRAND licensing as the exact interpretation and the associated reasonable licensing fees are not precisely defined in the current model (Teece, 2019 ). The extension toward cross-layered architecture functionalities and including data and algorithms will lead to the convergence of multiple connected ecosystems, introducing new roles and actors, especially related to system integration, management, and orchestration (Yrjölä et al., 2021 ).
Flexibility, scalability, and efficiency requirements combined with the long-tailed distribution needs of applications, may lead the 6G system to only specify a few core capabilities for the lower system layers with related open interfaces. Thus, higher layer distinct use case specifications for a complete connectivity platform will be done by different actors. For scalability and replicability among connectivity services, the lower-layer processing-intensive radio functions may continue to be specified by global standardization and continued to be implemented in custom silicon chipsets. On the other hand, the modular architecture with open interface specifications will enable the rest of the softwarized, programmable, and virtualized functions to be deployed on any commercial computing hardware. This will facilitate competition and entry, enabling stakeholders to access complementary assets through various forms of alliance with larger firms as well as to specialize within the ecosystem and develop complements to the platform. This suggests that value should be captured increasingly across multiple protocol layers and levels of the industry, and that the role of the de facto standard will need to be revised. Standards for systemic and complex general-purpose technologies, as Fig. 2.2 summarizes, will require coopetitive (i.e., simultaneous collaboration and competition) development to gain interoperability across ecosystems and industries.
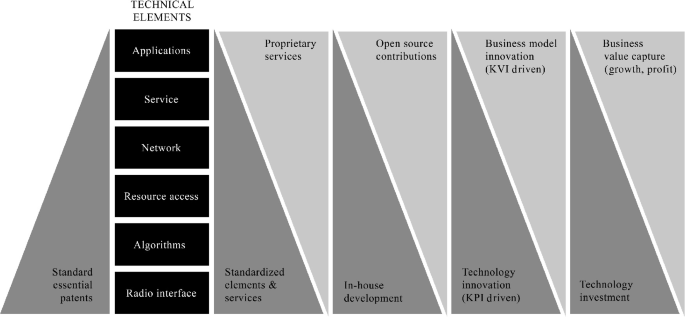
(Adapted from Yrjölä et al., 2022 )
The transformation of technology innovation across 6G system architecture layers stems from the 3rd Generation Partnership Project (3GPP) system architecture
One of the key challenges related to profiting from technological innovations in the 6G era is the protection and enforcement of intellectual property while fostering wide diffusion in the ecosystem. For example, starting from the discussion about who should acquire and pay for an SEP license: the OEMs, end-product manufacturers, or connectivity and application module suppliers. It will be essential to find a ruling that avoids the courts’ protracted resolution of licensing disputes, ensures adequate compensation for developers, and promotes widespread use of innovations through appropriate fees. A compromised ETSI FRAND model and a more proprietary vertically integrated model with the reduced IP protection may be priced into products and services (Teece, 2019 ) and severely reduce the existing significant positive externalities that mobile communications technologies offer and place the envisioned 6G role as a general-purpose technology at risk.
Regulatory Developments
The mobile communications sector is tightly regulated. Regulation takes place at national, regional, and international levels via different methods and focus areas. One fundamental area is spectrum regulation, because the radio spectrum is the most critical natural resource needed for all wireless communications (Anker, 2017 ). Mobile communication networks need spectrum to operate on and so do all other wireless communication systems such as satellites and terrestrial broadcasting, among others. However, if they use the same spectrum resources, there can be harmful interference that leads to significant service degradations. As a result, different wireless systems have traditionally sought their own exclusive use of the radio spectrum, which has been the foundation for mobile communications.
At the global level, the ITU-R sets requirements for systems to become part of the IMT family, that currently comprises 3G, 4G and 5G systems. At the regional level, coordination takes place between countries in specific regional organizations. In Europe, countries belonging to the European Union follow the European electronic communications code (EECC) directive, which defines the rules for electronic communication networks and services, and the spectrum used for mobile communications is harmonized. Many regulatory topics are a national matter including the actual spectrum awards determining who can deploy mobile communications networks and how. National level regulations consider international and regional approaches and define regulations that are considered appropriate in the country in question.
Spectrum Regulation
Spectrum regulation in particular plays a fundamental role in defining how, where, and when the developed technology is used and for what purpose (Matinmikko et al., 2014 ). Spectrum decisions made at the international, regional, and national levels significantly impact the resulting markets and the mobile communication sector is no exception. For mobile communications, every new technology generation has secured access to new spectrum, which has been internationally harmonized, leading to economies of scale by using the same equipment in larger markets.
Market regulations aim to achieve competitive markets where more than one MNO serves the end user customers in a country. Markets are directly impacted by spectrum regulatory decisions, especially via the rules in awarding of licenses. These national spectrum awarding decisions, which typically use spectrum auctions for mobile communications, significantly influence how many MNOs can operate in a country and how competitive the market is. Additionally, access regulation with rights and obligations concerning interconnection has a major influence on the markets.
Regulatory developments at the ITU-R regarding IMT-2000, IMT-Advanced and IMT-2020 systems have defined the development paths for 3G, 4G and 5G systems. The phases of regulatory development proceed from identifying technology trends and traffic characteristics to defining a joint vision, followed by detailed requirements definition, against which technology proposals are then evaluated. Finally, technology proposals that fulfill the requirements defined by the ITU-R become members of the IMT family and gain access to spectrum bands that are allocated to the mobile service and identified for IMT systems. The spectrum identification process goes in parallel with the IMT system process ranging from identifying spectrum needs based on market studies to studying candidate bands and their feasibility toward spectrum allocation decisions that are made at the World Radiocommunication Conferences (WRCs) of the ITU-R.
Regarding 6G, the process for IMT toward 2030 and beyond, which corresponds to 6G, is underway at the ITU-R. The technology trends have been identified and the report on future technology trends was published in 2022 (ITU-R, 2022 ). Work on the framework recommendation is ongoing and is expected to be completed in June 2023, presenting new usage scenarios for 6G. After WRC-23, which could develop an agenda item for the 6G spectrum for the following WRC in 2027 (WRC-27), the actual requirements definition phase will start in 2024. The requirements and needed evaluation criteria and processes will be finalized by the end of 2026. Technology proposals on 6G are expected in 2027–2028 with decisions taking place in 2029.
Regarding 6G, standardization phase 1 will likely start from 2025, leading to the first 6G specification in 3GPP Release 21 by 2028 and followed by commercial deployments around 2030. Meanwhile 5G will be enhanced by 5G-Advanced, which will be key focus for 3GPP in Release 18 and19 onward and will power commercial public and private networks starting in 2025. 5G-Advanced will provide new 5G features and boost 5G capabilities in four dimensions: experience, extension, expansion, and operational excellence.
The Evolution of the Business of Mobile Communications
The mobile communications industry has for long been referred to as an ecosystem (Zhang & Liang, 2011 ). In the current 4G-dominated world that is transitioning toward 5G dominance, the ecosystem comprises hardware providers, software providers, mobile equipment and infrastructure providers, content and application providers, network operators, content providers, OTT (over-the-top) Internet players, service providers such as MNOs (mobile network operators) and MVNOs (mobile virtual network operators), network infrastructure constructors, facility owners, regulatory bodies, and end users (Pujol et al., 2016 ). However, the way the ecosystem has been seen has changed over the history of mobile communication generations.
Latva-aho and Leppänen ( 2019 ) listed 29 different stakeholders for the envisioned 6G ecosystem, categorizing them into human, machine, enterprise, and public-sector type users, each with different demands and needs. In addition, they divided the stakeholders to have two different roles. Resource and asset stakeholders comprise device suppliers, network/cloud infra vendors, complementary technology providers, national regulators, public sector, government, data owners, context providers, content providers, context owners, edge cloud, data center, facility owner, site supplier, and building constructors. Meanwhile, matching and bridging stakeholders included mobile virtual network operators, mobile network operators, fixed operators, satellite operators, vertical-specific service providers, roaming service providers, application providers, digital twin providers, management service providers, data brokers, network resource brokers, broking/bridging providers, trust providers, and providers of security as a service.
From Value Chain to Business Ecosystem
Thus, the value chain in the mobile communication sector has evolved over the technology generations. The 2G era included state-owned MNOs and the market was opened to competition from new private MNOs. The value chain in 2G typically consisted of network infrastructure vendors, MNOs, device vendors, end users, and the regulator as depicted in Fig. 2.3 . 3G introduced mobile broadband, which made new services and applications available over the networks. Otherwise, the value chain remained as it was in 2G, but competition increased in several markets with new market entry, leading to market consolidation later. 4G brought mobile broadband on a large scale and MNO networks became bit pipes for OTT services. In the 4G era, the role of OTT services increased and the number of MNOs per country decreased as a result of acquisitions by the MNOs.
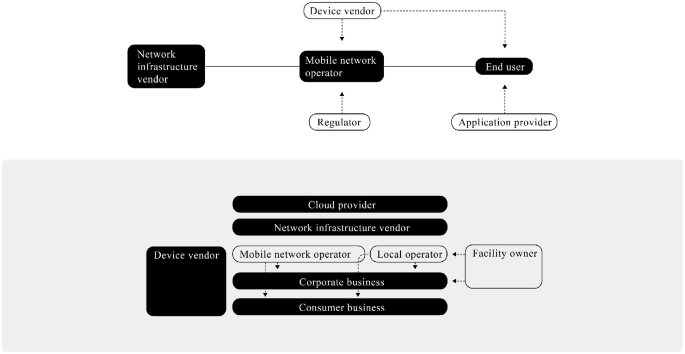
The value chain in 2G, 3G, 4G (upper part of the figure), and 5G (lower part of the figure)
The 5G era has introduced local networks deployed by different stakeholders, which has opened the market for new local entry. This development is still ongoing and varies a great deal between countries (Matinmikko et al., 2018 ). Local 5G networks have created local vertical specific ecosystems around their deployment areas where the stakeholders and their roles vary. Examples of this include the port and factory ecosystems.
From Engineering Platform to Service Modularity and Ecosystem
The definition of 5G opened the opportunity to change from connectivity-centric business models toward various connectivity with bundled content (data-based), context (location-based or service-specific), and commerce (platform) business models and offering the whole network as a service (NaaS). In parallel to this development, a disruption in the deployment models of mobile communication networks took place in the 5G era disrupting the ecosystem by enabling new entrants, such as utilities, ports, and manufacturing plants, to run their own local private 5G networks (Matinmikko et al., 2017 ). Additionally, other technologies such as cloud computing, AI, and Web3 have started to converge with or complement 5G introducing cloud computing “the fifth C” into the 4C business model characterization framework (Wirtz et al., 2010 ) as depicted in Fig. 2.4 .
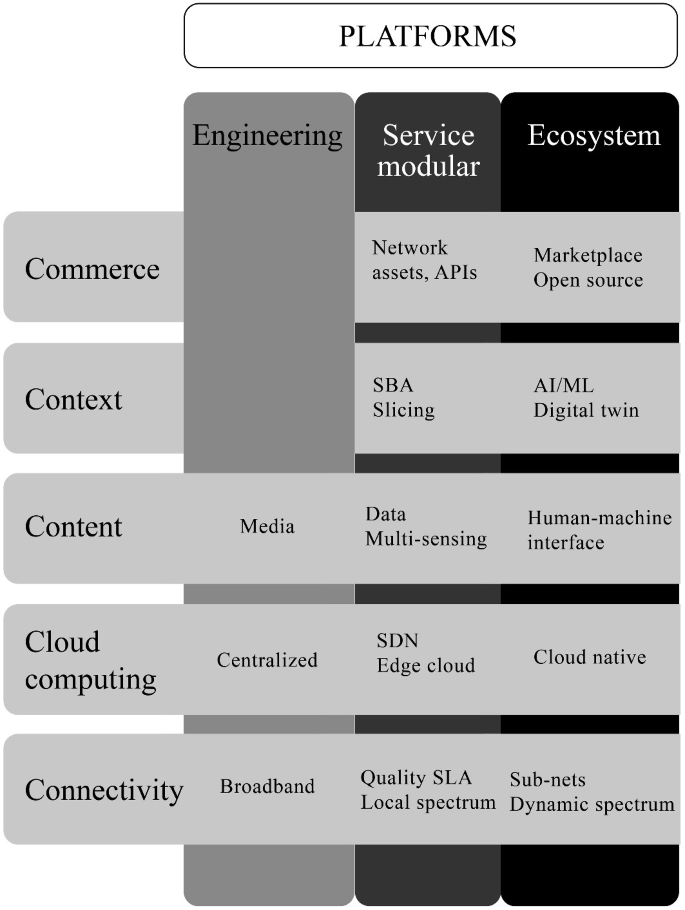
From engineering platforms toward service modularity and ecosystem platforms
Figure 2.4 illustrates the evolutionary view of the mobile communications system from the 4G engineering connectivity platform via 5G service modularity toward 6G connectivity platform-based ecosystem. In the 5C framework, the connection layer includes physical and virtualized communication network infrastructures for the ecosystemic value proposition of exchanging information. The newly introduced cloud computing infrastructure is an essential enabler for a variety of data and intelligence-based services. The third content layer aims to collect, select, compile, distribute, and present data in the ecosystem in a value-adding, convenient, and user-friendly way. In the context layer, the aim is to provide a structure, increase transparency, and reduce complexity by providing a platform for stakeholders’ communication and transaction. Finally, the commerce layer focuses on negotiation, initiation, payment, and service and product deliveries in the ecosystem, enabling low transaction costs and providing a cost-effective marketplace for matching and bridging supply and demand.
Despite massive investment in the current mobile communication networks, the MNOs’ opportunities for differentiation have been limited. The differentiation capacity has shifted toward devices and content and the mobile operating systems have become bottleneck assets in the mobile ecosystem. 5G can be seen as a service modular platform system stemming from interfaces that enable complementary offerings of elements and services. The digital platform business model enables software developers to add value through applications and complementary assets to the ecosystem by attracting users and building network effects. The ecosystemic 6G connectivity platform-based model facilitates value co-creation, co-capturing, and sharing to maximize the overall value generated and acquired not only by a focal traditional incumbent MNO but also by the ecosystem’s stakeholders. The 6G ecosystem can be seen both as an innovation engineering platform and e-commerce transaction platform (Evans & Gawer, 2016 ). This will enable digital business ecosystems to facilitate exchanges of otherwise fragmented groups of consumers and/or firms and to provide a technology and distribution system for other companies to base their technological and service innovations. Introduced service modularity on 5G platforms will on one hand enable fast-paced autonomous innovation, but on the other hand it will change the appropriability mechanism by reducing the role of complementary core assets.
Technological Architecture as a Starting Point
In 6G, the systemic architecture level innovations will be vital in enabling business model changes. Key transformational bottleneck assets such as AI/ML and human–machine interfaces (HMI) as general-purpose technologies will be leveraged across distributed a heterogeneous 6G cloud architecture. Intelligent 6G networks are based on common enablers for AI as a service, and federated learning as-a-service that leverage data acquisition, data exposure and a common cross-domain analytics framework. Intelligent network enablers will operate across the cloud continuum from the central cloud to the edge and to far edge including the UE. Extreme scalability and flexibility will become the new paradigm in 6G. Network automation and orchestration will be integral parts of intelligent networks using AI and analytics to manage and orchestrate the networks in a fully automated manner across all layers and parts of the network abstraction (Kaloxylos et al., 2021 ).
The primary focus in the current 4G and early 5G deployments has been on network planning, network diagnostics, and network optimization and control reducing capital expenditure, optimizing network performance, and building new revenue streams through the improved customer experience. 6G radios are envisioned to adopt AI/ML in a fundamental way for optimized air interface design, cognitive dynamic spectrum use, and context awareness. On the network level, hyper-specialized agile slicing will call for new fully AI automatized service management and orchestration for network automation, allowing dynamic adaptation of network resources according to changing service requests, reducing the deployment time of new services and mitigation of failures, and significantly reducing operating expenditure. Digital trust, enabled by quantum computing and distributed Web3 ledger technologies such as blockchain and smart contracts, will provide businesses securely and predictably with world-class cybersecurity, public safety, and fintech solutions.
Human augmentation will enable people to interact with and within the digital world. This will include VR headsets, XR glasses, remote control with haptics, and, in the future brain-machine interfaces and connected bio-medical implants. The fusion between the digital and physical realms will further enhance our capabilities to interact with dynamic representations of real-world objects, systems, and processes in the digital world such as digital twins and 6G network sensing data. Downstream digital application platforms will converge and there will be multimodal engagement with media, and the physicality of lived experiences will be seamlessly accessible through a HMI extended to all five senses, including the senses of touch and taste. Individual and collaborative users will seamlessly be able to switch between any form of immersive mobile extended reality, encompassing virtual reality, augmented reality, and mixed reality, comprising both virtual and augmented objects. HMI opportunities will be clearly differentiated between the consumer, the enterprise, and the industrial segment.
Toward the 6G World
Disruptions on multiple levels are a visible part of both organizational life as well as economic reality these days (e.g., Buckley, 2019 ). In the last few years, global industries have faced disruptions in the form of the China-US trade war, the technological war between different centers of power especially in emergent industries (Chin, 2019 ; Lukin, 2019 ; Petricevic & Teece, 2019 ), COVID-19, and more recently the Russia-Ukraine war. As a result, in recent times, we have witnessed a plethora of terms emerging; out of which the most famous is VUCA (volatility, uncertainty, complexity, and ambiguity) as a permanent feature of the current economy (Bennett & Lemoine, 2014 ; Millar et al., 2018 ) especially in industries which are significantly intertwined with global value creation. In this context, mobile communications is one of the sectors that has been very visibly linked to most elements of global disruptions because of its criticality to the economic competitiveness as well as its visible interlinkage to the emergent digital business models (Kilkki et al., 2018 ). A well-known example in this regard is the Chinese telecom giant Huawei which has received bans and strict oversight in different Western countries including USA due to the concerns about privacy and security. As the shift toward 6G is taking shape globally, there is a race for setting the standards, and geopoliticalGeopolitical disruptions (and considerations) are a core aspect of this debate (Klement, 2021 ; Yrjölä et al., 2020 ). At the same time, it is vital to stress that the influence of a variety of global disruptions on 6G development and planned implementation has not been studied specifically so far; thereby showing a visible gap in the extant literature.
A Business Architecture Perspective
In the engineering tradition, platforms have been seen as modular technological designs for facilitating innovation, whereas in the economics tradition platforms have been seen as two- or multi-sided markets connecting supply and demand. The traditional approach to a mobile communications ecosystem is based on a layered protocol-based technical infrastructure, an engineering platform consisting of elements and interfaces. As in digitalized industries in general, in mobile communications, business models can be seen to follow the nature of integration—vertical or horizontal (Ballon, 2007 ). The previous 4G and 5G business architectures have considered the ecosystem configuration either through vertical or horizontal business models as depicted in Fig. 2.5 .
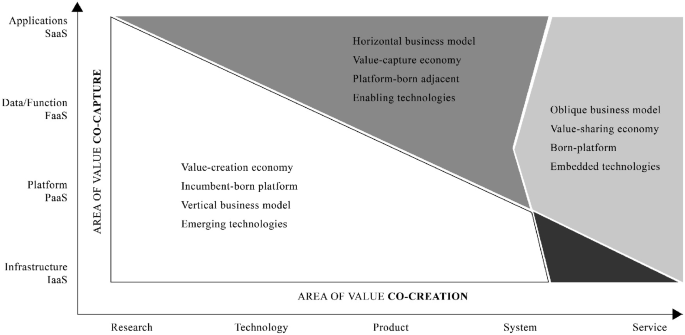
Evolution from vertical and horizontal business logics toward oblique value creation and value capture in 6G (Adapted form Yrjölä et al., 2022 )
In the vertical business model , traditionally employed in mobile communications, a firm controls its suppliers, distributors, or retail locations as part of its supply chain. To be competitive in this supply-sided model, a firm focuses on creating value for its customers, and is grounded inside its selected verticals. On the 4G engineering platform, a competitive advantage arises from focusing on value creation within narrow segments around connectivity and content (Ahokangas et al., 2019 ). As interfaces in mobile communications have been largely defined from the inside-out perspective, the telco APIs have not reached the developers’ ecosystem, and infrastructure providers have been controlling the complete technology and service solution (Basole & Karla, 2011 ). In the industry transition from 4G to 5G, the vertical integration strategy has been clearly visible with the acquisition of business operations within the same vertical. Deployed incumbent-born mobile communications connectivity platforms have typically been upstream platforms and dependent on the core product (Pundziene et al., 2022 ) and slow to respond to market dynamics.
The introduction of 5G has transformed the traditional vertical business model approaches of the mobile sector toward a horizontal model (Cave, 2018 ). The horizontal business model , adopted in consumer service-oriented businesses, to serve a wide clientele across different segments focuses on economies of scale and scope in order to maximize the value capture. This demand-side approach enables multiple stakeholders to focus on their respective fields through a common framework that allows faster innovations and a rapid scale-up of applications and businesses. Technological innovations, extreme cost consciousness, and risk awareness have been characteristic in capturing customer value while defending a position against competition. The horizontal 5G business models are highly dependent on the supporting infrastructure and complementors to run smoothly. The introduced service-based architecture (SBA) with softwarization and cloudification technology has enabled demand-side platformization (Camps-Aragó et al., 2019 ) that enables innovative as-a-service business models to serve a wider value constellation (Hmoud et al., 2020 ). The novel serverless cloud-native model allows developers to build and run applications without having to manage servers. IT and cloud Webscalers’ platform-born adjacent platforms can serve downstream users via transformative service innovations (Pundziene et al., 2022 ).
In the 6G era, the vertical integration in the value chain and/or horizontal diversification to any segment is unlikely as digital service chains are becoming more distributed, abstracted, and advanced built on resources provided as-a-service. Concepts centered around network-as-a-service (NaaS) will be very mature by 2030, and everything that can be offered as a service will be (Yrjölä et al., 2022 ). Cloud native design, open source, and standards will drive openness in the architecture of networks and operations, while enabling technologies such as hyper-specialized virtualization and slicing, abstracted data, while analytics capabilities will provide the right building blocks (Yrjölä et al., 2021 ). Simple-to-consume low-code/no-code APIs and network-as-a-code, backed by new levels of AI/ML-driven automation will be the enablers of new business and revenue for all players. This will require increased coopetition among network function vendors, network service providers, application service providers, and hyperscale companies, within an evolved ecosystem. In modern IT and software development, DevOps and infrastructure-as-a-code (IaC) are already mainstream, and SW developers are the drivers of a new kind of innovation and service delivery (Morris, 2016 ). This multi-sided platform-of-platforms model integrates the supply and demand side and can be seen to form a sharing economy. Wide adoption and maturity of business-to-business marketplaces are emerging for enterprises and IT in hyperscale cloud ecosystems. These developments will define the traction for telco exposure and abstraction with mobile in moving toward hybrid oblique business models. The oblique business model views 6G as a general-purpose technology and envisages network-as-a-code for developers. A loosely coupled oblique business model (Amit & Zott, 2015 ; Saebi & Foss, 2015 ) can be seen to follow the rationales of open innovation (Chesbrough, et al., 2014 ) and the timely concept of a sharing economy in which resource efficiency plays a crucial role (Stephany, 2015 ). In the 6G era, business models will not be built on one-sided technology or in industry silos, because it will be essential to consider the lifecycle stage of complementors, customers, and partners in the ecosystem. In a value-sharing economy, a cumulative, open-sourced effort of a community of developers will turn customers’, and ecosystems’ underutilized assets into more efficient or better used assets with fast-to-market strategies (Bogers & West, 2012 ; Chesbrough et al., 2014 ). Stakeholder interactions will aim to achieve common strategic objectives and eventually share a common fate and will no longer be based on customer–supplier relationships, (Iansiti & Levien, 2004 ). The oblique 6G business model characteristics will enable a novel born-platform approach, which will be a stand-alone multi-sided platform type of architecture building on a digital platform value proposition from the beginning of a new venture aiming at new market creation (Nambisan, 2017 ; Pundziene et al., 2022 ).
Implications
Despite the wide streams of platform and ecosystem business literature, little effort has been made to advance a coherent theory on hybrid ecosystemic platform-based business models that combines the characteristics of the both the transaction platforms focusing serving or mediating exchange and interactions (McIntyre & Srinivasan, 2017 , p. 143), and the innovation platform creating value through enabling innovations on the platform (Cusumano et al., 2020 ). 6G platforms can be seen as a composition of interacting subsystems that will always to some degree be interdependent and interoperate exclusively using predefined, stable interfaces (Eisenmann et al., 2006 ).
We emphasize the role of multi-sided platforms (Teece et al., 2022 ) to organize collaboration and control without owning the services whose exchange it inter-organizationally facilitates and governs. Moreover, the value co-creation (Saebi & Foss, 2015 ) by a compilation of peripheral enterprises connected to the platform via shared or open-source technologies or technology standardization (Cennamo & Santaló, 2013 ; Jacobides et al., 2018 ) will be seen in 6G. Similarly, the logic of value co-captured via sharing and distributing the revenue among ecosystem members, not only to capture by the focal enterprise can be envisioned (Oh et al., 2015 ; Upward & Jones, 2016 ; Zott et al., 2011 ).
The 6G ecosystem will be associated with both product and service systems (Tsujimoto et al., 2018 ), and both upstream and downstream value network actors, as well as related technologies and institutions with a varying degree of not fully hierarchically controlled multilateral, non-generic complementarities (Adner, 2017 ; Iansiti & Levien, 2004 ; Jacobides et al., 2018 ). This ecosystemic model will build upon customer-centricity (Weil & Woerner, 2015 ) and the dynamics of industry transformation, moving toward sustainable business, and can be viewed as an engine of social progress (Lüdeke-Freund et al., 2018 ), while the value-in-exchange may be captured on multiple levels (Lepak et al., 2007 ). The discussion above leads to the proposition of seeing ecosystem and platform concepts to be intertwined and thus defines a 6G ecosystemic platform-based business model as follows: An ecosystemic platform-based business model will connect various sides of multi-sided markets to facilitate value co-creation , co-capture, and sharing on multiple levels over a platform that facilitates interaction between users to collectively create innovations via matching, complementing, or sharing their resources sustainably .
Bibliography
Adner, R. (2017). Ecosystem as structure: An actionable construct for strategy. Journal of Management, 43 (1), 39–58.
Article Google Scholar
Ahokangas, P., Atkova, I., Yrjölä, S., & Matinmikko-Blue, M. (2023). Business model theory and the becoming of mobile communications technologies. In A. Aagaard, & C. Nielsen (Eds.), BMI game changers . Palgrave MacMillan.
Google Scholar
Ahokangas, P., Matinmikko, M., Yrjola, S., Okkonen, H., & Casey, T. (2013). Simple rules for mobile network operators’ strategic choices in future cognitive spectrum sharing networks. IEEE Wireless Communications Magazine, 20 , 20–26.
Ahokangas, P., Matinmikko-Blue, M., Yrjölä, S., Seppänen, V., Hämmäinen, H., Jurva, R., & Latva-aho, M. (2019). Business models for local 5G micro operators. IEEE Transactions on Cognitive Communications and Networking, 5 (3), 730–740.
Amit, R., & Zott, C. (2015). Crafting business architecture: The antecedents of business model design. Strategic Entrepreneurship Journal, 9 (4), 331–350.
Anker, P. (2017). From spectrum management to spectrum governance. Telecommunications Policy, 41 (5–6), 486–497.
Ballon, B. (2007). Business modelling revisited: The configuration of control and value. Info, 9 (5), 6–19.
Basole, R. C., & Karla, J. (2011). On the evolution of mobile platform ecosystem structure and strategy. Business & Information Systems Engineering, 3 (5), 313.
Bennett, N., & Lemoine, G. J. (2014). What a difference a word makes: Understanding threats to performance in a VUCA world. Business Horizons, 57 (3), 311–317.
Bogers, M., & West, J. (2012). Managing distributed innovation: Strategic utilization of open and user innovation. Creativity and Innovation Management, 21 (1), 61–75.
Buckley, P. (2019). International business in a VUCA world: The changing role of states and firms . Emerald Group Publishing.
Cave, M. (2018). How disruptive is 5G? Telecommunications Policy, 42 (8), 653–658.
Camps-Aragó, P., Delaere, S., & Ballon, P. (2019). 5G business models: Evolving mobile network operator roles in new ecosystems. Smart Cities & Information and Communication Technology (CTTE-FITCE) , 1–6.
Cennamo, C., & Santaló, J. (2013). Platform competition: Strategic trade, tradeoffs in platform markets. Strategic Management Journal, 34 (11), 1331–1350.
Chen, W., Montojo, J., Lee, J., Shafi, M., & Kim, Y. (2022). The standardization of 5G-Advanced in 3GPP. IEEE Communications Magazine, 60 (11), 98–104.
Chesbrough, H., Vanhaverbeke, W., & West, J. (2014). New frontiers in open innovation . Oxford University Press.
Book Google Scholar
Chin, W. (2019). Technology, war and the state: Past, present and future. International Affairs, 95 (4), 765–783.
Cusumano, M. A., Gawer, A., & Yoffie, D. B. (2019). The business of platforms: Strategy in the age of digital competition, innovation, and power . Harper Business.
Cusumano, M. A., Yoffie, D. B., & Gawer, A. (2020). The future of platforms. MIT Sloan Management Review, 61 (1), 26–34.
David, K., & Berndt, H. (2018). 6G vision and requirements: Is there any need for beyond 5G? IEEE Vehicular Technology Magazine, 13 (3), 72–80.
Eisenmann, T., Parker, G., & Van Alstyne, M. W. (2006). Strategies for two-sided markets. Harvard Business Review, 84 (10), 92.
Evans, P. C., & Gawer, A. (2016). The rise of the platform enterprise: A global survey . Center for Global Enterprise.
Ghosh, A., Maeder, A., Baker, M., & Chandramouli, D. (2019). 5G evolution: A view on 5G cellular technology beyond 3GPP release 15. IEEE Access, 7 , 127639–127651.
Hmoud, A. Y., Salim, J., & Yaakub, M. R. (2020). Platformisation of mobile operators business model: A proposition using design science approach and grounded theory principles. International Journal on Advanced Science Engineering Information Technology, 10 (2), 473–484.
Iansiti, M., & Levien, R. (2004). The keystone advantage: What the new dynamics of business ecosystems mean for strategy, innovation, and sustainability . Harvard Business Press.
ITU-R. (2020). IMT Vision—Framework and overall objectives of the future development of IMT for 2020 and beyond. International Telecommunication Union Radiocommunication Sector. https://www.itu.int/rec/R-REC-M.2083-0-201509-I .
ITU-R. (2022). Future technology trends of terrestrial International Mobile Telecommunications systems towards 2030 and beyond . International Telecommunication Union Radiocommunication Sector. https://www.itu.int/pub/R-REP-M.2516 .
Jacobides, M. G., Cennamo, C., & Gawer, A. (2018). Towards a theory of ecosystems. Strategic Management Journal, 39 (8), 2255–2276.
Kaloxylos, A., Gavras, A., Camps, D., Ghoraishi, M., & Hrasnica, H. (2021). AI and ML–Enablers for beyond 5G Networks . https://www.recercat.cat/bitstream/handle/2072/522533/AI-MLforNetworks-v1-0.pdf?sequence=1 .
Kilkki, K., Mäntylä, M., Karhu, K., Hämmäinen, H., & Ailisto, H. (2018). A disruption framework. Technological Forecasting and Social Change, 129 , 275–284.
Klement, J. (2021). Geo-economics: The interplay between geopolitics, economics, and investments . https://www.cfainstitute.org/-/media/documents/book/rf-publication/2021/geo-economics-full.pdf .
Latva-aho, M., & Leppänen, K. (2019). Key Drivers and Research Challenges for 6G Ubiquitous Wireless Intelligence [White paper]. University of Oulu. https://www.6gflagship.com/key-drivers-and-research-challenges-for-6g-ubiquitous-wireless-intelligence/ .
Lepak, D. P., Smith, K. G., & Taylor, M. S. (2007). Value creation and value capture: A multilevel perspective. Academy of Management Review, 32 (1), 180–194.
Lin, X. (2022). An overview of 5G advanced evolution in 3GPP release 18. IEEE Communications Standards Magazine, 6 (3), 77–83.
Lüdeke-Freund, F., Carroux, S., Joyce, A., Massa, L., & Breuer, H. (2018). The sustainable business model pattern taxonomy—45 patterns to support sustainability-oriented business model innovation. Sustainable Production and Consumption, 15 , 145–162.
Lukin, A. (2019). The US–China trade war and China’s strategic future. Survival, 61 (1), 23–50.
Matinmikko, M., Mustonen, M., Roberson, D., Paavola, J., Höyhtyä, M., Yrjölä, S., & Röning, J. (2014). Overview and comparison of recent spectrum sharing approaches in regulation and research: From opportunistic unlicensed access towards licensed shared access. IEEE DySPAN, McLean, VA, USA, 2014 , 92–102.
Matinmikko, M., Latva-aho, M., Ahokangas, P., Yrjölä, S., & Koivumäki, T. (2017). Micro operators to boost local service delivery in 5G. Wireless Personal Communications, 95 , 69–82.
Matinmikko, M., Latva-aho, M., Ahokangas, P., & Seppänen, V. (2018). On regulations for 5G: Micro licensing for locally operated networks. Telecommunications Policy, 42 (8), 622–635.
McIntyre, D. P., & Srinivasan, A. (2017). Networks, platforms, and strategy: Emerging views and next steps. Strategic Management Journal, 38 (1), 141–160.
Millar, C. C., Groth, O., & Mahon, J. F. (2018). Management innovation in a VUCA world: Challenges and recommendations. California Management Review, 61 (1), 5–14.
Moerel, L., & Timmers, P. (2021). Reflections on digital sovereignty . https://eucd.s3.eu-central-1.amazonaws.com/eucd/assets/khGGovSY/rif_timmersmoerel-final-for-publication.pdf .
Morris, K. (2016). Infrastructure as code: managing servers in the cloud . O’Reilly Media, Inc.
Nakamura, T. (2020, June). 5G Evolution and 6G. In 2020 IEEE symposium on VLSI technology (pp. 1–5). IEEE.
Nambisan, S. (2017). Digital entrepreneurship: Toward a digital technology perspective of entrepreneurship. Entrepreneurship Theory and Practice, 41 (6), 1029–1055.
Oh, J., Koh, B., & Raghunathan, S. (2015). Value appropriation between the platform provider and app developers in mobile platform mediated networks. Journal of Information Technology, 30 (3), 245–259.
Parkvall, S., Dahlman, E., Furuskar, A., & Frenne, M. (2017). NR: The new 5G radio access technology. IEEE Communications Standards Magazine, 1 (4), 24–30.
Petricevic, O., & Teece, D. J. (2019). The structural reshaping of globalization: Implications for strategic sectors, profiting from innovation, and the multinational enterprise. Journal of International Business Studies, 50 (9), 1487–1512.
Pujol, F., Elayoubi, S. E., Markendahl, J., & Salahaldin, L. (2016). Mobile telecommunications ecosystem evolutions with 5G. Communications & Strategies, 102 , 109.
Pundziene, A., Gutmann, T., Schlichtner, M., & Teece, D. J. (2022). Value impedance and dynamic capabilities: The case of medtech íncumbent-born digital healthcare platforms. California Management Review, 64 (4), 108–134.
Saebi, T., & Foss, N. J. (2015). Business models for open innovation: Matching heterogenous open innovation strategies with business model dimensions. European Management Journal, 33 (3), 201–213.
Stephany, A. (2015). The business of sharing: Making it in the new sharing economy . Palgrave MacMillan.
Teece, D. J. (2019). 5G and the global economy: How static competition policy frameworks can defeat open innovation . https://static1.squarespace.com/static/5a83233eb0786912d9c89545/t/5d9cbc3217af3e320d97270a/1570552889394/CPI_Antitrust_5GGlobalEcon_Sept2019.pdf .
Teece, D. J., Pundziene, A., Heaton, S., & Vadi, M. (2022). Managing multi-sided platforms: Platform origins and go-to-market strategy. California Management Review, 64 (4), 5–19.
Tsujimoto, M., Kajikawa, Y., Tomita, J., & Matsumoto, Y. (2018). A review of the ecosystem concept—towards coherent ecosystem design. Technological Forecasting and Social Change, 136 , 49–58.
The United States government (2020). The Clean Network . https://2017-2021.state.gov/the-clean-network/index.html .
Upward, A., & Jones, P. (2016). An ontology for strongly sustainable business models: Defining an enterprise framework compatible with natural and social science. Organization & Environment, 29 (1), 97–123.
Weill, P., & Woerner, S. L. (2015). Thriving in an increasingly digital ecosystem. MIT Sloan Management Review, 56 (4), 27.
Wirtz, B.W., Schilke, O., & Ullrich, S. (2010). Strategic development of business models: Implications of the web 2.0 for creating value on the internet. Long Range Planning , 43 (2–3), 272–290.
Yrjölä, S., Ahokangas, P., & Matinmikko-Blue, M. (2021). Platform-based business models in future mobile operator business. Journal of Business Models, 9 (4), 67–93.
Yrjölä, S., Ahokangas, P., & Matinmikko-Blue, M. (2022). Value creation and capture from technology innovation in the 6G Era. IEEE Access, 10 , 16299–16319.
Zhang, J., & Liang, X. J. (2011). Business ecosystem strategies of mobile network operators in the 3G era: The case of China Mobile. Telecommunications Policy, 35 (2), 156–171.
Zott, C., Amit, R., & Massa, L. (2011). The business model: Recent developments and future research. Journal of Management, 37 (4), 1019–1042.
Download references
Author information
Authors and affiliations.
Centre for Wireless Communications, University of Oulu, Oulu, Finland
Seppo Yrjölä
Nokia, Oulu, Finland
Infotech Oulu Focus Institute and Centre for Wireless Communications, University of Oulu, Oulu, Finland
Marja Matinmikko-Blue
Martti Ahtisaari Institute, Oulu Business School, University of Oulu, Oulu, Finland
Petri Ahokangas
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Seppo Yrjölä .
Editor information
Editors and affiliations.
Martti Ahtisaari Institute, University of Oulu, Oulu, Finland
Department of Management, Aarhus University, Aarhus, Denmark
Annabeth Aagaard
Rights and permissions
Open Access This chapter is licensed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made.
The images or other third party material in this chapter are included in the chapter's Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the chapter's Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
Reprints and permissions
Copyright information
© 2024 The Author(s)
About this chapter
Yrjölä, S., Matinmikko-Blue, M., Ahokangas, P. (2024). The Evolution of Mobile Communications. In: Ahokangas, P., Aagaard, A. (eds) The Changing World of Mobile Communications. Palgrave Macmillan, Cham. https://doi.org/10.1007/978-3-031-33191-6_2
Download citation
DOI : https://doi.org/10.1007/978-3-031-33191-6_2
Published : 18 October 2023
Publisher Name : Palgrave Macmillan, Cham
Print ISBN : 978-3-031-33190-9
Online ISBN : 978-3-031-33191-6
eBook Packages : Business and Management Business and Management (R0)
Share this chapter
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Publish with us
Policies and ethics
- Find a journal
- Track your research
- Search Menu
Sign in through your institution
- Browse content in Arts and Humanities
- Browse content in Archaeology
- Anglo-Saxon and Medieval Archaeology
- Archaeological Methodology and Techniques
- Archaeology by Region
- Archaeology of Religion
- Archaeology of Trade and Exchange
- Biblical Archaeology
- Contemporary and Public Archaeology
- Environmental Archaeology
- Historical Archaeology
- History and Theory of Archaeology
- Industrial Archaeology
- Landscape Archaeology
- Mortuary Archaeology
- Prehistoric Archaeology
- Underwater Archaeology
- Zooarchaeology
- Browse content in Architecture
- Architectural Structure and Design
- History of Architecture
- Residential and Domestic Buildings
- Theory of Architecture
- Browse content in Art
- Art Subjects and Themes
- History of Art
- Industrial and Commercial Art
- Theory of Art
- Biographical Studies
- Byzantine Studies
- Browse content in Classical Studies
- Classical Literature
- Classical Reception
- Classical History
- Classical Philosophy
- Classical Mythology
- Classical Art and Architecture
- Classical Oratory and Rhetoric
- Greek and Roman Papyrology
- Greek and Roman Archaeology
- Greek and Roman Epigraphy
- Greek and Roman Law
- Late Antiquity
- Religion in the Ancient World
- Digital Humanities
- Browse content in History
- Colonialism and Imperialism
- Diplomatic History
- Environmental History
- Genealogy, Heraldry, Names, and Honours
- Genocide and Ethnic Cleansing
- Historical Geography
- History by Period
- History of Emotions
- History of Agriculture
- History of Education
- History of Gender and Sexuality
- Industrial History
- Intellectual History
- International History
- Labour History
- Legal and Constitutional History
- Local and Family History
- Maritime History
- Military History
- National Liberation and Post-Colonialism
- Oral History
- Political History
- Public History
- Regional and National History
- Revolutions and Rebellions
- Slavery and Abolition of Slavery
- Social and Cultural History
- Theory, Methods, and Historiography
- Urban History
- World History
- Browse content in Language Teaching and Learning
- Language Learning (Specific Skills)
- Language Teaching Theory and Methods
- Browse content in Linguistics
- Applied Linguistics
- Cognitive Linguistics
- Computational Linguistics
- Forensic Linguistics
- Grammar, Syntax and Morphology
- Historical and Diachronic Linguistics
- History of English
- Language Evolution
- Language Reference
- Language Variation
- Language Families
- Language Acquisition
- Lexicography
- Linguistic Anthropology
- Linguistic Theories
- Linguistic Typology
- Phonetics and Phonology
- Psycholinguistics
- Sociolinguistics
- Translation and Interpretation
- Writing Systems
- Browse content in Literature
- Bibliography
- Children's Literature Studies
- Literary Studies (Romanticism)
- Literary Studies (American)
- Literary Studies (Modernism)
- Literary Studies (Asian)
- Literary Studies (European)
- Literary Studies (Eco-criticism)
- Literary Studies - World
- Literary Studies (1500 to 1800)
- Literary Studies (19th Century)
- Literary Studies (20th Century onwards)
- Literary Studies (African American Literature)
- Literary Studies (British and Irish)
- Literary Studies (Early and Medieval)
- Literary Studies (Fiction, Novelists, and Prose Writers)
- Literary Studies (Gender Studies)
- Literary Studies (Graphic Novels)
- Literary Studies (History of the Book)
- Literary Studies (Plays and Playwrights)
- Literary Studies (Poetry and Poets)
- Literary Studies (Postcolonial Literature)
- Literary Studies (Queer Studies)
- Literary Studies (Science Fiction)
- Literary Studies (Travel Literature)
- Literary Studies (War Literature)
- Literary Studies (Women's Writing)
- Literary Theory and Cultural Studies
- Mythology and Folklore
- Shakespeare Studies and Criticism
- Browse content in Media Studies
- Browse content in Music
- Applied Music
- Dance and Music
- Ethics in Music
- Ethnomusicology
- Gender and Sexuality in Music
- Medicine and Music
- Music Cultures
- Music and Media
- Music and Culture
- Music and Religion
- Music Education and Pedagogy
- Music Theory and Analysis
- Musical Scores, Lyrics, and Libretti
- Musical Structures, Styles, and Techniques
- Musicology and Music History
- Performance Practice and Studies
- Race and Ethnicity in Music
- Sound Studies
- Browse content in Performing Arts
- Browse content in Philosophy
- Aesthetics and Philosophy of Art
- Epistemology
- Feminist Philosophy
- History of Western Philosophy
- Metaphysics
- Moral Philosophy
- Non-Western Philosophy
- Philosophy of Language
- Philosophy of Mind
- Philosophy of Perception
- Philosophy of Action
- Philosophy of Law
- Philosophy of Religion
- Philosophy of Science
- Philosophy of Mathematics and Logic
- Practical Ethics
- Social and Political Philosophy
- Browse content in Religion
- Biblical Studies
- Christianity
- East Asian Religions
- History of Religion
- Judaism and Jewish Studies
- Qumran Studies
- Religion and Education
- Religion and Health
- Religion and Politics
- Religion and Science
- Religion and Law
- Religion and Art, Literature, and Music
- Religious Studies
- Browse content in Society and Culture
- Cookery, Food, and Drink
- Cultural Studies
- Customs and Traditions
- Ethical Issues and Debates
- Hobbies, Games, Arts and Crafts
- Natural world, Country Life, and Pets
- Popular Beliefs and Controversial Knowledge
- Sports and Outdoor Recreation
- Technology and Society
- Travel and Holiday
- Visual Culture
- Browse content in Law
- Arbitration
- Browse content in Company and Commercial Law
- Commercial Law
- Company Law
- Browse content in Comparative Law
- Systems of Law
- Competition Law
- Browse content in Constitutional and Administrative Law
- Government Powers
- Judicial Review
- Local Government Law
- Military and Defence Law
- Parliamentary and Legislative Practice
- Construction Law
- Contract Law
- Browse content in Criminal Law
- Criminal Procedure
- Criminal Evidence Law
- Sentencing and Punishment
- Employment and Labour Law
- Environment and Energy Law
- Browse content in Financial Law
- Banking Law
- Insolvency Law
- History of Law
- Human Rights and Immigration
- Intellectual Property Law
- Browse content in International Law
- Private International Law and Conflict of Laws
- Public International Law
- IT and Communications Law
- Jurisprudence and Philosophy of Law
- Law and Society
- Law and Politics
- Browse content in Legal System and Practice
- Courts and Procedure
- Legal Skills and Practice
- Primary Sources of Law
- Regulation of Legal Profession
- Medical and Healthcare Law
- Browse content in Policing
- Criminal Investigation and Detection
- Police and Security Services
- Police Procedure and Law
- Police Regional Planning
- Browse content in Property Law
- Personal Property Law
- Study and Revision
- Terrorism and National Security Law
- Browse content in Trusts Law
- Wills and Probate or Succession
- Browse content in Medicine and Health
- Browse content in Allied Health Professions
- Arts Therapies
- Clinical Science
- Dietetics and Nutrition
- Occupational Therapy
- Operating Department Practice
- Physiotherapy
- Radiography
- Speech and Language Therapy
- Browse content in Anaesthetics
- General Anaesthesia
- Neuroanaesthesia
- Clinical Neuroscience
- Browse content in Clinical Medicine
- Acute Medicine
- Cardiovascular Medicine
- Clinical Genetics
- Clinical Pharmacology and Therapeutics
- Dermatology
- Endocrinology and Diabetes
- Gastroenterology
- Genito-urinary Medicine
- Geriatric Medicine
- Infectious Diseases
- Medical Toxicology
- Medical Oncology
- Pain Medicine
- Palliative Medicine
- Rehabilitation Medicine
- Respiratory Medicine and Pulmonology
- Rheumatology
- Sleep Medicine
- Sports and Exercise Medicine
- Community Medical Services
- Critical Care
- Emergency Medicine
- Forensic Medicine
- Haematology
- History of Medicine
- Browse content in Medical Skills
- Clinical Skills
- Communication Skills
- Nursing Skills
- Surgical Skills
- Medical Ethics
- Browse content in Medical Dentistry
- Oral and Maxillofacial Surgery
- Paediatric Dentistry
- Restorative Dentistry and Orthodontics
- Surgical Dentistry
- Medical Statistics and Methodology
- Browse content in Neurology
- Clinical Neurophysiology
- Neuropathology
- Nursing Studies
- Browse content in Obstetrics and Gynaecology
- Gynaecology
- Occupational Medicine
- Ophthalmology
- Otolaryngology (ENT)
- Browse content in Paediatrics
- Neonatology
- Browse content in Pathology
- Chemical Pathology
- Clinical Cytogenetics and Molecular Genetics
- Histopathology
- Medical Microbiology and Virology
- Patient Education and Information
- Browse content in Pharmacology
- Psychopharmacology
- Browse content in Popular Health
- Caring for Others
- Complementary and Alternative Medicine
- Self-help and Personal Development
- Browse content in Preclinical Medicine
- Cell Biology
- Molecular Biology and Genetics
- Reproduction, Growth and Development
- Primary Care
- Professional Development in Medicine
- Browse content in Psychiatry
- Addiction Medicine
- Child and Adolescent Psychiatry
- Forensic Psychiatry
- Learning Disabilities
- Old Age Psychiatry
- Psychotherapy
- Browse content in Public Health and Epidemiology
- Epidemiology
- Public Health
- Browse content in Radiology
- Clinical Radiology
- Interventional Radiology
- Nuclear Medicine
- Radiation Oncology
- Reproductive Medicine
- Browse content in Surgery
- Cardiothoracic Surgery
- Gastro-intestinal and Colorectal Surgery
- General Surgery
- Neurosurgery
- Paediatric Surgery
- Peri-operative Care
- Plastic and Reconstructive Surgery
- Surgical Oncology
- Transplant Surgery
- Trauma and Orthopaedic Surgery
- Vascular Surgery
- Browse content in Science and Mathematics
- Browse content in Biological Sciences
- Aquatic Biology
- Biochemistry
- Bioinformatics and Computational Biology
- Developmental Biology
- Ecology and Conservation
- Evolutionary Biology
- Genetics and Genomics
- Microbiology
- Molecular and Cell Biology
- Natural History
- Plant Sciences and Forestry
- Research Methods in Life Sciences
- Structural Biology
- Systems Biology
- Zoology and Animal Sciences
- Browse content in Chemistry
- Analytical Chemistry
- Computational Chemistry
- Crystallography
- Environmental Chemistry
- Industrial Chemistry
- Inorganic Chemistry
- Materials Chemistry
- Medicinal Chemistry
- Mineralogy and Gems
- Organic Chemistry
- Physical Chemistry
- Polymer Chemistry
- Study and Communication Skills in Chemistry
- Theoretical Chemistry
- Browse content in Computer Science
- Artificial Intelligence
- Computer Architecture and Logic Design
- Game Studies
- Human-Computer Interaction
- Mathematical Theory of Computation
- Programming Languages
- Software Engineering
- Systems Analysis and Design
- Virtual Reality
- Browse content in Computing
- Business Applications
- Computer Games
- Computer Security
- Computer Networking and Communications
- Digital Lifestyle
- Graphical and Digital Media Applications
- Operating Systems
- Browse content in Earth Sciences and Geography
- Atmospheric Sciences
- Environmental Geography
- Geology and the Lithosphere
- Maps and Map-making
- Meteorology and Climatology
- Oceanography and Hydrology
- Palaeontology
- Physical Geography and Topography
- Regional Geography
- Soil Science
- Urban Geography
- Browse content in Engineering and Technology
- Agriculture and Farming
- Biological Engineering
- Civil Engineering, Surveying, and Building
- Electronics and Communications Engineering
- Energy Technology
- Engineering (General)
- Environmental Science, Engineering, and Technology
- History of Engineering and Technology
- Mechanical Engineering and Materials
- Technology of Industrial Chemistry
- Transport Technology and Trades
- Browse content in Environmental Science
- Applied Ecology (Environmental Science)
- Conservation of the Environment (Environmental Science)
- Environmental Sustainability
- Environmentalist Thought and Ideology (Environmental Science)
- Management of Land and Natural Resources (Environmental Science)
- Natural Disasters (Environmental Science)
- Nuclear Issues (Environmental Science)
- Pollution and Threats to the Environment (Environmental Science)
- Social Impact of Environmental Issues (Environmental Science)
- History of Science and Technology
- Browse content in Materials Science
- Ceramics and Glasses
- Composite Materials
- Metals, Alloying, and Corrosion
- Nanotechnology
- Browse content in Mathematics
- Applied Mathematics
- Biomathematics and Statistics
- History of Mathematics
- Mathematical Education
- Mathematical Finance
- Mathematical Analysis
- Numerical and Computational Mathematics
- Probability and Statistics
- Pure Mathematics
- Browse content in Neuroscience
- Cognition and Behavioural Neuroscience
- Development of the Nervous System
- Disorders of the Nervous System
- History of Neuroscience
- Invertebrate Neurobiology
- Molecular and Cellular Systems
- Neuroendocrinology and Autonomic Nervous System
- Neuroscientific Techniques
- Sensory and Motor Systems
- Browse content in Physics
- Astronomy and Astrophysics
- Atomic, Molecular, and Optical Physics
- Biological and Medical Physics
- Classical Mechanics
- Computational Physics
- Condensed Matter Physics
- Electromagnetism, Optics, and Acoustics
- History of Physics
- Mathematical and Statistical Physics
- Measurement Science
- Nuclear Physics
- Particles and Fields
- Plasma Physics
- Quantum Physics
- Relativity and Gravitation
- Semiconductor and Mesoscopic Physics
- Browse content in Psychology
- Affective Sciences
- Clinical Psychology
- Cognitive Psychology
- Cognitive Neuroscience
- Criminal and Forensic Psychology
- Developmental Psychology
- Educational Psychology
- Evolutionary Psychology
- Health Psychology
- History and Systems in Psychology
- Music Psychology
- Neuropsychology
- Organizational Psychology
- Psychological Assessment and Testing
- Psychology of Human-Technology Interaction
- Psychology Professional Development and Training
- Research Methods in Psychology
- Social Psychology
- Browse content in Social Sciences
- Browse content in Anthropology
- Anthropology of Religion
- Human Evolution
- Medical Anthropology
- Physical Anthropology
- Regional Anthropology
- Social and Cultural Anthropology
- Theory and Practice of Anthropology
- Browse content in Business and Management
- Business Ethics
- Business History
- Business Strategy
- Business and Technology
- Business and Government
- Business and the Environment
- Comparative Management
- Corporate Governance
- Corporate Social Responsibility
- Entrepreneurship
- Health Management
- Human Resource Management
- Industrial and Employment Relations
- Industry Studies
- Information and Communication Technologies
- International Business
- Knowledge Management
- Management and Management Techniques
- Operations Management
- Organizational Theory and Behaviour
- Pensions and Pension Management
- Public and Nonprofit Management
- Strategic Management
- Supply Chain Management
- Browse content in Criminology and Criminal Justice
- Criminal Justice
- Criminology
- Forms of Crime
- International and Comparative Criminology
- Youth Violence and Juvenile Justice
- Development Studies
- Browse content in Economics
- Agricultural, Environmental, and Natural Resource Economics
- Asian Economics
- Behavioural Finance
- Behavioural Economics and Neuroeconomics
- Econometrics and Mathematical Economics
- Economic History
- Economic Methodology
- Economic Systems
- Economic Development and Growth
- Financial Markets
- Financial Institutions and Services
- General Economics and Teaching
- Health, Education, and Welfare
- History of Economic Thought
- International Economics
- Labour and Demographic Economics
- Law and Economics
- Macroeconomics and Monetary Economics
- Microeconomics
- Public Economics
- Urban, Rural, and Regional Economics
- Welfare Economics
- Browse content in Education
- Adult Education and Continuous Learning
- Care and Counselling of Students
- Early Childhood and Elementary Education
- Educational Equipment and Technology
- Educational Strategies and Policy
- Higher and Further Education
- Organization and Management of Education
- Philosophy and Theory of Education
- Schools Studies
- Secondary Education
- Teaching of a Specific Subject
- Teaching of Specific Groups and Special Educational Needs
- Teaching Skills and Techniques
- Browse content in Environment
- Applied Ecology (Social Science)
- Climate Change
- Conservation of the Environment (Social Science)
- Environmentalist Thought and Ideology (Social Science)
- Natural Disasters (Environment)
- Social Impact of Environmental Issues (Social Science)
- Browse content in Human Geography
- Cultural Geography
- Economic Geography
- Political Geography
- Browse content in Interdisciplinary Studies
- Communication Studies
- Museums, Libraries, and Information Sciences
- Browse content in Politics
- African Politics
- Asian Politics
- Chinese Politics
- Comparative Politics
- Conflict Politics
- Elections and Electoral Studies
- Environmental Politics
- Ethnic Politics
- European Union
- Foreign Policy
- Gender and Politics
- Human Rights and Politics
- Indian Politics
- International Relations
- International Organization (Politics)
- International Political Economy
- Irish Politics
- Latin American Politics
- Middle Eastern Politics
- Political Behaviour
- Political Economy
- Political Institutions
- Political Theory
- Political Methodology
- Political Communication
- Political Philosophy
- Political Sociology
- Politics and Law
- Politics of Development
- Public Policy
- Public Administration
- Quantitative Political Methodology
- Regional Political Studies
- Russian Politics
- Security Studies
- State and Local Government
- UK Politics
- US Politics
- Browse content in Regional and Area Studies
- African Studies
- Asian Studies
- East Asian Studies
- Japanese Studies
- Latin American Studies
- Middle Eastern Studies
- Native American Studies
- Scottish Studies
- Browse content in Research and Information
- Research Methods
- Browse content in Social Work
- Addictions and Substance Misuse
- Adoption and Fostering
- Care of the Elderly
- Child and Adolescent Social Work
- Couple and Family Social Work
- Direct Practice and Clinical Social Work
- Emergency Services
- Human Behaviour and the Social Environment
- International and Global Issues in Social Work
- Mental and Behavioural Health
- Social Justice and Human Rights
- Social Policy and Advocacy
- Social Work and Crime and Justice
- Social Work Macro Practice
- Social Work Practice Settings
- Social Work Research and Evidence-based Practice
- Welfare and Benefit Systems
- Browse content in Sociology
- Childhood Studies
- Community Development
- Comparative and Historical Sociology
- Economic Sociology
- Gender and Sexuality
- Gerontology and Ageing
- Health, Illness, and Medicine
- Marriage and the Family
- Migration Studies
- Occupations, Professions, and Work
- Organizations
- Population and Demography
- Race and Ethnicity
- Social Theory
- Social Movements and Social Change
- Social Research and Statistics
- Social Stratification, Inequality, and Mobility
- Sociology of Religion
- Sociology of Education
- Sport and Leisure
- Urban and Rural Studies
- Browse content in Warfare and Defence
- Defence Strategy, Planning, and Research
- Land Forces and Warfare
- Military Administration
- Military Life and Institutions
- Naval Forces and Warfare
- Other Warfare and Defence Issues
- Peace Studies and Conflict Resolution
- Weapons and Equipment

The Oxford Handbook of Mobile Communication and Society

Rich Ling (PhD, University of Colorado) has focused his work on the social consequences of mobile communication. He was a professor at the IT University of Copenhagen, where he has served in department management, and he works at Telenor near Oslo, Norway. Ling has been the Pohs visiting professor of communication studies (2005) at the University of Michigan in Ann Arbor, where he has an adjunct position. He is the author of the book Taken for grantedness (2012 MIT Press), which was recently the subject of a complementary review in the journal Science. He has also written New tech, new ties (2008, MIT), The mobile connection (Morgan Kaufmann) and, along with Jonathan Donner, he has written the book Mobile phones and mobile communication (2009, Polity). Ling is a founding co-editor of the Sage journal Mobile Media and Communication. He is the co-editor of the Oxford University Press series Studies in Mobile Communication with Gerard Goggin and Leopoldina Fortunati. Along with Scott Campbell he is the founding editor of The Mobile Communication Research Series and he is an associate editor for The Information Society, The Journal of Computer Mediated Communication, and Information Technology and International Development.
Leopoldina Fortunati is a professor of sociology of communication and culture at the University of Udine, where she is the director of the Research Laboratory on New Media NuMe (nume.uniud.it). She is also a member of the Academia Europaea. For the past three decades, she has studied the role of mobile phones in societies. She has written or edited 21 books and published over 200 peer-reviewed papers and book chapters. She is associate editor of the journal The Information Society and a co-editor of the Oxford University Press series Studies in Mobile Communication. Her works have been published in 12 languages.
Gerard Goggin is the Wee Kim Wee Chair in Communication Studies at the Wee Kim Wee School of Communication and Information at Nanyang Technological University, Singapore. He is also professor of media and communications, University of Sydney. Goggin has published widely on mobile media and communication, with books including Cell Phone Culture (2006, Routledge), Global Mobile Media (2011, Routledge), Location Technology and Place (2012, Routledge), Routledge Companion to Mobile Media (2014, Routledge), Locative Media (2015, Routledge), Major Works: Mobile Technologies (2016), Routledge Companion to Global Internet Histories (2017, Routledge), Location Technologies in International Context (2019, Routledge), and Apps (2020).
Sun Sun Lim is professor of communication and technology and head of humanities, arts and social sciences at the Singapore University of Technology and Design. She studies the social implications of technology domestication by young people and families, charting the ethnographies of their internet and mobile phone use. She also investigates technology domestication writ large, focusing on digital literacy, user perceptions, and public understanding of pervasive ambient technologies deployed in smart cities. She has conducted extensive fieldwork in Asia including in China, Indonesia, Singapore, South Korea, and Vietnam, authoring over 70 articles, book chapters, and books. She serves on the editorial boards of 10 journals and serves actively on public bodies including the Media Literacy Council. Her latest book is Transcendent Parenting—Raising Children in the Mobile Age (forthcoming, Oxford University Press). See www.sunsunlim.com.
Yuling Li graduated from the Master of Mass Communication (MMC) program at Wee Kim Wee School of Communication and Information, Nanyang Technological University (NTU), in 2019. She received her bachelor of social science with honors in sociology from the National University of Singapore (NUS) in 2006. Her academic distinctions include being the recipient of the MMC Scholarship at NTU and her two-time placement on the dean’s list at NUS. Formerly a magazine editor, Yuling is currently a freelance writer, editor, researcher, and editorial consultant. She is also an associate lecturer at Republic Polytechnic, where she teaches communication and journalism modules. Her research interests include media sociology, mobile communication and culture, journalism, and social media. The co-editorship of the Oxford Handbook of Mobile Communication and Society and the co-authorship of the mobile photography chapter in the handbook are her latest scholarly contributions.
- Cite Icon Cite
- Permissions Icon Permissions
The smartphone has changed the dynamics of mobile communication in a multitude of ways. Earlier 2G phone facilitated point to point communication between individuals. With the development of 3G, we have seen the growth of the mobile internet and all that includes. Rather than simple dyadic communication, 3G and the smartphone have allowed multisided interaction as well as new forms of coordination, communication, consumption, and social interaction. The devices have given us access to news, information, shopping, and entertainment. In addition, they have facilitated threats to our privacy and cyberbullying. This book examines the evolving nature of mobile communication.
Signed in as
Institutional accounts.
- GoogleCrawler [DO NOT DELETE]
- Google Scholar Indexing
Personal account
- Sign in with email/username & password
- Get email alerts
- Save searches
- Purchase content
- Activate your purchase/trial code
- Add your ORCID iD
Institutional access
Sign in with a library card.
- Sign in with username/password
- Recommend to your librarian
- Institutional account management
- Get help with access
Access to content on Oxford Academic is often provided through institutional subscriptions and purchases. If you are a member of an institution with an active account, you may be able to access content in one of the following ways:
IP based access
Typically, access is provided across an institutional network to a range of IP addresses. This authentication occurs automatically, and it is not possible to sign out of an IP authenticated account.
Choose this option to get remote access when outside your institution. Shibboleth/Open Athens technology is used to provide single sign-on between your institution’s website and Oxford Academic.
- Click Sign in through your institution.
- Select your institution from the list provided, which will take you to your institution's website to sign in.
- When on the institution site, please use the credentials provided by your institution. Do not use an Oxford Academic personal account.
- Following successful sign in, you will be returned to Oxford Academic.
If your institution is not listed or you cannot sign in to your institution’s website, please contact your librarian or administrator.
Enter your library card number to sign in. If you cannot sign in, please contact your librarian.
Society Members
Society member access to a journal is achieved in one of the following ways:
Sign in through society site
Many societies offer single sign-on between the society website and Oxford Academic. If you see ‘Sign in through society site’ in the sign in pane within a journal:
- Click Sign in through society site.
- When on the society site, please use the credentials provided by that society. Do not use an Oxford Academic personal account.
If you do not have a society account or have forgotten your username or password, please contact your society.
Sign in using a personal account
Some societies use Oxford Academic personal accounts to provide access to their members. See below.
A personal account can be used to get email alerts, save searches, purchase content, and activate subscriptions.
Some societies use Oxford Academic personal accounts to provide access to their members.
Viewing your signed in accounts
Click the account icon in the top right to:
- View your signed in personal account and access account management features.
- View the institutional accounts that are providing access.
Signed in but can't access content
Oxford Academic is home to a wide variety of products. The institutional subscription may not cover the content that you are trying to access. If you believe you should have access to that content, please contact your librarian.
For librarians and administrators, your personal account also provides access to institutional account management. Here you will find options to view and activate subscriptions, manage institutional settings and access options, access usage statistics, and more.
Our books are available by subscription or purchase to libraries and institutions.
- About Oxford Academic
- Publish journals with us
- University press partners
- What we publish
- New features
- Open access
- Rights and permissions
- Accessibility
- Advertising
- Media enquiries
- Oxford University Press
- Oxford Languages
- University of Oxford
Oxford University Press is a department of the University of Oxford. It furthers the University's objective of excellence in research, scholarship, and education by publishing worldwide
- Copyright © 2024 Oxford University Press
- Cookie settings
- Cookie policy
- Privacy policy
- Legal notice
This Feature Is Available To Subscribers Only
Sign In or Create an Account
This PDF is available to Subscribers Only
For full access to this pdf, sign in to an existing account, or purchase an annual subscription.

Essay on Impact Of Mobile Phones On Society
Students are often asked to write an essay on Impact Of Mobile Phones On Society in their schools and colleges. And if you’re also looking for the same, we have created 100-word, 250-word, and 500-word essays on the topic.
Let’s take a look…
100 Words Essay on Impact Of Mobile Phones On Society
Communication changes.
Mobile phones have changed the way we talk to each other. Before, we had to use landlines or write letters that took days to reach. Now, we can call or send a message to someone far away and they will know it in seconds. This makes keeping in touch with family and friends easier.
Information at Our Fingertips
With mobile phones, we can look up anything we want to know in an instant. They are like small computers that fit in our pockets. This means we can learn new things and find answers quickly, which is very helpful for school work and general knowledge.
Entertainment Everywhere
Phones are not just for calls; they are also for fun. We can play games, watch videos, and listen to music whenever we want. This is great for passing time, but it can also make us spend too much time on our phones instead of playing outside or reading books.
Safety and Help
Mobile phones can help us feel safer. If we are in trouble or get lost, we can call for help. Parents can also check where their children are, which helps them worry less. But, it is important to remember that we should not share our location with strangers.
Changes in Manners
Mobile phones have also changed how we act in public. Sometimes people focus on their phones instead of talking to the people they are with. This can be rude and make others feel unimportant. It’s good to remember to put our phones away during meals and conversations.
250 Words Essay on Impact Of Mobile Phones On Society
Changes in communication.
Mobile phones have changed the way we talk to each other. Before, people would write letters or use landlines to chat. Now, with mobiles, we can send messages, make calls, and even see each other on video anytime and anywhere. This makes staying in touch with friends and family much easier.
Information at Your Fingertips
With mobile phones, we can look up facts, news, and other information quickly. They are like small computers in our pockets. We can learn new things, do schoolwork, and satisfy our curiosity just by tapping on the screen.
Mobile phones are not just for talking; they are also for fun. We can play games, listen to music, and watch videos. This means we can enjoy ourselves while waiting for a bus or during a break at school.
Mobile phones can make us feel safer. If we get lost or need help, we can call our family or the police. Parents also feel better knowing they can reach their children anytime.
Not Always Good
Even though mobile phones have many good points, they can also cause problems. People sometimes pay more attention to their phones than the world around them. This can make them less aware and even cause accidents.
In conclusion, mobile phones have a big effect on our lives. They help us communicate, learn, have fun, and stay safe. But it’s important to use them carefully and not let them distract us too much from real life.
500 Words Essay on Impact Of Mobile Phones On Society
Introduction to mobile phones.
Mobile phones have changed the world. These small devices that we carry in our pockets allow us to talk to anyone, anywhere, at any time. They have become a part of our daily lives. Many people cannot imagine a day without their phone. This essay talks about how mobile phones affect society.
Communication Made Easy
The first big change that mobile phones brought is in the way we talk to each other. Before mobile phones, we had to use landline phones that were stuck in one place. Now, we can call or send a message to our friends and family no matter where we are. This has made staying in touch with loved ones much easier.
Mobile phones give us access to a lot of information. With the internet on our phones, we can look up anything we want to know. This is very helpful for students who can now find facts for their homework easily. It’s also good for anyone who needs to find out something quickly.
Entertainment in Our Hands
Our phones are not just for talking or getting information. They are also for fun. We can play games, listen to music, or watch videos on our phones. This means we can have entertainment with us all the time. This is nice when we are waiting for something or when we want to relax.
Work Goes Mobile
Phones have also changed the way we work. Many jobs now allow people to use their phones to do their work. This means that some people can work from anywhere. They do not have to be in an office. This can make work more flexible, but it can also mean that people are working more since they can always be reached.
Mobile phones can keep us safe. If we are in trouble or get lost, we can call for help. Parents often feel better knowing their children have a phone with them. This way, they can call if there is a problem.
Problems Caused by Mobile Phones
Even though mobile phones have many good points, they can also cause problems. For example, people can spend too much time on their phones and not enough time talking to people face to face. This can hurt relationships. Also, using phones too much can be bad for our health, like causing eye strain or bad posture.
In conclusion, mobile phones have a big impact on society. They make communication, getting information, working, and entertainment easier and better. They can also help keep us safe. But we must be careful not to let our phones take over our lives. We should remember to spend time with people in real life and not just on our phones. It is important to find a good balance.
That’s it! I hope the essay helped you.
If you’re looking for more, here are essays on other interesting topics:
- Essay on Dream House
- Essay on Impact Of Globalization On Economy
- Essay on Impact Of Drugs On Society
Apart from these, you can look at all the essays by clicking here .
Happy studying!
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.

Technological Generations of Mobile Communications Essay
- To find inspiration for your paper and overcome writer’s block
- As a source of information (ensure proper referencing)
- As a template for you assignment
Introduction
The distinct life of the mobile communications has taken different phases. This can be traced from the 1G to the most rest 4G. G, 2G, 3G and 4G are a wireless phone or a cellular phone standard way of classification based on generations/ cellular phone evolution. This paper is a critical comparison of all these technological generations with an aim of tracking the trend that is followed in the developments.
Grandpa and Grandma 1G
Grandpa and Grandma 1G was the very first generation of wireless technology that originated around 1980’s. The cellular phones of this time were big in size (handbag phones) and used a high power voltage. Communication in the first generation cellular phones was enhanced by use of analog radio waves/ signals; use of radio antennas (a radio transmitter on one end and receiver on the other end.
Analogue technology could only accommodate voice communication the passing of analogue signals. While this was the best technological developments at the time, it had a couple of limitations. The first generation wireless technology covered a relatively small area. Communication was only possible between parties of the same nation/within a nation’s boundary’s/ within the grounds of a particular nation (Fendelman).
This first generation wireless technology supports only one way communication at a time. For instance the intended recipient has to be calm till the sender finishes talking then he/she can begin answering incase he/she speaks before then, his/her message won’t be delivered.
All the above services are possible through a technology that interprets voice calls called circuit switching -Circuit switching is easily distorted by a simple physical noise thus destroying the quality of a conversation. All these limitations lead the players in the industry to look for more advanced technology which could fill the loopholes in communication (News from Rohde and Schwarz, 2002).
2G – The second generation of the wireless digital technology
1G was later thrown out/replaced by 2G that came with greater and better technological benefits like the additional data services. At this level people could send text messages on top of the voice communication they initially had.
The radio signals were digital and the conversations digitally encrypted unlike the initial analog. This therefore allowed the mobile phone services to be passed over a wider area (great service penetration levels).The wireless digital network use brings more voice clarity to the conversation being carried out.
This enhanced intercontinental communications, more privacy in communication as well as storage of communication. The messages sent through this technology could easily be referred to later.
The second generation phones are however, costly compared to the first generation wireless cellular phones. Unlike the first wireless technology where communications were only possible within a nation, 2G ventures into a wide area in terms of service coverage area due to the additional roaming facility.
3G – The third wireless telephone / cellular phone generation
The second generation is however overthrown by this third cellular phone evolution which uses a wide band width. This big band width in turn came with a more clear voice communication that is almost perfect (very minimal distractions and cases of eavesdropping- a situation where the signals sent are lost to the surrounding environment).
Communication in this case is possible through a technology packet switching; a situation where data is addressed like the IP addressing then sent over and on reaching its destination, its again recollects in the order sent then decoded/ interconnected to have the conversation (News from Rohde and Schwarz, 2002)..
3G wireless services are widely spread and now almost in all parts of the world. 3G has an added advantage of the global roaming facility which allows communication across the world. One can send text messages, video conference, and chat, download 3dimentional games, and talk to any one and anywhere in this world without distractions like they are having real conversation (News from Rohde and Schwarz , 2002).
3G uses a higher band width also a wide band voice channel compared to the 1G and 2G generations which greatly attributes to high voice clarity and people can talk without any disturbance or with very minimal distractions.
There is an additional multimedia facility brought about by this third generation cellular phones like very fast communication (conversations and text messaging), video conferencing (hold video meetings with people in different locations), internet (surfing/browsing/online chatting), mobile television (watch television’s favorite programs on phone), video calls (like Skye), multi media messaging service (MMS) (sharing of photos and music), etc are now available on 3G phones (Arshad, Farooq, Shah, 2010)
The 3G phones are costly compared to the first and second wireless cellular phone generation. Currently 3G is widely in use. Almost everyone is moving or has moved to 3G technology for its interesting features and high speed wireless service.
Despite the numerous advantages to using this kind of phone and very interesting features, 3G wireless telephones however have short battery life compared to the second and first generation phones. Thus the use of this technology is dependent on the proximity to power supply. In remote areas thus, persons are forced to use less advanced technologies to avoid frustrations.
However, some wireless technology users use both technologies concurrently (Arshad, Farooq, Shah, 2010). 3G technology is usually common for users who depend on the wireless communication in internetworking. Most of the service providers carry out promotional advertisements encouraging users to use the technology based on its speed and coverage.
4G – The fourth generation wireless telephones / cellular phone service also known as a complete 3G replacement.
4G operates more like 3G much as it is a step up from 3G. It appears to operate in a hopeful state, like providing its clients with very speedy wireless services. Being the new born baby this fourth generation wireless technology is availed in limited places/areas.
It’s not widely spread and only in use in very few regions like Japan. 4G is anticipated and designed to deliver very high speed internet and generally high wireless services. Also a high network capacity-allowing more people to operate/ access its resources simultaneously (Fendelman,).
They too have the multimedia added feature but with very clear voice and video output compared to the initial generations just like the normal television. The fourth generation cellular phones are damn expensive (high cost) compared to the previous generations. The costs mentioned here are the installation costs. However, the technological requires less maintenance costs.
Similarities
All the above mentioned technologies are wireless technologies. They all are able to pass/enhance analog communication. They all can pass voice communications. The first and Second generation covers a relatively small area in terms of geographical boundaries. Each of the technological development has come with increased area coverage than the preceding development.
Both the first and Second generation use a narrow band width, while the third and fourth generation uses wide band width. Both 1G and 2G deal/ are good in voice calls and in the process need to utilize the maximum bandwidth provided (Ashiho, 2003)
The technological development in the wireless communication has grown from one phase to another. As each phase is introduced, it leads to changes in other industries that depend on this technology for communication and other purposes. It is paramount to note that each of the above technologies has its own specifications.
Thus, there is always a need for any firm to have a technician who shall introduce the members of the institutions on how to operate the different technological developments. The ability of a firm to use the most modern technology is for its advantage as this leads to less maintenance costs. The only additional costs in the generational growth are the initial installation costs (Ashiho, 2003).
The developments that have been discussed in this paper have been enhanced by various firms and individuals. The need for the improvements has always rendered the players in the wireless communication busy with efforts of improving each of the development.
While the current technology is viewed by many as perfect, it is expected that a need will arise for the provision of services that it does not offer. Thus, it is arguable to conclude that the development in the wireless communication cannot be optimum.
Arshad, j., Farooq, A., Shah, A., (2010) Evolution and Development Towards 4th Generation (4G) Mobile Communication Systems . Web.
Ashiho, L. S. (2003). Mobile Technology: Evolution from 1G to 4G . Web.
Fendelman, A. (n.d). Cell Phone Glossary: What is 1G vs. 2G vs. 2.5G vs. 3G vs. 4G? Web.
News from Rohde and Schwarz (2002). Measuring the Acoustic Characteristics of 3G Mobile Phones . Web.
Peter, K. (n.d). Analysis and Comparison of 1G, 2G, 3G, 4G and 5G Telecom Services . Web.
- Comparison of 3G Wireless Networks to 4G Wireless Networks
- IPhone 3G: Reviev and Specifications
- Periodic Time and the Simple Length of the Pendulum
- Can Cell Phones Close Digital Divide?
- Blackberry Messenger and the Older People
- The best phone in the year 2013
- The Mobile Phone as an Electronic Wallet
- The Go-Phone by AT&T Company
- Chicago (A-D)
- Chicago (N-B)
IvyPanda. (2019, March 21). Technological Generations of Mobile Communications. https://ivypanda.com/essays/technological-generations/
"Technological Generations of Mobile Communications." IvyPanda , 21 Mar. 2019, ivypanda.com/essays/technological-generations/.
IvyPanda . (2019) 'Technological Generations of Mobile Communications'. 21 March.
IvyPanda . 2019. "Technological Generations of Mobile Communications." March 21, 2019. https://ivypanda.com/essays/technological-generations/.
1. IvyPanda . "Technological Generations of Mobile Communications." March 21, 2019. https://ivypanda.com/essays/technological-generations/.
Bibliography
IvyPanda . "Technological Generations of Mobile Communications." March 21, 2019. https://ivypanda.com/essays/technological-generations/.
Uses of Mobile Phones Essay for Students and Children
500+ words essay on uses of mobile phones.
Mobile phones are one of the most commonly used gadgets in today’s world. Everyone from a child to an adult uses mobile phones these days. They are indeed very useful and help us in so many ways.

Mobile phones indeed make our lives easy and convenient but at what cost? They are a blessing only till we use it correctly. As when we use them for more than a fixed time, they become harmful for us.
Uses of Mobile Phone
We use mobile phones for almost everything now. Gone are the days when we used them for only calling. Now, our lives revolve around it. They come in use for communicating through voice, messages, and mails. We can also surf the internet using a phone. Most importantly, we also click photos and record videos through our mobile’s camera.
The phones of this age are known as smartphones . They are no less than a computer and sometimes even more. You can video call people using this phone, and also manage your official documents. You get the chance to use social media and play music through it.
Moreover, we see how mobile phones have replaced computers and laptops . We carry out all the tasks through mobile phones which we initially did use our computers. We can even make powerpoint presentations on our phones and use it as a calculator to ease our work.
Get the huge list of more than 500 Essay Topics and Ideas
Disadvantages of Mobile Phones
While mobile phones are very beneficial, they also come to a lot of disadvantages. Firstly, they create a distance between people. As people spend time on their phones, they don’t talk to each other much. People will sit in the same room and be busy on their phones instead of talking to each other.
Subsequently, phones waste a lot of time. People get distracted by them easily and spend hours on their phones. They are becoming dumber while using smartphones . They do not do their work and focus on using phones.
Most importantly, mobile phones are a cause of many ailments. When we use phones for a long time, our eyesight gets weaker. They cause strain on our brains. We also suffer from headaches, watery eyes, sleeplessness and more.
Moreover, mobile phones have created a lack of privacy in people’s lives. As all your information is stored on your phone and social media , anyone can access it easily. We become vulnerable to hackers. Also, mobile phones consume a lot of money. They are anyway expensive and to top it, we buy expensive gadgets to enhance our user experience.
In short, we see how it is both a bane and a boon. It depends on us how we can use it to our advantage. We must limit our usage of mobile phones and not let it control us. As mobile phones are taking over our lives, we must know when to draw the line. After all, we are the owners and not the smartphone.
FAQs on Uses of Mobile Phones
Q.1 How do mobile phones help us?
A.1 Mobile phones are very advantageous. They help us in making our lives easy and convenient. They help us communicate with our loved ones and carry out our work efficiently. Furthermore, they also do the work of the computer, calculator, and cameras.
Q.2 What is the abuse of mobile phone use?
A.2 People are nowadays not using but abusing mobile phones. They are using them endlessly which is ruining their lives. They are the cause of many ailments. They distract us and keep us away from important work. Moreover, they also compromise with our privacy making us vulnerable to hackers.
Customize your course in 30 seconds
Which class are you in.

- Travelling Essay
- Picnic Essay
- Our Country Essay
- My Parents Essay
- Essay on Favourite Personality
- Essay on Memorable Day of My Life
- Essay on Knowledge is Power
- Essay on Gurpurab
- Essay on My Favourite Season
- Essay on Types of Sports

Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Download the App


Essay on Mobile Phone for Students [100, 150, 250, 400 Words]
Essay on Mobile Phone: Mobile Phone is a wonderful gift of science. In this article, you are going to learn to write an essay on Mobile Phone in English (100, 150, 250 and 400 Words). So, let’s get started.
Table of Contents
Essay on Mobile Phone: 100 Words
The mobile phone is one of the greatest gifts of modern science. It is also called cell phone or smart phone. It is a great medium of communication. In earlier times mobile phones were used only for communication. But now-a-days a mobile phone is used as an entertainment device. We can use it for watching videos, listening to music, capturing pictures, web browsing, calculating, navigating and many more purposes.
The mobile phone has many advantages but we should use it in moderation. Excessive use of mobile phones can affect our physical and mental health. Students often misuse it and their study is affected badly. We should use our mobile phones very wisely.

Mobile Phone Essay: 150 Words
The mobile phone is a miracle of science. From a minor student to an ordinary Worker, everyone possesses a cell phone. Indeed, this is a very popular item today. It is truly, a mark of modern living, a part of the modern life-style. Of course, its usefulness is undeniable. Now a man can have communication anywhere, anytime to anyone sitting thousands of kilometers from him.
Today it is not only a communication device. It can be used for a number of purposes like online ticket booking, navigation, playing video games, taking pictures, recording videos, web browsing, video calling etc. In fact, now we use mobile phone for taking online classes. Hence it is called a Smart Phone. At the same time, the excessive craze for this is not desirable and may even prove dangerous. Mobile phone is to be taken as an utility service, and not as a show-piece.

Also Read: Paragraph on Computer in English
Essay on Mobile Phone: 250 Words
A mobile phone or cell phone is a hand-held portable radiophone that uses the cellular or satellite network for voice or data communication. Unlike landline phones, which are fixed, mobile phones can be easily carried, and one can contact a person anywhere whether at home, on the bus, in street, or in a meeting. Apart from talking, it can be used for sending SMS, e-mail and for taking photos and videos.
High-end mobiles act as mini computers, offering services like internet, diary, music, iPod, calculator, alarm clock, etc. It is extremely useful in emergencies. But there is a tendency to abuse it. To many, it is an Addiction rather than a necessity. A cell phone ringing in an auditorium is most annoying. Using a mobile phone while driving a car or a motorbike and crossing a road or a railway track had led to many accidents.
Teleshopping is a great nuisance. Privacy is often violated, as most mobile users are unaware that they could be photographed or tracked. Terrorists use this gadget to trigger bombs and achieve their ends. Mobiles can also cause health hazards. The radiations from mobiles may cause injury to the brain. Cellphones on vibration mode put in front pocket may damage the heartbeat system. With all its advantages, what is, therefore, needed is moderation in the use of mobile phones.
Also Read: Essay on Television in English
Essay on Mobile Phones: 400 Words
When telephone was first introduced in the world in the 1950s, people were keenly interested in it. As an easier way of communication, telephone has its own merit. Of late, the introduction of mobiles makes an easy access to communication. It is in fact inevitable in the present day of hurry and business. People have warmly accepted mobiles as the blessing of science. There is little doubt that without the use of mobiles none is nowadays able to lead one’s life quite normally. One is capable of communicating with people, staying far away very quickly. Thus many a problem can be well- solved by way of using these mobiles.
But everything has its merit and demerit. As science is a bane as well as a boon, mobiles are to some extent to be cursed. People, especially the young generation, have been abusing mobiles. They not only chat in an unexpected way but also indulge themselves in leading immoral life by abusing mobiles. Apart from this, several mercenary companies exploit the advantage of mobiles to meet their selfish ends. They do business through mobiles. As a result, young people have been misguided. To use mobiles is for them to be up to date. They avail themselves of the opportunity of the internet connection in their mobiles and do whatever they like to do. Obscene video clippings and some other versions of immoral entertainment are now available in mobiles. Therefore, the students have now tremendous fascination for the mobiles. Consequently, instead of studying, concentrate on using mobiles for sheer fun.
Another demerit is that because of the excessive use of the mobiles different companies plunge themselves into doing profitable business. Consequently, numerous towers have been erected for the network of mobiles. It is well known that a particular wave which is responsible for the mobile network does harm to the ecological balance of the environment. It is evident in the pale colors of the trees and fruits adjacent to the mobile towers.
Thus, it is the time to be conscious of the abuse of the mobiles. The concerned authority should take immediate steps to stop immoral business which is proliferating in abusing mobiles. All should remember that the sole purpose of mobile is to communicate. Entertainment may be available in the network of mobiles. But there should be no immoral design. Above all, the government should restrict the use of mobiles, so much so that anti-social activities may not be done through mobiles.
Read More: 1. Newspaper Essay in English 2. Essay on Elephant 3. APJ Abdul Kalam Essay
Related Posts
Apj abdul kalam essay in english | 100, 200, 300, 500 words, blood donation essay in english | 150, 200, 300 words, my mother essay in english 10 lines [5 sets], essay on mother teresa in english for students [300 words], 3 thoughts on “essay on mobile phone for students [100, 150, 250, 400 words]”.
I really enjoyed reading your blog post on the benefits of using a mobile phone for students. I think it is a great idea to have students use mobile phones to stay connected and organized. I also think it is important for students to be
I really like your thinking on Mobile phones thanks
Alot of good information on this blog, thanks!
Leave a Comment Cancel Reply
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
- School Guide
- English Grammar Free Course
- English Grammar Tutorial
- Parts of Speech
- Figure of Speech
- Tenses Chart
- Essay Writing
- Email Writing
- NCERT English Solutions
- English Difference Between
- SSC CGL English Syllabus
- SBI PO English Syllabus
- SBI Clerk English Syllabus
- IBPS PO English Syllabus
- IBPS CLERK English Syllabus
Essay on Disadvantages and Advantages of Mobile Phones
- Advantages and Disadvantages of Java Sockets
- Advantages and Disadvantages of Personal Area Network
- Telecommuting: Meaning, Advantages and Disadvantages
- Advantages and Disadvantages of E-mail
- Advantages and disadvantages of mobile computers
- Advantages and Disadvantages of VoLTE
- Advantages and disadvantages of Optical Disks
- Advantages and Disadvantages of IoT
- Advantages and Disadvantages of Laptops
- Advantages and Disadvantages of WLAN
- Advantages and Disadvantages of LAN, MAN and WAN
- Advantages and Disadvantages of Electronic Wallets
- Advantages and Disadvantages of ARM processor
- Advantages and Disadvantages of Internet
- Advantages and disadvantages of Repeater
- Advantages and Disadvantages of Operating System
- Advantages and Disadvantages of Google Chrome
- Advantages and Disadvantages of Telecommunication
- Advantages and disadvantages of CDMA
Mobile Phones have become an integral part of our day-to-day life. Teaching children to use their phones more thoughtfully can benefit them in both their personal and academic lives and help them become more effective citizens of society.
A mobile phone is a personal communication device that uses a wireless connection to do various functions such as sending and receiving messages, making and receiving calls, and accessing the internet. This article will help the readers to have an overview of the examples of different types of essays on the topic “Advantages and Disadvantages of Mobile Phones”.
Let’s dive right in.

Table of Content
Advantages and Disadvantages of Mobile Phone Essay 100 words
200 words essay on advantages and disadvantages of mobile phone, advantages and disadvantages of mobile phone essay 300 words, advantages of mobile phone, disadvantages of mobile phone, 10 lines essay on advantages and disadvantages of mobile phones.
There are advantages and disadvantages to mobile phones. First, let’s discuss the positive aspects. Our mobile phones facilitate easy communication with friends and family. With our phones, we may use the internet to discover new things as well. With their maps, they make it easy for us to locate our route, and we can even snap photos with them.
However, there are also some drawbacks. Overuse of phones by some individuals can be problematic. It might cause eye pain or even make it difficult to fall asleep. Furthermore, excessive phone use might cause us to lose focus when driving or walking, which is risky.
Thus, we must use our phones responsibly. It’s important to remember to take pauses and not use them excessively. Similar to consuming candy, moderation is key when it comes to this. Utilizing our phones sensibly may make them enjoyable and beneficial. However, we must exercise caution so as not to allow them to cause us issues.
With so many benefits, mobile phones have become an essential part of our life. They facilitate communication and let us stay in touch with loved ones no matter where we are or when we want. Additionally, mobile phones offer instant access to information, which keeps us up to date on global events. They are also useful for navigation, taking pictures to save memories, and even handling our money using mobile banking.
But there are also some disadvantages to these advantages. Overuse of a phone can become addictive, diverting our attention and decreasing our productivity. Extended periods of screen usage can lead to health problems like strained eyes and disturbed sleep cycles. Other drawbacks include privacy issues and the possibility of cyberbullying, which emphasise how crucial it is to use mobile phones properly.
In conclusion, even while mobile phones are incredibly beneficial for communication, information access, and convenience, it is important to consider the possible risks they may pose to one’s health, privacy, and general well-being. Maintaining a balance in the use of mobile phones is crucial to maximise their benefits while minimising their drawbacks.
People also View:
- English Essay Writing Tips, Examples, Format
- Difference Between Article and Essay
Mobile phones also referred to as cell phones, are now an essential component of our everyday existence. As with every technology, they have disadvantages in addition to their many advantages.
- Earning Money: People can investigate flexible job choices by using mobile technology, which offers potential for generating revenue through a variety of channels, including freelance work, online markets, and gig economy applications .
- Navigation: Cell phones with built-in GPS technology make travelling easier by making it simple for users to get directions, explore new areas, and successfully navigate uncharted territory.
- Photography: The inclusion of high-quality cameras in mobile phones has made photography more accessible to a wider audience by encouraging innovation, enabling quick moment capture and sharing, and providing a platform for individual expression.
- Safety: Cell phones help people stay safe because they give them a way to communicate in an emergency, ask for assistance, get in touch with authorities, and keep aware of their surroundings.
- Health Problems: Extended usage of mobile phones is linked to possible long-term health hazards resulting from continuous exposure to radiofrequency radiation, as well as physical health problems such as soreness in the neck and back.
- Cyber Bullying: Cell phones provide people with a platform to harass, threaten, or disseminate damaging information online, which puts the victims’ mental health in serious danger.
- Road Accidents: Cell phone usage while driving increases the risk of distracted driving and traffic accidents, endangering the safety of both pedestrians and drivers.
- Noise & Disturbance: M obile phone use may cause noise pollution in public areas, which can disrupt the peace and discomfort of others. This includes loud phone conversations, notification noises, and other mobile phone-related disruptions.
- Easy Communication: Instantaneous and convenient communication is made possible by cell phones, which also develop real-time connections and bridge geographical distances, improving interpersonal relationships and job productivity.
- Online Education: Since the development of mobile technology, more people have had access to educational materials than ever before, which enables them to pursue online courses, pick up new skills, and engage in lifelong learning at their own speed.
- Social Connectivity: Through the use of various social media platforms, cell phones enable social engagement and networking, keeping individuals in touch with friends, family, and coworkers and promoting a feeling of community and shared experiences.
- Banking & Transactions: The ease with which users may manage their accounts, transfer money, and complete transactions is made possible by mobile banking applications, which lessen the need for in-person bank visits and increase overall financial accessibility.
- Promoting Buisness: Cell phones are effective instruments for marketing, communication, and company promotion. They let companies advertise to a wider audience, interact creatively with clients, and promote their goods and services.
- Entertainment: Mobile phones have completely changed the entertainment sector by giving consumers access to a vast array of games, streaming services, and multimedia material that can be enjoyed while on the go.
- Emergency Assistance: When it comes to emergency circumstances, cell phones are invaluable since they provide prompt access to emergency services, facilitate communication during emergencies, and serve as a lifeline for those in need of rapid aid.
- Addiction & Distraction: Cell phone addiction may result from excessive use, which also makes people easily distracted, reduces productivity, and lessens in-person social contacts.
- Sleeping Disorders: Due to the blue light that cell phones emit, prolonged use of them, especially right before bed, can interfere with sleep cycles, impair the generation of melatonin, and worsen insomnia and other sleeping problems.
- Hearing issues: Long-term exposure to high decibel levels via headphones or phone conversations can cause hearing issues, such as loss or impairment of hearing, and pose a serious risk to the health of the auditory system.
- Vision Problems: Digital eye strain, which can result in symptoms including dry eyes, headaches, and impaired vision, may be exacerbated by excessive cell phone screen usage. This condition may eventually cause long-term visual issues.
- Privacy & Security Risks: Since personal data is vulnerable to hacking, unauthorised access, and abuse, there is a danger to both individuals and organisations while using mobile phones, which has led to worries about privacy breaches and security threats.
- Wastage of Time: Using mobile phones excessively for unproductive purposes, including endlessly browsing social media or playing games, may lead to a major time waster that interferes with both personal and professional obligations.
The below are the 10 lines on advantages and disadvantages of mobile phones in English:
- Mobile phones help us talk to friends and family easily.
- They provide quick access to information through the internet.
- Mobiles make it easy to find our way using maps and GPS.
- We can capture memories with cameras on our phones.
- Banking and managing money is convenient with mobile apps.
- Mobiles offer entertainment with games and videos.
- Using phones too much can be bad for our health.
- It might disturb our sleep and hurt our eyes.
- Too much phone use can be a distraction and affect our work.
- Privacy can be at risk, and there might be issues like cyberbullying.
People Also View:
- Essay on My Favourite Teacher (10 Lines, 100 Words, 200 Words)
- Essay on Women Empowerment
- Essay on Ayodhya Ram Mandir in English for Students
FAQs on Advantages and Disadvantages of Mobile Phones Essay
What are the advantages of using mobile phones.
The advantages of using mobile phones are that they make our lives easier. They help us in easy communication, online education, banking and transactions, safety, emergency assistance etc.
What are the disadvantages of using mobile phones?
Some disadvantages of using mobile phones include addiction & distractions, sleeping disorders, hearing aids, noise & disturbance, wastage of time etc.
Why are mobile phones important?
Mobile phones are very important nowadays because they make an individual’s life more convenient and are the perfect way to stay connected with everyone.
How does using mobile phones affect an individual’s brain?
Research from the US National Institute of Health indicates that using a cell phone damages our brains. According to their findings, our brains utilise more sugar after every fifty minutes of phone usage. This is because sugar is an indicator of increased activity, which is detrimental for the brain.
What are the advantages of phone and disadvantages of phone?
Mobile phones offer communication and provide us the access to enormous information, but at the same time they can be addictive, cause distractions and invade our privacy.
Please Login to comment...
Similar reads.
- Banking English
- SSC English
- School English
- SSC/Banking
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
Mobile Communications and Networks
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Purdue Online Writing Lab Purdue OWL® College of Liberal Arts
Welcome to the Purdue Online Writing Lab

Welcome to the Purdue OWL
This page is brought to you by the OWL at Purdue University. When printing this page, you must include the entire legal notice.
Copyright ©1995-2018 by The Writing Lab & The OWL at Purdue and Purdue University. All rights reserved. This material may not be published, reproduced, broadcast, rewritten, or redistributed without permission. Use of this site constitutes acceptance of our terms and conditions of fair use.
The Online Writing Lab at Purdue University houses writing resources and instructional material, and we provide these as a free service of the Writing Lab at Purdue. Students, members of the community, and users worldwide will find information to assist with many writing projects. Teachers and trainers may use this material for in-class and out-of-class instruction.
The Purdue On-Campus Writing Lab and Purdue Online Writing Lab assist clients in their development as writers—no matter what their skill level—with on-campus consultations, online participation, and community engagement. The Purdue Writing Lab serves the Purdue, West Lafayette, campus and coordinates with local literacy initiatives. The Purdue OWL offers global support through online reference materials and services.
A Message From the Assistant Director of Content Development
The Purdue OWL® is committed to supporting students, instructors, and writers by offering a wide range of resources that are developed and revised with them in mind. To do this, the OWL team is always exploring possibilties for a better design, allowing accessibility and user experience to guide our process. As the OWL undergoes some changes, we welcome your feedback and suggestions by email at any time.
Please don't hesitate to contact us via our contact page if you have any questions or comments.
All the best,
Social Media
Facebook twitter.
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- My Account Login
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 03 June 2024
Applying large language models for automated essay scoring for non-native Japanese
- Wenchao Li 1 &
- Haitao Liu 2
Humanities and Social Sciences Communications volume 11 , Article number: 723 ( 2024 ) Cite this article
185 Accesses
2 Altmetric
Metrics details
- Language and linguistics
Recent advancements in artificial intelligence (AI) have led to an increased use of large language models (LLMs) for language assessment tasks such as automated essay scoring (AES), automated listening tests, and automated oral proficiency assessments. The application of LLMs for AES in the context of non-native Japanese, however, remains limited. This study explores the potential of LLM-based AES by comparing the efficiency of different models, i.e. two conventional machine training technology-based methods (Jess and JWriter), two LLMs (GPT and BERT), and one Japanese local LLM (Open-Calm large model). To conduct the evaluation, a dataset consisting of 1400 story-writing scripts authored by learners with 12 different first languages was used. Statistical analysis revealed that GPT-4 outperforms Jess and JWriter, BERT, and the Japanese language-specific trained Open-Calm large model in terms of annotation accuracy and predicting learning levels. Furthermore, by comparing 18 different models that utilize various prompts, the study emphasized the significance of prompts in achieving accurate and reliable evaluations using LLMs.
Similar content being viewed by others

Accurate structure prediction of biomolecular interactions with AlphaFold 3

Testing theory of mind in large language models and humans

Highly accurate protein structure prediction with AlphaFold
Conventional machine learning technology in aes.
AES has experienced significant growth with the advancement of machine learning technologies in recent decades. In the earlier stages of AES development, conventional machine learning-based approaches were commonly used. These approaches involved the following procedures: a) feeding the machine with a dataset. In this step, a dataset of essays is provided to the machine learning system. The dataset serves as the basis for training the model and establishing patterns and correlations between linguistic features and human ratings. b) the machine learning model is trained using linguistic features that best represent human ratings and can effectively discriminate learners’ writing proficiency. These features include lexical richness (Lu, 2012 ; Kyle and Crossley, 2015 ; Kyle et al. 2021 ), syntactic complexity (Lu, 2010 ; Liu, 2008 ), text cohesion (Crossley and McNamara, 2016 ), and among others. Conventional machine learning approaches in AES require human intervention, such as manual correction and annotation of essays. This human involvement was necessary to create a labeled dataset for training the model. Several AES systems have been developed using conventional machine learning technologies. These include the Intelligent Essay Assessor (Landauer et al. 2003 ), the e-rater engine by Educational Testing Service (Attali and Burstein, 2006 ; Burstein, 2003 ), MyAccess with the InterlliMetric scoring engine by Vantage Learning (Elliot, 2003 ), and the Bayesian Essay Test Scoring system (Rudner and Liang, 2002 ). These systems have played a significant role in automating the essay scoring process and providing quick and consistent feedback to learners. However, as touched upon earlier, conventional machine learning approaches rely on predetermined linguistic features and often require manual intervention, making them less flexible and potentially limiting their generalizability to different contexts.
In the context of the Japanese language, conventional machine learning-incorporated AES tools include Jess (Ishioka and Kameda, 2006 ) and JWriter (Lee and Hasebe, 2017 ). Jess assesses essays by deducting points from the perfect score, utilizing the Mainichi Daily News newspaper as a database. The evaluation criteria employed by Jess encompass various aspects, such as rhetorical elements (e.g., reading comprehension, vocabulary diversity, percentage of complex words, and percentage of passive sentences), organizational structures (e.g., forward and reverse connection structures), and content analysis (e.g., latent semantic indexing). JWriter employs linear regression analysis to assign weights to various measurement indices, such as average sentence length and total number of characters. These weights are then combined to derive the overall score. A pilot study involving the Jess model was conducted on 1320 essays at different proficiency levels, including primary, intermediate, and advanced. However, the results indicated that the Jess model failed to significantly distinguish between these essay levels. Out of the 16 measures used, four measures, namely median sentence length, median clause length, median number of phrases, and maximum number of phrases, did not show statistically significant differences between the levels. Additionally, two measures exhibited between-level differences but lacked linear progression: the number of attributives declined words and the Kanji/kana ratio. On the other hand, the remaining measures, including maximum sentence length, maximum clause length, number of attributive conjugated words, maximum number of consecutive infinitive forms, maximum number of conjunctive-particle clauses, k characteristic value, percentage of big words, and percentage of passive sentences, demonstrated statistically significant between-level differences and displayed linear progression.
Both Jess and JWriter exhibit notable limitations, including the manual selection of feature parameters and weights, which can introduce biases into the scoring process. The reliance on human annotators to label non-native language essays also introduces potential noise and variability in the scoring. Furthermore, an important concern is the possibility of system manipulation and cheating by learners who are aware of the regression equation utilized by the models (Hirao et al. 2020 ). These limitations emphasize the need for further advancements in AES systems to address these challenges.
Deep learning technology in AES
Deep learning has emerged as one of the approaches for improving the accuracy and effectiveness of AES. Deep learning-based AES methods utilize artificial neural networks that mimic the human brain’s functioning through layered algorithms and computational units. Unlike conventional machine learning, deep learning autonomously learns from the environment and past errors without human intervention. This enables deep learning models to establish nonlinear correlations, resulting in higher accuracy. Recent advancements in deep learning have led to the development of transformers, which are particularly effective in learning text representations. Noteworthy examples include bidirectional encoder representations from transformers (BERT) (Devlin et al. 2019 ) and the generative pretrained transformer (GPT) (OpenAI).
BERT is a linguistic representation model that utilizes a transformer architecture and is trained on two tasks: masked linguistic modeling and next-sentence prediction (Hirao et al. 2020 ; Vaswani et al. 2017 ). In the context of AES, BERT follows specific procedures, as illustrated in Fig. 1 : (a) the tokenized prompts and essays are taken as input; (b) special tokens, such as [CLS] and [SEP], are added to mark the beginning and separation of prompts and essays; (c) the transformer encoder processes the prompt and essay sequences, resulting in hidden layer sequences; (d) the hidden layers corresponding to the [CLS] tokens (T[CLS]) represent distributed representations of the prompts and essays; and (e) a multilayer perceptron uses these distributed representations as input to obtain the final score (Hirao et al. 2020 ).
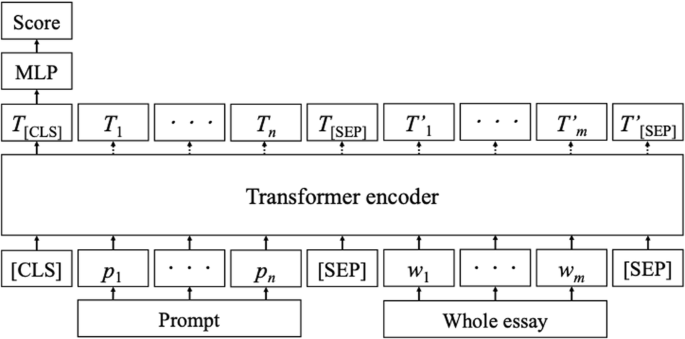
AES system with BERT (Hirao et al. 2020 ).
The training of BERT using a substantial amount of sentence data through the Masked Language Model (MLM) allows it to capture contextual information within the hidden layers. Consequently, BERT is expected to be capable of identifying artificial essays as invalid and assigning them lower scores (Mizumoto and Eguchi, 2023 ). In the context of AES for nonnative Japanese learners, Hirao et al. ( 2020 ) combined the long short-term memory (LSTM) model proposed by Hochreiter and Schmidhuber ( 1997 ) with BERT to develop a tailored automated Essay Scoring System. The findings of their study revealed that the BERT model outperformed both the conventional machine learning approach utilizing character-type features such as “kanji” and “hiragana”, as well as the standalone LSTM model. Takeuchi et al. ( 2021 ) presented an approach to Japanese AES that eliminates the requirement for pre-scored essays by relying solely on reference texts or a model answer for the essay task. They investigated multiple similarity evaluation methods, including frequency of morphemes, idf values calculated on Wikipedia, LSI, LDA, word-embedding vectors, and document vectors produced by BERT. The experimental findings revealed that the method utilizing the frequency of morphemes with idf values exhibited the strongest correlation with human-annotated scores across different essay tasks. The utilization of BERT in AES encounters several limitations. Firstly, essays often exceed the model’s maximum length limit. Second, only score labels are available for training, which restricts access to additional information.
Mizumoto and Eguchi ( 2023 ) were pioneers in employing the GPT model for AES in non-native English writing. Their study focused on evaluating the accuracy and reliability of AES using the GPT-3 text-davinci-003 model, analyzing a dataset of 12,100 essays from the corpus of nonnative written English (TOEFL11). The findings indicated that AES utilizing the GPT-3 model exhibited a certain degree of accuracy and reliability. They suggest that GPT-3-based AES systems hold the potential to provide support for human ratings. However, applying GPT model to AES presents a unique natural language processing (NLP) task that involves considerations such as nonnative language proficiency, the influence of the learner’s first language on the output in the target language, and identifying linguistic features that best indicate writing quality in a specific language. These linguistic features may differ morphologically or syntactically from those present in the learners’ first language, as observed in (1)–(3).
我-送了-他-一本-书
Wǒ-sòngle-tā-yī běn-shū
1 sg .-give. past- him-one .cl- book
“I gave him a book.”
Agglutinative
彼-に-本-を-あげ-まし-た
Kare-ni-hon-o-age-mashi-ta
3 sg .- dat -hon- acc- give.honorification. past
Inflectional
give, give-s, gave, given, giving
Additionally, the morphological agglutination and subject-object-verb (SOV) order in Japanese, along with its idiomatic expressions, pose additional challenges for applying language models in AES tasks (4).
足-が 棒-に なり-ました
Ashi-ga bo-ni nar-mashita
leg- nom stick- dat become- past
“My leg became like a stick (I am extremely tired).”
The example sentence provided demonstrates the morpho-syntactic structure of Japanese and the presence of an idiomatic expression. In this sentence, the verb “なる” (naru), meaning “to become”, appears at the end of the sentence. The verb stem “なり” (nari) is attached with morphemes indicating honorification (“ます” - mashu) and tense (“た” - ta), showcasing agglutination. While the sentence can be literally translated as “my leg became like a stick”, it carries an idiomatic interpretation that implies “I am extremely tired”.
To overcome this issue, CyberAgent Inc. ( 2023 ) has developed the Open-Calm series of language models specifically designed for Japanese. Open-Calm consists of pre-trained models available in various sizes, such as Small, Medium, Large, and 7b. Figure 2 depicts the fundamental structure of the Open-Calm model. A key feature of this architecture is the incorporation of the Lora Adapter and GPT-NeoX frameworks, which can enhance its language processing capabilities.
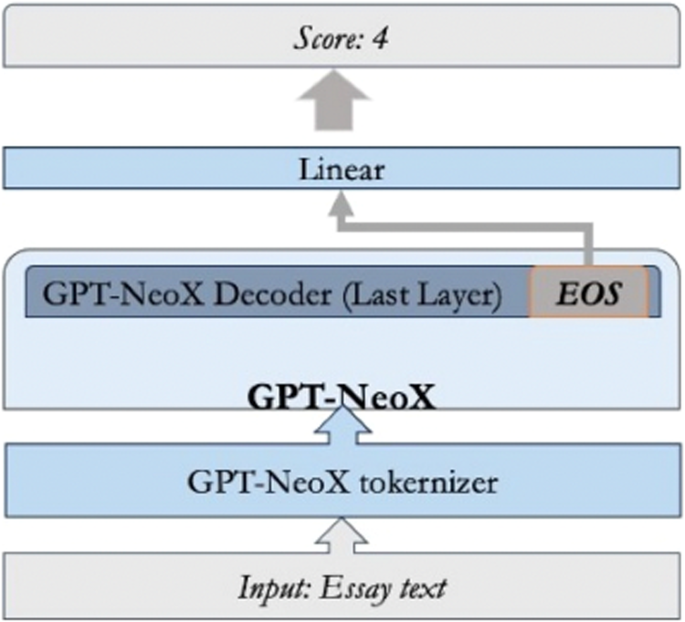
GPT-NeoX Model Architecture (Okgetheng and Takeuchi 2024 ).
In a recent study conducted by Okgetheng and Takeuchi ( 2024 ), they assessed the efficacy of Open-Calm language models in grading Japanese essays. The research utilized a dataset of approximately 300 essays, which were annotated by native Japanese educators. The findings of the study demonstrate the considerable potential of Open-Calm language models in automated Japanese essay scoring. Specifically, among the Open-Calm family, the Open-Calm Large model (referred to as OCLL) exhibited the highest performance. However, it is important to note that, as of the current date, the Open-Calm Large model does not offer public access to its server. Consequently, users are required to independently deploy and operate the environment for OCLL. In order to utilize OCLL, users must have a PC equipped with an NVIDIA GeForce RTX 3060 (8 or 12 GB VRAM).
In summary, while the potential of LLMs in automated scoring of nonnative Japanese essays has been demonstrated in two studies—BERT-driven AES (Hirao et al. 2020 ) and OCLL-based AES (Okgetheng and Takeuchi, 2024 )—the number of research efforts in this area remains limited.
Another significant challenge in applying LLMs to AES lies in prompt engineering and ensuring its reliability and effectiveness (Brown et al. 2020 ; Rae et al. 2021 ; Zhang et al. 2021 ). Various prompting strategies have been proposed, such as the zero-shot chain of thought (CoT) approach (Kojima et al. 2022 ), which involves manually crafting diverse and effective examples. However, manual efforts can lead to mistakes. To address this, Zhang et al. ( 2021 ) introduced an automatic CoT prompting method called Auto-CoT, which demonstrates matching or superior performance compared to the CoT paradigm. Another prompt framework is trees of thoughts, enabling a model to self-evaluate its progress at intermediate stages of problem-solving through deliberate reasoning (Yao et al. 2023 ).
Beyond linguistic studies, there has been a noticeable increase in the number of foreign workers in Japan and Japanese learners worldwide (Ministry of Health, Labor, and Welfare of Japan, 2022 ; Japan Foundation, 2021 ). However, existing assessment methods, such as the Japanese Language Proficiency Test (JLPT), J-CAT, and TTBJ Footnote 1 , primarily focus on reading, listening, vocabulary, and grammar skills, neglecting the evaluation of writing proficiency. As the number of workers and language learners continues to grow, there is a rising demand for an efficient AES system that can reduce costs and time for raters and be utilized for employment, examinations, and self-study purposes.
This study aims to explore the potential of LLM-based AES by comparing the effectiveness of five models: two LLMs (GPT Footnote 2 and BERT), one Japanese local LLM (OCLL), and two conventional machine learning-based methods (linguistic feature-based scoring tools - Jess and JWriter).
The research questions addressed in this study are as follows:
To what extent do the LLM-driven AES and linguistic feature-based AES, when used as automated tools to support human rating, accurately reflect test takers’ actual performance?
What influence does the prompt have on the accuracy and performance of LLM-based AES methods?
The subsequent sections of the manuscript cover the methodology, including the assessment measures for nonnative Japanese writing proficiency, criteria for prompts, and the dataset. The evaluation section focuses on the analysis of annotations and rating scores generated by LLM-driven and linguistic feature-based AES methods.
Methodology
The dataset utilized in this study was obtained from the International Corpus of Japanese as a Second Language (I-JAS) Footnote 3 . This corpus consisted of 1000 participants who represented 12 different first languages. For the study, the participants were given a story-writing task on a personal computer. They were required to write two stories based on the 4-panel illustrations titled “Picnic” and “The key” (see Appendix A). Background information for the participants was provided by the corpus, including their Japanese language proficiency levels assessed through two online tests: J-CAT and SPOT. These tests evaluated their reading, listening, vocabulary, and grammar abilities. The learners’ proficiency levels were categorized into six levels aligned with the Common European Framework of Reference for Languages (CEFR) and the Reference Framework for Japanese Language Education (RFJLE): A1, A2, B1, B2, C1, and C2. According to Lee et al. ( 2015 ), there is a high level of agreement (r = 0.86) between the J-CAT and SPOT assessments, indicating that the proficiency certifications provided by J-CAT are consistent with those of SPOT. However, it is important to note that the scores of J-CAT and SPOT do not have a one-to-one correspondence. In this study, the J-CAT scores were used as a benchmark to differentiate learners of different proficiency levels. A total of 1400 essays were utilized, representing the beginner (aligned with A1), A2, B1, B2, C1, and C2 levels based on the J-CAT scores. Table 1 provides information about the learners’ proficiency levels and their corresponding J-CAT and SPOT scores.
A dataset comprising a total of 1400 essays from the story writing tasks was collected. Among these, 714 essays were utilized to evaluate the reliability of the LLM-based AES method, while the remaining 686 essays were designated as development data to assess the LLM-based AES’s capability to distinguish participants with varying proficiency levels. The GPT 4 API was used in this study. A detailed explanation of the prompt-assessment criteria is provided in Section Prompt . All essays were sent to the model for measurement and scoring.
Measures of writing proficiency for nonnative Japanese
Japanese exhibits a morphologically agglutinative structure where morphemes are attached to the word stem to convey grammatical functions such as tense, aspect, voice, and honorifics, e.g. (5).
食べ-させ-られ-まし-た-か
tabe-sase-rare-mashi-ta-ka
[eat (stem)-causative-passive voice-honorification-tense. past-question marker]
Japanese employs nine case particles to indicate grammatical functions: the nominative case particle が (ga), the accusative case particle を (o), the genitive case particle の (no), the dative case particle に (ni), the locative/instrumental case particle で (de), the ablative case particle から (kara), the directional case particle へ (e), and the comitative case particle と (to). The agglutinative nature of the language, combined with the case particle system, provides an efficient means of distinguishing between active and passive voice, either through morphemes or case particles, e.g. 食べる taberu “eat concusive . ” (active voice); 食べられる taberareru “eat concusive . ” (passive voice). In the active voice, “パン を 食べる” (pan o taberu) translates to “to eat bread”. On the other hand, in the passive voice, it becomes “パン が 食べられた” (pan ga taberareta), which means “(the) bread was eaten”. Additionally, it is important to note that different conjugations of the same lemma are considered as one type in order to ensure a comprehensive assessment of the language features. For example, e.g., 食べる taberu “eat concusive . ”; 食べている tabeteiru “eat progress .”; 食べた tabeta “eat past . ” as one type.
To incorporate these features, previous research (Suzuki, 1999 ; Watanabe et al. 1988 ; Ishioka, 2001 ; Ishioka and Kameda, 2006 ; Hirao et al. 2020 ) has identified complexity, fluency, and accuracy as crucial factors for evaluating writing quality. These criteria are assessed through various aspects, including lexical richness (lexical density, diversity, and sophistication), syntactic complexity, and cohesion (Kyle et al. 2021 ; Mizumoto and Eguchi, 2023 ; Ure, 1971 ; Halliday, 1985 ; Barkaoui and Hadidi, 2020 ; Zenker and Kyle, 2021 ; Kim et al. 2018 ; Lu, 2017 ; Ortega, 2015 ). Therefore, this study proposes five scoring categories: lexical richness, syntactic complexity, cohesion, content elaboration, and grammatical accuracy. A total of 16 measures were employed to capture these categories. The calculation process and specific details of these measures can be found in Table 2 .
T-unit, first introduced by Hunt ( 1966 ), is a measure used for evaluating speech and composition. It serves as an indicator of syntactic development and represents the shortest units into which a piece of discourse can be divided without leaving any sentence fragments. In the context of Japanese language assessment, Sakoda and Hosoi ( 2020 ) utilized T-unit as the basic unit to assess the accuracy and complexity of Japanese learners’ speaking and storytelling. The calculation of T-units in Japanese follows the following principles:
A single main clause constitutes 1 T-unit, regardless of the presence or absence of dependent clauses, e.g. (6).
ケンとマリはピクニックに行きました (main clause): 1 T-unit.
If a sentence contains a main clause along with subclauses, each subclause is considered part of the same T-unit, e.g. (7).
天気が良かった の で (subclause)、ケンとマリはピクニックに行きました (main clause): 1 T-unit.
In the case of coordinate clauses, where multiple clauses are connected, each coordinated clause is counted separately. Thus, a sentence with coordinate clauses may have 2 T-units or more, e.g. (8).
ケンは地図で場所を探して (coordinate clause)、マリはサンドイッチを作りました (coordinate clause): 2 T-units.
Lexical diversity refers to the range of words used within a text (Engber, 1995 ; Kyle et al. 2021 ) and is considered a useful measure of the breadth of vocabulary in L n production (Jarvis, 2013a , 2013b ).
The type/token ratio (TTR) is widely recognized as a straightforward measure for calculating lexical diversity and has been employed in numerous studies. These studies have demonstrated a strong correlation between TTR and other methods of measuring lexical diversity (e.g., Bentz et al. 2016 ; Čech and Miroslav, 2018 ; Çöltekin and Taraka, 2018 ). TTR is computed by considering both the number of unique words (types) and the total number of words (tokens) in a given text. Given that the length of learners’ writing texts can vary, this study employs the moving average type-token ratio (MATTR) to mitigate the influence of text length. MATTR is calculated using a 50-word moving window. Initially, a TTR is determined for words 1–50 in an essay, followed by words 2–51, 3–52, and so on until the end of the essay is reached (Díez-Ortega and Kyle, 2023 ). The final MATTR scores were obtained by averaging the TTR scores for all 50-word windows. The following formula was employed to derive MATTR:
\({\rm{MATTR}}({\rm{W}})=\frac{{\sum }_{{\rm{i}}=1}^{{\rm{N}}-{\rm{W}}+1}{{\rm{F}}}_{{\rm{i}}}}{{\rm{W}}({\rm{N}}-{\rm{W}}+1)}\)
Here, N refers to the number of tokens in the corpus. W is the randomly selected token size (W < N). \({F}_{i}\) is the number of types in each window. The \({\rm{MATTR}}({\rm{W}})\) is the mean of a series of type-token ratios (TTRs) based on the word form for all windows. It is expected that individuals with higher language proficiency will produce texts with greater lexical diversity, as indicated by higher MATTR scores.
Lexical density was captured by the ratio of the number of lexical words to the total number of words (Lu, 2012 ). Lexical sophistication refers to the utilization of advanced vocabulary, often evaluated through word frequency indices (Crossley et al. 2013 ; Haberman, 2008 ; Kyle and Crossley, 2015 ; Laufer and Nation, 1995 ; Lu, 2012 ; Read, 2000 ). In line of writing, lexical sophistication can be interpreted as vocabulary breadth, which entails the appropriate usage of vocabulary items across various lexicon-grammatical contexts and registers (Garner et al. 2019 ; Kim et al. 2018 ; Kyle et al. 2018 ). In Japanese specifically, words are considered lexically sophisticated if they are not included in the “Japanese Education Vocabulary List Ver 1.0”. Footnote 4 Consequently, lexical sophistication was calculated by determining the number of sophisticated word types relative to the total number of words per essay. Furthermore, it has been suggested that, in Japanese writing, sentences should ideally have a length of no more than 40 to 50 characters, as this promotes readability. Therefore, the median and maximum sentence length can be considered as useful indices for assessment (Ishioka and Kameda, 2006 ).
Syntactic complexity was assessed based on several measures, including the mean length of clauses, verb phrases per T-unit, clauses per T-unit, dependent clauses per T-unit, complex nominals per clause, adverbial clauses per clause, coordinate phrases per clause, and mean dependency distance (MDD). The MDD reflects the distance between the governor and dependent positions in a sentence. A larger dependency distance indicates a higher cognitive load and greater complexity in syntactic processing (Liu, 2008 ; Liu et al. 2017 ). The MDD has been established as an efficient metric for measuring syntactic complexity (Jiang, Quyang, and Liu, 2019 ; Li and Yan, 2021 ). To calculate the MDD, the position numbers of the governor and dependent are subtracted, assuming that words in a sentence are assigned in a linear order, such as W1 … Wi … Wn. In any dependency relationship between words Wa and Wb, Wa is the governor and Wb is the dependent. The MDD of the entire sentence was obtained by taking the absolute value of governor – dependent:
MDD = \(\frac{1}{n}{\sum }_{i=1}^{n}|{\rm{D}}{{\rm{D}}}_{i}|\)
In this formula, \(n\) represents the number of words in the sentence, and \({DD}i\) is the dependency distance of the \({i}^{{th}}\) dependency relationship of a sentence. Building on this, the annotation of sentence ‘Mary-ga-John-ni-keshigomu-o-watashita was [Mary- top -John- dat -eraser- acc -give- past] ’. The sentence’s MDD would be 2. Table 3 provides the CSV file as a prompt for GPT 4.
Cohesion (semantic similarity) and content elaboration aim to capture the ideas presented in test taker’s essays. Cohesion was assessed using three measures: Synonym overlap/paragraph (topic), Synonym overlap/paragraph (keywords), and word2vec cosine similarity. Content elaboration and development were measured as the number of metadiscourse markers (type)/number of words. To capture content closely, this study proposed a novel-distance based representation, by encoding the cosine distance between the essay (by learner) and essay task’s (topic and keyword) i -vectors. The learner’s essay is decoded into a word sequence, and aligned to the essay task’ topic and keyword for log-likelihood measurement. The cosine distance reveals the content elaboration score in the leaners’ essay. The mathematical equation of cosine similarity between target-reference vectors is shown in (11), assuming there are i essays and ( L i , …. L n ) and ( N i , …. N n ) are the vectors representing the learner and task’s topic and keyword respectively. The content elaboration distance between L i and N i was calculated as follows:
\(\cos \left(\theta \right)=\frac{{\rm{L}}\,\cdot\, {\rm{N}}}{\left|{\rm{L}}\right|{\rm{|N|}}}=\frac{\mathop{\sum }\nolimits_{i=1}^{n}{L}_{i}{N}_{i}}{\sqrt{\mathop{\sum }\nolimits_{i=1}^{n}{L}_{i}^{2}}\sqrt{\mathop{\sum }\nolimits_{i=1}^{n}{N}_{i}^{2}}}\)
A high similarity value indicates a low difference between the two recognition outcomes, which in turn suggests a high level of proficiency in content elaboration.
To evaluate the effectiveness of the proposed measures in distinguishing different proficiency levels among nonnative Japanese speakers’ writing, we conducted a multi-faceted Rasch measurement analysis (Linacre, 1994 ). This approach applies measurement models to thoroughly analyze various factors that can influence test outcomes, including test takers’ proficiency, item difficulty, and rater severity, among others. The underlying principles and functionality of multi-faceted Rasch measurement are illustrated in (12).
\(\log \left(\frac{{P}_{{nijk}}}{{P}_{{nij}(k-1)}}\right)={B}_{n}-{D}_{i}-{C}_{j}-{F}_{k}\)
(12) defines the logarithmic transformation of the probability ratio ( P nijk /P nij(k-1) )) as a function of multiple parameters. Here, n represents the test taker, i denotes a writing proficiency measure, j corresponds to the human rater, and k represents the proficiency score. The parameter B n signifies the proficiency level of test taker n (where n ranges from 1 to N). D j represents the difficulty parameter of test item i (where i ranges from 1 to L), while C j represents the severity of rater j (where j ranges from 1 to J). Additionally, F k represents the step difficulty for a test taker to move from score ‘k-1’ to k . P nijk refers to the probability of rater j assigning score k to test taker n for test item i . P nij(k-1) represents the likelihood of test taker n being assigned score ‘k-1’ by rater j for test item i . Each facet within the test is treated as an independent parameter and estimated within the same reference framework. To evaluate the consistency of scores obtained through both human and computer analysis, we utilized the Infit mean-square statistic. This statistic is a chi-square measure divided by the degrees of freedom and is weighted with information. It demonstrates higher sensitivity to unexpected patterns in responses to items near a person’s proficiency level (Linacre, 2002 ). Fit statistics are assessed based on predefined thresholds for acceptable fit. For the Infit MNSQ, which has a mean of 1.00, different thresholds have been suggested. Some propose stricter thresholds ranging from 0.7 to 1.3 (Bond et al. 2021 ), while others suggest more lenient thresholds ranging from 0.5 to 1.5 (Eckes, 2009 ). In this study, we adopted the criterion of 0.70–1.30 for the Infit MNSQ.
Moving forward, we can now proceed to assess the effectiveness of the 16 proposed measures based on five criteria for accurately distinguishing various levels of writing proficiency among non-native Japanese speakers. To conduct this evaluation, we utilized the development dataset from the I-JAS corpus, as described in Section Dataset . Table 4 provides a measurement report that presents the performance details of the 14 metrics under consideration. The measure separation was found to be 4.02, indicating a clear differentiation among the measures. The reliability index for the measure separation was 0.891, suggesting consistency in the measurement. Similarly, the person separation reliability index was 0.802, indicating the accuracy of the assessment in distinguishing between individuals. All 16 measures demonstrated Infit mean squares within a reasonable range, ranging from 0.76 to 1.28. The Synonym overlap/paragraph (topic) measure exhibited a relatively high outfit mean square of 1.46, although the Infit mean square falls within an acceptable range. The standard error for the measures ranged from 0.13 to 0.28, indicating the precision of the estimates.
Table 5 further illustrated the weights assigned to different linguistic measures for score prediction, with higher weights indicating stronger correlations between those measures and higher scores. Specifically, the following measures exhibited higher weights compared to others: moving average type token ratio per essay has a weight of 0.0391. Mean dependency distance had a weight of 0.0388. Mean length of clause, calculated by dividing the number of words by the number of clauses, had a weight of 0.0374. Complex nominals per T-unit, calculated by dividing the number of complex nominals by the number of T-units, had a weight of 0.0379. Coordinate phrases rate, calculated by dividing the number of coordinate phrases by the number of clauses, had a weight of 0.0325. Grammatical error rate, representing the number of errors per essay, had a weight of 0.0322.
Criteria (output indicator)
The criteria used to evaluate the writing ability in this study were based on CEFR, which follows a six-point scale ranging from A1 to C2. To assess the quality of Japanese writing, the scoring criteria from Table 6 were utilized. These criteria were derived from the IELTS writing standards and served as assessment guidelines and prompts for the written output.
A prompt is a question or detailed instruction that is provided to the model to obtain a proper response. After several pilot experiments, we decided to provide the measures (Section Measures of writing proficiency for nonnative Japanese ) as the input prompt and use the criteria (Section Criteria (output indicator) ) as the output indicator. Regarding the prompt language, considering that the LLM was tasked with rating Japanese essays, would prompt in Japanese works better Footnote 5 ? We conducted experiments comparing the performance of GPT-4 using both English and Japanese prompts. Additionally, we utilized the Japanese local model OCLL with Japanese prompts. Multiple trials were conducted using the same sample. Regardless of the prompt language used, we consistently obtained the same grading results with GPT-4, which assigned a grade of B1 to the writing sample. This suggested that GPT-4 is reliable and capable of producing consistent ratings regardless of the prompt language. On the other hand, when we used Japanese prompts with the Japanese local model “OCLL”, we encountered inconsistent grading results. Out of 10 attempts with OCLL, only 6 yielded consistent grading results (B1), while the remaining 4 showed different outcomes, including A1 and B2 grades. These findings indicated that the language of the prompt was not the determining factor for reliable AES. Instead, the size of the training data and the model parameters played crucial roles in achieving consistent and reliable AES results for the language model.
The following is the utilized prompt, which details all measures and requires the LLM to score the essays using holistic and trait scores.
Please evaluate Japanese essays written by Japanese learners and assign a score to each essay on a six-point scale, ranging from A1, A2, B1, B2, C1 to C2. Additionally, please provide trait scores and display the calculation process for each trait score. The scoring should be based on the following criteria:
Moving average type-token ratio.
Number of lexical words (token) divided by the total number of words per essay.
Number of sophisticated word types divided by the total number of words per essay.
Mean length of clause.
Verb phrases per T-unit.
Clauses per T-unit.
Dependent clauses per T-unit.
Complex nominals per clause.
Adverbial clauses per clause.
Coordinate phrases per clause.
Mean dependency distance.
Synonym overlap paragraph (topic and keywords).
Word2vec cosine similarity.
Connectives per essay.
Conjunctions per essay.
Number of metadiscourse markers (types) divided by the total number of words.
Number of errors per essay.
Japanese essay text
出かける前に二人が地図を見ている間に、サンドイッチを入れたバスケットに犬が入ってしまいました。それに気づかずに二人は楽しそうに出かけて行きました。やがて突然犬がバスケットから飛び出し、二人は驚きました。バスケット の 中を見ると、食べ物はすべて犬に食べられていて、二人は困ってしまいました。(ID_JJJ01_SW1)
The score of the example above was B1. Figure 3 provides an example of holistic and trait scores provided by GPT-4 (with a prompt indicating all measures) via Bing Footnote 6 .

Example of GPT-4 AES and feedback (with a prompt indicating all measures).
Statistical analysis
The aim of this study is to investigate the potential use of LLM for nonnative Japanese AES. It seeks to compare the scoring outcomes obtained from feature-based AES tools, which rely on conventional machine learning technology (i.e. Jess, JWriter), with those generated by AI-driven AES tools utilizing deep learning technology (BERT, GPT, OCLL). To assess the reliability of a computer-assisted annotation tool, the study initially established human-human agreement as the benchmark measure. Subsequently, the performance of the LLM-based method was evaluated by comparing it to human-human agreement.
To assess annotation agreement, the study employed standard measures such as precision, recall, and F-score (Brants 2000 ; Lu 2010 ), along with the quadratically weighted kappa (QWK) to evaluate the consistency and agreement in the annotation process. Assume A and B represent human annotators. When comparing the annotations of the two annotators, the following results are obtained. The evaluation of precision, recall, and F-score metrics was illustrated in equations (13) to (15).
\({\rm{Recall}}(A,B)=\frac{{\rm{Number}}\,{\rm{of}}\,{\rm{identical}}\,{\rm{nodes}}\,{\rm{in}}\,A\,{\rm{and}}\,B}{{\rm{Number}}\,{\rm{of}}\,{\rm{nodes}}\,{\rm{in}}\,A}\)
\({\rm{Precision}}(A,\,B)=\frac{{\rm{Number}}\,{\rm{of}}\,{\rm{identical}}\,{\rm{nodes}}\,{\rm{in}}\,A\,{\rm{and}}\,B}{{\rm{Number}}\,{\rm{of}}\,{\rm{nodes}}\,{\rm{in}}\,B}\)
The F-score is the harmonic mean of recall and precision:
\({\rm{F}}-{\rm{score}}=\frac{2* ({\rm{Precision}}* {\rm{Recall}})}{{\rm{Precision}}+{\rm{Recall}}}\)
The highest possible value of an F-score is 1.0, indicating perfect precision and recall, and the lowest possible value is 0, if either precision or recall are zero.
In accordance with Taghipour and Ng ( 2016 ), the calculation of QWK involves two steps:
Step 1: Construct a weight matrix W as follows:
\({W}_{{ij}}=\frac{{(i-j)}^{2}}{{(N-1)}^{2}}\)
i represents the annotation made by the tool, while j represents the annotation made by a human rater. N denotes the total number of possible annotations. Matrix O is subsequently computed, where O_( i, j ) represents the count of data annotated by the tool ( i ) and the human annotator ( j ). On the other hand, E refers to the expected count matrix, which undergoes normalization to ensure that the sum of elements in E matches the sum of elements in O.
Step 2: With matrices O and E, the QWK is obtained as follows:
K = 1- \(\frac{\sum i,j{W}_{i,j}\,{O}_{i,j}}{\sum i,j{W}_{i,j}\,{E}_{i,j}}\)
The value of the quadratic weighted kappa increases as the level of agreement improves. Further, to assess the accuracy of LLM scoring, the proportional reductive mean square error (PRMSE) was employed. The PRMSE approach takes into account the variability observed in human ratings to estimate the rater error, which is then subtracted from the variance of the human labels. This calculation provides an overall measure of agreement between the automated scores and true scores (Haberman et al. 2015 ; Loukina et al. 2020 ; Taghipour and Ng, 2016 ). The computation of PRMSE involves the following steps:
Step 1: Calculate the mean squared errors (MSEs) for the scoring outcomes of the computer-assisted tool (MSE tool) and the human scoring outcomes (MSE human).
Step 2: Determine the PRMSE by comparing the MSE of the computer-assisted tool (MSE tool) with the MSE from human raters (MSE human), using the following formula:
\({\rm{PRMSE}}=1-\frac{({\rm{MSE}}\,{\rm{tool}})\,}{({\rm{MSE}}\,{\rm{human}})\,}=1-\,\frac{{\sum }_{i}^{n}=1{({{\rm{y}}}_{i}-{\hat{{\rm{y}}}}_{{\rm{i}}})}^{2}}{{\sum }_{i}^{n}=1{({{\rm{y}}}_{i}-\hat{{\rm{y}}})}^{2}}\)
In the numerator, ŷi represents the scoring outcome predicted by a specific LLM-driven AES system for a given sample. The term y i − ŷ i represents the difference between this predicted outcome and the mean value of all LLM-driven AES systems’ scoring outcomes. It quantifies the deviation of the specific LLM-driven AES system’s prediction from the average prediction of all LLM-driven AES systems. In the denominator, y i − ŷ represents the difference between the scoring outcome provided by a specific human rater for a given sample and the mean value of all human raters’ scoring outcomes. It measures the discrepancy between the specific human rater’s score and the average score given by all human raters. The PRMSE is then calculated by subtracting the ratio of the MSE tool to the MSE human from 1. PRMSE falls within the range of 0 to 1, with larger values indicating reduced errors in LLM’s scoring compared to those of human raters. In other words, a higher PRMSE implies that LLM’s scoring demonstrates greater accuracy in predicting the true scores (Loukina et al. 2020 ). The interpretation of kappa values, ranging from 0 to 1, is based on the work of Landis and Koch ( 1977 ). Specifically, the following categories are assigned to different ranges of kappa values: −1 indicates complete inconsistency, 0 indicates random agreement, 0.0 ~ 0.20 indicates extremely low level of agreement (slight), 0.21 ~ 0.40 indicates moderate level of agreement (fair), 0.41 ~ 0.60 indicates medium level of agreement (moderate), 0.61 ~ 0.80 indicates high level of agreement (substantial), 0.81 ~ 1 indicates almost perfect level of agreement. All statistical analyses were executed using Python script.
Results and discussion
Annotation reliability of the llm.
This section focuses on assessing the reliability of the LLM’s annotation and scoring capabilities. To evaluate the reliability, several tests were conducted simultaneously, aiming to achieve the following objectives:
Assess the LLM’s ability to differentiate between test takers with varying levels of oral proficiency.
Determine the level of agreement between the annotations and scoring performed by the LLM and those done by human raters.
The evaluation of the results encompassed several metrics, including: precision, recall, F-Score, quadratically-weighted kappa, proportional reduction of mean squared error, Pearson correlation, and multi-faceted Rasch measurement.
Inter-annotator agreement (human–human annotator agreement)
We started with an agreement test of the two human annotators. Two trained annotators were recruited to determine the writing task data measures. A total of 714 scripts, as the test data, was utilized. Each analysis lasted 300–360 min. Inter-annotator agreement was evaluated using the standard measures of precision, recall, and F-score and QWK. Table 7 presents the inter-annotator agreement for the various indicators. As shown, the inter-annotator agreement was fairly high, with F-scores ranging from 1.0 for sentence and word number to 0.666 for grammatical errors.
The findings from the QWK analysis provided further confirmation of the inter-annotator agreement. The QWK values covered a range from 0.950 ( p = 0.000) for sentence and word number to 0.695 for synonym overlap number (keyword) and grammatical errors ( p = 0.001).
Agreement of annotation outcomes between human and LLM
To evaluate the consistency between human annotators and LLM annotators (BERT, GPT, OCLL) across the indices, the same test was conducted. The results of the inter-annotator agreement (F-score) between LLM and human annotation are provided in Appendix B-D. The F-scores ranged from 0.706 for Grammatical error # for OCLL-human to a perfect 1.000 for GPT-human, for sentences, clauses, T-units, and words. These findings were further supported by the QWK analysis, which showed agreement levels ranging from 0.807 ( p = 0.001) for metadiscourse markers for OCLL-human to 0.962 for words ( p = 0.000) for GPT-human. The findings demonstrated that the LLM annotation achieved a significant level of accuracy in identifying measurement units and counts.
Reliability of LLM-driven AES’s scoring and discriminating proficiency levels
This section examines the reliability of the LLM-driven AES scoring through a comparison of the scoring outcomes produced by human raters and the LLM ( Reliability of LLM-driven AES scoring ). It also assesses the effectiveness of the LLM-based AES system in differentiating participants with varying proficiency levels ( Reliability of LLM-driven AES discriminating proficiency levels ).
Reliability of LLM-driven AES scoring
Table 8 summarizes the QWK coefficient analysis between the scores computed by the human raters and the GPT-4 for the individual essays from I-JAS Footnote 7 . As shown, the QWK of all measures ranged from k = 0.819 for lexical density (number of lexical words (tokens)/number of words per essay) to k = 0.644 for word2vec cosine similarity. Table 9 further presents the Pearson correlations between the 16 writing proficiency measures scored by human raters and GPT 4 for the individual essays. The correlations ranged from 0.672 for syntactic complexity to 0.734 for grammatical accuracy. The correlations between the writing proficiency scores assigned by human raters and the BERT-based AES system were found to range from 0.661 for syntactic complexity to 0.713 for grammatical accuracy. The correlations between the writing proficiency scores given by human raters and the OCLL-based AES system ranged from 0.654 for cohesion to 0.721 for grammatical accuracy. These findings indicated an alignment between the assessments made by human raters and both the BERT-based and OCLL-based AES systems in terms of various aspects of writing proficiency.
Reliability of LLM-driven AES discriminating proficiency levels
After validating the reliability of the LLM’s annotation and scoring, the subsequent objective was to evaluate its ability to distinguish between various proficiency levels. For this analysis, a dataset of 686 individual essays was utilized. Table 10 presents a sample of the results, summarizing the means, standard deviations, and the outcomes of the one-way ANOVAs based on the measures assessed by the GPT-4 model. A post hoc multiple comparison test, specifically the Bonferroni test, was conducted to identify any potential differences between pairs of levels.
As the results reveal, seven measures presented linear upward or downward progress across the three proficiency levels. These were marked in bold in Table 10 and comprise one measure of lexical richness, i.e. MATTR (lexical diversity); four measures of syntactic complexity, i.e. MDD (mean dependency distance), MLC (mean length of clause), CNT (complex nominals per T-unit), CPC (coordinate phrases rate); one cohesion measure, i.e. word2vec cosine similarity and GER (grammatical error rate). Regarding the ability of the sixteen measures to distinguish adjacent proficiency levels, the Bonferroni tests indicated that statistically significant differences exist between the primary level and the intermediate level for MLC and GER. One measure of lexical richness, namely LD, along with three measures of syntactic complexity (VPT, CT, DCT, ACC), two measures of cohesion (SOPT, SOPK), and one measure of content elaboration (IMM), exhibited statistically significant differences between proficiency levels. However, these differences did not demonstrate a linear progression between adjacent proficiency levels. No significant difference was observed in lexical sophistication between proficiency levels.
To summarize, our study aimed to evaluate the reliability and differentiation capabilities of the LLM-driven AES method. For the first objective, we assessed the LLM’s ability to differentiate between test takers with varying levels of oral proficiency using precision, recall, F-Score, and quadratically-weighted kappa. Regarding the second objective, we compared the scoring outcomes generated by human raters and the LLM to determine the level of agreement. We employed quadratically-weighted kappa and Pearson correlations to compare the 16 writing proficiency measures for the individual essays. The results confirmed the feasibility of using the LLM for annotation and scoring in AES for nonnative Japanese. As a result, Research Question 1 has been addressed.
Comparison of BERT-, GPT-, OCLL-based AES, and linguistic-feature-based computation methods
This section aims to compare the effectiveness of five AES methods for nonnative Japanese writing, i.e. LLM-driven approaches utilizing BERT, GPT, and OCLL, linguistic feature-based approaches using Jess and JWriter. The comparison was conducted by comparing the ratings obtained from each approach with human ratings. All ratings were derived from the dataset introduced in Dataset . To facilitate the comparison, the agreement between the automated methods and human ratings was assessed using QWK and PRMSE. The performance of each approach was summarized in Table 11 .
The QWK coefficient values indicate that LLMs (GPT, BERT, OCLL) and human rating outcomes demonstrated higher agreement compared to feature-based AES methods (Jess and JWriter) in assessing writing proficiency criteria, including lexical richness, syntactic complexity, content, and grammatical accuracy. Among the LLMs, the GPT-4 driven AES and human rating outcomes showed the highest agreement in all criteria, except for syntactic complexity. The PRMSE values suggest that the GPT-based method outperformed linguistic feature-based methods and other LLM-based approaches. Moreover, an interesting finding emerged during the study: the agreement coefficient between GPT-4 and human scoring was even higher than the agreement between different human raters themselves. This discovery highlights the advantage of GPT-based AES over human rating. Ratings involve a series of processes, including reading the learners’ writing, evaluating the content and language, and assigning scores. Within this chain of processes, various biases can be introduced, stemming from factors such as rater biases, test design, and rating scales. These biases can impact the consistency and objectivity of human ratings. GPT-based AES may benefit from its ability to apply consistent and objective evaluation criteria. By prompting the GPT model with detailed writing scoring rubrics and linguistic features, potential biases in human ratings can be mitigated. The model follows a predefined set of guidelines and does not possess the same subjective biases that human raters may exhibit. This standardization in the evaluation process contributes to the higher agreement observed between GPT-4 and human scoring. Section Prompt strategy of the study delves further into the role of prompts in the application of LLMs to AES. It explores how the choice and implementation of prompts can impact the performance and reliability of LLM-based AES methods. Furthermore, it is important to acknowledge the strengths of the local model, i.e. the Japanese local model OCLL, which excels in processing certain idiomatic expressions. Nevertheless, our analysis indicated that GPT-4 surpasses local models in AES. This superior performance can be attributed to the larger parameter size of GPT-4, estimated to be between 500 billion and 1 trillion, which exceeds the sizes of both BERT and the local model OCLL.
Prompt strategy
In the context of prompt strategy, Mizumoto and Eguchi ( 2023 ) conducted a study where they applied the GPT-3 model to automatically score English essays in the TOEFL test. They found that the accuracy of the GPT model alone was moderate to fair. However, when they incorporated linguistic measures such as cohesion, syntactic complexity, and lexical features alongside the GPT model, the accuracy significantly improved. This highlights the importance of prompt engineering and providing the model with specific instructions to enhance its performance. In this study, a similar approach was taken to optimize the performance of LLMs. GPT-4, which outperformed BERT and OCLL, was selected as the candidate model. Model 1 was used as the baseline, representing GPT-4 without any additional prompting. Model 2, on the other hand, involved GPT-4 prompted with 16 measures that included scoring criteria, efficient linguistic features for writing assessment, and detailed measurement units and calculation formulas. The remaining models (Models 3 to 18) utilized GPT-4 prompted with individual measures. The performance of these 18 different models was assessed using the output indicators described in Section Criteria (output indicator) . By comparing the performances of these models, the study aimed to understand the impact of prompt engineering on the accuracy and effectiveness of GPT-4 in AES tasks.
Based on the PRMSE scores presented in Fig. 4 , it was observed that Model 1, representing GPT-4 without any additional prompting, achieved a fair level of performance. However, Model 2, which utilized GPT-4 prompted with all measures, outperformed all other models in terms of PRMSE score, achieving a score of 0.681. These results indicate that the inclusion of specific measures and prompts significantly enhanced the performance of GPT-4 in AES. Among the measures, syntactic complexity was found to play a particularly significant role in improving the accuracy of GPT-4 in assessing writing quality. Following that, lexical diversity emerged as another important factor contributing to the model’s effectiveness. The study suggests that a well-prompted GPT-4 can serve as a valuable tool to support human assessors in evaluating writing quality. By utilizing GPT-4 as an automated scoring tool, the evaluation biases associated with human raters can be minimized. This has the potential to empower teachers by allowing them to focus on designing writing tasks and guiding writing strategies, while leveraging the capabilities of GPT-4 for efficient and reliable scoring.
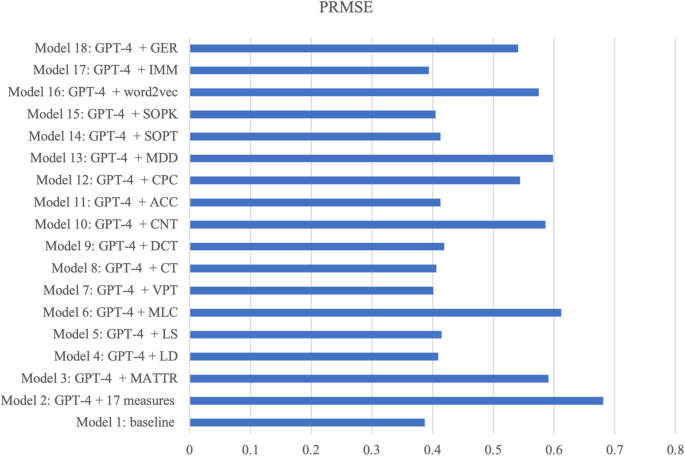
PRMSE scores of the 18 AES models.
This study aimed to investigate two main research questions: the feasibility of utilizing LLMs for AES and the impact of prompt engineering on the application of LLMs in AES.
To address the first objective, the study compared the effectiveness of five different models: GPT, BERT, the Japanese local LLM (OCLL), and two conventional machine learning-based AES tools (Jess and JWriter). The PRMSE values indicated that the GPT-4-based method outperformed other LLMs (BERT, OCLL) and linguistic feature-based computational methods (Jess and JWriter) across various writing proficiency criteria. Furthermore, the agreement coefficient between GPT-4 and human scoring surpassed the agreement among human raters themselves, highlighting the potential of using the GPT-4 tool to enhance AES by reducing biases and subjectivity, saving time, labor, and cost, and providing valuable feedback for self-study. Regarding the second goal, the role of prompt design was investigated by comparing 18 models, including a baseline model, a model prompted with all measures, and 16 models prompted with one measure at a time. GPT-4, which outperformed BERT and OCLL, was selected as the candidate model. The PRMSE scores of the models showed that GPT-4 prompted with all measures achieved the best performance, surpassing the baseline and other models.
In conclusion, this study has demonstrated the potential of LLMs in supporting human rating in assessments. By incorporating automation, we can save time and resources while reducing biases and subjectivity inherent in human rating processes. Automated language assessments offer the advantage of accessibility, providing equal opportunities and economic feasibility for individuals who lack access to traditional assessment centers or necessary resources. LLM-based language assessments provide valuable feedback and support to learners, aiding in the enhancement of their language proficiency and the achievement of their goals. This personalized feedback can cater to individual learner needs, facilitating a more tailored and effective language-learning experience.
There are three important areas that merit further exploration. First, prompt engineering requires attention to ensure optimal performance of LLM-based AES across different language types. This study revealed that GPT-4, when prompted with all measures, outperformed models prompted with fewer measures. Therefore, investigating and refining prompt strategies can enhance the effectiveness of LLMs in automated language assessments. Second, it is crucial to explore the application of LLMs in second-language assessment and learning for oral proficiency, as well as their potential in under-resourced languages. Recent advancements in self-supervised machine learning techniques have significantly improved automatic speech recognition (ASR) systems, opening up new possibilities for creating reliable ASR systems, particularly for under-resourced languages with limited data. However, challenges persist in the field of ASR. First, ASR assumes correct word pronunciation for automatic pronunciation evaluation, which proves challenging for learners in the early stages of language acquisition due to diverse accents influenced by their native languages. Accurately segmenting short words becomes problematic in such cases. Second, developing precise audio-text transcriptions for languages with non-native accented speech poses a formidable task. Last, assessing oral proficiency levels involves capturing various linguistic features, including fluency, pronunciation, accuracy, and complexity, which are not easily captured by current NLP technology.
Data availability
The dataset utilized was obtained from the International Corpus of Japanese as a Second Language (I-JAS). The data URLs: [ https://www2.ninjal.ac.jp/jll/lsaj/ihome2.html ].
J-CAT and TTBJ are two computerized adaptive tests used to assess Japanese language proficiency.
SPOT is a specific component of the TTBJ test.
J-CAT: https://www.j-cat2.org/html/ja/pages/interpret.html
SPOT: https://ttbj.cegloc.tsukuba.ac.jp/p1.html#SPOT .
The study utilized a prompt-based GPT-4 model, developed by OpenAI, which has an impressive architecture with 1.8 trillion parameters across 120 layers. GPT-4 was trained on a vast dataset of 13 trillion tokens, using two stages: initial training on internet text datasets to predict the next token, and subsequent fine-tuning through reinforcement learning from human feedback.
https://www2.ninjal.ac.jp/jll/lsaj/ihome2-en.html .
http://jhlee.sakura.ne.jp/JEV/ by Japanese Learning Dictionary Support Group 2015.
We express our sincere gratitude to the reviewer for bringing this matter to our attention.
On February 7, 2023, Microsoft began rolling out a major overhaul to Bing that included a new chatbot feature based on OpenAI’s GPT-4 (Bing.com).
Appendix E-F present the analysis results of the QWK coefficient between the scores computed by the human raters and the BERT, OCLL models.
Attali Y, Burstein J (2006) Automated essay scoring with e-rater® V.2. J. Technol., Learn. Assess., 4
Barkaoui K, Hadidi A (2020) Assessing Change in English Second Language Writing Performance (1st ed.). Routledge, New York. https://doi.org/10.4324/9781003092346
Bentz C, Tatyana R, Koplenig A, Tanja S (2016) A comparison between morphological complexity. measures: Typological data vs. language corpora. In Proceedings of the workshop on computational linguistics for linguistic complexity (CL4LC), 142–153. Osaka, Japan: The COLING 2016 Organizing Committee
Bond TG, Yan Z, Heene M (2021) Applying the Rasch model: Fundamental measurement in the human sciences (4th ed). Routledge
Brants T (2000) Inter-annotator agreement for a German newspaper corpus. Proceedings of the Second International Conference on Language Resources and Evaluation (LREC’00), Athens, Greece, 31 May-2 June, European Language Resources Association
Brown TB, Mann B, Ryder N, et al. (2020) Language models are few-shot learners. Advances in Neural Information Processing Systems, Online, 6–12 December, Curran Associates, Inc., Red Hook, NY
Burstein J (2003) The E-rater scoring engine: Automated essay scoring with natural language processing. In Shermis MD and Burstein JC (ed) Automated Essay Scoring: A Cross-Disciplinary Perspective. Lawrence Erlbaum Associates, Mahwah, NJ
Čech R, Miroslav K (2018) Morphological richness of text. In Masako F, Václav C (ed) Taming the corpus: From inflection and lexis to interpretation, 63–77. Cham, Switzerland: Springer Nature
Çöltekin Ç, Taraka, R (2018) Exploiting Universal Dependencies treebanks for measuring morphosyntactic complexity. In Aleksandrs B, Christian B (ed), Proceedings of first workshop on measuring language complexity, 1–7. Torun, Poland
Crossley SA, Cobb T, McNamara DS (2013) Comparing count-based and band-based indices of word frequency: Implications for active vocabulary research and pedagogical applications. System 41:965–981. https://doi.org/10.1016/j.system.2013.08.002
Article Google Scholar
Crossley SA, McNamara DS (2016) Say more and be more coherent: How text elaboration and cohesion can increase writing quality. J. Writ. Res. 7:351–370
CyberAgent Inc (2023) Open-Calm series of Japanese language models. Retrieved from: https://www.cyberagent.co.jp/news/detail/id=28817
Devlin J, Chang MW, Lee K, Toutanova K (2019) BERT: Pre-training of deep bidirectional transformers for language understanding. Proceedings of the 2019 Conference of the North American Chapter of the Association for Computational Linguistics, Minneapolis, Minnesota, 2–7 June, pp. 4171–4186. Association for Computational Linguistics
Diez-Ortega M, Kyle K (2023) Measuring the development of lexical richness of L2 Spanish: a longitudinal learner corpus study. Studies in Second Language Acquisition 1-31
Eckes T (2009) On common ground? How raters perceive scoring criteria in oral proficiency testing. In Brown A, Hill K (ed) Language testing and evaluation 13: Tasks and criteria in performance assessment (pp. 43–73). Peter Lang Publishing
Elliot S (2003) IntelliMetric: from here to validity. In: Shermis MD, Burstein JC (ed) Automated Essay Scoring: A Cross-Disciplinary Perspective. Lawrence Erlbaum Associates, Mahwah, NJ
Google Scholar
Engber CA (1995) The relationship of lexical proficiency to the quality of ESL compositions. J. Second Lang. Writ. 4:139–155
Garner J, Crossley SA, Kyle K (2019) N-gram measures and L2 writing proficiency. System 80:176–187. https://doi.org/10.1016/j.system.2018.12.001
Haberman SJ (2008) When can subscores have value? J. Educat. Behav. Stat., 33:204–229
Haberman SJ, Yao L, Sinharay S (2015) Prediction of true test scores from observed item scores and ancillary data. Brit. J. Math. Stat. Psychol. 68:363–385
Halliday MAK (1985) Spoken and Written Language. Deakin University Press, Melbourne, Australia
Hirao R, Arai M, Shimanaka H et al. (2020) Automated essay scoring system for nonnative Japanese learners. Proceedings of the 12th Conference on Language Resources and Evaluation (LREC 2020), pp. 1250–1257. European Language Resources Association
Hunt KW (1966) Recent Measures in Syntactic Development. Elementary English, 43(7), 732–739. http://www.jstor.org/stable/41386067
Ishioka T (2001) About e-rater, a computer-based automatic scoring system for essays [Konpyūta ni yoru essei no jidō saiten shisutemu e − rater ni tsuite]. University Entrance Examination. Forum [Daigaku nyūshi fōramu] 24:71–76
Hochreiter S, Schmidhuber J (1997) Long short- term memory. Neural Comput. 9(8):1735–1780
Article CAS PubMed Google Scholar
Ishioka T, Kameda M (2006) Automated Japanese essay scoring system based on articles written by experts. Proceedings of the 21st International Conference on Computational Linguistics and 44th Annual Meeting of the Association for Computational Linguistics, Sydney, Australia, 17–18 July 2006, pp. 233-240. Association for Computational Linguistics, USA
Japan Foundation (2021) Retrieved from: https://www.jpf.gp.jp/j/project/japanese/survey/result/dl/survey2021/all.pdf
Jarvis S (2013a) Defining and measuring lexical diversity. In Jarvis S, Daller M (ed) Vocabulary knowledge: Human ratings and automated measures (Vol. 47, pp. 13–44). John Benjamins. https://doi.org/10.1075/sibil.47.03ch1
Jarvis S (2013b) Capturing the diversity in lexical diversity. Lang. Learn. 63:87–106. https://doi.org/10.1111/j.1467-9922.2012.00739.x
Jiang J, Quyang J, Liu H (2019) Interlanguage: A perspective of quantitative linguistic typology. Lang. Sci. 74:85–97
Kim M, Crossley SA, Kyle K (2018) Lexical sophistication as a multidimensional phenomenon: Relations to second language lexical proficiency, development, and writing quality. Mod. Lang. J. 102(1):120–141. https://doi.org/10.1111/modl.12447
Kojima T, Gu S, Reid M et al. (2022) Large language models are zero-shot reasoners. Advances in Neural Information Processing Systems, New Orleans, LA, 29 November-1 December, Curran Associates, Inc., Red Hook, NY
Kyle K, Crossley SA (2015) Automatically assessing lexical sophistication: Indices, tools, findings, and application. TESOL Q 49:757–786
Kyle K, Crossley SA, Berger CM (2018) The tool for the automatic analysis of lexical sophistication (TAALES): Version 2.0. Behav. Res. Methods 50:1030–1046. https://doi.org/10.3758/s13428-017-0924-4
Article PubMed Google Scholar
Kyle K, Crossley SA, Jarvis S (2021) Assessing the validity of lexical diversity using direct judgements. Lang. Assess. Q. 18:154–170. https://doi.org/10.1080/15434303.2020.1844205
Landauer TK, Laham D, Foltz PW (2003) Automated essay scoring and annotation of essays with the Intelligent Essay Assessor. In Shermis MD, Burstein JC (ed), Automated Essay Scoring: A Cross-Disciplinary Perspective. Lawrence Erlbaum Associates, Mahwah, NJ
Landis JR, Koch GG (1977) The measurement of observer agreement for categorical data. Biometrics 159–174
Laufer B, Nation P (1995) Vocabulary size and use: Lexical richness in L2 written production. Appl. Linguist. 16:307–322. https://doi.org/10.1093/applin/16.3.307
Lee J, Hasebe Y (2017) jWriter Learner Text Evaluator, URL: https://jreadability.net/jwriter/
Lee J, Kobayashi N, Sakai T, Sakota K (2015) A Comparison of SPOT and J-CAT Based on Test Analysis [Tesuto bunseki ni motozuku ‘SPOT’ to ‘J-CAT’ no hikaku]. Research on the Acquisition of Second Language Japanese [Dainigengo to shite no nihongo no shūtoku kenkyū] (18) 53–69
Li W, Yan J (2021) Probability distribution of dependency distance based on a Treebank of. Japanese EFL Learners’ Interlanguage. J. Quant. Linguist. 28(2):172–186. https://doi.org/10.1080/09296174.2020.1754611
Article MathSciNet Google Scholar
Linacre JM (2002) Optimizing rating scale category effectiveness. J. Appl. Meas. 3(1):85–106
PubMed Google Scholar
Linacre JM (1994) Constructing measurement with a Many-Facet Rasch Model. In Wilson M (ed) Objective measurement: Theory into practice, Volume 2 (pp. 129–144). Norwood, NJ: Ablex
Liu H (2008) Dependency distance as a metric of language comprehension difficulty. J. Cognitive Sci. 9:159–191
Liu H, Xu C, Liang J (2017) Dependency distance: A new perspective on syntactic patterns in natural languages. Phys. Life Rev. 21. https://doi.org/10.1016/j.plrev.2017.03.002
Loukina A, Madnani N, Cahill A, et al. (2020) Using PRMSE to evaluate automated scoring systems in the presence of label noise. Proceedings of the Fifteenth Workshop on Innovative Use of NLP for Building Educational Applications, Seattle, WA, USA → Online, 10 July, pp. 18–29. Association for Computational Linguistics
Lu X (2010) Automatic analysis of syntactic complexity in second language writing. Int. J. Corpus Linguist. 15:474–496
Lu X (2012) The relationship of lexical richness to the quality of ESL learners’ oral narratives. Mod. Lang. J. 96:190–208
Lu X (2017) Automated measurement of syntactic complexity in corpus-based L2 writing research and implications for writing assessment. Lang. Test. 34:493–511
Lu X, Hu R (2022) Sense-aware lexical sophistication indices and their relationship to second language writing quality. Behav. Res. Method. 54:1444–1460. https://doi.org/10.3758/s13428-021-01675-6
Ministry of Health, Labor, and Welfare of Japan (2022) Retrieved from: https://www.mhlw.go.jp/stf/newpage_30367.html
Mizumoto A, Eguchi M (2023) Exploring the potential of using an AI language model for automated essay scoring. Res. Methods Appl. Linguist. 3:100050
Okgetheng B, Takeuchi K (2024) Estimating Japanese Essay Grading Scores with Large Language Models. Proceedings of 30th Annual Conference of the Language Processing Society in Japan, March 2024
Ortega L (2015) Second language learning explained? SLA across 10 contemporary theories. In VanPatten B, Williams J (ed) Theories in Second Language Acquisition: An Introduction
Rae JW, Borgeaud S, Cai T, et al. (2021) Scaling Language Models: Methods, Analysis & Insights from Training Gopher. ArXiv, abs/2112.11446
Read J (2000) Assessing vocabulary. Cambridge University Press. https://doi.org/10.1017/CBO9780511732942
Rudner LM, Liang T (2002) Automated Essay Scoring Using Bayes’ Theorem. J. Technol., Learning and Assessment, 1 (2)
Sakoda K, Hosoi Y (2020) Accuracy and complexity of Japanese Language usage by SLA learners in different learning environments based on the analysis of I-JAS, a learners’ corpus of Japanese as L2. Math. Linguist. 32(7):403–418. https://doi.org/10.24701/mathling.32.7_403
Suzuki N (1999) Summary of survey results regarding comprehensive essay questions. Final report of “Joint Research on Comprehensive Examinations for the Aim of Evaluating Applicability to Each Specialized Field of Universities” for 1996-2000 [shōronbun sōgō mondai ni kansuru chōsa kekka no gaiyō. Heisei 8 - Heisei 12-nendo daigaku no kaku senmon bun’ya e no tekisei no hyōka o mokuteki to suru sōgō shiken no arikata ni kansuru kyōdō kenkyū’ saishū hōkoku-sho]. University Entrance Examination Section Center Research and Development Department [Daigaku nyūshi sentā kenkyū kaihatsubu], 21–32
Taghipour K, Ng HT (2016) A neural approach to automated essay scoring. Proceedings of the 2016 Conference on Empirical Methods in Natural Language Processing, Austin, Texas, 1–5 November, pp. 1882–1891. Association for Computational Linguistics
Takeuchi K, Ohno M, Motojin K, Taguchi M, Inada Y, Iizuka M, Abo T, Ueda H (2021) Development of essay scoring methods based on reference texts with construction of research-available Japanese essay data. In IPSJ J 62(9):1586–1604
Ure J (1971) Lexical density: A computational technique and some findings. In Coultard M (ed) Talking about Text. English Language Research, University of Birmingham, Birmingham, England
Vaswani A, Shazeer N, Parmar N, et al. (2017) Attention is all you need. In Advances in Neural Information Processing Systems, Long Beach, CA, 4–7 December, pp. 5998–6008, Curran Associates, Inc., Red Hook, NY
Watanabe H, Taira Y, Inoue Y (1988) Analysis of essay evaluation data [Shōronbun hyōka dēta no kaiseki]. Bulletin of the Faculty of Education, University of Tokyo [Tōkyōdaigaku kyōiku gakubu kiyō], Vol. 28, 143–164
Yao S, Yu D, Zhao J, et al. (2023) Tree of thoughts: Deliberate problem solving with large language models. Advances in Neural Information Processing Systems, 36
Zenker F, Kyle K (2021) Investigating minimum text lengths for lexical diversity indices. Assess. Writ. 47:100505. https://doi.org/10.1016/j.asw.2020.100505
Zhang Y, Warstadt A, Li X, et al. (2021) When do you need billions of words of pretraining data? Proceedings of the 59th Annual Meeting of the Association for Computational Linguistics and the 11th International Joint Conference on Natural Language Processing, Online, pp. 1112-1125. Association for Computational Linguistics. https://doi.org/10.18653/v1/2021.acl-long.90
Download references
This research was funded by National Foundation of Social Sciences (22BYY186) to Wenchao Li.
Author information
Authors and affiliations.
Department of Japanese Studies, Zhejiang University, Hangzhou, China
Department of Linguistics and Applied Linguistics, Zhejiang University, Hangzhou, China
You can also search for this author in PubMed Google Scholar
Contributions
Wenchao Li is in charge of conceptualization, validation, formal analysis, investigation, data curation, visualization and writing the draft. Haitao Liu is in charge of supervision.
Corresponding author
Correspondence to Wenchao Li .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Ethical approval
Ethical approval was not required as the study did not involve human participants.
Informed consent
This article does not contain any studies with human participants performed by any of the authors.
Additional information
Publisher’s note Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary information
Supplemental material file #1, rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Li, W., Liu, H. Applying large language models for automated essay scoring for non-native Japanese. Humanit Soc Sci Commun 11 , 723 (2024). https://doi.org/10.1057/s41599-024-03209-9
Download citation
Received : 02 February 2024
Accepted : 16 May 2024
Published : 03 June 2024
DOI : https://doi.org/10.1057/s41599-024-03209-9
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Skip to Content
Open(AI) and shut: What ChatGPT deals with media outlets mean for the future of news
You are here.
- Share via Twitter
- Share via Facebook
- Share via LinkedIn
- Share via E-mail
By Joe Arney Photo of Patrick Ferrucci, below, by Kimberly Coffin (CritMedia, StratComm’18)

A former reporter and current chair of the journalism department at the University of Colorado Boulder’s College of Media, Communication and Information, Ferrucci studies the institutions, businesses and technologies that are rapidly reshaping the discipline.
So when he learned The Atlantic and Vox Media agreed last week to license their journalism to ChatGPT creator OpenAI, he thought back to agreements traditional publishers once signed with Facebook, Google and Twitter—deals that augmented audiences while wrecking revenue.
“I don’t get it,” he said.
“Maybe they see a monetary infusion at what’s undeniably a difficult financial time for the media. But we’ve seen this before, and each time, that financial infusion doesn’t benefit the actual journalism.”
ChatGPT was hailed as a breakthrough when it arrived in the winter of 2022, able to respond to questions and create content that was seen as a value add for businesses and individuals. Some of the shine has since worn off as creators and artists have accused the company of stealing their work to train the chatbot to write more convincingly—the large-language models ChatGPT are trained on enormous amounts of data that come from novelists, poets, journalists, even regular users of social media platforms who post content and comments.
“We’ve seen this before, and each time, that financial infusion doesn’t benefit the actual journalism.” Patrick Ferrucci, chair, journalism
While he criticized the short-term benefits at the potential cost of long-term viability, Ferrucci said there could be other advantages for media companies that sign up with OpenAI.
“It could allow the journalism industry to get an understanding of what those tools can do,” he said. “And if they get a head start with those tools, and learn to implement them into their processes early on, it will give them a leg up on companies that fought against it.”
A different tactic: See you in court
Representing those companies fighting against it is The New York Times , which last year sued OpenAI after changing its terms of service to prevent A.I. systems from scraping its work . At the time, Robin Burke , a professor of information science at CMCI, called ChatGPT’s honeymoon period “a free ride, because nobody was paying attention to what they were doing. Now, I think it makes sense that the organizations producing content are thinking, ‘Do I really agree with this as a usage of my work?’”
It’s a fair question, but Ferrucci said he expects we’ll see more deals like this going forward.
“There are companies that can do investigative journalism because it doesn’t matter if you sue them,” he said. “And there are others who essentially self-censor because the threat of a lawsuit, no matter how frivolous, could destroy the business. If you show these news companies some money, I don’t think all of them can afford to look away.”

But for her, the most interesting issue isn’t copyright.
“I think the more profound thing is this idea that you used my work to build a technology that will replace me,” she said. “That’s why so many people are upset. It feels like a violation—you’re using my art to build this technology so that you don’t have to pay artists anymore.”
- information science
Apply Visit Donate
Thanks for your interest in CU Boulder’s College of Media, Communication and Information. We welcome your questions or comments and will respond as quickly as possible.
AT&T resolves service issue reported across US

The "nationwide issue" that affected communication between AT&T customers and other non-AT&T customers was resolved Tuesday, the company said.
AT&T customers reported a loss or disruption to services Tuesday afternoon, with those serviced by the carrier writing on social media that they could not make calls or send texts. The total number of customers impacted by the issue was not immediately available.
The company said they were "working as quickly as possible to diagnose and resolve the issue," reporting a couple hours later that "the interoperability issue between carriers had been resolved."
"We collaborated with the other carrier to find a solution and appreciate our customers patience during this period," an AT&T spokesperson shared with USA TODAY.
AT&T customers were still able to make calls between other AT&T customers and calls to emergency services.
The Federal Communications Commission chimed in as the situation developed, writing on X that the agency would be investigating why "consumers in multiple states are unable to make wireless calls."
Verizon customers also report service loss
AT&T wasn't the only telecommunications company dealing with network issues. Verizon customers began to report disruption and loss of service around the same time.
A Verizon spokesperson said its network was operating normally, but that customers "in the Northeast and Midwest, are experiencing issues when calling or texting with customers served by another carrier." And that they would continue to monitor the situation accordingly.
Verizon could not be reached for comment Tuesday night.
AT&T, Verizon customers were over it, react accordingly
At&t customers were left in the dark earlier this year.
Millions of AT&T customers experienced issues with their service earlier this year, when the company reported that a "technical error" was the reason why customers were unable to make calls or send messages for most of Feb. 22, USA TODAY reported.
The company formally addressed the outage days later, stating that "the application and execution of an incorrect process" was the reason for the malfunction. And that they were not victims of a "cyberattack."
A $5 rebate was offered to customers who were impacted by the outage.
This is a developing story, check back for updates.
Contributing: Mike Snider
- Skip to main content
- Skip to search
- Skip to footer
Products and Services
Routers and SD-WAN appliances
Connect and protect every network.
Connect and secure networks of any scale—from the edge to the cloud.
Discover smarter, more secure routing
Build an intelligent, self-defending network with advanced analytics, automated provisioning, and integrated security.
Protect your users and data
Boost security from the WAN to the cloud, with trusted authentication, robust encryption, and granular segmentation.
Accelerate your deployment
Deploy integrated network services on demand—anywhere, anytime.
Transform application experience
Get in-depth analytics, visibility, and control to make excellent application experience a cornerstone of your operations.
Centralize network management
Easily deploy SD-WAN and security while maintaining policy across thousands of sites.

Build a resilient and secure SD-WAN.

Future-ready routers for every network
cisco catalyst 8300 series edge platforms.
Get SASE-ready with SD-WAN, cloud-native agility, multilayer security, flexible routing, and edge intelligence.
Cisco Catalyst 8200 Series Edge Platforms
Move to secure access service edge (SASE) with secure and scalable SD-WAN and intelligent multicloud connectivity.
Cisco 1000 Series Integrated Services Routers
Boost performance with advanced security, multicloud access, and wireless capability—in one device.
Cisco Meraki MX security and SD-WAN appliances
Build a complete SD-branch on a cloud-first platform with secure SD-WAN, access, and IoT.
Fixed wireless access devices
Deliver secure, reliable, and scalable connectivity for remote and branch offices.
Hybrid work
Cisco remote worker gateways.
Experience reliable connectivity with enterprise Wi-Fi access at home without the need for a VPN.
Industrial
Cisco catalyst ir1100 rugged series routers.
Securely connect remote industrial operations with this rugged, compact, and modular SD-WAN-enabled router.
Cisco Catalyst IR1800 Rugged Series Routers
Speed digitization at the mobile edge, with high performance and industry-leading flexibility.
Cisco Catalyst IR8100 Heavy Duty Series Routers
Unite your outdoor edge with this IP67-rated and SD-WAN-enabled router that’s fully modular.
Cisco Catalyst IR8300 Rugged Series Routers
Deliver peak industrial networking and SD-WAN performance with rugged all-in-one routing and switching.
Service providers
Cisco 8000 series routers.
Deliver the performance and scale to build the internet of the future with cloud-enhanced systems.
Cisco Network Convergence System 5700 Series Routers
Scale with high-density 400G routers for long-term growth and segment routing for SLA-based services.
Cisco ASR 9000 Series Aggregation Services Routers
Support the application performance required to power your services with scalable routing systems.
Cisco Network Convergence System 500 Series Routers
Simplify your access network and converge services with these secure and programmable routers.
Small business
Streamline your small business with secure SD-WAN, access, and IoT on a cloud-first platform.
Cisco 1000 Series Integrated Services Routers
Boost performance with advanced security, multicloud access, and wireless capability—in one device.
Cisco 900 Series Integrated Services Routers
Combine WAN, switching, security, and advanced connectivity options in a compact, fanless platform.
Cisco Catalyst 8000V Edge Software
Optimize applications and enhance user experience with secure, multicloud connectivity.
Cisco Meraki vMX appliances
Securely extend SD-WAN to public and private cloud infrastructure-as-a-service (IaaS) environments in three clicks.
Cisco IOS XRd Virtual Router
Experience greater agility, improved network efficiency, and lower costs with virtual and containerized routers.

Find a fast route to value
Power your network with secure and reliable experiences for campus, branch, edge, and data center.
Explore routing solutions
Cisco catalyst sd-wan.
Lower costs and complexity, and enrich the user experience at your branches.
Secure access where users and applications reside, with one cloud-native service.
For service providers
Deliver quality services fast and easily with advanced network automation.
Support to get you started
Cisco Success Tracks
Make the most of your IT investment
Optimize the value of your routing solutions for faster results, with digital insights and services expertise.
Business Critical Services
Move your business forward faster
Modernize IT environments and boost agility with analytics-driven advisory services.
Find your router
Compare and contrast Cisco routers of all types and sizes. Quickly find the router to meet your needs.

COMMENTS
As mobile phone technology continues to evolve, it is crucial to adapt our habits and practices to ensure that mobile phones enhance our lives without compromising our well-being and social connections. Here we have shared the Essay on Mobile Phone in detail so you can use it in your exam or assignment of 150, 250, 400, 500, or 1000 words.
500+ Words Essay on Mobile Phone. Essay on Mobile Phone: Mobile Phone is often also called "cellular phone". It is a device mainly used for a voice call. Presently technological advancements have made our life easy. Today, with the help of a mobile phone we can easily talk or video chat with anyone across the globe by just moving our fingers.
Mobile Phones and True Communication Essay. Communication is the conveyance of information, experience, emotion and so on between two parties through a certain channel. It should be true or sincere (without the need for clarification). The receiver should perceive the message in the right format intended by the sender.
As with every disruptive technology, mobile phones have negative attributes as well. Perhaps we first realized this in 1989 when mobile phones first rang in movie theaters. While some may have been annoyed or angered, we were dismayed. Our abiding belief in the potential of the mobile phone blinded us to the ways in which it could be antisocial.
Sample Essay on Mobile Phone (500 words) Mobile Phone is a portable telephone that performs a variety of functions for its users. The smartphone can be used to text, call, watch movies, listen to music, and even use social media applications. This cellular device has its own advantages and disadvantages.
The smartphone has "invaded every sphere of our lives" (Ling, 2012: xi).But while smartphones are becoming an essential part of our communication toolkit (Ling, 2012; Schnauber-Stockmann and Karnowski, 2020), the omnipresence of mobile communication also poses new methodological challenges.Traditional surveys do not capture dynamic and short-lived mobile communication episodes and using ...
The impact of mobile communication development is personal communication services. Between 1960 and 1970, Bell Laboratories developed the cellular concepts. An exponential growth was observed in wireless communication. Wireless technologies penetration is witnessed more in our day to day lives as compared to other communications.
See here what this mobile phone paragraph has to say. Stay connected: - Mobile phones are the best way to stay connected with your friends and family living away from you. Voice calls, video calls, emails, messages and texts- thus, the communication modes via cell phones are multitude. Mode of entertainment: - As technology advances, you ...
Abstract. This chapter introduces the evolution of mobile communications. As the mobile communications' context is expected to become increasingly platform-based and ecosystemic, it is important to distinguish relevant perspectives and map the developments in the field. This chapter provides an outlook from the first (1G) to fifth (5G ...
The devices have given us access to news, information, shopping, and entertainment. In addition, they have facilitated threats to our privacy and cyberbullying. This book examines the evolving nature of mobile communication. Keywords: Mobile theory, Mobile convergence, Mobile methods, Mobile communication and the social sphere, Social ...
250 Words Essay on Impact Of Mobile Phones On Society Changes in Communication. Mobile phones have changed the way we talk to each other. Before, people would write letters or use landlines to chat. Now, with mobiles, we can send messages, make calls, and even see each other on video anytime and anywhere. This makes staying in touch with ...
The distinct life of the mobile communications has taken different phases. This can be traced from the 1G to the most rest 4G. G, 2G, 3G and 4G are a wireless phone or a cellular phone standard way of classification based on generations/ cellular phone evolution. This paper is a critical comparison of all these technological generations with an ...
A.1 Mobile phones are very advantageous. They help us in making our lives easy and convenient. They help us communicate with our loved ones and carry out our work efficiently. Furthermore, they also do the work of the computer, calculator, and cameras.
The Evolution Of Mobile Communication 1 Evolution of Mobile Communication A mobile communication is evaluates through different generations: First Generation(1G): First generation of mobile communication developed in 1980 's and completed in early 1990 's based on analog system systems are based on AMPS(Advanced
The metaphorical richness of mobile communication The close tie between mobile communication and social practices and meaning-making can also be seen in its metaphorical richness. An area that has turned out to be particularly rich in metaphors is 'mobile time', which is often connected with spatiality, 'mobile time-space' (Arminen, 2007).
Essay on Mobile Phone: 250 Words. A mobile phone or cell phone is a hand-held portable radiophone that uses the cellular or satellite network for voice or data communication. Unlike landline phones, which are fixed, mobile phones can be easily carried, and one can contact a person anywhere whether at home, on the bus, in street, or in a meeting.
PDF | On Dec 1, 2007, Ilkka Arminen published Review Essay Mobile Communication Society? | Find, read and cite all the research you need on ResearchGate
Advantages and Disadvantages of Mobile Phone Essay 100 words. There are advantages and disadvantages to mobile phones. First, let's discuss the positive aspects. Our mobile phones facilitate easy communication with friends and family. With our phones, we may use the internet to discover new things as well.
1. Introduction. Over the last three decades, mobile communication networks have undergone significant revolutionary development [1], [2], [3].Several emerging applications and sectors have rapidly grown to include the internet of everything (IoE), virtual reality (VR), three-dimensional (3D) media, artificial intelligence (AI), machine-to-machine (M2M) communication, enhanced mobile broadband ...
The rise of the fifth generation of mobile wireless communications (5G) is driving significant scientific and technological progress in the area of mobile systems and networks. This first appearance of the new Mobile Communications and Networks Series addresses some of the most significant aspects of 5G networks, providing key insights into relevant system and network design challenges, as ...
Arminen, I. ( 2007) ` Mobile Time-Space — Arena for New Kinds of Social Actions ', Mobile Communication Research Annual 1. Google Scholar. Arminen, I. and Leinonen, M. ( 2006) ` Mobile Phone Call Openings — Tailoring Answers to Personalized Summons ', Discourse Studies 8: 339 — 68. Google Scholar | SAGE Journals | ISI.
Essay On Mobile Communication. 2357 Words10 Pages. Global System for Mobile Communication is the most widely means of communication today. This, though useful may pose great nuisance in noise restricted areas such as classrooms, churches, mosques, Libraries, hospitals etc. Mobile phone jammers are employed to prevent mobile phones from ...
Mission. The Purdue On-Campus Writing Lab and Purdue Online Writing Lab assist clients in their development as writers—no matter what their skill level—with on-campus consultations, online participation, and community engagement. The Purdue Writing Lab serves the Purdue, West Lafayette, campus and coordinates with local literacy initiatives.
Recent advancements in artificial intelligence (AI) have led to an increased use of large language models (LLMs) for language assessment tasks such as automated essay scoring (AES), automated ...
By Joe Arney Photo of Patrick Ferrucci, below, by Kimberly Coffin (CritMedia, StratComm'18) Patrick Ferrucci has seen this movie before. A former reporter and current chair of the journalism department at the University of Colorado Boulder's College of Media, Communication and Information, Ferrucci studies the institutions, businesses and technologies that are rapidly reshaping the discipline.
Browse Calls for Papers beta. Browse 5,060 journals and 35,600 books. A; A Review on Diverse Neurological Disorders. Pathophysiology, Molecular Mechanisms, and Therapeutics. ... Academic Press Library in Mobile and Wireless Communications. Transmission Techniques for Digital Communications. Book • 2016. Academic Press Library in Signal ...
A Message from Our Chief Communications & Corporate Responsibility Officer. By Janice V. Kapner, Chief Communications and Corporate Responsibility OfficerJune 03, 2024. 2 min read Listen. As we continue into the next chapter of the Un-carrier, we remain committed to using our network, scale, and resources for good while building a more ...
Mobile Media & Communication is looking for a new Editor to join Adriana de Souza e Silva from February 2025. The application deadline is 6th September 2024. This journal is a peer-reviewed forum for international, interdisciplinary academic research on the dynamic field of mobile media and communication.
0:04. 0:51. The "nationwide issue" that affected communication between AT&T customers and other non-AT&T customers was resolved Tuesday, the company said. AT&T customers reported a loss or ...
Transform application experience. Get in-depth analytics, visibility, and control to make excellent application experience a cornerstone of your operations. Centralize network management. Easily deploy SD-WAN and security while maintaining policy across thousands of sites. Build a resilient and secure SD-WAN.