Networking | Cloud | DevOps | IaC

IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server is an important element to networking in the real world. User location cannot be predicted as they may be at and out of a desk and up and about should they need to do so. Tying them to a local VLAN may only be helpful if they are bound to desks in those locations, although the most ideal outcome, it is not the most practical.
It is only wise to incorporate IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server in areas where you expect different teams to come to. Meeting rooms could for a moment have the accounting group or the development group meeting there and based on the intelligent and dynamic vlan assignmnet with 802.1x authentication, users port-access are defined their appropriate vlans for their respective access to resources on the network.
How to Provision 802.1 X Authentication Step By Step With Dynamic VLAN Assignment With Windows Radius Server For 802.1x Clients.
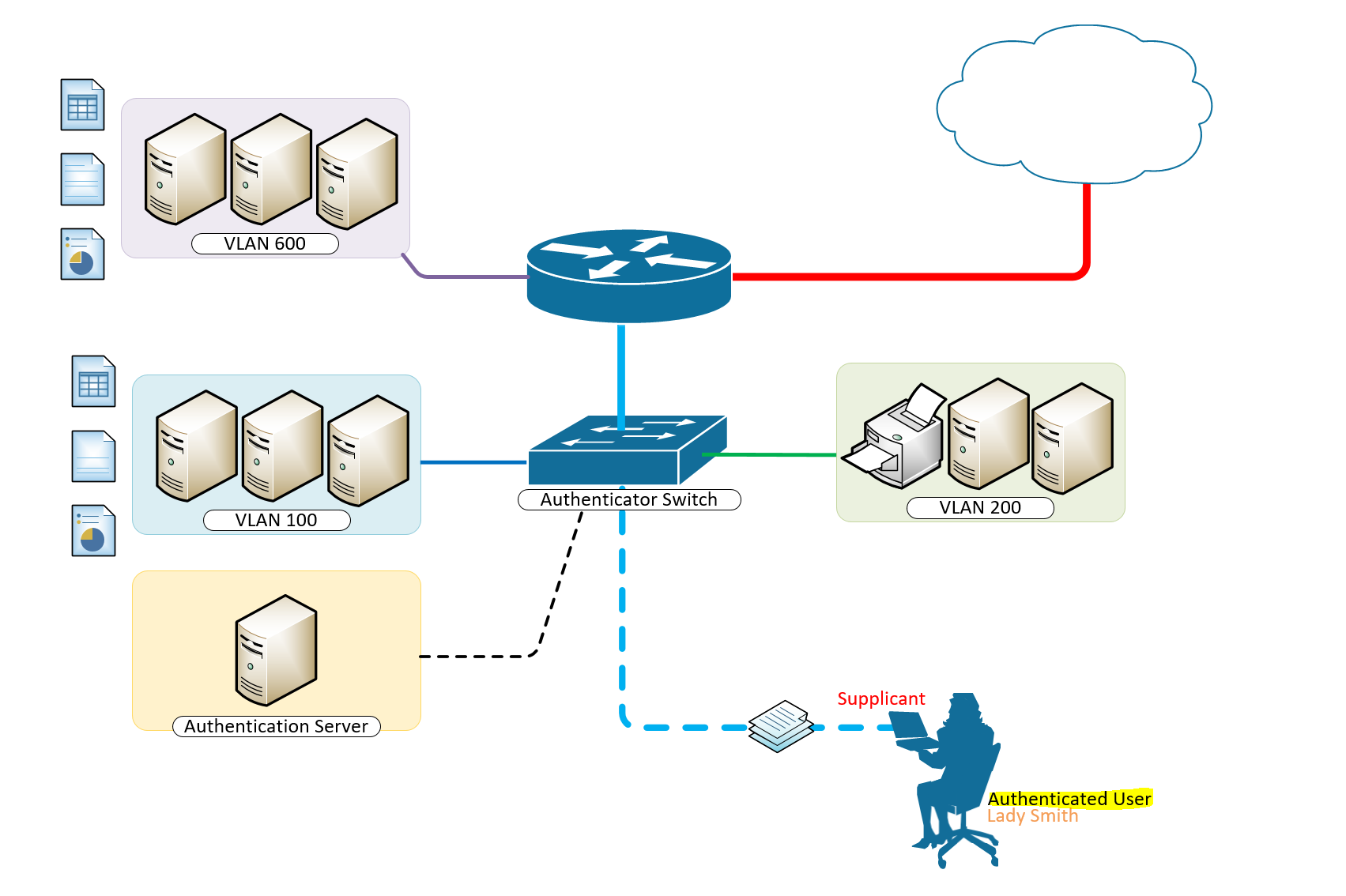
A typical configuration for a system under IEEE 802.1x Authentication control is shown in the following figure.
In this scenario, “Lady Smith” wishes to use services offered by servers on the LAN behind the switch. There are multiple VLANs with resources available based on user vlan membership. Her laptop computer is connected to a port on the Aruba 2920 Edge Switch that has 802.1x port authentication control enabled.
The laptop computer must therefore act in a supplicant role. Message exchanges take place between the supplicant and the authenticator which is the Aruba 2920 Switch, and the authenticator passes the supplicant’s credentials which is her (Windows Active Directory User Account Credentials) to the authentication server for verification. The NPS Server which is the authentication server then informs the authenticator whether or not the authentication attempt succeeded, at which point “Lady Smith” is either granted or denied access to the LAN behind the switch.
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
- Supplicant: Laptop running Microsoft Windows 10 or Windows 7
- Authenticator: HP Aruba 2920 Edge Switch
- Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2.
- User Database : Active Directory
For Windows Infrastructure
Create NPS Server – Add Role on Windows Server 2012 R2
- Create DHCP Scopes for VLANS
Create RADIUS Client on NAC using Network Policy Server
- Create Network Policies
- Configure a Network Policy for VLANs
- Start Wired Auto-Config Service
- Enable Network Authentication
Create the DHCP Scopes for VLAN100 and VLAN200 Groups
- Development Group Scope – VLAN 100
SVI: ip address 172.16.80.254 255.255.255.0 Scope Subnet: 172.16.80.1/24
- Accounting Group Scope – VLAN 200
SVI:ip address 172.16.70.254 255.255.255.0 Scope Subnet: 172.16.70.0/24
Secret Key: secret12
Add Edge Switch Management IP as the RADIUS Client
The Shared Secret Key: secret12 will be used in the Switch Configuration.
Create Network Policy Settings for Accounting Group for VLAN 200
Configuration Example
Here’s an example of how you might consider when configuring Microsoft NPS Server to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. This configuration has worked flawlessly on the HP Aruba 2920 Switch. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the Aruba 2920 Switch) by the authentication server (i.e. Microsoft NPS Server) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to.
The other elements that need to be returned by the NPS Server are as follows:
- Tunnel-PVT-Group-ID: 200
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
For Client Infrastructure
On the Supplicant, Windows 7 or 10 configure the following steps on the Ethernet Adapter to enable IEEE 802.1X Authentication
For Network Infrastructure
Connect Server Infrastructure to VLAN 400
Create VLAN for Accounting Group
Create VLAN for Development Group
Create AAA Configuration on Switch for Radius Authentication
Download the Switch Configuration:
Test the IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server
Verify Port-Access with the following user groups – VLAN 100 and VLAN 200
Think of what other clever things you can do from the information below;
Breakdown of Commands for RADIUS Authentication
Verification Commands
Thanks for reading. Please share your thoughts in the comment box below;
Published in Configuring , Design , Installing and Configuring , Networking , Security and Switching
- 802.1 x authentication step by step aruba
- 802.1 x authentication step by step cisco
- 802.1 x wireless authentication step by step
- 802.1x authentication process
- 802.1x authentication windows 10
- 802.1x authentication windows server 2012
- 802.1x certificate authentication
- assignment wlc
- cisco dot1x
- cisco ise dynamic vlan
- cisco ise dynamic vlan assignment wlc
- cisco wireless radius attributes
- configuration example
- dynamic vlan assignment cisco 2960 dynamic vlan configuration in packet tracer
- dynamic vlan assignment with windows radius server
- dynamic vlan cisco
- dynamic vlan ruckus
- meraki dynamic vlan assignment
- nps mac authentication wired
- nps policy for mac-based authentication
- radius multiple vlans
- vlan radius server
- vlan steering
- vmps server

Microsoft NPS as a RADIUS Server for WiFi Networks: Dynamic VLAN Assignment
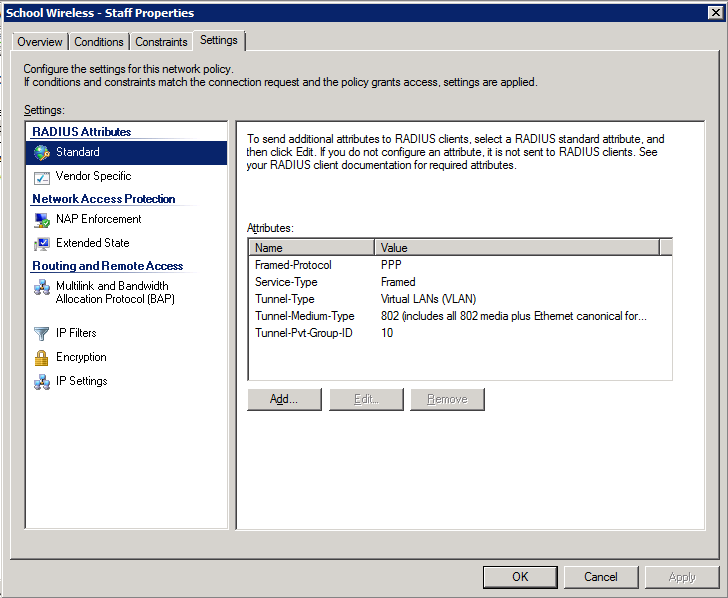
Configuration Example Here’s an example of how to configure NPS to assign users to a VLAN based on their user group, using NPS for the authentication and authorization of users. The key to getting this to work is the use of a RADIUS element called: ‘Tunnel-PVT-Group-ID’. This is a RADIUS attribute that may be passed back to the authenticator (i.e. the WLC or AP) by the authentication server (i.e.NPS) when a successful authentication has been achieved. There are a few other elements which need to accompany it, but this is the key element, as it specifies the VLAN number that the user should be assigned to. The other elements that need to be returned by NPS are:
- Service-Type: Framed
- Tunnel-Type: VLAN
- Tunnel-Medium-Type: 802
- Tunnel-PVT-Group-ID: <VLAN Number>
We’ll have a look at how we specify each of these attributes in an NPS policy. For our example, we’ll assign all ‘staff’ users to VLAN 10 and all ‘student’ users to VLAN 20. Here is an overview of what the network might look like (this is obviously very simplified, but gives an overview of the type of thing that might be achieved):
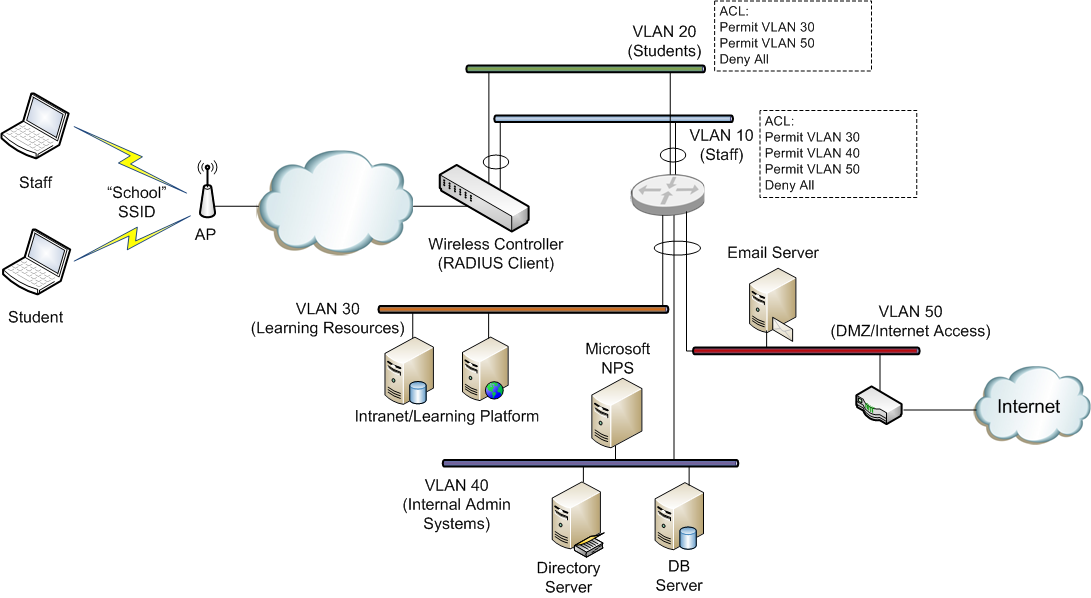
VLAN 10 has an ACL (access control list) that allows users on this VLAN to access all systems across the school network. The ACL would generally be configured on the layer 3 switch or router that interconnects the school VLANs) VLAN 20 has an ACL which only allow access to the learning system VLAN and the Internet related services. By studying the example above, you can see that if we can control a users VLAN assignment, based on their AD group membership, we can ensure that they only receive the network access to which they are entitled (purely via their AD group membership). Also, note that this is all being done on a single SSID (“School” in this case). Now we’ll take a look at how we achieve this using NPS. NPS Configuration To configure NPS to provide the VLAN assignments outlined above, we will create 2 policies within NPS:
- School Wireless – Staff (to assigned members of the staff AD group to VLAN 10)
- School Wireless – Students (to assign members of the students AD group to VLAN 20)
The screen-shots below outline the configuration required. Here is the policy summary screen within NPS. Note that when configuring multiple policies, the order of the policies is important. Policies are assessed top-down, so make sure the policies that need to be hit are enabled and above any disabled polices.
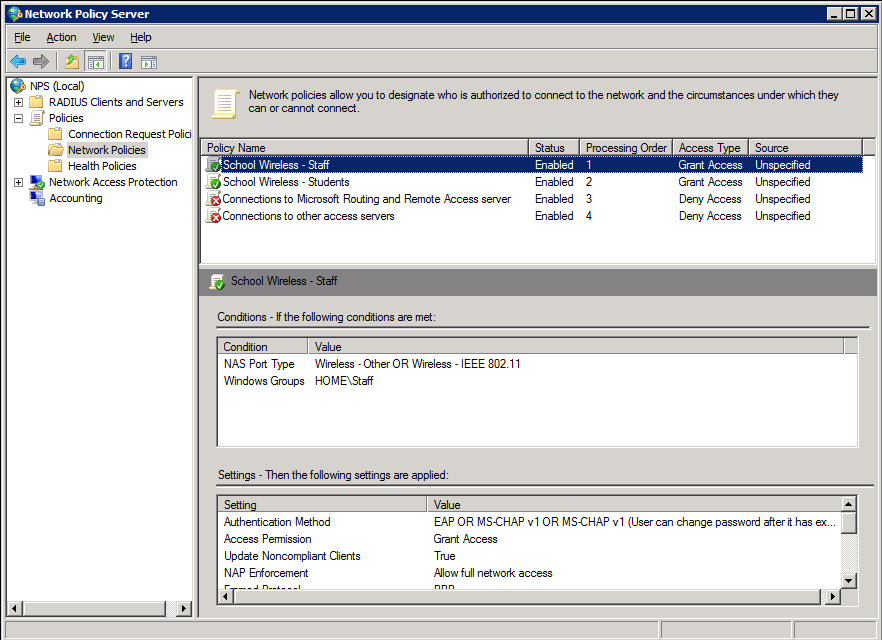
Staff Policy 1. Create the policy and enable it:
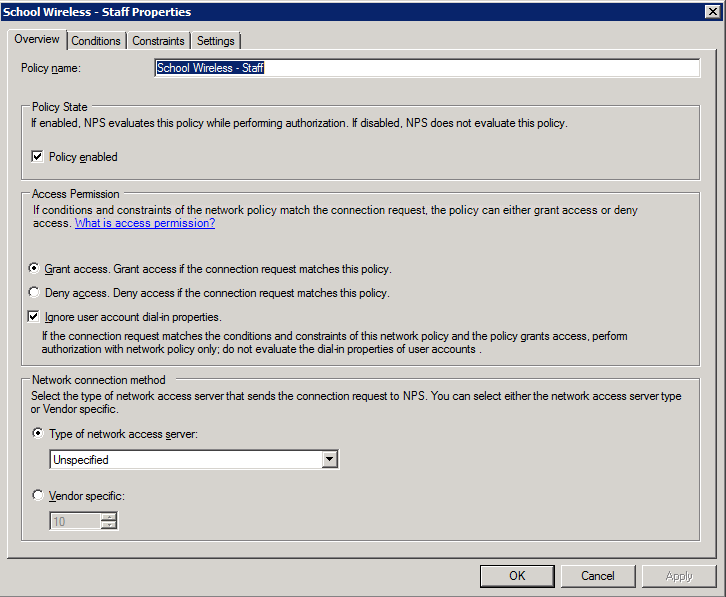
2. Add the NAS type and AD group membership conditions (must be members of the staff group):
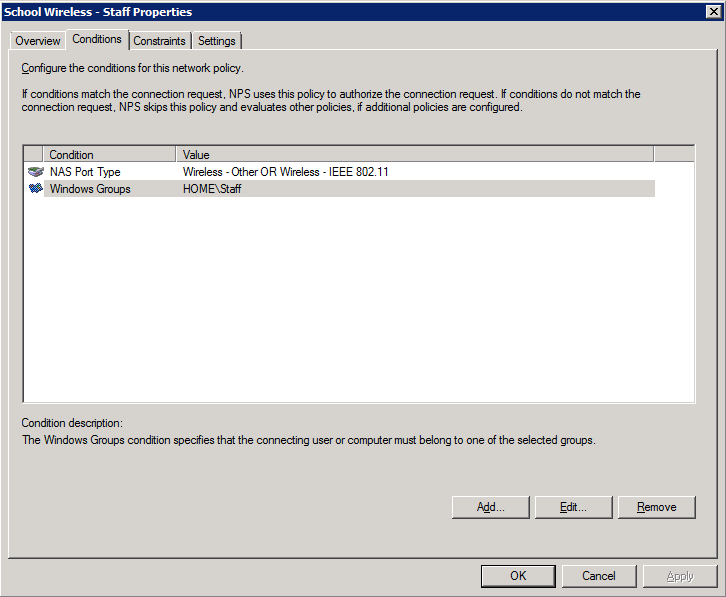
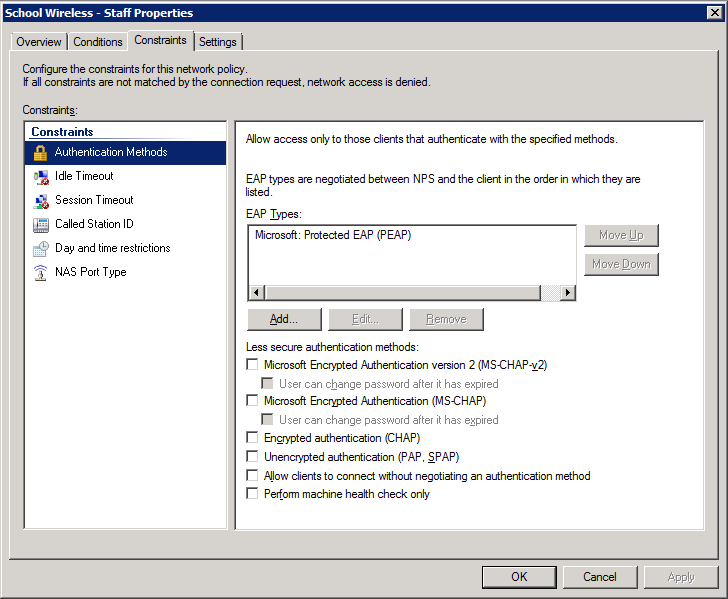
3. Select and configure an EAP type (note this may be PEAP or EAP-TLS – we’ve shown PEAP just as an example)
4. Configure the settings for this policy to assign any users which match this policy to VLAN 10:
Students Policy 1. Create the policy and enable it:
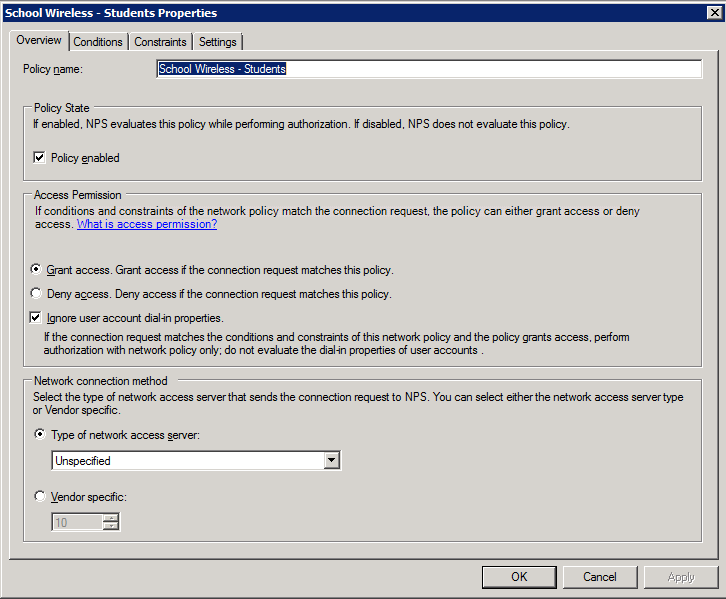
2. Add the NAS type and AD group membership conditions: (must be members of the students group to match this policy)
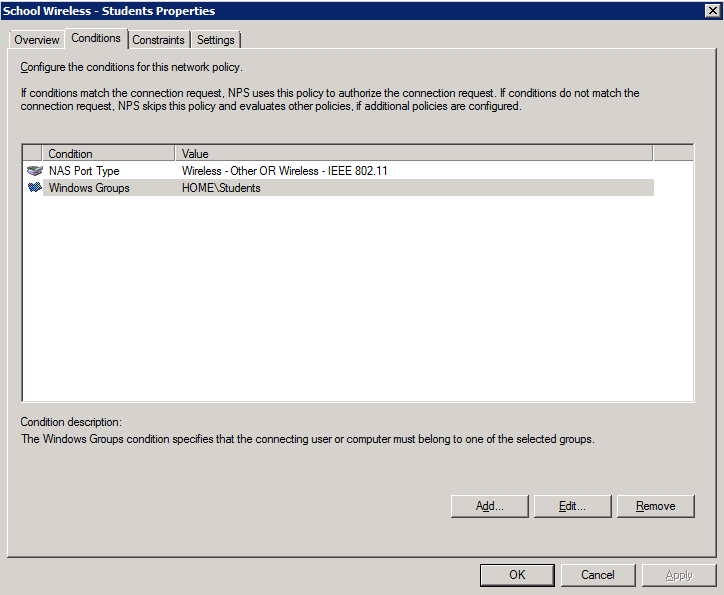
4. Configure the settings for this policy to assign any users which match this policy to VLAN 20:
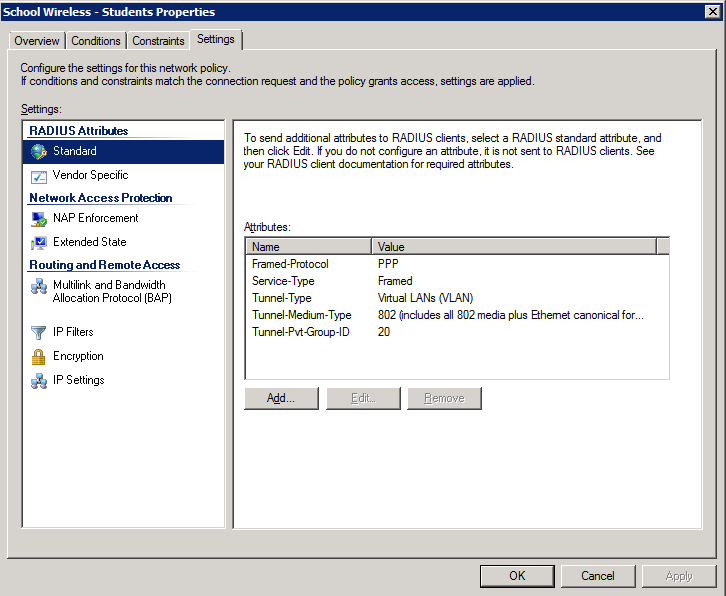
Once NPS has been configured with policies similar to those shown above, users can be dynamically assigned to an appropriate VLAN based on their AD group membership. As we’ve already discussed, this provides great benefits in reducing additional overheads associated with multiple SSIDs on a WiFi network. In addition, it simplifies user wireless management by allowing all users to be configured with a single wireless client profile, with their access being configured via Microsoft AD. One caveat to note when trying to use this technique is that all users must be using the same security mechanisms to join the SSID. For instance, all users must be using 802.1x (EAP) – you can’t have a mix of PSK & 802.1x authenticated devices on the same SSID. Generally, they should also be using the same WPA version (i.e. WPA or WPA2).
Related Articles
How to use openpath mobile pass (avigilon alta), integrate your existing network policy server (nps) infrastructure with azure ad multi-factor authentication, how to find out who the user profile disk belongs to terminal server rds, how to sign up and use chatgpt, sage 50 payroll – change database path, generate a report of all passwords for all cameras on your milestone xprotect vms., leave a reply cancel reply.
Your email address will not be published. Required fields are marked *
Save my name, email, and website in this browser for the next time I comment.
Power by IT Capture
Network Guys
Share your knowledge!

How to use 802.1x/mac-auth and dynamic VLAN assignment
Hello guys! Today I want to show you how to secure your edge-switches with 802.1x and mac-authentication fallback in combination with HPE comware-based switches. The 802.1x protocol is used for network access control. For devices like printers, cameras, etc. we will use mac-authentication as a fallback. We will also use dynamic VLAN assignment for the connected ports.
Our radius server will be Microsoft NPS. You can activate this role on the Windows server:
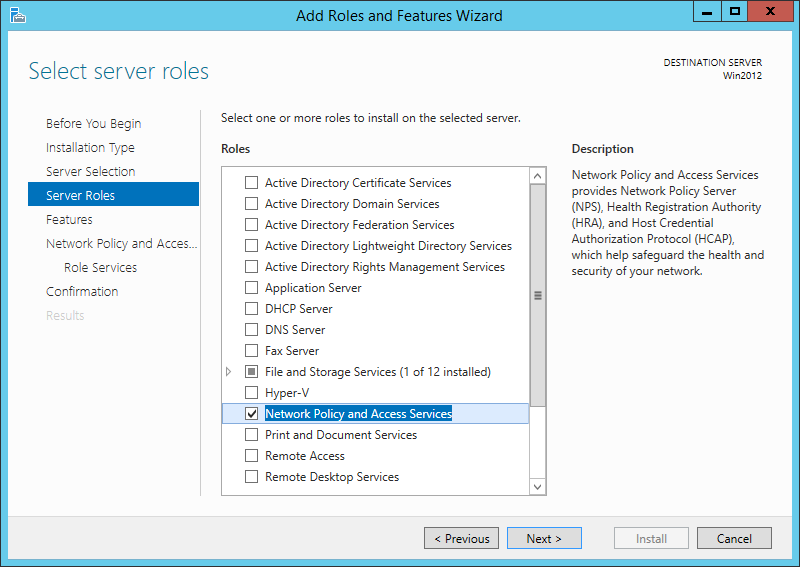
After the installation, open the NPS console and register the radius server in your Active Directory:
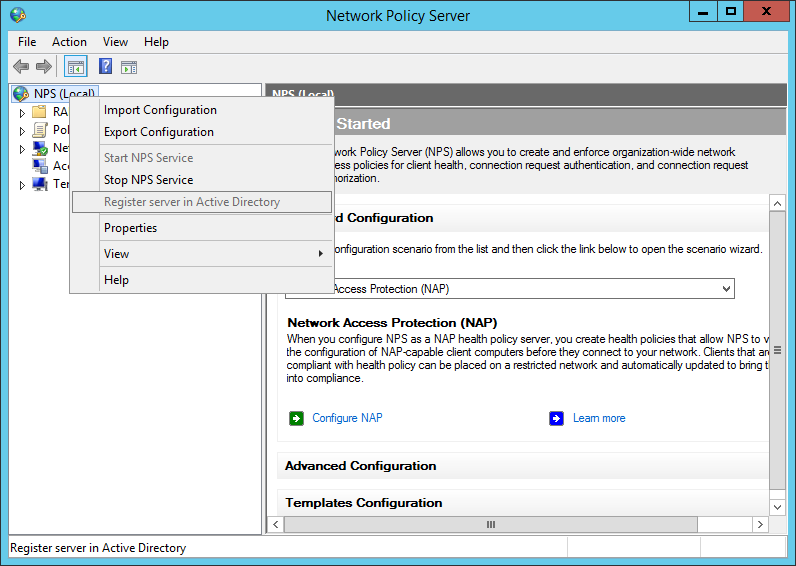
add your switches or your management network as a radius-client:
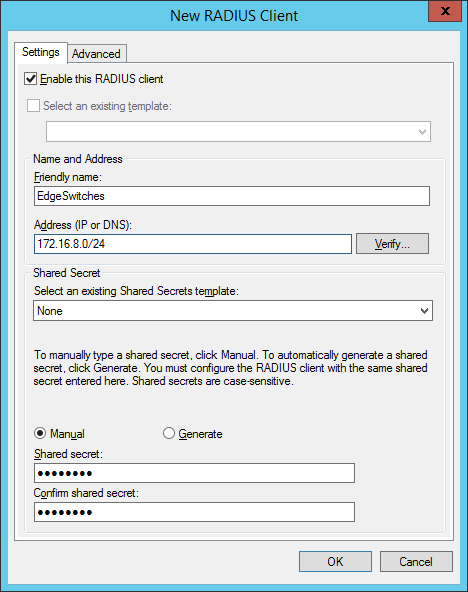
the shared secret will be used in the switch configuration. In created two groups within my test environment:
- “ VLAN2-802.1x ” containing computer accounts
- “ VLAN3-MAC-Auth ” containing user accounts (username+password = mac-address of the device)
So we will now configure two network policies for our network access control:
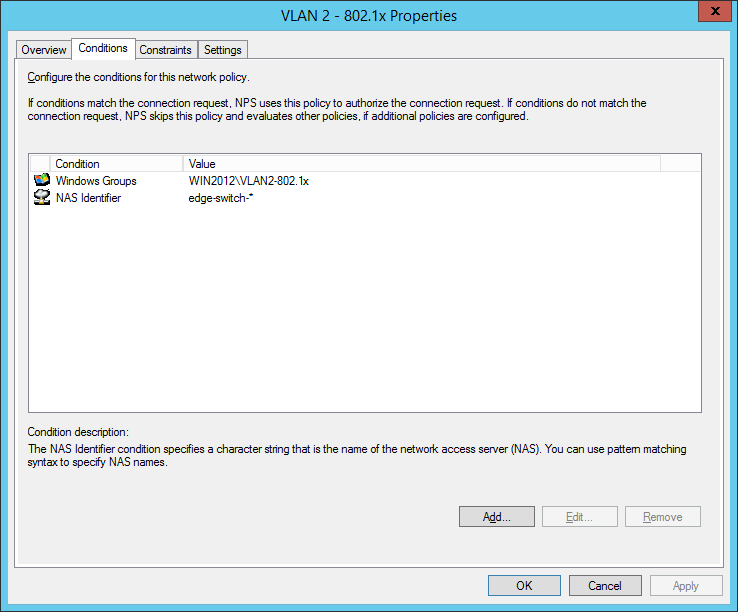
I also configured a NAS Identifier so no other device can use the radius server. The clients will use their computer certificate so you will need a running internal certification authority. Choose PEAP only as the authentication method:
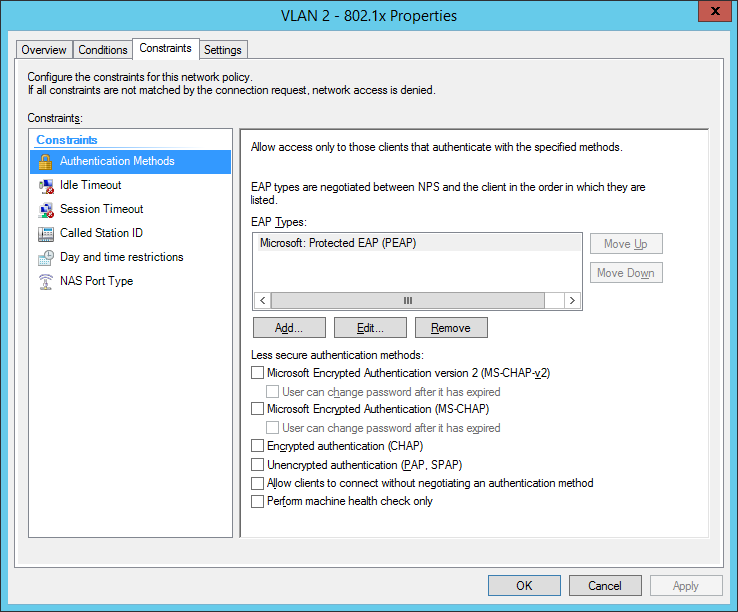
the next step is for our dynamic VLAN assignment. Dot1x devices are bound to VLAN 2:
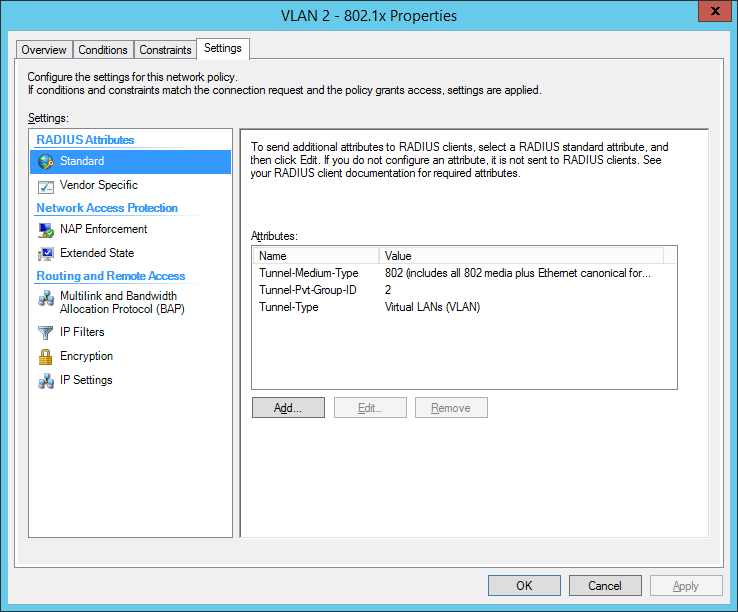
the final dot1x configuration in the NPS:
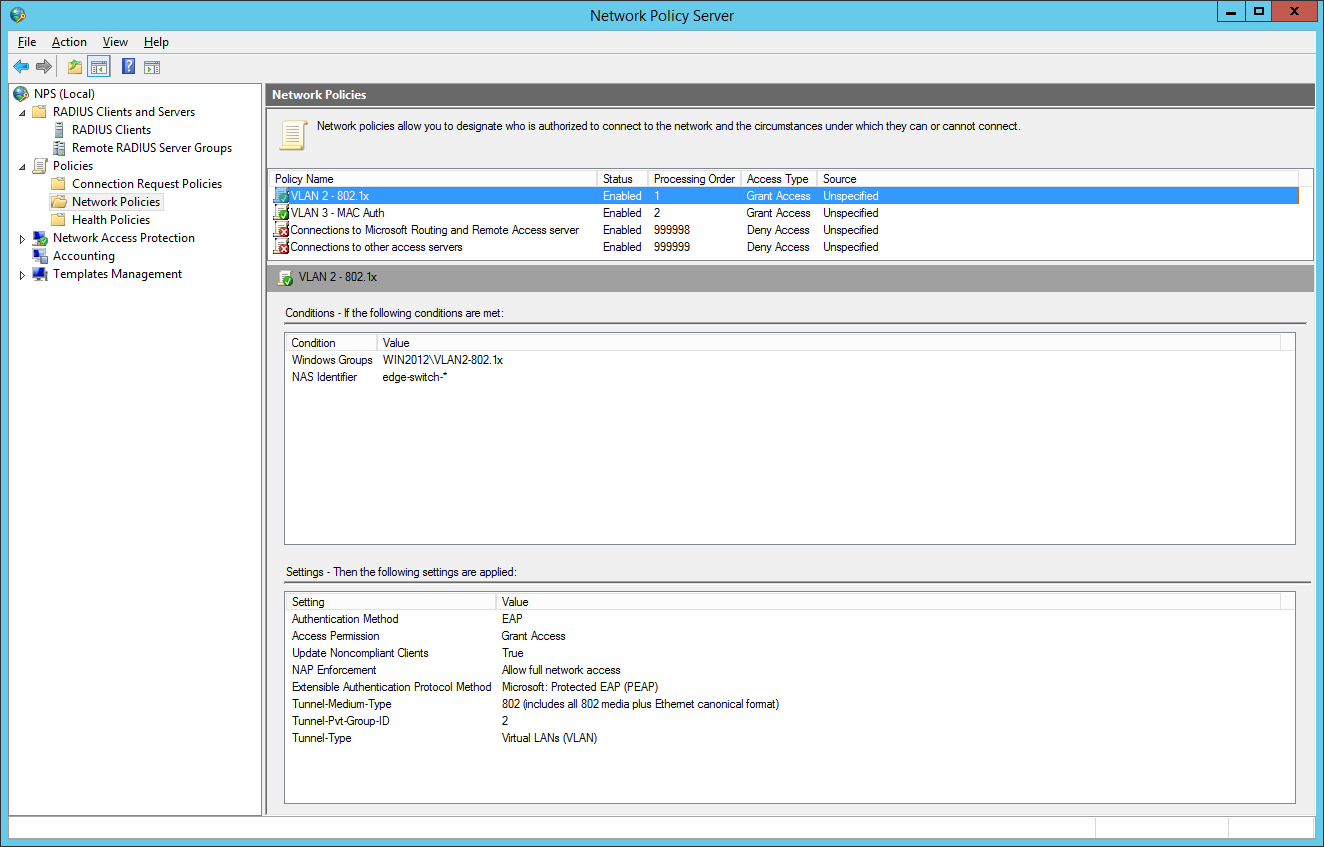
the second network policy is for the mac-based authentication:
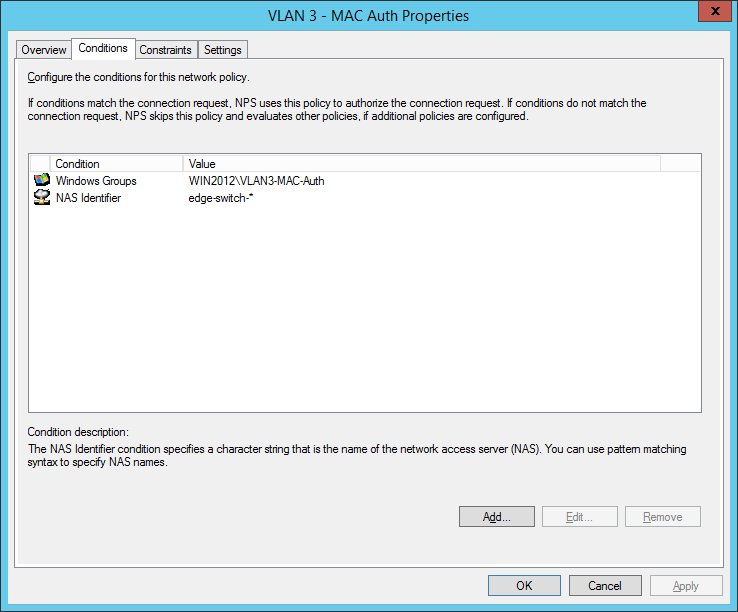
Comware switches are sending MAC-Auth-requests via PAP (maybe you know how to change it to CHAP):
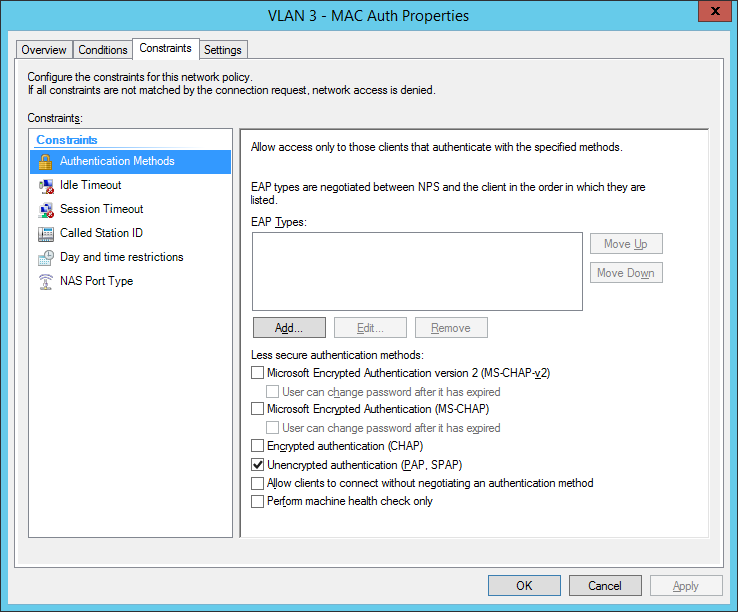
final MAC auth profile:
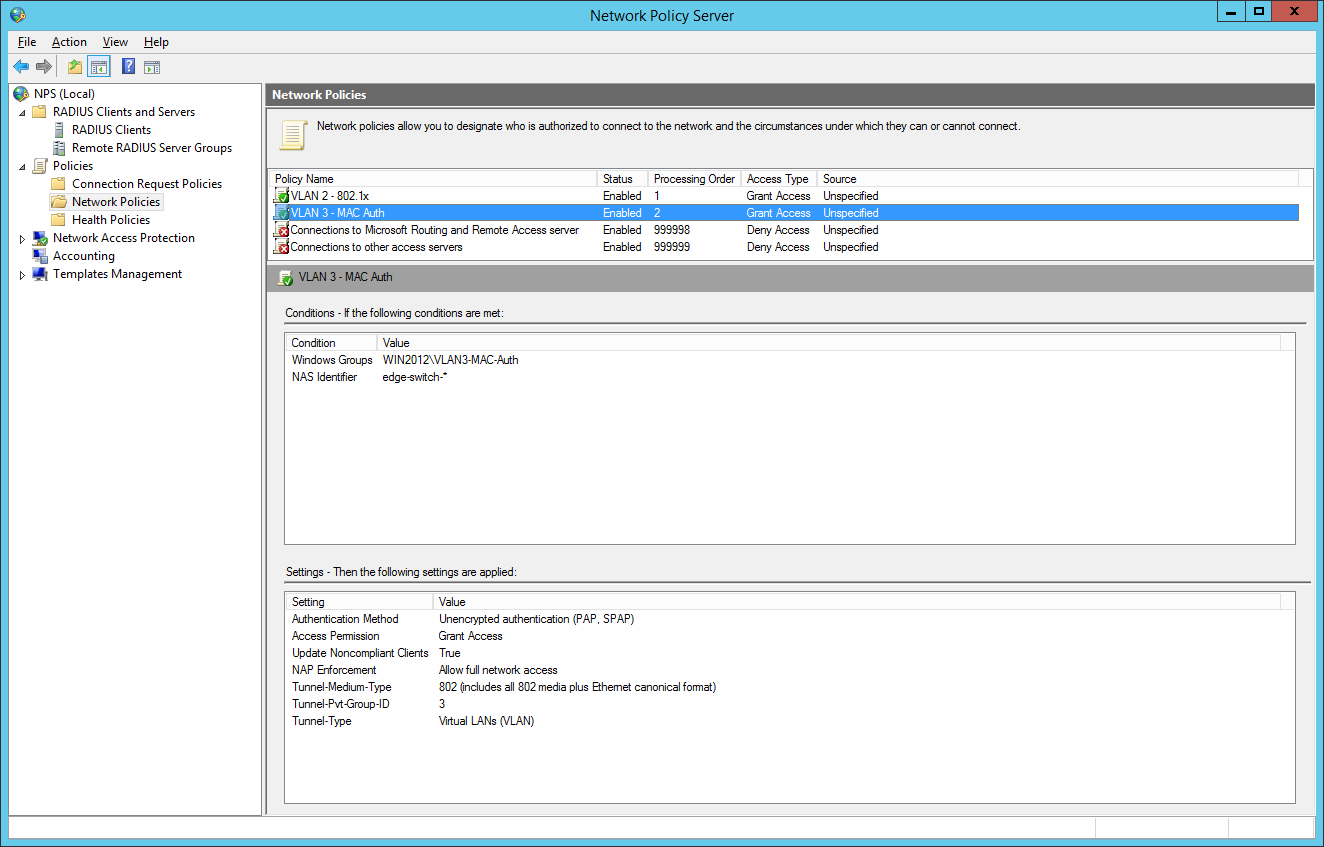
for now we have built up our authentication server. Now let’s go to the switch configuration. You have global configuration parameters and parameters for each interface. The best way is to use interface-range command to be safe at your configuration. Users who cant authenticate, will be forced to VLAN 999 (quarantine VLAN with no gateway). Here are the global parameters with explanations inline:
now we will configure the interfaces: Added 2 entries
the last part is to configure all windows clients to send 802.1x auth data to the cable network. I’ve done this via a global group policy. You can find the settings under Computer Configuration / Policies / Windows Settings / Security Settings / Wired Network (IEEE 802.3) Policies:
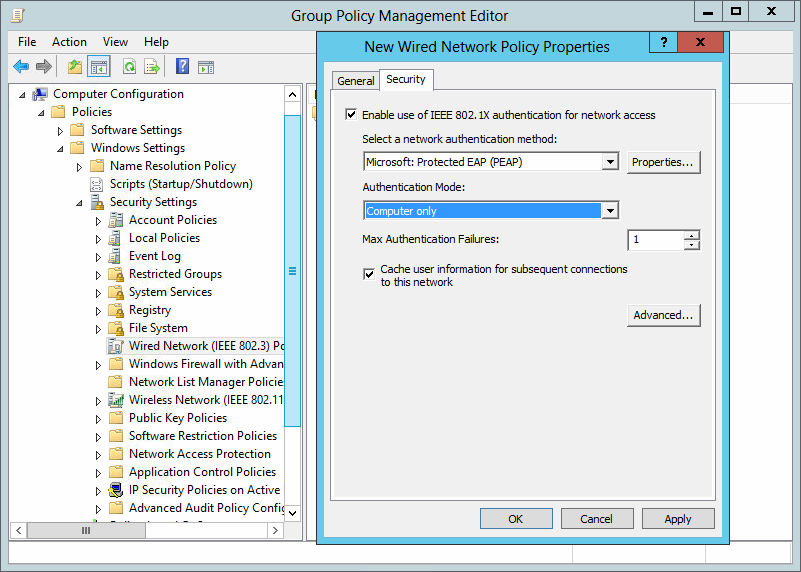
So how does a working 802.1x-auth looks like?
%Jan 3 01:59:59:531 2013 edge-switch-01 DOT1X/6/DOT1X_LOGIN_SUCC: -IfName=GigabitEthernet1/0/10-MACAddr=0023-2415-42a3-AccessVLANID=1- AuthorizationVLANID=2 -Username= host/PC123.mycompany.local ; User passed 802.1X authentication and came online.
Successful Mac-Authentication of a printer:
%Jan 3 01:31:28:782 2013 de-pad-l19-edg01 MACA/6/MACA_LOGIN_SUCC: -IfName=GigabitEthernet1/0/9-MACAddr=0017-c82d-e9bf-AccessVLANID=1- AuthorizationVLANID=3 -Username= 0017c82de9bf -UsernameFormat=MAC address; User passed MAC authentication and came online.
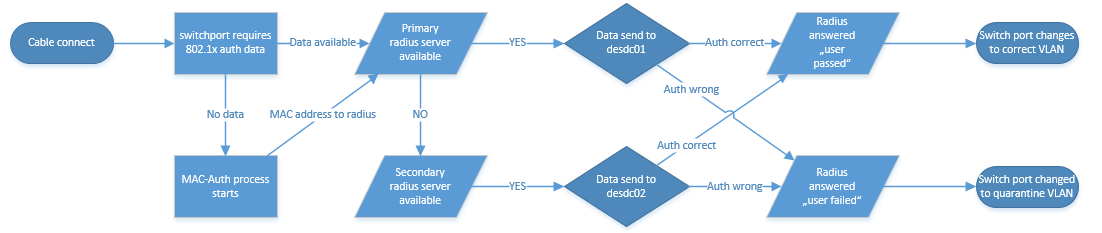
I tried to draw a flow chart which shows the authentication process, I hope it’s ok for you :)
Do you have questions? Feel free to write them into the comments and I will try to answer.
Have a nice and sunny day!
/edit: If you can’t see success and failure events, follow this instruction: NPS / Radius Server is not logging
/edit 2018-05-14: I corrected the global and interface configuration, we had problems with the old configuration
12 Responses
Thanks for this, I need to setup dynamic VLAN assignment in the near future but for Juniper equipment.
This at least gives me a good starting point, thanks for the write up.
Many thanks for the perfect tutorial on How to use 802.1x/Mac-Auth and dynamic VLAN assignment. Many of us can take help from it. Really nice.
Nice write-up. This was a great starting point for configuring the base for dynamic polices. Thanks!
hi Mike, how ‘s about hybrid port with voice-vlan? does it work?
thanks Tung Duong
we had several problems with this config, currently we are investigating hyprid ports with “port security” command. I will update this post if we have prooved this version.
Can you tell me why I would do this over conventional static VLANs? What are the benefits radius dynamic VLANs?
we have customers which want to divide the network for clients, printers and “special devices”. So you have different group/radius-policies to directly place the devices in the right VLAN. Dynamic VLAN is only a bonus feature which you can use. Of course, you can use only the 802.1x and Mac authentication for security purpose.
I’m on the desktop side of things, so apologies if I use any incorrect terminology here.
Our Infrastructure team are looking at introducing 8021x in our schools. They have a test setup where all 8021x devices pick up a data centre VLAN regardless of which building they’re in – eg 10.100.50.
Each building WIRED has its own unique IP – SchoolA=10.120, SchoolB = 10.130 and so on.
I’ve asked if the 8021x setup can be where 8021x devices in SchoolA will get 10.120.50; SchoolB will get 10.130.50
This would allow us to easily determine which building LaptopA actually is, in the same way as we can with our wired desktops. It also saves on SCCM boundary issues causing applications/updates to be pulled over the WAN rather than the LAN.
It’s been suggested that this may not be possible. Could someone confirm this?
Thanks in advance.
Hello! This is of course possible!
My idea (with examples):
SchoolA=10.120 (Location: Chicago) SchoolB=10.130 (Location: Dallas)
So at Chicago you will have VLAN 333, every device is getting an IP address with 10.120.x.x. At Dallas every device in VLAN 333 is getting an IP address with 10.130.x.x. So the VLAN ID “333” is the same at every school but the DHCP scope and default gateway has it’s own address. So the device is getting the VLAN 333 at every location but another IP address. It’s very simple.
It’s not working if all schools are connected via Layer2 so VLAN333 can’t be a “standalone VLAN” at each geographical location.
Ask me any questions, I will try to help you.
- Pingback: 802.1x, MAC-Authentication and VLAN assignment at ProCurve/aruba Switches – Network Guy
- Pingback: Port Auth, Dynamic VLAN and Radius | samuelnotes
- Pingback: HPE Comware problem with mac authentication and printer - Network Guy
Leave a Reply Cancel reply
Click on the button to load the content from jetpack.wordpress.com.
Load content
This site uses Akismet to reduce spam. Learn how your comment data is processed .
Certificates

Post Categories
Post archives, recent posts.
- Sophos UTM 9.712-13 HA update problem 14. November 2022
- Sophos UTM 9.712-12 update released 24. August 2022
- Aruba OS Switch automatic vlan assignment for aruba APs 5. May 2022
- Sophos UTM 9.711-5 update released 22. April 2022
- Sophos UTM 9.710-1 update released 20. March 2022
Recent Comments
- Sophos Ssl Vpn Client Anmeldung - Login and Portal on Auto-Logon with Sophos SSL VPN Client (OpenVPN)
- Russell on Install Sophos UTM from USB Stick
- arno on Problems with incoming mails
- GigaTech IT on Installing Realtek Driver on ESXi 6.7
- Sophos User Portal Login Ssl Vpn - Online Login on Auto-Logon with Sophos SSL VPN Client (OpenVPN)
Franky’s Web Website from my friend Frank. News and Tricks about Microsoft products, primarly Exchange Server
Copyright by networkguy.de
Imprint · Privacy Policy

IMAGES
VIDEO
COMMENTS
Setup Structure for IEEE 802.1X Authentication and Dynamic VLAN Assignment with NPS Radius Server. Supplicant: Laptop running Microsoft Windows 10 or Windows 7; Authenticator: HP Aruba 2920 Edge Switch; Authentication Server: Microsoft NPS (Network Policy Server) running on Windows Server 2012 R2. User Database : Active Directory; For Windows ...
Hi guys I'm pretty new to posting on forums, so be kind please 🙂 I have AD and Microsoft NPS 2016 configured (correctly i think) as authentication is successful (i.e. the Cisco shows a successful auth and the Windows 10 machine is waiting for a DHCP address). However, what isnt getting to the switch (Cisco 2960S) is the VLAN ID. I have configured the "Tunnel-Pvt-Group-ID" attribute ...
Configure a RADIUS Server and WLC for Dynamic VLAN Assignment - Cisco. Also, if I understand correctly, now you are evaluating products for deploying MSI. In this case, take a look at our cloud-based solution Action1 for deploying different types of software (msi and exe) on all computers on your network at the same time. Thanks for the info.
Learn how to assign VLANs dynamically with RADIUS to Unleashed access points.For more information on this topic and many others, check out the Ruckus Support...
This procedure explains how to configure the users in the RADIUS server and the RADIUS (IETF) attributes used to assign VLAN IDs to these users. Complete these steps: From the ACS GUI, click User Setup. In the User Setup window, enter a username in the User field and click Add/Edit.
2. Add the NAS type and AD group membership conditions: (must be members of the students group to match this policy) 3. Select and configure an EAP type (note this may be PEAP or EAP-TLS - we've shown PEAP just as an example) 4. Configure the settings for this policy to assign any users which match this policy to VLAN 20: Once NPS has been ...
6. Our current 802.11 setup has a large number of SSIDs to segregate traffic by subnet. This isn't ideal, and I've been attempting to consolidate to a single SSID but use dynamic VLANs instead. This is on a Ruckus Zonedirector 3000 and Microsoft NPS as the RADIUS server. My test clients connect to the SSID, and are prompted for credentials.
dynamic VLAN assignment working with NPS and Cisco for a wired network. I have AD and Microsoft NPS 2016 configured (correctly i think) as authentication is successful (i.e. the Cisco shows a successful auth and the Windows 10 machine is waiting for a DHCP address). However, what isnt getting to the switch (Cisco 2960S) is the VLAN ID.
Wireless (Ruckus) and Dynamic VLAN Assignment via Microsoft NPS. 5. Configure Cisco Aironet 1600 AP with RADIUS and multiple VLANs. 4. EAP packets generated for plain MAC-based authentication. 3. VLAN tagging, routing, and general pain. 7. Why is routing not working on my Dell N2048 switch. 2.
Respective Groups are added to ISE and can be saved. Press Save. Add WLC to the ISE Network device list - navigate to Administration > Network Resources > Network Devices and press Add. Complete configuration, by providing WLC management IP address and RADIUS shared secret between WLC and ISE.
Complete these steps: From the ISE GUI, navigate to Administration > Identity Management > Identities and select Add. Complete the configuration with the username, password, and user group as shown in the image: Step 3. Configure the RADIUS (IETF) attributes used for dynamic VLAN Assignment.
I'm wanting to setup MAB w/ dynamic VLANs on some 2960s using a Microsoft NPS server. So far, I've gotten MAB working, but not the dynamic VLAN portion. I'd set this up on some NX-OS switches before, and believe I've got the same configuration now, but it's not working. dot1x system -auth-control aaa authentication dot1x default group radius ...
Configuring Dynamic Access Ports on a VMPS Client. To configure a dynamic access port on a VMPS client switch, perform this task: Enters global configuration mode. Enters interface configuration mode and specifies the port to be configured. Sets the port to access mode. Configures the port as eligible for dynamic VLAN access.
The 802.1x protocol is used for network access control. For devices like printers, cameras, etc. we will use mac-authentication as a fallback. We will also use dynamic VLAN assignment for the connected ports. Our radius server will be Microsoft NPS. You can activate this role on the Windows server:
Bias-Free Language. The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality.
Dynamic VLAN Membership Overview. When a port is configured as "dynamic," it receives VLAN information based on the MAC-address that is on the port. The VLAN is not statically assigned to the port; it is dynamically acquired from the VMPS based on the MAC-address on the port. A dynamic port can belong to one VLAN only.