- Trending Now
- Foundational Courses
- Data Science
- Practice Problem
- Machine Learning
- System Design
- DevOps Tutorial
- Top 10 Cloud Computing Research Topics in 2020
- Top 10 Cloud Computing Trends [2024]
- An Insight to Cloud Computing
- Top 10 Job Opportunities in Cloud Computing
- 10 Best Cloud Computing Project Ideas
- Orchestration in Cloud Computing
- Cloud computing Research challenges
- Issues in Cloud Computing
- Economics of Cloud Computing
- History of Cloud Computing
- Cloud Computing Infrastructure
- Top 5 Cloud Computing Companies to Work For in 2024
- Security Issues in Cloud Computing
- Cloud Computing Services in Financial Market
- Top Cloud Computing Platforms for Machine Learning
- Cloud Computing Interview Questions
- How to Make a Career in Cloud Computing?
- Energy Efficiency in Cloud Computing
- Principles of Cloud Computing
- Cloud Computing Platforms and Technologies

Top 15 Cloud Computing Research Topics in 2024
Cloud computing has suddenly seen a spike in employment opportunities around the globe with tech giants like Amazon , Google , and Microsoft hiring people for their cloud infrastructure . Before the onset of cloud computing , companies and businesses had to set up their own data centers , and allocate resources and other IT professionals thereby increasing the cost. The rapid development of the cloud has led to more flexibility , cost-cutting , and scalability .

The Cloud Computing market is at an all-time high with the current market size at USD 371.4 billion and is expected to grow up to USD 832.1 billion by 2025 ! It’s quickly evolving and gradually realizing its business value along with attracting more and more researchers , scholars , computer scientists , and practitioners. Cloud computing is not a single topic but a composition of various techniques which together constitute the cloud . Below are 10 of the most demanded research topics in the field of cloud computing .
What is Cloud Computing?
Cloud computing is the practice of storing and accessing data and applications on remote servers hosted over the internet, as opposed to local servers or the computer’s hard drive. Cloud computing, often known as Internet-based computing, is a technique in which the user receives a resource as a service via the Internet. Files, photos, documents, and other storable documents can all be considered types of data that are stored.
Let us look at the latest in cloud computing research for 2024! We’ve compiled 15 important cloud computing research topics that are changing how cloud computing is used.
1. Big Data
Big data refers to the large amounts of data produced by various programs in a very short duration of time. It is quite cumbersome to store such huge and voluminous amounts of data in company-run data centers . Also, gaining insights from this data becomes a tedious task and takes a lot of time to run and provide results, therefore cloud is the best option. All the data can be pushed onto the cloud without the need for physical storage devices that are to be managed and secured. Also, some popular public clouds provide comprehensive big data platforms to turn data into actionable insights.
DevOps is an amalgamation of two terms, Development and Operations . It has led to Continuous Delivery , Integration, and Deployment therefore reducing boundaries between the development team and the operations team . Heavy applications and software need elaborate and complex tech stacks that demand extensive labor to develop and configure which can easily be eliminated by cloud computing . It offers a wide range of tools and technologies to build , test , and deploy applications within a few minutes and a single click. They can be customized as per the client’s requirements and can be discarded when not in use hence making the process seamless and cost-efficient for development teams .
3. Cloud Cryptography
Data in the cloud needs to be protected and secured from foreign attacks and breaches . To accomplish this, cryptography in the cloud is a widely used technique to secure data present in the cloud . It allows users and clients to easily and reliably access the shared cloud services since all the data is secured using either encryption techniques or by using the concept of the private key . It can make the plain text unreadable and limit the view of the data being transferred. Best cloud cryptographic security techniques are the ones that do not compromise the speed of data transfer and provide security without delaying the exchange of sensitive data.
4. Cloud Load Balancing
It refers to splitting and distributing the incoming load to the server from various sources. It permits companies and organizations to govern and supervise workload demands or application demands by redistributing, reallocating, and administering resources between different computers, networks, or servers. Cloud load balancing encompasses holding the circulation of traffic and demands that exist over the Internet. This reduces the problem of sudden outages, results in an improvement in overall performance, has rare chances of server crashes and also provides an advanced level of security. Cloud-based server farms can accomplish more precise scalability and accessibility using the server load balancing mechanism . Due to this, the workload demands can be easily distributed and controlled.
5. Mobile Cloud Computing
It is a mixture of cloud computing , mobile computing , and wireless network to provide services such as seamless and abundant computational resources to mobile users, network operators, and cloud computing professionals. The handheld device is the console and all the processing and data storage takes place outside the physical mobile device. Some advantages of using mobile cloud computing are that there is no need for costly hardware, battery life is longer, extended data storage capacity and processing power, improved synchronization of data, and high availability due to “store in one place, accessible from anywhere”. The integration and security aspects are taken care of by the backend that enables support to an abundance of access methods.
6. Green Cloud Computing
The major challenge in the cloud is the utilization of energy-efficient and hence develop economically friendly cloud computing solutions. Data centers that include servers , cables , air conditioners , networks , etc. in large numbers consume a lot of power and release enormous quantities of Carbon Dioxide in the atmosphere. Green Cloud Computing focuses on making virtual data centers and servers to be more environmentally friendly and energy-efficient. Cloud resources often consume so much power and energy leading to a shortage of energy and affecting the global climate. Green cloud computing provides solutions to make such resources more energy efficient and to reduce operational costs. This pivots on power management , virtualization of servers and data centers, recycling vast e-waste , and environmental sustainability .
7. Edge Computing
It is the advancement and a much more efficient form of Cloud computing with the idea that the data is processed nearer to the source. Edge Computing states that all of the computation will be carried out at the edge of the network itself rather than on a centrally managed platform or data warehouse. Edge computing distributes various data processing techniques and mechanisms across different positions. This makes the data deliverable to the nearest node and the processing at the edge . This also increases the security of the data since it is closer to the source and eliminates late response time and latency without affecting productivity
8. Containerization
Containerization in cloud computing is a procedure to obtain operating system virtualization . The user can work with a program and its dependencies utilizing remote resource procedures . The container in cloud computing is used to construct blocks, which aid in producing operational effectiveness , version control , developer productivity , and environmental stability . The infrastructure is upgraded since it provides additional control over the granular activities of the resources. The usage of containers in online services assists storage with cloud computing data security, elasticity, and availability. Containers provide certain advantages such as a steady runtime environment , the ability to run virtually anywhere, and the low overhead compared to virtual machines .
9. Cloud Deployment Model
There are four main cloud deployment models namely public cloud , private cloud , hybrid cloud , and community cloud . Each deployment model is defined as per the location of the infrastructure. The public cloud allows systems and services to be easily accessible to the general public . The public cloud could also be less reliable since it is open to everyone e.g. Email. A private cloud allows systems and services to be accessible inside an organization with no access to outsiders. It offers better security due to its access restrictions. A hybrid cloud is a mixture of private and public clouds with critical activities being performed using the private cloud and non-critical activities being performed using the public cloud. Community cloud allows systems and services to be accessible by a group of organizations.
10. Cloud Security
Since the number of companies and organizations using cloud computing is increasing at a rapid rate, the security of the cloud is a major concern. Cloud computing security detects and addresses every physical and logical security issue that comes across all the varied service models of code, platform, and infrastructure. It collectively addresses these services, however, these services are delivered in units, that is, the public, private, or hybrid delivery model. Security in the cloud protects the data from any leakage or outflow, theft, calamity, and removal. With the help of tokenization, Virtual Private Networks , and firewalls , data can be secured.
11. Serverless Computing
Serverless computing is a way of running computer programs without having to manage the underlying infrastructure. Instead of worrying about servers, networking, and scaling, you can focus solely on writing code to solve your problem. In serverless computing, you write small pieces of code called functions. These functions are designed to do specific tasks, like processing data, handling user requests, or performing calculations. When something triggers your function, like a user making a request to your website or a timer reaching a certain time, the cloud provider automatically runs your function for you. You don’t have to worry about setting up servers or managing resources.
12. Cloud-Native Applications
Modern applications built for the cloud , also known as cloud-native applications , are made so to take full advantage of cloud computing environments . Instead of bulky programs like monolithic systems , they’re built to prioritize flexibility , easy scaling , reliability , and constant updates . This modular approach allows them to adapt to changing needs by growing or shrinking on demand, making them perfect for the ever-shifting world of cloud environments. Deployed in various cloud environments like public, private, or hybrid clouds, they’re optimized to make the most of cloud-native technologies and methodologies . Instead of one big chunk, they’re made up of lots of smaller pieces called microservices .
13. Multi-Cloud Management
Multi-cloud management means handling and controlling your stuff (like software, data, and services) when they’re spread out across different cloud companies, like Amazon, Google, or Microsoft. It’s like having a central command center for your cloud resources spread out across different cloud services. Multi-cloud gives you the freedom to use the strengths of different cloud providers. You can choose the best service for each specific workload, based on factors like cost, performance, or features. This flexibility allows you to easily scale your applications up or down as required by you. Managing a complex environment with resources spread across multiple cloud providers can be a challenge. Multi-cloud management tools simplify this process by providing a unified view and standardized management interface.
14. Blockchain in Cloud Computing
Cloud computing provides flexible storage and processing power that can grow or shrink as needed. Blockchain keeps data secure by spreading it across many computers. When we use them together, blockchain apps can use the cloud’s power for big tasks while keeping data safe and transparent. This combo boosts cloud data security and makes it easy to track data. It also lets people manage their identities without a central authority. However, there are challenges like making sure different blockchain and cloud systems work well together and can handle large amounts of data.
15. Cloud-Based Internet of Things (IoT)
Cloud-based Internet of Things (IoT) refers to the integration of cloud computing with IoT devices and systems. This integration allows IoT devices to leverage the computational power, storage, and analytics capabilities of cloud platforms to manage, process, and analyze the vast amounts of data they generate. The cloud serves as a central hub for connecting and managing multiple IoT devices, regardless of their geographical location. This connectivity is crucial for monitoring and controlling devices remotely.
Also Read Cloud computing Research challenges 7 Privacy Challenges in Cloud Computing Difference Between Cloud Computing and Fog Computing
Cloud computing has helped businesses grow by offering greater scalability , flexibility , and saving money by charging less money for the same job. As cloud computing is having a great growth period right now, it has created lots of employment opportunities and research work is done is different areas which is changing the future of this technology. We have discussed about the top 15 cloud computing research topics . You can try to explore and research in these areas to contribute to the growth of cloud computing technology .

Please Login to comment...
Similar reads.
- Cloud-Computing
Improve your Coding Skills with Practice
What kind of Experience do you want to share?
- Cloud Computing Tutorials
12 Latest Cloud Computing Research Topics
Free AWS Course for AWS Certified Cloud Practitioner (CLF-C01) Start Now!!
Cloud Computing is gaining so much popularity an demand in the market. It is getting implemented in many organizations very fast.
One of the major barriers for the cloud is real and perceived lack of security. There are many Cloud Computing Research Topics , which can be further taken to get the fruitful output.
In this tutorial, we are going to discuss 12 latest Cloud Computing Research Topics. These Cloud computing topics will help in your researches, projects and assignments.
So, let’s start the Cloud Computing Research Topics.
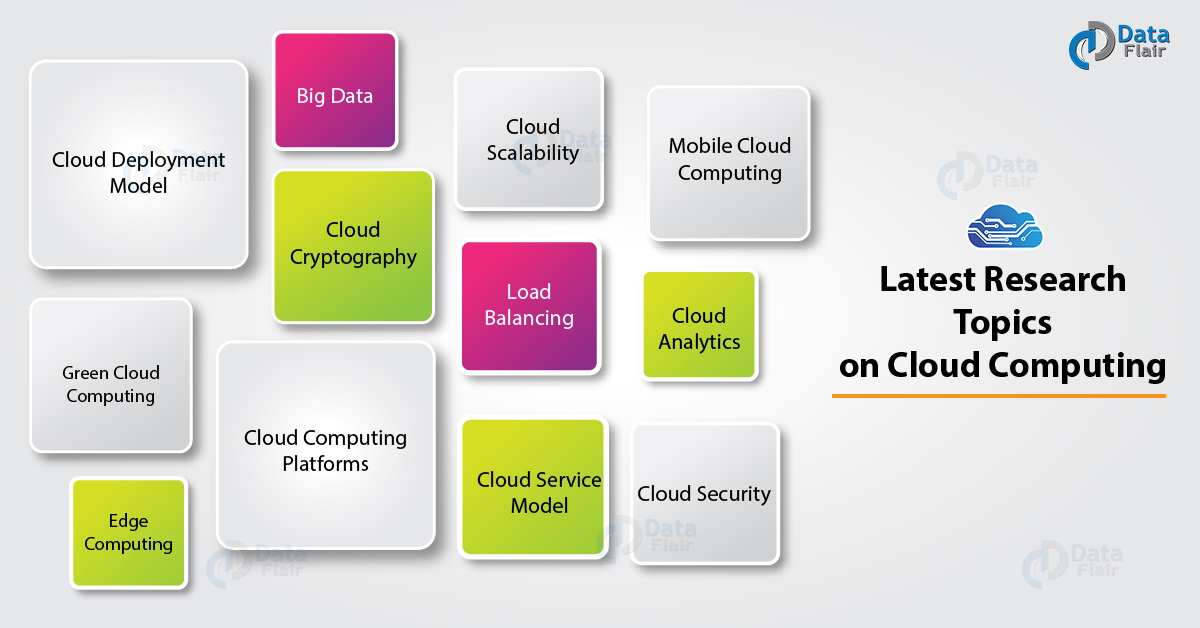
List of Cloud Computing Research Topics
These Cloud Computing researches topics, help you to can eliminate many issues and provide a better environment. We can assoicate these issues with:
- Virtualizations infrastructure
- Software platform
- Identity management
- Access control
There is some important research direction in Cloud Security in areas such as trusted computing, privacy-preserving models, and information-centric security. These are the following Trending Cloud Computing Research Topics .
- Green Cloud Computing
- Edge Computing
- Cloud Cryptography
- Load Balancing
- Cloud Analytics
- Cloud Scalability
- Service Model
- Cloud Computing Platforms
- Mobile Cloud Computing
- Cloud Deployment Model
- Cloud Security
i. Green Cloud Computing
Green Cloud Computing is a broad topic, that makes virtualized data centres and servers to save energy. The IT services are utilizing so many resources and this leads to the shortage of resources.
Green Cloud Computing provides many solutions, which makes IT resources more energy efficient and reduces the operational cost. It can also take care of power management, virtualization , sustainability, and recycling the environment.
ii. Edge Computing
Although edge computing has several benefits, it is frequently combined with cloud computing to form a hybrid strategy. In this hybrid architecture, certain data processing and analytics take place at the edge, while more intense and extensive long-term data storage and analysis happen in the central cloud infrastructure. The edge-to-cloud continuum refers to this fusion of edge and cloud computing.
iii. Cloud Cryptography
Cloud cryptography is the practise of securing data and communications in cloud computing environments using cryptographic methods and protocols. Sensitive data is secured against unauthorised access and possible security breaches by encrypting it both in transit and at rest.
By allowing consumers to keep control of their data while entrusting it to cloud service providers, cloud cryptography protects the confidentiality, integrity, and authenticity of that data. Cloud cryptography improves the security posture of cloud-based apps and services, promoting trust and compliance with data privacy rules by using encryption methods and key management procedures.
iv. Load Balancing
Load Balancing is the distribution of the load over the servers so that the work can be easily done. Due to this, the workload demands can be distributed and managed. There are several advantages of load balancing and they are-
- Fewer chances of the server crash.
- Advanced security.
- Improvement in overall performance.
The load balancing techniques are easy to implement and less expensive. Moreover, the problem of sudden outages is diminished.
v. Cloud Analytics
Cloud analytics can become an interesting topic for researchers, as it has evolved from the diffusion of data analytics and cloud computing technologies . The Cloud analytics is beneficial for small as well as large organizations.
It has been observed that there is tremendous growth in the cloud analytics market. Moreover, it can be delivered through various models such as
- Community model
Analysis has a wide scope, as there are many segments to perform research. Some of the segments are business intelligence tools , enterprise information management, analytics solutions, governance, risk and compliance, enterprise performance management, and complex event processing
vi. Scalability
Scalability can reach much advancement if proper research is done on it. Many limits can be reached and tasks such as workload in infrastructure can be maintained. It also has the ability to expand the existing infrastructure.
There are two types of scalability:
The applications have rooms to scale up and down, which eliminates the lack of resources that hamper the performance.
vii. Cloud Computing Platforms
Cloud Computing platforms include different applications run by organizations. It is a very vast platform and we can do many types of research within it. We can do research in two ways: individually or in an existing platform, some are-
- Amazon’s Elastic Compute Cloud
- IBM Computing
- Microsoft’s Azure
- Google’s AppEngine
- Salesforce.com
viii. Cloud Service Model
There are 3 cloud service models. They are:
- Platform as a Service (PaaS)
- Software as a Service (SaaS)
- Infrastructure as a Service (IaaS)
These are the vast topics for research and development as IaaS provides resources such as storage , virtual machines, and network to the users. The user further deploys and run software and applications. In software as a service , the software services are delivered to the customer.
The customer can provide various software services and can do research on it. PaaS also provides the services over the internet such as infrastructure and the customers can deploy over the existing infrastructure.
ix. Mobile Cloud Computing
In mobile cloud computing , the mobile is the console and storage and processing of the data takes outside of it. It is one of the leading Cloud Computing research topics.
The main advantage of Mobile Cloud Computing is that there is no costly hardware and it comes with extended battery life. The only disadvantage is that has low bandwidth and heterogeneity.
x. Big Data
Big data is the technology denotes the tremendous amount of data. This data is classified in 2 forms that are structured (organized data) and unstructured (unorganized).
Big data is characterized by three Vs which are:
- Volume – It refers to the amount of data which handled by technologies such as Hadoop.
- Variety – It refers to the present format of data.
- Velocity – It means the speed of data (generation and transmission).
This can be used for research purpose and companies can use it to detect failures, costs, and issues. Big data along with Hadoop is one of the major topics for research.
xi. Cloud Deployment Model
Deployment model is one of the major Cloud Computing research topics, which includes models such as:
Public Cloud – It is under the control of the third party. It has a benefit of pay-as-you-go.
Private Cloud – It is under a single organization and so it has few restrictions. We can use it for only single or a particular group of the organization.
Hybrid Cloud – The hybrid cloud comprises of two or more different models. Its architecture is complex to deploy.
Community Cloud
x. Cloud Security
Cloud Security is one of the most significant shifts in information technology. Its development brings revolution to the current business model. There is an open Gate when cloud computing as cloud security is becoming a new hot topic.
To build a strong secure cloud storage model and Tekken issues faced by the cloud one can postulate that cloud groups can find the issues, create a context-specific access model which limits data and preserve privacy.
In security research, there are three specific areas such as trusted computing, information-centric security, and privacy-preserving models.
Cloud Security protects the data from leakage, theft, disaster, and deletion. With the help of tokenization, VPNs, and firewalls, we can secure our data. Cloud Security is a vast topic and we can use it for more researches.
The number of organizations using cloud services is increasing. There are some security measures, which will help to implement the cloud security-
- Accessibility
- Confidentiality
So, this was all about Cloud Computing Research Topics. Hope you liked our explanation.
Hence, we can use Cloud Computing for remote processing of the application, outsourcing, and data giving quick momentum. The above Cloud Computing research topics can help a lot to provide various benefits to the customer and to make the cloud better.
With these cloud computing research, we can make this security more advanced. There are many high-level steps towards security assessment framework. This will provide many benefits in the future to cloud computing. Furthermore, if you have any query, feel free to ask in the comment section.
Did you like our efforts? If Yes, please give DataFlair 5 Stars on Google
Tags: big data Cloud Analytics Cloud Computing Platforms cloud computing research Cloud Computing Research Topics Cloud Computing Topics Cloud Cryptography Cloud Deployment Model Cloud Scalability Cloud Security Cloud Service Model Edge Computing Green Cloud Computing Load Balancing Mobile Cloud Computing Research Topics on Cloud Computing
15 Responses
- Comments 15
- Pingbacks 0
Dear, I wants to write a research paper on the cloud computing security, will also discuss the comparison of the present security shecks vs improvement suggested, I am thankful to you, as your paper helps me…
hay thanks for this valueable information dear i am just going to start my research in cloud computing from scratch i dnt now more about this field but i have to now work hard for this so plz give me idea how i start with effiecient manner
Hey Yaseen, Research is a great way to explore the entire topic. But it is recommended you master Cloud computing first, then start your research. Refer to our Free Cloud Computing Tutorial Series You can research on topics like Cloud Security, Optimization of resources, and Cloud cryptography.
Hi, Thank you for your article. I’m working on Cloud Computing Platforms research paper. Would you recommend any sources where I can get a real data or DB with numbers on cloud computing platforms. So, I can analyze it, create graphs, and draw a conclusion. Thank you
….or any sources with data on Cloud Service Models. Thank you
Can you please provide your contact details as I am also starting to research on Cloud Computing, Am a 11 years exp Consultant in an MNC working in Large Infrastructure. My email is partha.059@gmail .com so that we can communicate accordingly.
Can you please put some references you used, so that we can refer for more information? Thanks.
Hi, Very much pleased to know the latest topic for research. very informative, thanks for this i am interested in optimizing the resource here when i say resource it becomes too vast in terms of cloud computing components according to the definition of cloud computing. bit confused to hit the link.. could you plz.
hello iam searching for research gap in cloud computing I cant identify the problem please suggest me research topic on cloud computing
hello I am searching for research gap in cloud computing I cant identify the problem please suggest me research topic on cloud computing
we discuss optimization of resources, the gaps available
I want to do research in cloud databases,may i know the latest challenges in cloud databases?
I am a student of MS(computer science) and i am currently finding research topics in the area of cloud computing, Please let me know the topic of cloud computing and as well research gap so i will continue the research ahead with research gap.
Hi I am a student of MS(computer science) and i am currently finding research topics in the area of cloud computing, Please let me know the topic of cloud computing and as well research gap so I will continue the research.
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
- Cloud – Introduction
- Cloud – Features
- Cloud – Pros & Cons
- Cloud – Working
- Cloud – Applications
- Cloud – Architecture
- Cloud – List of Certifications
- Cloud – SaaS
- Cloud – PaaS
- Cloud – IaaS
- Cloud – NaaS
- Cloud – IDaaS
- Cloud – Public Cloud
- Cloud – Private Cloud
- Cloud – Hybrid Cloud
- Cloud – Community Cloud
- Cloud – Virtualization
- Cloud – Hardware Virtualization
- Cloud – Software Virtualization
- Cloud – Server Virtualization
- Cloud – Linux Virtualization
- Cloud – Storage Virtualization
- Cloud – OS Virtualization
- Cloud – Operations
- Cloud – Challenges
- Cloud – Storage
- Cloud – Management
- Cloud – Technologies
- Cloud – Service Providers
- Cloud – Cube Model
- Cloud – Security
- Cloud – Books
- Cloud – Research Topics
- Google Cloud Platform
- Cloud – Mobile Cloud Computing
- Grid Computing Vs Cloud Computing
- Big Data Vs Cloud Computing
- Big Data & Cloud Computing for Business
- Future of Cloud Computing
- What’s Next After Cloud Computing
- Interview Questions Part-1
- Cloud Computing Quiz Part-1
- Cloud Computing Quiz Part-2
- Cloud Computing Quiz Part-3
- Cloud Computing Quiz Part-4
Top 10 Cloud Computing Research Topics in 2022
Table of contents.
Cloud computing as a technology may have been in the cards for a long time, but its widespread application and popularity have increased in recent times. Moreover, at its current size, this industry is valued at approximately $850 billion. However, this number will not hold on for long as it is likely to go up in the coming years.
Nonetheless, if you are interested in this field and willing to learn more about it, here are 10 research topics on cloud computing that can help you start.
Top 10 Research Topics for Cloud Computing in 2022
Here are ten research topics for cloud computing to look forward to in 2022 –
- Cloud analytics
Cloud analytics is a cloud-related analytical tool that helps to analyze data and reduce data storage costs. It is used for research in genomics, exploring oil and gas reserves, business intelligence, Internet of Things (IoT) and cybersecurity. It unleashes the power of data to improve the organizational performance of a company.
- Load balancing
The workload distribution for soft computing over the server is known as load balancing. It helps in the distribution of resources over various local servers, networks and industrial servers for workload management and requirement of applications, and it also helps to keep the system stable and boost its efficiency so that there is no malfunctioning or failure of any type.
- Green cloud computing
The consumption of energy consumption is increasing in data centres due to an increase in demand for cloud services. Green cloud computing will help to minimise the consumption of energy and reduce e-waste generation. Management of power, virtualisation of the system along with the computation of the system sustainability, and recycling of environmental resources will be handled by green cloud computing systems.
- Edge computing
Processing of data at the edge of a network instead of a data warehouse is called edge computing. Some innovations are possible only due to cloud computing, which amplifies a network edge's capabilities and helps expand the domain of wireless connections.
- Cloud cryptography
Cloud cryptography adds strong protection layers which help in giving security to the cloud storage infrastructure. It helps to prevent the breach of data by saving sensitive data containing any information transmitted to third parties. Cloud cryptography systems convert plain text into an unreadable form of code. It is helped by computers and algorithms that restrict the preview of data during its delivery.
- Cloud scalability
Cloud scalability is the capability of scaling the IT resources over the cloud up or down as per the computing changes requirements. A system can be scaled horizontally, diagonally and vertically. Scalability can be applied to Memory and Disk I/O, CPU and Network I/O.
- Mobile cloud computing
These refer to the cloud computing systems that are typically for the Mobile computing system, which allows different OS, computing tasks, and data storage. Mobile cloud has many advantages. It increases the speed and flexibility of the system. It enables resource sharing across multiple systems. Mobile Cloud Computing helps in the integration of data.
Big data is the technology that helps handle large network-based systems with copious amounts from different sources. All unstructured data is connected to structured data and organised in a particular way so that handling it becomes hassle-free. Moreover, it becomes easy to manage them from one dashboard. A lot of innovation is going into this field.
- Cloud deployment model
Nowadays, a lot of apps are hosted and stored on cloud systems. So for each type of application, there needs to be a model which is based on scalability, access, scalability, ownership, cloud nature and purpose of the deployment. A cloud deployment model helps to find out which cloud environment determines the infrastructure of the cloud that suits the system best.
DevOps is all about delivering apps and services that enhance an organisation’s product, making it better and faster. The research in DevOps can help to achieve advanced security in cloud computing systems.
To conclude, this write-up has offered much-needed clarity regarding the cloud computing research topics that are popular nowadays. Hopefully, it will help you find your niche, get a more in-depth understanding of the topic, and build your career around it.

Steps to Build a RAG Application with Real-Time Data Using PGVector and Llama 3

Step-by-Step Guide to Build an AI News Reader

Fine-Tuning Llama 3 to Create a Hindi Language Chatbot: Step-by-Step Guide

Guide to Fine-Tuning Llama 3 on TIR for Financial Queries

Upcoming Events - June 2024

Chat with Your City: Steps to Build an AI Chatbot Using Llama 3 and DSPy

A Complete Guide To Customer Acquisition For Startups
Any business is enlivened by its customers. Therefore, a strategy to constantly bring in new clients is an ongoing requirement. In this regard, having a proper customer acquisition strategy can be of great importance.
So, if you are just starting your business, or planning to expand it, read on to learn more about this concept.
The problem with customer acquisition
As an organization, when working in a diverse and competitive market like India, you need to have a well-defined customer acquisition strategy to attain success. However, this is where most startups struggle. Now, you may have a great product or service, but if you are not in the right place targeting the right demographic, you are not likely to get the results you want.
To resolve this, typically, companies invest, but if that is not channelized properly, it will be futile.
So, the best way out of this dilemma is to have a clear customer acquisition strategy in place.
How can you create the ideal customer acquisition strategy for your business?
- Define what your goals are
You need to define your goals so that you can meet the revenue expectations you have for the current fiscal year. You need to find a value for the metrics –
- MRR – Monthly recurring revenue, which tells you all the income that can be generated from all your income channels.
- CLV – Customer lifetime value tells you how much a customer is willing to spend on your business during your mutual relationship duration.
- CAC – Customer acquisition costs, which tells how much your organization needs to spend to acquire customers constantly.
- Churn rate – It tells you the rate at which customers stop doing business.
All these metrics tell you how well you will be able to grow your business and revenue.
- Identify your ideal customers
You need to understand who your current customers are and who your target customers are. Once you are aware of your customer base, you can focus your energies in that direction and get the maximum sale of your products or services. You can also understand what your customers require through various analytics and markers and address them to leverage your products/services towards them.
- Choose your channels for customer acquisition
How will you acquire customers who will eventually tell at what scale and at what rate you need to expand your business? You could market and sell your products on social media channels like Instagram, Facebook and YouTube, or invest in paid marketing like Google Ads. You need to develop a unique strategy for each of these channels.
- Communicate with your customers
If you know exactly what your customers have in mind, then you will be able to develop your customer strategy with a clear perspective in mind. You can do it through surveys or customer opinion forms, email contact forms, blog posts and social media posts. After that, you just need to measure the analytics, clearly understand the insights, and improve your strategy accordingly.
Combining these strategies with your long-term business plan will bring results. However, there will be challenges on the way, where you need to adapt as per the requirements to make the most of it. At the same time, introducing new technologies like AI and ML can also solve such issues easily. To learn more about the use of AI and ML and how they are transforming businesses, keep referring to the blog section of E2E Networks.
Reference Links
https://www.helpscout.com/customer-acquisition/
https://www.cloudways.com/blog/customer-acquisition-strategy-for-startups/
https://blog.hubspot.com/service/customer-acquisition

Image-based 3D Object Reconstruction State-of-the-Art and trends in the Deep Learning Era
3D reconstruction is one of the most complex issues of deep learning systems . There have been multiple types of research in this field, and almost everything has been tried on it — computer vision, computer graphics and machine learning, but to no avail. However, that has resulted in CNN or convolutional neural networks foraying into this field, which has yielded some success.
The Main Objective of the 3D Object Reconstruction
Developing this deep learning technology aims to infer the shape of 3D objects from 2D images. So, to conduct the experiment, you need the following:
- Highly calibrated cameras that take a photograph of the image from various angles.
- Large training datasets can predict the geometry of the object whose 3D image reconstruction needs to be done. These datasets can be collected from a database of images, or they can be collected and sampled from a video.
By using the apparatus and datasets, you will be able to proceed with the 3D reconstruction from 2D datasets.
State-of-the-art Technology Used by the Datasets for the Reconstruction of 3D Objects
The technology used for this purpose needs to stick to the following parameters:
Training with the help of one or multiple RGB images, where the segmentation of the 3D ground truth needs to be done. It could be one image, multiple images or even a video stream.
The testing will also be done on the same parameters, which will also help to create a uniform, cluttered background, or both.
The volumetric output will be done in both high and low resolution, and the surface output will be generated through parameterisation, template deformation and point cloud. Moreover, the direct and intermediate outputs will be calculated this way.
- Network architecture used
The architecture used in training is 3D-VAE-GAN, which has an encoder and a decoder, with TL-Net and conditional GAN. At the same time, the testing architecture is 3D-VAE, which has an encoder and a decoder.
- Training used
The degree of supervision used in 2D vs 3D supervision, weak supervision along with loss functions have to be included in this system. The training procedure is adversarial training with joint 2D and 3D embeddings. Also, the network architecture is extremely important for the speed and processing quality of the output images.
- Practical applications and use cases
Volumetric representations and surface representations can do the reconstruction. Powerful computer systems need to be used for reconstruction.
Given below are some of the places where 3D Object Reconstruction Deep Learning Systems are used:
- 3D reconstruction technology can be used in the Police Department for drawing the faces of criminals whose images have been procured from a crime site where their faces are not completely revealed.
- It can be used for re-modelling ruins at ancient architectural sites. The rubble or the debris stubs of structures can be used to recreate the entire building structure and get an idea of how it looked in the past.
- They can be used in plastic surgery where the organs, face, limbs or any other portion of the body has been damaged and needs to be rebuilt.
- It can be used in airport security, where concealed shapes can be used for guessing whether a person is armed or is carrying explosives or not.
- It can also help in completing DNA sequences.
So, if you are planning to implement this technology, then you can rent the required infrastructure from E2E Networks and avoid investing in it. And if you plan to learn more about such topics, then keep a tab on the blog section of the website .
https://tongtianta.site/paper/68922
https://github.com/natowi/3D-Reconstruction-with-Deep-Learning-Methods

A Comprehensive Guide To Deep Q-Learning For Data Science Enthusiasts
For all data science enthusiasts who would love to dig deep, we have composed a write-up about Q-Learning specifically for you all. Deep Q-Learning and Reinforcement learning (RL) are extremely popular these days. These two data science methodologies use Python libraries like TensorFlow 2 and openAI’s Gym environment.
So, read on to know more.
What is Deep Q-Learning?
Deep Q-Learning utilizes the principles of Q-learning, but instead of using the Q-table, it uses the neural network. The algorithm of deep Q-Learning uses the states as input and the optimal Q-value of every action possible as the output. The agent gathers and stores all the previous experiences in the memory of the trained tuple in the following order:
State> Next state> Action> Reward
The neural network training stability increases using a random batch of previous data by using the experience replay. Experience replay also means the previous experiences stocking, and the target network uses it for training and calculation of the Q-network and the predicted Q-Value. This neural network uses openAI Gym, which is provided by taxi-v3 environments.
Now, any understanding of Deep Q-Learning is incomplete without talking about Reinforcement Learning.
What is Reinforcement Learning?
Reinforcement is a subsection of ML. This part of ML is related to the action in which an environmental agent participates in a reward-based system and uses Reinforcement Learning to maximize the rewards. Reinforcement Learning is a different technique from unsupervised learning or supervised learning because it does not require a supervised input/output pair. The number of corrections is also less, so it is a highly efficient technique.
Now, the understanding of reinforcement learning is incomplete without knowing about Markov Decision Process (MDP). MDP is involved with each state that has been presented in the results of the environment, derived from the state previously there. The information which composes both states is gathered and transferred to the decision process. The task of the chosen agent is to maximize the awards. The MDP optimizes the actions and helps construct the optimal policy.
For developing the MDP, you need to follow the Q-Learning Algorithm, which is an extremely important part of data science and machine learning.
What is Q-Learning Algorithm?
The process of Q-Learning is important for understanding the data from scratch. It involves defining the parameters, choosing the actions from the current state and also choosing the actions from the previous state and then developing a Q-table for maximizing the results or output rewards.
The 4 steps that are involved in Q-Learning:
- Initializing parameters – The RL (reinforcement learning) model learns the set of actions that the agent requires in the state, environment and time.
- Identifying current state – The model stores the prior records for optimal action definition for maximizing the results. For acting in the present state, the state needs to be identified and perform an action combination for it.
- Choosing the optimal action set and gaining the relevant experience – A Q-table is generated from the data with a set of specific states and actions, and the weight of this data is calculated for updating the Q-Table to the following step.
- Updating Q-table rewards and next state determination – After the relevant experience is gained and agents start getting environmental records. The reward amplitude helps to present the subsequent step.
In case the Q-table size is huge, then the generation of the model is a time-consuming process. This situation requires Deep Q-learning.
Hopefully, this write-up has provided an outline of Deep Q-Learning and its related concepts. If you wish to learn more about such topics, then keep a tab on the blog section of the E2E Networks website.
https://analyticsindiamag.com/comprehensive-guide-to-deep-q-learning-for-data-science-enthusiasts/
https://medium.com/@jereminuerofficial/a-comprehensive-guide-to-deep-q-learning-8aeed632f52f

GAUDI: A Neural Architect for Immersive 3D Scene Generation
The evolution of artificial intelligence in the past decade has been staggering, and now the focus is shifting towards AI and ML systems to understand and generate 3D spaces. As a result, there has been extensive research on manipulating 3D generative models. In this regard, Apple’s AI and ML scientists have developed GAUDI, a method specifically for this job.
An introduction to GAUDI
The GAUDI 3D immersive technique founders named it after the famous architect Antoni Gaudi. This AI model takes the help of a camera pose decoder, which enables it to guess the possible camera angles of a scene. Hence, the decoder then makes it possible to predict the 3D canvas from almost every angle.
What does GAUDI do?
GAUDI can perform multiple functions –
- The extensions of these generative models have a tremendous effect on ML and computer vision. Pragmatically, such models are highly useful. They are applied in model-based reinforcement learning and planning world models, SLAM is s, or 3D content creation.
- Generative modelling for 3D objects has been used for generating scenes using graf, pigan, and gsn, which incorporate a GAN (Generative Adversarial Network). The generator codes radiance fields exclusively. Using the 3D space in the scene along with the camera pose generates the 3D image from that point. This point has a density scalar and RGB value for that specific point in 3D space. This can be done from a 2D camera view. It does this by imposing 3D datasets on those 2D shots. It isolates various objects and scenes and combines them to render a new scene altogether.
- GAUDI also removes GANs pathologies like mode collapse and improved GAN.
- GAUDI also uses this to train data on a canonical coordinate system. You can compare it by looking at the trajectory of the scenes.
How is GAUDI applied to the content?
The steps of application for GAUDI have been given below:
- Each trajectory is created, which consists of a sequence of posed images (These images are from a 3D scene) encoded into a latent representation. This representation which has a radiance field or what we refer to as the 3D scene and the camera path is created in a disentangled way. The results are interpreted as free parameters. The problem is optimized by and formulation of a reconstruction objective.
- This simple training process is then scaled to trajectories, thousands of them creating a large number of views. The model samples the radiance fields totally from the previous distribution that the model has learned.
- The scenes are thus synthesized by interpolation within the hidden space.
- The scaling of 3D scenes generates many scenes that contain thousands of images. During training, there is no issue related to canonical orientation or mode collapse.
- A novel de-noising optimization technique is used to find hidden representations that collaborate in modelling the camera poses and the radiance field to create multiple datasets with state-of-the-art performance in generating 3D scenes by building a setup that uses images and text.
To conclude, GAUDI has more capabilities and can also be used for sampling various images and video datasets. Furthermore, this will make a foray into AR (augmented reality) and VR (virtual reality). With GAUDI in hand, the sky is only the limit in the field of media creation. So, if you enjoy reading about the latest development in the field of AI and ML, then keep a tab on the blog section of the E2E Networks website.
https://www.researchgate.net/publication/362323995_GAUDI_A_Neural_Architect_for_Immersive_3D_Scene_Generation
https://www.technology.org/2022/07/31/gaudi-a-neural-architect-for-immersive-3d-scene-generation/
https://www.patentlyapple.com/2022/08/apple-has-unveiled-gaudi-a-neural-architect-for-immersive-3d-scene-generation.html
Build on the most powerful infrastructure cloud

cloud computing Recently Published Documents
Total documents.
- Latest Documents
- Most Cited Documents
- Contributed Authors
- Related Sources
- Related Keywords
Simulation and performance assessment of a modified throttled load balancing algorithm in cloud computing environment
<span lang="EN-US">Load balancing is crucial to ensure scalability, reliability, minimize response time, and processing time and maximize resource utilization in cloud computing. However, the load fluctuation accompanied with the distribution of a huge number of requests among a set of virtual machines (VMs) is challenging and needs effective and practical load balancers. In this work, a two listed throttled load balancer (TLT-LB) algorithm is proposed and further simulated using the CloudAnalyst simulator. The TLT-LB algorithm is based on the modification of the conventional TLB algorithm to improve the distribution of the tasks between different VMs. The performance of the TLT-LB algorithm compared to the TLB, round robin (RR), and active monitoring load balancer (AMLB) algorithms has been evaluated using two different configurations. Interestingly, the TLT-LB significantly balances the load between the VMs by reducing the loading gap between the heaviest loaded and the lightest loaded VMs to be 6.45% compared to 68.55% for the TLB and AMLB algorithms. Furthermore, the TLT-LB algorithm considerably reduces the average response time and processing time compared to the TLB, RR, and AMLB algorithms.</span>
An improved forensic-by-design framework for cloud computing with systems engineering standard compliance
Reliability of trust management systems in cloud computing.
Cloud computing is an innovation that conveys administrations like programming, stage, and framework over the web. This computing structure is wide spread and dynamic, which chips away at the compensation per-utilize model and supports virtualization. Distributed computing is expanding quickly among purchasers and has many organizations that offer types of assistance through the web. It gives an adaptable and on-request administration yet at the same time has different security dangers. Its dynamic nature makes it tweaked according to client and supplier’s necessities, subsequently making it an outstanding benefit of distributed computing. However, then again, this additionally makes trust issues and or issues like security, protection, personality, and legitimacy. In this way, the huge test in the cloud climate is selecting a perfect organization. For this, the trust component assumes a critical part, in view of the assessment of QoS and Feedback rating. Nonetheless, different difficulties are as yet present in the trust the board framework for observing and assessing the QoS. This paper talks about the current obstructions present in the trust framework. The objective of this paper is to audit the available trust models. The issues like insufficient trust between the supplier and client have made issues in information sharing likewise tended to here. Besides, it lays the limits and their enhancements to help specialists who mean to investigate this point.
Cloud Computing Adoption in the Construction Industry of Singapore: Drivers, Challenges, and Strategies
An extensive review of web-based multi granularity service composition.
The paper reviews the efforts to compose SOAP, non-SOAP and non-web services. Traditionally efforts were made for composite SOAP services, however, these efforts did not include the RESTful and non-web services. A SOAP service uses structured exchange methodology for dealing with web services while a non-SOAP follows different approach. The research paper reviews the invoking and composing a combination of SOAP, non-SOAP, and non-web services into a composite process to execute complex tasks on various devices. It also shows the systematic integration of the SOAP, non-SOAP and non-web services describing the composition of heterogeneous services than the ones conventionally used from the perspective of resource consumption. The paper further compares and reviews different layout model for the discovery of services, selection of services and composition of services in Cloud computing. Recent research trends in service composition are identified and then research about microservices are evaluated and shown in the form of table and graphs.
Integrated Blockchain and Cloud Computing Systems: A Systematic Survey, Solutions, and Challenges
Cloud computing is a network model of on-demand access for sharing configurable computing resource pools. Compared with conventional service architectures, cloud computing introduces new security challenges in secure service management and control, privacy protection, data integrity protection in distributed databases, data backup, and synchronization. Blockchain can be leveraged to address these challenges, partly due to the underlying characteristics such as transparency, traceability, decentralization, security, immutability, and automation. We present a comprehensive survey of how blockchain is applied to provide security services in the cloud computing model and we analyze the research trends of blockchain-related techniques in current cloud computing models. During the reviewing, we also briefly investigate how cloud computing can affect blockchain, especially about the performance improvements that cloud computing can provide for the blockchain. Our contributions include the following: (i) summarizing the possible architectures and models of the integration of blockchain and cloud computing and the roles of cloud computing in blockchain; (ii) classifying and discussing recent, relevant works based on different blockchain-based security services in the cloud computing model; (iii) simply investigating what improvements cloud computing can provide for the blockchain; (iv) introducing the current development status of the industry/major cloud providers in the direction of combining cloud and blockchain; (v) analyzing the main barriers and challenges of integrated blockchain and cloud computing systems; and (vi) providing recommendations for future research and improvement on the integration of blockchain and cloud systems.
Cloud Computing and Undergraduate Researches in Universities in Enugu State: Implication for Skills Demand
Cloud building block chip for creating fpga and asic clouds.
Hardware-accelerated cloud computing systems based on FPGA chips (FPGA cloud) or ASIC chips (ASIC cloud) have emerged as a new technology trend for power-efficient acceleration of various software applications. However, the operating systems and hypervisors currently used in cloud computing will lead to power, performance, and scalability problems in an exascale cloud computing environment. Consequently, the present study proposes a parallel hardware hypervisor system that is implemented entirely in special-purpose hardware, and that virtualizes application-specific multi-chip supercomputers, to enable virtual supercomputers to share available FPGA and ASIC resources in a cloud system. In addition to the virtualization of multi-chip supercomputers, the system’s other unique features include simultaneous migration of multiple communicating hardware tasks, and on-demand increase or decrease of hardware resources allocated to a virtual supercomputer. Partitioning the flat hardware design of the proposed hypervisor system into multiple partitions and applying the chip unioning technique to its partitions, the present study introduces a cloud building block chip that can be used to create FPGA or ASIC clouds as well. Single-chip and multi-chip verification studies have been done to verify the functional correctness of the hypervisor system, which consumes only a fraction of (10%) hardware resources.
Study On Social Network Recommendation Service Method Based On Mobile Cloud Computing
Cloud-based network virtualization in iot with openstack.
In Cloud computing deployments, specifically in the Infrastructure-as-a-Service (IaaS) model, networking is one of the core enabling facilities provided for the users. The IaaS approach ensures significant flexibility and manageability, since the networking resources and topologies are entirely under users’ control. In this context, considerable efforts have been devoted to promoting the Cloud paradigm as a suitable solution for managing IoT environments. Deep and genuine integration between the two ecosystems, Cloud and IoT, may only be attainable at the IaaS level. In light of extending the IoT domain capabilities’ with Cloud-based mechanisms akin to the IaaS Cloud model, network virtualization is a fundamental enabler of infrastructure-oriented IoT deployments. Indeed, an IoT deployment without networking resilience and adaptability makes it unsuitable to meet user-level demands and services’ requirements. Such a limitation makes the IoT-based services adopted in very specific and statically defined scenarios, thus leading to limited plurality and diversity of use cases. This article presents a Cloud-based approach for network virtualization in an IoT context using the de-facto standard IaaS middleware, OpenStack, and its networking subsystem, Neutron. OpenStack is being extended to enable the instantiation of virtual/overlay networks between Cloud-based instances (e.g., virtual machines, containers, and bare metal servers) and/or geographically distributed IoT nodes deployed at the network edge.
Export Citation Format
Share document.

Advances, Systems and Applications
- Open access
- Published: 10 September 2021
Welcome to the new Journal of Cloud Computing by Springer
- Chunming Rong 1 &
- Zhiming Zhao 2
Journal of Cloud Computing volume 10 , Article number: 49 ( 2021 ) Cite this article
5955 Accesses
1 Citations
1 Altmetric
Metrics details
Since 2012, the Journal of Cloud Computing has been promoting research and technology development related to Cloud Computing, as an elastic framework for provisioning complex infrastructure services on-demand, including service models such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). The industry has been driving the Cloud development at an ever rapid pace, especially recently in relation to industrial automation, artificial intelligence, blockchain and Cloud-Edge-IoT convergence as well as 5G and Next Generation Internet. There are efforts in improving and facilitating modern scientific research, supporting high-tech industry, and creating a more effective general collaborative environment for different human activities. There is a vital need to involve more academic research on Cloud Computing technologies.
The journal shall become the gathering place for academic researchers, practitioners and business innovators alike, where they may publish their work together to embrace, promote and enhance cloud computing technologies and their applications.
Leading the new editorial team, the Editor-in-Chief (EiC) Prof. Chunming Rong has served extensively in leadership of IEEE Cloud Computing communities and led the transition to the IEEE CS Technical Committee on Cloud Computing (TCCLD). He served as the steering chair (2016–2019), steering member and associate editor of the IEEE Transactions on Cloud Computing (TCC) since 2016. Prof. Rong has extensive experience in managing large-scale research and innovation projects, both in Norway and the EU.
Furthermore, the review workflow is operationally handled by the Managing Editor-in-Chief Dr. Zhiming Zhao, who is an active researcher in the area of cloud computing, distributed systems, and blockchain. Since 2015, he has led the research and development efforts related to cloud automation, advanced cloud service model, and cloud data management in several EU H2020 projects, including SWITCH, ARTICONF, ENVRIplus and ENVRI-FAIR.
Together with the new editorial teams, led by topic chairs in Advanced Cloud Service, Cloud-Edge-IoT, Cloud Network, Security, Datacenter Infrastructure, and Applications.
Our goal is to promote the journal to reach board recognition and higher impact factors.
We welcome your articles as well as proposals of special issues related to emerging topics involving at least one of our associate editors.
Prof. Chunming Rong (Editor-in-Chief)
Dr. Zhiming Zhao (Managing Editor-in-Chief)
Author information
Authors and affiliations.
University of Stavanger, Stavanger, Norway
Chunming Rong
University of Amsterdam, Amsterdam, The Netherlands
Zhiming Zhao
You can also search for this author in PubMed Google Scholar
Contributions
The authors read and approved the final manuscript.
Corresponding author
Correspondence to Chunming Rong .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
Rong, C., Zhao, Z. Welcome to the new Journal of Cloud Computing by Springer. J Cloud Comp 10 , 49 (2021). https://doi.org/10.1186/s13677-021-00263-5
Download citation
Published : 10 September 2021
DOI : https://doi.org/10.1186/s13677-021-00263-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative

Latest Research Topics on Cloud Computing (2022 Updated)
Cloud computing is now a vital online technology that is used worldwide. The market size of cloud computing is expected to reach $832.1 billion by 2025 . Its demand will always increase in the future, and there are many major reasons behind it. It has acquired popularity because it is less expensive for companies rather than setting up their on-site server implementations.
In this article, we’ve covered the top 14 in-demand research topics on cloud computing that you need to know.
📌 These cloud Computing research topics are:
- Green cloud computing
- Edge computing
- Cloud cryptography
- Load balancing
- Cloud analytics
- Cloud scalability
- Mobile cloud computing
- Cloud deployment model
- Cloud security
- Cloud computing platforms
- Cloud service model
- Containerization
Top 14 Cloud Computing Research Topics For 2022
1. green cloud computing.
Due to rapid growth and demand for cloud, the energy consumption in data centers is increasing. Green Cloud Computing is used to minimize energy consumption and helps to achieve efficient processing and reduce the generation of E-waste.
It is also called GREEN IT. The goal is to go paperless and decrease the carbon footprint in the environment due to remote working.
Power management, virtualization, sustainability, and environmental recycling will all be handled by green cloud computing.
2. Edge Computing
A rapidly growing field where the data is processed at the network’s edge instead of being processed in a data warehouse is known as edge computing. The real-time computing capacity is driving the development of edge-computing platforms. The data is processed from the device itself to the point of origin without relying on a central location which also helps to increase the system’s security. It gives certain benefits such as cost-effectiveness, powerful performance, and new functionality which wasn’t previously available.
Some innovations are made with the help of cloud computing by increasing the ability of network edge capabilities and expanding wireless connections.
3. Cloud Cryptography
Cloud Cryptography is a strong layer of protection through codes that helps to give security to the cloud storage and breach of the data. It saves sensitive data content without delaying the transmission of information. It can turn plain text into unreadable code with the help of computers and algorithms and restrict the view of data being delivered.
The clients can use the cryptographic keys only to access this data. The user’s information is kept private, which results in fewer chances of cybercrime from the hackers.
4. Load Balancing
The workload distribution over the server for soft computing is called load balancing. It helps distribute resources over multiple PCs, networks, and servers and allows businesses to manage workloads and application needs. Due to the rapid increase in traffic over the Internet, the server gets overloaded—two ways to solve the problem of overload of the servers: single-server and multiple-server solutions.
Keeping the system stable, boosting the system’s efficiency, and avoiding system failures are some reasons to use load balancing. It can be balanced by using software-based and hardware-based load balancers.
5. Cloud Analytics
Cloud analytics is a set of societal and analytical tools that analyze data on a private or public cloud to reduce data storage costs and management. It is specially designed to help clients get information from massive data. It is widely used in industrial applications such as genomics research, oil and gas exploration, business intelligence, security, and the Internet of Things (IoT).
It can help any industry improve its organizational performance and drive new value from its data. It is delivered through various models: public, private, hybrid, and community models.
6. Cloud Scalability
Cloud scalability refers to the capacity to scale up or down IT resources as per the need for change in computing. Scalability is usually used to fulfill the static needs where the workload is handled linearly when resource deployment is persistent.
The types of scalability are vertical, horizontal, and diagonal. Horizontal scaling is regarded as a long-term advantage; on the other hand, vertical scaling is considered a short-term advantage. The benefits of cloud scalability are reliability, cost-effectiveness, ease, and speed. It is critical to understand how much those changes will cost and how they will benefit the company.
It can be applied to Disk I/O, Memory, Network I/O, and CPU.
7. Mobile Cloud Computing
Mobile cloud computing helps to deliver applications to mobile devices through cloud computing. It allows different devices with different operating systems to have operating systems, computing tasks, and data storage. Mobile cloud helps speed and flexibility, resource sharing, and integrated data. Mobile Cloud Computing advantages are:
- Increased battery life
- Improvement in reliability and scalability
- Simple Integration
- Low cost and data storage capacity
- Processing power improvement
The only drawback is that the bandwidth and variability are limited. It has been chosen due to productivity and demand, increasing connectivity.
8. Big Data
Big data is a technology generated by large network-based systems with massive amounts of data produced by different sources. The data get classified through structured (organized data) and unstructured (unorganized data), and semi-structured forms. The data are analyzed through algorithms which may vary depending upon the data means. Its characteristics are Volume, Variety, Velocity, and Variability.
Organizations can make better decisions with the help of external intelligence, which includes improvements in customer service, evaluation of consumer feedback, and identification of any risks to the product/services.
9. Cloud Deployment Model
The way people use the cloud has evolved based on ownership, scalability, access, and the cloud’s nature and purpose. A cloud deployment model identifies a particular sort of cloud environment that determines the cloud infrastructure’s appearance.
Cloud computing deployment models are classified according to their geographical location. Deployment methods are available in public, private, hybrid, community, and multi-cloud models.
It depends on the firms to choose as per their requirements as each model has its unique value and contribution.
10. Cloud Security
Cloud security brings the revolution to the current business model through shifts in information technology. With the rapid increase in the number of cloud computing, the organization needs the security of the cloud, which has become a significant concern.
Cloud Security protects the data from any leakage or outflow, with the removal of theft and catastrophe. The cloud has public, private, and hybrid clouds for security purposes.
Cloud security is needed to secure clients’ data, such as secret design documents and financial records. Its benefits are lower costs, reduced ongoing operational and administrative expenses, increased data reliability and availability, and reduced administration.
11. Cloud Computing Platforms
In an Internet-based data center, a server’s operating system and hardware are referred to as a cloud platform. Cloud platforms work when a firm rents to access computer services, such as servers, databases, storage, analytics, networking, software, and intelligence. So the companies don’t have to set up their data centers or computing infrastructure; they need to pay for what they use. It is a very vast platform where we can do many types of research.
12. Cloud Service Model
The use of networks hosted on the Internet to store from remote servers used in managing and processing data, rather than from a local server or a personal computer. It has three models namely Infrastructure-as-a-Service (IaaS), Software-as-a-Service (SaaS),and Platform-as-a-Service (PaaS).Each type of cloud computing service provides different control, flexibility, and management levels to choose the right services for your requirements.
The ability to deliver applications and services increases an organization’s ability to evolve and improve products faster. This model helps the firms have their benefits more quickly and better than traditional software. In the DevOps approach, development and operations teams are integrated into a single unit, enabling them to develop diverse skills that aren’t limited to a particular task. The benefits of DevOps are rapidity, increase in frequency, reliability, scale, improved collaboration, and security.
It provides a wide range of tools and technologies to meet clients’ needs.
14. Containerization
Containerization is a popular software development technique that is rapidly evolving and can be used in addition to virtualization. It includes packaging software code and all of its components so that it may run consistently and uniformly across any infrastructure. The developers and operational teams see its benefit as it helps create and locate applications quickly and more securely. It benefits developers and development groups as it provides flexibility/ portability, the ability to move swiftly and efficiently, speed, fault isolation, efficiency, easily manageable, and security.
Final Words
Hence, all the above are new technologies of cloud computing developed to benefit users worldwide. But there are some challenges that need to be overcome. People nowadays have become skeptical about whether their data is private, secure, or not. This research can make this security more advanced and help to provide innovations in cloud computing.
We hope this article helps you to know some best research topics on cloud computing and how they’re changing the world.
10Pie Editorial Team is a team of certified technical content writers and editors with experience in the technology field combined with expert insights . Learn more about our editorial process to ensure the quality and accuracy of the content published on our website.

10Pie is your go-to resource hub to start and grow your Tech Career.
Send us your queries at [email protected]
CAREER GUIDES
- Data Science
- Cyber Security
- Cloud Computing
- Artificial Intelligence
- Business Intelligence
- Contributors
- Tech Glossary
- Editorial Policy
- Tech Companies
- Privacy policy
📈 Tech career paths
- AI career paths
- Python career paths
- DevOps career paths
- Data engineer career paths
- Data science career paths
- Software testing career paths
- Software engineer career paths
🏆 Tech courses
- Cloud computing courses in Pune
- Data analytics courses in Hyderabad
- Data science courses in Mangalore
- Cloud computing courses in Hyderabad
- Data analytics courses in Indore
- Data analytics courses in Mumbai
- Data analytics courses in Pune
📌 Featured articles
- AI seminar topics
- Which tech career is right for me?
- Will AI replace software engineers?
- Top data annotation companies
- Cyber security career roadmap
- How Tesla uses Artificial Intelligence
- Cloud computing seminar topics
© 2023 All rights reserved. All content is copyrighted, republication is prohibited.
Cloud Computing Trends (All You Need To Know)

Cloud computing enables new opportunities for growth and digitalization. It allows developers to build, test, deploy, and manage applications without an in-house infrastructure. Cloud industry expectations evolve as developers continue incorporating cloud services into their software development life cycle. Development teams want more powerful servers, tighter security, faster performance, and smoother workflows.
But it sometimes feels like the resulting developments emerge faster than you can integrate your previous round of changes. So, to help you stay ahead of the game and make well-informed decisions for your organization, read on and explore the latest trends in cloud computing.
The Top Cloud Computing Trend? More of It
In a recent article , Gartner predicted that more than 85% of organizations will embrace cloud-first principles by 2025. Today, a significant part of software development incorporates cloud computing in some way. Software development is a rapidly evolving field. Developers must stay abreast of the latest cloud trends to stay relevant in the industry. They can reap the benefits and fully execute a digital strategy if software engineers, IT managers, DevOps engineers , and system administrators consistently work on optimizing the systems even as cloud computing constantly evolves.
Let’s explore some of what’s new in cloud computing.
The Trend Toward Hybrid Cloud Servers
Hybrid cloud servers combine the strength of public and private cloud servers and let you create a tailored IT architecture that spans multiple different environments. Previously, you would have to compromise between public and private cloud servers depending on what fits your application’s requirements. The public cloud offers efficient data access, near-unlimited scalability, no capital investment, and pay-as-you-go services. A private cloud is the first choice for handling sensitive data that requires monitored access and control.
With a hybrid approach, you can create a custom public-private cloud solution. You aren’t stuck with a single provider and can embrace the best of both worlds. You can also choose services from multiple cloud vendors or providers and incorporate multi-cloud solutions.

Pushing the Cloud to the Edge
Edge computing is a decentralized computing infrastructure where computing and storage occur nearer to end users. Edge computing puts data and processing closer to the end user’s device instead of providing service in a central location that might be far from those users. The edge could be the user edge (smartphones and Internet of Things devices) or the network edge (a service provider’s edge network).
Although edge computing might seem counterintuitive to cloud computing, the two complement each other. It solves challenges that currently persist in the cloud. For performance-sensitive applications where systems need to process data incredibly fast, edge computing solves the problem of latency. It also saves bandwidth since vast amounts of data don’t have to travel to distant servers.
Edge computing also supports privacy and compliance, as enterprise data centers can remain in a specific location and adhere to those regulations.
Edge computing is likely to coexist with the cloud. Cloud companies are already racing to develop ways to extend their cloud services to edge locations.
Here at Kinsta, we’re helping our Managed WordPress Hosting customers get data closer to their audiences by deploying a CDN and webpage Edge Caching across CloudFlare’s global network of 260+ data centers.

The Cloud Gets Smarter With AI
Artificial intelligence (AI) helps data engineers manage copious data stored in the cloud and maintain data quality. It autonomously determines data patterns and gains insights to apply across the enterprise. These capabilities elevate data analysis to the next level. AI-driven cloud computing also provides intelligent automation and monitors critical workflows. Developers can leverage existing AI services provided by cloud vendors to add speech, vision, and decision-making capabilities to applications. Many cloud platforms come with existing AI solutions that let developers integrate state-of-the-art machine learning (ML) applications without requiring ML expertise.
AI platforms also need access to powerful servers. ML tasks require significant processing power, but an in-house infrastructure can be very costly. Cloud computing makes AI cost-efficient by providing access to powerful servers and computing infrastructure. This way, ML engineers can train large deep learning models without worrying about investing in costly hardware and maintaining an AI infrastructure.
Also Trending: Serverless Computing
Serverless computing enables you to delegate the task of maintaining server infrastructure and provisioning services. Instead, a cloud provider service manages the infrastructure, allocates resources, and provisions complex server clusters. Depending on the requirements and activity on the server, these servers can be scaled indefinitely and automatically.
With serverless computing, developers never have to deal with servers or perform any environment configuration before deployment. They can simply upload small code snippets or a function and run these on servers close to the end user, thereby reducing latency. Unlike traditional servers, where servers run even when not in use, most cloud providers offer a pay-as-you-go service where you only pay for what you use instead of paying fixed amounts for storage and computation.
Incorporating serverless computing simplifies the process of creating and deploying new features. It eliminates the risk of failures due to hardware. As a result, you can focus on adding value to the core business and increasing productivity rather than spending time on overhead tasks like maintaining server clusters.
Secure Access Service Edge (SASE)
Security threats continue to rise as companies adopt digital transformation. There’s a vital need for a strategy to mitigate IT security risks. IT managers must implement best-in-class security practices to mitigate threats. It’s crucial to look for weaknesses in your current cloud system, develop workflows for monitoring, generate insights, and take proactive measures.
Companies are increasingly adopting secure access service edge (SASE) to ramp up their cloud security. SASE enhances network security by delivering services such as CASB , FWaaS , and Zero Trust using a cloud-delivered service model. A SASE architecture allows organizations to apply secure access methods and authenticate users regardless of location.
A cloud-based security service enables flexibility and cuts costs since the whole security stack is consolidated into a single security service model. It also reduces the complexity by minimizing the number of points an IT team would need to manage.

Making the Cloud More Sustainable
More companies are more concerned with sustainability than ever, which bleeds into the cloud space. Consumers want to see sustainability as an imperative feature in the cloud in addition to its security, agility, and other benefits.
Cloud features such as serverless computing, containerization, and disaster recovery strategies enable sustainable software development. Deploying code using serverless functions helps lower energy consumption rates than virtual machines. Containerizing applications also leads to a lower energy cost since containers do not require hypervisors. Developers can embrace green cloud computing to reduce costs and become ecologically and socially responsible in their software development practices.
Businesses also gain financial incentives by committing to sustainability. A report by Accenture reveals that companies that incorporate sustainability into their practices yield 4.7 times higher margins than others.
Cloud companies also embed sustainable solutions into their infrastructure to meet this demand, like reduced carbon emissions. They’re prioritizing responsible innovation that uses renewable energy sources for operations. Public clouds, for instance, reduce individual carbon footprints produced by local computing and require less energy consumption. The cloud also offers better server utilization rates, making it more cost-effective than building an in-house infrastructure for enterprise-owned data centers. That makes the cloud an appealing platform for applications with high usage.
Cloud computing lets developers build efficient, flexible, and sustainable infrastructure that improves the software development process. To prepare for growth, developers should be well-equipped with the latest cloud computing trends and experiment with new ideas.
Switching to hybrid cloud servers can combine the power of public and private clouds. Incorporate edge computing to increase the performance of your application. Make data-driven decisions using cutting-edge AI. Delegate the process of maintaining and provisioning services by tapping into serverless computing. Lastly, adapt to sustainable services for a greener future.
The future of cloud computing brings endless opportunities for growth and innovation. And you can explore Kinsta’s Application Hosting and Database Hosting platform to take the world by storm with your own cloud-based project.
Salman Ravoof is a self-taught web developer, writer, creator, and a huge admirer of Free and Open Source Software (FOSS). Besides tech, he's excited by science, philosophy, photography, arts, cats, and food. Learn more about him on his website , and connect with Salman on Twitter .
Related Articles and Topics
Powerful Managed WordPress Hosting

Intro to Serverless PHP: Key Features, Use Cases, and How to Get Started with Bref on Lambda
- Web Development
Leave a Reply Cancel reply
By submitting this form: You agree to the processing of the submitted personal data in accordance with Kinsta's Privacy Policy , including the transfer of data to the United States.
You also agree to receive information from Kinsta related to our services, events, and promotions. You may unsubscribe at any time by following the instructions in the communications received.
The digital forecast: 40-plus cloud computing stats and trends to know in 2023

Blair Franklin
Contributing Writer, Google Cloud
Stay in the know and spark dialogue with the latest cloud computing insights from our live blog. Bonus: Every stat has a grab-and-go slide.
Why google cloud.
Get unmatched cloud technology built on Google’s infrastructure.
How are IT leaders changing their cloud strategies in times of uncertainty? What are the biggest barriers to achieving true corporate sustainability? What’s helping to reduce burnout on software and IT teams? Where does Vint Cerf get all of his stylish pocket squares? (We're still gathering data on that last one.)
The cloud computing landscape is as dynamic as the weather. As the pace of innovation in the cloud and the availability of new tools and services continues to explode, Gartner® forecasts worldwide public cloud end-user spending to reach nearly $600 billion in 2023. It’s an exciting, promising, and sometimes dizzying space.
To help the C-suite, IT, and business decision-makers keep up with industry-shaping trends, we’re kicking off this live blog to share the latest insights across topics that matter to today’s organizational leaders: business resilience, data analytics, artificial intelligence (AI) and machine learning (ML), cloud infrastructure, cybersecurity, corporate sustainability, and more.
Bonus: Every stat has a complementary visual slide available to download. We’ll be adding to this post each week, so bookmark it as a go-to resource for the latest cloud computing trends, statistics, and insights to shape decision-making in 2023.
Explore by category — new topics will be added regularly:
Business resilience
Artificial intelligence (AI) and machine learning (ML)
Culture of innovation
Cloud infrastructure
Cloud security
Corporate sustainability
Financial resilience stats

1. IT leaders are looking to the cloud to help prepare for whatever lies ahead.
Due to the current macroeconomic climate, cloud leaders say they are increasing their use of cloud-based services and products (41.4%), planning to migrate from legacy enterprise software to cloud-based tools (33.4%), and migrating on-premises workloads to the cloud (32.8%). Download slide Source: Google Cloud Brand Pulse Survey, Q4 2022. Learn more about how decision-makers are preparing for uncertainty .
2. Cloud decision-makers are prioritizing staffing efforts when it comes to cloud cost optimization.
More than half of organizations are either hiring new staff or re-training existing staff to better optimize their cloud spend. Download slide Source: Forrester, 2022 Infrastructure Cloud Survey
3. Most companies have yet to embrace cloud FinOps.
In a 2022 survey of cloud FinOps practitioners, 37.1% of the 572 respondents who answered a question about the maturity level of their cloud FinOps efforts said they were in the “crawl” stage — getting the basics in place. Another 41.7% were in the “walk” stage, where practitioners have established practices but not yet perfected them, while just 19.5% of participants were at the leading edge of maturity, where cloud FinOps is business as usual (the “run” stage). The remaining respondents comprised a “pre-crawl” segment. Download slide Source: The State of FinOps 2022 , FinOps Foundation. Learn more about harnessing the power of FinOps .
4. Companies in every industry can capture substantial value from cloud.
A detailed review of cloud cost-optimization levers and value-oriented business use cases foresees more than $1 trillion in run-rate EBITDA across Fortune 500 companies as up for grabs in 2030. Download slide Source: Cloud’s trillion-dollar prize is up for grabs , McKinsey, 2021
5. “Industry clouds” will increase organizational agility, speed innovation, and accelerate time to value.
By 2027, more than 50% of enterprises will use industry cloud platforms to accelerate their business initiatives. Industry cloud platforms enable a shift from generic solutions to platforms designed to fit the specifics of the user’s industry. Download slide Source: Gartner® ebook, Gartner's 2023 Top Strategic Technology Trends , 2022. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
6. Automated cloud cost optimization policies can save time and reduce wasted spend.
More than 40% of technical and business professionals are using automated policies to shut down workloads after hours and to rightsize underutilized instances. Automated cloud cost optimization policies can save time while ensuring organizations monitor their environments consistently to eliminate waste. Download slide Source: Flexera 2022 State of the Cloud Report
7. When it comes to a strategic cloud computing partner, decision-makers are looking for three specific characteristics.
The majority (54%) of global tech and business leaders want a cloud service provider who helps them identify technology strategies to increase revenue or reduce costs. Further, 50% define a “strategic partner” as one who “understands where my industry is going and has solutions for future needs,” and 50% say it’s “having a services organization that helps implement and maintain my infrastructure.” Download slide Source: Internal data from the Google Cloud Brand Pulse Survey, Q3 2022
Artificial intelligence (AI) and machine learning (ML) stats

1. Get ready to reskill rather than just hiring new employees for AI skills.
IDC research suggests organizations realize they can’t simply hire data scientists to solve AI talent issues and will invest internally in reskilling and AI-enabled augmentation of existing employees. Some 34% of worldwide AI service buyers chose “IT training or education” as a top service line for AI investment in the next 12 months (and for those in IT roles, the figure increased to 38%). Download slide Source: IDC FutureScape: Worldwide Artificial Intelligence and Automation 2023 Predictions , doc #US49748122, October 2022
2. AI/ML is a top workload requirement driving multicloud deployments.
Today’s tech leaders need cloud infrastructure that can support AI/ML workloads, and they’ll use other cloud providers beyond their primary cloud provider to get what they need. According to Enterprise Strategy Group research, 39% cite AI/ML as a top workload and/or workload requirement leading to their use of other cloud providers in addition to their primary cloud provider. Application development and testing (39%), database clustering (33%), and global service delivery (31%) are some other top requirements. Download slide . Source: Enterprise Strategy Group eBook, Multicloud Application Deployment & Delivery Decision Making , February 2023
3. AI and computing advancements are helping to scale digital transformation and propel AI towards mainstream adoption.
As AI adoption ramps up and the pressure to keep pace with demand for AI-based services and tools increases, most organizations will use codeless development tools for at least 30% of AI and automation initiatives by 2024. Download slide Source: IDC FutureScape: Worldwide Artificial Intelligence and Automation 2023 Predictions , doc #US49748122, October 2022
4. AI is finding its way into every layer of technology that organizations use to help drive automation.
By 2026, AI-driven features will be embedded across business technology categories with 60% of organizations using them to drive better outcomes without relying on technical AI talent. Download slide Source: IDC FutureScape: Worldwide Artificial Intelligence and Automation 2023 Predictions , doc #US49748122, October 2022
5. AI has the potential to help organizations and people to be more productive.
Trends show that by 2026, 85% of enterprises will combine human expertise with AI, ML, natural language processing (NLP), and pattern recognition to help augment foresight, increasing worker productivity by 25%. Download slide Source: IDC FutureScape: Worldwide Artificial Intelligence and Automation 2022 Predictions , doc #US48298421, October 2021
6. Organizations have not reached a level of maturity in their AI infrastructure.
When it comes to AI/ML initiatives, survey results from the International Data Corporation (IDC) show that most organizations are still in the experimentation, evaluation and testing, or prototyping phases. Only 31% of respondents said they had AI in production — and just a third from that segment claimed to have reached a mature state of adoption, where the entire organization benefits from an enterprise-wide AI strategy. Download slide Source: IDC Press Release, IDC Survey Illustrates the Growing Importance of Purpose-built AI Infrastructure in the Modern Enterprise , February 2022. Read more: Build an effective AI strategy: Overcome four common adoption challenges
7. CxOs are leveraging AI to turn IT operations into a well-oiled machine.
Nearly 40% of decision-makers are using AI to improve efficiencies in IT operations. CxOs also indicated this is their most common use case for AI. Download slide Source: Forrester 2022 Data & Analytics survey
8. Adaptive AI accelerates value and continuously keeps AI aligned to enterprise goals in real time.
By 2026, enterprises that have adopted AI engineering practices to build and manage adaptive AI systems will outperform their peers in the operationalizing AI models by at least 25%. Adaptive AI systems use real-time feedback to learn dynamically and adjust, even for unforeseen real-world changes. Download slide Source: Gartner® ebook, Gartner's 2023 Top Strategic Technology Trends , 2022. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Culture of innovation stats

Source: Google Cloud Brand Pulse Survey, Q4 2022. Download the slide or read the full article .
1. The meaning of digital transformation is changing.
72% of cloud decision-makers view digital transformation as something more than a simple lift-and-shift exercise where systems are moved from data centers to the cloud. Download slide Source: Google Cloud Brand Pulse Survey, Q2 2022. Read more about how the definition of digital transformation is changing .
2. Organizations plan to focus on investments towards innovation over the next five years.
Some 75% of enterprises plan to invest in new technology platforms to facilitate innovation exchange. Other significant areas include investing in additional training programs on innovation (64%), evolving hiring policies to capture more diverse ideas and approaches (53%), and strengthening data gathering and analysis processes to support decision making (42%). Download slide Source: Create a Culture of Innovation , Google Cloud, 2022
3. Process optimization and customer experience are at the heart of digital transformations.
Around 47% of cloud decision-makers say digital transformation means optimizing processes and becoming more operationally agile, and another 40% say it’s improving customer experience. Download slide and bonus gif Source: Google Cloud Brand Pulse Survey, Q2 2022. Read more about how business leaders define digital transformation .
4. Culture has a significant effect on whether individuals struggle with burnout as a result of working remotely.
Teams with a generative culture, composed of people who felt included and like they belonged on their team, were half as likely to experience burnout during the pandemic. This finding reinforces the importance of prioritizing team and culture. Teams that do better are equipped to weather more challenging periods that put pressure on both the team and on individuals. Download slide Source: 2021 State of DevOps Report , commissioned by the Google Cloud DORA Team
5. The experiences of diverse employees are leading to poor outcomes for individuals and employers.
50% of employees are estimated to have left a job due to DEI shortcomings. Download slide Source: " It’s Time to Reimagine Diversity, Equity, and Inclusion ," Boston Consulting Group, May 2021
6. The use of cloud computing has a positive impact on overall organizational performance.
IT leaders and practitioners that use cloud computing are 14% more likely to exceed organizational performance goals than peers that do not. Download slide Source: 2022 State of DevOps Report , commissioned by the Google Cloud DORA Team
Cloud infrastructure stats

1. Leading IT professionals embrace multicloud. In order to scale applications to meet the needs of their users, more and more organizations are managing their resources in distributed application environments.
According to a recent survey by Enterprise Strategy Group, the majority of organizations deploy applications in 2+ on-premises data centers, 2+ colocation providers, 3+ IaaS providers, and 3+ PaaS providers. The age of multicloud is officially here, as 85% of organizations indicated they deploy applications on two or more IaaS providers. Download slide Source: Enterprise Strategy Group eBook, Multicloud Application Deployment & Delivery Decision Making , February 2023
2. When it comes to selecting the right cloud provider, more groups are getting a seat at the table.
For many, choosing a cloud provider used to be the sole responsibility of the IT department. But today, it is a highly strategic decision involving multiple members across IT, information security, the C-suite, and more. On average, 3.7 groups in an organization own cloud selection decisions. The top groups cited that have decision-making authority are IT Leadership (50%), Information Security, (47%), IT Infrastructure and Management (47%), and non-IT Executive Management/C-suite (44%). Download slide Source: Enterprise Strategy Group eBook, Multicloud Application Deployment & Delivery Decision Making , February 2023
3. Cloud-first is the dominant policy for deploying new applications.
Across deployment strategies for net-new applications and workloads, 47% of organizations within various industries follow a cloud-first strategy by deploying new applications using public cloud services. Meanwhile, 27% of organizations consider both public cloud services and on-premises resources for new applications, while 26% are on-premises-first but still consider compelling cases to deploy in cloud. Download slide Source: Enterprise Strategy Group eBook, Multicloud Application Deployment & Delivery Decision Making , February 2023
4. The desire for flexibility fuels multicloud decision making, and the type of desired flexibility varies by industry.
Performance flexibility (35%) is the top cited reason for using more than one public cloud infrastructure provider. Industry also plays a role in what type of prioritization IT leaders care about. For example, healthcare organizations (45%) lean more heavily towards cost flexibility. Retail (48%) and technology (45%) organizations want teams to be able to use their preferred clouds of choice. Finance organizations (43%) want to avoid vendor lock-in. Download slide Source: Enterprise Strategy Group eBook, Multicloud Application Deployment & Delivery Decision Making , February 2023
5. Organizations are doubling down on cloud and hybrid cloud, pushing even more applications out of on-premises environments.
In 2022, 93% of technology leaders said they were “mostly cloud” in some form — up from 83% two years ago — and 48% said they were “mostly hybrid,” up from 40% two years ago. Meanwhile, the number of respondents who said they were “mostly on-premises'' dropped by half to 7%. Download slide Source: 2022 State of APIs and Applications
6. IT leaders say APIs give their business an edge. More than six in 10 (61%) say that APIs help build better digital experiences and products, and 54% say they accelerate innovation by facilitating collaboration with partners. Download slide . Source: 2022 State of APIs and Applications
7. Tools built by cloud providers are a preferred starting place for operations and management teams working in the cloud.
69% of IT leaders and decision-makers trust that cloud providers can build better tools to manage their own clouds. Download slide Source: “A Built-In Observability Tool Adoption Blueprint for Public Cloud: Driving Quantified Value for DevOps, Development, Operations, and SRE Teams,” IDC whitepaper sponsored by Google Cloud, 2022
8. Budgets are increasing across both internal private cloud and public, and across cloud workload types.
In the 2022 Infrastructure Cloud Survey, respondents reported an increase in IT budget for both public cloud (75%) and internal private cloud (77%) during 2022. Download slide . Source: Forrester 2022 Infrastructure Cloud Survey
9. Multicloud and hybrid cloud use is on the rise.
Some 26% of people reported using multiple public clouds in 2022, up from 21% in 2021. Hybrid cloud use also increased from 25% to 42.5%. Download slide . Source: 2022 State of DevOps Report , commissioned by the Google Cloud DORA Team
10. The use of cloud computing continues to accelerate.
During 2022, 76% of people reported using the public cloud, including multiple clouds — up from 56% in 2021. Download slide . Source: 2022 State of DevOps Report , commissioned by the Google Cloud DORA Team
Cloud security stats

1. Cybersecurity is the No. 1 investment priority for organizations in 2023.
Approximately (31%) of 4,332 global enterprise cloud decision makers ranked “cybersecurity” as a top investment priority for their organization in 2023 over data management and/or data analytics (25%), AI&ML (20%), app and/or infrastructure modernization (12%), and productivity & collaboration (11%). Download slide Source: Google Cloud Brand Pulse Survey, Wave 5, 2022
2. When it comes to trusting a cloud provider, IT leaders say data protection and interoperability/openness are the two most important capabilities or provisions.
Globally, enterprise cloud decision makers feel that “strong capabilities for protecting and controlling my data in the cloud” (40%) and “working well with existing security solutions and other security vendors” (38%) are the top ways cloud providers can gain trust. Download slide Source: Google Cloud Brand Pulse Survey, Wave 5, 2022
3. Supply chains are growing as an attractive target that acts as an entry point to multiple vendors.
Supply chain was identified as the initial infection vector — the first path attackers used to gain access to an environment — in 17% of security intrusions in 2021, compared to less than 1% in 2020. Download slide Source: M-Trends 2022 , Mandiant
4. Business and professional services and financial services are the top targeted industries across the globe.
The top five industries favored by adversaries in 2021, based on Mandiant incident response engagements, include business and professional services, financial, healthcare, retail and hospitality, and high tech. Download slide Source: M-Trends 2022 , Mandiant
5. API security is affecting the pace of innovation for many organizations.
More than half (53%) of organizations have delayed the rollout of a new service or application due to API security concerns. For those who have experienced an incident in the past 12 months, more than three quarters (77%) have delayed the rollout of a new service or application. Download slide . Source: API Security: Latest Insights & Key Trends
6. Companies are prioritizing being proactive with API security.
To stay ahead of security threats, many organizations look for solutions that allow them to be proactive while minimizing the burden on their security teams. Capabilities that proactively identify security threats (60%) and improve automation (57%) are at the top of most IT leaders’ wish lists. Download slide . Source: API Security: Latest Insights & Key Trends
7. Development teams that embrace security see significant value driven to the business.
Teams who integrate security best practices throughout their development process are 1.6 times more likely to meet or exceed their organizational goals. Download slide Source: 2021 State of DevOps Report , commissioned by the Google Cloud DORA Team
8. The biggest predictor of an organization's software security practices is cultural, not technical.
High-trust, low-blame cultures focused on performance were 1.6 times more likely to have above-average adoption of emerging security practices than low-trust, high-blame cultures focused on power or rules. Download slide Source: 2022 State of DevOps Report , commissioned by the Google Cloud DORA Team
9. Europe may surpass the United States as the most targeted region for ransomware.
Ransomware continues to have a significant impact on businesses across the globe. While reports show that the U.S. is the country most targeted by ransomware attacks worldwide, small indicators show that ransomware activity is decreasing in the United States and growing in other regions. For instance, the number of European victims is on the rise, and if that increase continues, Europe will likely become the most targeted region in 2023. Download slide Source: Cybersecurity Forecast 2023 , Mandiant
Corporate sustainability stats

1. Technology innovation is the top utility executives believe will impact the sustainable growth of their organization.
More than 91% of respondents agree that “technology makes it possible for our organization to be more sustainable.” Download slide Source: CEOs are Ready to Fund a Sustainable Transformation , The Harris Poll survey for Google Cloud, 2022
2. Increasingly, sustainable technology will be a must-have; not a nice-to-have. By 2025, 50% of CIOs will have performance metrics tied to the sustainability of the IT organization.
Sustainable technology is a framework of digital solutions that can be used to enable ESG outcomes. Download slide Source: Gartner® ebook, Gartner's 2023 Top Strategic Technology Trends , 2022. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
3. Many organizations still struggle to overcome internal barriers to achieving corporate sustainability.
When asked about the top barriers to achieving true environmental sustainability, executives identified the following as their biggest challenges: lack of investment in the right technology (36%), lack of understanding about the issue (36%), too much focus on growth and profit (34%), limited budget for sustainability measures (34%), and lack of regulatory incentives or political will (34%). Download slide Source: CEOs are Ready to Fund a Sustainable Transformation , The Harris Poll survey for Google Cloud, 2022
4. Digital technologies have the potential to help minimize carbon emissions across the entire digital value chain.
Digital solutions will play an enabling role for at least 20-25% of the reductions required to achieve a net-zero economy in Europe. Download slide Source: Digital Decarbonisation , Implement Consulting Group (ICG) study commissioned by Google, 2022
5. Digitalization is correlated with a higher degree of decoupling between economic growth and emissions.
The most advanced digital economies in the EU reduced greenhouse gas emissions by 25% between 2003 and 2019 while increasing economic output by 30% in the same period. Download slide Source: Digital Decarbonization, Implement Consulting Group (ICG) study commissioned by Google, 2022
6. Authentically achieving sustainability is a big challenge.
Only 36% of executives said that their organizations have measurement tools in place to quantify their sustainability efforts, and just 17% are using those measurements to optimize based on results. Download slide Source: CEOs are Ready to Fund a Sustainable Transformation , The Harris Poll survey for Google Cloud, 2022
7. Technology is key to transforming corporate sustainability.
Nearly 80% of executives cite technology as critical for their future sustainability efforts, attesting that it helps transform operations, socialize their initiatives more broadly, and measure and report on the impact of their efforts. Download slide Source: CEOs are Ready to Fund a Sustainable Transformation , The Harris Poll survey for Google Cloud, 2022
- Transform with Google Cloud
Related articles

Survey says: Leaders are doubling down on cloud for stability and financial resilience
By Blair Franklin • 5-minute read

The 4 questions executives should be asking about their organization's business resilience
By Alison Jarris • 4-minute read

Solving for hard things: How De' Longhi streamlined operations around the world
By Fabrizio Clerici • 3-minute read

Multicloud's moment: Everybody's doing it, but are you doing it right? Here's eight dos and don'ts
By Richard Seroter • 6-minute read
- Internet of Services
- Computing Methodologies
- Distributed Computing
- Computer Science
- Cloud Computing
Cloud Computing: A Systematic Literature Review and Future Agenda
- January 2021

- Hacettepe University
- This person is not on ResearchGate, or hasn't claimed this research yet.

- Yasar University
Discover the world's research
- 25+ million members
- 160+ million publication pages
- 2.3+ billion citations

- Younes Lafraxo
- Int J Logist Manag
- Haowei Zhang
- Kailing Liu

- Vaishnavi Chandgadkar
- Prachi Pathak
- Aditya Solanki
- Namita Pulgam
- J GLOB INF MANAG
- Jeffrey Hsu

- Muhammad Rifqi Sakti
- Akhyar Lubis
- INT J PROD RES
- Int J Emerg Market
- Huosong Xia
- Yulong (David) Liu

- J Enterprise Inform Manag
- Niki Kyriakou

- Abdullah Sheikh

- David Budgen

- Cüneyt Sevgi

- Recruit researchers
- Join for free
- Login Email Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google Welcome back! Please log in. Email · Hint Tip: Most researchers use their institutional email address as their ResearchGate login Password Forgot password? Keep me logged in Log in or Continue with Google No account? Sign up
Updated: 14 February 2024 Contributors: Stephanie Susnjara, Ian Smalley
Cloud computing is the on-demand access of computing resources—physical servers or virtual servers, data storage, networking capabilities, application development tools, software, AI-powered analytic tools and more—over the internet with pay-per-use pricing.
The cloud computing model offers customers greater flexibility and scalability compared to traditional on-premises infrastructure.
Cloud computing plays a pivotal role in our everyday lives, whether accessing a cloud application like Google Gmail, streaming a movie on Netflix or playing a cloud-hosted video game.
Cloud computing has also become indispensable in business settings, from small startups to global enterprises. Its many business applications include enabling remote work by making data and applications accessible from anywhere, creating the framework for seamless omnichannel customer engagement and providing the vast computing power and other resources needed to take advantage of cutting-edge technologies like generative AI and quantum computing .
A cloud services provider (CSP) manages cloud-based technology services hosted at a remote data center and typically makes these resources available for a pay-as-you-go or monthly subscription fee.
Read how Desktop as a service (DaaS) enables enterprises to achieve the same level of performance and security as deploying the applications on-premises.
Register for the guide on app modernization
Compared to traditional on-premises IT that involves a company owning and maintaining physical data centers and servers to access computing power, data storage and other resources (and depending on the cloud services you select), cloud computing offers many benefits, including the following:
Cloud computing lets you offload some or all of the expense and effort of purchasing, installing, configuring and managing mainframe computers and other on-premises infrastructure. You pay only for cloud-based infrastructure and other computing resources as you use them.
With cloud computing, your organization can use enterprise applications in minutes instead of waiting weeks or months for IT to respond to a request, purchase and configure supporting hardware and install software. This feature empowers users—specifically DevOps and other development teams—to help leverage cloud-based software and support infrastructure.
Cloud computing provides elasticity and self-service provisioning, so instead of purchasing excess capacity that sits unused during slow periods, you can scale capacity up and down in response to spikes and dips in traffic. You can also use your cloud provider’s global network to spread your applications closer to users worldwide.
Cloud computing enables organizations to use various technologies and the most up-to-date innovations to gain a competitive edge. For instance, in retail, banking and other customer-facing industries, generative AI-powered virtual assistants deployed over the cloud can deliver better customer response time and free up teams to focus on higher-level work. In manufacturing, teams can collaborate and use cloud-based software to monitor real-time data across logistics and supply chain processes.
The origins of cloud computing technology go back to the early 1960s when Dr. Joseph Carl Robnett Licklider (link resides outside ibm.com), an American computer scientist and psychologist known as the "father of cloud computing", introduced the earliest ideas of global networking in a series of memos discussing an Intergalactic Computer Network. However, it wasn’t until the early 2000s that modern cloud infrastructure for business emerged.
In 2002, Amazon Web Services started cloud-based storage and computing services. In 2006, it introduced Elastic Compute Cloud (EC2), an offering that allowed users to rent virtual computers to run their applications. That same year, Google introduced the Google Apps suite (now called Google Workspace), a collection of SaaS productivity applications. In 2009, Microsoft started its first SaaS application, Microsoft Office 2011. Today, Gartner predicts worldwide end-user spending on the public cloud will total USD 679 billion and is projected to exceed USD 1 trillion in 2027 (link resides outside ibm.com).
The following are a few of the most integral components of today’s modern cloud computing architecture.
CSPs own and operate remote data centers that house physical or bare metal servers , cloud storage systems and other physical hardware that create the underlying infrastructure and provide the physical foundation for cloud computing.
In cloud computing, high-speed networking connections are crucial. Typically, an internet connection known as a wide-area network (WAN) connects front-end users (for example, client-side interface made visible through web-enabled devices) with back-end functions (for example, data centers and cloud-based applications and services). Other advanced cloud computing networking technologies, including load balancers , content delivery networks (CDNs) and software-defined networking (SDN) , are also incorporated to ensure data flows quickly, easily and securely between front-end users and back-end resources.
Cloud computing relies heavily on the virtualization of IT infrastructure —servers, operating system software, networking and other infrastructure that’s abstracted using special software so that it can be pooled and divided irrespective of physical hardware boundaries. For example, a single hardware server can be divided into multiple virtual servers . Virtualization enables cloud providers to make maximum use of their data center resources.
IaaS (Infrastructure-as-a-Service), PaaS (Platform-as-a-Service), SaaS (Software-as-a-Service) and serverless computing are the most common models of cloud services, and it’s not uncommon for an organization to use some combination of all four.
IaaS (Infrastructure-as-a-Service) provides on-demand access to fundamental computing resources—physical and virtual servers, networking and storage—over the internet on a pay-as-you-go basis. IaaS enables end users to scale and shrink resources on an as-needed basis, reducing the need for high up-front capital expenditures or unnecessary on-premises or "owned" infrastructure and for overbuying resources to accommodate periodic spikes in usage.
According to a Business Research Company report (link resides outside ibm.com), the IaaS market is predicted to grow rapidly in the next few years, growing to $212.34 billion in 2028 at a compound annual growth rate (CAGR) of 14.2%.
PaaS (Platform-as-a-Service) provides software developers with an on-demand platform—hardware, complete software stack, infrastructure and development tools—for running, developing and managing applications without the cost, complexity and inflexibility of maintaining that platform on-premises. With PaaS, the cloud provider hosts everything at their data center. These include servers, networks, storage, operating system software, middleware and databases. Developers simply pick from a menu to spin up servers and environments they need to run, build, test, deploy, maintain, update and scale applications.
Today, PaaS is typically built around container s , a virtualized compute model one step removed from virtual servers. Containers virtualize the operating system, enabling developers to package the application with only the operating system services it needs to run on any platform without modification and the need for middleware.
Red Hat® OpenShift ® is a popular PaaS built around Docker containers and Kubernetes , an open source container orchestration solution that automates deployment, scaling, load balancing and more for container-based applications.
SaaS (Software-as-a-Service) , also known as cloud-based software or cloud applications, is application software hosted in the cloud. Users access SaaS through a web browser, a dedicated desktop client or an API that integrates with a desktop or mobile operating system. Cloud service providers offer SaaS based on a monthly or annual subscription fee. They may also provide these services through pay-per-usage pricing.
In addition to the cost savings, time-to-value and scalability benefits of cloud, SaaS offers the following:
- Automatic upgrades: With SaaS, users use new features when the cloud service provider adds them without orchestrating an on-premises upgrade.
- Protection from data loss: Because SaaS stores application data in the cloud with the application, users don’t lose data if their device crashes or breaks.
SaaS is the primary delivery model for most commercial software today. Hundreds of SaaS solutions exist, from focused industry and broad administrative (for example, Salesforce) to robust enterprise database and artificial intelligence (AI) software. According to an International Data Center (IDC) survey (the link resides outside IBM), SaaS applications represent the largest cloud computing segment, accounting for more than 48% of the $778 billion worldwide cloud software revenue.
Serverless computing , or simply serverless, is a cloud computing model that offloads all the back-end infrastructure management tasks, including provisioning, scaling, scheduling and patching to the cloud provider. This frees developers to focus all their time and effort on the code and business logic specific to their applications.
Moreover, serverless runs application code on a per-request basis only and automatically scales the supporting infrastructure up and down in response to the number of requests. With serverless, customers pay only for the resources used when the application runs; they never pay for idle capacity.
FaaS, or Function-as-a-Service , is often confused with serverless computing when, in fact, it’s a subset of serverless. FaaS allows developers to run portions of application code (called functions) in response to specific events. Everything besides the code—physical hardware, virtual machine (VM) operating system and web server software management—is provisioned automatically by the cloud service provider in real-time as the code runs and is spun back down once the execution is complete. Billing starts when execution starts and stops when execution stops.
A public cloud is a type of cloud computing in which a cloud service provider makes computing resources available to users over the public internet. These include SaaS applications, individual virtual machines (VMs) , bare metal computing hardware, complete enterprise-grade infrastructures and development platforms. These resources might be accessible for free or according to subscription-based or pay-per-usage pricing models.
The public cloud provider owns, manages and assumes all responsibility for the data centers, hardware and infrastructure on which its customers’ workloads run. It typically provides high-bandwidth network connectivity to ensure high performance and rapid access to applications and data.
Public cloud is a multi-tenant environment where all customers pool and share the cloud provider’s data center infrastructure and other resources. In the world of the leading public cloud vendors, such as Amazon Web Services (AWS), Google Cloud, IBM Cloud®, Microsoft Azure and Oracle Cloud, these customers can number in the millions.
Most enterprises have moved portions of their computing infrastructure to the public cloud since public cloud services are elastic and readily scalable, flexibly adjusting to meet changing workload demands. The promise of greater efficiency and cost savings through paying only for what they use attracts customers to the public cloud. Still, others seek to reduce spending on hardware and on-premises infrastructure. Gartner predicts (link resides outside ibm.com) that by 2026, 75% of organizations will adopt a digital transformation model predicated on cloud as the fundamental underlying platform.
A private cloud is a cloud environment where all cloud infrastructure and computing resources are dedicated to one customer only. Private cloud combines many benefits of cloud computing—including elasticity, scalability and ease of service delivery—with the access control, security and resource customization of on-premises infrastructure.
A private cloud is typically hosted on-premises in the customer’s data center. However, it can also be hosted on an independent cloud provider’s infrastructure or built on rented infrastructure housed in an offsite data center.
Many companies choose a private cloud over a public cloud environment to meet their regulatory compliance requirements. Entities like government agencies, healthcare organizations and financial institutions often opt for private cloud settings for workloads that deal with confidential documents, personally identifiable information (PII), intellectual property, medical records, financial data or other sensitive data.
By building private cloud architecture according to cloud-native principles, an organization can quickly move workloads to a public cloud or run them within a hybrid cloud (see below) environment whenever ready.
A hybrid cloud is just what it sounds like: a combination of public cloud, private cloud and on-premises environments. Specifically (and ideally), a hybrid cloud connects a combination of these three environments into a single, flexible infrastructure for running the organization’s applications and workloads.
At first, organizations turned to hybrid cloud computing models primarily to migrate portions of their on-premises data into private cloud infrastructure and then connect that infrastructure to public cloud infrastructure hosted off-premises by cloud vendors. This process was done through a packaged hybrid cloud solution like Red Hat® OpenShift® or middleware and IT management tools to create a " single pane of glass ." Teams and administrators rely on this unified dashboard to view their applications, networks and systems.
Today, hybrid cloud architecture has expanded beyond physical connectivity and cloud migration to offer a flexible, secure and cost-effective environment that supports the portability and automated deployment of workloads across multiple environments. This feature enables an organization to meet its technical and business objectives more effectively and cost-efficiently than with a public or private cloud alone. For instance, a hybrid cloud environment is ideal for DevOps and other teams to develop and test web applications. This frees organizations from purchasing and expanding the on-premises physical hardware needed to run application testing, offering faster time to market. Once a team has developed an application in the public cloud, they may move it to a private cloud environment based on business needs or security factors.
A public cloud also allows companies to quickly scale resources in response to unplanned spikes in traffic without impacting private cloud workloads, a feature known as cloud bursting. Streaming channels like Amazon use cloud bursting to support the increased viewership traffic when they start new shows.
Most enterprise organizations today rely on a hybrid cloud model because it offers greater flexibility, scalability and cost optimization than traditional on-premises infrastructure setups. According to the IBM Transformation Index: State of Cloud , more than 77% of businesses and IT professionals have adopted a hybrid cloud approach.
To learn more about the differences between public, private and hybrid cloud, check out “ Public cloud vs. private cloud vs. hybrid cloud: What’s the difference? ”
Watch the IBM hybrid cloud architecture video series.
Multicloud uses two or more clouds from two or more different cloud providers. A multicloud environment can be as simple as email SaaS from one vendor and image editing SaaS from another. But when enterprises talk about multicloud, they typically refer to using multiple cloud services—including SaaS, PaaS and IaaS services—from two or more leading public cloud providers.
Organizations choose multicloud to avoid vendor lock-in, to have more services to select from and to access more innovation. With multicloud, organizations can choose and customize a unique set of cloud features and services to meet their business needs. This freedom of choice includes selecting “best-of-breed” technologies from any CSP, as needed or as they emerge, rather than being locked into offering from a single vendor. For example, an organization may choose AWS for its global reach with web-hosting, IBM Cloud for data analytics and machine learning platforms and Microsoft Azure for its security features.
A multicloud environment also reduces exposure to licensing, security and compatibility issues that can result from " shadow IT "— any software, hardware or IT resource used on an enterprise network without the IT department’s approval and often without IT’s knowledge or oversight.
Today, most enterprise organizations use a hybrid multicloud model. Apart from the flexibility to choose the most cost-effective cloud service, hybrid multicloud offers the most control over workload deployment, enabling organizations to operate more efficiently, improve performance and optimize costs. According to an IBM® Institute for Business Value study , the value derived from a full hybrid multicloud platform technology and operating model at scale is two-and-a-half times the value derived from a single-platform, single-cloud vendor approach.
Yet the modern hybrid multicloud model comes with more complexity. The more clouds you use—each with its own management tools, data transmission rates and security protocols—the more difficult it can be to manage your environment. With over 97% of enterprises operating on more than one cloud and most organizations running 10 or more clouds , a hybrid cloud management approach has become crucial. Hybrid multicloud management platforms provide visibility across multiple provider clouds through a central dashboard where development teams can see their projects and deployments, operations teams can monitor clusters and nodes and the cybersecurity staff can monitor for threats.
Learn more about hybrid cloud management.
Traditionally, security concerns have been the primary obstacle for organizations considering cloud services, mainly public cloud services. Maintaining cloud security demands different procedures and employee skillsets than in legacy IT environments. Some cloud security best practices include the following:
- Shared responsibility for security: Generally, the cloud service provider is responsible for securing cloud infrastructure, and the customer is responsible for protecting its data within the cloud. However, it’s also essential to clearly define data ownership between private and public third parties.
- Data encryption: Data should be encrypted while at rest, in transit and in use. Customers need to maintain complete control over security keys and hardware security modules.
- Collaborative management: Proper communication and clear, understandable processes between IT, operations and security teams will ensure seamless cloud integrations that are secure and sustainable.
- Security and compliance monitoring: This begins with understanding all regulatory compliance standards applicable to your industry and establishing active monitoring of all connected systems and cloud-based services to maintain visibility of all data exchanges across all environments, on-premises, private cloud, hybrid cloud and edge.
Cloud security is constantly changing to keep pace with new threats. Today’s CSPs offer a wide array of cloud security management tools, including the following:
- Identity and access management (IAM): IAM tools and services that automate policy-driven enforcement protocols for all users attempting to access both on-premises and cloud-based services.
- Data loss prevention (DLP): DLP services that combine remediation alerts data encryption and other preventive measures to protect all stored data, whether at rest or in motion.
- Security information and event management (SIEM) : SIEM is a comprehensive security orchestration solution that automates threat monitoring, detection and response in cloud-based environments. SIEM technology uses artificial intelligence (AI)-driven technologies to correlate log data across multiple platforms and digital assets. This allows IT teams to successfully apply their network security protocols, enabling them to react to potential threats quickly.
- Automated data compliance platforms: Automated software solutions provide compliance controls and centralized data collection to help organizations adhere to regulations specific to their industry. Regular compliance updates can be baked into these platforms so organizations can adapt to ever-changing regulatory compliance standards.
Learn more about cloud security.
Sustainability in business , a company’s strategy to reduce negative environmental impact from their operations in a particular market, has become an essential corporate governance mandate. Moreover, Gartner predicts (link resides outside ibm.com) that by 2025, the carbon emissions of hyperscale cloud services will be a top-three criterion in cloud purchase decisions.
As companies strive to advance their sustainability objectives, cloud computing has evolved to play a significant role in helping them reduce their carbon emissions and manage climate-related risks. For instance, traditional data centers require power supplies and cooling systems, which depend on large amounts of electrical power. By migrating IT resources and applications to the cloud, organizations only enhance operational and cost efficiencies and boost overall energy efficiency through pooled CSP resources.
All major cloud players have made net-zero commitments to reduce their carbon footprints and help clients reduce the energy they typically consume using an on-premises setup. For instance, IBM is driven by sustainable procurement initiatives to reach NetZero by 2030. By 2025, IBM Cloud worldwide data centers will comprise energy procurement drawn from 75% renewable sources .
According to an International Data Corporation (IDC) forecast (link resides outside ibm.com), worldwide spending on the whole cloud opportunity (offerings, infrastructure and services) will surpass USD 1 trillion in 2024 while sustaining a double-digit compound annual growth rate (CAGR) of 15.7%. Here are some of the main ways businesses are benefitting from cloud computing:
- Scale infrastructure: Allocate resources up or down quickly and easily in response to changes in business demands.
- Enable business continuity and disaster recovery: Cloud computing provides cost-effective redundancy to protect data against system failures and the physical distance required to apply disaster recovery strategies and recover data and applications during a local outage or disaster. All of the major public cloud providers offer Disaster-Recovery-as-a-Service (DRaaS) .
- Build and test cloud-native applications : For development teams adopting Agile, DevOps or DevSecOps to streamline development, the cloud offers on-demand end-user self-service that prevents operations tasks, such as spinning up development and test servers, from becoming development bottlenecks.
- Support edge and IoT environments: Address latency challenges and reduce downtime by bringing data sources closer to the edge . Support Internet of Things (IoT) devices (for example, patient monitoring devices and sensors on a production line) to gather real-time data.
- Leverage cutting-edge technologies: Cloud computing supports storing and processing huge volumes of data at high speeds—much more storage and computing capacity than most organizations can or want to purchase and deploy on-premises. These high-performance resources support technologies like blockchain , quantum computing and large language models (LLMs ) that power generative AI platforms like customer service automation.
Create a no-charge IBM Cloud account and access more than 40 always-free products in cloud and AI.
IBM Cloud for VMware Solutions enables you to seamlessly migrate and modernize VMware workloads to the cloud, allowing you to leverage your existing investments for a consistent VMware experience—retaining the same level of access, security and control.
Let IBM Cloud manage your infrastructure while you manage your environment. Pay only for what you use.
Tackle large-scale, compute-intensive challenges and speed time to insight with hybrid cloud HPC solutions.
An industry-specific cloud, built to support your unique modernization and AI transformation needs.
Hybrid cloud integrates public cloud services, private cloud services and on-premises infrastructure into a single distributed computing environment.
DevOps speeds delivery of higher quality software by combining and automating the work of software development and IT operations teams.
Cloud migration is the process of relocating an organization’s data, applications, and workloads to a cloud infrastructure.
Although cloud computing is only a different way to deliver computer resources rather than a new technology, it has sparked a revolution in the way organizations provide information and service.
Determining the best cloud computing architecture for enterprise business is critical for overall success. That’s why it is essential to compare the different functionalities of private cloud versus public cloud versus hybrid cloud.
We're excited to introduce a three-part lightboarding video series that will delve into the world of hybrid cloud architecture. In this intro video, our guide, Sai Vennam, lays out the three major hybrid cloud architecture issues that we're going to cover: Connectivity, Modernization and Security.
Designed for industry, security and the freedom to build and run anywhere, IBM Cloud is a full stack cloud platform with over 170 products and services covering data, containers, AI, IoT and blockchain. Use IBM Cloud to build scalable infrastructure at a lower cost, deploy new applications instantly and scale up workloads based on demand.

Home / Cloud Computing Topics
Cloud Computing Topics
Cloud computing is the process of offering resources and services depends the user demand in regardless of location. It is the computing system which classify under of these 3 service models of cloud.
- Platform as a Service (PAAS) – offers a well-established platform for developing the software / application
- Software as a Service (SAAS) – provides a GUI based application for third party access through the internet
- Infrastructure as a Service (IAAS) – affords the cloud-oriented service / infrastructure includes networking, virtualization and storage

As you know already, the cloud computing has in-build unique features to support revolutionary technological advancement in the modern society. Here, we have given the characteristics based on three major aspects as follows,
Key Features of Cloud Computing
- Here, the user not tied up with the network and present applications accompany with the users by the cloud.
- Support fast deployment of pay-as-you-go model
- No need to care about installation updates
- User can access the service or resource from any location
- Improves the user’s capacity more than the standard local host
- Support huge volume of processing power and storage
When dealing with cloud computing , it is must to be ware with the different varieties of cloud deployments. For any cloud developments, the environment is based on the any of the following type.
Types of Cloud Deployments
- Recommended for Stand-alone Organization / Institution
- Useful for Business People with Control Norms
- Large-capacity of Storage Space with Scalability Provision
- Useful for Software Project and other Developments
- Multi-Tenant and Cooperative Platform
- Useful to Industrialists to Share Data within Organization
- Combing two different platforms as Public with Private
- Suggested for enterprise to handle Big Data with Standard Privacy Norms
So far, we have debated the cloud service, service types and its supporting features. Now, we can see about the how the task is scheduled in cloud system. In this, the scheduling process takes place in following three phases. Scheduling in cloud can be generalized into three phases namely:
- Task Allocation: Task is surrender to targeted resource
- Resource Discovering And Filtering: Data Center Broker find out all available resources in the network with their current status information
- Resource Selection: Decide on target resource depends on specific task metrics
Then, we are going to talk over about the most frequently asked cloud computing questions in google with the agreeing solutions. Since, it gives new dimension in creating novel Cloud Computing Topics .
FAQs in Cloud Computing
- Solution: Use VM migration, load balancing or scheduling schemes to assign the tasks to the particular servers. It reduces the storage overhead and also uses the resources appropriately. Due to the optimization of storage servers, it can be scale and flexible well for the large volume of tasks.
- Solution: Use blockchain or cryptography mechanisms for ensuring the security and privacy for both users, and cloud service providers. Application layer security is the crucial need for the current cloud applications and services.
- Solution: Today, tasks from the users are heterogeneous (Video, Voice or multimedia applications) and the requirements of each task are different with respect to the QoS (response time, latency and resources). Optimally choose the service provider for the corresponding task.
- Solution: At first, select the most apt approach to do each task depend on end-user or service provider request. Then, assign the resources to tasks by priority.
- Solution: CPU, memory and network bandwidth usage is estimated for task and sensitive tasks are allocated by the resources and then non-sensitive tasks are assigned using appropriate method. Due to the estimation of accurate amount of resources for the required task, applications are executed without any error.
In addition, we have given the new future direction of the cloud computing. These are handpicked by our experts after the thorough research of current advancement in cloud computing.
What is the Next in cloud?
- Cloud Computing Vendors
- Virtualization and Containers
- Server less and Microservices
- Software Define Network and Storage
- Migration of Internal Service and Private Cloud
- Private Cloud Operation and Administration
- Container Orchestration and Container as a Service
- New Technologies for IaaS based Cloud Computing and Network Security
- And other Upcoming Public Cloud Project
When working on cloud computing projects, make sure that the following things are answered in the selected research topic. Since, these aspects give the add-on score in your research work.
Research Issues in Cloud Computing
- How to address the heterogeneity of mixed clouds?
- How to incorporate multiple clouds to increase scalability
- How to model high persistent and performance caching approaches?
- How cache overcome the trustworthiness issues and enhance the performance
Just to let you know, we have given the top-demanding Cloud Computing Topics. These topics are suitable for all active cloud computing scholars as well as final year candidates. And, it is classified into 5 different categorizes for your ease.
Cloud computing project topics for final year
- Cloud Service Composition
- Business Process Management
- Cloud Federation and Interoperability
- Clouds Energy Issues
- Adaptive and also Dynamic Services
- Service Life Cycles and also Service Governance
- Container Deployment
- Architectural Models
- Service Privacy and also Security
- Building Service based Applications
- Self-Organizing Service Architectures
- Crowd and Social based Cloud
- Cloud and also in Service Business Models
- Scientific Computing
- Smart Cities
- RESTful Services and also clouds
- DevOps in the cloud
- Microservices Management and also Deployment
- Trends in Computation, Storage and also in Network Clouds
- Next Gen Service Repositories
- Edge/Fog Computing
- Real-Time and Embedded Services
- Fog to Multi Cloud Services
- IoT service Engineering
- Cloud to Fog Computing Solutions
- IoT Delivery Models
- Mobile Services and also Clouds
- PaaS and IaaS Cloud Services
- Industry Clouds: Rapidly Growing Segments
- Internet of Things and Artificial Intelligence
- Hyper-scale Providers also on Cloud
- Hybrid Cloud Platform and Services
- Severless Computing
- Workload Acceleration
- Data Center Proliferation
- Hardened/ Trusted/ Shield VMs
- Resource Allocation
Cloud Computing Tools and Simulators
Now, shall we see about the implementation tools for cloud computing. Normal tools addresses the user demands based on resource features (storage size, processing ability in MIPs, deadlines). Further, advance tools analyze the task interdependence for real-world cloud communication.
In overall, Cloud simulation tools measures the performance and readiness of critical cloud system. In addition, it monitors, handles and assesses the applications, infrastructure, architecture and services. Below, we have suggested some important cloud monitoring tools,
- Logic Monitor
- AppDynamics
- Amazon CloudWatch
- Microsoft Cloud Monitoring
Moreover, cloud computing is incorporated with several advantages to assist both clients and hosts. And, it is easy to access, upload, download the info in very low time.
- Internet of Things
- Fog / Edge Computing
- Green computing (Green cloud)
Before get into the cloud oriented research work, one should know the fundamental theories of Cloud computing. By referring the good textbook materials, one can strong build their technical skills. Also, the following things are very essential for active scholars to create a successful cloud system.

How to be Successful in the Cloud?
- Software Defined Storage and Network
- Various Container Solutions (rkt, docket and more)
- Cloud based Applications Logging, Monitoring and Debugging
- Cloud CI/CD Services (Continuous Integration and Developments)
- Primary cloud offering models (private, public and hybrid) and services (SaaS, IaaS and PasS)
At the end of development phase, it is required to analysis the overall system perform to bring out the original worth of the selected research topic. Through, one can prove that their selected topic is better than other existing ones. Most importantly, it should meet the user QoS in all aspects.
Performance Analysis in Cloud Computing
Quality of Service
- Measure the network overall performance and services
- Parameters: bit rate, jitter, latency, availability, packet loss and throughput
- Has varied priority based on users, applications and data flow. For instance: telecommunication – resource advance booking and traffic ranking using Voice over IP technology
Qualities of Traffic
Here, QoS factor is varied based on the human and technical factors. In some cases, the network may miss to drop some packets because of network traffic.
- Human factors – service availability, stability, quality, waiting times and user data
- Technical factors – scalability, reliability, maintainability, effectiveness and network jamming
Due to unpredictable user load the QoS metric may vary to assess the performance. Here, we have given some common parameters that being used in developing Cloud Computing Topics.
- User (click rates, page views, etc.)
- Throughput (http, cables, network, etc.)
- Performance (response time, queries/sec, cpu, etc.)
- Availability (link breaks, uptime, service and host failure, etc.)
- Resource Utilization (disk, bandwidth, database tables, memory, etc.)
- Performance Indicators (no. of. users, revenue / hour and cost / transaction, etc.)

Related Pages
Cloud Computing Based Projects
Cloud Based Projects
Cloud Computing Final Year Projects
Fog Computing Projects
Project On Cloud Computing Security
Cloud Computing Mini Projects
Projects On Cloud Computing Security
Cloud Computing Project Ideas
Project On Cloud Computing Final Year
Cloud Computing Open Source Projects
Projects Related To Cloud Computing
Cloud Computing Projects For Final Year Cse
Cloud Computing Projects In Java
Cloud Computing Projects For Engineering Students
Final Year Engineering Projects For Cse On Cloud Computing
Key Services
- Literature Survey
- Research Proposal
- System Development
- AWS Integration
- Algorithm Writing
- Paper Writing
- Conference Paper
- Thesis Writing
- Dissertation Writing
- Assignments
Testimonials
I really appreciate your project development team. Since, your source codes are very easy to understand and execute it. Thank you!

You’re amazing and great working with you! I am totally satisfied with your paper writing. Keep up the best service for scholars!

Thank you so much for my project support and you guys are well done in project explanation. I get a clear vision about it.

You’ve been so helpful because my project is based on the AWS and HDFS integration. Before my commitment with you, I’ve a lot of fear, but you people rocked on my project.

Your project development is good and you made it so simple. Especially, codes are very new and running without any error.

You exactly did my project according to my demand. I tried many services, but I get the correct result from you. So surely I will keep working with you!


- Cloud Computing
Top 22 Cloud Computing Project Ideas in 2024 [Source Code]
Home Blog Cloud Computing Top 22 Cloud Computing Project Ideas in 2024 [Source Code]
The simplest and most effective way to gain proficiency in a domain is to focus on getting hands-on experience. When you work on live projects, you face real issues, gain familiarity with the actual scenarios, and gain expert-level understanding. So, when you plan and start your career in the cloud industry, you should work on a cloud computing project. It will help you understand the industry better. Moreover, you learn about the future scope of cloud computing. Based on this experience, you can choose the certifications that can boost your career and help you fetch excellent job opportunities. The idea behind working on cloud computing projects is to understand the field and plan the professional journey to get fruitful results.
In this article, we will discuss what is a cloud computing project, list of cloud computing project ideas based on skills, and a few examples for better understanding.
List of Cloud Computing Projects Ideas in 2024
Here is a list of curated cloud computing projects for all level skills, one should know in 2024:
- Cloud-enabled attendance system
- Online blood bank system
- Online cloud-enabled bookstore system
- Data redundancy removal system
- Detecting data leaks using SQL injection
- Cloud-based bus pass system
- Making a chatbot
- Secure text transfer
- Bug tracking functionality
| Attendance tracking | Online blood bank system | Bug tracking |
| Bus ticketing | Information Chatbot | File storage system using hybrid cryptography |
| Automation of university or college data | Online bookstore | Rural banking |
| Personal cloud | E-learning | Data leaks |
| Android Offloading |
Top Cloud Computing Projects [Based on Levels]
Learning cloud computing starts with getting hands-on experience. Check out the and get started with the cloud:
1. Cloud-enabled attendance system
We can use a cloud-enabled automatic attendance system to scan details. Also, all the scanned information can be directly synchronized and stored on the cloud in real-time. Detailed information like check-in time, check-out time, date, and total working hours, to name a few, can be stored and saved. Administrators must register new students/employees on the system and provide some personal information.

Source Code: Cloud-Enabled Attendance System
Advantages Of a Cloud-Enabled Attendance System:
- Data and Analytics: You can easily generate reports
- Flexibility: You can track attendance in a variety of ways
- Remote management: Cloud-based attendance systems make use of software that can be accessed from anywhere on any device that has Internet access.
Disadvantages Of a Cloud-Enabled Attendance System:
- Not effective in monitoring buddy punching: This software is ineffective at detecting buddy punching. There is a greater possibility of malpractice occurring here. However, if it is equipped with biometric technology, it can be properly monitored.
- Difficult to maintain and repair:nMaintaining and repairing software is difficult. Though it may be uncommon, once damaged, there will be costs associated with repairing it.
- Ineffective when there is no power supply: Without a power supply, the software is of no use. The entire system is powered by electricity. This is not the case with the traditional method of taking attendance.
2. Online blood bank system
Using cloud computing, we can create a central repository for numerous blood deposits, including blood details and depositor information. The blood details would include blood type, storage area, and storage date to help maintain and monitor the blood depositors. This cloud-based system would allow for greater transparency in determining the availability of the desired blood depositor. This system will also contain patient and contact information.

Source Code : Online Blood Bank System
Advantages of Online Blood Bank System
- Error probability is reduced to a minimum.
- Easy and effective information retrieval.
- The system shows the blood nearing expiry and those that have expired. Hence the unhealthy blood can easily be discarded.
3. Online cloud-enabled bookstore system
This system can function as an internet bookstore by utilizing SQL and C#. The books would be divided into sections to help users find their desired book without becoming overwhelmed by a database. Additionally, the bookstore records additional information such as a brief synopsis of the books. A notification system is added to help users stay up to date on their eagerly anticipated books and their availability.
Source Code: Online Cloud-Enabled Bookstore System
Advantages of Online Cloud-Enabled Book Store System
- Lower costs as users are not required to purchase a powerful computer or server to support the system's operation.
- Lower barriers to use. uses the service through the user's browser, the overall interface will be clearer and clearer, and the display effect of each functional module will be more intuitive and adapt to the user’s device
- Higher security as maintenance of the server is the responsibility of the system supplier.
4. Data redundancy removal system
This project is focused on accurately removing unnecessary and redundant data in a short amount of time. It accomplishes this by classifying the test data as redundant or false positive. Also, the cloud-enabled system validates the newly-added data to keep the database free from duplicity. If the data is not found in the database, new data gets appended.
Source Code: Data redundancy removal system
Advantages of Data Redundancy Removal System
- Alternative data backup method
- Better data security
- Faster data access and updates
- Improved reliability
5. Detecting data leaks using SQL injection
This cloud-enabled data leak detection system operates over the Internet and does not require any particular system configuration. The system aims to enhance security and provide measures against SQL injection hacking. By storing users’ information in AES 256 encryption form, it meets all the security needs. It injects SQL through a capability code and establishes a connection between the cloud server and the application itself; this system doubles the security against it.
Source Code: Data Leakage Detection
Advantages of This Project
- Get 100% database security and detect data leakers effortlessly.
- Distributors can easily identify counterfeit agents leaking their confidential data and take strict action against them.
6. Cloud-based bus pass system
It is a cloud-based adaptation of purchasing tickets over the Internet. This solves many common problems, such as misplaced, stolen, or incorrectly priced tickets. In addition, if the load on a typical bus booking website is too high, the website chokes and stops working. However, an additional load can be handled by provisioning new servers in the computing.
Source Code: Cloud-based Bus Pass System
Advantages of Cloud-based Bus Pass System
- Allows customers to check the availability of bus tickets before purchasing them
- Secure. Passengers must first register with the system to verify their identity. After they have been verified, the system allows them to book passes for any route online.
- Users can recharge using their credit/debit cards.
7. Making a chatbot
A chatbot is an AI-enabled software designed to interact with users when they visit a website. These bots are assigned to websites to streamline user interaction when they land on the website for the first time. The goal is to provide real-time and immediate responses to customer inquiries. To work on the chatbot application, you can use retrieval-based or generative-based models. If you want to use the chatbot on a commercial website, you should pre-define the input patterns.
Source Code: Chatbot
Advantages of Chatbots
- Seamless live communication
- Reduced people-to-people interactions
- Makes customer service available 24/7
8. Secure text transfer
Encryption is essential to protect confidential data safe against unauthorized access or misuse. This encryption safeguards confidential information in a key-password combination. This combination employs Diffie-Hellman key exchange, which applies to private and public encryption concepts.
This project can be used to exchange text messages while maintaining maximum security and speed. This system can be modified and repurposed to work for image exchange. SQL databases to store all information for exchange strengthen the entire system.
Source Code: Secure Text Transfer
Advantages of Secure Text Transfer System
- Content is encrypted to prevent access by hackers and unauthorized people.
- .NET framework simplifies the development process.
9. Bug tracking functionality
Using cloud computing, developers could identify the type and origin of bugs by simply logging into the application. The project will be divided into three parts: customer, administrator, and staff.
By entering a username and password, the customer will create an account. They can log in to the bug tracking application with their credentials and send a bug report with screenshots of the bugs they encountered. Staff can log in using their respective accounts to view bugs and determine whether they need to be fixed. And administrators can contact the user directly about the bugs they sent and quickly resolve them. Depending on the load of the reports, this can vary significantly.

Source Code: Bug Tracking System
Advantages of Bug Tracking System
- Deliver a high-quality product.
- Better communication and connectivity.
- Better customer service.
Enroll in KnowledgeHut training and courses to start your journey today. We provide study materials, cloud computing projects pdf, and the best resources to help you reach your cloud computing goals. Reach out to us to know our Cloud Computing course duration and fee in detail .
Cloud Computing Projects for Beginners
Are you new to the cloud and looking to explore your knowledge in cloud computing? There is no better way than trying some hands-on experience with a few basic projects. Here is a list of cloud computing projects for beginners that you must certainly give it a try.
1. Attendance tracking
This allows schools, colleges, institutions, and even offices to keep track of students' and employees' absences. Students and employees can mark their attendance by logging in, which is saved in the database and can later be checked by the institute's office.
Source Code: Attendance Tracking
2. Bus ticketing
Allow passengers to book bus tickets remotely. There will be no more hassles or concerns if the ticket is misplaced. Distributing tickets and passes to passengers can be done quickly and seamlessly. Also, passengers can use the bus ticketing app to check updates such as seat availability, schedules and timings, discounts, and much more.
Source Code: Bus Ticketing
3. Automation of university or college data
This project will assist you in creating a portal for a university or college. This portal allows them to register students, track their placements in various companies, and view their final results.
While it provides separate login portals for teachers and students, it also serves as a liaison between staff, students, and companies to deliver necessary information, collect feedback, declares results, etc.
Source Code: Automation of University
4. Personal cloud
You can create a personal cloud server with this project. Raspberry Pi and a Micro SD card will be required to build a private cloud. The hard drive will be the primary cloud storage in this project, and it will help you understand how a cloud server works.
Source Code: Personal Cloud
5. Android Offloading
Installing and offloading the processing requirements of an application is strenuous and time-consuming. The android offloading project aims to solve the problem by making it easy for applications to overload the compute parts explicitly. Using static analysis, this framework enhances an app's functionality. Users can choose a process and files to be encrypted and stored in the cloud. Visit AWS Cloud Practitioner Essentials Certification Training and learn AWS from scratch.
Source Code: Android Offloading
Intermediate Cloud Computing Projects with Source Code
Suppose you have a basic understanding of the cloud basics and you are comfortable working with computing, storage, and security. In that case, you must try a step forward than the entry-level projects. Here is the list of intermediate cloud computing projects from GitHub with source code. Let us check each in detail:
1. Online blood bank system
This cloud-based application serves as a central information database for the various blood deposits, including the donor's name and blood type information. The cloud can also store information such as blood type, storage data, blood type availability in a given area, etc. This facilitates quick access to blood in an emergency.
GitHub Source Code: Online Blood Bank System
2. Information Chatbot
Most companies have implemented chatbots on their websites to improve customer service and increase efficiency. In this project, you will create a chatbot in Python that will interact with users, answer their questions, and collect data that you will save in a cloud database.
GitHub Source Code: Information Chatbot
3. Online bookstore
This application can keep a catalog of books with the title, author, price, and even the ability to read them online. For the convenience of the customers, the books can be classified according to several criteria, such as author, genre, year of publication, and so on.
GitHub Source Code: Online Bookstore
4. E-learning
Online education platforms are nothing new to today's generation. These platforms have their advantages, resources, and time and cost flexibility and thus rank among the most popular learning mediums. Converting the project to a cloud project can drastically reduce costs. A learning space where study materials and relevant videos are kept for the learner's benefit. They are available for students to access and use as needed.
GitHub Source Code: E-learning
Looking to boost your career? Enroll in our ITIL certification course online ! Gain valuable skills and knowledge to excel in the ever-evolving IT industry. Don't miss out, sign up today!
Advanced Cloud Computing Project Ideas with Source Code
If you are a professional and have a sound understanding of cloud technologies, then you must opt for advanced cloud computing projects to elevate your skills to the next level. Here are a few hard-to-crack cloud computing projects with source code:
1. Bug tracking
Bug tracking is a project aimed at detecting and tracking the type and location of a bug on a website or app. Some common real-world applications designed using this concept include Backlog and Zoho bug tracker.
GitHub Source Code: Bug tracking
2. File storage system using hybrid cryptography
The project's goal is to secure the files using hybrid cryptography. Such applications are used in banking applications and systems to protect information and data sets.
You can encrypt the files with Blowfish because it is accurate and fast. Use symmetric algorithms for decryption. Even in remote servers, the hybrid technique can provide exceptional cloud security. With this project, you can add data security to your skill set, which is in high demand due to the increased frequency of security risks and attacks. Cryptography will be used to convert the data sets into unreadable forms.
GitHub Source Code: File storage system
3. Rural banking
This cloud project aims to create a cloud-based banking system for rural areas where banking facilities and amenities are inadequate to provide people with banking convenience.
GitHub Source Code: Rural banking
4. Data leaks
SQL injection refers to data leakage in the database as a common business problem. It is an excellent portal for anyone working or planning to work as an e-commerce platform. The primary aim of SQL injectors is to safeguard data and secure the privacy of the information from scammers. Developers employ standard encryption technology to create this SQL injection system
GitHub Source Code: Data leaks
Best Platforms to Work on Cloud Computing Project
Cloud offers different platforms on which you can run your projects. These platforms provide specific features based on which you can handle projects where you need to manage those particular aspects. Some of the cloud computing project platforms are:
- Microsoft Azure: Azure provides a wide range of services, making it the most accessible platform in the cloud environment. Any organization with any requirements can opt for Microsoft Azure as it will cater to all of them. It would be fair to say that Microsoft Azure is a dependable option for enterprises.
- Google Cloud: This platform provides new-age companies with a trustworthy, user-friendly, and protective cloud environment to the organizations. You get enough services in Google Cloud to cater to all the IaaS or PaaS requirements.
- IBM Cloud: The three models that IBM Cloud primarily focuses on are IaaS (infrastructure as a service), SaaS (software as a service), and PaaS (platform as a service). It is a cost-effective platform where you can make an adjustment to reduce the overall expense.
Importance of Cloud Computing Projects
Whether you a professional getting started with cloud computing or an experienced folk with experience in the cloud, these projects will help you streamline your learning process in many ways. Check out the importance of cloud computing projects and why it is a must for you:
- Cloud computing applications cover many domains, technologies, scales, and applications. Cloud computing mini projects or real-time cloud computing projects will provide adequate exposure and experience with cloud technologies.
- With the massive expansion of both technologies, virtualization and cloud computing projects are in high demand. Cloud computing has several applications in terms of programming languages and frameworks. Java cloud computing projects, Android cloud computing projects, PHP cloud computing projects, and other popular programming languages can be developed.
- Cloud computing projects for students have many applications in their academic careers. Cloud delivery and deployment models can be used to develop cloud computing projects for final-year engineering or cloud computing projects for MTech. Cloud computing projects are used in entertainment, education, healthcare, retail, banking, marketing, and other industrial and business domains.
Factors Affecting Cloud Computing
Cloud computing based on the pay-as-you-go model is affected by a number of factors. Let us discuss each in brief:
- Cost: The developers must keep in mind that it must be cost-effective and allow the company to achieve cost-saving benefits. Most businesses choose Cloud Computing because it is less expensive.
- Application in the future: Its potential applications should be designed so that they not only benefit the company in terms of current needs but are also adaptable enough to benefit the organization in the future as changes occur.
- Mobility: It is essential to design a Cloud Computing project to be easily moved between private and public clouds to check and access resources or data.
- Security: Security is the top priority when considering the entire aspect of data and resources. As a result, data security should be prioritized while a project is being developed.
- Increased bandwidth: When working in the cloud, it is important to consider increased bandwidth. Increased bandwidth significantly reduces transfer times, especially when handling big chunks of data.
I hope, we have covered the top cloud computing projects along with source code. Cloud is a high-demand domain with an increasing number of opportunities. Companies are switching to cloud environments because of the accessibility and data safety features. So, it would be fruitful to consider planning a career in this domain. If you can gain proficiency and prove your worth in the market, you can enjoy a monetarily sound and secure professional career. Start by getting all the information about this industry and find projects that can give you the right kind of experience. You can also join Cloud Computing certification courses that can train you in the right tools and techniques to help you establish a promising professional career in the cloud. If you plan everything strategically, your dream job is not far-fetched.
Frequently Asked Questions (FAQs)
These are the projects one must do to know how the notions of cloud computing can be applied in the real world.
Here are some cloud computing projects for beginners that you can build to learn more about the technology while also having fun:
A human-interfaced cloud-based student data chatbot.
Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
The father of cloud computing is American computer scientist J.C.R. Licklider.
The cost considerations in a cloud computing project include predicting the cost of cloud service. Furthermore, the cost of tools and the expense of individual resources also get included in cost consideration.
The security considerations in a cloud computing project include network security risks. Furthermore, the cloud relies on shared resources, so you should consider separation and segmentation.
The common challenges in implementing a cloud computing project include data security and privacy issues, multi-cloud environments, and high network dependencies.

Kingson Jebaraj
Kingson Jebaraj is a highly respected technology professional, recognized as both a Microsoft Most Valuable Professional (MVP) and an Alibaba Most Valuable Professional. With a wealth of experience in cloud computing, Kingson has collaborated with renowned companies like Microsoft, Reliance Telco, Novartis, Pacific Controls UAE, Alibaba Cloud, and G42 UAE. He specializes in architecting innovative solutions using emerging technologies, including cloud and edge computing, digital transformation, IoT, and programming languages like C, C++, Python, and NLP.
Avail your free 1:1 mentorship session.
Something went wrong
Upcoming Cloud Computing Batches & Dates
| Name | Date | Fee | Know more |
|---|
Cloud Computing Topics
Cloud app development & management.
To develop, deploy and manage cloud applications, an organization needs to write and configure apps in ways that meet performance and reliability goals without consuming an inordinate amount of costly cloud resources. These requirements demand that an IT team create -- and commit to -- a realistic cloud app development and management strategy. More about Cloud App Development & Management
Cloud Deployment & Architecture
Cloud service providers offer myriad options, from infrastructure to software to platforms. To make informed decisions about cloud deployment and architecture, organizations must know how to choose the resources that suit their workloads and budgets. That could mean adoption of a hybrid or even a multi-cloud architecture. More about Cloud Deployment & Architecture
Cloud Infrastructure
Cloud computing delivers numerous benefits, but only if an IT organization is prepared to manage a cloud environment. Proper cloud infrastructure design and management entails an understanding of automation, orchestration, monitoring, compliance, pricing, availability, and other key elements of cloud services. More about Cloud Infrastructure
Cloud Providers
When a business is ready to proceed with a cloud migration, it's prudent to consider which cloud provider platforms and tools meet business objectives and align with a staff’s skills. Hyperscale providers AWS, Azure and Google lead the market, offering ever-expanding portfolios of tools and services, but other providers deliver competitive offerings as well. More about Cloud Providers
StorMagic looks to court customers with smaller data centers for SMBs and the edge with SvHCI, a new VMware alternative with a ...
A main focus of the Dell Technologies World 2024 conference was AI and how it impacts infrastructure environments. Dell ...
In this Q&A, Dell's Matt Baker lays out how its AI Factory is designed for faster AI adoption, why there are so many chatbots and...
Companies need to prepare for the risks and responsibilities of using open source software, according to Chainguard's Dan Lorenc....
Grafana and Kibana are two strong contenders for on-premises data visualization tools. Compare the two and pick which tool is ...
Open source software maintenance is broken. Tobie Langel has a big picture idea for how to fix it, which he shares in this ...
Many organizations struggle to manage their vast collection of AWS accounts, but Control Tower can help. The service automates ...
There are several important variables within the Amazon EKS pricing model. Dig into the numbers to ensure you deploy the service ...
AWS users face a choice when deploying Kubernetes: run it themselves on EC2 or let Amazon do the heavy lifting with EKS. See ...
This year’s VMware Explore conference ran from Aug. 21 to 24. Read the latest news and announcements about and from the event, ...
TechTarget hosts its Best of VMware Explore Awards to recognize outstanding products that help organizations create ...
Submit your entry for the Best of VMware Explore 2023 Awards for a chance to win.

- NIH Grants & Funding
- Blog Policies
NIH Extramural Nexus
Making Advanced Research Computing More Accessible With NIH Cloud Lab
Guest post by Sean Mooney, PhD, recently appointed Director of the NIH Center for Information Technology , to announce the launch of NIH Cloud Lab for all NIH-affiliated* researchers. Learn more or request an account here .

As I step into my role as Director of the NIH Center for Information Technology (CIT), I am continually amazed by the contributions our NIH community makes to the digital ecosystem underpinning biomedical research. A key focus of mine is the advancement of collaborative, data-driven research in “the cloud”, and my colleagues and I are determined to make access to and expertise in cloud computing more widely available across the NIH research community.
Researchers today often face barriers when adopting and integrating cloud-based technologies. Common concerns range from complex procurement processes and unpredictable costs to the availability of relevant training and assurances on data security. As a response, the NIH Center for Information Technology has partnered with NIH’s Office of Data Science Strategy to offer two programs: the NIH STRIDES Initiative and NIH Cloud Lab.
NIH STRIDES streamlines the procurement of commercial cloud services from our partners: Amazon Web Services, Google Cloud, and Microsoft Azure. Participating NIH-funded researchers benefit from exclusive features, favorable pricing, dedicated support, and discounted cloud training . As of May 2024, more than 2,300 research programs have enrolled in STRIDES, storing over 300 petabytes of data!
For those interested in using cloud technology without making an initial long-term commitment, NIH Cloud Lab enables researchers to try cloud capabilities at no cost in a secure, NIH-approved environment. Participants receive 90 days of access to Amazon Web Services, Google Cloud, or Microsoft Azure along with $500 of no-cost cloud credits.
To help accelerate researchers’ cloud fluency, we offer an extensive repository of interactive tutorials that demonstrate how to run realistic bioinformatic, data science, and AI workflows. Tutorials address a variety of scientific topics, including generative AI, variant calling, single-cell RNA sequencing, proteomics, medical imaging, and more! The best part is these tutorials are also public and available in GitHub to anyone with a self-funded cloud account.
Cloud Lab’s breadth of technical features and support from bioinformatic and cloud experts make it a good fit for individuals with all levels of cloud knowledge, from cloud beginners to experienced researchers. Regardless of a participant’s level of experience, Cloud Lab’s integration with the Researcher Auth Services (RAS) solution minimizes time spent setting up an account by enabling most researchers to log in with their home institution username and password. This helps participants get up and running as quickly as possible.
One of the most significant benefits of this simplified onboarding process has been the democratization of access to computational and data science resources. Since 2023, Cloud Lab has seen participation from 368 National Institute of General Medical Sciences (NIGMS) grantees from 102 research institutions in the Institutional Development Program , which builds research capacity in states that have historically received low levels of NIH funding. Our team also integrated twelve interactive bioinformatics tutorials developed by NIGMS grantees into the Cloud Lab experience!
NIH-affiliated* researchers interested in Cloud Lab are welcome to sign up at any time by visiting our Cloud Lab homepage , and academic institutions looking to supplement their coursework or workshops with Cloud Lab can contact our team at [email protected] . Stay tuned to the CIT homepage for exciting updates and enhancements to our offerings. We’re looking forward to helping you on your cloud adoption journey!
*NIH-affiliated includes recipients of NIH funding and researchers at institutions eligible for NIH funding who may not have an active award.
RELATED NEWS
One comment.
I’m interested in using AI for clinical data analysis. Can you assist? Thanks.
Before submitting your comment, please review our blog comment policies.
Your email address will not be published. Required fields are marked *
More From Forbes
Sky-high innovation: unveiling the future of cloud computing in industry 4.0.
- Share to Facebook
- Share to Twitter
- Share to Linkedin
Nicola Sfondrini - Partner Digital and Cloud Strategy at PWC .
Industry 4.0, or the Fourth Industrial Revolution, introduces automation and data exchange in manufacturing technologies. This includes advancements such as smart integrated systems, the Internet of Things (IoT) and cloud computing.
These technologies allow for the interconnection of smart devices in industrial settings, supporting two-way, real-time communication in smart production environments. By connecting people, devices and industrial systems, cloud computing promotes data exchange and leverages advanced technologies to strengthen the ability to design, monitor and manage innovative, highly adaptable, automated and self-optimizing production processes.
Given the large amount of data involved in real-time automation and control, cloud computing is a key component enabling the operational economy. Cloud computing offers on-demand network access to a shared pool of configurable computing resources, which can be rapidly deployed and released, providing flexibility and scalability in the management of such huge datasets, thus allowing companies to extract knowledge from raw data and respond more quickly and effectively to market requirements.
Emerging Trends In Cloud Computing
This discussion will center on three pivotal trends that are currently reshaping the industrial landscape in the digital age, as part of the evolving cloud computing paradigm.
Best High-Yield Savings Accounts Of 2024
Best 5% interest savings accounts of 2024.
• Edge Computing: Designed to process data near or at its point of generation, this approach can help to cut latency and reduce bandwidth requirements. For example, automotive factory assembly lines can use edge computing to conduct and process activities in real time on the plant floor without having to send large volumes of data to distant data centers. This can be critical for scenarios requiring real-time observability, such as predictive maintenance and automated quality control that call for instantaneous adjustments or actions.
• Integration With Artificial Intelligence And Machine Learning: Traditional cloud environments can be integrated with artificial intelligence (AI) and machine learning (ML) algorithms, so that they employ next-gen computational power to, for example, carry out sophisticated automated measurements for their overall operation.
AI algorithms not only track system behaviors and system failures but also use huge volumes of cloud data to sift for possible optimization, thus minimizing costs and carrying out proactive prevention. ML, on the other hand, learns from new data to become more efficient, possibly changing the course of process optimization and innovation.
• Quantum Cloud Computing: Still in its infancy, I believe quantum cloud computing will allow for unimaginable speed-ups to complex operating setups with large numbers of variables, surpassing what can be achieved using classical computing. For example, it would allow us to better understand the increasingly exotic states of particles, such as the electron, or allow us to solve complex logistical problems.
The beginnings of this technology are starting to emerge, with various new companies working on extending processing capabilities via the cloud (such processing is sometimes now performed in quantum hardware, kept cold enough to maintain its subatomic properties until the algorithmic tasks are completed). This technology might, in the future, enable the simulation of material properties at millions of scales, radically changing the nature of manufacturing.
Case Studies: Success Stories Of Cloud Integration
Germany is out in front of Industry 4.0 technologies, with many examples of cloud integration.
• Bosch Rexroth ActiveCockpit: This interactive communication platform represents good real-time data processing in a manufacturing setting. The ActiveCockpit collects, processes and displays production shop floor data in real time. With this system, production is operationalized more effectively.
All the critical manufacturing control variables are viewable at the manufacturing facility in an easy-to-understand manner to facilitate informed decision-making. It improves process efficiency, quickly diagnoses and remedies problems with production inefficiencies and maintains efficient machine operation. Cloud connectivity prevents downtime and conserves labor hours through predictive maintenance.
• Siemens Insights Hub: Siemens has created Insights Hub (previously MindSphere), an open cloud-based IoT operating system that connects analog infrastructure to the digital world via high-speed sensor technology. Insights Hub is particularly good at aggregating, processing, analyzing, visualizing and managing data.
Such IoT devices generate massive amounts of complex data from humble infrastructure that is hidden underneath, which the Hub can use to refine its own processes and develop new services (for example, in predictive maintenance, energy data management and so on). This system underpins Siemens' state-of-the-art Amberg plant in Germany, which is a leading automated and digitized factory globally.
Future Projections And Challenges
Cloud computing is set to lead the way to Industry 4.0. Innovations such as the distributed cloud, which merges cloud and telecommunications approaches, and the multi-access edge computing (MEC) market, which delivers services closer to the data source, will further enhance the transformative potential of cloud computing. As these innovations continue to emerge, the impact of cloud computing will only increase.
Yet, these new technologies bring new vulnerabilities, too, especially in terms of cybersecurity and data privacy. As manufacturing becomes increasingly digitized (via virtualized cloud-based platforms), the exposure to both cyberattacks and data breaches increases. Cloud-based technologies designed to strengthen critical infrastructure must also comply with increasingly stringent data protection regulation, which varies across legal jurisdictions.
The existence of these hurdles makes it easier to understand why cloud computing takes center stage in the digitalization process of Industry 4.0. As I said earlier, if any technology had the unique capacity to increase connectivity levels, process data in a smart way and analyze processes in an efficient and effective manner, that technology would be the cloud.
For these reasons and more, the adoption of cloud technology will bring numerous upgrades to the manufacturing industry over the next few years, opening up new opportunities for business models and value creation.
Forbes Technology Council is an invitation-only community for world-class CIOs, CTOs and technology executives. Do I qualify?

- Editorial Standards
- Reprints & Permissions
Research trends in deep learning and machine learning for cloud computing security
- Open access
- Published: 02 May 2024
- Volume 57 , article number 132 , ( 2024 )
Cite this article
You have full access to this open access article

- Yehia Ibrahim Alzoubi 1 ,
- Alok Mishra 2 &
- Ahmet Ercan Topcu 3
1725 Accesses
Explore all metrics
Deep learning and machine learning show effectiveness in identifying and addressing cloud security threats. Despite the large number of articles published in this field, there remains a dearth of comprehensive reviews that synthesize the techniques, trends, and challenges of using deep learning and machine learning for cloud computing security. Accordingly, this paper aims to provide the most updated statistics on the development and research in cloud computing security utilizing deep learning and machine learning. Up to the middle of December 2023, 4051 publications were identified after we searched the Scopus database. This paper highlights key trend solutions for cloud computing security utilizing machine learning and deep learning, such as anomaly detection, security automation, and emerging technology's role. However, challenges such as data privacy, scalability, and explainability, among others, are also identified as challenges of using machine learning and deep learning for cloud security. The findings of this paper reveal that deep learning and machine learning for cloud computing security are emerging research areas. Future research directions may include addressing these challenges when utilizing machine learning and deep learning for cloud security. Additionally, exploring the development of algorithms and techniques that comply with relevant laws and regulations is essential for effective implementation in this domain.
Similar content being viewed by others

Machine Learning: Algorithms, Real-World Applications and Research Directions

Machine learning and deep learning

Big data in healthcare: management, analysis and future prospects
Avoid common mistakes on your manuscript.
1 Introduction
The SANS Institute found that 84% of effective cyberattacks exploit human behaviors. The SANS Institute is a collaborative research and educational institution that specializes in cybersecurity education and training (SANS 2024 ). SANS stands for "SysAdmin, Audit, Network, Security," reflecting its initial emphasis on system administrators and network security professionals. Additionally, a Ponemon Institute study found that the average cost of a data leak brought on by network failures is $4.1 million. The Ponemon Institute is a research group that focuses on information security policy, privacy, and data protection. They conduct independent research, surveys, and studies on topics such as data breaches, privacy practices, cybersecurity trends, and risk management (PonemonInstitute. 2024 ). Cybersecurity Ventures projects that the yearly cybercrime cost will exceed USD 7 trillion globally in 2022 and $10.5 trillion by 2025 (Morgan 2022 ). Cybersecurity Ventures is a leading researcher and publisher covering the global cybersecurity market. They provide industry insights, cybersecurity statistics, market forecasts, and trends through their reports, newsletters, and articles (CybercrimeMagazine 2024 ). Furthermore, research by the Information Systems Security Association found that using various data sources could improve the precision of vulnerability management identification by up to 50% (Oltsik 2023 ). The Information Systems Security Association is a nonprofit organization that provides educational forums, publications, and networking opportunities to cybersecurity professionals (ISSA 2024 ). The amount of sensitive information is anticipated to increase by 50% annually, according to a report by the International Association of Computer Science and Information Technology (IACSIT). Also, according to the same report, anomaly detection can identify up to 85% of breaches. Unfortunately, the same report claimed that adversarial cyberattacks can deceive Deep Learning (DL) models up to 90% of the time. The IACSIT is a professional organization that brings together researchers, scholars, and practitioners in the fields of computer science and information technology (IACSIT 2024 ). On the other hand, using security intelligence may decrease the time necessary to find a security breach by up to 50%, according to research by the SANS Institute. According to the same research, the SANS Institute found that finding a security event takes an average of 200 days (Spitzner 2022 ). These statistics provide a clear picture of the scope of the security issue and the role that Machine Learning (ML) and DL can play in addressing it in the future.
Contemporary malware presents a significant challenge for traditional detection systems due to its sophisticated and deceptive nature (Rao and Jain 2024 ). In cloud environments, antivirus programs often struggle to detect complex malware, such as encrypted or metamorphic variants, leading to an increased risk of undetected attacks (Abbas and Myeong 2023 ). Despite their widespread use, traditional security methods like firewalls and Intrusion Detection Systems (IDS) have limitations in cloud settings. They cannot effectively identify novel threats, zero-day attacks, or malicious mining programs, nor can they handle large volumes of data (Belal and Sundaram 2022 ). Consequently, there is a pressing need to ensure high detection rates with accuracy to reduce false positives and bolster security measures. One promising approach to addressing these challenges is adopting ML-based and DL-based IDS (Amiri et al. 2024 ). Powerful methods like ML and DL can be used to increase the security of cloud computing systems (Heidari et al. 2023 ). They have been demonstrated to be efficient in recognizing and preventing security threats and can be utilized for tasks including intrusion detection, anomaly detection, and classification. In order to find patterns and anomalies, categorize data, and generate predictions, these techniques may analyze and learn from massive amounts of data. This can aid in spotting malicious activity, detecting intrusions, and identifying other security concerns.
However, while several literature reviews have explored ML and DL role in cloud computing security, none of these studies included bibliographic analyses. Additionally, most previous review papers on ML and DL usage for cloud computing security have focused either on different ML and DL techniques or algorithms, or on specific techniques such as Convolutional Neural Networks (CNN), or types of attacks like denial-of-service attacks, as elaborated in Sect. 2.4 . Moreover, the field of ML and DL for cloud computing security is continuously evolving. Thus, this paper aims to fill this gap by offering a comprehensive review of the trends and challenges associated with using ML and DL for cloud computing security. This investigation is crucial for understanding such a dynamic field. Identifying trends, patterns, and connections between various research projects can also aid in synthesizing existing information. It can help identify potential biases and limitations in earlier research, thereby preventing the repetition of these errors and ensuring the study's thoroughness and validity (Herrera-Franco et al. 2020 ). Furthermore, conducting a bibliographic analysis helps in understanding previous research, identifying addressed problems, and pinpointing gaps in the literature that require further investigation.
The paper contributes to the field of cloud computing security by utilizing DL and ML in several ways. First, the paper addresses the need of comprehensive reviews by offering updated statistics on the development and research landscape of cloud computing security using DL and ML techniques. We conducted a bibliographical analysis before analyzing the field’s recent and upcoming developments. Second, the paper highlights trending ML and DL solutions to address cloud security issues, including anomaly detection, security automation, cloud-native security, image-based detection, network traffic analysis, and the role of emerging technologies, providing insights into current approaches for addressing cloud security threats. Third, the paper identifies challenges including data privacy, scalability, explainability, generalizability, and label bias associated with using ML and DL for cloud security, bringing attention to areas that require further exploration and refinement. Fourth, the paper identifies several new algorithms and approaches being developed. Thus, both ML and DL are continuously growing in the context of cloud computing security. Finally, based on the findings, the paper draws future research directions focused on addressing challenges and developing algorithms and techniques that comply with relevant regulations and laws, emphasizing the importance of advancing the field in a responsible and compliant manner.
The remainder of this paper is structured as follows: The background of ML, DL, and cloud computing is covered in Section 2 . The research methodology employed in this study is explained in Section 3 . The bibliographical analysis of the relevant literature is discussed in Section 4 . The current and future trends of deploying ML and DL for cloud computing security are discussed in Section 5 . Section 6 concludes this paper. The definitions of the abbreviations used in this study are summarized in Table 1 .
2 Background and related work
2.1 cloud computing.
Cloud computing is an information services delivery model that makes resources available to users through the Internet as needed and on a pay-as-you-go basis (Alzoubi et al. 2022a ). It makes it possible for users to acquire and use pooled computational resources, like storage, servers, and applications, without worrying about maintaining and managing those resources’ infrastructure (Alzoubi et al. 2021 ). In cloud computing, there are three primary services: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) (Abdel-Basset et al. 2018 ). While SaaS offers consumers subscription-based access to software services like customer relationship management and email, PaaS provides a platform for users to design, execute, and administer applications. On the other hand, IaaS gives consumers access to hardware-related resources like CPUs, storage, and memory.
In addition, other deployment options are available with cloud computing, including private, public, and hybrid clouds. Third-party suppliers run public clouds, accessible to everyone, whereas a single enterprise runs private clouds. Enterprises may exploit the advantages of both private and public clouds by combining them in hybrid clouds (Abdel-Basset et al. 2018 ). Cloud computing services are offered by several major companies, such as (Gartner. 2023 ):
Amazon Web Services: Amazon Web Services owned 32% of the cloud computing industry in 2021, making it the leading provider. It has a worldwide network of data centers and offers several services, including SaaS, PaaS, and IaaS.
Microsoft Azure: With a 20% market share, Azure is the second-largest cloud computing service. It provides IaaS, PaaS, and SaaS services comparable to those of AWS and has a worldwide network of data centers.
Google Cloud Platform: With a 7.7% share of the market, Google Cloud Platform is the third-largest cloud computing service. It offers a wide variety of services, such as SaaS, PaaS, and IaaS, and has a worldwide network of data centers.
Alibaba Cloud: With a 4.6% share of the market, Alibaba Cloud is the fourth-largest provider of cloud computing services. It is a division of Alibaba Group that provides several services, including SaaS, PaaS, and IaaS, and a worldwide network of data centers. Still, it is mainly concentrated on the Asian market.
2.2 Machine learning and deep learning
With ML, a type of artificial intelligence, machines may automatically pick up new skills and improve over time (Mishra and Tyagi 2022 ). It entails employing algorithms to examine data, gain knowledge, and determine a forecast or course of action without involving humans (Lin et al. 2022 ). The size of the worldwide ML market is anticipated to increase from $8.41 billion in 2020 to $39.09 billion by 2025 at a CAGR of 36.5% throughout the forecast period (MarketsandMarkets. 2023 ). The three main types of ML are supervised learning, reinforcement learning, and unsupervised learning (Belal and Sundaram 2022 ; Gupta et al. 2017 ; Topcu et al. 2023 ).
Supervised learning: Voice recognition, picture categorization, and Natural Language Processing (NLP) are examples of tasks that require supervised learning. Labeled data is used in supervised learning to train a model to forecast outcomes based on fresh data.
Unsupervised learning: It is employed for activities like grouping and anomaly detection. It entails discovering structures or trends in unlabeled data without a clear prediction objective.
Reinforcement learning: It is employed in activities like robotics and gaming. It entails preparing an agent to choose between incentives and punishments when making decisions.
DL is a subclass of ML that models and resolves complex issues, including decision-making, NLP, and voice and picture recognition, using artificial neural networks (Amiri et al. 2024 ; Heidari et al. 2022 ). These neural networks are composed of multiple layers, so they are called "deep" learning. The DL market size is anticipated to increase from $1.81 billion in 2020 to $10.95 billion by 2025 at a CAGR of 44.1% throughout the forecast period (MarketsandMarkets. 2023 ). Rather than relying on human feature extraction, DL algorithms can enhance the performance of ML models by automatically extracting features from raw data (Aldallal 1916 ). Since the data is complicated and unorganized, it is beneficial for voice and picture detection tasks.
2.3 Machine learning and deep learning for cloud computing security
As effective techniques for improving cloud computing security, ML and DL have come to light. Traditional methods frequently fail to handle the dynamic and complex nature of cyber threats in cloud security (Ge et al. 2021 ). In cloud environments, ML and its subset, DL, provide flexible and intelligent solutions to strengthen security and reduce risks. Massive volumes of data created in the cloud may be analyzed by ML algorithms, which can then find patterns and abnormalities that could point to security lapses. Proactive threat identification is made possible by ML models that utilize previous data to learn how to differentiate between harmful and regular activity (Gupta et al. 2017 ). This is furthered by DL, which uses neural network architecture to automatically extract complex aspects and representations from data, enabling more precise and nuanced threat detection.
One noteworthy usage is intrusion detection, where ML and DL algorithms are used to continually watch user behavior and network activity (Kasongo 2023 ). These systems offer real-time protection against possible attacks by triggering warnings or automatic replies in the event that abnormalities or suspicious patterns are discovered (Ma et al. 2023 ). Furthermore, cloud security systems may foresee and proactively handle new vulnerabilities using ML and DL approaches in predictive analysis (Kumar et al. 2022a ). ML and DL technologies are increasingly essential in strengthening the resilience of cloud infrastructure against various cyber threats as cloud computing advances. The following explains the critical ML and DL milestones for cloud security (Belal and Sundaram 2022 ; Yıldız 2024 ; Dasgupta et al. 2022 ; Saran et al. 2022 ).
The cloud computing sector grew significantly after 2010, coinciding with the understanding that more advanced security measures were required. Security systems for virus analysis, anomaly detection, and user behavior analytics started to use ML algorithms. The goal was to improve the detection and reaction to threats capabilities by utilizing ML.
The introduction of DL, especially with the rise in popularity of neural networks and deep neural architectures, was a significant turning point in 2012. DL methods, such as Recurrent Neural Networks (RNN) and Convolutional Neural Networks (CNNs), have a remarkable ability to process intricate data structures.
Concerning cloud security, DL has made significant progress in pattern and picture recognition, increasing threat detection accuracy. After 2015, as cloud environments advanced in sophistication, so did cyber threats. ML and DL played key roles when creating IDS for cloud-based infrastructures. These systems used ML algorithms to continuously monitor user activity and network traffic to spot behavioral anomalies that could be signs of impending security problems.
Predictive analytics has received more attention in cloud security since 2019. These days, historical data analysis, trend identification, and possible security risk prediction are all done using ML and DL models. Moreover, real-time reactions to security issues are made possible by integrating automation with ML and DL, which shortens the time between detection and mitigation. One of the innovations is the creation of adversarial ML, which improves resistance to complex assaults. There are still issues to be resolved, such as the requirement for interpretability in intricate DL models and handling moral questions related to security and artificial intelligence.
2.4 Related survey literature
To contextualize our study, we surveyed pertinent review articles regarding the utilization of ML and DL in cloud security. We specifically focused on papers published between 2022 and 2024, examining titles and abstracts in the Scopus database to select comprehensive literature reviews. Papers exclusively addressing singular techniques (e.g., (Ravinder and Kulkarni 2023 ) and (Pandey et al. 2023 )) or specific attacks (e.g., (Nair et al. 2023 ) and (Gupta et al. 2022 )) were excluded. It was essential to focus only on articles discussing ML and DL techniques for cloud security purposes, in general. Table 2 outlines the key insights gleaned from these reviews, revealing three overarching themes: the application, challenges, and emerging trends of ML and DL in cloud security.
Application of ML and DL for cloud computing security: The literature provides insights into the application of ML and DL techniques for enhancing cybersecurity across various domains. In (Abdullahi et al. 2022 ), the authors categorized AI techniques for IoT cybersecurity, highlighting SVMs and RF as popular choices. The authors in Belal and Sundaram ( 2022 ) emphasized SVM, RF, and KNN for cloud security. The authors in Hernandez-Jaimes et al. ( 2023 ) analyzed AI methods for securing medical IoT devices, and the authors in Roy et al. ( 2023 ) evaluated ML methods for edge device security, focusing on Extreme Gradient Boosting and RF. Similarly, the authors of Bhuvaneshwari and Kaythry ( 2023 ) highlighted DL techniques like RNN and CNN for cybersecurity. Furthermore, the authors in Salem and Al-Saedi ( 2023 ) discussed DL and data mining in cloud security, emphasizing CNN and SVM.
Challenges and trade-offs of using ML and DL for cloud computing security: In (Kornaros 2022 ), the authors examined ML and DL techniques for IoT device security, addressing integration trade-offs. The authors of Aldhaheri et al. ( 2023 ) discussed DL's advanced structure and trade-offs, proposing edge computing and transfer learning as solutions. Moreover, the authors of Yi et al. ( 2023 ) examined DL's role in network threat detection, categorizing models like Self-Autoencoder and RNN. Additionally, the authors of Vinolia et al. 2023 assessed DL-based unsupervised techniques for intrusion detection.
Emerging trends and future directions for using ML and DL for cloud computing security: The authors of Sarker et al. ( 2023 ) explored ML and DL methodologies for IoT security, covering various classification and clustering methods. Also, authors in Dasgupta et al. ( 2022 ) identified DL methods like RNN for network traffic analysis. Moreover, the authors of Balobaid et al. ( 2024 ) discussed ML and DL techniques for IoT-based cloud computing security, highlighting the importance of updated security measures and methods like KNN and Deep Stack Encoder Neural Networks.
Finally, the authors in Mishra ( 2024 ) discussed several uses of ML and DL that were documented. This included anomaly detection, threat intelligence, analytics of user and entity behavior, network security, data security, endpoint security, identity and access management, incident response, security information and event management, continuous monitoring, and adaptation. This study is still under review but was added as a preprint to the SSRN database. Our paper offers several advancements compared to recent literature in the field. It conducts a comprehensive bibliometric analysis of all papers on ML and DL for cloud security within the Scopus database. Additionally, it delineates the latest trends in this domain, covering topics such as anomaly detection, security automation, cloud-native security, emerging technology's role, insider threats, CASB, image-based malware detection, and network traffic analysis. These trends are examined individually for both ML and DL techniques. Furthermore, the paper identifies the most prevalent ML and DL methods utilized in cloud security and addresses the associated challenges. Finally, it discusses the practical implications of these findings for industry applications.
3 Research method
A systematic review is highly relevant for investigations since it delves into the topic of study and assists the investigator in creating research questions that will expand their knowledge base. In a similar vein, bibliometric investigation features a strict and clear methodology that enables the selection and assessment of the literature using a transparent, repeatable process that allows understanding of a field of study (Herrera-Franco et al. 2020 ).
3.1 Study design
The bibliometric technique was used as our primary research method, with current and upcoming trends as secondary. The research covered the publications until the middle of December 2023. The study's approach was predicated on the notion that employing DL and ML for cloud security has garnered considerable scientific interest. The bibliometric investigation, centered on analyzing the literature of published articles assembled in a database, is considered a branch of science since it displays a thorough map of the knowledge structure and its assessment. This type of analysis enables a detailed investigation of the development of the phenomenon over time in a specific academic topic (Khudzari et al. 2018 ).
The sources or repositories' identities must be accurate and trustworthy. The Scopus database was selected primarily for its high-quality standards, broad coverage, simplicity of fetching data, and the most comprehensive library of computer and engineering journals (Herrera-Franco et al. 2020 ). Moreover, the Scopus database enables bibliography analysis through operational features like document type, source name, author names and affiliations, publication year, h-index performance measures for documents, and the number of citations, among others (Sweileh 2018 ).
3.2 Search strategy
The choice of search terms is crucial in the bibliometric analysis since they significantly affect the results. The search technique was based on title or abstract searches to reduce false-positive findings. Search terms were collected from recently reported ML and DL literature. The search approach was not language- or document-type-specific (i.e., article, conference proceedings, or book chapter) (Sweileh 2018 ). To search for the Scopus document, we employed the following Boolean operators: “machine learning” OR “deep learning” AND “cloud” OR “fog” OR “edge” AND “security” AND “attack” OR “protection” OR “detection” OR “response” OR “prediction.” By including these keywords, the search is tailored to capture publications that discuss the utilization of ML and DL in cloud security, as well as related topics such as anomaly detection, security automation, and emerging technologies. This focused approach ensures that the retrieved publications are more likely to provide valuable insights into the trends, solutions, and challenges associated with ML and DL in cloud computing security, which is the primary focus of the study. Additionally, using specific keywords helps narrow down the search results and improves the relevance of the retrieved publications to the research topic.
The acquired data were checked for accuracy and looked at for their relevance to the study question. As a result, 2820 (i.e., 2438 ML and 1613 DL) publications were identified. We were able to count the number of ML and DL papers in cloud security by using built-in Scopus search features like "year," "author name," "subject area," and other fields (Sweileh 2018 ). The findings of this paper focused only on the highest 15 publications regarding the bibliographic characteristics (i.e., highest citations, affiliations, and so on). 15 was randomly chosen as the criterion to list the findings; this option has been employed in other bibliometric studies (Sweileh 2018 ).
We utilized the advanced search interface provided by Scopus, enabling us to specify search terms, publication types, date ranges, and other filters. Inclusion criteria likely specified that publications must pertain to cloud computing security and involve ML or DL techniques. Additionally, we restricted our selection to peer-reviewed articles, book sections, or conference papers, and only articles written in English were considered during the analysis stage due to the authors' proficiency in English. Publications needing clear relevance to cloud computing, ML, DL, and security were excluded.
Following the retrieval of the initial set of search results, manual screening processes were employed to refine the selection further. This involved reviewing the publications’ titles, abstracts, and keywords to assess their relevance to the topic of interest. Publications failing to meet the inclusion criteria were excluded at this stage. Subsequently, data extraction was carried out to collect pertinent information from each publication, including publication title, authors, publication year, journal/conference, abstract, and keywords. This data was compiled and analyzed to generate the statistics presented in the paper.
3.3 Thematic analysis
We employed thematic analysis methodologies (Alzoubi and Gill 2021 ) to distill the ML and DL trends for cloud computing security and delineate associated challenges, as expounded in Sect. 5 . Thematic analysis served as the methodological approach for dissecting the gathered data, aiming to unearth commonalities and significant insights prevalent across the selected articles. Following the structured guidelines delineated by Miles and Huberman ( 1994 ), the analysis unfolded in four distinct phases: data collection, data reduction, data display, and conclusion drawing. During the data reduction phase, the collected information underwent meticulous preparation and familiarization to render it amenable for analysis (Miles and Huberman 1994 ). Preliminary coding, crucial for transforming raw data into a manageable format, employed keywords extracted from Scopus search results as a foundational framework (Alzoubi and Gill 2021 ). Subsequently, major themes emerged as the data were scrutinized to unveil pertinent issues, concepts, and challenges pertaining to the objectives of the study, encompassing trends, techniques, and hurdles encountered in the realms of ML and DL within cloud computing security. Coded data were systematically grouped into cohesive categories, fostering thematic exploration and understanding.
Data display, a pivotal facet of the analytical process, involves organizing and synthesizing information into a more coherent and accessible format, facilitating comprehension, and facilitating the transition to subsequent analysis stages (Alzoubi and Gill 2021 ). This stage was recurrent throughout the analysis, aligning with the progress made and laying the groundwork for subsequent analytical endeavors. Finally, the synthesis of tables and charts marked the culmination of the analysis, synthesizing the myriad data points into a cohesive and meaningful narrative that encapsulated the identified ML and DL trends within cloud computing security (Miles and Huberman 1994 ). This concluding phase unfolded concurrently with other analytical stages, underscoring its integral role in shaping the coherent portrayal of the study's focal points.
4 Bibliographic findings
The vast majority of the documents identified were written in English, with 2420 (99.2%) documents on ML and 1586 (98.3%) documents on DL. A small number of documents were written in Chinese, with 27 (1%) on ML and 27 (1.7%) on DL, while only one ML document was written in Turkish and one in Portuguese. Also, only one DL document was written in Turkish, and the other one was written in Korean. As shown in Fig. 1 , over the past five or six years, there has been significant growth in both the volume of ML and DL articles. While ML articles first appeared in 2006, DL literature began in 2014. By the end of 2023, we anticipate that over 600 articles will have been published if the current trend continues. As shown in Table 3 , the documents were published in nine different categories: articles (1715, or 42.3%), conferences (1515, or 37.4%), review conferences (503, or 12.4%), book chapters (145, or 3.5%), reviews articles (79, or 2.8%), and books (39, or 1.0%).

Published document number until middle of December 2023
4.1 Top 15 search keywords used
Figure 2 depicts the visualization of the 15 most commonly used keywords. The term "machine learning" was the most frequently utilized keyword in ML, appearing 1212 times, while "computer crime" was the least frequently used, with only 247 appearances. The ML keywords were classified into four broad categories: learning, detection, security, and computing. The first category, learning, included keywords such as "machine learning," "machine-learning," "learning systems," "learning algorithms", “artificial intelligence”, and "deep learning," which had a combined total of 3424 occurrences. The second category, computing, included "edge computing”, "Internet of things”, "cloud-computing", and "cloud computing", with a total of 1825 occurrences. The third category, security, consisted of "network security," "computer crime," and "security," with a total of 1454 occurrences. The fourth and final category, detection, comprised "intrusion detection" and "intrusion detection systems" with 744 occurrences.

Top 15 used keywords
On the other hand, in the field of DL, the most frequently used keyword was "deep learning" with 1170 appearances, while "cybersecurity" was the least frequently used with only 140 appearances. Like ML, DL keywords could also be broadly classified into four categories: learning, detection, security, and computing. The learning category included keywords such as "deep learning," "learning systems," "learning algorithms," "machine learning", and "deep neural networks", with a combined total of 2079 occurrences. The second category, the computing category, included "edge computing”, "Internet of things”, "cloud computing", and "cloud-computing", with a total of 1082 occurrences. The third category, security, consisted of "network security", "computer crime", “cybersecurity”, and "security", with a total of 1033 occurrences. Finally, the detection was comprised of "intrusion detection" and "intrusion detection systems" with a total of 437 occurrences.
4.2 Top 15 research domains
Table 4 summarizes the top 15 research domains of the published article identified in the study. Out of the total 2438 documents, 2137 (87.6%) of the ML documents were categorized under computer science. In contrast, only 11 (0.56%) belonged to medicine, and biological sciences and other fields, including neuroscience, health, multidisciplinary, economics, arts, psychology, and immunology, accounted for only 87 (3.5%) ML documents. Similarly, out of the 1613 DL documents, 1427 (88.4%) were categorized under computer science, while only 17 (1.0%) belonged to the field of environmental science, and the remaining 44 (2.7%) were classified under other fields, including chemical engineering, multidisciplinary, health, nursing, and pharmacology.
4.3 Top 15 active countries
Figure 3 depicts the visualization of the 15 most active countries. The study highlights the global nature of ML and DL research for cloud security, with researchers from many countries contributing to the field. Authors from 98 different countries have contributed to the field of ML and DL research for cloud security. The top 15 active countries published 89.6% (2185) of ML documents and 98.2% (1584) of DL documents. China, India, and the USA are the leading nations in both ML and DL research. Regarding ML research, with 26.6% (649), India had the most publications, followed by China and the USA with 15.7% (348) each. The countries with the least number of ML publications were France, with 1.7% (42), and Taiwan, with 1.68% (41) studies of the total. Of the top 15 active countries for ML research, six were in Asia, four in Europe, two in the Middle East, and two in North America. In DL research, China led with 24.4% (394) of the published documents, followed by India with 23.8% (384), and the USA with 10.4% (169). Of the top 15 active countries for DL research, seven were in Asia, three in the Middle East, two in Europe, and two in North America.

Top 15 active countries
4.4 Top 15 active institutions
Figure 4 depicts the visualization of the 15 most active institutions. ML and DL research for cloud security has received contributions from 98 countries and 149 institutions worldwide. In ML, Vellore Institute of Technology is the most active organization in this subject in India, accounting for 1.1% (27 articles) of the documents. SRM Institute of Science and Technology (India), Chinese Academy of Science (China), and Qatar University (Qatar) followed closely behind, each contributing 1% (18 articles) of the documents. Among the top 15 active institutions, five were in China, four in Saudi Arabia, three in India, and one in Australia, Singapore, and Qatar. These statistics demonstrate the significant global presence of research in this field. In DL literature, the Chinese Academy of Sciences in China was the most active institution, contributing 1.8% (30 articles) of the documents. The University of Electronic Science and Technology of China (China) published 1.36% (23 articles), and Nanyang Technological University (Singapore) published 1.3% (21 articles). Among the top 15 active institutions, eight were in China, two in Saudi Arabia and India, and one in Singapore and Qatar. These figures highlight the substantial contributions of Chinese and Indian institutions to DL research.

Top 15 active institutions
4.5 Top 15 active authors
Figure 5 displays the authors who are most active in the fields of ML and DL regarding cloud security. 175 authors authored the ML-retrieved documents, with 224 papers needing to be specified. Of these documents, roughly 36 were written by a single individual, 120 by two authors, and the remainder by at least three, except those with undefined authors. The most active authors are Professors Azidine Guezzaz and Said Benkirane from Université Cadi Ayyad in Morocco, Professor Mourade Azrour from Université Moulay Ismaïl in Morocco, and Professor Mohsen Mokhtar Guizani from Mohamed Bin Zayed University of Artificial Intelligence in the United Arab Emirates, who published 10 (0.4%) of the documents.

Top 15 active authors
On the other hand, 162 authors contributed to publishing the documents retrieved by DL, with 224 authors not specified. Of these documents, 11 were authored by a single individual, 70 by two authors, and the rest by at least three, except those with undefined authors. The most active authors were Professor Mohsen Guizani from Qatar University and Professor Prabhat Kumar from LUT University in Finland, who published eight (0.5%) documents each. Professor Jong Hyuk Park from Seoul National University of Science and Technology in South Korea and Professor Mohamed Amine Ferrag from Guelma University in Algeria tied for second place, having published seven (0.4%) documents each.
4.6 Top 15 publication channels
Table 5 depicts the 15 most preferred publication channels. The ML documents that were retrieved were published on a total of 161 different channels. Among these, the majority were conference articles, with 1,003 (41.1%) publications, followed by journal articles, with 937 (38.4%) proceedings and workshops. The most active publication channel in this field was the Lecture Notes in Computer Science, including the Lecture Notes in Computer Science Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics series, which accounted for 97 (3.9%) documents. The Lecture Notes in Networks and Systems series, also published by Springer, had 94 (3.8%) documents. Among individual scientific journals, IEEE Access had the highest number of publications with 84 (3.4%) documents, followed by Communications in Computer and Information Science Journal with 63 (2.6%) documents.
The DL documents that were retrieved were published on a total of 163 different channels. Journal articles accounted for the majority of publications, with 778 (48.2%), followed by conference proceedings, with 512 (31.7%) proceedings and workshops. The most active publication channel in this field was IEEE Access with 72 (4.4%) documents, followed closely by the Lecture Notes in Computer Science Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics series, with 61 (3.7%) documents.
4.7 Top 15 cited document
The retrieved ML documents received more than 14,000 citations, averaging about 5.7 citations per document. Similarly, the retrieved DL documents received 15,000 citations, averaging 9.6 citations per document. Table 6 provides an overview of the 15 most cited documents published since 2019. The ML document by Hassija et al. (Hassija et al. 2019 ) (published in IEEE Access in 2019) received the highest number of citations at 867, while the second highest cited ML document was by Mothukuri et al. (Mothukuri et al. 2021a ) (published by Future Generation Computer Systems in 2021) with 545 citations. The highest-cited DL document (Tuli et al. 2020 ), with 413 citations, was published by Future Generation Computer Systems in 2020, and the second highest-cited DL document, cited 296 times, was authored by Priya et al. (Priya et al. 2020 ) (published by Computer Communications in 2020).
5 Trends of machine learning and deep learning for cloud security
We should analyze the majority of the identified documents on Scopus in order to give a thorough picture of present and future trends in ML and DL for cloud security. However, we used systematic sampling due to the large number of papers (4051) (Mostafa and Ahmad 2018 ). Every k th case in the population is chosen for the sample using the systematic sampling technique, where k equals the size of the population divided by the size of the sample. If the population is arranged in a certain way, such as by year or alphabetically, like in the case of this study, this strategy works well (Mostafa and Ahmad 2018 ). Systematic sampling has the advantages of being reasonably simple to apply and lowering the likelihood of sample bias since every k th member is chosen, guaranteeing a reasonably equitable representation of the population (Alzoubi et al. 2022a ). The following two considerations were applied in the systematic sampling:
All the top 15 cited articles (reported in Table 5 ) were included in the review for both ML and DL.
To select the five studies for each of the past five years (2019–2023), as shown in Table 7 , we employed a systematic approach. Given the substantial increase in research on cloud security utilizing ML and DL since 2019, we aimed to ensure comprehensive coverage of relevant studies. Initially, we conducted a systematic sampling process based on the articles deemed most relevant to our topic. This relevance was determined by carefully examining the titles and keywords of the 4051 articles retrieved from our search in the Scopus database, excluding the top 15 cited articles. This exclusion was to ensure that our selection process remained focused on identifying lesser-known but potentially valuable contributions to the field. By using this method, we aimed to provide a well-rounded representation of research developments, particularly considering publications from 2023 that may not yet have garnered citations. Some articles were found to be relevant to both ML and DL. To address this overlap, we adopted a meticulous approach to ensure consistency. We carefully reviewed each manuscript in its entirety to determine whether its primary focus leaned more towards ML or DL. Accordingly, we were able to categorize each paper according to its predominant emphasis, thus ensuring clarity and coherence in our analysis.
We had to establish a set of themes or categories for the common trends before we could begin examining the chosen articles. In order to do this, we systematically looked into the Scopus database's keywords for both ML and DL searches. A cross-analysis of the terms in both ML and DL was also done. The terms "Intrusion Detection", "Anomaly Detection", "Blockchain", "Feature Extraction", "Forecasting", "Attack Detection", "Feature Selection", "Authentication", "Information Management", "Automation", "Performance", and "optimization" were found to be frequently occurring keywords for both ML and DL. These keywords enabled us to generate the first set of themes and then organize the findings from the chosen articles according to how closely each topic was linked to the others. "Anomaly Detection”, "Security Automation", "Native Security", and "Emerging Technologies" are the four common themes that we found. Apart from the shared themes between DL and ML, we observed that DL concentrates more on image identification and network traffic analysis, whereas ML search terms are more focused on insider threats and security brokers. These foci were consequently added to the DL and ML themes, respectively. Table 8 summarizes these trends.
5.1 Machine learning trends
This review revealed several trends and objectives for applying ML to cloud security. Insider threats, anomaly detection, security automation and intelligence, cloud-native security, and emerging technology impact are the six general categories that we used in this article to group them.
5.1.1 Anomaly detection
Due to its effectiveness in identifying and responding to security incidents, ML-based anomaly detection is increasingly employed in cloud systems (Hassija et al. 2019 ; Jaber and Rehman 2020 ). Compared to conventional rule-based systems, ML-based anomaly detection is generally considered more accurate and effective (Chkirbene et al. 2020 ; Heidari and Jabraeil Jamali 2023 ). It is important to remember that anomaly detection is a typical application for ML and has been thoroughly investigated and used in various fields, including fraud detection, intrusion detection, and system monitoring (Dey et al. 2019 ; Rahila and Khonde 2019 ). Consequently, ML-based anomaly detection is expected to remain a common method for protecting cloud systems (Ghazal et al. 2021 ; Tian et al. 2021 ; Hameed et al. 2021 ; Abidi et al. 2021 ).
Anomaly detection involves finding patterns or occurrences inside a system that differ from typical behavior. It encompasses various techniques such as monitoring and classification of data to distinguish between regular and irregular activities, as well as real-time detection and response mechanisms to promptly address detected anomalies (Belal and Sundaram 2022 ; Saran et al. 2022 ). This area also emphasizes efficient cloud data management practices to handle the large volumes of data generated during anomaly detection processes (Mothukuri et al. 2021a ). Additionally, resource management strategies are essential for optimizing computational resources and ensuring timely anomaly detection (Wu et al. 2019 ). Finally, the integration of multiple ML algorithms and models enhances the accuracy and robustness of anomaly detection systems by leveraging diverse perspectives and approaches (Angelopoulos et al. 2020 ).
5.1.2 Security automation and intelligence
ML models constantly get better based on the information they gather over time. ML-based systems can self-learn and modify their detection and response to evolving threat environments. According to research, more people are using security automation. According to a 2019 SANS Institute survey, 42% of respondents claimed they were adopting security automation to enhance incident response (Spitzner 2022 ). Moreover, Gartner forecasted that 30% of all security incident response processes will be improved by artificial intelligence and ML by 2021 in order to strengthen incident detection and response (Gartner. 2023 ). On the other hand, the SANS survey revealed that 53% of respondents claimed they used threat intelligence to enhance incident response and cloud security. Automation of security-related tasks and security inelegance have been suggested as ML benefits.
Security automation and intelligence aim to streamline security operations and enhance threat detection and response capabilities through automated processes and intelligent decision-making (Rosero et al. 2021 ). Automated incident response mechanisms enable rapid identification and containment of security incidents, minimizing their impact on the organization (Quraishi 2022 ). Automatic threat intelligence visualization facilitates the interpretation of complex security data, enabling security professionals to make informed decisions effectively (Narayanan and Muthukumar 2022 ). Automated policy enforcement ensures compliance with security policies and regulations across various systems and applications, reducing the risk of security breaches. Security orchestration automates the coordination of security tools and processes, improving efficiency and effectiveness in managing security incidents (Kumar et al. 2021 ). Predictive modeling techniques leverage historical security data to forecast potential threats and vulnerabilities, enabling proactive risk mitigation measures (Narayanan and Muthukumar 2022 ).
5.1.3 Cloud-native security
In cloud-native security, security should be built into the cloud-based platforms, infrastructure, and applications. Multiple layers of protection are implemented, and security is continuously monitored for emerging vulnerabilities from the beginning of the development process to production. As more businesses use cloud-based technology, cloud-native security becomes more crucial, and ML is frequently used as a significant component of these solutions. There is an increase in the use of cloud-native security solutions. 55% of enterprises are employing cloud-native security solutions, according to a survey by IDC 2020 , and that percentage is anticipated to reach 70% by 2022 (IDC. Idc marketscape worldwide managed security services 2020 vendor assessment. 2020 ). Additionally, according to a 2019 SANS Institute survey, 41% of participants claimed they were employing cloud-native security to enhance incident response and cloud security (Spitzner 2022 ).
Cloud-native security focuses on integrating security measures directly into cloud environments to protect cloud-native applications and data (Mishra et al. 2022a ). This includes implementing cloud-native network security solutions to safeguard network communications and data transmission within cloud environments. Cloud-native management platforms offer centralized security management capabilities, enabling organizations to monitor and enforce security policies consistently across cloud resources (Narayanan and Muthukumar 2022 ). Cloud-native security policy management involves defining and enforcing security policies tailored to the specific requirements and configurations of cloud-native applications and services. Considerations such as multi-tenancy and dynamic resource allocation are essential for addressing the unique challenges of securing cloud-native environments effectively (Kumar et al. 2022b ).
5.1.4 Role of emerging technologies
In the ML and cloud security frameworks, plenty of investigation has been conducted to fully explore the possibilities of new technologies like blockchain and quantum computing. Although integration is not always possible immediately, the ideas present exciting possibilities for breakthroughs in the future (Gupta et al. 2017 ). Blockchain technology ensures the integrity and provenance of security data, enhancing trust and transparency in security operations (Heidari et al. 2023 ). Quantum-resistant cryptography protects sensitive data and ML models against emerging threats posed by quantum computing (Amin et al. 2023 ). Secure multi-party computation enables collaborative model building and inference without compromising data privacy and confidentiality (Mishra et al. 2023 ). Homomorphic encryption allows ML algorithms to operate directly on encrypted data, preserving privacy while enabling data analysis (Dasgupta et al. 2022 ; Huang et al. 2022 ). Zero trust network access models enhance security by enforcing strict access controls based on user and device attributes, minimizing the risk of data breaches and unauthorized access (Saran et al. 2022 ; Gupta et al. 2022 ). These emerging technologies complement ML approaches to address evolving security challenges effectively.
5.1.5 Identifying insider threats
ML is being utilized increasingly to detect and address insider threats, as they are among the most significant concerns for enterprises. According to studies, ML-based systems are more precise and effective than conventional rule-based systems for detecting insider threats (Gupta et al. 2017 ). Additionally, studies have demonstrated that companies use behavioral analytics to identify and stop insider threats. 68% of respondents to a 2019 SANS Institute survey stated they used behavioral analytics to identify insider threats (Spitzner 2022 ). Identifying insider threats involves detecting and mitigating security risks posed by individuals within an organization who have access to sensitive information and resources (Dasgupta et al. 2022 ). ML techniques are applied to analyze user behavior, profile users, and process natural language to identify anomalous activities indicative of insider threats (Narayanan and Muthukumar 2022 ). Behavioral detection models monitor user actions and interactions with IT systems to detect deviations from normal behavior patterns (Tian et al. 2020 ). User profiling techniques leverage ML algorithms to create profiles of individual users based on their behavior, preferences, and access privileges, enabling organizations to identify suspicious activities and potential insider threats (Tian et al. 2021 ). NLP technologies analyze textual data, such as emails and chat logs, to identify language patterns associated with insider threats (Mothukuri et al. 2021b ). Graph analysis techniques model relationships between users, devices, and data to uncover hidden connections and potential security risks within the organization's network (Amiri et al. 2024 ).
5.1.6 Cloud access security broker
CASB is software deployed in the cloud or installed on-premises and serves as a bridge between customers and cloud service providers (SANS 2024 ). The ability of CASB to automatically detect and prohibit malicious activities has been improved by applying ML algorithms. CASB offers security features, including encryption, data loss prevention, and intrusion prevention. ML is frequently employed as a crucial component of CASB solutions, which are becoming increasingly popular. According to an IDC survey from 2020, 45% of businesses are utilizing CASB solutions, and by 2022, that percentage is predicted to reach 60% (IDC. Idc marketscape worldwide managed security services 2020 vendor assessment. 2020 ). In addition, a 2019 SANS Institute survey revealed that 37% of participants claimed they used CASB to enhance incident response and cloud security (Spitzner 2022 ).
CASB solutions provide visibility and control over cloud services and applications to ensure data security and compliance in cloud environments. ML-powered CASB platforms offer identity and access management capabilities, enabling organizations to enforce granular access controls and authentication mechanisms to protect against unauthorized access (Yu et al. 2021 ). Data loss prevention features leverage ML algorithms to detect and prevent data leaks or unauthorized sharing of sensitive information on cloud storage and collaboration platforms (Narayanan and Muthukumar 2022 ). Threat protection modules utilize ML-driven threat intelligence to identify and block malicious activities, such as malware infections and phishing attacks, targeting cloud services and applications (Balobaid et al. 2024 ). Compliance management functionalities enable organizations to assess and enforce compliance with industry regulations and standards, such as the Insurance Portability and Accountability Act (HIPAA), PCIDSS, General Data Protection Regulation (GDPR), and CCPA, by analyzing cloud usage and data handling practices against regulatory requirements (PonemonInstitute. 2024 ).
5.2 Deep learning trends
Although DL for cloud security is an emerging research area, several focuses and aims were identified in this review. This review revealed several trends and objectives for applying DL to cloud security. Anomaly detection, image-based malware detection, cloud-native security, and security automation are the six general categories used in this article to group them. The endeavors in this context have concentrated on utilizing a range of neural network architectures, including CNNs, RNN, and Long Short-Term Memory (LSTM) (Kumar et al. 202a ; Rjoub et al. 2021 ; Zhang et al. 2022 ; Abou El Houda et al. 2022 ). Furthermore, the focus has been on assessing the effectiveness of the network traffic analysis system through performance metrics such as F1-score, precision, and accuracy (Zhou et al. 2021 ; Thilagam and Aruna 2021 ; Makkar et al. 2021 ; Landman and Nissim 2021 ).
5.2.1 Anomaly detection
An important field of research and development, the use of DL for anomaly detection is growing in acceptance (Heidari and Jabraeil Jamali 2023 ). The application of DL in anomaly detection is a burgeoning area of research and development, gaining popularity due to its potential for learning intricate non-linear relationships, automatic feature extraction, and improved performance over time (Doriguzzi-Corin et al. 2020 ). DL has been demonstrated to be effective in several anomaly detection tasks across various domains, including spotting cyberattacks in network systems, intrusion detection, fraudulent financial transactions, and machinery breakdowns in industrial systems. According to a 2019 SANS Institute poll, the usage of DL in anomaly detection is anticipated to rise over the next two years, with 37% of respondents stating they intended to do so (Spitzner 2022 ). Here, the focus has been on generative models, such as Variational Autoencoders (VAE) and Generative Adversarial Networks (GAN), which are employed to create synthetic data that can be used to train models for detecting anomalies. Moreover, the focus has been on assessing the anomaly detection system's performance using various metrics such as precision, recall, F1-score, and the Receiver Operating Characteristic Curve (AUC-ROC), which evaluates the system's ability to identify anomalies.
Anomaly detection involves identifying irregular patterns or events within a system that deviate from normal behavior (Kasongo 2023 ). DL techniques, such as deep neural networks, are employed to analyze complex and high-dimensional data to detect anomalies across various domains, including cybersecurity, finance, and industrial systems (Aldallal 1916 ). DL-based anomaly detection systems leverage advanced architectures such as CNNs and RNN to capture intricate non-linear relationships in data and automatically extract relevant features for anomaly detection (Mahdavifar and Ghorbani 2019 ). Evaluation metrics such as recall, precision, accuracy, and F1-score are used to assess the effectiveness of DL-based anomaly detection systems in detecting and mitigating security threats (Zhou et al. 2023 ; Lahande and Kaveri 2022 ).
5.2.2 Security automation
Based on the works cited in this paper, the following sections provide a summary of the previous work on utilizing DL for security automation (Tuli et al. 2020 ; Rjoub et al. 2021 ; Rosero et al. 2021 ; Zhang et al. 2022 ; Quraishi 2022 ). First, automation of anomaly detection has been demonstrated to be very accurate and have low false-positive rates when detecting unexpected patterns or behaviors that might point to a security problem. Second, automated incident response, in which DL has been used to automate responding to and mitigating issues, as well as prioritizing and escalating incidents depending on their severity or possible effect. DL has also been used to recover from incidents, such as by automatically rolling back modifications or restoring impacted resources. Third, self-learning: in incident response circumstances, when the cause of an occurrence is automated and rapidly determined, DL models that can explain how they came to their judgments might be very crucial. Finally, root cause analysis, where the underlying cause of events, such as a particular vulnerability or attack vector, has been found using DL. Moreover, DL has been used to predict and prevent future incidents.
5.2.3 Cloud-native security
Another prominent area of study and development is the application of DL for cloud-native security, which is growing in acceptance. This entails employing DL algorithms to integrate native security capabilities such as firewalls, IDS, and security information and event management systems into cloud-based services. Cloud-native security involves leveraging DL algorithms to integrate native security capabilities into cloud environments, such as firewalls, IDS, and SIEM systems (Dalal et al. 2023 ). DL-based native security solutions enable organizations to monitor and analyze security data in real-time, identify threats and vulnerabilities, and automate incident response processes (Landman and Nissim 2021 ). DL algorithms are used to evaluate security data in cloud systems, such as by detecting threat trends, identifying abnormal activities, and automating security tool orchestration. Additionally, DL-based incident management systems enable organizations to handle security events, determine incident causes, and remediate security issues effectively. Cloud-agnostic DL models are developed to ensure compatibility with various cloud platforms and address unique challenges in securing cloud environments, such as multi-tenancy and dynamic resource allocation (Parra et al. 2020 ; Thilagam and Aruna 2021 ). Compliance and regulatory management solutions leverage DL techniques to ensure cloud environments comply with industry regulations and standards, such as HIPAA and PCI-DSS, thereby enhancing data security and privacy in cloud deployments (Parra et al. 2020 ; Thilagam and Aruna 2021 ).
5.2.4 Role of emerging technologies
Cloud security may benefit significantly from the mix of emerging technologies and DL. The role of emerging technologies in DL encompasses various advancements aimed at enhancing the security and efficiency of DL applications. Blockchain technology ensures the integrity and reliability of training data by providing tamper-proof data provenance, thereby improving the trustworthiness of DL models (Alzoubi et al. 2022a , 2022b , 2022c ; Rathore et al. 2019 ; Kumar et al. 2021 ; Dai et al. 2020 ; Ahmed et al. 2023 ). Quantum-resistant cryptography safeguards DL models and sensitive data against future quantum computing threats, ensuring long-term security (Amin et al. 2023 ). Secure multi-party computation enables collaborative DL model training and inference without compromising data privacy, facilitating secure knowledge sharing and insight generation. Homomorphic encryption allows DL computations to be performed directly on encrypted data, preserving data privacy and enabling privacy-preserving analytics in cloud environments (Gupta et al. 2017 ; Pandey et al. 2023 ; Wu et al. 2020 ). Zero-trust network access enhances DL infrastructure security by dynamically controlling access based on user and device profiles, reducing the risk of insider threats and unauthorized access (Landman and Nissim 2021 ).
5.2.5 Image-based malware detection
The usage of this technology is growing in popularity and is an active field of study and development. This entails applying DL algorithms to examine images and find malware concealed in images or other multimedia files, such as Trojans and ransomware (Rao and Jain 2024 ). Image-based malware detection leverages DL algorithms to analyze images and multimedia files for the presence of malware, such as Trojans and ransomware (Nahmias et al. 2020 ). Malware behavior analysis involves using DL models to analyze the behavior of malware, such as its propagation methods and actions, to detect and mitigate threats effectively [100. Malware classification employs DL techniques to categorize malware into different types, aiding in identifying and addressing specific threats. Malware variant detection utilizes DL models to identify new iterations of existing malware, enhancing threat detection capabilities {Wu et al. 2022 #253]. Visualization techniques are used to understand how DL models make decisions and identify features used for malware detection, improving model interpretability and detection accuracy. Malware image compression employs DL to condense malware images, enhancing detection model efficiency while reducing storage and processing requirements (Ahmed et al. 2023 ; Wu et al. 2022 ).
5.2.6 Network traffic analysis
As an active field of research and development, the use of DL for network traffic analysis is growing in acceptance. To do this, DL algorithms are used to examine network data and spot trends that might point to a possible security problem, such as malware or a network incursion (Dai et al. 2020 ). DL-based network traffic analysis focuses on using DL algorithms to analyze network data for security threat detection and performance optimization (Chen et al. 2020 ). Network traffic classification involves categorizing network traffic into different groups, such as legitimate or malicious traffic, using DL models to enhance threat detection capabilities (Pandey et al. 2023 ). Traffic flow analysis utilizes DL to evaluate network traffic flows, identify fraudulent activities, and improve network performance through anomaly detection. Network traffic manipulation employs DL techniques to compress, generate, or standardize network traffic data, enhancing the efficiency and effectiveness of detection models while reducing resource requirements and data complexity (Gu et al. 2019 ; Dai et al. 2020 ).
5.3 Major machine learning and deep learning techniques and algorithms
It's critical to remember that the distinctions between ML and DL are not always apparent, and specific approaches may fall somewhere in the middle. For instance, gradient boosting and RF are ML techniques that may also be applied in DL settings.
5.3.1 Machine learning techniques
It is also essential to remember that applying ML approaches to cloud computing security is still a very young field of study, and new methods and algorithms are always being created. Identifying the optimum strategy is challenging since it will change based on the particular use case and dataset (Nissim et al. 2019 ; Balamurugan and Saravanan 2019 ; Yao et al. 2019 ). The proper settings, characteristics, and data pre-processing should be employed with the technique of choice in order to get good results. The following summarizes the major ML techniques (Mishra and Tyagi 2022 ; Saran et al. 2022 ; Nair et al. 2023 ; Butt et al. 2020 ; Chkirbene et al. 2020 ; Alzoubi et al. 2023 ). It is critical to select the appropriate methods and settings for a given problem since the performance of various strategies might vary based on the particular use case and dataset.
RF: This method is an ensemble method that can be used for intrusion detection and classification tasks.
SVM: This method is a potent algorithm that may be applied to problems requiring classification and regression.
K-means: This method uses a clustering algorithm to find patterns and irregularities in huge datasets.
Gradient boosting: This ensemble method may be applied to challenges, including classification and regression.
Genetic algorithm: The ML models' parameters are optimized using this method.
Transfer learning: This method applies the information gained from one task to another to enhance the performance of the ML models.
Federated learning: With the help of this method, several parties may train ML models without sharing any data.
Multi-task learning: Teaching the ML models to carry out several tasks at once is a strategy that helps them perform better.
Hyperparameter tuning: By adjusting the hyperparameters, this method helps ML models perform as well as possible.
Decision trees: One type of ML method that may be applied to classification and regression applications is decision trees. They may be used to find patterns and correlations in data, which helps detect intrusions and other security-related activities.
Bayesian networks: An example of a probabilistic graphic model is a Bayesian network, which may be applied to tasks like intrusion detection, anomaly detection, and classification.
Hidden Markov Models (HMM): Intrusion detection, anomaly detection, and sequence prediction are just a few examples of the activities that may be performed with HMMs, a category of probabilistic models.
Logistic regression: A statistical technique used for classification tasks is logistic regression. It may be utilized for data pattern recognition and intrusion detection.
Naive Bayes: Naive Bayes can be referred to as a probabilistic classifier. It may be utilized for data pattern recognition and intrusion detection.
5.3.2 Deep learning techniques
DL techniques are thus named because they feature several layers, enabling them to learn more abstract and complicated input representations. The essential DL techniques revealed in this work are listed below (Gupta et al. 2017 ; Tuli et al. 2020 ; Dai et al. 2020 ; Wu et al. 2020 ; Ramchandran and Sangaiah 2020 ).
Reinforcement learning: This technique has recently been utilized to strengthen cloud computing security by teaching the agent how to behave securely.
RNN: These are a class of DL techniques used in applications, including intrusion detection, anomaly detection, and sequence prediction in cloud computing settings. They work especially well with sequential data, such as time series.
LSTM networks: This type of RNN algorithm may be applied to intrusion detection and time series analysis.
Neural networks: One example of ML technology that draws inspiration from the structure and operation of the human brain is neural networks. They can be applied to many tasks, including intrusion detection, anomaly detection, and classification.
Autoencoder: This technique uses a specific kind of neural network that may be applied to anomaly and intrusion detection.
GAN: Data creation and anomaly detection are possible applications for this technique, a kind of neural network.
CNNs: These are a family of DL methods frequently employed for image and video analysis jobs, and they have been applied to jobs like intrusion detection, anomaly detection, and classification in cloud computing settings.
Adversarial training: By creating and using adversarial instances throughout the training process, this method teaches a model to be resistant to them.
Adversarial examples: These instances were created deliberately to trick ML models, and they were used to gauge how reliable ML models were for cloud computing security.
DBN: A type of deep neural network called a DBN is capable of feature extraction and categorization. This model can be employed to identify spam and phishing emails.
Capsule networks: A relatively new type of DL model called capsule networks is designed to better deal with spatial interactions between features. They have been utilized in security systems for image identification and categorization tasks.
Attention Mechanisms: Attention techniques are utilized to direct a DL model's attention to particular areas of the input data. They have been applied to intrusion detection and network traffic analysis.
Deep Residual Networks (ResNets): Deep neural networks called ResNets are made to deal with the vanishing gradient problem, which can happen while training very deep networks. They have been applied to classification and image recognition tasks in security systems.
VAE: An autoencoder class called VAE is employed to create fresh data samples. They have been used to create fake network traffic data for testing and refining security models and solutions.
Siamese networks: One class of deep neural network called a Siamese network compares two input data samples and produces a similarity score. They have been used to spot network traffic irregularities and malware samples that are similar or identical.
6 Discussion
The primary objective of this study was to evaluate and examine the patterns observed in published literature relating to ML and DL for cloud computing security. The study initially performed a bibliographic analysis by utilizing the Scopus database, which was crucial in identifying the areas, countries, institutions, and authors that demonstrated the most interest in this subject. Subsequently, the study utilized a systematic sampling approach to identify the trends and focal arguments of research papers published in this field to gain a more thorough understanding of ML and DL's role in cloud computing security. The study discovered a total of 4051 relevant documents as of mid-December 2023, with the literature on ML dating back to 2006 and the literature on DL beginning in 2016. This substantial volume of literature in a relatively short period underscores the significance of this subject.
As shown in Fig. 1 , there has been a significant growth in ML and DL articles related to cloud computing security in recent years. This may relate to the combination of technological advancements, increased data availability, industry adoption, evolving threats, academic interest, and interdisciplinary collaboration. Exploring these factors further can provide valuable insights into the underlying drivers of this trend. Regarding contributions by regions and countries, Asian nations such as India and China were found to be the most productive based on the number of documents published (1033 in India and 742 in China). The top 15 active countries account for the majority of ML and DL publications, highlighting the concentration of research efforts in these nations. Among the top 15 active countries, there is a diverse regional representation, with countries from Asia, Europe, the Middle East, and North America featuring prominently. This suggests widespread interest and involvement in ML and DL research for cloud security across different regions. In both ML and DL research, Asia emerges as the most active continent, with a significant number of countries contributing to the publications. The Middle East also demonstrates notable participation, particularly in DL research.
The top 15 active institutions, notably from China, Saudi Arabia, India, and other countries, demonstrate global collaboration and contributions to ML research. Similarly, in DL research, these regions, along with Singapore and Qatar, show strong representation among the top 15 institutions, highlighting collaborative efforts. These statistics underscore the global presence of research institutions in ML and DL for cloud security, reflecting collective efforts to address challenges through collaborative research. Taking into account the influence and output of scientific publications, the Lecture Notes in Computer Science Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics , which includes subseries on artificial intelligence and bioinformatics, had the highest number of published articles (158), followed by IEEE Access (156), which is a multidisciplinary, open access journal that publishes in engineering, computer science, and materials science. IEEE Access ranked as a Q1 according to the evaluation by quartiles in SJR (0.93) with an H-index of 204.
The research trends in ML and DL for cloud computing security reveal eight primary focus areas, including anomaly detection, security automation, native cloud security, insider threats, security brokers, network traffic analysis, image-based analysis, and the impact of emerging technologies. A closer examination of the literature on ML and DL demonstrates that DL serves as an extension of ML, either by expanding upon the work of ML or by employing more advanced capabilities provided by DL. Additionally, it is worth noting that ML and DL are relatively new technologies in the realm of cloud computing security, and ongoing research in this field indicates that there is still significant potential for the development of new techniques and algorithms.
6.1 Machine learning and deep learning—finding cross analysis
To conduct a cross-analysis between the ML and DL findings, we identify common themes, compare methodologies, and highlight differences or complementary aspects. We break down the analysis based on the main themes identified in both the ML and DL discussed in Sect. 5 .
Anomaly detection: DL and ML algorithms are broadly used for anomaly detection in cloud security. ML techniques include monitoring and classification, detection and response, cloud data management, resource management, and the use of multiple ML algorithms and models. However, DL techniques, such as unsupervised autoencoders and generative models like VAE and GAN, are employed for anomaly detection. DL focus areas include traffic analysis, handling imbalanced datasets, multi-model solutions, real-time analysis, and cloud anomaly monitoring.
Security automation: ML-based security automation involves automatic incident response, threat intelligence visualization, policy enforcement, security orchestration, threat intelligence feedback, and predictive modeling. ML techniques include automated analysis of threat intelligence data, policy enforcement, and security orchestration using ML algorithms. However, DL is utilized for automating anomaly detection, incident response, self-learning, and root cause analysis. DL focuses on the accuracy and low false-positive rates of automated detection systems and automating incident response and recovery processes.
Cloud-native security: ML techniques are integrated into cloud-native security solutions for network security, management platforms, security policy management, and compliance management. However, DL is applied to native security analysis, incident management, cloud-agnostic solutions, and compliance management. DL focus areas include using DL to automate incident response, manage security incidents, and ensure compliance with regulations.
Role of emerging technologies: ML and DL explore the integration of emerging technologies like blockchain, quantum-resistant cryptography, homomorphic encryption, secure multi-party computation, and zero-trust network access. They emphasize the potential benefits of these technologies in enhancing data security, privacy, and threat detection in cloud environments.
6.2 Practical implications
Both ML and DL offer practical implications for the industry, including improved security measures, automation of security processes, enhanced anomaly detection, and compliance management. While ML and DL share common objectives for enhancing cloud security, they employ different methodologies and techniques. ML tends to focus on traditional algorithms and supervised/unsupervised learning, while DL leverages neural network architectures and DL models for more complex pattern recognition tasks. Integrating both approaches can offer comprehensive solutions for handling various cloud computing security issues. ML and DL enable organizations to better protect their cloud environments, respond to security incidents more efficiently, and adapt to evolving threat landscapes. Additionally, ML is applied to identify insider threats, enhance CASB, and manage cloud-native security. However, DL techniques are used for image-based malware detection and network traffic analysis, focusing on malware behavior analysis, classification, variant detection, and visualization.
6.3 Challenges and research directions of machine learning and deep learning in the cloud security
While ML and DL are considered vital tools for cloud computing security, it is essential to understand the underlying data and the specific use case to select the correct algorithm, employ the proper feature engineering, and establish suitable thresholds to get the required performance (Pandey et al. 2023 ). Although ML and DL are not a one-size-fits-all solution, they should be used in conjunction with other security measures, including access control, network security, and incident management processes. The application of ML and DL for cloud security faces several difficulties, including the following:
Data privacy: Large volumes of data are needed to train ML and DL models, and this data must be protected to maintain user privacy (Narayanan and Muthukumar 2022 ). This might not be easy in cloud computing, where data is often processed and stored on shared infrastructure. Insider threats may be intricate and multidimensional. Therefore, it's crucial to remember that ML-based solutions alone might not be enough. A thorough security plan that may include technological, administrative, and physical measures should be in place to guard against insider threats (Mishra et al. 2023 , 2022b ). The implementation of robust data encryption and access control mechanisms can also help safeguard sensitive data. Employment techniques such as differential privacy can help to anonymize datasets while preserving their utility for training ML models (Nair et al. 2023 ). Additionally, utilizing federated learning approaches can help train models directly on decentralized data sources without exposing raw data to third parties (Abusitta et al. 2019 ). It is crucial to make sure that user privacy is maintained, given the growing usage of ML and DL in cloud security (Gupta et al. 2017 ). Creating methods for protecting privacy may be possible while enabling helpful research in this field (Alasmary et al. 2019 ).
Adversarial attacks: Adversarial attacks, in which a perpetrator tampers with the model's input to make it make the wrong judgments, are possible against ML and DL models (Saran et al. 2022 ). Models may be installed in untrusted contexts in cloud computing environments, making this particularly difficult. Adversarial ML research is crucial because cloud security increasingly uses ML models (Rathore et al. 2019 ). This entails creating techniques to strengthen the resistance of ML models to hostile cases and methods to recognize and fend off adversarial attacks. Moreover, incorporating techniques like input preprocessing and model regularization to enhance robustness against adversarial perturbations can be helpful (Ullah et al. 2022 ). Additionally, the employment of anomaly detection algorithms can help to identify and mitigate adversarial instances in real-time, coupled with dynamic model retraining to adapt to evolving attack strategies (Bhuvaneshwari and Kaythry 2023 ).
Scalability and performance: It might be challenging to apply ML and DL models in cloud systems where several users share resources since it is computationally costly to integrate ML and DL models with current infrastructure and security systems since these systems may have distinct needs and limitations (Heidari et al. 2022 ; Mishra et al. 2020 ). In addition, cloud computing security ML and DL models must abide by several laws and standards, including GDPR, HIPAA, and PCI-DSS (Mishra et al. 2022c ). In order to effectively utilize cloud resources, the recommendations made here are centered on optimizing ML and DL algorithms for distributed computing systems (Heidari and Jabraeil Jamali 2023 ). Another recommendation is to modularize ML components and enable smooth integration with the current cloud infrastructure by leveraging containerization and microservice architecture (Gupta et al. 2017 ). Furthermore, to ensure optimal performance and resource utilization, the implementation of auto-scaling techniques can help to dynamically assign computing resources based on workload demands (Dasgupta et al. 2022 ).
Explainability: Many ML and DL models are difficult to read, making it challenging to comprehend the models' decision-making processes (AlAhmad et al. 2021 ). This may be particularly difficult regarding cloud computing security since it's crucial to understand a decision's justification (Hossain et al. 2020 ). The recommendations made here are centered on using explainable AI methods to clarify the variables affecting model predictions, such as feature importance analysis and model visualization (Gupta et al. 2017 ). Moreover, using decision trees or rule-based models in conjunction with intricate ML and DL models can produce clear decision-making logic. The documentation of the model training and evaluation procedures may improve accountability and transparency in cloud security operations (Bhuvaneshwari and Kaythry 2023 ).
Generalization: It might be difficult for ML and DL models to generalize successfully to previously unknown data due to the possibility of novel attack types and abnormalities (Mahdavifar and Ghorbani 2019 ). In order to improve model generalization across various circumstances, the recommendations made here center on augmenting training datasets with a variety of representative samples (Dasgupta et al. 2022 ). Additionally, transfer learning techniques are used to deploy pre-trained models and modify them for use in particular cloud security tasks, which lessens the requirement for large amounts of labeled data (Bhuvaneshwari and Kaythry 2023 ). Overall, maintaining the model's performance and updating it frequently are recommended to take into account fresh threat intelligence and adjust to changing security issues (Lei et al. 2022 ).
Label bias: The performance of the models depends on the data quality, and bias in the data might lead to bias in the models. Although the data cannot always be indicative of real-world events, this might offer difficulty for cloud computing security (Yao et al. 2019 ; Krishnan et al. 2019 ). The recommendations made here center on the use of implementation data preparation techniques such as undersampling or oversampling to reduce label bias and guarantee that all classes are equally represented in training datasets (Belal and Sundaram 2022 ). To further promote equality and inclusion in cloud security applications, employment fairness-aware learning algorithms may be used to identify and reduce biased practices in model predictions (Krishnan et al. 2019 ). Furthermore, bias propagation in ML and DL models can be minimized by carrying out comprehensive evaluations of the quality of the data and establishing precise criteria for data collection and annotation (Gupta et al. 2017 ).
It is worth noting that ML, DL, and cloud computing security are all active research areas. New techniques and algorithms are evolving every day. The promising research areas found in this review are listed below.
More research is needed in the developing domains of automated incident response, image-based malware detection, and cloud-native security.
ML algorithms applied to cloud-native security, which entails utilizing ML algorithms to assess and safeguard cloud-native apps and services, is the subject of growing research.
In big and complicated cloud settings, there is a need to create more effective and efficient ways for identifying abnormalities and intrusions. Further developments in this area may bring up new elements and variables in ML and DL for security event correlation.
Federated learning presents a viable approach to augmenting security in cloud computing since it enables cooperation across several organizations.
As it enables the model to identify and stop various security risks, multi-task learning may benefit cloud computing security.
Cloud security is increasingly dependent on edge/fog computing as more and more devices and sensors are connected to the internet (Alzoubi and Aljaafreh 2023 ). To increase security and privacy, research in this field may focus on creating ML and DL approaches that can be used on edge and fog devices.
IoT-based data processing in cloud computing environments needs more sophisticated, secure operations using ML and DL.
6.4 Study limitations
There are certain limitations to the current investigation. They used only one database (Scopus) without considering other databases often utilized in the academic community, such as Dimensions and Web of Science. While this study exclusively utilizes the Scopus database, it's important to acknowledge its status as a comprehensive academic repository, encompassing many journals and conferences also indexed in the Web of Science, for example. While we recognize the value of other databases such as Web of Science, our decision to focus solely on Scopus was based on several factors, including accessibility, coverage of relevant literature, and familiarity with the platform. Nonetheless, it's possible that some sources are not included. Despite this limitation, the findings offer valuable insights into the emerging research theme, benefiting researchers in the field.
While retrieving literature from the Scopus database, there was a slight bias in favor of nations having a lot of articles indexed there. Scopus has a bias in favor of academic journals with English-language publications. As a result, publications published in languages other than English were not retrieved, potentially leaving out essential contributions made in those other languages, notwithstanding their preponderance. In the identified articles, non-English publications were primarily in Chinese, Turkish, and Portuguese, comprising 1.1% of ML and 1.8% of DL papers. It's important to note that we lack proficiency in these languages, limiting our ability to analyze the findings from these papers. This limitation may have impacted the comprehensiveness of our study, particularly in capturing insights from non-English sources.
As with all prior bibliometric research, the current study excluded gray literature. This study's search method may have produced some false-positive or false-negative findings. Thus, these constraints should be taken into account while interpreting the results. Nonetheless, the study outlines a strict approach for the chosen papers and uses a database widely regarded as trustworthy by experts. A study effort that may be utilized as a reference for future researchers can be presented thanks to the word choice, period, and number of documents used. Future studies might usefully apply our analytical methodology to another language (such as Chinese or Turkish) and provide a thorough worldwide understanding of the literature.
7 Conclusions
Cloud security is a critical concern as organizations increasingly rely on cloud computing for data storage, processing, and application hosting. Traditional security measures face challenges in detecting and mitigating sophisticated cyber threats targeting cloud environments. In response, ML and DL techniques have emerged as powerful tools to bolster cloud security. Massive data sets can be analyzed by ML algorithms to find trends and abnormalities that point to cyberattacks, while DL models excel at image-based threat detection and network traffic analysis. Although numerous papers have been published on utilizing ML and DL to bolster cloud security, there remains a dearth of comprehensive bibliographic reviews that synthesize the techniques, trends, and challenges in this domain. Therefore, this paper seeks to provide current insights into the research landscape of cloud computing security, focusing on the utilization of DL and ML techniques. This offers a novel perspective on the research area, expanding on previous studies. Additionally, the bibliometric analysis conducted in this work allows for a systematic evaluation of scientific output and trends, contributing methodologically to the field.
The integration of ML and DL presents promising avenues to bolster the security of cloud computing systems, offering efficient means to detect and counteract security risks across various tasks. Our study highlights key trends in ML’s role in cloud security, including anomaly detection, security automation, native security, insider threats, security brokers, and emerging technology roles. The study also highlights key trends in the DL's role in cloud security, including anomaly detection, security automation, native security, image-based detection, network traffic analysis, and emerging technology roles. However, challenges such as integration issues, performance concerns, and data privacy remain. Addressing these challenges requires proper system architecture, appropriate method selection, and the incorporation of explainable AI technologies. By navigating these challenges, researchers, policymakers, and practitioners can harness the full potential of ML and DL to fortify cloud computing security and safeguard data effectively. Researchers can explore different ML and DL techniques for securing cloud computing environments. Moreover, policymakers can incorporate these techniques into regulatory frameworks for enhanced security measures, and practitioners can deploy these solutions to proactively detect and respond to security threats. Future research may focus on automated incident response, image-based malware detection, and ML algorithms for cloud-native security. Future research may also focus on techniques to enhance anomaly detection in complex cloud environments. Additionally, future research in edge/fog computing and IoT-based data processing can enhance security and privacy in cloud environments.
Abbas Z, Myeong S (2023) Enhancing industrial cyber security, focusing on formulating a practical strategy for making predictions through machine learning tools in cloud computing environment. Electronics 12:2650
Article Google Scholar
Abdel-Basset M, Mohamed M, Chang V (2018) NMCDA: A framework for evaluating cloud computing services. Futur Gener Comput Syst 86:12–29
Abdullahi M, Baashar Y, Alhussian H, Alwadain A, Aziz N, Capretz LF, Abdulkadir SJ (2022) Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 11:198
Abidi I, Kumar V, Sen R (2021) Practical attestation for edge devices running compute heavy machine learning applications. In: Proceedings of the Annual Computer Security Applications Conference (ACSAC), ACM. Austin, Texas, USA, 323–336
Abosata N, Al-Rubaye S, Inalhan G (2023) Customised intrusion detection for an industrial IoT heterogeneous network based on machine learning algorithms called FTL-CID. Sensors 23:321
Abou El Houda Z, Brik B, Ksentini A, Khoukhi L, Guizani M (2022) When federated learning meets game theory: A cooperative framework to secure iiot applications on edge computing. IEEE Trans Indust Inform 18:7988–7997
Abusitta A, Bellaiche M, Dagenais M, Halabi T (2019) A deep learning approach for proactive multi-cloud cooperative intrusion detection system. Futur Gener Comput Syst 98:308–318
Ahmad W, Rasool A, Javed AR, Baker T, Jalil Z (2022) Cyber security in iot-based cloud computing: A comprehensive survey. Electronics 11:16
Ahmed I, Anisetti M, Ahmad A, Jeon G (2023) A multilayer deep learning approach for malware classification in 5G-enabled IIoT. IEEE Trans Industr Inf 19:1495–1503
AlAhmad AS, Kahtan H, Alzoubi YI, Ali O, Jaradat A (2021) Mobile cloud computing models security issues: A systematic review. J Netw Comput Appl 190:103152
Alasmary H, Khormali A, Anwar A, Park J, Choi J, Abusnaina A, Awad A, Nyang D, Mohaisen A (2019) Analyzing and detecting emerging Internet of things malware: A graph-based approach. IEEE Int Things J 6:8977–8988
Aldallal A (1916) Toward efficient intrusion detection system using hybrid deep learning approach. Symmetry 2022:14
Google Scholar
Aldhaheri A, Alwahedi F, Ferrag MA, Battah A (2023) Deep learning for cyber threat detection in IoT networks: A review. Int Things Cyber-Phys Syst 4:110–128
Alkadi O, Moustafa N, Turnbull B, Choo K-KR (2020) A deep blockchain framework-enabled collaborative intrusion detection for protecting IoT and cloud networks. IEEE Internet Things J 8:9463–9472
Aloqaily M, Otoum S, Al Ridhawi I, Jararweh Y (2019) An intrusion detection system for connected vehicles in smart cities. Ad Hoc Netw 90:101842
Alrashdi I, Alqazzaz A, Aloufi E, Alharthi R, Zohdy M, Ming H (2019) Ad-iot: Anomaly detection of iot cyberattacks in smart city using machine learning. In: Proceedings of the 9th Annual Computing and Communication Workshop and Conference (CCWC), IEEE. Las Vegas, NV, USA, pp 0305–0310
Alzoubi YI, Aljaafreh A (2023) Blockchain-fog computing integration applications: A systematic review. Cyber Inform Technol 23:3–37
Alzoubi Y, Gill A (2021) The critical communication challenges between geographically distributed agile development teams: Empirical findings. IEEE Trans Prof Commun 64:322–337
Alzoubi YI, Osmanaj VH, Jaradat A, Al-Ahmad A (2021) Fog computing security and privacy for the internet of thing applications: State-of-the-art. Secur Privacy 4:e145
Alzoubi YI, Gill A, Mishra A (2022a) A systematic review of the purposes of blockchain and fog computing integration: Classification and open issues. J Cloud Comput 11:1–36
Alzoubi YI, Al-Ahmad A, Kahtan H (2022b) Blockchain technology as a Fog computing security and privacy solution: An overview. Comput Commun 182:129–152
Alzoubi YI, Al-Ahmad A, Kahtan H, Jaradat A (2022c) Internet of things and blockchain integration: Security, privacy, technical, and design challenges. Future Int 14:216
Alzoubi YI, Topcu AE, Erkaya AE (2023) Machine learning-based text classification comparison: Turkish language context. Appl Sci 13:9428
Amin J, Anjum MA, Ibrar K, Sharif M, Kadry S, Crespo RG (2023) Detection of anomaly in surveillance videos using quantum convolutional neural networks. Image vis Comput 135:104710
Amiri Z, Heidari A, Navimipour NJ, Unal M, Mousavi A (2024) Adventures in data analysis: A systematic review of Deep Learning techniques for pattern recognition in cyber-physical-social systems. Multimedia Tools Applic 83:22909–22973
Angelopoulos A, Michailidis ET, Nomikos N, Trakadas P, Hatziefremidis A, Voliotis S, Zahariadis T (2020) Tackling faults in the industry 4.0 era—a survey of machine-learning solutions and key aspects. Sensors 20:109
Balamurugan V, Saravanan R (2019) Enhanced intrusion detection and prevention system on cloud environment using hybrid classification and OTS generation. Clust Comput 22:13027–13039
Balobaid AS, Shaik S, Komandur S (2024) A review on cyber security issues in IoT-based cloud computing. Intl J Intell Syst Appl Eng 12:278–285
Belal MM, Sundaram DM (2022) Comprehensive review on intelligent security defences in cloud: Taxonomy, security issues, ML/DL techniques, challenges and future trends. J King Saud Univ-Comput Inform Sci 34:9102–9131
Bhattacharya P, Tanwar S, Bodkhe U, Tyagi S, Kumar N (2019) Bindaas: Blockchain-based deep-learning as-a-service in healthcare 4.0 applications. IEEE Trans Net Sci Eng 8:1242–1255
Bhattacherjee SS, Kumar NS, Rajalakshmi P (2019) Emotion detection IoT enabled edge-node for citizen security. In: Proceedings of the 5th World Forum on Internet of Things (WF-IoT), IEEE. Limerick, Ireland, pp 925–930
Bhuvaneshwari A, Kaythry P (2023) A review of deep learning strategies for enhancing cybersecurity in networks: Deep learning strategies for enhancing cybersecurity. J Sci Ind Res 82:1316–1330
Brown P, Brown A, Gupta M, Abdelsalam M (2022) Online malware classification with system-wide system calls in cloud iaas. In: Proceedings of the 23rd International Conference on Information Reuse and Integration for Data Science (IRI), IEEE. San Diego, CA, USA, pp 146–151
Butt UA, Mehmood M, Shah SBH, Amin R, Shaukat MW, Raza SM, Suh DY, Piran MJ (2020) A review of machine learning algorithms for cloud computing security. Electronics 9:1379
Chen C, Liu B, Wan S, Qiao P, Pei Q (2020) An edge traffic flow detection scheme based on deep learning in an intelligent transportation system. IEEE Trans Intell Transp Syst 22:1840–1852
Chkirbene Z, Erbad A, Hamila R, Gouissem A, Mohamed A, Hamdi M (2020) Machine learning based cloud computing anomalies detection. IEEE Network 34:178–183
CybercrimeMagazine (2024) Cybercrime Magazine. https://cybersecurityventures.com/ , accessed 2 April 2024.
Dai Y, Xu D, Zhang K, Maharjan S, Zhang Y (2020) Deep reinforcement learning and permissioned blockchain for content caching in vehicular edge computing and networks. IEEE Trans Veh Technol 69:4312–4324
Dalal S, Manoharan P, Lilhore UK, Seth B, Simaiya S, Hamdi M, Raahemifar K (2023) Extremely boosted neural network for more accurate multi-stage Cyber attack prediction in cloud computing environment. J Cloud Comput 12:1–22
Dasgupta D, Akhtar Z, Sen S (2022) Machine learning in cybersecurity: A comprehensive survey. J Defense Model Simul 19:57–106
Dey S, Ye Q, Sampalli S (2019) A machine learning based intrusion detection scheme for data fusion in mobile clouds involving heterogeneous client networks. Inform Fusion 49:205–215
Doriguzzi-Corin R, Millar S, Scott-Hayward S, Martinez-del-Rincon J, Siracusa D (2020) LUCID: A practical, lightweight deep learning solution for DDoS attack detection. IEEE Trans Netw Serv Manage 17:876–889
Dovom EM, Azmoodeh A, Dehghantanha A, Newton DE, Parizi RM, Karimipour H (2019) Fuzzy pattern tree for edge malware detection and categorization in IoT. J Syst Architect 97:1–7
Ferrag MA, Babaghayou M, Yazici MA (2020) Cyber security for fog-based smart grid SCADA systems: Solutions and challenges. J Inform Secur Appl 52:102500
Ferrag MA, Friha O, Hamouda D, Maglaras L, Janicke H (2022) Edge-IIoTset: A new comprehensive realistic cyber security dataset of IoT and IIoT applications for centralized and federated learning. IEEE Access 10:40281–40306
Gartner (2023) Gartner research. gartner.com. https://www.gartner.com/en/information-technology/research/research-index . Viewed 8 December 2023.
Ge M, Syed NF, Fu X, Baig Z, Robles-Kelly A (2021) Towards a deep learning-driven intrusion detection approach for Internet of Things. Comput Netw 186:107784
Ghazal TM, Hasan MK, Alshurideh MT, Alzoubi HM, Ahmad M, Akbar SS, Al Kurdi B, Akour IA (2021) IoT for smart cities: Machine learning approaches in smart healthcare—A review. Future Int 13:218
Goh GD, Sing SL, Yeong WY (2021) A review on machine learning in 3D printing: Applications, potential, and challenges. Artif Intell Rev 54:63–94
Gu T, Liu K, Dolan-Gavitt B, Garg S (2019) Badnets: Evaluating backdooring attacks on deep neural networks. IEEE Access 7:47230–47244
Gupta C, Johri I, Srinivasan K, Hu Y-C, Qaisar SM, Huang K-Y (2017) A systematic review on machine learning and deep learning models for electronic information security in mobile networks. Sensors 2022:22
Gupta M, Abdelsalam M, Khorsandroo S, Mittal S (2020) Security and privacy in smart farming: Challenges and opportunities. IEEE Access 8:34564–34584
Gupta I, Singh AK, Lee C-N, Buyya R (2022) Secure data storage and sharing techniques for data protection in cloud environments: A systematic review, analysis, and future directions. IEEE Access 10:71247–71277
Hameed SS, Selamat A, Abdul Latiff L, Razak SA, Krejcar O, Fujita H, Ahmad Sharif MN, Omatu S (2021) A hybrid lightweight system for early attack detection in the IoMT fog. Sensors 21:8289
Hassija V, Chamola V, Saxena V, Jain D, Goyal P, Sikdar B (2019) A survey on IoT security: Application areas, security threats, and solution architectures. IEEE Access 7:82721–82743
Heidari A, Jabraeil Jamali MA (2023) Internet of Things intrusion detection systems: a comprehensive review and future directions. Clust Comput 26:3753–3780
Heidari A, Navimipour NJ, Unal M (2022) Applications of ML/DL in the management of smart cities and societies based on new trends in information technologies: A systematic literature review. Sustain Cities Soc 85:104089
Heidari A, Navimipour NJ, Unal M (2023) A secure intrusion detection platform using blockchain and radial basis function neural networks for internet of drones. IEEE Internet Things J 10:8445–8454
Hernandez-Jaimes ML, Martinez-Cruz A, Ramírez-Gutiérrez KA, Feregrino-Uribe C (2023) Artificial intelligence for IoMT security: a review of intrusion detection systems, attacks, datasets and Cloud-Fog-Edge architectures. Internet of Things 23:100887
Herrera-Franco G, Montalván-Burbano N, Carrión-Mero P, Apolo-Masache B, Jaya-Montalvo M (2020) Research trends in geotourism: A bibliometric analysis using the scopus database. Geosciences 10:379
Hossain MS, Muhammad G, Guizani N (2020) Explainable AI and mass surveillance system-based healthcare framework to combat COVID-I9 like pandemics. IEEE Network 34:126–132
Huang H, Wang Y, Zong H (2022) Support vector machine classification over encrypted data. Appl Intell 52:5938–5948
IACSIT (2024) The international association of computer science and information technology. https://www.iacsit.org/ , accessed 2 April 2024.
IDC. Idc marketscape worldwide managed security services 2020 vendor assessment. International Data Coorporation. https://www.idc.com/getdoc.jsp?containerId=US46235320 . Viewed 15 December 2023. 2020.
ISSA (2024) The information systems security association. https://www.issa.org/ , accessed 2 April 2024.
Jaber AN, Rehman SU (2020) FCM–SVM based intrusion detection system for cloud computing environment. Clust Comput 23:3221–3231
Jia Y, Zhong F, Alrawais A, Gong B, Cheng X (2020) Flowguard: An intelligent edge defense mechanism against IoT DDoS attacks. IEEE Int Things J 7:9552–9562
Kasongo SM (2023) A deep learning technique for intrusion detection system using a recurrent neural networks based framework. Comput Commun 199:113–125
Khudzari JM, Kurian J, Tartakovsky B, Raghavan GV (2018) Bibliometric analysis of global research trends on microbial fuel cells using Scopus database. Biochem Eng J 136:51–60
Kornaros G (2022) Hardware-assisted machine learning in resource-constrained IoT environments for security: Review and future prospective. IEEE Access 10:58603–58622
Krishnan P, Duttagupta S, Achuthan K (2019) VARMAN: Multi-plane security framework for software defined networks. Comput Commun 148:215–239
Kumar P, Kumar R, Srivastava G, Gupta GP, Tripathi R, Gadekallu TR, Xiong NN (2021) PPSF: A privacy-preserving and secure framework using blockchain-based machine-learning for IoT-driven smart cities. IEEE Trans Net Sci Eng 8:2326–2341
Kumar A, Umurzoqovich RS, Duong ND, Kanani P, Kuppusamy A, Praneesh M, Hieu MN (2022) An intrusion identification and prevention for cloud computing: from the perspective of deep learning. Optik 270:170044
Kumar S, Prethi KA, Singh S, Lourens M, Patil N (2022) Role of machine learning in managing cloud computing security. In Proceedings of the 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), IEEE. Greater Noida, India, 2366–2369
Lahande PV, Kaveri PR (2022) Reinforcement learning applications for performance improvement in cloud computing—A systematic review. In: Aurelia S, Hiremath SS, Subramanian K, Biswas SK (eds) Sustainable advanced computing: lecture notes in electrical engineering, vol 840. Springer, Singapore, pp 91–112
Landman T, Nissim N (2021) Deep-Hook: A trusted deep learning-based framework for unknown malware detection and classification in Linux cloud environments. Neural Netw 144:648–685
Lei W, Pang Z, Wen H, Hou W, Han W (2022) FDI attack detection at the edge of smart grids based on classification of predicted residuals. IEEE Trans Industr Inf 18:9302–9311
Lin H, Xue Q, Feng J, Bai D (2022) Internet of things intrusion detection model and algorithm based on cloud computing and multi-feature extraction extreme learning machine. Digital Communications and Networks, In Press, https://doi.org/10.1016/j.dcan.2022.09.021
Liu D, Shen J, Wang A, Wang C (2020) Secure real-time image protection scheme with near-duplicate detection in cloud computing. J Real-Time Image Proc 17:175–184
Ma X, Wu J, Xue S, Yang J, Zhou C, Sheng QZ, Xiong H, Akoglu L (2023) A comprehensive survey on graph anomaly detection with deep learning. IEEE Trans Knowl Data Eng 35:12012–12038
Mahdavifar S, Ghorbani AA (2019) Application of deep learning to cybersecurity: A survey. Neurocomputing 347:149–176
Makkar A, Ghosh U, Sharma PK (2021) Artificial intelligence and edge computing-enabled web spam detection for next generation IoT applications. IEEE Sens J 21:25352–25361
MarketsandMarkets (2023) Artificial intelligence (AI) market. MarketsandMarkets.com. https://www.marketsandmarkets.com/Market-Reports/artificial-intelligence-market-74851580.html . Accessed 5 Jan 2024
Miles MB, Huberman AM (1994) Qualitative data analysis: An expanded sourcebook. Sage, Beverly Hills, USA
Mishra S, Sharma SK, Alowaidi MA (2020) Multilayer self-defense system to protect enterprise cloud. Comput, Mater Contin 66:71–85
Mishra A, Alzoubi YI, Gill AQ, Anwar MJ (2022b) Cybersecurity enterprises policies: A comparative study. Sensors 22:538
Mishra A, Alzoubi YI, Anwar MJ, Gill AQ (2022c) Attributes impacting cybersecurity policy development: An evidence from seven nations. Comput Secur 120:102820
Mishra A, Jabar TS, Alzoubi YI, Mishra KN (2023) Enhancing privacy-preserving mechanisms in Cloud storage: A novel conceptual framework. Concurr Comput: Pract Exp 35:e7831
Mishra DP (2024) A review of cloud security solutions: Leveraging machine learning and deep learning techniques. Available at SSRN 4704331, SSRN: https://ssrn.com/abstract=4704331 . Accessed 5 Jan 2024
Mishra S, Tyagi AK (2022) Emerging trends and techniques in machine learning and Internet of things-based cloud applications. In: Tyagi AK, Sreenath N (eds) Handbook of research of internet of things and cyber-physical systems, 1st edn. Apple Academic Press: CRC Press. Taylor Francis Group, pp 149–167
Mishra N, Singh R, Yadav S (2022) Detection of DDoS vulnerability in cloud computing using the perplexed bayes classifier. Computational Intelligence and Neuroscience 2022
Morgan, S (2022) Boardroom cybersecurity 2022 report. Cybercrime Magazine. https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021/ . Viewed 31 November 2023.
Mostafa SA, Ahmad IA (2018) Recent developments in systematic sampling: A review. J Stat Theor Pract 12:290–310
Article MathSciNet Google Scholar
Mothukuri V, Parizi RM, Pouriyeh S, Huang Y, Dehghantanha A, Srivastava G (2021a) A survey on security and privacy of federated learning. Futur Gener Comput Syst 115:619–640
Mothukuri V, Khare P, Parizi RM, Pouriyeh S, Dehghantanha A, Srivastava G (2021b) Federated-learning-based anomaly detection for IoT security attacks. IEEE Internet Things J 9:2545–2554
Moustafa N (2021) A new distributed architecture for evaluating AI-based security systems at the edge: Network TON_IoT datasets. Sustain Cities Soc 72:102994
Moustafa N, Hu J, Slay J (2019) A holistic review of network anomaly detection systems: A comprehensive survey. J Netw Comput Appl 128:33–55
Nahmias D, Cohen A, Nissim N, Elovici Y (2020) Deep feature transfer learning for trusted and automated malware signature generation in private cloud environments. Neural Netw 124:243–257
Nair AK, Sahoo J, Raj ED (2023) Privacy preserving federated learning framework for IoMT based big data analysis using edge computing. Computer Standards & Interfaces 86:103720
Narayanan E, Muthukumar B (2022) A machine learning framework for providing data integrity and confidentiality for sensitive data cloud applications. Int J Syst Assur Eng Manag. https://doi.org/10.1007/s13198-022-01741-y,1-12
Nissim N, Lahav O, Cohen A, Elovici Y, Rokach L (2019) Volatile memory analysis using the MinHash method for efficient and secured detection of malware in private cloud. Comput Secur 87:101590
Oltsik J (2022) Technology perspectives from cybersecurity professionals. https://www.issa.org/ . Viewed 31 November 2023.
Pandey BK, Veeramanickam M, Ahmad S, Rodriguez C, Esenarro D (2023) ExpSSOA-deep maxout: Exponential shuffled shepherd optimization based deep maxout network for intrusion detection using big data in cloud computing framework. Comput Secur 124:102975
Parra GDLT, Rad P, Choo K-KR, Beebe N (2020) Detecting Internet of things attacks using distributed deep learning. J Netw Comput Appl 163:102662
PonemonInstitute (2024) Advancing responsible information management. https://www.ponemon.org/ , accessed 2 April 2024.
Prasad VM, Bharathi B (2022) A novel trust negotiation protocol for analysing and approving IoT edge computing devices using machine learning algorithm. Int J Comput Net Appl 9:712–723
Priya S, Maddikunta PKR, Parimala M, Koppu S, Gadekallu TR, Chowdhary CL, Alazab M (2020) An effective feature engineering for DNN using hybrid PCA-GWO for intrusion detection in IoMT architecture. Comput Commun 160:139–149
Quraishi SJ (2022) Machine learning approach for cloud computing security. In: Proceedings of the 3rd International Conference on Intelligent Engineering and Management (ICIEM), IEEE. London, United Kingdom, pp 158–163
Rahila S, Khonde S (2019) SAAS: Attack detection and prevention with forensic in cloud environment. Intl J Innov Technol Exploring Eng 9:1199–1203
Ramchandran A, Sangaiah AK (2020) Unsupervised deep learning system for local anomaly event detection in crowded scenes. Multimedia Tools Appl 79:35275–35295
Rao SM, Jain A (2024) Advances in malware analysis and detection in cloud computing environments: A review. Int J Safety Secur Eng 14:225
Rathore S, Kwon BW, Park JH (2019) BlockSecIoTNet: Blockchain-based decentralized security architecture for IoT network. J Netw Comput Appl 143:167–177
Ravi N, Shalinie SM (2020) Learning-driven detection and mitigation of DDoS attack in IoT via SDN-cloud architecture. IEEE Int Things J 7:3559–3570
Ravinder M, Kulkarni V (2023) A review on cyber security and anomaly detection perspectives of smart grid. In: Proceedings of the 5th international conference on smart systems and inventive technology (ICSSIT), IEEE. Tirunelveli, India, pp 692–697
Rjoub G, Bentahar J, Abdel Wahab O, Saleh Bataineh A (2021) Deep and reinforcement learning for automated task scheduling in large-scale cloud computing systems. Concurr Comput: Pract Experience 33:e5919
Rosero D, Díaz N, Trujillo C (2021) Cloud and machine learning experiments applied to the energy management in a microgrid cluster. Appl Energy 304:117770
Roy I, Modak R, Ghosh E, Rahaman SN, Chatterjee S, Majumder K, Shaw RN, Ghosh A (2023) A review on machine learning based security in edge computing environment. In Advanced Communication and Intelligent Systems. ICACIS 2023. Communications in Computer and Information Science, Shaw, R.N., Paprzycki, M., Ghosh, A., Eds.; Springer, Cham, 1921, 120–137.
Salem IE, Al-Saedi KH (2023) Enhancing cloud security through the integration of deep learning and data mining techniques: A comprehensive review. Period Eng Nat Sci 11:176–192
SANS (2024) The most trusted source for cyber security training, certification and research. https://www.sans.org/mlp/middle-east-turkey-africa/ , accessed 2 April 2024.
Saran M, Yadav RK, Tripathi UN (2022) Machine learning based security for cloud computing: A survey. Int J Appl Eng Res 17:332–337
Saranya T, Sridevi S, Deisy C, Chung TD, Khan MA (2020) Performance analysis of machine learning algorithms in intrusion detection system: A review. Proc Comput Sci 171:1251–1260
Sarker IH, Khan AI, Abushark YB, Alsolami F (2023) Internet of things (iot) security intelligence: A comprehensive overview, machine learning solutions and research directions. Mob Net Appl 28:296–312
Spitzner L (2022) SANS 2022 security awareness report. SANS. https://www.sans.org/blog/sans-2022-security-awareness-report/ . Viewed 14 December 2023.
Sugi SSS, Ratna SR (2020) A novel distributed training on fog node in IoT backbone networks for security. Soft Comput 24:18399–18410
Sweileh WM (2018) Research trends on human trafficking: A bibliometric analysis using Scopus database. Glob Health 14:106
Thakkar A, Lohiya R (2021) A review on machine learning and deep learning perspectives of IDS for IoT: recent updates, security issues, and challenges. Arch Comput Methods Eng 28:3211–3243
Thilagam T, Aruna R (2021) Intrusion detection for network based cloud computing by custom RC-NN and optimization. ICT Express 7:512–520
Tian Z, Luo C, Qiu J, Du X, Guizani M (2020) A distributed deep learning system for web attack detection on edge devices. IEEE Trans Industr Inf 16:1963–1971
Tian P, Chen Z, Yu W, Liao W (2021) Towards asynchronous federated learning based threat detection: A DC-Adam approach. Comput Secur 108:102344
Topcu AE, Alzoubi YI, Elbasi E, Camalan E (2023) Social media zero-day attack detection using TensorFlow. Electronics 12:3554
Tuli S, Basumatary N, Gill SS, Kahani M, Arya RC, Wander GS, Buyya R (2020) HealthFog: An ensemble deep learning based smart healthcare system for automatic diagnosis of heart diseases in integrated IoT and fog computing environments. Futur Gener Comput Syst 104:187–200
Ullah F, Srivastava G, Ullah S (2022) A malware detection system using a hybrid approach of multi-heads attention-based control flow traces and image visualization. J Cloud Comput 11:1–21
Vinolia A, Kanya N, Rajavarman V (2023) Machine learning and deep learning based intrusion detection in cloud environment: a review. In: Proceedings of the 5th International Conference on Smart Systems and Inventive Technology, IEEE. Tirunelveli, India, pp 952–960.
Vu L, Nguyen QU, Nguyen DN, Hoang DT, Dutkiewicz E (2022) Deep generative learning models for cloud intrusion detection systems. IEEE Trans Cybern 53:565–577
Wu M, Song Z, Moon YB (2019) Detecting cyber-physical attacks in CyberManufacturing systems with machine learning methods. J Intell Manuf 30:1111–1123
Wu H, Li X, Deng Y (2020) Deep learning-driven wireless communication for edge-cloud computing: opportunities and challenges. J Cloud Comput 9:1–14
Wu Z, Wang L, Xu Z, Li H, Yang J (2022) GPU virtualization technology and security issues: A survey. J Cyber Secur 7:30–58
Yao H, Gao P, Zhang P, Wang J, Jiang C, Lu L (2019) Hybrid intrusion detection system for edge-based IIoT relying on machine-learning-aided detection. IEEE Network 33:75–81
Yi T, Chen X, Zhu Y, Ge W, Han Z (2023) Review on the application of deep learning in network attack detection. J Netw Comput Appl 212:103580
Yıldız M (2023) History of machine learning. https://clarusway.com/history-of-machine-learning/ , accessed 6 January 2024.
Yu S, Chen X, Zhou Z, Gong X, Wu D (2021) When deep reinforcement learning meets federated learning: Intelligent multitimescale resource management for multiaccess edge computing in 5G ultradense network. IEEE Int Things J 8:2238–2251
Zhang L, Lai S, Xia J, Gao C, Fan D, Ou J (2022) Deep reinforcement learning based IRS-assisted mobile edge computing under physical-layer security. Physical Commun 55:101896
Zhou X, Xu X, Liang W, Zeng Z, Yan Z (2021) Deep-learning-enhanced multitarget detection for end–edge–cloud surveillance in smart IoT. IEEE Int Things J 8:12588–12596
Zhou Y, Wang R, Mo X, Li Z, Tang T (2023) Robust hierarchical federated learning with anomaly detection in cloud-edge-end cooperation networks. Electronics 12:112
Download references
Open access funding provided by NTNU Norwegian University of Science and Technology (incl St. Olavs Hospital - Trondheim University Hospital)
Author information
Authors and affiliations.
College of Business Administration, American University of the Middle East, Eqaila, Kuwait
Yehia Ibrahim Alzoubi
Faculty of Engineering, Norwegian University of Science and Technology (NTNU), Trondheim, Norway
Alok Mishra
College of Engineering and Technology, American University of the Middle East, Eqaila, Kuwait
Ahmet Ercan Topcu
You can also search for this author in PubMed Google Scholar
Contributions
Author Contributions: Y.A. conceptualized and presented the idea. A.T. developed the theoretical analysis. A.M. supervised the findings of this research. Y.A. took the lead in writing the manuscript with participation of A.T., and A. M. All authors provided critical feedback and help in finalizing the research, results discussion and contributed to the final manuscript. All authors reviewed the manuscript.
Corresponding author
Correspondence to Alok Mishra .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Alzoubi, Y.I., Mishra, A. & Topcu, A.E. Research trends in deep learning and machine learning for cloud computing security. Artif Intell Rev 57 , 132 (2024). https://doi.org/10.1007/s10462-024-10776-5
Download citation
Accepted : 24 April 2024
Published : 02 May 2024
DOI : https://doi.org/10.1007/s10462-024-10776-5
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Cloud security
- Deep learning
- Machine learning
- Cybersecurity
- Find a journal
- Publish with us
- Track your research
- Trustworthy AI
Our trust in technology relies on understanding how it works. It’s important to understand why AI makes the decisions it does. We’re developing tools to make AI more explainable, fair, robust, private, and transparent.
Tiny benchmarks for large language models
- Foundation Models
IBM’s Granite model is one of the most transparent LLMs in the world

- AI Transparency
- Open Source
What is red teaming for generative AI?
- Adversarial Robustness and Privacy
- Fairness, Accountability, Transparency
- Natural Language Processing
An AI model trained on data that looks real but won’t leak personal information
- Data and AI Security
The latest AI safety method is a throwback to our maritime past

- Explainable AI
- Generative AI
What is AI alignment?
- Automated AI
- See more of our work on Trustworthy AI
- AI Testing We’re designing tools to help ensure that AI systems are trustworthy, reliable and can optimize business processes.
- Adversarial Robustness and Privacy We’re making tools to protect AI and certify its robustness, and helping AI systems adhere to privacy requirements.
- Explainable AI We’re creating tools to help AI systems explain why they made the decisions they did.
- Fairness, Accountability, Transparency We’re developing technologies to increase the end-to-end transparency and fairness of AI systems.
- Trustworthy Generation We’re developing theoretical and algorithmic frameworks for generative AI to accelerate future scientific discoveries.
- Uncertainty Quantification We’re developing ways for AI to communicate when it's unsure of a decision across the AI application development lifecycle.

Science for Social Good
IBM Science for Social Good partners IBM Research scientists and engineers with academic fellows, subject matter experts from NGOs, public sector agencies, and social enterprises to tackle emerging societal challenges using science and technology.
Publications
- Andong Wang
- Cynthia Dwork
- Kristjan Greenewald
- Frank Libsch
- Steve Bedell
- Assala Benmalek
- Celia Cintas
- Leshem Choshen
- LREC-COLING 2024
Building trustworthy AI with Watson
Our research is regularly integrated into Watson solutions to make IBM’s AI for business more transparent, explainable, robust, private, and fair.

IMAGES
VIDEO
COMMENTS
We've compiled 15 important cloud computing research topics that are changing how cloud computing is used. 1. Big Data. Big data refers to the large amounts of data produced by various programs in a very short duration of time. It is quite cumbersome to store such huge and voluminous amounts of data in company-run data centers.
4. Blockchain data-based cloud data integrity protection mechanism. The "Blockchain data-based cloud data integrity protection mechanism" paper suggests a method for safeguarding the integrity of cloud data and which is one of the Cloud computing research topics. In order to store and process massive amounts of data, cloud computing has grown ...
Cloud Computing is gaining so much popularity an demand in the market. It is getting implemented in many organizations very fast. One of the major barriers for the cloud is real and perceived lack of security. There are many Cloud Computing Research Topics, which can be further taken to get the fruitful output.. In this tutorial, we are going to discuss 12 latest Cloud Computing Research Topics.
With the rapid development of cloud computing technology, cloud storage services are becoming more and more mature. However, the storage of sensitive data on remote servers poses privacy risks and is presently... Danial Shiraly, Ziba Eslami and Nasrollah Pakniat. Journal of Cloud Computing 2024 13 :112. Research Published on: 26 May 2024.
Here are ten research topics for cloud computing to look forward to in 2022 -. Cloud analytics. Cloud analytics is a cloud-related analytical tool that helps to analyze data and reduce data storage costs. It is used for research in genomics, exploring oil and gas reserves, business intelligence, Internet of Things (IoT) and cybersecurity.
Here are five themes that stood out to us from this brand-new research. 1. Cloud computing will move to the forefront of enterprise technology over the next decade, backed by strong executive support. Globally, 47 percent of survey participants said that the majority of their companies' IT infrastructures already use public or private cloud ...
The paper further compares and reviews different layout model for the discovery of services, selection of services and composition of services in Cloud computing. Recent research trends in service composition are identified and then research about microservices are evaluated and shown in the form of table and graphs. Download Full-text.
The Journal of Cloud Computing, Advances, Systems and Applications (JoCCASA) has been launched to offer a high quality journal geared entirely towards the research that will offer up future generations of Clouds. The journal publishes research that addresses the entire Cloud stack, and as relates Clouds to wider paradigms and topics.
We present a meta-analysis of cloud computing research in information systems. The study includes 152 referenced journal articles published between January 2010 to June 2023. We take stock of the literature and the associated research themes, research frameworks, the employed research methodology, and the geographical distribution of the articles.
Metrics. Since 2012, the Journal of Cloud Computing has been promoting research and technology development related to Cloud Computing, as an elastic framework for provisioning complex infrastructure services on-demand, including service models such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service ...
Cloud computing research started to gain recognition around 2009 and has seen considerable rise over the years. From 6 journal articles in year 2009, cloud computing research continues to rise yearly as there are over 200 journal articles currently. We predict that more studies will be conducted on cloud computing in the coming years.
About this book. This book addresses the emerging area of cloud computing, providing a comprehensive overview of the research areas, recent work and open research problems. The move to cloud computing is no longer merely a topic of discussion; it has become a core competency that every modern business needs to embrace and excel at.
Top 14 Cloud Computing Research Topics For 2022. 1. Green Cloud Computing. Due to rapid growth and demand for cloud, the energy consumption in data centers is increasing. Green Cloud Computing is used to minimize energy consumption and helps to achieve efficient processing and reduce the generation of E-waste.
3 Cloud Computing Continuum Research Topics and Challenges. The following is a brief description of the initial set of research themes and challenges. While the primary source of the research challenges is the analysis of research venues, it has been complemented by inputs from context analysis, surveys, interviews, and research projects.
1. Introduction. Cloud computing is a paradigm that provides on-demand computing resources such as storage, network, servers, databases, platforms, and so on as a service to its users via the internet, using a pay-as-you-go model [1], [2].Cloud computing has changed the way Micro, Small, and Medium Enterprises provide and use computing services.
October 2, 2023. Cloud computing enables new opportunities for growth and digitalization. It allows developers to build, test, deploy, and manage applications without an in-house infrastructure. Cloud industry expectations evolve as developers continue incorporating cloud services into their software development life cycle.
1. IT leaders are looking to the cloud to help prepare for whatever lies ahead. Due to the current macroeconomic climate, cloud leaders say they are increasing their use of cloud-based services and products (41.4%), planning to migrate from legacy enterprise software to cloud-based tools (33.4%), and migrating on-premises workloads to the cloud (32.8%).
review is thought to inspire enterprises and managers that would like to use cloud computing in. terms of the scope, solution methods, factors, dimensions, and the results achieved in a holistic ...
Cloud computing is the on-demand access of computing resources—physical servers or virtual servers, data storage, networking capabilities, application development tools, software, AI-powered analytic tools and more—over the internet with pay-per-use pricing. The cloud computing model offers customers greater flexibility and scalability ...
Cloud Computing Topics. Cloud computing is the process of offering resources and services depends the user demand in regardless of location. It is the computing system which classify under of these 3 service models of cloud. Platform as a Service (PAAS) - offers a well-established platform for developing the software / application.
Here is a list of curated cloud computing projects for all level skills, one should know in 2024: Cloud-enabled attendance system. Online blood bank system. Online cloud-enabled bookstore system. Data redundancy removal system. Detecting data leaks using SQL injection.
Cloud computing delivers numerous benefits, but only if an IT organization is prepared to manage a cloud environment. Proper cloud infrastructure design and management entails an understanding of automation, orchestration, monitoring, compliance, pricing, availability, and other key elements of cloud services. More about Cloud Infrastructure.
A key focus of mine is the advancement of collaborative, data-driven research in "the cloud", and my colleagues and I are determined to make access to and expertise in cloud computing more widely available across the NIH research community. Researchers today often face barriers when adopting and integrating cloud-based technologies.
Much of the information that can help transform enterprises is locked away in text, like documents, tables, and charts. We're building advanced AI systems that can parse vast bodies of text to help unlock that data, but also ones flexible enough to be applied to any language problem.
Innovations such as the distributed cloud, which merges cloud and telecommunications approaches, and the multi-access edge computing (MEC) market, which delivers services closer to the data source ...
2.1 Cloud computing. Cloud computing is an information services delivery model that makes resources available to users through the Internet as needed and on a pay-as-you-go basis (Alzoubi et al. 2022a).It makes it possible for users to acquire and use pooled computational resources, like storage, servers, and applications, without worrying about maintaining and managing those resources ...
By harnessing the might of PostgreSQL in the cloud—with all the scalability and convenience you expect—comes Microsoft Azure Database for PostgreSQL. This fully managed service takes the hassle out of managing your PostgreSQL instances, allowing you to focus on what really matters: building amazing, AI-powered applications.
At IBM Research, we're working on a range of approaches to ensure that AI systems built in the future are fair, robust, explainable, account, and align with the values of the society they're designed for. We're ensuring that in the future, AI applications are as fair as they are efficient across their entire lifecycle.
Azure Virtual Machines provide on-demand, scalable computing resources with a broad range of configurations to meet various workloads. Whether you need a single VM for development purposes or a cluster of VMs to run complex, large-scale applications, Azure offers a solution tailored to your requirements.
5. Amazon Web Services (AWS) Cloud Practitioner. Cloud computing, along with security, is one of the most in-demand fields in IT, and Amazon Web Services (AWS) is currently the most-used cloud platform in the world. So learning the AWS platform may give you an edge in this growing industry.