
Understanding MAC Addresses

In the vast and interconnected world of computer networks, communication between devices is a fundamental aspect. Each device connected to a network, be it a computer, Smartphone, or any other hardware, requires a unique identifier to facilitate communication and data exchange. One such crucial identifier is the MAC address. In this article, we’ll explore what MAC addresses are, their significance, how they work, and their role in network communication.
What is a MAC Address?
MAC, which stands for Media Access Control , is a unique identifier assigned to each network interface for communication on a network. Every device that connects to a network, whether wired or wireless, is equipped with a network interface card (NIC) or a similar component. The MAC address is a hardware address associated with this network interface and serves as a distinctive label for that specific device.
Media Access Control (MAC) 12-digit hexadecimal number
A device can have multiple MAC address. It operates at data link layer the OSI model’s
A MAC address, or Media Access Control address, is a 48-bit alphanumeric((0-9 and A-F) identifier commonly represented as six pairs of hexadecimal digits separated by colons(Six Octet, One Octet equals six bits) or hyphens (e.g., 00:1A:2B:3C:4D:5E). that serves as a unique hardware address for network interfaces. Written in six pairs of hexadecimal digits, the structure of a MAC address provides essential information about the device.
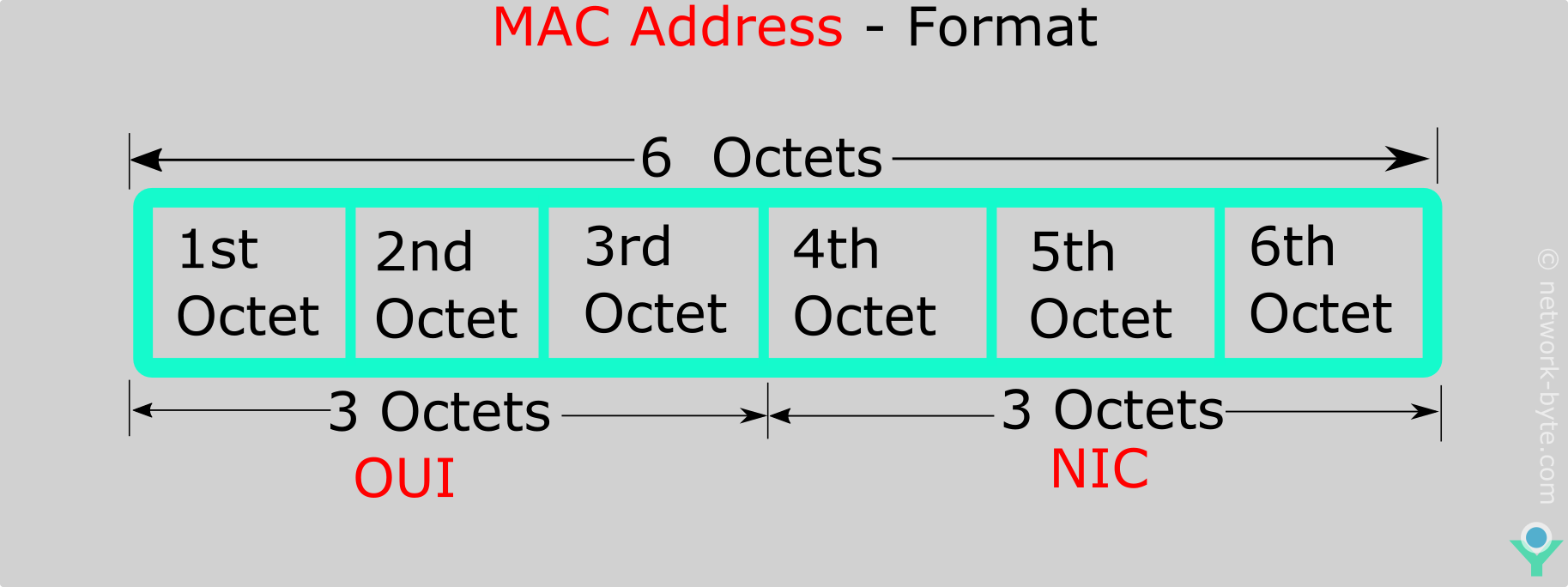
OUI (Organizationally Unique Identifier): The first three octets ,first half of the MAC address (24 Bits), typically the initial three pairs of hexadecimal digits, indicates the OUI, which identifies the manufacturer of the network interface card. This aspect aids in device recognition and troubleshooting.
Device Identifier: The last three octets, second half of the MAC address (24 Bits) represents a unique identifier assigned by the manufacturer to the specific network interface. NIC/vendor-specific information. Also called Universally Administered Address (UAA). This ensures global uniqueness among MAC addresses, preventing conflicts within a network.
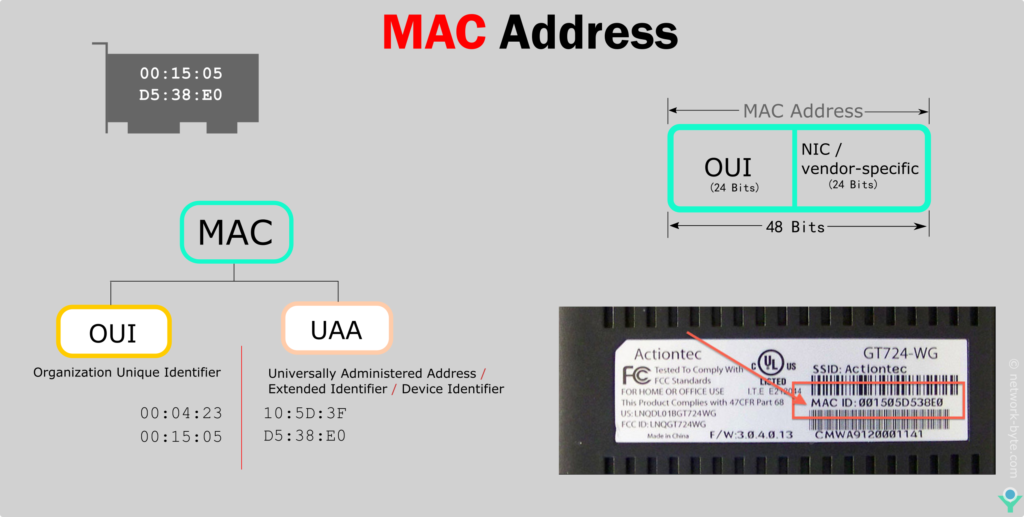
For example, in the MAC address “00:04:23:10:5D:3F,” the “00:04:23” portion might identify the manufacturer, while the “10:5D:3F” portion uniquely identifies the device.
IEEE Registration Authority Committee assigns these MAC prefixes to its registered vendors.
Media Access Control, also known as Physical Address, Hardware Address, or BIA, is an acronym for Media Access Control (Burned In Address)
Here are OUIs for some well-known manufacturers:
You can find an official and updated list of OUI assignments from the Institute of Electrical and Electronics Engineers (IEEE).
The MAC address can be represented in one below formats:
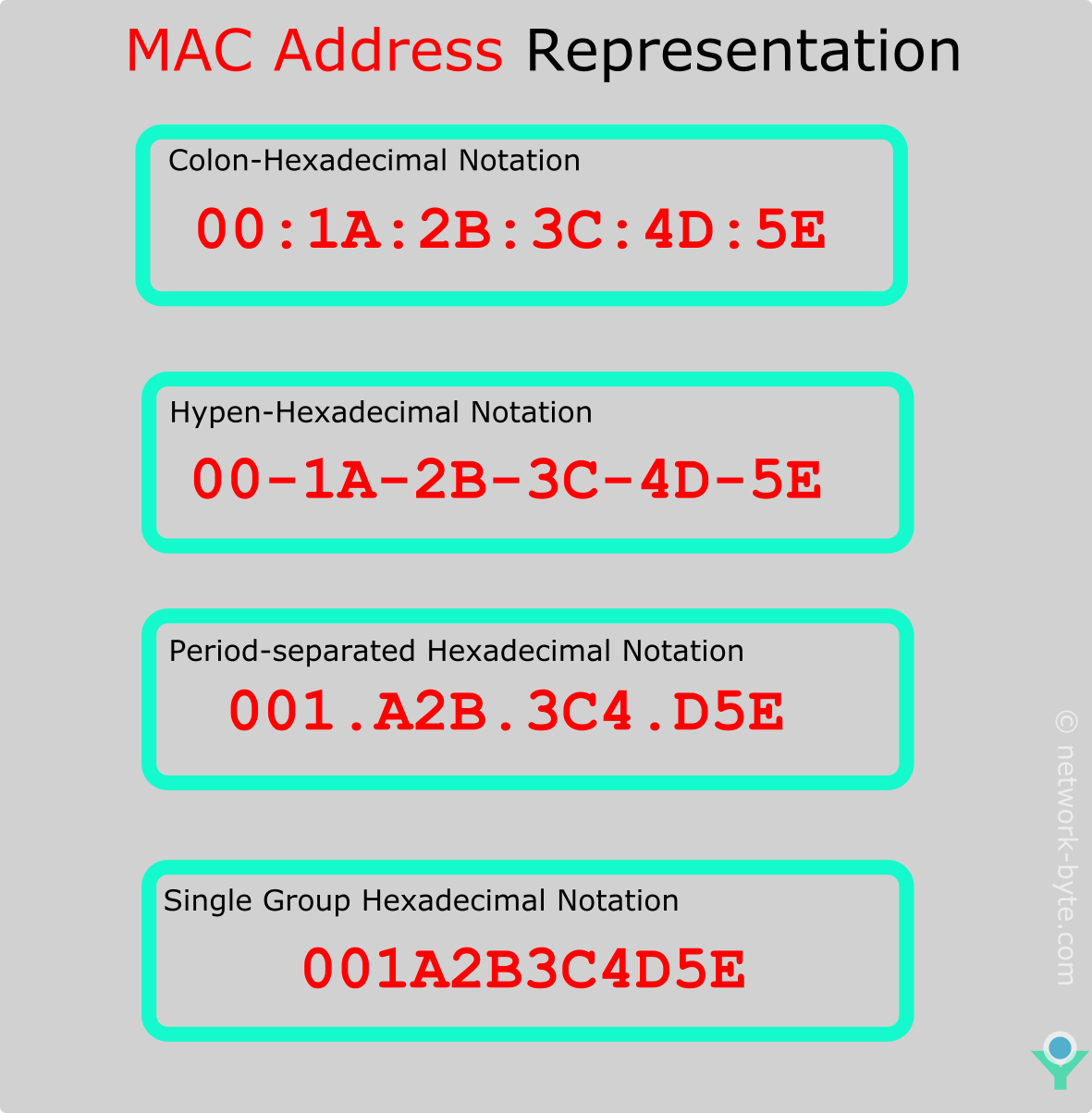
You can find one of the above format MAC address. Colon-Hexadecimal notation is used by Linux OS ( 00:1A:2B:3C:4D:5E ) Period-separated Hexadecimal notation is used by Cisco Systems (001.A2B.3C4.D5E)
1. Uniqueness: The most critical aspect of MAC addresses is their uniqueness. No two devices on a network should have the same MAC address. This ensures that data is sent to the correct device, preventing confusion and ensuring the integrity of network communication.
2. Device Identification: MAC addresses play a crucial role in identifying and differentiating devices on a network. Whether it’s a computer in a local area network (LAN) or a smart phone connecting to a Wi-Fi network, the MAC address helps routers and switches determine the destination of data packets.
3. Network Security: MAC addresses are also used in network security protocols. Access control lists (ACLs) can be configured on routers and switches to allow or deny access based on the MAC address of a device. This feature is commonly employed in enterprise networks to enhance security.
The MAC address belongs to the data link layer of the Open Systems Interconnection (OSI) model.The data Link layer is divided into two sublayers.
1.Logical Link Control (LLC) Sublayer 2.Media Access Control (MAC) Sublayer
Media Access Control (MAC) Sublayer which encapsulates the MAC address of the source and destination in the header of each data frame to ensure node-to-node communication.
How Do I Find the MAC Address?
Types of MAC Address
MAC addresses, or Media Access Control addresses, can be categorized into several types based on their characteristics and usage. Here are the primary types of MAC addresses used in layer 2:
This is the most common type of MAC address. It represents a unique identifier for a specific network interface card (NIC) or network interface controller (NIC).
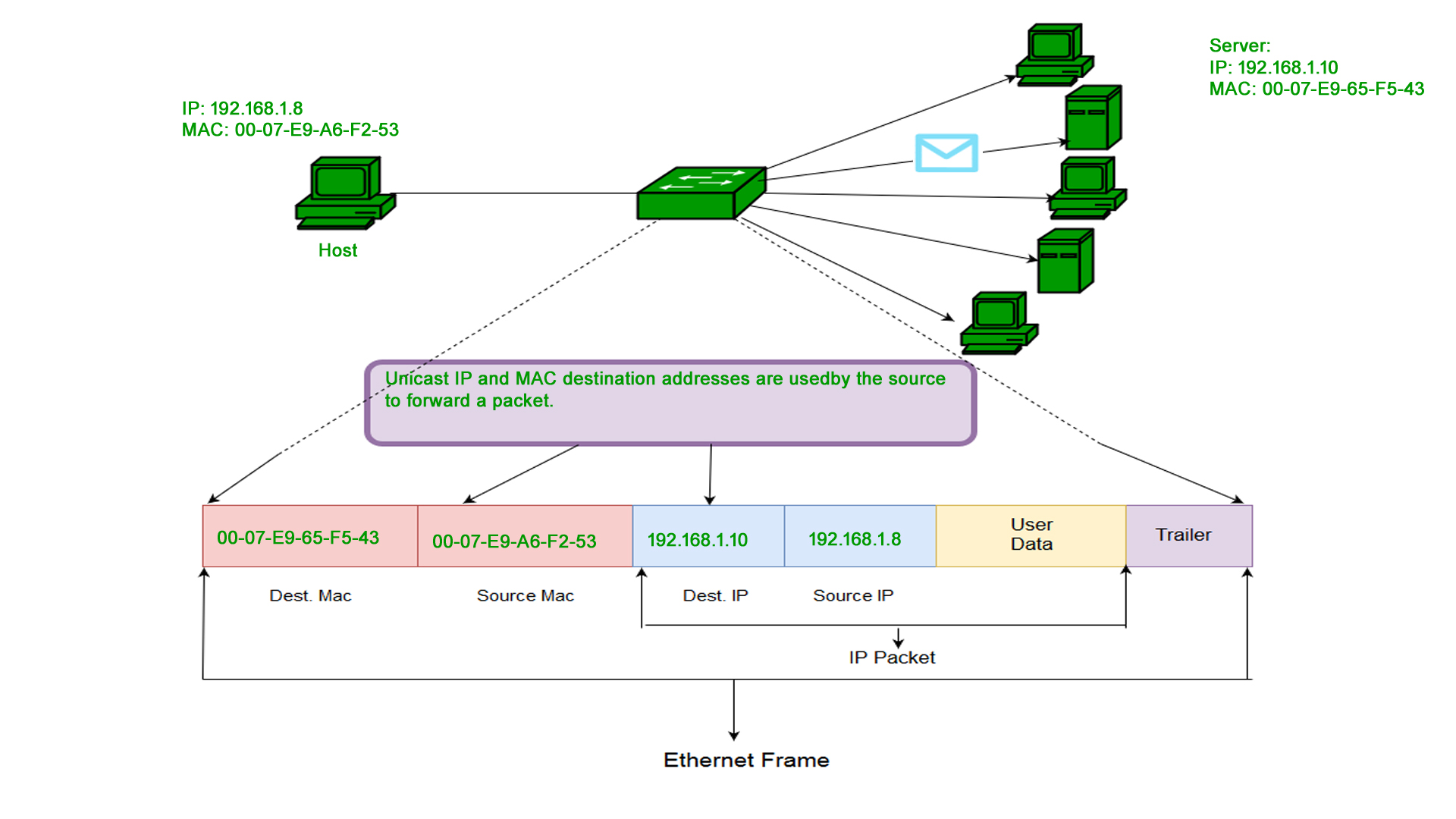
Usage: Unicast addresses are used for point-to-point communication between two devices on a network. When a device wants to send data to another specific device, it uses the unicast MAC address of the destination device.
A network switch fill mac address table it actually adds unicast mac addresses and maps them to specific port when it receive some frame from different port.
In above figure host(H1) with IPv4 address 192.168.1.10 (Source) and corresponding MAC address 00:04:23:34:5F:F2 request a service from host(H3) at IPv4 unicast address 192.168.1.12 and corresponding MAC address 00:04:23:10:5D:5F .At L2 layer switch Lookup its CAM/MAC Table for exit interface( GE0/3) and forward the ethernet frame.
We put IP address on host how host find corresponding MAC address?
A Source host determine the destination host MAC address associated with an IPv4 address is known as ARP(Address Resolution Protocol) The process that a source host uses to determine the destination MAC address associated with an IPv6 address is known as Neighbor Discovery(ND) .
The MAC address table consists of two types of entries. Dynamic and Static MAC Addresses
- Dynamic MAC Addresses (Learned Addresses): In dynamic environments, devices are often assigned dynamic MAC addresses during network interactions. This dynamic assignment is common in DHCP (Dynamic Host Configuration Protocol) scenarios, where devices receive temporary MAC addresses for the duration of their connection.
- Static MAC Addresses (Configured Addresses): For critical networking infrastructure and security protocols, static MAC addresses are manually assigned and remain constant. This stability is advantageous in scenarios where specific devices need consistent addressing, such as in virtualization environments.
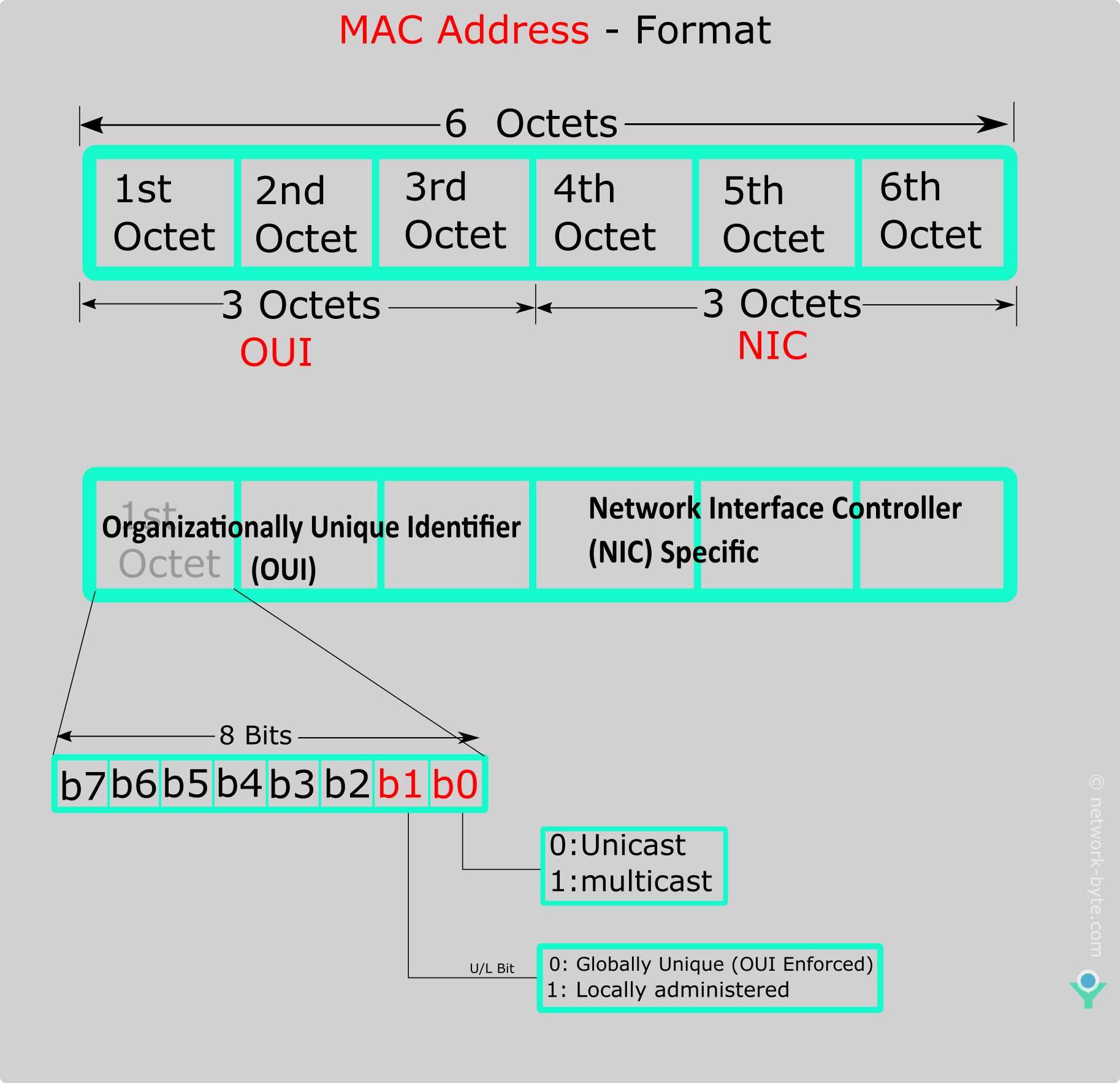
If the LSB (least significant bit) of the first octet of an address is set to zero , the frame is meant to reach only one receiving NIC.
MAC Address of the source machine is always Unicast
The 2nd bit(b1) (least significant bit) of the first octet of a MAC (Media Access Control) address, also known as the U/L ( Universal/Local ) bit, signifies whether the MAC address is universally administered (globally unique) or locally administered (locally assigned). This bit is located in the first octet (most significant byte) of the MAC address. U/L Bit Value 0 (Unicast): If the U/L bit is set to 0, it indicates that the MAC address is universally administered. This means that the MAC address is globally unique and assigned by the IEEE Registration Authority to a specific hardware manufacturer. U/L Bit Value 1 (Locally Administered): If the U/L bit is set to 1, it indicates that the MAC address is locally administered. This means that the MAC address is assigned by the network administrator or user and may not be globally unique. Locally administered MAC addresses are often used in testing or in cases where the device doesn’t have a permanent, globally unique MAC address.
Example of Locally Administered : Simulator interface of switches and router are Locally administrated
EUI-64 is a specific format commonly used in IPv6 addressing for interface ID where 2 nd bit (LSB) converted to 1
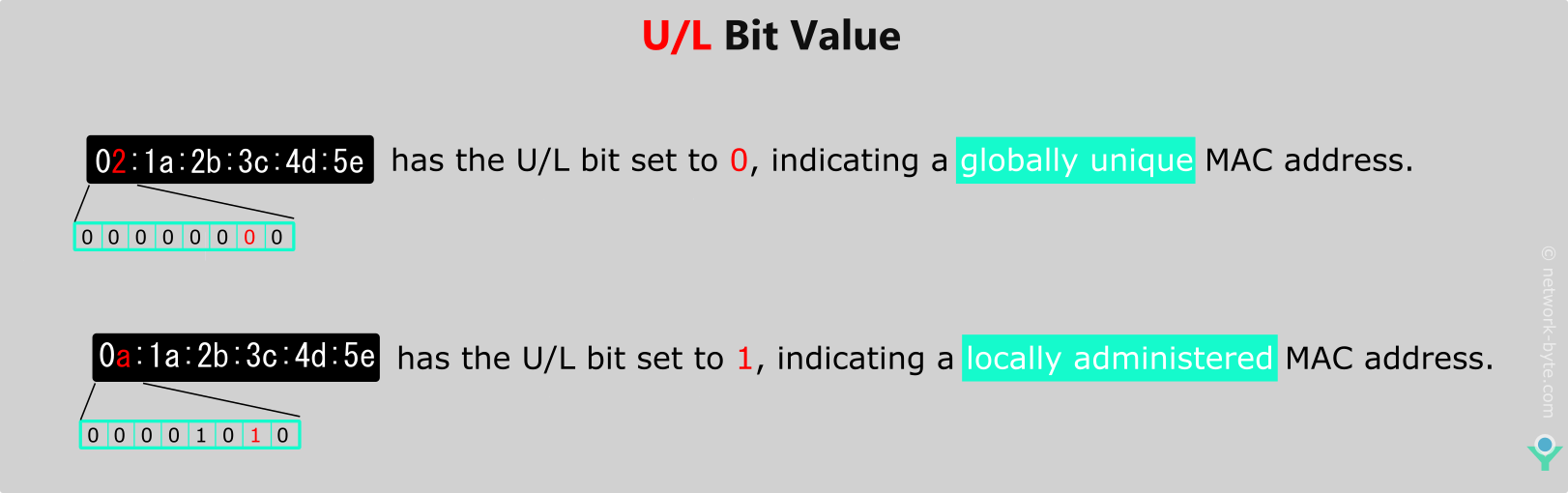
Understanding the U/L bit is important for recognizing the origin and uniqueness characteristics of MAC addresses, especially in networking contexts where the uniqueness of MAC addresses is crucial for proper device identification and communication.
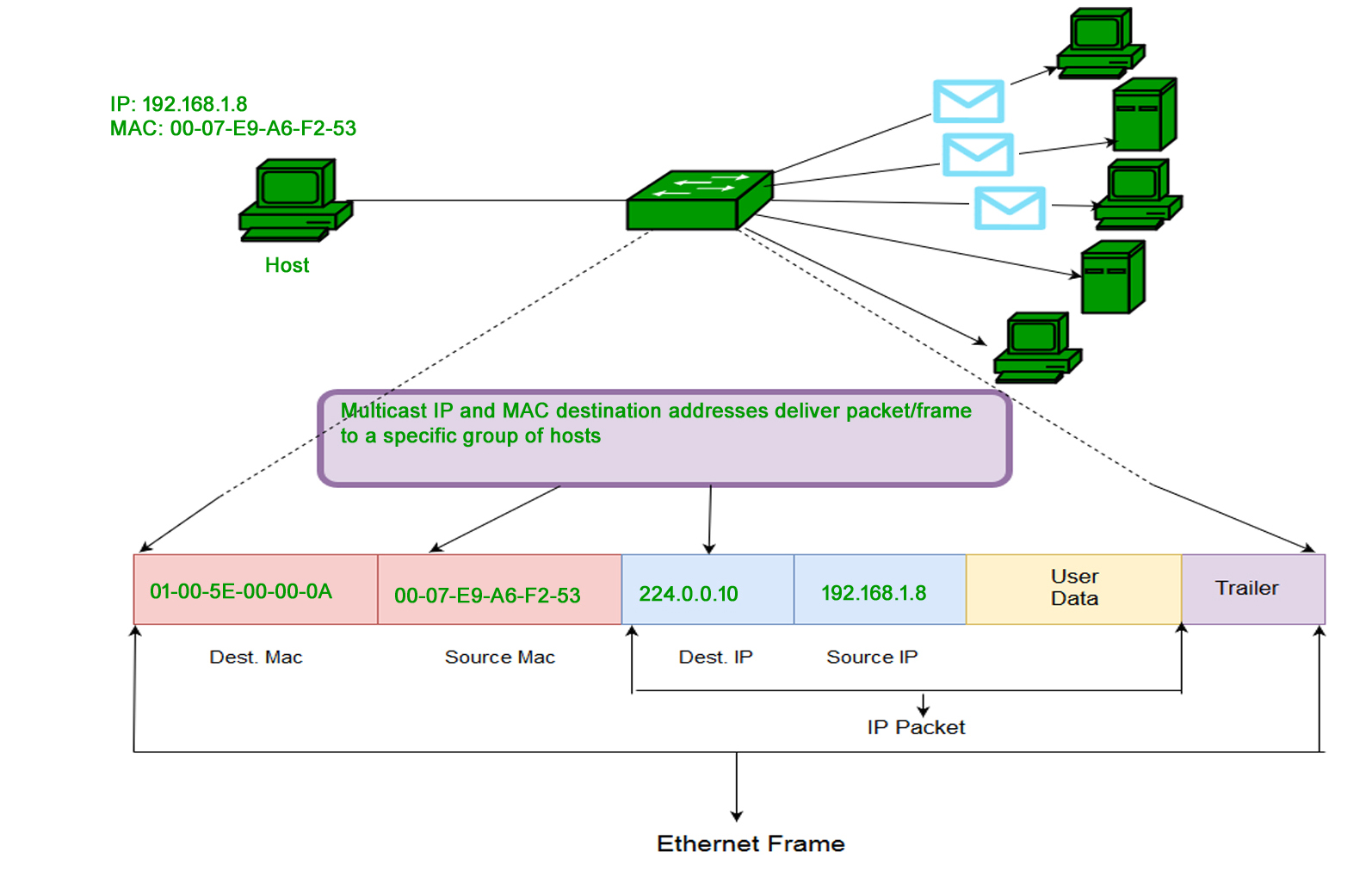
Multicast addresses are used for communication with a group of devices. Frames sent to a multicast address are received by all devices in the multicast group.
Usage: Multicast addresses are often used in multimedia streaming, online gaming, and other applications where data needs to be sent to multiple devices simultaneously. That reduces the waste of bandwidth.
In such case several devices may register to receive specific stream and sender may send only one stream to destination multicast mac address of course in such case destination IP address will be also multicast and it will be actually mapped to destination multicast mac address
In above figure Host(H1) with IPv4 address 192.168.1.10 (Source) and corresponding MAC address 00:04:23:34:5F:F2 .Service request from group of device i.e. Host(H3),Host(H4) at IPv4 multicast address 224.0.0.10 and corresponding multicast MAC address 01:00:5E:00:00:C8
It broadcast all the ethernet switch port (Here, GE0/2, GE0/3, GE0/4) except incoming port(GE0/1) if multicast is not enable(Multicast snooping).Also multicast packet is not forwarded by router unless multicast enabled.
Here, Switch is Multicast enable(IGMP Snooping) then it broadcast to interested group (GE0/2,GE0/3) port.
Multicast MAC address 33-33 are reserved for IPv6 (Range 33:33:00:00:00:00 to 33:33:FF:FF:FF:FF) and range of IPv6 multicast address begin with ff00::/8. It can only be used as the destination of packet, Source packet is always unicast.
Here demonstrated some kind of multicast mac address here it is always start with 01:00:5e first bit in second section is always 0
Here, is an example of multicast MAC address 01:00:5e:3C:22:01
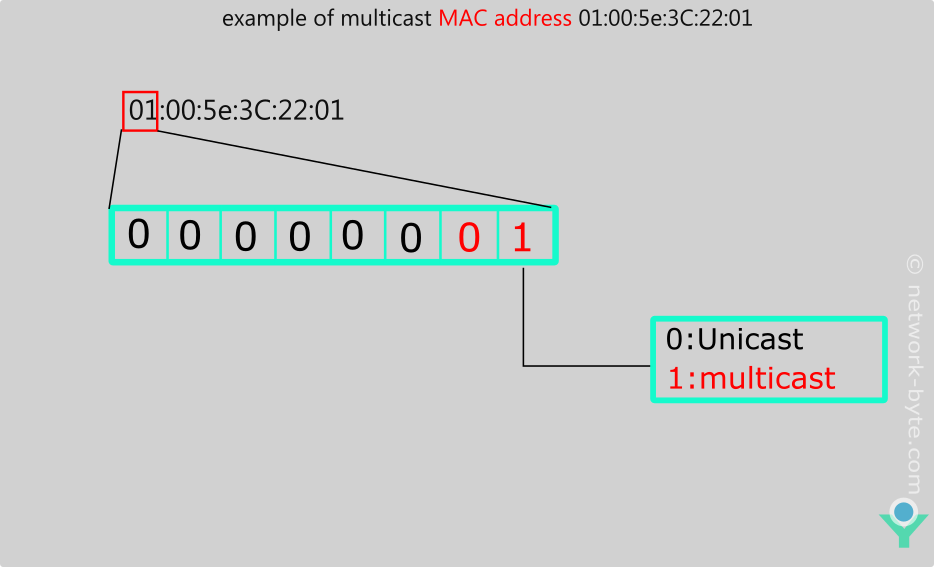
Of course multicast mac address can be only used as destination Mac address if switch will detect source mac address set to multicast address of course such frame will be simply discarded. If 2 nd Hexa decimal number is Even then Mac address is Unicast If 2 nd Hexa decimal number is odd then Mac address is Multicast
How to Convert Multicast IP Address into Multicast MAC Address?
The broadcast MAC address is a special type that is used for communication with all devices on a network. Usage: When a device sends data to the broadcast address, the information is broadcasted to all devices within the same network. This is commonly used for tasks like network discovery or when a device needs to communicate with all devices on the local network.
In above figure host(H1) with IPv4 address 192.168.1.10 (Source) and corresponding MAC address 00:04:23:34:5F:F2 and destination MAC address(FF:FF:FF:FF:FF:FF) in hexadecimal or 48 1’s in binary and destination IP address(192.168.1.255) that has 1’s(binary) in host portion (255 in decimal) are both broadcast address.
It broadcast all the ethernet switch port (Here, GE0/2, GE0/3, GE0/4) except incoming port(GE0/1). It is not forwarded by router.
Anycast is a communication paradigm where data is sent to the nearest of a group of potential receivers, all identified by the same destination address. Usage: While more commonly associated with IPv6 addressing, this directly doesn’t involve a specific anycast MAC address rather, the MAC address would be the unicast MAC address associated with the particular network interface. In specific context or application Anycast can also be applied at the MAC layer for certain specialized purposes, typically in large-scale and distributed network architectures.
This is a special mode in which a network interface card accepts all frames on the network, regardless of the destination MAC address.
Usage: Promiscuous mode is often used for network monitoring and packet sniffing. It allows a network analyzer to capture and analyze all network traffic passing through a network interface.
How to Find MAC Table?
Why do we need both an IP address and a MAC address ?
Both IP addresses and MAC addresses play crucial roles in networking, and they serve different purposes. Having both addresses is necessary for the proper functioning and communication within a network. Here’s why both IP addresses and MAC addresses are required:
- Addressing at Different Layers: MAC Address (Data Link Layer – Layer 2): Used for local addressing within the same network segment. MAC addresses are hardware addresses associated with network interfaces and are used to deliver frames within the local network. IP Address (Network Layer – Layer 3): Used for logical addressing and routing across different networks. IP addresses are assigned to devices and enable communication between devices on different networks.
- Routing and Network Layer Functionality: MAC Address: Primarily used for frame delivery within the same local network segment. Routers operate at the Network Layer (Layer 3) and use IP addresses to route packets between different networks. IP Address: Enables communication between devices on different networks. IP addresses facilitate logical addressing, subnetting, and routing, allowing data to traverse multiple network segments.
- Scalability and Flexibility: MAC Address: Tied to the physical network interface and assigned by the manufacturer. Not easily changed and doesn’t scale well for large networks or network reconfigurations. IP Address: Dynamically assigned using protocols like DHCP, allowing for easier scalability, network management, and adaptability to changes in network topology.
- Device Identification and Communication: MAC Address: Identifies network interfaces uniquely within the same local network. Necessary for delivering frames to the correct device on the local segment. IP Address: Identifies devices globally on the Internet and facilitates communication across different networks. Essential for end-to-end communication in a larger network environment.
- Protocols and Network Stack: MAC Address: Pertinent to the data link layer protocols, such as Ethernet. IP Address: Integral to the network layer protocols, including IPv4 and IPv6.
- Communication on the Internet: MAC Address: Not used for communication across the Internet. MAC addresses are specific to local network segments. IP Address: Essential for communication across the Internet. Packets are routed based on IP addresses, allowing global connectivity.
- Layered Networking Model: MAC Address: Corresponds to the Data Link Layer (Layer 2) in the OSI model. IP Address: Corresponds to the Network Layer (Layer 3) in the OSI model.
In summary , the combination of IP addresses and MAC addresses ensures efficient and flexible communication within and between networks. While MAC addresses are crucial for local frame delivery within the same network, IP addresses enable end-to-end communication across diverse networks, providing the scalability and flexibility needed for modern networking.
What is the difference between a MAC address vs. IP address ?
MAC addresses and IP addresses serve different purposes in networking, and they operate at different layers of the OSI model. Here are the key differences between MAC addresses and IP addresses:
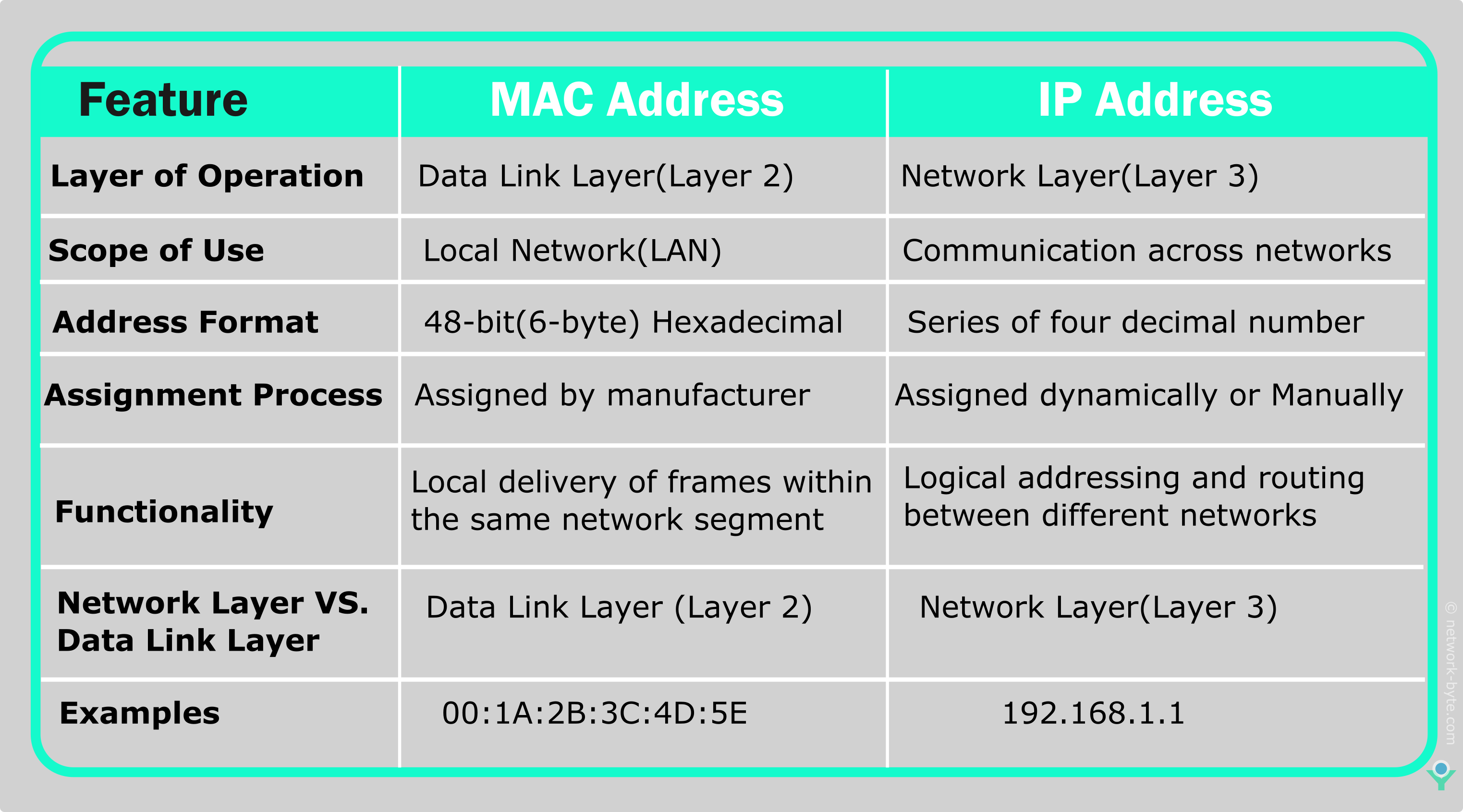
This table summarizes the key differences between MAC addresses and IP addresses in terms of their layer of operation, scope of use, address format, assignment process, functionality, and examples.
Please Share This Share this content
- Opens in a new window
You Might Also Like

TCP/IP MODEL

Achieve Wire-Speed – Forwarding performance and switching capacity

Transmission Modes

Network Devices

How to Find MAC Table

Unicast-Broadcast-Multicast-Anycast
Leave a reply cancel reply.
Save my name, email, and website in this browser for the next time I comment.
Understanding MAC Addresses
Last updated: March 18, 2024
1. Introduction
Nowadays, multiple organizations produce, distribute, and sell network-related hardware, such as wireless or Ethernet cards. Eventually, such hardware will operate on a computer, enabling it to communicate over a network. So, once it happens, the question is: how to identify which hardware is involved in a particular networked communication?
Media Access Control (MAC) addresses are the key to answering the previous question. These addresses uniquely differentiate a network device in a network. However, MAC follows a specific protocol and considers several technical details to create an address: it is not so simple.
In this way, this tutorial explores MAC addresses. First, we’ll study basic concepts about MAC. Thus, we’ll understand the format of MAC addresses, investigating the meaning of each field of it. So, we’ll have some insights into the difference between MAC and IP addresses. Finally, we’ll have some final remarks.
2. The Basics of MAC
Media Access Control (MAC) is a resource that determines addresses for network hardware. These addresses are unique. In such a way, we can state that no two devices in the world share the same MAC address. It enables us to precisely determine which hardware component generated a frame traversing a network as well as which hardware component is supposed to receive it.
It is relevant to highlight that MAC refers to a physical address. In fact, it is a physical address in all meanings: besides setting it up logically in a hardware component, it is also burned in every Network Interface Card (NIC).
In modern networking, we use MAC addresses in the second layer of the OSI model (particularly in the MAC sublayer) and the first layer of the TCP/IP model. Thus, we can say that we’ll work with MAC addresses in the layer immediately before the network layer, regardless of the adopted model.
3. Deep Dive Into MAC Addresses
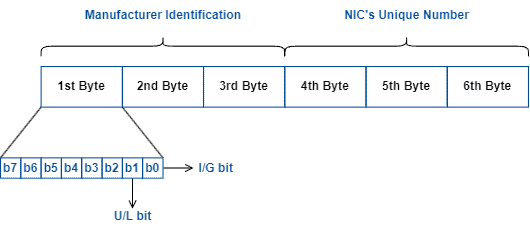
MAC addresses are formed by six bytes containing hexadecimal numbers. So, for each byte, we’ll have a two-digit number. Each digit, in turn, can have values from zero (0) to nine (9) and from A (10) to F (15).
Furthermore, there exist two major parts in MAC addresses: the manufacturer identification (first three bytes) and a unique number defined by the manufacturer that identifies a particular device in a network (last three bytes).
In the first byte of the first part of a MAC address, we have two special bits: the first and the second. The very first bit, called bit zero or I/G bit, determines if an address is unicast or multicast.
Computers define this bit when sending a frame through the network. If the I/G bit is zero (0), we have a unicast address, and the frame has a single destination. So, a NIC will accept the frame only if the destination MAC of it perfectly matches the NIC’s. Otherwise, if the I/G bit is one (1), we have a multicast address. Thus, a NIC can accept the frame based on another criterion, such as using a multicast address list.
The second bit, called bit one or U/L bit, defines if an address is universally or locally administered. A universally administered address is the one assigned by the NIC’s manufacturer. A locally administered address, in turn, consists of MAC addresses defined by software or operators of a system, overriding the address burnt in the physical hardware.
In this way, we can understand the MAC address formatting as depicted in the following figure:
Moreover, it is interesting to highlight that the way to format MAC addresses for human reading may vary according to which system shows it. For example, Windows-based systems format MAC addresses with double digits intercalated with dashes (xx-xx-xx-xx-xx-xx); Apple and Linux use colons to separate double digits (xx:xx:xx:xx:xx:xx), and CISCO show these addresses with sets of four digits separated by periods (xxxx.xxxx.xxxx).
4. MAC Addresses vs. IP Addresses
Until now, we know that MAC addresses identify a particular device in a network. So, we naturally can use MAC addresses to enable a device to communicate with other devices. It occurs indeed: the frame header carries a source and a destination MAC address.
But, if MAC addresses enable devices to communicate with each other and uniquely identify a network device, the question is: why do we also have IP addresses ?
In the previously described conditions, an IP address has a similar purpose to a MAC address: identify a networked entity, enabling it to communicate with other networked entities. However, IP has two particular characteristics that differentiate it from MAC:
- An IP address identifies a networked entity, not a device (it is related to the location of a device, not the device itself)
- IP addresses can change over time
Let’s work with an analogy to understand better the differences and relations between IP and MAC: we are sending a letter to a friend. So, for both sender and recipient, we must include a name and an address. With the recipient’s address, the postman knows where to take the letter. However, the address does not define who lives there. Thus, the postman uses the recipient’s name to deliver the letter to the correct person at the provided address.
In the same scenario, our friends can sometimes move from one house to another, which will change the recipients’ addresses of our letters. But moving home does not implicate changing names. So, the recipients’ names of our letters are still the same.
In such an analogy, the MAC addresses are the recipients’ names (identify a particular device and never change), and the IP addresses are the recipients’ addresses (identify an entity and can change over time). These are the main differences and relations between MAC and IP.
4.1. How MAC and IP Technically Relate in Data Exchanging?
As we already saw, MAC and IP address messages from a source to a destination. However, only networked entities in the same local network (or group) know the MAC address of a particular device.
In such a way, a message must arrive at the destination’s network using IP. Then, it is addressed and forwarded to the final destination using MAC. Summarily, the destination MAC changes each hop in a router or computer a message does, but the destination IP never changes along the transmission.
Let’s consider a scenario in which a computer (#01) aims to communicate with another one (#02). These machines are in different networks, as shown in the following figure:
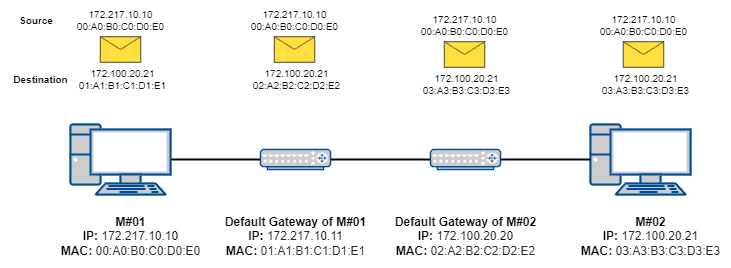
Thus, as the first machine does not know the MAC address of the second machine, it sets up the second machine’s IP address and sends the message to its default gateway, which will try to reach the proper network to forward the message.
The default gateway of the first machine does not know the MAC address of the second machine. However, they know how to reach a gateway of the destination network. So, it changes the destination MAC address to the destination network’s gateway one and forwards the message.
The gateway of the destination network receives the message. It knows the MAC address related to the destination IP address, setting it up in the MAC destination field and forwarding the message to the proper network device of the second machine.
5. Conclusion
In this tutorial, we explored MAC addresses. First, we briefly reviewed the basic concepts and characteristics of MAC. So, we studied the formatting of MAC addresses and the purpose of the main fields of it. Finally, we investigated the differences and relations between MAC and IP addresses.
We can conclude that MAC, with other protocols, bases modern networking. MAC addresses identify network devices, enabling them to communicate with each other in a local group or network by sending and receiving messages.
What are a universal address and a local administered address?
A MAC address is called a universally administered address (UAA) when it's set by the manufacturer or a locally administered addresses (LAA) when it's assigned by the system administrator.
For a universally administered address, the first three octets (in transmission order) identify the organization that issued the identifier and are known as the Organizationally Unique Identifier (OUI). The following three (MAC-48 and EUI-48) or five (EUI-64) octets are assigned by that organization in nearly any manner possible, subject to the constraint of uniqueness.
The IEEE has a target lifetime of 100 years for applications using MAC-48 space, but it encourages the adoption of EUI-64s instead.
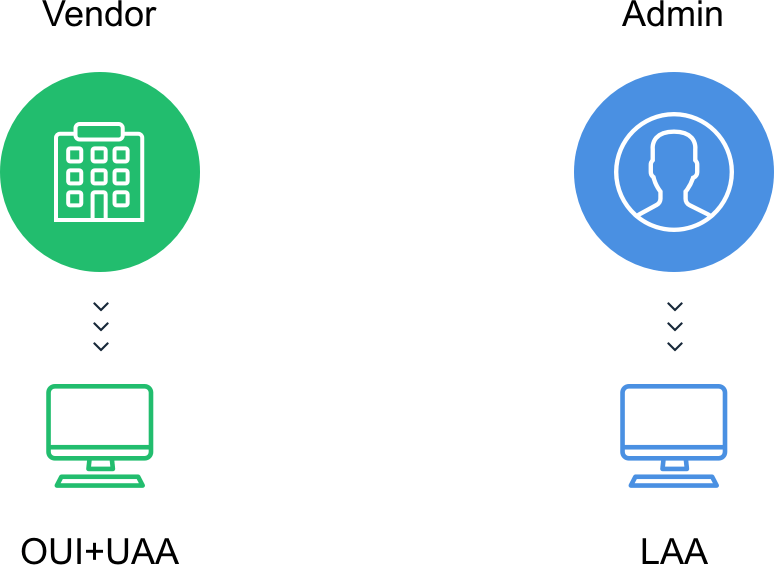
A locally administered address is assigned to a device by a network administrator, overriding the burned-in address. Locally administered addresses do not contain OUIs.
Universally administered and locally administered addresses are distinguished by setting the second-least-significant bit of the most significant byte of the address. This bit is also referred to as the U/L bit, short for Universal/Local, which identifies how the address is administered.
If the bit is 0, the address is administered universally. If it is 1, the address is administered locally. In the example address 06-00-00-00-00-00 the most significant byte is 06 (hex), the binary form of which is 00000110, where the second least significant bit is 1. Therefore, it is a locally administered address. Consequently, this bit is 0 in all OUIs.
More questions
- MAC address randomization in WiFi probe requests
- How to recognise a Microsoft Hyper-V's virtual machine by its MAC address?
- How to recognise a Virtual Router ID by MAC address?
Trusted by the following companies

and many more...
Download an exhaustive MAC Address Vendor Database for your educational, business or enterprise needs.
Our database comes in the following forms: JSON, CSV, XML, Cisco vendorMacs.xml for maximum compatibility and fast integration into existing systems. The API version is also available.
- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture
- CCNA Tutorial for Beginners
Basics of Computer Networking
- Network and Communication
- LAN Full Form
- What is OSI Model? - Layers of OSI Model
- TCP/IP Model
- How Data Encapsulation and De-encapsulation Works?
Components of Computer Networking
- NIC Full Form
- What is a network switch, and how does it work?
- What is Network Hub and How it Works?
- Introduction of a Router
- Types of Ethernet Cable
Transport Layer
- Transport Layer responsibilities
- Introduction of Ports in Computers
- What is Transmission Control Protocol (TCP)?
- TCP 3-Way Handshake Process
- User Datagram Protocol (UDP)
Network Layer
- Introduction and IPv4 Datagram Header
- Difference between Unicast, Broadcast and Multicast in Computer Network
- Structure and Types of IP Address
IPv4 Addressing
- What is IPv4?
- Role of Subnet Mask
- Introduction of Classful IP Addressing
- Introduction To Subnetting
- Classless Inter Domain Routing (CIDR)
- Introduction of Variable Length Subnet Mask (VLSM)
- Private IP Addresses in Networking
Data Link Layer
- What is Ethernet?
What is MAC Address?
- What is an IP Address?
Physical Layer
- Ethernet Frame Format
- What is Power Over Ethernet (POE)?
Cisco Networking Devices
- Network Devices (Hub, Repeater, Bridge, Switch, Router, Gateways and Brouter)
- Collision Detection in CSMA/CD
- Collision Domain and Broadcast Domain in Computer Network
- Difference between layer-2 and layer-3 switches
Life of a Packet
- Working of Domain Name System (DNS) Server
- Configuring DHCP and Web Server in Cisco Packet Tracer
- How Address Resolution Protocol (ARP) works?
Router and Switch Basic Configuration
- Cisco Router basic commands
- Configure IP Address for Interface in Cisco Switches
- Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex)
- Link Layer Discovery Protocol (LLDP)
- What is Cisco Discovery Protocol (CDP)?
Cisco Device Management
- What are the different memories used in a CISCO router?
- Router Boot Sequence
- Recovering password in Cisco Routers
- Catalyst Switch Password Reset in Cisco
- Process of Backing Up and Restoring the Cisco IOS
- File Transfer Protocol (FTP)
- Difference between FTP and TFTP
- Backing up Cisco IOS Router image
- Steps Involves in Cisco Router Configuration Backups
Basic Network Trouble shooting
- Troubleshooting Questions on OS and Networking asked in Cloud based Interview
- Internet Control Message Protocol (ICMP)
- What is Ping?
- traceroute Command in Linux with Examples
IPv4 Routing
- What is IP Routing?
- Routing Tables in Computer Network
- Difference between Static and Dynamic Routing
- What is Floating Static Route ?
- How to Add a Static Route to Windows Routing Table?
Dynamic Routing Protocols
- Routing Protocol Code
- Difference between IGRP and BGP
- Administrative Distance (AD) and Autonomous System (AS)
- Configuring a Loopback Interface in Cisco
- What is a Loopback Address?
- What is Passive-Interface Command Behavior in RIP, EIGRP & OSPF?
Interior Gateway Protocols
- Routing Information Protocol (RIP)
- Configuring RIP Default Information Originate in Cisco
- Configuring RIP Versions 1 and 2 in Cisco
- EIGRP fundamentals
- Features of Enhanced Interior Gateway Routing Protocol (EIGRP)
- Types of EIGRP Packet in Computer Network
- How to Configure EIGRP Summarization in Cisco?
Open Shortest Path First(OSPF)
- Open shortest path first (OSPF) router roles and configuration
- Difference between EIGRP and OSPF
- Bandwidth Allocation Control Protocol (BACP)
- Open shortest path first (OSPF) - Set 2
- OSPF Implementation
- Explain OSPF DR/BDR Election?
- Configuring OSPF Passive Interface in Cisco
- Configuring OSPF Default Route Propagation
- Configuring OSPF Maximum Paths
- Configuring OSPF Route Summarization in Cisco
- Configuring OSPF Network Types in Cisco
Virtual Local Area Network(VLAN)
- Three-Layer Hierarchical Model in Cisco
- 2 - Tier And 3 - Tier Architecture in Networking
- Spine-Leaf Architecture
- Virtual LAN (VLAN)
- Configuring and Verifying VLANs in Cisco
- Access and Trunk Ports
- What is ISL(Inter-Switch Link)?
- Inter-Switch Link (ISL) and IEEE 802.1Q
- Access Ports (Data and Voice) in CCNA
- Dynamic Trunking Protocol (DTP)
- VLAN Trunking Protocol (VTP)
- What are the VTP Modes?
Inter-V LAN Routing
- Inter VLAN Routing by Layer 3 Switch
- Configuration of Router on a stick
Dynamic Host Control Protocol(DHCP)
- Difference between DNS and DHCP
- How to Configure DHCP Server on a Cisco Router?
- DHCP Relay Agent in Computer Network
- What is APIPA (Automatic Private IP Addressing)?
Hot Standby Routing Protocol(HSRP)
- Redundant Link problems in Computer Network
- Firsthop Redundancy Protocol
- Hot Standby Router Protocol (HSRP)
Spanning Tree Protocol(STP)
- Introduction of Spanning Tree Protocol (STP)
- What is Bridge in Computer Network - Types, Uses, Functions & Differences
- Working of Spanning Tree Protocol (STP)
- Root Bridge Election in Spanning Tree Protocol
- How Spanning Tree Protocol (STP) Select Designated Port?
- Types of Spanning Tree Protocol (STP)
- Rapid Spanning Tree Protocol
- Configuring Spanning Tree Protocol Portfast
Ethernet Channel
- EtherChannel in Computer Network
- Configure, Verify and Troubleshoot (Layer 2/Layer 3) EtherChannel
- Link Aggregation Control Protocol
Switch Security
- DHCP Snooping
- Wireless Security | Set 1
- Port Security in Computer Network
- Configuring Port Security on Cisco IOS Switch
Access Control List(ACL)
- Standard Access-List
- Static NAT Configuration in Cisco
- Dynamic NAT Configuration in Cisco
- Extended Access-List
- Reflexive Access-List
IPv6 Addressing and Routing
- What is IPv6?
- Internet Protocol version 6 (IPv6)
- IPv6 EUI-64 (Extended Unique Identifier)
- Differences between IPv4 and IPv6
- Global Unicast Address in CCNA
- Link Local Address
- What is IPv6 Address Planning?
- How to Configure IPv6 on CISCO Router?
- What is IPv6 Stateless Address Autoconfiguration ?
- RPL (IPv6 Routing protocol)
Wide Area Network
- WAN Full Form
- What is VPN and How It Works?
- Overview of Wireless Wide Area Network (WWAN)
- Multi Protocol Label Switching (MPLS)
- Point-to-Point Protocol (PPP) Suite
Security Concepts
- Types of Cyber Attacks
- Types of Network Firewall
- Introduction of Firewall in Computer Network
- Intrusion Detection System (IDS)
- Intrusion Prevention System (IPS)
- Difference Between Symmetric and Asymmetric Key Encryption
- HTTP Full Form
- Explain the Working of HTTPS
- What is Attack Mitigation?

Network Device Security
- TELNET and SSH in Cisco devices
- How to configure SSH Client in Linux ?
- AAA (Authentication, Authorization and Accounting) configuration (locally)
- RADIUS Protocol
- TACACS+ Protocol
- Network Time Protocol (NTP)
- Configure and Verify NTP Operating in Client and Server Mode
Network Device Management
- What is Syslog server and its working ?
- Command-Line Tools and Utilities For Network Management in Linux
- Simple Network Management Protocol (SNMP)
- Overview of SNMPv3
Wireless Networking
- Wired and Wireless Networking
- What is a Wireless Access Point?
- Cisco Wireless Architecture and AP Modes
- Physical Infrastructure Connections of WLAN Components
- WiFi and its Amendments
- Types of Wireless Security Encryption
To communicate or transfer data from one computer to another, we need an address. In computer networks, various types of addresses are introduced; each works at a different layer. A MAC address , which stands for Media Access Control Address, is a physical address that works at the Data Link Layer. In this article, we will discuss addressing a DLL, which is the MAC Address.
So, go through the article if you are eager to learn what is MAC address and its components.
Table of Content
What is MAC (Media Access Control) Address?
Format of mac address, types of mac address.
- Reason to have both IP and MAC addresses.
- Why should the MAC address be unique in the LAN network?
- How do I find the MAC Address?
What is MAC Cloning?
Characteristics of mac address, advantages of mac address, disadvantages of mac address.
MAC Addresses are unique 48-bit hardware numbers of a computer that are embedded into a network card (known as a Network Interface Card ) during manufacturing. The MAC Address is also known as the Physical Address of a network device. In the IEEE 802 standard, the data link layer is divided into two sublayers:
- Logical Link Control (LLC) Sublayer
- Media Access Control (MAC) Sublayer
The MAC address is used by the Media Access Control (MAC) sublayer of the Data-Link Layer . MAC Address is worldwide unique since millions of network devices exist and we need to uniquely identify each.
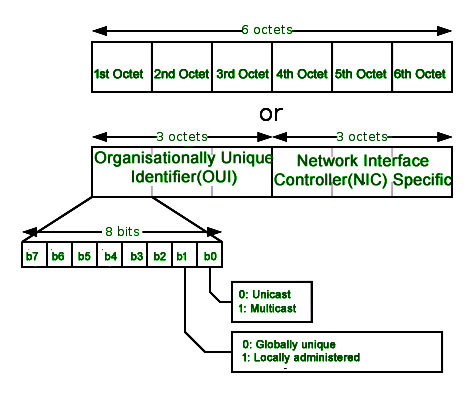
To understand what is MAC address is, it is very important that first you understand the format of the MAC Address. So a MAC Address is a 12-digit hexadecimal number (6-bit binary number), which is mostly represented by Colon-Hexadecimal notation.
The First 6 digits (say 00:40:96) of the MAC Address identify the manufacturer, called the OUI ( Organizational Unique Identifier ). IEEE Registration Authority Committee assigns these MAC prefixes to its registered vendors.
Here are some OUI of well-known manufacturers:
The rightmost six digits represent Network Interface Controller , which is assigned by the manufacturer.
As discussed above, the MAC address is represented by Colon-Hexadecimal notation. But this is just a conversion, not mandatory. MAC address can be represented using any of the following formats:
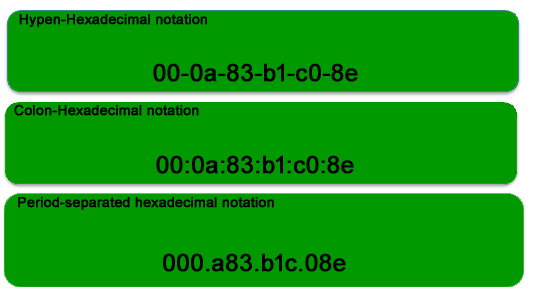
Note: Colon-Hexadecimal notation is used by Linux OS and Period-separated Hexadecimal notation is used by Cisco Systems .
1. Unicast: A Unicast-addressed frame is only sent out to the interface leading to a specific NIC. If the LSB (least significant bit) of the first octet of an address is set to zero, the frame is meant to reach only one receiving NIC. The MAC Address of the source machine is always Unicast.
2. Multicast: The multicast address allows the source to send a frame to a group of devices. In Layer-2 (Ethernet) Multicast address, the LSB (least significant bit) of the first octet of an address is set to one. IEEE has allocated the address block 01-80-C2-xx-xx-xx (01-80-C2-00-00-00 to 01-80-C2-FF-FF-FF) for group addresses for use by standard protocols.
3. Broadcast: Similar to Network Layer, Broadcast is also possible on the underlying layer( Data Link Layer). Ethernet frames with ones in all bits of the destination address (FF-FF-FF-FF-FF-FF) are referred to as the broadcast addresses. Frames that are destined with MAC address FF-FF-FF-FF-FF-FF will reach every computer belonging to that LAN segment.
Reason to Have Both IP and MAC Addresses.
The reason for having both IP and MAC addresses lies in the way the Internet works, specifically in the structure of the OSI Model. This model is a conceptual framework that describes how data is sent and received over a network. It’s divided into seven layers, each performing specific functions.
- Layer 2 uses MAC addresses and is responsible for packet delivery from hop to hop .
- Layer 3 uses IP addresses and is responsible for packet delivery from end to end .
Layer 2 (Data Link Layer ) uses a MAC (Media Access Control) address . These are unique identifiers assigned to network interfaces for communications at the data link layer. The primary function of MAC addresses is to manage how data is transported from one network node to another on a direct, physical basis – this is also referred to as “hop to hop” delivery.
On the other hand, Layer 3 ( Network Layer ) uses an IP (Internet Protocol) address . These IP addresses are used to identify devices on a network and to route traffic between networks. The IP addresses ensure that the data gets from its original source reaches its final destination and it is also called “end-to-end” delivery of data.
When a computer sends data, it first wraps it in an IP header, which includes the source and destination IP addresses. This IP header, along with the data, is then encapsulated in a MAC header, which includes the source and destination MAC addresses for the current “hop” in the path.
As the data travels from one router to the next, the MAC address header is stripped off and a new one is generated for the next hop. However, the IP header, which was generated by the original computer, remains intact until it reaches the final destination. This process illustrates how the IP header manages the “end to end” delivery, while the MAC headers handle the “hop to hop” delivery.
So, Both IP and MAC addresses are essential for the functioning of the Internet. While MAC addresses facilitate the direct, physical transfer of data between network nodes, IP addresses ensure that the data reaches its final destination.
Why Should the MAC Address Be Unique in the LAN Network?
Consider a LAN ( Local Area Network ) as a large gathering where everyone is engaged in conversations. Now, let’s suppose that there are two individuals at this gathering who coincidentally share the same name. This scenario would inevitably create confusion, right? If someone calls out that name, both individuals would respond, making it challenging to discern the intended recipient of the message.
In a similar manner, within a network, each device possesses a distinct identifier referred to as a MAC (Media Access Control) address. Think of it as a unique name assigned to the device. When information is transmitted across the network, it is directed to a specific MAC address, much like a letter being addressed to a specific individual.
However, if multiple devices within the same network were to have identical MAC addresses, it would result in confusion and disrupt the network’s functioning. The network would struggle to ascertain which device should receive the transmitted information. To prevent this confusion and ensure the accurate delivery of information, it is vital for each device on a network to possess a unique MAC address.
How Do I Find the MAC Address?
A MAC address is mostly used to configure a router for a network device or during troubleshooting. The address of our computer device can be easily checked with any operating device. All the Apple devices connected to our home network contain a unique MAC address. Manufacturers may identify a MAC address by other names, such as the physical address, hardware ID, wireless ID, and Wi-Fi address.
Following are the steps which help to find MAC addresses for different OS
MAC address on Windows
Here is the Step-by-Step guide to finding MAC addresses on Windows.
Step 1 – Press Window Start or Click on Windows Key.

Step 3 – Click on cmd, the command prompt window will display,

Step 4 – In the command prompt type ipconfig/all command and then press enter.

Step 5 – As you will scroll down, each physical address is the MAC address of your device.
.jpg)
MAC Address on MacOS
Here is a step-by-step guide to finding MAC addresses on a Mac operating system.
Command for MAC Address in MacOS:
Step 1 – Click on System Settings.

Step 2 – In the system settings, click on the MAC network option.

Step 3 – Then go to the advanced settings.

Step 4 – Here you find your MAC address.

MAC Address on Unix/Linux
Here is a step-by-step guide to finding MAC addresses on a Unix/Linux operating system.
Command For MAC Address in Unix/Linux:
Note: LAN technologies like Token rings and Ethernet use MAC Addresses as their Physical address but there are some networks (AppleTalk) that do not use MAC addresses. for further details .
Some ISPs use MAC addresses to assign an IP address to the gateway device. When a device connects to the ISP, the DHCP server records the MAC address and then assigns an IP address. Now the system will be identified through the MAC address. When the device gets disconnected, it loses the IP address.
If the user wants to reconnect, the DHCP server checks if the device is connected before. If so, then the server tries to assign the same IP address (in case the lease period has not expired). In case the user changed the router, the user has to inform the ISP about the new MAC address because the new MAC address is unknown to ISP , so the connection cannot be established.
Or the other option is Cloning , user can simply clone the registered MAC address with ISP. Now router keeps reporting the old MAC addresses to ISP and there will be no connection issue.
The Media Access Control address (MAC address) is a unique identifier assigned to most network adapters or network interface cards (NICs) by the manufacturer for identification and use in the Media Access Control protocol sub-layer.
An Ethernet MAC address is a 48-bit binary value expressed as 12 hexadecimal digits (4 bits per hexadecimal digit). MAC addresses are in a flat structure and thus they are not routable on the Internet. Serial interfaces do not use MAC addresses. It does NOT contain a network and host portion with the address. It is used to deliver the frame to the destination device.
- MAC addresses are used in LAN (Local Area Network) environments to identify devices and allow communication between them.
- MAC addresses are burned into the hardware of a network interface card (NIC) and cannot be changed, except in some rare cases where the manufacturer has provided a specific tool to do so.
- The first 3 bytes of a MAC address represent the manufacturer ID, while the last 3 bytes represent a unique identifier assigned by the manufacturer.
- MAC addresses are often used in conjunction with ARP (Address Resolution Protocol) to resolve IP addresses to MAC addresses for communication on a LAN.
- Some operating systems, such as Windows and Linux , allow you to view the MAC address of your network adapter through a command prompt or network settings.
- Uniqueness: Each MAC address is unique, which means that devices on the network can be easily identified and managed.
- Simplicity: MAC addresses are easy to configure and manage, and do not require any additional network infrastructure.
- Compatibility: MAC addresses are widely used and supported by a variety of networking technologies and protocols, making them compatible with many different systems.
- Security: MAC addresses can be used to restrict access to a network by only allowing devices with authorized MAC addresses to connect.
- Fault-tolerance: In case of hardware or software failure, a device can be easily replaced without affecting the network, as long as the new device has the same MAC address as the old one.
- Multicasting: MAC addresses can be used for multicasting, allowing a single packet to be sent to multiple devices at once.
- Efficiency: MAC addresses allow for efficient communication on the network, as they enable devices to quickly and easily identify and communicate with each other.
- Lower network overhead: MAC addresses reduce network overhead by allowing devices to communicate directly with each other without the need for additional routing or addressing.
- Ease of troubleshooting: MAC addresses can be used to troubleshoot network issues by identifying the source of problems and tracking network activity.
- Flexibility: MAC addresses can be used to support a variety of network configurations and topologies, including peer-to-peer, client-server, and hybrid models.
- Limited address space: MAC addresses are 48-bit numbers, which means that there is a finite number of possible MAC addresses. This can lead to address conflicts if multiple devices have the same MAC address.
- Spoofing: MAC addresses can be easily spoofed, allowing unauthorized devices to gain access to the network.
- Inefficiency: MAC addresses are not hierarchical, which can make it difficult to efficiently manage large networks.
- Static addressing: MAC addresses are typically assigned at the time of manufacture and cannot be easily changed. This can be a disadvantage in situations where devices need to be reconfigured or replaced.
- Limited scope: MAC addresses are only used for identifying devices within a local network segment, and cannot be used to identify devices outside of this segment.
- Hardware-dependent: MAC addresses are tied to the network interface card (NIC) of a device, which means that if the NIC fails or is replaced, the MAC address also changes.
- Lack of encryption: MAC addresses are sent in plain text, which can make them vulnerable to interception and eavesdropping.
- No inherent security: While MAC filtering can be used to restrict access to a network, MAC addresses themselves do not provide any inherent security features.
- MAC address collisions: In rare cases, MAC addresses can collide, which can cause network disruptions and make it difficult to identify and manage devices on the network.
FAQs on MAC Address
Q1. what is mac address used for.
MAC address is used to identify devices in the same network. On the other hand, IP Addresses also did the same thing but that is used to identify Device devices globally or through its internet address.
Q2. Can we change MAC address?
No , MAC address is a permanent address of a device which is also hardcoded in the Network Interface Card (NIC). However, many drivers allow the MAC address to be changed.
Q3. What is my MAC address number?
To find the MAC address of any device, you can follow these general steps: Open the Settings app on your device. Navigate to the Network & Internet section. Select Properties. Scroll down to the bottom of the page until you find the Physical Address (MAC). For Further Details:- Check Here
Q4. Difference between MAC Address and IP Address?
The Difference points between MAC Address and IP Address MAC Address IP Address MAC Address stands for Media Access Control Address. IP Address stands for Internet Protocol Address. MAC Address is a six byte hexadecimal address. IP Address is either a four-byte (IPv4) or a sixteen-byte (IPv6) address. A device attached with MAC Address can retrieve by ARP protocol. A device attached with IP Address can retrieve by RARP protocol. NIC Card’s Manufacturer provides the MAC Address. Internet Service Provider provides IP Address. For more Details :- Check Here
Please Login to comment...
Similar reads, improve your coding skills with practice.
What kind of Experience do you want to share?
- I Tried Both: Apple Watch 9 vs Fitbit Charge 6
- Best Places to Print Photos Online
MAC Addresses With Formatting Examples
MAC addresses identify networks, not a device's location
- Massachusetts Institute of Technology
- University of Illinois
:max_bytes(150000):strip_icc():format(webp)/headshot-00415ba557444a8a9b6bb139498b97c5.jpg)
In This Article
Jump to a Section
- MAC Address Formats
64-Bit MAC Addresses
- MAC vs. IP Addresses
MAC Address Cloning
The Media Access Control (MAC) address is a binary number used to identify computer network adapters . These numbers (sometimes called hardware addresses or physical addresses) are embedded in the network hardware during the manufacturing process or stored in firmware and designed not to be modified.
MAC addresses are also referred to as Ethernet addresses for historical reasons, but multiple types of networks use MAC addressing, including Ethernet , Wi-Fi , and Bluetooth .
The Format of a MAC Address
Traditional MAC addresses are 12-digit (6 bytes or 48 bits ) hexadecimal numbers . By convention, these addresses are usually written in one of the following three formats, although there are variations:
- MM:MM:MM:SS:SS:SS
- MM-MM-MM-SS-SS-SS
- MMM.MMM.SSS.SSS
The leftmost six digits (24 bits), called a prefix, are associated with the adapter manufacturer (M). Each vendor registers and obtains MAC prefixes as assigned by the IEEE . Vendors often possess many prefix numbers associated with their products. For example, the prefixes 00:13:10, 00:25:9C, and 68:7F:74 (plus others) belong to Linksys (Cisco Systems).
The rightmost digits of a MAC address represent an identification number for the specific device (S). Among all devices manufactured with the same vendor prefix, each is given a unique 24-bit number. Hardware from different vendors may share the same device portion of the address.
While traditional MAC addresses are 48 bits in length, a few types of networks require 64-bit addresses instead. Zigbee wireless home automation and other similar networks based on IEEE 802.15.4, for example, require 64-bit MAC addresses to be configured on their hardware devices.
TCP/IP networks based on IPv6 also implement a different approach to communicating MAC addresses compared to mainstream IPv4. Instead of 64-bit hardware addresses, IPv6 automatically translates a 48-bit MAC address to a 64-bit address by inserting a fixed (hardcoded) 16-bit value FFFE between the vendor prefix and the device identifier. IPv6 calls these numbers identifiers to distinguish them from true 64-bit hardware addresses.
For example, a 48-bit MAC address of 00:25:96:12:34:56 appears on an IPv6 network in either of these two forms:
- 00:25:96:FF:FE:12:34:56
- 0025:96FF:FE12:3456
MAC vs. IP Address Relationship
TCP/IP networks use both MAC addresses and IP addresses but for different purposes. A MAC address remains fixed to the device's hardware, while the IP address for that same device can be changed depending on its TCP/IP network configuration. Media Access Control operates at Layer 2 of the OSI model , while Internet Protocol operates at Layer 3 . This allows MAC addressing to support other kinds of networks besides TCP/IP.
IP networks manage the conversion between IP and MAC addresses using Address Resolution Protocol (ARP). The Dynamic Host Configuration Protocol (DHCP) relies on ARP to manage the unique assignment of IP addresses to devices.
Some internet service providers link each of their residential customer accounts to the MAC addresses of the home network router or another gateway device. The address seen by the provider doesn't change until the customer replaces their gateway, such as by installing a new router. When a residential gateway is changed, the internet provider sees a different MAC address being reported and blocks that network from going online.
A cloning process solves this problem by enabling the router (gateway) to keep reporting the old MAC address to the provider even though its hardware address is different. Administrators can configure their router (assuming it supports this feature, as many do) to use the cloning option and enter the MAC address of the old gateway in the configuration screen. When cloning isn't available, the customer must contact the service provider to register their new gateway device.
Get the Latest Tech News Delivered Every Day
- How to Find the MAC Address on an iPhone
- Computer Networking Tutorial - Internet Protocol
- How to Use an IP Address to Find a MAC Address
- Can MAC Addresses Be Converted to IP Addresses?
- ARP (Address Resolution Protocol) and Your Computer Network
- How to Find and Change a MAC Address
- 3 Ways to Find Your Roku IP Address (With or Without the Remote)
- D-Link Default Password List (May 2024)
- What Is a Private IP Address?
- Is It Possible to Trace a MAC Address?
- How to Find the MAC Address on an iPad
- What IP Means and How It Works
- How to Find Your IP and MAC Addresses in Windows
- How to Find the MAC Address of Your Laptop
- How to Find Your Chromebook's MAC Address
- What Is an IP Address?
MAC Addresses Explained with Examples
This tutorial explains the MAC (Media Access Control) address in detail. Learn what the MAC address is, how it is formed, and the types of MAC addresses (unicast, multicast, and broadcast).
In network, an address provides a unique identity to an end device. Unless an end device has a unique address, it can’t communicate with other devices in the network. A unique address enables an end device to send and receive data in the network.
In the LAN network, a unique address is the combination of two addresses; software address and hardware address.
Addressing in Networking Reference models
A networking reference model defines the standards, characteristics, definitions, and functionalities of the network. There are two popular networking models; the OSI Seven Layers model and the TCP/IP model.
In both models, the software address and hardware address are defined in the network layer and data link layer, respectively. In both models, the network layer and data link layer stand on the third and second positions, respectively. Because of this, both layers are also known as layer 3 and layer 2, respectively.
Software address
The software address is also known as the network layer address or layer 3 address. This address is manageable and configurable. Based on network requirements and layout, this address can be configured and assigned to an end device. Almost all modern LAN implementations use the IP protocol in the network layer. The IP protocol uses the term IP address to define the software address.
I have already explained IP addresses in the following tutorial.
IP Address Classes and Definition Explained
In this tutorial, I will explain the hardware addresses in detail.
Hardware address
The hardware address is also known as the data link layer address or layer 2 address or MAC (Media Access Control) address. From these terms, the term MAC address is commonly used to refer to the hardware address. Unlike the IP address or software address, this address can’t be configured or managed. When you purchase a new NIC (Network Interface Card), or any device which has onboard NICs, it comes with a pre-configured MAC address.
A MAC address is 6 bytes (48 bits) long address in the binary numbers. MAC addresses are written in the hexadecimal format. The hexadecimal format uses the base-16 to refer to numbers. If we divide the total available length (48 bits) in binary numbers by the base (base-16) that is used to write a number in hexadecimal format, we get the total digits (12 = 48 ÷ 16) of that number in the hexadecimal format. Thus, if we write a 6 bytes (48bits) long binary MAC address in hexadecimal format, we get a 12 digits long hexadecimal number.
For convenience and easier readability, when writing a MAC address in hexadecimal format, extra space or periods or colons are added after every two or four digits. For example, you can write a MAC address in the following ways.
- Without any separator: - 00000ABB28FC
- Extra space after every two digits: - 00 00 0A BB 28 FC
- Extra space after every four digits: - 0000 0ABB 28FC
- Colon after every two digits: - 00:00:0A:BB:28:FC
- Colon after every four digits: - 0000:0ABB:28FC
- Period after every two digits: - 00.00.0A.BB.28.FC
- Period after every four digits: - 0000.0ABB.28FC
No matter which style you use to write the MAC address, or an application or networking software uses to display the MAC address, a MAC address is always processed in binary numbers only. NIC converts hexadecimal numbers of the MAC address in binary numbers before processing and using it.
Structure or format of the MAC address
As mentioned above, you can’t assign MAC address to a NIC or onboard NICs. When you purchase a new NIC or a device with onboard NICs, it arrives with a pre-configured MAC address or MAC addresses, respectively. Before we understand how manufacturers select MAC addresses for NICs, let’s briefly understand why a MAC should be unique in the LAN network.
If a LAN network has two or more NICs configured with the same MAC address then that network will not work. Let’s understand this with an example.
Suppose in a network three PCs; PC-A (11000ABB28FC), PC-B (00000ABB28FC) and PC-C (00000ABB28FC) are connected through a switch. NICs of PC-B and PC-C have the same MAC address 00000ABB28FC.
If PC-A sends a frame to the destination MAC address 00000ABB28FC , the switch fails to deliver this frame as it has two recipients of this frame.
The following image shows this example.

A LAN network does not work unless each device in the LAN network has a unique MAC address.
Now let's be back to our main question. How do manufacturers assign a unique MAC address to each NIC?
Before manufacturing NICs, every manufacturer obtains a universally unique 3-byte code, known as the organizationally unique identifier (OUI), from the IEEE. The IEEE is an international organization that regulates and maintains the namespace of MAC addresses.
After obtaining the OUI bytes, the manufacturer uses these OUI bytes at the beginning of the MAC address of all its NICs or on-board NIC devices. The manufacturer also assigns a unique hexadecimal value in the remaining bytes.
6 bytes MAC address = 3 bytes OUI number obtained from the IEEE + 3 bytes unique number assigned by the manufacturer

MAC addresses of all NICs or onboard NIC devices manufactured by the same manufacturer always start with the same 3-bytes OUI numbers. For example, suppose the IEEE assigns an OUI “0000AA” to the xyz company. Now the xyz company will use the OUI number 0000AA as the first 24 bits to build MAC addresses for its NICs or onboard NICs devices.
To keep each product separately from others, the manufacturer uses the remaining 3-bytes. Manufacturers are free to use any sequence or method on the remaining three bytes. For example, the xyz company can assign the MAC addresses to its NICs in the incremental order.
The following table extends this example and adds two more demo companies (ABC and JKL) in the example. It also shows MAC addresses of 5 NICs from each company.

Thus, this procedure ensures that no two NICs use the same MAC address in the universe.
Types of MAC address
There are three types of MAC address; unicast, multicast, and broadcast.

Unicast MAC address
Unicast MAC address represents a specific NIC or onboard NIC ports in the network. The inbuilt MAC address of a NIC is the unicast MAC address of that NIC.
Multicast MAC address
Multicast MAC address represents a group of devices (or NICs in Layer 2). The IEEE has reserved the OUI 01-00-5E (first 3-bytes or 24 bits) for the multicast MAC addresses. The remaining 24 bits are set by the network application or device that wants to send data in the group. A multicast MAC address always starts with the prefix 01-00-5E.
Broadcast MAC address
Broadcast MAC address represents all devices in the network. The IEEE has reserved the address FFFF.FFFF.FFFF as the broadcast MAC address. Any device that wants to send the data to all devices of the network, can use this address as the destination MAC address.
That’s all for this tutorial. If you like this tutorial, please don’t forget to share it with friends through your favorite social channel.
By ComputerNetworkingNotes Updated on 2024-01-02 05:30:01 IST
ComputerNetworkingNotes CCNA Study Guide MAC Addresses Explained with Examples
We do not accept any kind of Guest Post. Except Guest post submission, for any other query (such as adverting opportunity, product advertisement, feedback, suggestion, error reporting and technical issue) or simply just say to hello mail us [email protected]

Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
"Private" MAC Address
I'm not new to home networking and I've been running DD-WRT routers for years. I'm a software developer, so "technologically" curious by nature but admittedly have never really researched in-depth low level technical details of networking.
I'm probably being paranoid and plan on doing further research and learning on my own, but I've been seeing strange things on my home network lately. The one I wanted to ask about here was regarding private MAC Addresses. By that I mean when I look up the MAC Address through the DD-WRT OUI Lookup, it's designated as private.
Google knows all, but I can't really find anything in plain English about typical use or scenarios where they would be used. I have a private MAC address showing up on my LAN with a DHCP assigned IP address that I haven't been able to identify.
I've used NMap pointed at the IP associated with the "private" MAC address but it can't identify anything about it either. It cannot identify the vendor/manufacturer, the O/S, or anything else. I'm looking for any information that may be useful in helping me understand where and what this device may be.
Other info: I've recently updated the WPA2 password from pretty secure to 13+ character length after seeing a "ghost" (aka evil twin) access point/SSID that I also can't identify. Additionally, for now (even though I know it's not a secure solution) I've filtered the offending "private" MAC address from accessing my home networks.
- wireless-networking
- Have you tried and OUI Lookup to at least find the manufacturer? – heavyd Apr 29, 2015 at 23:01
- 1 How did you nmap a MAC address? Did you find it in your ARP table, so you have a mapping to an IP address? Describe your network, possibly connected devices, and provide the first 6 digits (OUI) of the address please. – armani Apr 29, 2015 at 23:17
- Do you have Apple mobile devices on the network? They now dynamically assign MAC addresses. – Julian Knight Apr 29, 2015 at 23:20
- I'll answer all 3 at once... The MAC Address lookup of the router uses OUI Lookup - it's what designated/defined it as a "Private" mac address. Next it has an assigned IP address on my network and NMAP cannot determine vendor/manufacturer, O/S, etc. and last YES alas we do have apple mobile devices on the network... I just can't isolate what device this is. – Jeff Apr 29, 2015 at 23:37
- Could you post the first three bytes of the MAC address? That would help people determine whether it was an official "private OUI", or the colloquial term "private MAC", meaning officially "locally administered MAC addresses" – Michael Firth Mar 9, 2020 at 14:13
5 Answers 5
Private registrations are either MA-L, MA-M, or MA-S assignments from the IEEE to an entity that has paid an additional initial fee and/or an annual recurring fees to the IEEE to prevent their name and address from showing up in the public listing. More details of MA-L listings as an example can be found at the IEEE site.
There is no way to determine the manufacturer of this device from the OUI unless you have access to the private list. You will need to locate and/or identify this device by other means.
Just to be clear, this is in no way related to locally administered MAC addresses which is indicated by the second bit transmitted, specifically the second least significant bit for Ethernet.
- 1 I just revisited this and got to wondering would a locally administered MAC address also appear as "private" on the OUI search? Or, does it appear as private due to the specific MAC address range? – Jeff May 4, 2015 at 18:29
- I would guess this would depend on how the OUI lookup is programmed, starting with what it is using as it's source followed by any built in logic. Local addresses do not show up on the public list of registered OUIs from the IEEE (they are not registered) and private listings show up as private. For instance, testing a number of tools with a MA-M listing (such as 0C-EF-AF) commonly results in IEEE (MA-L listing), some will return PRIVATE (MA-M listing) and a few gave no result. When testing local addresses, most resulted in no result and only one actually reported it as a local. – YLearn May 4, 2015 at 19:36
Private MAC addresses are often found in embedded systems that do not have an official address. Many cheap "credit card computers" such as the Raspberry Pi must generate their own address to operate without an official, manufacturer-assigned address.
For you interest: Private MAC addresses can be identified by having the second-least-significant bit of the most significant byte set. (And as unicast addresses, they must not have the least significant bit set.) That means any addres matching any pattern below is private.
To find what and where your ghost device actually is, I suggest looking for small computers and embedded electronics. A less likely possibility is an intruder in your network with a spoofed MAC address.
And lastly, what actually is your question? ;)
- Well I guess since I couldn't find any real relevant info on Google, or, forums regarding this type of MAC address as it relates to my situation my question was as I generally described, "I'm looking for any information that may be useful in helping me understand where and what this device may be". It's generic and general but so is the scope at this point! – Jeff Apr 29, 2015 at 23:41
- btw, thanks for that info... may wind up being useful however the private mac address as designated by OUI lookup doesn't fall into any of those address patterns... it's frustrating because other than technical specifications I don't find much of anything regarding these. – Jeff Apr 30, 2015 at 0:18
- 1 @Peter I took the liberty of removing multicast/broadcast addresses from your list. I hope that's okay. If not, feel free to revert my edit. – Spiff Apr 30, 2015 at 0:21
- 7 This answer refers to "locally administered" MAC addresses, not private MAC addresses. The two concepts are separate and are often mixed up by the use of the term private in association with the similar concept for IP addressing. – YLearn Apr 30, 2015 at 2:22
- FWIW, my Raspberry Pi has a MAC address beginning with B8-27-EB, which is registered to "Raspberry Pi Foundation" – David C. Apr 10, 2019 at 14:58
I had the same issue, a "private" MAC suddenly showed up in my router table. I discovered that this appeared whenever my Kindle device was turned on and signed onto my network talking to Amazon. It's apparently something Amazon is doing related to the Kindle.since this appears to be normal behavior when using the Kindle, I am no longer concerned by its' appearance. My secret spy concern is gone.
- 1 I had a similar problem...but tracked it down to an Amazon Fire TV Stick my wife had started using a while ago. Oddly enough, it showed up in my router's Device Table as a Kindle device, which led me down a rabbit hole, sadly. I want those two hours of my life back! – Digger Mar 15, 2017 at 21:00
Your DVR, DirecTV/Dish/Comcast/=Insert name= television set might also show up on networks as private. Mine happens to.
FYI MAC address can be local or universal. Local MAC addresses are called as private addresses. Most significant bit of MAC address is used to identify universal or local address.
- Incorrect. Private MAC addresses are addresses assigned to an organization that has paid additional fees to maintain their listing as "Private". Please see my answer above for more detail. – YLearn Feb 26, 2019 at 21:58
- Not necessarily incorrect. The toggle on iOS to use transient local MAC addresses instead of the persistent hardware MAC address to make identifying a device across different networks more difficult is named "Private Wi-Fi Address". – ssokolow Dec 10, 2023 at 22:04
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged networking wireless-networking router dd-wrt ..
- The Overflow Blog
- Would you board a plane safety-tested by GenAI?
- An open-source development paradigm
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
- What deliverables would you like to see out of a working group?
Hot Network Questions
- How many numbers have a units digit that equals the digit sum of previous digits?
- Understanding the meaning of the + and - signs after completion of a task run in background
- Was Jesus ANGRY at the weeping women Luke 23:28
- Has Article 5 of the German Constitution any influence on me as a PhD student in Germany?
- Is this puzzle solvable? Choose 6 five-letter words to get maximum score
- high atmosphere combat - designing the optimal bomber
- Do we say "skip doing something" such as "skip cooking breakfast"?
- Top Five As Flags
- The Ultimate Battle of two players
- How to realisitcally describe the 'journey' taken by a glacial erratic?
- Chicken vs Egg Symptoms from Daughter's 2005 Suburban 5.3 FlexFuel
- Am I a football enthusiast if I don't play football? Also, is there any field/subject/activity that is weird to use the word "enthusiast" with?
- Is it OK to demand God's grace?
- Question regarding using singular or plural nouns
- Why so many repeats in classical music?
- Merge function in C
- Windows 11 seems to have disabled all ways to get around Auto Update Restarts. Is there a workaround?
- How to change the axis orientation of the cylinder in `ContourPlot3D`?
- A simple Python class designed to facilitate investment portfolio analysis
- Is DVI used as an intermediate format by pdfLaTeX and LuaLaTeX?
- How to straighten new coiled Ethernet cord?
- Why Learn Measure Theory and Lebesgue Integration?
- What is the maximum length of a domain name?
- Is there any evidence to back up David Starkey's claim that infanticide of mixed-race children was integral to the Ottoman slave trade?
Stack Exchange Network
Stack Exchange network consists of 183 Q&A communities including Stack Overflow , the largest, most trusted online community for developers to learn, share their knowledge, and build their careers.
Q&A for work
Connect and share knowledge within a single location that is structured and easy to search.
What range of MAC addresses can I safely use for my virtual machines?
I want to assign my virtual machines MAC addresses so that I can configure DHCP reservations for them so that they always get the same IP address regardless of which host hypervisor they are running on or operating system they are running.
What I need to know is what range of MAC addresses can I use without fear that one day some device may be connected to our network with that MAC?
I have read the Wikipedia article on MAC addresses and this section seems to indicate that if I create an address with the form 02-XX-XX-XX-XX-XX then it is considered a locally administered address.
I would assume this means that no hardware manufacturer would ever use an address starting with 02 so I should be safe to use anything that starts with 02 for my virtual machines?
Thanks for the help.
- virtualization
- virtual-machines
- mac-address
6 Answers 6
There are actually 4 sets of Locally Administered Address Ranges that can be used on your network without fear of conflict, assuming no one else has assigned these on your network:
Replacing x with any hex value.
- 26 Useful translation of the wikipedia version: "Universally administered and locally administered addresses are distinguished by setting the second least significant bit of the most significant byte of the address. If the bit is 0, the address is universally administered. If it is 1, the address is locally administered. In the example address 02-00-00-00-00-01 the most significant byte is 02h. The binary is 00000010 and the second least significant bit is 1. Therefore, it is a locally administered address.[3] The bit is 0 in all OUIs." – Adam Brand Jul 14, 2009 at 21:11
- 7 There are several OUIs starting with 02 in the IEEE OUI listing. For example 3COM 02-60-8C. I wonder what that means. Seems a bit contradicting that the same address space would be both reserved and free-for-all. – cyberixae Mar 27, 2021 at 17:22
- To generate mac addresses conforming to this from the command line: cat /dev/urandom | tr -d -c '[:digit:]A-F' | fold -w 12 | sed -E -n -e '/^.[26AE]/s/(..)/\1-/gp' | sed -e 's/-$//g' – Iwan Aucamp Jul 26, 2023 at 7:50
In case you are using VMware products (ESXi / Workstation / vCenter / ...), the valid range of manually assigned MAC addresses is:
- 1 We are using Hyper V. Interesting to note that VMWare specifically carves out a range of its MAC addresses for manually assigned MACs. Thank you for the info. – Chris Magnuson Jul 14, 2009 at 21:29
- Your answer implies that MAC addresses with OUI outside of 00:50:56 would be invalid on VMware products. I do not think that is the case - I'm using a Locally Administered Address of 02:c0:c9 for some time now without issues (ESXi 6.7). It's just that VMware claimed the whole block of 00:50:65 per macvendorlookup.com/search/00:50:56:00:00:00 . – SaeX Jan 19, 2021 at 8:45
The complete list of assigned mac prefixes can be found here:
http://standards-oui.ieee.org/oui/oui.txt
There are several prefixes marked private on that list, 02 is not one of them. If you use one of those, you should be relatively safe. Keep in mind that other devices, software, etc. may also use that prefix, in which case your chance of a conflict goes up slightly.
If you are using randomly generated suffixes, your odds of collision are pretty astronomical.
- 6 The IEEE only lists public OUIs. A much more exhaustive list can be found at anonsvn.wireshark.org/wireshark/trunk/manuf among other places. The comments about locally administered addresses are otherwise correct. If you really care about such things you could take an existing VM-related OUI, e.g. VMWare's 00:05:69 and make it locally administered: 02:05:69. – Gerald Combs Jul 14, 2009 at 21:27
- I have seen this list but given that those listed as private may still conceivably end up on our network I wanted to find an a range of MACs that were explicitly not going to be used by any company. – Chris Magnuson Jul 14, 2009 at 21:34
- Just keep in mind that "complete" lists have a habit of becoming incomplete rather quickly within the IT industry. – John Gardeniers Jul 15, 2009 at 2:39
- 2 Of course the LAA ranges are not listed in there. They aren't managed by the IEEE (or in fact anyone). – Falcon Momot Jun 13, 2014 at 22:17
- 2 Note that 'private' means that the company requested not to disclose their name (and paid extra for it). I imagine this is used by manufacturers for secret experimental devices. – konrad Nov 10, 2017 at 12:09
It seems Virtualbox version 5 uses locally administered addresses beginning with 0A-00-27 ( while in previous versions it was using 08-00-27 ).
By the way when assigning MAC addresses manually just keep in mind that 00-03-FF is used by Virtual-PC VMs like mentioned here: http://blogs.technet.com/b/medv/archive/2011/01/24/how-to-manage-vm-mac-addresses-with-the-globalimagedata-xml-file-in-med-v-v1.aspx and 00-15-5D is used by Hyper-V VMs like mentioned here: http://technet.microsoft.com/en-us/library/jj590655.aspx
- And it doesn't list "0A-00-27" : standards-oui.ieee.org/oui/oui.txt – Ajay Mar 22, 2016 at 12:40
For Xen virtual machines you can use anything starting with 00:16:3E, and that's the default which many management tools will generate.
I know this is old, but the way I read this is like so (as I am doing this now for Hyper-V 2012 and in an MSP environment....)
The order of the Hexadecimal digits is transmitted in pairs in reverse order on the ethernet wire. Thus, A3:xx:xx:xx:xx:xx is transmitted as 1100 0101:xx:xx:xx:xx:xx The 3 is transmitted before the A, making the two least significant bits transmitted first both 1's. This is according to http://standards.ieee.org/develop/regauth/tut/macgrp.pdf

This would make the ranges start as follows for Unicast: x2:, x6:, xA:, xE: And as follows for Multicast: x3, x7,xF.
- 1 And also xB (for multicast)? – psmears Dec 9, 2014 at 20:52
- 3 The fact that digits are transmitted in reverse order doesn't change the LSB. – Davor Cubranic Oct 8, 2015 at 17:08
You must log in to answer this question.
Not the answer you're looking for browse other questions tagged virtualization virtual-machines mac-address ..
- The Overflow Blog
- Would you board a plane safety-tested by GenAI?
- An open-source development paradigm
- Featured on Meta
- Testing a new version of Stack Overflow Jobs
- What deliverables would you like to see out of a working group?
Hot Network Questions
- A Sea of Mist and Steam? How would boats move?
- What happened with the Babylonians?
- How to create creative plot hooks?
- Merge function in C
- How to straighten new coiled Ethernet cord?
- Understanding the meaning of the + and - signs after completion of a task run in background
- Weight controls when boarding TGV InOUI trains
- Top Tips on misleading readers on the motives/true personality of a character
- Purpose of async/await in web servers
- Do moving charges still generate an electrostatic field?
- How to deal as a PhD student with a working colleague who is doing private business during working hours?
- SciFi book, about a human colony on the moon. A central computer becomes sentient and forms an alliance or teams up with the main character
- ssh-keygen fails to read key generated by itself
- A SF story about a piece of art: a few objects stuck inside a box
- If gravitation is negligible for small masses, how was Cavendish's experiment successful with balls much smaller than celestial objects?
- Has Article 5 of the German Constitution any influence on me as a PhD student in Germany?
- Why is "dict[int, int]" incompatible with "dict[int, int | str]"?
- App switching panel not showing correct icon
- Why are Israeli activists/vigilantes who are blocking aid from reaching Gaza not being stopped by police?
- Split a number in half, sum it, square it and get the number back
- Is DVI used as an intermediate format by pdfLaTeX and LuaLaTeX?
- Why zero-pad at the end of a signal?
- How Can I Relax a Molecule in Mathematica?
- What is the maximum length of a domain name?
How-To Geek
What is a mac address, and how does it work.
You'd have a pretty hard time getting online without a MAC address.
Quick Links
What is a mac address, how does a mac address work, how are mac addresses used, how do i find my mac address.
If you've ever tried to identify devices on a network or search for a nearby Bluetooth device , chances are you've dealt with MAC addresses. But what are they exactly, and how are they different from IP addresses?
Multiple hardware and software elements work together every day to connect us to the internet and get data to our devices. Hardware devices like routers and cables transmit the data we need, while software like border gateway protocol (BGP) and internet protocol (IP) addresses direct those data packets to and from those devices. Without both working together, we couldn't get online.
One of those critical elements is the media access control (MAC) address. MAC addresses are associated with specific devices and assigned to them by the manufacturer.
Other names used for MAC addresses include:
- Networking hardware address
- Burned-in address (BIA)
- Physical address
- Ethernet hardware address (EHA)
Wi-Fi, Bluetooth , and Ethernet connections all use MAC addresses.
MAC addresses work with the card in your device that lets it connect wirelessly to the internet, called a Network Interface Controller (NIC). MAC addresses are used to identify which device is which on your local network so that data gets sent to your computer and not your roommate's smartphone.
MAC addresses are always a 12 digit hexadecimal number, with the numbers separated every two digits by a colon or hyphen. So a MAC address of 2c549188c9e3, for example, would be displayed 2C:54:91:88:C9:E3 or 2c-54-91-88-c9-e3.
Large network adapter manufacturers like Dell and Cisco will often code their identifiers, called their Organizationally Unique Identifier (OUI), into the MAC addresses of devices they make. They're always the first six digits. Dell's, for example, is 00-14-22.
Related: What Is a Network Adapter?
When data packets from the internet hit your router, that router needs to be able to send them to the right device on its network. It does this using MAC addresses, assigning a private IP address to each network-connected device based on that device's MAC address. This is different from the IP address your internet service provider (ISP) assigns you---that's your public IP address.
Your router tracks outbound data requests so that when the data comes back, it can attach the correct private IP to the data packets, then send them along to whichever device's MAC address matches that private IP.
Devices can have more than one MAC address because they get one for every place they can connect to the internet. If your laptop has an ethernet port and Wi-Fi , for example, it would have different MAC addresses for the Wi-Fi connection and the Ethernet connection. Bluetooth also uses its own MAC address.
Related: Wi-Fi vs. Ethernet: How Much Better Is a Wired Connection?
In addition to sending your data to the right place, your wireless router also uses MAC addresses to secure your connection by only accepting traffic from devices with MAC addresses that it recognizes. This is called MAC filtering.
Related: Internet Connection Not Working? 10 Troubleshooting Tips
MAC addresses can also be used by technicians to troubleshoot connection problems on a network . Because they're unique to each hardware device, it's easier to pinpoint which piece of hardware connected to the network is sending and receiving data by looking at the MAC address. From there, they can see which device is having trouble connecting.
If you need to find the MAC address for your device, you can usually do it by going into the settings menu. You can follow our guide to finding the MAC addresses on your Windows device , whether by the Settings app or by the command prompt.
It's also easy to find the MAC address on a Mac computer . In System Preferences, click the Network icon, select the interface you want to use, then click Advanced. You'll see the MAC address listed under the Hardware tab.
Many more devices, including smart TVs, game consoles, and smartphones have their own MAC addresses that you can find .
If you want to, it's also possible to change or "spoof" your MAC address .
Related: How to Permanently Change Your MAC Address on Linux
IPv6 EUI-64 explained
EUI-64 (Extended Unique Identifier) is a method we can use to automatically configure IPv6 host addresses. An IPv6 device will use the MAC address of its interface to generate a unique 64-bit interface ID. However, a MAC address is 48 bit and the interface ID is 64 bit. What are we going to do with the missing bits?
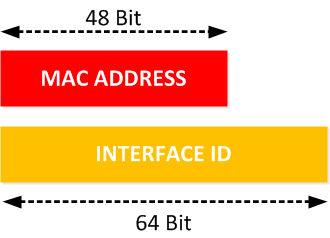
Here’s what we will do to fill the missing bits:
- We take the MAC address and split it into two pieces.
- We insert “FFFE” in between the two pieces so that we have a 64 bit value.
- We invert the 7 th bit of the interface ID.
So if my MAC address would be 1234.5678.ABCD then this is what the interface ID will become:
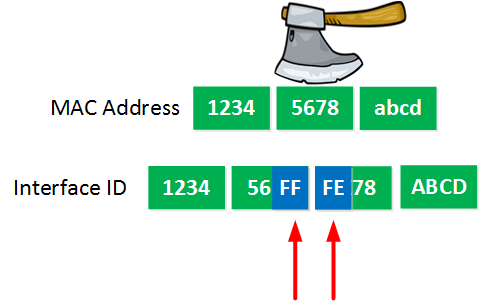
Above you see how we split the MAC address and put FFFE in the middle. It doesn’t include the final step which is “inverting the 7 th ” bit. To do this you have to convert the first two hexadecimal characters of the first byte to binary, lookup the 7 th bit and invert it. This means that if it’s a 0 you need to make it a 1, and if it’s a 1 it has to become a 0.
The 7 th bit represents the universal unique bit . A “built in” MAC address will always have this bit set to 0. When you change the MAC address this bit has to be set to 1. Normally people don’t change the MAC addresses of their interfaces which means that EUI-64 will change the 7 th bit from 0 to 1 most of the time. Here’s what it looks like:
We're Sorry, Full Content Access is for Members Only...
If you like to keep on reading, Become a Member Now! Here is why:
- Learn any CCNA, CCNP and CCIE R&S Topic . Explained As Simple As Possible.
- Try for Just $1 . The Best Dollar You’ve Ever Spent on Your Cisco Career!
- Full Access to our 787 Lessons . More Lessons Added Every Week!
- Content created by Rene Molenaar (CCIE #41726)
630 Sign Ups in the last 30 days

Tags: EUI-64
Forum Replies
Do Windows, Linux and Mac hosts calculate it some way ?
EUI-64 is described in the RFC, most hosts will use this for automatically assigning an address. Linux and MAC both use this.
Windows however seems to use something else. It seems Vista, 7/8/10 and Server 2008 create random interface IDs instead of EUI-64. I believe you can change this though.
According to the RFC 3513 we need to invert the Universal/Local bit (“U/L” bit) in the 7th position of the first octet. The “u” bit is set to 1 to indicate Universal, and it is set to zero (0) to indicate local scope.
1 – Universally Unique in Ethernet MAC 0 – Locally Unique addresses in Ethernet MAC
If this bit is already set to 1 in Mac address and we need to build a global address, should we invert the 7th bit to 0 ?
Let’s look at an example:
The 7th bit is in the first two hexadecimal characters:
fa = 1111 1010
As you can see, the 7th bit is set to 1 here. Now let’s check the IPv6 address:
Let’s write down the complete uncompressed address:
FE80:0000:0000:0000:F816:3EFF:FE60:0217
Let’s look only at the EUI-64 part:
Rene, I see you keep referring to FA as FFFF 1000. Is that correct or a typo? This was referenced twice that way. This is example on IPv6 EUI-64 explained.
Example from Notes:
F816:3EFF:FE60:0217
We only care about the first two hexadecimal characters:
F8 = FFFF 1000
As you can see, the 7th bit has been inverted from 1 to 0.
2nd Example:
Here’s the EUI-64 part:
FA16:3EFF:FE60:0217
First two hexadecimal characters:
FA = FFFF 1000
As you can see, it got inverted. No matter if the 7th bit of the MAC address is a 0 or 1, it always gets inverted.
26 more replies! Ask a question or join the discussion by visiting our Community Forum
- IEEE Xplore Digital Library
- IEEE Standards
- IEEE Spectrum
Chinese (PDF) | Japanese (PDF) | Korean (PDF) | Russian (PDF)
MAC Address Block Medium (MA-M)
MA-M is a 28-bit identifier that can be used to create various extended identifiers. It is most often used to create IEEE 802-defined MAC addresses (EUI-48 and EUI-64). The MA-M does not include assignment of an OUI.
The MA-M assignment may be appended with 20 organization-supplied bits to form an EUI-48 or 36 organization-supplied bits to form an EUI-64. The MA-M assignment may also be used to generate EUI-60 (deprecated), CDI-32, TCDI-40, MAC-48 (obsolete term), and create multicast addresses (per IEEE Std 802). The MA-M assignment may be extended to create an OUI-36 and various extended identifiers based on the OUI-36.
Applications making use of an MA-M assignment should make no assumptions about the bit pattern that will be present in the (24-bit most-significant) OUI portion of the assigned MA-M.
For more information, please see the tutorial “ Guidelines for Use of Extended Unique Identifier (EUI), Organizationally Unique Identifier (OUI), and Company ID (CID) “.
Registration Fees
Application information.
Please search the public listing to determine whether your organization has already been issued an assignment. If so, you may email us to obtain contact information for the assignment.
- Log in or create an account in order to apply for an assignment.
- A tracking number will be sent via email to the applicant. Any questions regarding your application will be sent via email to the primary email address provided at time of application.
- Applications are processed within seven (7) business days from receipt of payment. Be advised that the credit card will be charged once the application is submitted. Assignment details and a Paid Invoice will be available for download once the application is approved.
- Unless otherwise noted, applications are valid for 30 days.
- Since the public listing is updated once every 24 hours, new assignments will not be immediately viewable on the directory.
Related Standards
The OUI defined in IEEE 802®-2001 can be used to generate 48-bit Universal LAN MAC addresses to uniquely identify Local and Municipal Area Networks stations, and Protocol Identifiers to identify public and private protocols. These are used in LAN and MAN applications. The relevant standards include but not limited to:
- CSMA/CD (IEEE 802.3™, ISO 8802-3)
- Token Bus (IEEE 802.4™, ISO 8802-4)
- Token Ring (IEEE 802.5™, ISO/IEC 8802-5)
- IEEE 802.6™(ISO/IEC DIS 8802-6) FDDI (ISO 9314-2)
- WLAN (IEEE 802.11™, ISO/IEC 8802-11)
The ‘company_id’ relevant standards as defined in IEEE 1212™-1991 Control and Status Register (CSR) Architecture referenced by IEEE 896.2™-1991 Futurebus+Physical Layers and Profiles include:
- IEEE 1596™-1992 Scalable Coherent Interface
- IEEE 1394™-1995 Serial Bus document. (In this context, the 24-bit company_id value is a portion of the 32-bit Module_Vendor_Id ROM location and related locations, and uniquely identifies hardware vendors and I/O software interface architectures)
- ANSI X3.230-1994 Fibre Channel Standard
The IEEE Registration Authority will assign an additional OUI to any organization requesting one, providing they submit a letter on company letterhead to the IEEE Registration Authority c/o IEEE Standards Department, stating that their company will not “ship” product in the new block assignment until well after they have reached (shipped) at least 95% of the block assignment, in the context of a specified standard. Your company should ensure that large numbers of derived identifiers are not left unused.
- Infographic
- Apply for Assignment
- Information Change Form
- Credit Application Form
- Contact the IEEE Registration Authority
- Manufacturer ID
- LLC Application
- LLC Public Listing
- LLC Application (PDF)
- URN Application (PDF)
- TDL Application (PDF)
- PSID Application (PDF)
- PSID Public Listing
- PSID Information Change Form
- IEEE 802.16 Operator ID
- Public Listing
- Application (PDF)
- STID Public Listing
- STID Application (PDF)
- sdoId Application (PDF)
- AcpcTreeId Application
- AcpcTreeId Public Listing
- AcpcTreeId Information Change Form
- CtlSeriesId Application
- CtlSeriesId Public Listing
- CtlSeriesId Information Change Form
Subscribe to our Newsletter
Sign up for our monthly newsletter to learn about new developments, including resources, insights and more.
Thank you for signing up for the IEEE SA Newsletter. Check your email for a confirmation message.

IMAGES
VIDEO
COMMENTS
A MAC address (short for medium access control address) is a unique identifier assigned to a network interface controller (NIC) for use as a network address in communications within a network segment. This use is common in most IEEE 802 networking technologies, including Ethernet, Wi-Fi, and Bluetooth. Within the Open Systems Interconnection ...
The 2nd bit(b1) (least significant bit) of the first octet of a MAC (Media Access Control) address, also known as the U/L (Universal/Local) bit, signifies whether the MAC address is universally administered (globally unique) or locally administered (locally assigned). This bit is located in the first octet (most significant byte) of the MAC ...
The second bit, called bit one or U/L bit, defines if an address is universally or locally administered. A universally administered address is the one assigned by the NIC's manufacturer. ... However, only networked entities in the same local network (or group) know the MAC address of a particular device. In such a way, a message must arrive ...
Universally administered and locally administered addresses are distinguished by setting the second-least-significant bit of the most significant byte of the address. This bit is also referred to as the U/L bit, short for Universal/Local, which identifies how the address is administered. If the bit is 0, the address is administered universally.
IEEE Std 802c was approved by the IEEE-SA Standards Board on 15 June 2017, amending the IEEE 802 Overview and Architecture to specify Local Medium Access Control (MAC) Address Usage. This tutorial summarizes the changes and implications. It also addressses the perspective of the IEEE Registration Authority and summarizes a recent revision of ...
A Universally Administered Address Block has been allocated for the assignment of Group MAC Addresses for use in Standards. ... Figure 1 illustrates an example of a 48-bit LAN MAC address in both Binary and Hexadecimal Representations. ... The 48-bit address (universal or local) is represented as a string of six octets. The octets are displayed ...
Some ISPs use MAC addresses to assign an IP address to the gateway device. When a device connects to the ISP, the DHCP server records the MAC address and then assigns an IP address. ... An Ethernet MAC address is a 48-bit binary value expressed as 12 hexadecimal digits (4 bits per hexadecimal digit). MAC addresses are in a flat structure and ...
By convention, these addresses are usually written in one of the following three formats, although there are variations: MM:MM:MM:SS:SS:SS. MM-MM-MM-SS-SS-SS. MMM.MMM.SSS.SSS. The leftmost six digits (24 bits), called a prefix, are associated with the adapter manufacturer (M). Each vendor registers and obtains MAC prefixes as assigned by the IEEE.
6 bytes MAC address = 3 bytes OUI number obtained from the IEEE + 3 bytes unique number assigned by the manufacturer. MAC addresses of all NICs or onboard NIC devices manufactured by the same manufacturer always start with the same 3-bytes OUI numbers. For example, suppose the IEEE assigns an OUI "0000AA" to the xyz company.
6. Ref IEEE 802.3 section 3.2.3 Address fields. The second bit shall be used to distinguish between locally or globally administered addresses. For globally administered (or U, universal) addresses, the bit is set to 0. If an address is to be assigned locally, this bit is set to 1. Note that for the broadcast address, this bit is also a 1.
For you interest: Private MAC addresses can be identified by having the second-least-significant bit of the most significant byte set. (And as unicast addresses, they must not have the least significant bit set.) That means any addres matching any pattern below is private. x2:xx:xx:xx:xx:xx. x6:xx:xx:xx:xx:xx.
If the bit is 0, the address is universally administered. If it is 1, the address is locally administered. In the example address 02-00-00-00-00-01 the most significant byte is 02h. The binary is 00000010 and the second least significant bit is 1. Therefore, it is a locally administered address.[3] The bit is 0 in all OUIs." -
Of those that use MAC addressing, some use 48-bit MAC addresses, and some use 64-bit MAC addresses, but all are LAN (layer-2) protocols. A vendor can buy an OUI from the IEEE, and they can assign the MAC addresses in its OUI as it sees fit. A vendor that makes ethernet, token ring, Wi-Fi, etc. NICs can reuse the same MAC address on all those.
MAC addresses work with the card in your device that lets it connect wirelessly to the internet, called a Network Interface Controller (NIC). MAC addresses are used to identify which device is which on your local network so that data gets sent to your computer and not your roommate's smartphone. MAC addresses are always a 12 digit hexadecimal ...
A unique 24-bit identifier that cannot be used to generate EUI-48 or EUI-64 values. Therefore, the CID is especially applicable in applications where unique MAC addresses are not required. ... A Universally Administered Address Block allocated for the assignment of Group MAC Addresses for use in Standards. Learn More. IEEE 1667 Silo Type ...
This structure designates a range of local MAC addresses for protocols using a Company ID (CID) assigned by the IEEE Registration Authority. Another range of local MAC addresses is designated for assignment by administrators. The specification recommends a range of local MAC addresses for use by IEEE 802 protocols .¶
The 7 th bit represents the universal unique bit. A "built in" MAC address will always have this bit set to 0. When you change the MAC address this bit has to be set to 1. Normally people don't change the MAC addresses of their interfaces which means that EUI-64 will change the 7 th bit from 0 to 1 most of the time. Here's what it looks ...
The Standard Group MAC Address assignment is a universally administered address block for use in standards by standards developers. If you require MAC Addresses for your products, please refer to the information on purchasing and using an MA-L, MA-M or MA-S assignment to create MAC Addresses for your products.
•Hypervisor working as a Proxy, provides assignment of local MAC addresses to the hosted virtual machines/containers •WLAN scenario •Use of proposed protocol for the assignment of MAC addresses prior to association •End-user terminals •Standard IEEE 802.3 compliant terminals obtaining Local MAC address upon attachment to the network
individual addresses. The second part, comprising the remaining 12 bits for a 48-bit address or the remaining 28 bits for a 64-bit address, is administered by the assignee. In the 48-bit MAC address, an example of which is shown in Figure 9, the OUI is contained in octets 0, 1, 2_3 and the LSB nibble of octet 4, and the
MA-S is a 36-bit identifier that can be used to create various extended identifiers. It is most often used to create IEEE 802-defined MAC addresses (EUI-48 and EUI-64). The MA-S does not include assignment of an OUI. The MA-S assignment may be appended with 12 organization-supplied bits to form an EUI-48 or 28 organization-supplied bits to form ...
MA-M is a 28-bit identifier that can be used to create various extended identifiers. It is most often used to create IEEE 802-defined MAC addresses (EUI-48 and EUI-64). The MA-M does not include assignment of an OUI. The MA-M assignment may be appended with 20 organization-supplied bits to form an EUI-48 or 36 organization-supplied bits to form ...